CyberOps Associate 1.02 & CA v1.0 Modules 3 – 4: Operating System Overview Group Exam Answers 2025 Full 100%
CyberOps Associate 1.02 & CA v1.0 Modules 3 – 4: Operating System Overview Group Exam Answers Full 100% 2025
These are both versions of NetAcad Cisco CA 1.02 and CyberOps Associate (Version 1.0) – Modules 3 – 4: Operating System Overview Group Exam Full 100% in 2025 verified by experts with explanations and hints.
| CyberOps - Associate 1.0 & 1.01 | |
| Final Exam Answers | |
| This Modules 3 - 4 | |
| Modules 3 - 4 Exam Answers | Online Test |
| Next Modules 5 - 10 | |
| Modules 5 - 10 Exam Answers | Online Test |
-
What are two advantages of the NTFS file system compared with FAT32? (Choose two.)
- NTFS allows faster access to external peripherals such as a USB drive.
- NTFS supports larger files.
- NTFS provides more security features.
- NTFS allows faster formatting of drives.
- NTFS is easier to configure.
- NTFS allows the automatic detection of bad sectors.
Answers Explanation & Hints: The file system has no control over the speed of access or formatting of drives, and the ease of configuration is not file system-dependent.
-
What technology was created to replace the BIOS program on modern personal computer motherboards?
- UEFI
- RAM
- CMOS
- MBR
Answers Explanation & Hints: As of 2015, most personal computer motherboards are shipped with UEFI as the replacement for the BIOS program.
-
A technician has installed a third party utility that is used to manage a Windows 7 computer. However, the utility does not automatically start whenever the computer is started. What can the technician do to resolve this problem?
- Uninstall the program and then choose Add New Programs in the Add or Remove Programs utility to install the application.
- Use the Add or Remove Programs utility to set program access and defaults.
- Change the startup type for the utility to Automatic in Services .
- Set the application registry key value to one.
Answers Explanation & Hints: The Services console in Windows OS allows for the management of all the services on the local and remote computers. The setting of Automatic in the Services console enables the chosen service to start when the computer is started.
-
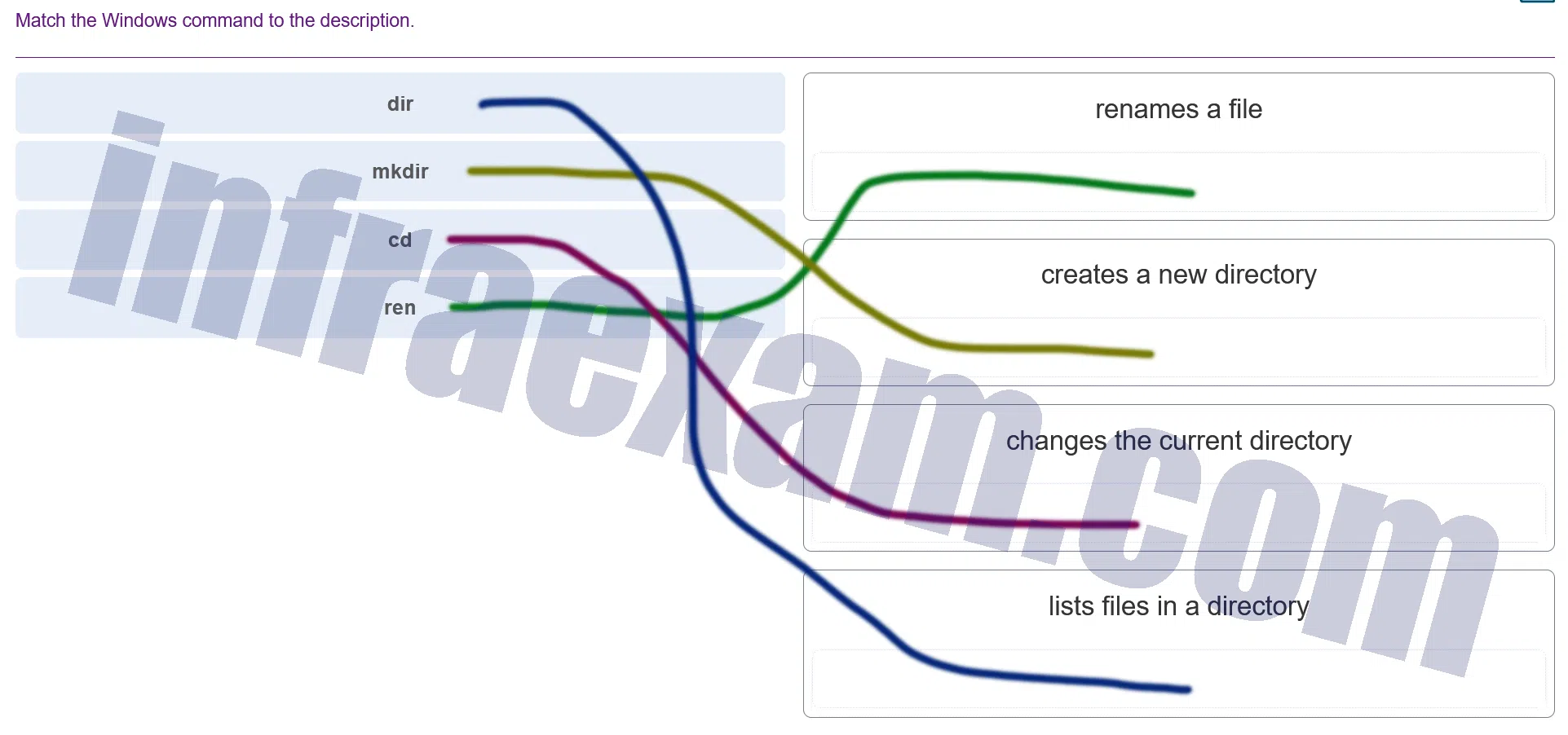
Match the Windows command to the description.
Modules 3 – 4 Operating System Overview Group Exam Answers 001 Explanation & Hint: The commands and their descriptions are partially visible, but the watermark obscures some of the content. From what I can discern, the task is to match the command to its function. Here are the commands and their typical functions:
dir– Lists files in a directory.mkdir– Creates a new directory.cd– Changes the current directory.renorrename– Renames a file or directory.
