CyberOps Associate 1.02 & CA v1.0 Modules 13 – 17: Threats and Attacks Group Exam Answers Full 100% 2023 2024
These are both versions of NetAcad Cisco CA 1.02 and CyberOps Associate (Version 1.0) – Modules 13 – 17: Threats and Attacks Group Exam Full 100% in 2023 and 2024 verified by experts with explanations and hints.
-
Which cyber attack involves a coordinated attack from a botnet of zombie computers?
- DDoS
- MITM
- ICMP redirect
- address spoofing
Answers Explanation & Hints: DDoS is a distributed denial-of-services attack. A DDoS attack is launched from multiple coordinated sources. The sources of the attack are zombie hosts that the cybercriminal has built into a botnet. When ready, the cybercriminal instructs the botnet of zombies to attack the chosen target.
-
An attacker is redirecting traffic to a false default gateway in an attempt to intercept the data traffic of a switched network. What type of attack could achieve this?
- DHCP snooping
- DHCP spoofing
- MAC address starvation
- MAC address snooping
Answers Explanation & Hints: In DHCP spoofing attacks, an attacker configures a fake DHCP server on the network to issue DHCP addresses to clients with the aim of forcing the clients to use a false default gateway, and other false services. DHCP snooping is a Cisco switch feature that can mitigate DHCP attacks. MAC address starvation and MAC address snooping are not recognized security attacks. MAC address spoofing is a network security threat.
-
What technique is a security attack that depletes the pool of IP addresses available for legitimate hosts?
- reconnaissance attack
- DHCP spoofing
- DHCP snooping
- DHCP starvation
Answers Explanation & Hints: DHCP starvation attacks create a denial of service for network clients. The attacker sends DHCP discovery messages that contain fake MAC addresses in an attempt to lease all of the IP addresses. In contrast, DHCP spoofing occurs when a cybercriminal configures a rogue DHCP server to provide network clients with incorrect IP configuration information.
-
What are two methods used by cybercriminals to mask DNS attacks? (Choose two.)
- reflection
- tunneling
- fast flux
- domain generation algorithms
- shadowing
Answers Explanation & Hints: Fast flux, double IP flux, and domain generation algorithms are used by cybercrimals to attack DNS servers and affect DNS services. Fast flux is a technique used to hide phishing and malware delivery sites behind a quickly-changing network of compromised DNS hosts (bots within botnets). The double IP flux technique rapidly changes the hostname to IP address mappings and the authoritative name server. Domain generation algorithms randomly generate domain names to be used as rendezvous points.
-
What is the result of a passive ARP poisoning attack?
- Confidential information is stolen.
- Data is modified in transit or malicious data is inserted in transit.
- Multiple subdomains are created.
- Network clients experience a denial of service.
Answers Explanation & Hints: ARP poisoning attacks can be passive or active. The result of a passive attack is that cybercriminals steal confidential information. With an active attack, cybercriminals modify data in transit or they inject malicious data.
-
What is the function of a gratuitous ARP sent by a networked device when it boots up?
- to request the netbios name of the connected system
- to request the IP address of the connected network
- to request the MAC address of the DNS server
- to advise connected devices of its MAC address
Answers Explanation & Hints: A gratuitous ARP is often sent when a device first boots up to inform all other devices on the local network of the MAC address of the new device.
-
How can a DNS tunneling attack be mitigated?
- by using a filter that inspects DNS traffic
- by securing all domain owner accounts
- by using strong passwords and two-factor authentication
- by preventing devices from using gratuitous ARP
Answers Explanation & Hints: To be able to stop DNS tunneling, a filter that inspects DNS traffic must be used. Also, DNS solutions such as Cisco OpenDNS block much of the DNS tunneling traffic by identifying suspicious domains.
-
What is a vulnerability that allows criminals to inject scripts into web pages viewed by users?
- Cross-site scripting
- XML injection
- SQL injection
- buffer overflow
Answers Explanation & Hints: Cross-site scripting (XSS) allows criminals to inject scripts that contain malicious code into web applications.
-
What would be the target of an SQL injection attack?
- database
- DHCP
- DNS
- email
Answers Explanation & Hints: SQL is the language used to query a relational database. Cybercriminals use SQL injections to get information, create fake or malicious queries, or to breach the database in some other way.
-
Which protocol is exploited by cybercriminals who create malicious iFrames?
- DNS
- DHCP
- HTTP
- ARP
Answers Explanation & Hints: An HTML element known as an inline frame or iFrame allows the browser to load a different web page from another source.
-
Why would a rootkit be used by a hacker?
- to do reconnaissance
- to try to guess a password
- to gain access to a device without being detected
- to reverse engineer binary files
Answers Explanation & Hints: Hackers use rootkits to avoid detection as well as hide any software installed by the hacker.
-
Which two characteristics describe a worm? (Choose two.)
- executes when software is run on a computer
- is self-replicating
- hides in a dormant state until needed by an attacker
- infects computers by attaching to software code
- travels to new computers without any intervention or knowledge of the user
Answers Explanation & Hints: Worms are self-replicating pieces of software that consume bandwidth on a network as they propagate from system to system. They do not require a host application, unlike a virus. Viruses, on the other hand, carry executable malicious code which harms the target machine on which they reside.