-
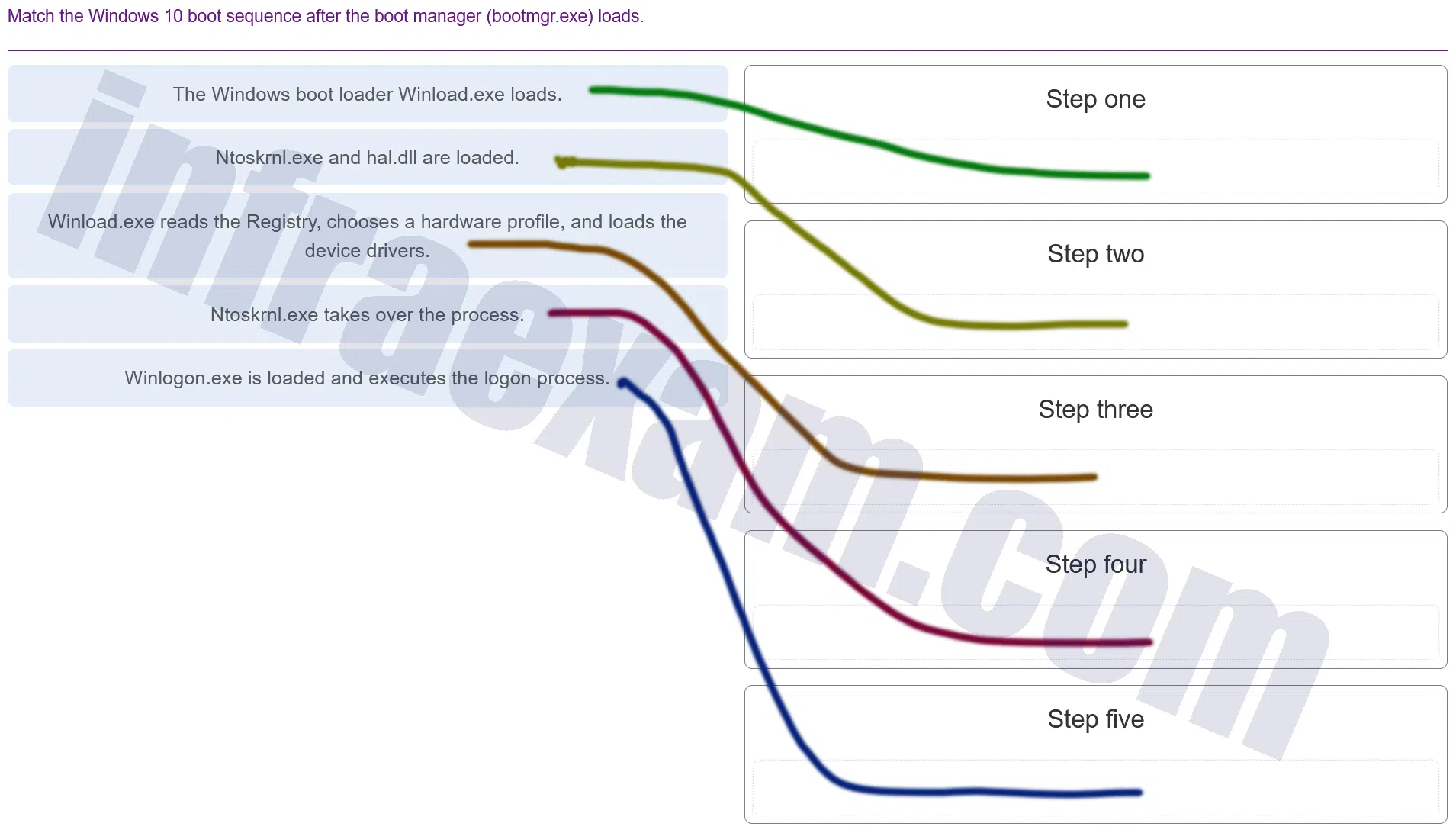
Match the Windows 10 boot sequence after the boot manager (bootmgr.exe) loads.
Modules 3 – 4 Operating System Overview Group Exam Answers 002 Explanation & Hint: - The Windows boot loader Winload.exe loads: Winload.exe is the component that is responsible for loading the Windows operating system kernel (ntoskrnl.exe) and the Hardware Abstraction Layer (hal.dll). It’s part of the Windows Boot Manager and gets the system ready for the handoff to the operating system.
- Ntoskrnl.exe and hal.dll are loaded: The ntoskrnl.exe is the Windows NT operating system kernel that handles system-level management, such as process and memory management. The hal.dll is the Hardware Abstraction Layer that facilitates communication between the hardware and the kernel.
- Winload.exe reads the Registry, chooses a hardware profile, and loads the device drivers: Before handing control over to the operating system, Winload.exe reads the system registry to get the necessary configuration information, selects a hardware profile, and loads the necessary device drivers for the hardware components.
- Ntoskrnl.exe takes over the process: After the necessary drivers and system files are loaded into memory, control is passed from the boot loader to the operating system kernel (ntoskrnl.exe), which continues the boot process.
- Winlogon.exe is loaded and executes the logon process: Winlogon.exe is responsible for handling the user logon and logoff processes. It manages the secure attention sequence, loads user profiles upon logon, and facilitates the launching of the shell (usually Explorer.exe in Windows).
-
Which two commands could be used to check if DNS name resolution is working properly on a Windows PC? (Choose two.)
- nslookup cisco.com
- net cisco.com
- ping cisco.com
- nbtstat cisco.com
- ipconfig /flushdns
Answers Explanation & Hints: The ping command tests the connection between two hosts. When ping uses a host domain name to test the connection, the resolver on the PC will first perform the name resolution to query the DNS server for the IP address of the host. If the ping command is unable to resolve the domain name to an IP address, an error will result.
Nslookup is a tool for testing and troubleshooting DNS servers.
-
A user logs in to Windows with a regular user account and attempts to use an application that requires administrative privileges. What can the user do to successfully use the application?
- Right-click the application and choose Run as root .
- Right-click the application and choose Run as Priviledge .
- Right-click the application and choose Run as Superuser .
- Right-click the application and choose Run as Administrator .
Answers Explanation & Hints: As a security best practice, it is advisable not to log on to Windows using the Administrator account or an account with administrative privileges. When it is necessary to run or install software that requires the privileges of the Administrator, the user can right-click the software in the Windows File Explorer and choose Run as Administrator .
-
Which type of Windows PowerShell command performs an action and returns an output or object to the next command that will be executed?
- scripts
- cmdlets
- routines
- functions
Answers Explanation & Hints: The types of commands that PowerShell can execute include the following: cmdlets – perform an action and return an output or object to the next command that will be executed
PowerShell scripts – files with a .ps1 extension that contain PowerShell commands that are executed
PowerShell functions – pieces of code that can be referenced in a script
-
A user creates a file with .ps1 extension in Windows. What type of file is it?
- PowerShell script
- PowerShell cmdlet
- PowerShell function
- PowerShell documentation
Answers Explanation & Hints: The types of commands that PowerShell can execute include the following: cmdlets – perform an action and return an output or object to the next command that will be executed
PowerShell scripts – files with a .ps1 extension that contain PowerShell commands that are executed
PowerShell functions – pieces of code that can be referenced in a script
-
What is the purpose of using the net accounts command in Windows?
- to start a network service
- to display information about shared network resources
- to show a list of computers and network devices on the network
- to review the settings of password and logon requirements for users
Answers Explanation & Hints: These are some common net commands:
net accounts – sets password and logon requirements for users
net start – starts a network service or lists running network services
net use – connects, disconnects, and displays information about shared network resources
net view – shows a list of computers and network devices on the network
When used without options, the net accounts command displays the current settings for password, logon limitations, and domain information.
-
What is the purpose of entering the netsh command on a Windows PC?
- to create user accounts
- to test the hardware devices on the PC
- to change the computer name for the PC
- to configure networking parameters for the PC
Answers Explanation & Hints: The netsh.exe tool can be used to configure networking parameters for the PC from a command prompt.
-
Which statement describes the function of the Server Message Block (SMB) protocol?
- It is used to manage remote PCs.
- It is used to stream media contents.
- It is used to share network resources.
- It is used to compress files stored on a disk.
Answers Explanation & Hints: The Server Message Block (SMB) protocol is primarily used by Microsoft to share network resources.
-
A PC user issues the netstat command without any options. What is displayed as the result of this command?
- a local routing table
- a network connection and usage report
- a list of all established active TCP connections
- a historical list of successful pings that have been sent
Answers Explanation & Hints: When used by itself (without any options), the netstat command will display all the active TCP connections that are available.
-
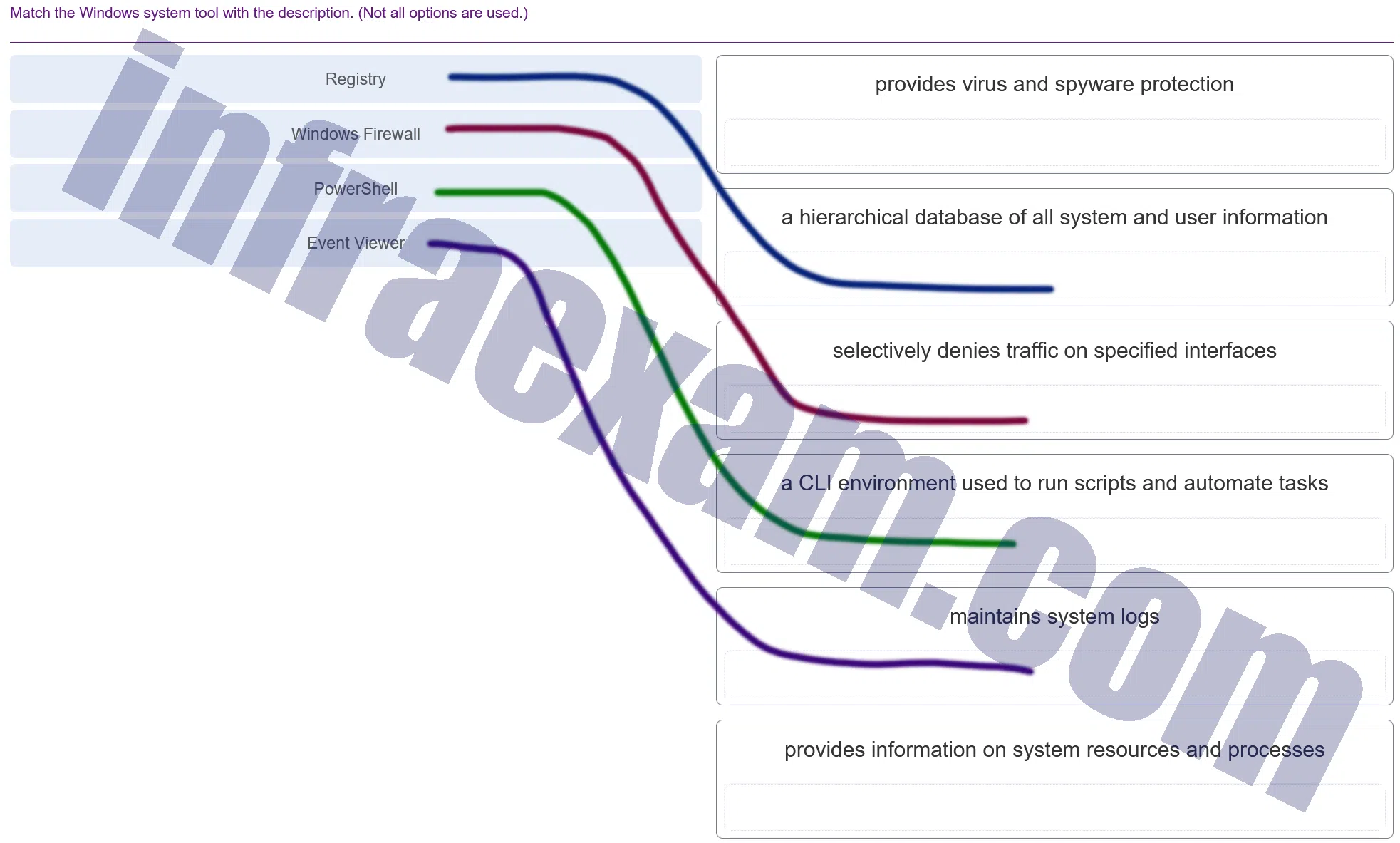
Match the Windows system tool with the description. (Not all options are used.)
Modules 3 – 4 Operating System Overview Group Exam Answers 003 Explanation & Hint: - Registry – This is typically a hierarchical database that contains all system and user settings and information. It’s where Windows and many applications store their configuration settings.
- Windows Firewall – This tool selectively denies or allows traffic on specified interfaces, providing a level of protection against unauthorized access from the internet or other networks.
- PowerShell – A command-line interface (CLI) and scripting language that is used to automate tasks and manage system configurations. It’s more advanced and powerful than the traditional Command Prompt.
- Event Viewer – This tool maintains and displays system logs. It is used to view event logs, audit logs, and other system messages that provide information on system resources and processes.
-
Which Windows tool can be used by a cybersecurity administrator to secure stand-alone computers that are not part of an active directory domain?
- Local Security Policy
- Windows Defender
- Windows Firewall
- PowerShell
Answers Explanation & Hints: Windows systems that are not part of an Active Directory Domain can use the Windows Local Security Policy to enforce security settings on each stand-alone system.
-
An IT technician wants to create a rule on two Windows 10 computers to prevent an installed application from accessing the public Internet. Which tool would the technician use to accomplish this task?