-
Which type of security threat would be responsible if a spreadsheet add-on disables the local software firewall?
- DoS
- buffer overflow
- Trojan horse
- brute-force attack
Answers Explanation & Hints: A Trojan horse is software that does something harmful, but is hidden in legitimate software code. A denial of service (DoS) attack results in interruption of network services to users, network devices, or applications. A brute-force attack commonly involves trying to access a network device. A buffer overflow occurs when a program attempts to store more data in a memory location than it can hold.
-
What is the significant characteristic of worm malware?
- Worm malware disguises itself as legitimate software.
- A worm can execute independently of the host system.
- A worm must be triggered by an event on the host system.
- Once installed on a host system, a worm does not replicate itself.
Answers Explanation & Hints: Worm malware can execute and copy itself without being triggered by a host program. It is a significant network and Internet security threat.
-
What are the three major components of a worm attack? (Choose three.)
- an enabling vulnerability
- an infecting vulnerability
- a payload
- a penetration mechanism
- a probing mechanism
- a propagation mechanism
Answers Explanation & Hints: A computer can have a worm installed through an email attachment, an executable program file, or a Trojan Horse. The worm attack not only affects one computer, but replicates to other computers. What the worm leaves behind is the payload–the code that results in some action.
-
Which two characteristics describe a virus? (Choose two.)
- A self-replicating attack that is independently launched.
- Malicious code that can remain dormant before executing an unwanted action.
- Program code specifically designed to corrupt memory in network devices.
- Malware that relies on the action of a user or a program to activate.
- Malware that executes arbitrary code and installs copies of itself in memory.
Answers Explanation & Hints: A virus is malicious code that is attached to legitimate programs or executable files. Most viruses require end user activation, can lie dormant for an extended period, and then activate at a specific time or date. In contrast, a worm executes arbitrary code and installs copies of itself in the memory of the infected computer. The main purpose of a worm is automatic replication to spread quickly across a network. A worm does not require a host program to run.
-
Which type of Trojan horse security breach uses the computer of the victim as the source device to launch other attacks?
- FTP
- data-sending
- DoS
- proxy
Answers Explanation & Hints: The attacker uses a proxy Trojan horse attack to penetrate one device and then use that device to launch attacks on other devices. The DoS Trojan horse slows or halts network traffic. The FTP trojan horse enables unauthorized file transfer services when port 21 has been compromised. A data-sending Trojan horse transmits data back to the hacker that could include passwords.
-
A user is curious about how someone might know a computer has been infected with malware. What are two common malware behaviors? (Choose two.)
- The computer beeps once during the boot process.
- The computer emits a hissing sound every time the pencil sharpener is used.
- The computer gets increasingly slower to respond.
- No sound emits when an audio CD is played.
- The computer freezes and requires reboots.
Answers Explanation & Hints: Common symptoms of computers infected with malware:Appearance of files, applications, or desktop icons
Security tools such as antivirus software or firewalls turned off or changed
System crashes
Emails spontaneously sent to others
Modified or missing files
Slow system or browser response
Unfamiliar processes or services running
Unknown TCP or UDP ports open
Connections made to unknown remote devices
-
A user receives a phone call from a person who claims to represent IT services and then asks that user for confirmation of username and password for auditing purposes. Which security threat does this phone call represent?
- DDoS
- spam
- social engineering
- anonymous keylogging
Answers Explanation & Hints: Social engineering attempts to gain the confidence of an employee and convince that person to divulge confidential and sensitive information, such as usernames and passwords. DDoS attacks, spam, and keylogging are all examples of software based security threats, not social engineering.
-
Which two types of attacks are examples of reconnaissance attacks? (Choose two.)
- port scan
- SYN flood
- ping sweep
- brute force
- man-in-the-middle
Answers Explanation & Hints: Reconnaissance attacks attempt to gather information about the targets. Ping sweeps will indicate which hosts are up and responding to pings, whereas port scans will indicate on which TCP and UDP ports the target is listening for incoming connections. Man-in-the-middle and brute force attacks are both examples of access attacks, and a SYN flood is an example of a denial of service (DoS) attack.
-
The IT department is reporting that a company web server is receiving an abnormally high number of web page requests from different locations simultaneously. Which type of security attack is occurring?
- adware
- DDoS
- phishing
- social engineering
- spyware
Answers Explanation & Hints: Phishing, spyware, and social engineering are security attacks that collect network and user information. Adware consists, typically, of annoying popup windows. Unlike a DDoS attack, none of these attacks generate large amounts of data traffic that can restrict access to network services.
-
What causes a buffer overflow?
- launching a security countermeasure to mitigate a Trojan horse
- downloading and installing too many software updates at one time
- attempting to write more data to a memory location than that location can hold
- sending too much information to two or more interfaces of the same device, thereby causing dropped packets
- sending repeated connections such as Telnet to a particular device, thus denying other data sources
Answers Explanation & Hints: By sending too much data to a specific area of memory, adjacent memory locations are overwritten, which causes a security issue because the program in the overwritten memory location is affected.
-
What are two evasion methods used by hackers? (Choose two.)