- Computer Management
- DMZ
- Local Security Policy
- Windows Defender Firewall with Advanced Security
Answers Explanation & Hints: Windows Firewall with Advanced Security or the Windows 10 Windows Defender Firewall with Advanced Security is used to create inbound and outbound rules, connection security rules such as security traffic between two computers, and monitoring any active connection security rules.
-
Why would a network administrator choose Linux as an operating system in the Security Operations Center (SOC)?
- It is easier to use than other operating systems.
- It is more secure than other server operating systems.
- More network applications are created for this environment.
- The administrator has more control over the operating system.
Answers Explanation & Hints: There are several reasons why Linux is a good choice for the SOC.Linux is open source.
The command line interface is a very powerful environment.
The user has more control over the operating system.
Linux allows for better network communication control.
-
Which type of tool allows administrators to observe and understand every detail of a network transaction?
- log manager
- ticketing system
- packet capture software
- malware analysis tool
Answers Explanation & Hints: Network packet capture software is an important tool because it makes it possible to observe and understand the details of a network transaction.
-
Why is Kali Linux a popular choice in testing the network security of an organization?
- It is an open source Linux security distribution containing many penetration tools.
- It can be used to intercept and log network traffic.
- It can be used to test weaknesses by using only malicious software.
- It is a network scanning tool that prioritizes security risks.
Answers Explanation & Hints: Kali is an open source Linux security distribution that is commonly used by IT professionals to test the security of networks.
-
A Linux system boots into the GUI by default, so which application can a network administrator use in order to access the CLI environment?
- file viewer
- system viewer
- terminal emulator
- package management tool
Answers Explanation & Hints: A terminal emulator is an application program a user of Linux can use in order to access the CLI environment.
-
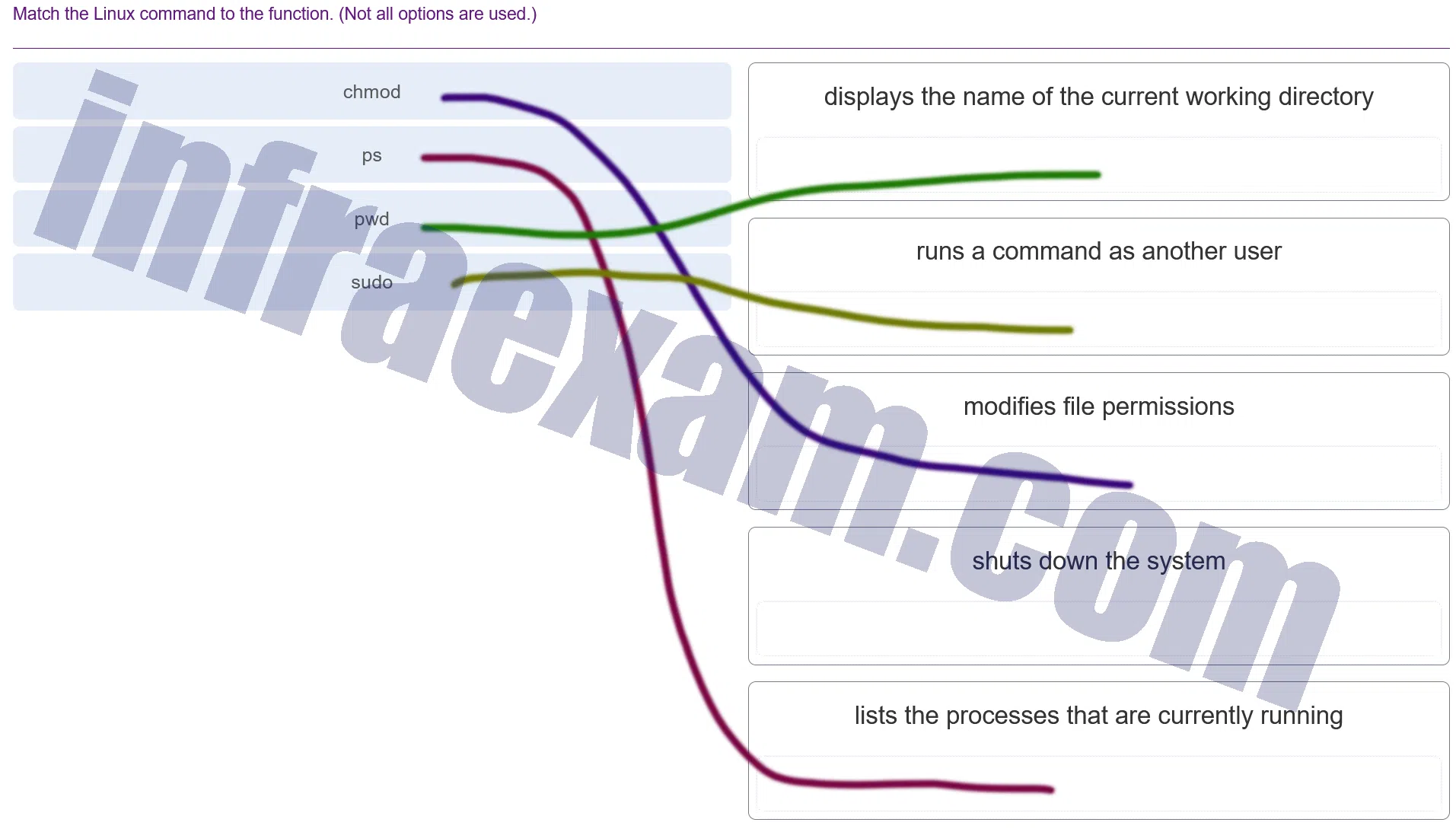
Match the Linux command to the function. (Not all options are used.)
Modules 3 – 4 Operating System Overview Group Exam Answers 004 Explanation & Hint: chmod: This command is used to change the permissions of a file or directory. In Linux, file permissions control the actions that can be performed on the file or directory.ps: Thepscommand is used to display information about the processes running on a system.pwd: This stands for “print working directory,” and it displays the current directory you’re in.sudo: This command stands for “superuser do,” and it allows a permitted user to execute a command as the superuser or another user, as specified by the security policy.
-
What is the outcome when a Linux administrator enters the man man command?
- The man man command configures the network interface with a manual address
- The man man command provides a list of commands available at the current prompt
- The man man command provides documentation about the man command
- The man man command opens the most recent log file
Answers Explanation & Hints: The man command is short for manual and is used to obtain documentation about a Linux command. The command man man would provide documentation about how to use the manual.
-
Which Linux command can be used to display the name of the current working directory?
- ps
- pwd
- chmod
- sudo
Answers Explanation & Hints: One of the most important commands in Linux is the pwd command, which stands for print working directory. It shows users the physical path for the directory they are working in.
-
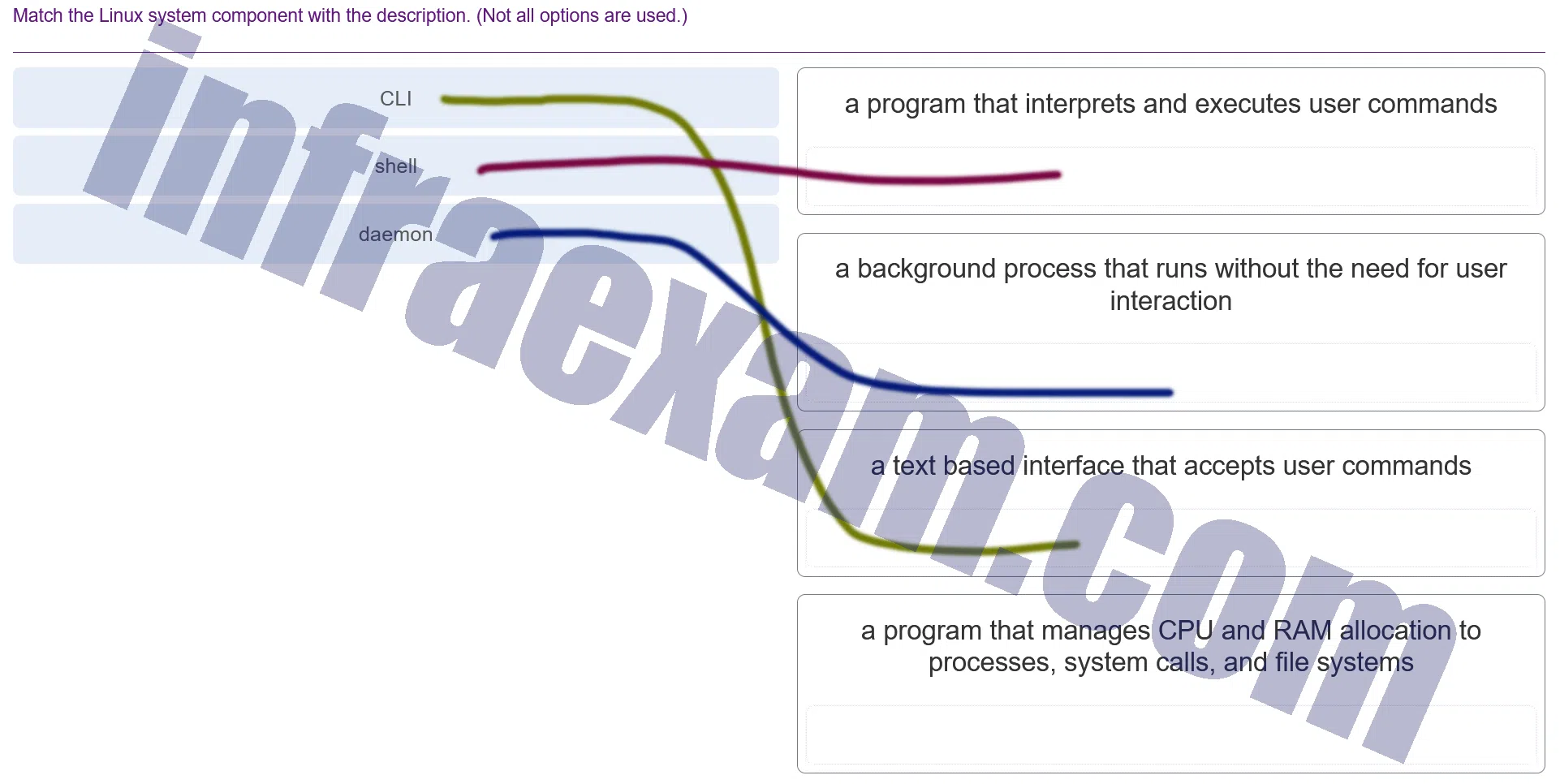
Match the Linux system component with the description. (Not all options are used.)
Modules 3 – 4 Operating System Overview Group Exam Answers 005 Explanation & Hint: - CLI (Command Line Interface) – This is a text-based interface that accepts user commands. It allows users to interact with the system by typing commands into a console or terminal.
- Shell – A shell is a program that interprets and executes user commands. It acts as an interface between the user and the kernel of the operating system.
- Daemon – A daemon is a background process that runs without the need for user interaction. These processes usually start at boot time and are independent of user sessions.
- The description “a program that manages CPU and RAM allocation to processes, system calls, and file systems” most likely refers to the kernel. The kernel is the core component of the operating system that manages these resources and facilitates interactions between hardware and software components.
-
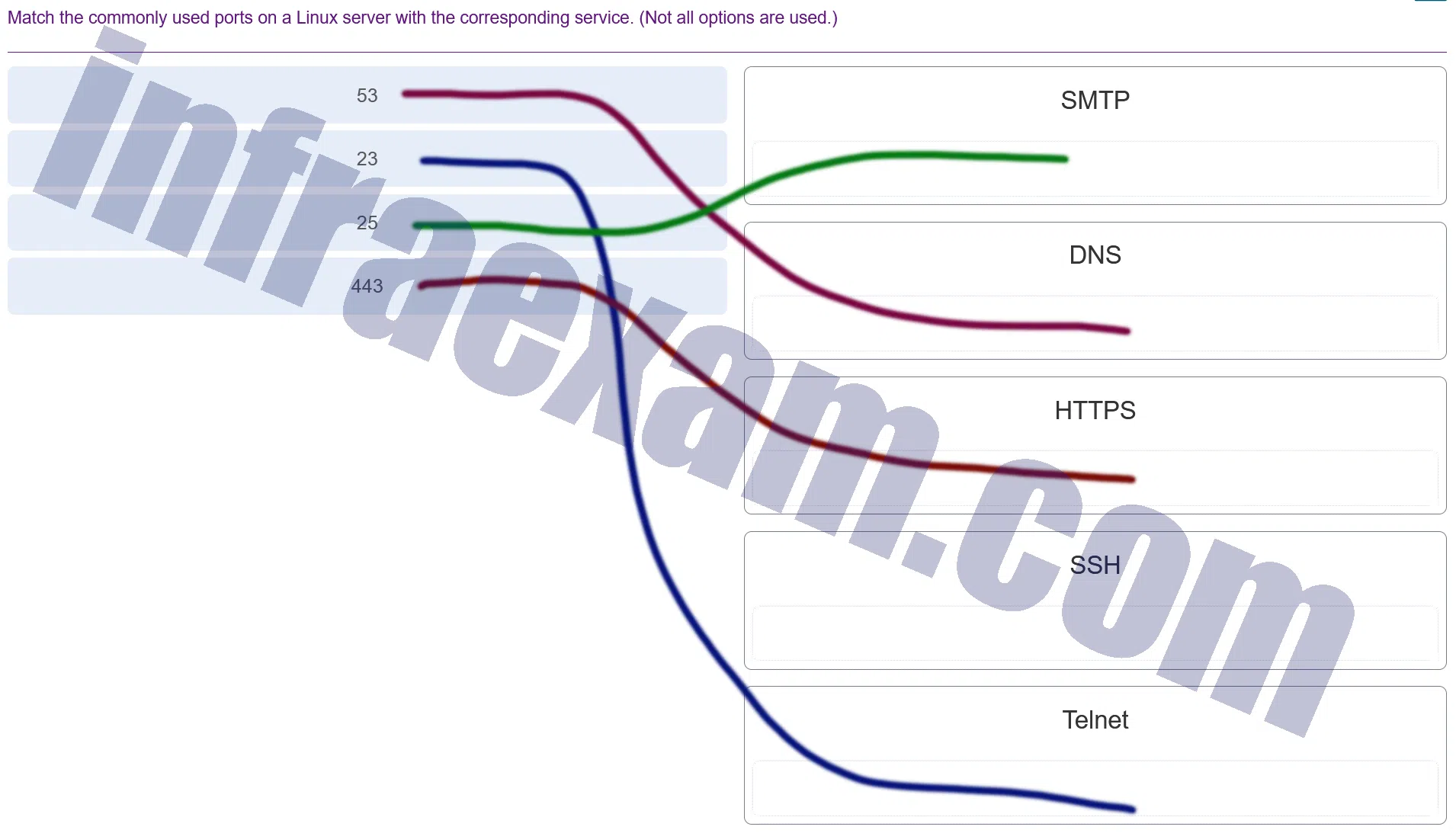
Match the commonly used ports on a Linux server with the corresponding service. (Not all options are used.)