- encryption
- phishing
- access attack
- resource exhaustion
- scanning
Answers Explanation & Hints: The following methods are used by hackers to avoid detection:Encryption and tunneling – hide or scramble the malware content
Resource exhaustion – keep the host device too busy to detect the invasion
Traffic fragmentation – split the malware into multiple packets
Protocol-level misinterpretation – sneak by the firewall
Pivot – use a compromised network device to attempt access to another device
Rootkit – allow the hacker to avoid detection as well as hide software installed by the hacker
-
Which type of security attack would attempt a buffer overflow?
- reconnaissance
- ransomware
- DoS
- scareware
Answers Explanation & Hints: Denial of service (DoS) attacks attempt to disrupt service on the network by either sending a particular device an overwhelming amount of data so no other devices can access the attacked device or by sending malformed packets.
-
What are two examples of DoS attacks? (Choose two.)
- phishing
- ping of death
- SQL injection
- port scanning
- buffer overflow
Answers Explanation & Hints: The buffer overflow and ping of death DoS attacks exploit system memory-related flaws on a server by sending an unexpected amount of data or malformed data to the server.
-
Why would an attacker want to spoof a MAC address?
- so that a switch on the LAN will start forwarding frames to the attacker instead of to the legitimate host
- so that a switch on the LAN will start forwarding all frames toward the device that is under control of the attacker (that can then capture the LAN traffic)
- so that the attacker can capture traffic from multiple VLANs rather than from just the VLAN that is assigned to the port to which the attacker device is attached
- so that the attacker can launch another type of attack in order to gain access to the switch
Answers Explanation & Hints: MAC address spoofing is used to bypass security measures by allowing an attacker to impersonate a legitimate host device, usually for the purpose of collecting network traffic.
-
Which field in the IPv6 header points to optional network layer information that is carried in the IPv6 packet?
- flow label
- version
- traffic class
- next header
Answers Explanation & Hints: Optional Layer 3 information about fragmentation, security, and mobility is carried inside of extension headers in an IPv6 packet. The next header field of the IPv6 header acts as a pointer to these optional extension headers if they are present.
-
Which devices should be secured to mitigate against MAC address spoofing attacks?
- Layer 7 devices
- Layer 4 devices
- Layer 2 devices
- Layer 3 devices
Answers Explanation & Hints: Layer 2 attacks such as MAC address spoofing can be mitigated by securing Layer 2 devices.
-
A network administrator is checking the system logs and notices unusual connectivity tests to multiple well-known ports on a server. What kind of potential network attack could this indicate?
- access
- reconnaissance
- denial of service
- information theft
Answers Explanation & Hints: A reconnaissance attack is the unauthorized discovery and mapping of systems, services, or vulnerabilities. One of the most common reconnaissance attacks is performed by using utilities that automatically discover hosts on the networks and determine which ports are currently listening for connections.
-
What are two purposes of launching a reconnaissance attack on a network? (Choose two.)
- to retrieve and modify data
- to scan for accessibility
- to escalate access privileges
- to gather information about the network and devices
- to prevent other users from accessing the system
Answers Explanation & Hints: Gathering information about a network and scanning for access is a reconnaissance attack. Preventing other users from accessing a system is a denial of service attack. Attempting to retrieve and modify data, and attempting to escalate access privileges are types of access attacks.
-
What kind of ICMP message can be used by threat actors to create a man-in-the-middle attack?
- ICMP echo request
- ICMP unreachable
- ICMP mask reply
- ICMP redirects
Answers Explanation & Hints: Common ICMP messages of interest to threat actors include the following:
ICMP echo request and echo reply: used to perform host verification and DoS attacks
ICMP unreachable: used to perform network reconnaissance and scanning attacks
ICMP mask reply: used to map an internal IP network
ICMP redirects: used to lure a target host into sending all traffic through a compromised device and create a man-in-the-middle attack
ICMP router discovery: used to inject bogus route entries into the routing table of a target host
-
Which type of network attack involves randomly opening many Telnet requests to a router and results in a valid network administrator not being able to access the device?
- spoofing
- man-in-the-middle
- SYN flooding
- DNS poisoning
Answers Explanation & Hints: The TCP SYN Flood attack exploits the TCP three-way handshake. The threat actor continually sends TCP SYN session request packets with a randomly spoofed source IP address to an intended target. The target device replies with a TCP SYN-ACK packet to the spoofed IP address and waits for a TCP ACK packet. Those responses never arrive. Eventually the target host is overwhelmed with half-open TCP connections and denies TCP services.
-
Which type of attack is carried out by threat actors against a network to determine which IP addresses, protocols, and ports are allowed by ACLs?
- phishing
- reconnaissance
- denial of service
- social engineering
Answers Explanation & Hints: Packet filtering ACLs use rules to filter incoming and outgoing traffic. These rules are defined by specifying IP addresses, port numbers, and protocols to be matched. Threat actors can use a reconnaissance attack involving port scanning or penetration testing to determine which IP addresses, protocols, and ports are allowed by ACLs.
-
Which two types of hackers are typically classified as grey hat hackers? (Choose two.)
- state-sponsored hackers
- hacktivists
- script kiddies
- cyber criminals
- vulnerability brokers
Answers Explanation & Hints: Grey hat hackers may do unethical or illegal things, but not for personal gain or to cause damage. Hacktivists use their hacking as a form of political or social protest, and vulnerability brokers hack to uncover weaknesses and report them to vendors. Depending on the perspective one possesses, state-sponsored hackers are either white hat or black hat operators. Script kiddies create hacking scripts to cause damage or disruption. Cyber criminals use hacking to obtain financial gain by illegal means.
-
Match the type of cyberattackers to the description. (Not all options are used.)
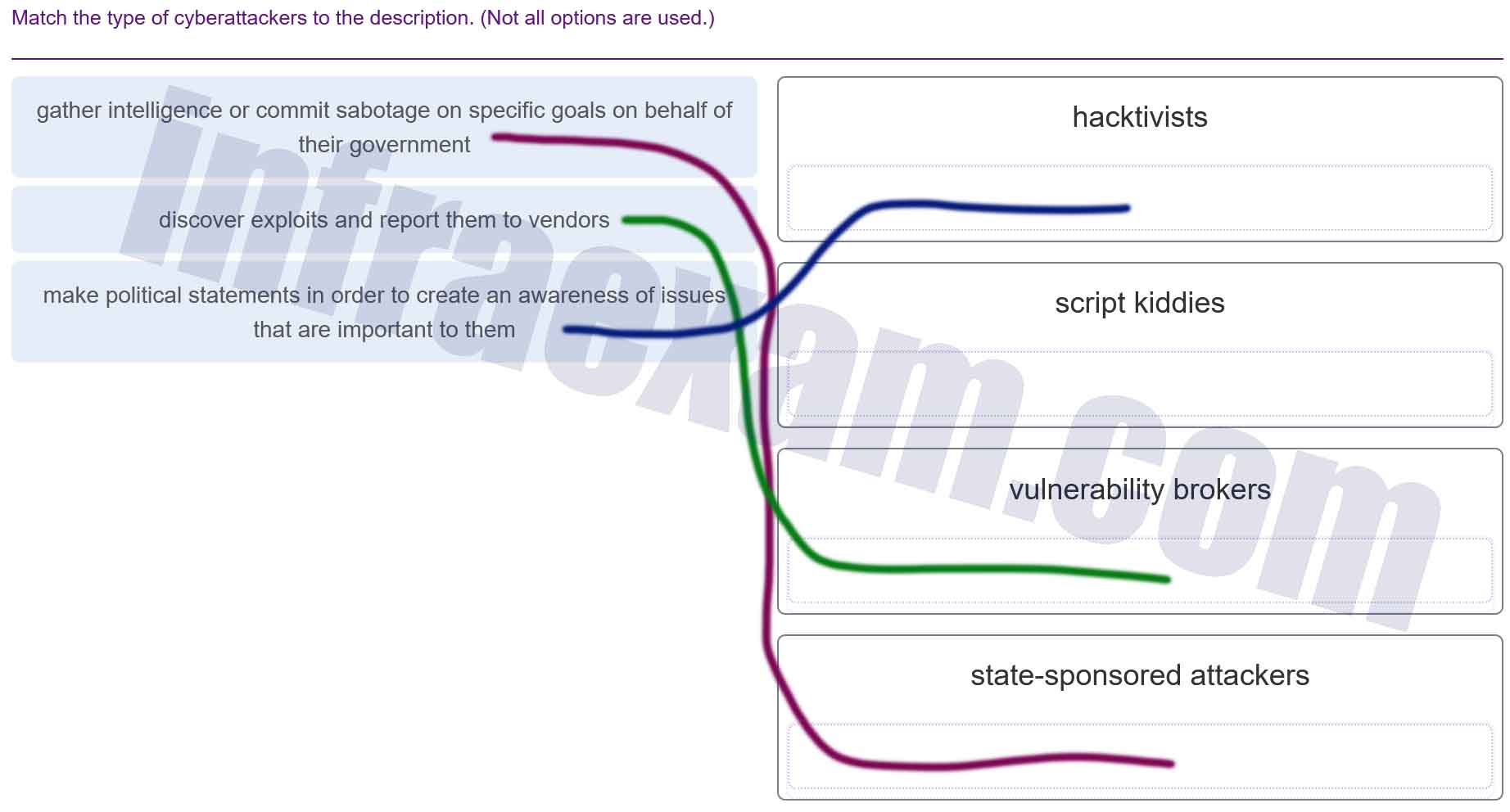
Modules 13 – 17 Threats and Attacks Group Exam Answers 001 Explanation & Hint: - State-sponsored attackers: These are individuals or groups that gather intelligence or commit sabotage on specific goals on behalf of their government. This type of attacker is typically well-funded and highly skilled, with the backing of a nation-state.
- Hacktivists: These attackers make political statements in order to create an awareness of issues that are important to them. Hacktivism is the act of hacking, or breaking into a computer system, for a politically or socially motivated purpose.
- Vulnerability brokers: While not directly mentioned in the exercise, these are entities that discover exploits and report them to vendors, or alternatively, sell the information in underground markets. They are essentially middlemen in the trade of vulnerabilities.
- Script kiddies: This term is often used to describe inexperienced cyberattackers who use existing computer scripts or code to hack into computers, lacking the expertise to write their own.
-
What is the goal of a white hat hacker?