Modules 3 – 4 Operating System Overview Group Exam Answers 006 Explanation & Hint: - Port 25: This is commonly used by SMTP (Simple Mail Transfer Protocol) for email routing between mail servers.
- Port 53: This port is used by DNS (Domain Name System) for translating domain names into IP addresses.
- Port 443: HTTPS (Hypertext Transfer Protocol Secure) uses this port for secure communication over a computer network within a web browser, utilizing encryption.
- Port 23: Telnet, a protocol used for accessing remote computers, uses this port.
- Port 22: Not shown in your list, but SSH (Secure Shell) uses this port for securely accessing remote machines over a network.
Each of these ports is associated with a specific protocol that enables various services on a network. In your activity, you would draw lines to match each port number to the service it is commonly used for.
-
What is the well-known port address number used by DNS to serve requests?
- 25
- 110
- 53
- 60
Answers Explanation & Hints: Port numbers are used in TCP and UDP communications to differentiate between the various services running on a device. The well-known port number used by DNS is port 53.
-
Which two methods can be used to harden a computing device? (Choose two.)
- Allow USB auto-detection.
- Ensure physical security.
- Enforce the password history mechanism.
- Allow default services to remain enabled.
- Update patches on a strict annual basis irrespective of release date.
Answers Explanation & Hints: The basic best practices for device hardening are as follows:
Ensure physical security.
Minimize installed packages.
Disable unused services.
Use SSH and disable the root account login over SSH.
Keep the system updated.
Disable USB auto-detection.
Enforce strong passwords.
Force periodic password changes.
Keep users from reusing old passwords.
Review logs regularly.
-
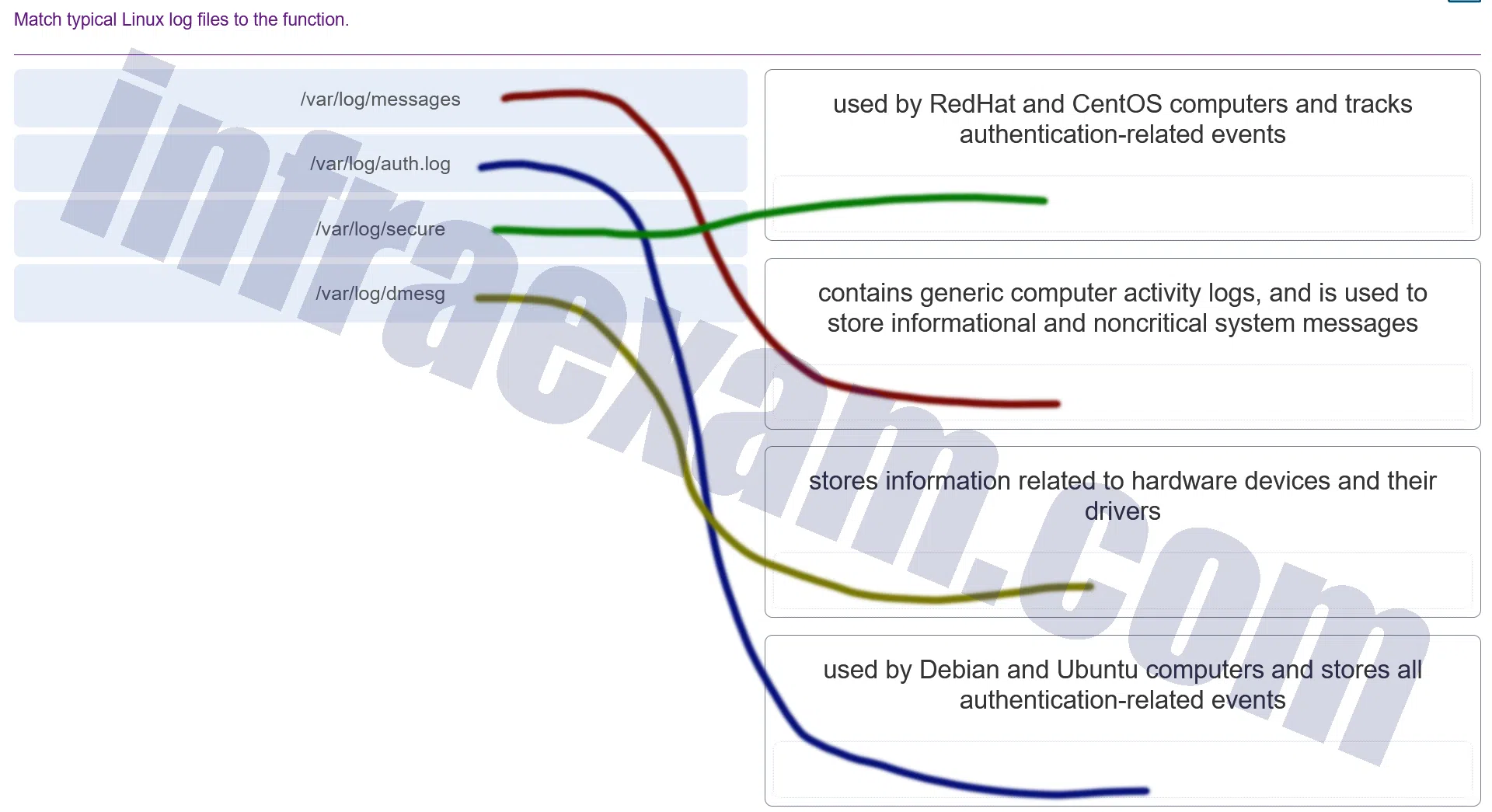
Match typical Linux log files to the function.