- protecting data
- stealing data
- modifying data
- validating data
Answers Explanation & Hints: White hat hackers are actually “good guys” and are paid by companies and governments to test for security vulnerabilities so that data is better protected.
-
What scenario describes a vulnerability broker?
- a teenager running existing scripts, tools, and exploits, to cause harm, but typically not for profit
- a threat actor attempting to discover exploits and report them to vendors, sometimes for prizes or rewards
- a threat actor publicly protesting against governments by posting articles and leaking sensitive information
- a State-Sponsored threat actor who steals government secrets and sabotages networks of foreign governments
Answers Explanation & Hints: Vulnerability brokers typically refers to grey hat hackers who attempt to discover exploits and report them to vendors, sometimes for prizes or rewards.
-
Match the threat actors with the descriptions. (Not all options are used.)
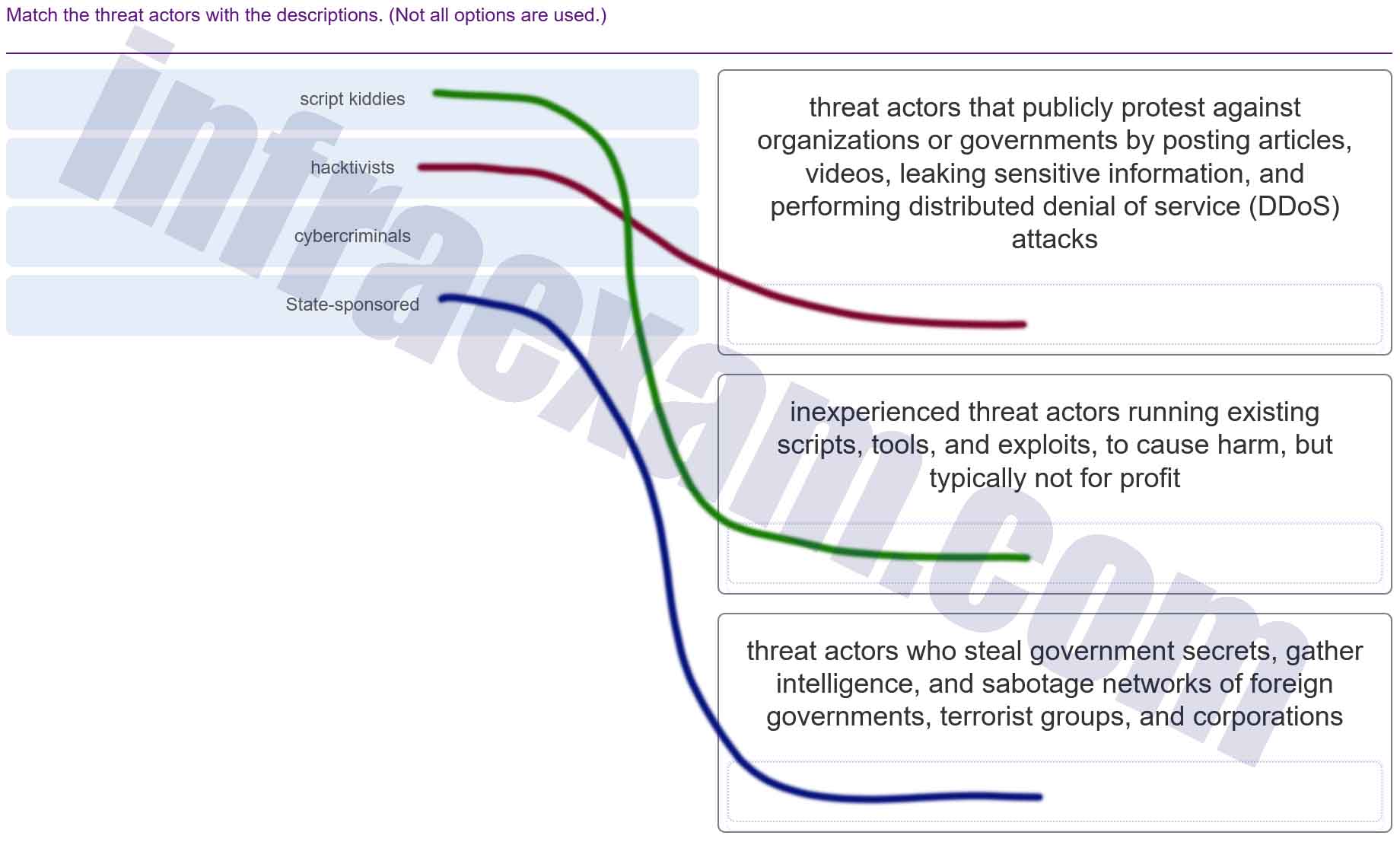
Modules 13 – 17 Threats and Attacks Group Exam Answers 002 Explanation & Hint: - Hacktivists: They are threat actors that publicly protest against organizations or governments by posting articles, videos, leaking sensitive information, and performing distributed denial of service (DDoS) attacks.
- Script kiddies: These are inexperienced threat actors running existing scripts, tools, and exploits, to cause harm, but typically not for profit.
- State-sponsored: These are threat actors who steal government secrets, gather intelligence, and sabotage networks of foreign governments, terrorist groups, and corporations.