Modules 3 – 4 Operating System Overview Group Exam Answers 007 Explanation & Hint: /var/log/messages: This log file typically contains global system messages, including the messages that are logged during system startup. It includes a variety of messages by system applications outside the kernel, especially system daemons. It’s one of the primary logs you would check for troubleshooting general issues./var/log/auth.log: This log file is used by Debian-based systems such as Ubuntu to record authentication logs, including user logins and authentication mechanisms that have been triggered./var/log/secure: This is the equivalent ofauth.logon RedHat-based systems like CentOS and Fedora. It tracks security-related events such as authentication failures and sudo log entries./var/log/dmesg: This log file contains kernel ring buffer messages. It is useful for finding hardware and driver messages that are generated during the boot process. After the system has booted, it can also be used to find messages related to hardware events.
Each log file has its specific use cases and is critical for system administrators when monitoring and diagnosing system issues. Understanding where to find and how to interpret these logs is an essential skill in Linux system administration.
-
Consider the result of the ls -l command in the Linux output below. What are the file permissions assigned to the sales user for the analyst.txt file?
ls –l analyst.txt -rwxrw-r-- sales staff 1028 May 28 15:50 analyst.txt
- read, write, execute
- read only
- read, write
- write only
Answers Explanation & Hints: The file permissions are always displayed in the User, Group and Other order. In the example displayed, the file has the following permissions:
The dash ( – ) means that this is a file. For directories, the first dash would replaced with a “d”.
The first set of characters is for user permission (rwx). The user, sales, who owns the file can read, write and execute the file.
The second set of characters is for group permissions (rw-). The group, staff, who owns the file can read and write to the file.
The third set of characters is for any other user or group permissions (r–). Any other user or group on the computer can only read the file.
-
Which user can override file permissions on a Linux computer?
- any user that has ‘group’ permission to the file
- root user
- any user that has ‘other’ permission to the file
- only the creator of the file
Answers Explanation & Hints: A user has as much rights to a file as the file permissions allow. The only user that can override file permission on a Linux computer is the root user. Because the root user has the power to override file permissions, the root user can write to any file.
-
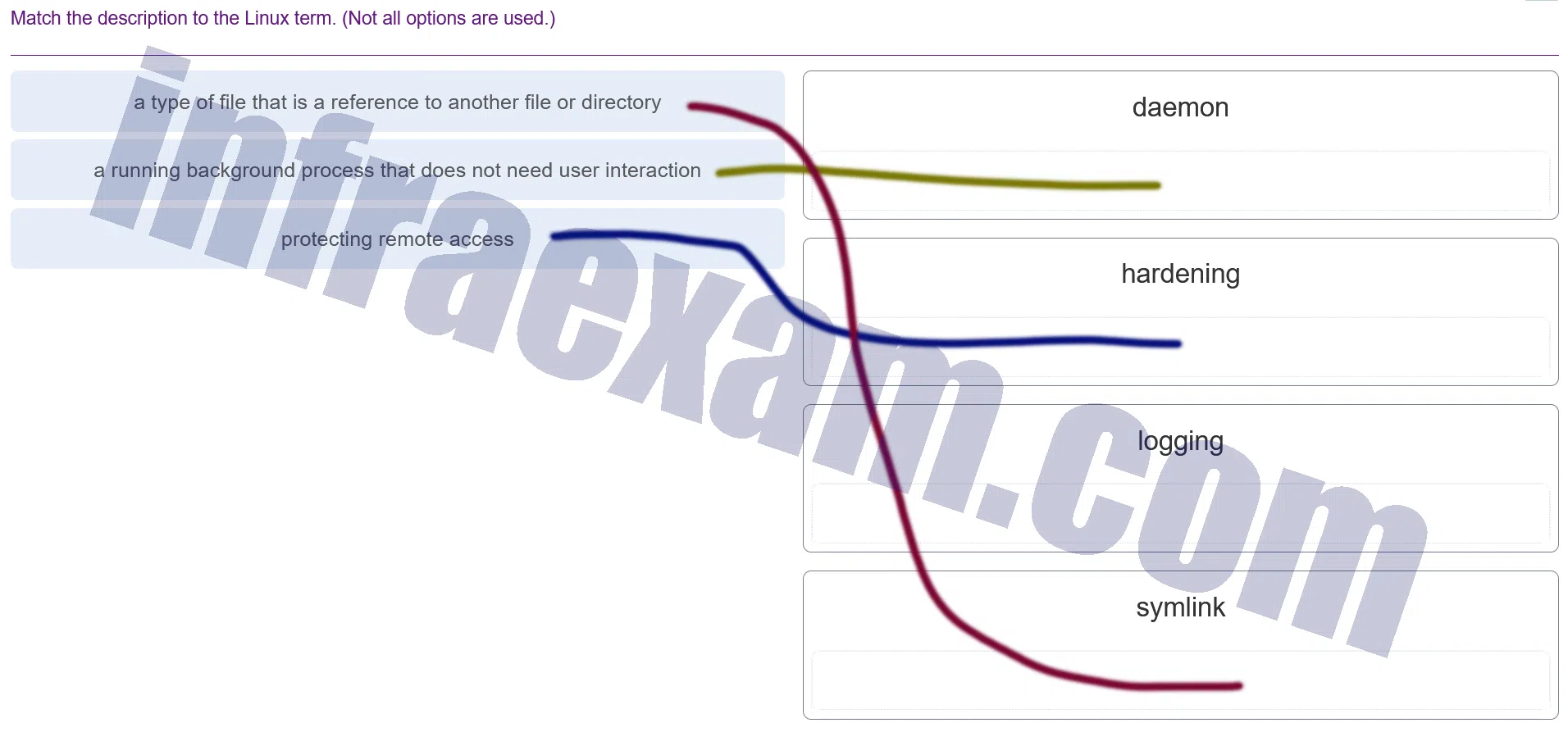
Match the description to the Linux term. (Not all options are used.)
Modules 3 – 4 Operating System Overview Group Exam Answers 008 Explanation & Hint: - Daemon – This is a running background process that does not need user interaction. Daemons are common in Unix and Unix-like operating systems, such as Linux, performing various tasks behind the scenes.