-
An administrator discovers a vulnerability in the network. On analysis of the vulnerability the administrator decides the cost of managing the risk outweighs the cost of the risk itself. The risk is accepted, and no action is taken. What risk management strategy has been adopted?
- risk avoidance
- risk acceptance
- risk reduction
- risk transfer
Answers Explanation & Hints: Risk acceptance is when the cost of risk management options outweighs the cost of the risk itself, the risk is accepted, and no action is taken.
-
Once a cyber threat has been verified, the US Cybersecurity Infrastructure and Security Agency (CISA) automatically shares the cybersecurity information with public and private organizations. What is this automated system called?
- NCASM
- AIS
- NCSA
- ENISA
Answers Explanation & Hints: The US CISA uses a system called Automated Indicator Sharing (AIS). The AIS system shares verified attack vectors and indicators with the private and public sectors.
-
In what type of attack is a cybercriminal attempting to prevent legitimate users from accessing network services?
- DoS
- MITM
- session hijacking
- address spoofing
Answers Explanation & Hints: In a DoS or denial-of-service attack, the goal of the attacker is to prevent legitimate users from accessing network services.
-
Which attack involves threat actors positioning themselves between a source and destination with the intent of transparently monitoring, capturing, and controlling the communication?
- DoS attack
- ICMP attack
- SYN flood attack
- man-in-the-middle attack
Answers Explanation & Hints: The man-in-the-middle attack is a common IP-related attack where threat actors position themselves between a source and destination to transparently monitor, capture, and control the communication.
-
Match the security tool with the description. (Not all options apply.)
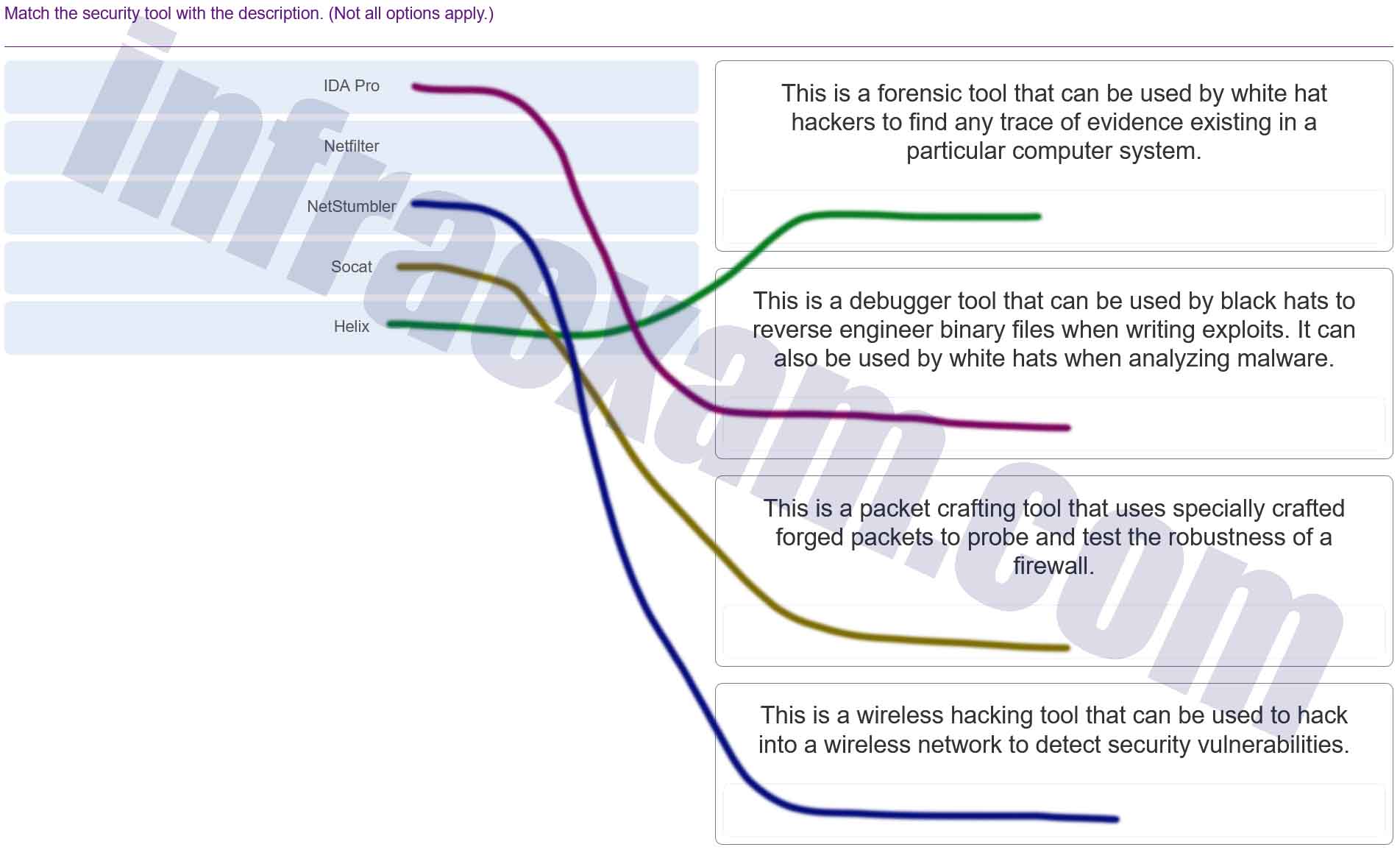
Modules 13 – 17 Threats and Attacks Group Exam Answers 003 Explanation & Hint: - Helix: This is a forensic tool that can be used by white hat hackers to find any trace of evidence existing in a particular computer system.
- IDA Pro: This is a debugger tool that can be used by black hats to reverse engineer binary files when writing exploits. It can also be used by white hats when analyzing malware.
- Socat: This is a packet crafting tool that uses specially crafted forged packets to probe and test the robustness of a firewall.
- NetStumbler: This is a wireless hacking tool that can be used to hack into a wireless network to detect security vulnerabilities.
Note: Netfilter is a framework provided by Linux that allows various networking-related operations to be implemented in the form of customized handlers.
-
A white hat hacker is using a security tool called Skipfish to discover the vulnerabilities of a computer system. What type of tool is this?
- debugger
- packet sniffer
- vulnerability scanner
- fuzzer
Answers Explanation & Hints: Fuzzers are tools used by threat actors when attempting to discover the vulnerabilities of a computer system. Examples of fuzzers include Skipfish, Wapiti, and W3af.
-
Match the security concept to the description.
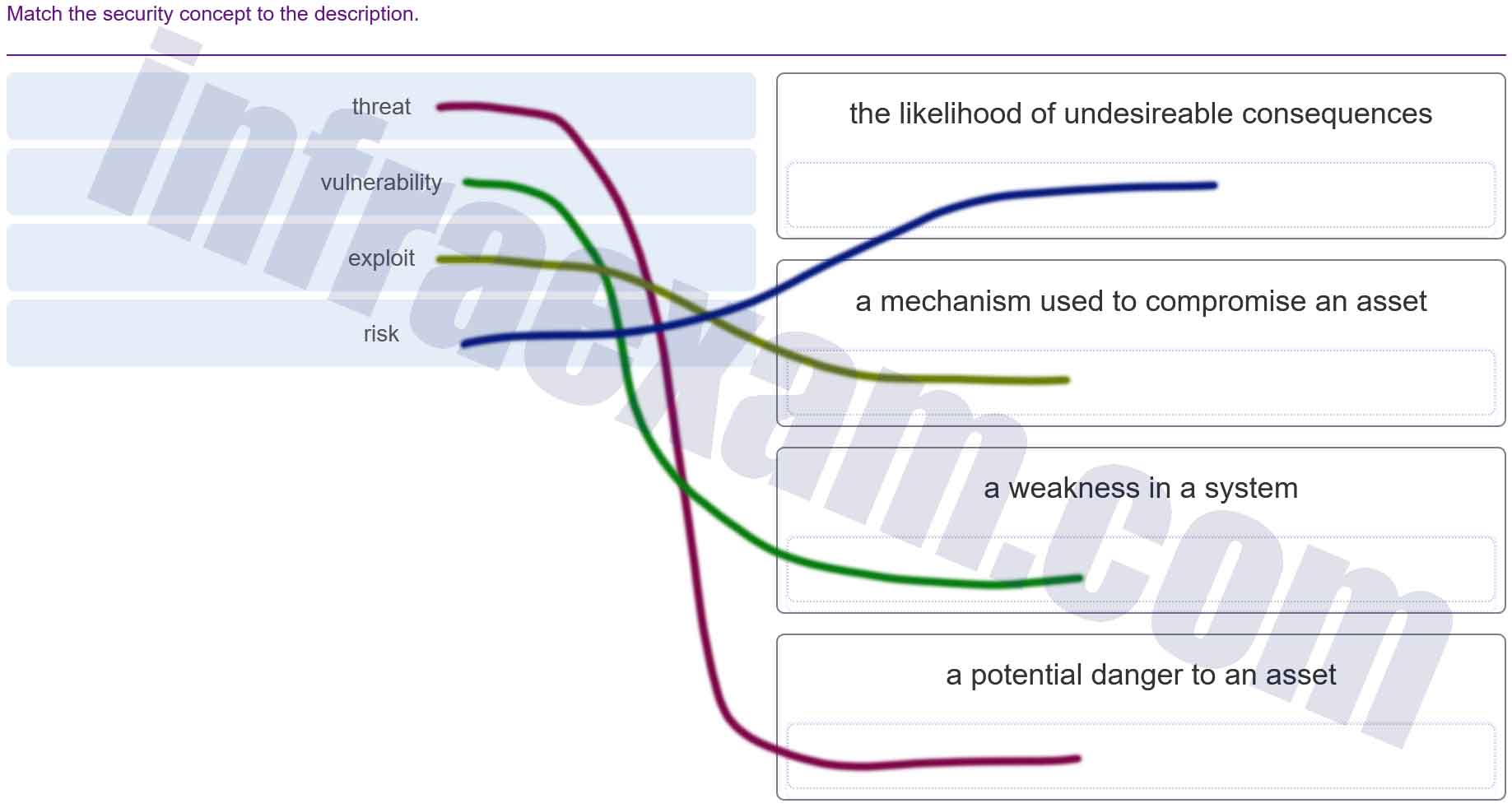
Modules 13 – 17 Threats and Attacks Group Exam Answers 004 Explanation & Hint: - Vulnerability: This is a weakness in a system. It can be a flaw, a missing update, a misconfiguration, or any issue that a threat actor could exploit to perform unauthorized actions within a computer system.