- Hardening – This term refers to the process of securing a system by reducing its surface of vulnerability, which includes “protecting remote access” to the system. Hardening involves implementing a set of standards and best practices to mitigate security risks.
- Symlink (Symbolic Link) – This is “a type of file that is a reference to another file or directory.” A symbolic link is a pointer to another file or directory and can be used to create shortcuts or to mask the complexity of a file system.
Based on the descriptions listed, the connections should be as follows:
- Daemon to “a running background process that does not need user interaction.”
- Hardening to “protecting remote access.”
- Symlink to “a type of file that is a reference to another file or directory.”
-
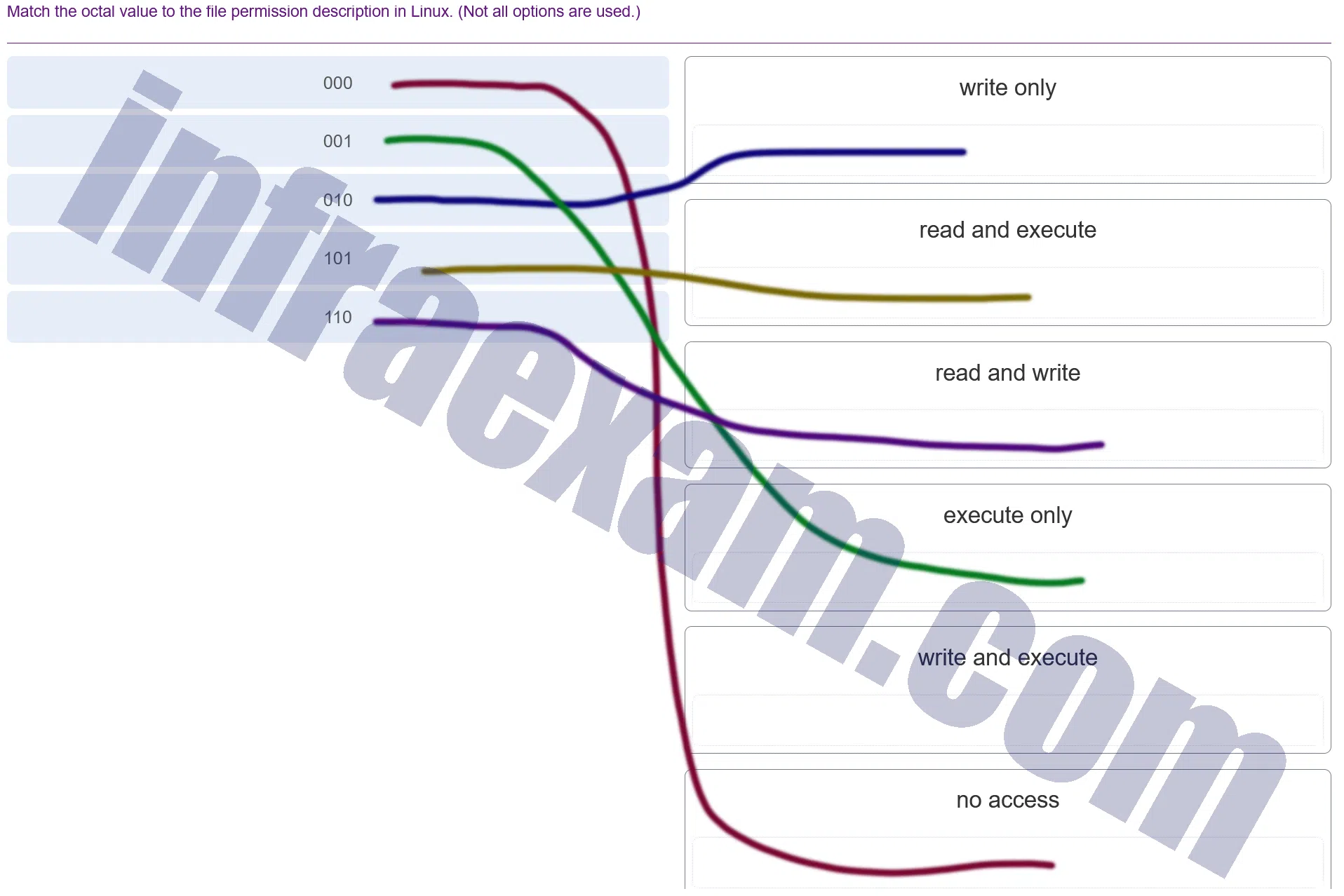
Match the octal value to the file permission description in Linux. (Not all options are used.)
Modules 3 – 4 Operating System Overview Group Exam Answers 009 Explanation & Hint: In Linux file permissions, there are three types of access:
- Read (r)
- Write (w)
- Execute (x)
These permissions are represented numerically as:
- Read (r) = 4
- Write (w) = 2
- Execute (x) = 1
The octal value is a sum of these numbers:
- 0 means no permissions
- 1 means execute only
- 2 means write only
- 3 means write and execute (2+1)
- 4 means read only
- 5 means read and execute (4+1)
- 6 means read and write (4+2)
- 7 means read, write, and execute (4+2+1)
For example, an octal value of 644 in a Linux system would give the owner of the file read and write permissions (6), and the group and others read-only permissions (4).
-
What are two benefits of using an ext4 partition instead of ext3? (Choose two.)
- compatibility with CDFS
- compatibility with NTFS
- decreased load time
- improved performance
- an increase in the number of supported devices
- increase in the size of supported files
Answers Explanation & Hints: Based on the ex3 file system, an ext4 partition includes extensions that improve performance and an increase in the of supported files. An ext4 partition also supports journaling, a file system feature that minimizes the risk of file system corruption if power is suddenly lost to the system.
-
In the Linux shell, which character is used between two commands to instruct the shell to combine and execute these two commands in sequence?
- $
- |
- #
- %
Answers Explanation & Hints: In the Linux shell, several commands can be combined to perform a complex task. This technique is known as piping. The piping process is indicated by inserting the character “|” between two consecutive commands.
-
Why is Linux considered to be better protected against malware than other operating systems?
- customizable penetration and protection tools
- fewer deployments
- file system structure, file permissions, and user account restrictions
- integrated firewall
Answers Explanation & Hints: The Linux operating design including how the file system is structured, standard file permissions, and user account restrictions make Linux a better protected operating system. However, Linux still has vulnerabilities and can have malware installed that affects the operating system.
| CyberOps - Associate 1.0 & 1.01 | |
| Final Exam Answers | |
| This Modules 3 - 4 | |
| Modules 3 - 4 Exam Answers | Online Test |
| Next Modules 5 - 10 | |
| Modules 5 - 10 Exam Answers | Online Test |