- Exploit: This is a mechanism used to compromise an asset. It takes advantage of vulnerabilities in a system to perform unauthorized actions, such as gaining control, elevating privileges, or denying service to legitimate users.
- Risk: This is the likelihood of undesirable consequences. In cybersecurity, it’s typically quantified as the potential for loss or damage when a threat exploits a vulnerability.
- Threat: This is a potential danger to an asset. It represents a possible event or action that could cause harm to the system or organization by exploiting vulnerabilities.
-
Which statement describes the function of the SPAN tool used in a Cisco switch?
- It supports the SNMP trap operation on a switch.
- It provides interconnection between VLANs over multiple switches.
- It is a secure channel for a switch to send logging to a syslog server.
- It copies the traffic from one switch port and sends it to another switch port that is connected to a monitoring device.
Answers Explanation & Hints: To analyze network traffic passing through a switch, switched port analyzer (SPAN) can be used. SPAN can send a copy of traffic from one port to another port on the same switch where a network analyzer or monitoring device is connected. SPAN is not required for syslog or SNMP. SPAN is used to mirror traffic, while syslog and SNMP are configured to send data directly to the appropriate server.
-
What functionality is provided by Cisco SPAN in a switched network?
- It mitigates MAC address overflow attacks.
- It prevents traffic on a LAN from being disrupted by a broadcast storm.
- It mirrors traffic that passes through a switch port or VLAN to another port for traffic analysis.
- It protects the switched network from receiving BPDUs on ports that should not be receiving them.
- It inspects voice protocols to ensure that SIP, SCCP, H.323, and MGCP requests conform to voice standards.
- It copies traffic that passes through a switch interface and sends the data directly to a syslog or SNMP server for analysis.
Answers Explanation & Hints: SPAN is a Cisco technology used by network administrators to monitor suspicious traffic or to capture traffic to be analyzed.
-
Match the network monitoring solution with a description. (Not all options are used.)

Modules 13 – 17 Threats and Attacks Group Exam Answers 005 Explanation & Hint: - SPAN (Switched Port Analyzer) or port mirroring: This network monitoring solution is used to copy frames received on one or more ports to a port connected to an analysis device.
- Protocol analyzer: This tool is used to capture traffic and show what is happening on the network. It’s essentially a type of software that captures and analyzes the packets of data being transmitted over a network.
- IPS (Intrusion Prevention System): This solution monitors traffic and compares it against configured rules. An IPS can take action on the traffic it monitors, such as blocking malicious traffic.
-
Which technology is a proprietary SIEM system?
- StealthWatch
- SNMP agent
- NetFlow collector
- Splunk
Answers Explanation & Hints: Security Information Event Management (SIEM) is a technology that is used in enterprise organizations to provide real-time reporting and long-term analysis of security events. Splunk is a proprietary SIEM system.
-
Which two functions are provided by NetFlow? (Choose two.)
- It provides a complete audit trail of basic information about every IP flow forwarded on a device.
- It provides 24×7 statistics on packets that flow through a Cisco router or multilayer switch.
- It uses artificial intelligence to detect incidents and aid in incident analysis and response.
- It allows an administrator to capture real-time network traffic and analyze the entire contents of packets.
- It presents correlated and aggregated event data in real-time monitoring and long-term summaries.
Answers Explanation & Hints: NetFlow is a Cisco IOS technology that provides statistics and complete audit trails on TCP/IP flows on the network. Some of the capabilities of NetFlow include the following: 24×7 network and security monitoring, network planning, traffic analysis, identification of network bottlenecks, and IP accounting for billing purposes.
-
What are three functionalities provided by SOAR? (Choose three.)
- It provides case management tools that allow cybersecurity personnel to research and investigate incidents.
- It uses artificial intelligence to detect incidents and aid in incident analysis and response.
- It automates complex incident response procedures and investigations.
- It provides 24×7 statistics on packets that flow through a Cisco router or multilayer switch.
- It provides a complete audit trail of basic information about every IP flow forwarded on a device.
- It presents the correlated and aggregated event data in real-time monitoring and long-term summaries.
Answers Explanation & Hints: SOAR security platforms offer these functionalities:
• Gather alarm data from each component of the system
• Provide tools that enable cases to be researched, assessed, and investigated
• Emphasize integration as a means of automating complex incident response workflows that enable more rapid response and adaptive defense strategies
• Include predefined playbooks that enable automatic response to specific threats
-
Which statement describes an operational characteristic of NetFlow?
- NetFlow captures the entire contents of a packet.
- NetFlow can provide services for user access control.
- NetFlow flow records can be viewed by the tcpdump tool.
- NetFlow collects basic information about the packet flow, not the flow data itself.
Answers Explanation & Hints: NetFlow does not capture the entire contents of a packet. Instead, NetFlow collects metadata, or data about the flow, not the flow data itself. NetFlow information can be viewed with tools such as nfdump and FlowViewer.