CCNA3 ENSA Practice PT Skills Assessment (PTSA) Answers v7 & v7.02
CCNA3 ENSA Practice PT Skills Assessment (PTSA) Answers v7 & v7.02
Enterprise Networking, Security, and Automation (Version 7.00) – ENSA Practice PT Skills Assessment (PTSA)
ENSA Practice PT Skills Assessment (PTSA) (Answers Version)
Text in red and gray highlight does not appear in the student version of these instructions.
This assessment activity is designed to provide practice in preparation for the final Skills Assessment in this course. This activity uses variables to create variations of this assessment that are presented to the student. The variations consist of changes to the topology layout and labeling and the names of the devices. These device naming variations appear in the instructions as well as the topologies. This means that students will receive different versions of the assessment that combine different names and labels with different topology layouts. There are a number of possible combinations. Each time the student starts the assessment, they will receive a different variation unless they are resuming work on a previously saved assessment.
In the instructions below, values that are contained in double brackets, such as [[Router0Name]], are placeholders for values that will vary for each assessment. Students will not see the double-bracketed terms, instead they will see the device names and labels for their version of the activity.
The variations that students will receive do not affect the difficulty of the assessment activities.
In addition, you will find this assessment activity to be more “open-ended” than some of the activities that the student has experienced in the initial portion of the course. As the course progresses, the instructions become less prescriptive, allowing the student the opportunity to get a better measure of their knowledge and skills. More “open-ended” requirements also allow the Answers the opportunity to target misconceptions or weak areas for students. Students are given the overall requirement to complete or goal to achieve but not the specific details on how to achieve success. This presents a more real-world assessment of their preparedness for the tasks and gives them an opportunity to explore where they may need more study and practice before taking the final Skills Assessment for the course. Depending on the nature of the Skills Assessment you will provide to your students, you may want to provide more or less guidance to optimize the learning experience for your students.
A few things to keep in mind while completing this activity:
- Do not use the browser Back button or close or reload any exam windows during the exam.
- Do not close Packet Tracer when you are done. It will close automatically.
- Click the Submit Assessment button in the browser window to submit your work.
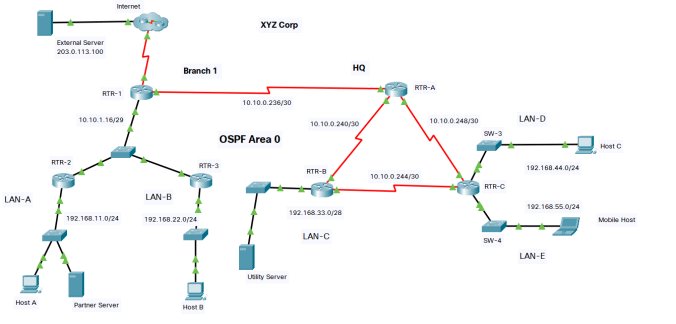
Topology
Addressing Table
|
G0/0/0 |
10.10.1.17/29 |
|
|
[[R1Name]] |
G0/0/0 |
10.10.1.17/29 |
|
[[R1Name]] |
S0/1/0 |
10.10.0.237/30 |
|
[[R1Name]] |
S0/1/1 |
192.0.2.113/29 |
|
[[R2Name]] |
G0/0/0 |
192.168.11.1/24 |
|
[[R2Name]] |
G0/0/1 |
10.10.1.18/29 |
|
[[R3Name]] |
G0/0/0 |
192.168.22.1/24 |
|
[[R3Name]] |
G0/0/1 |
10.10.1.19/29 |
|
[[[[R4Name]]R4Name]] |
S0/1/0 |
10.10.0.249/30 |
|
[[R4Name]] |
S0/1/1 |
10.10.0.241/30 |
|
[[R4Name]] |
S0/2/0 |
10.10.0.238/30 |
|
[[R5Name]] |
G0/0/0 |
192.168.33.1/28 |
|
[[R5Name]] |
S0/1/0 |
10.10.0.245/30 |
|
[[R5Name]] |
S0/1/1 |
10.10.0.242/30 |
|
[[R6Name]] |
G0/0/0 |
192.168.44.1/24 |
|
[[R6Name]] |
G0/0/1 |
192.168.55.1/24 |
|
[[R6Name]] |
S0/1/0 |
10.10.0.250/30 |
|
[[R6Name]] |
S0/1/1 |
10.10.0.246/30 |
|
[[PC1Name]] |
NIC |
192.168.11.11 |
|
[[PC2Name]] |
NIC |
192.168.22.22 |
|
[[PC3Name]] |
NIC |
192.168.44.44 |
|
[[WGServerName]] |
NIC |
192.168.33.14 |
|
[[IntServerName]] |
NIC |
192.168.11.100 |
|
[[LaptopName]] |
NIC |
192.168.55.55 |
|
[[InternetServerName]] |
NIC |
203.0.113.100 |
Introduction
You are completing the configuration of the [[CompanyName]] network.
You are not required to configure host addressing.
You will practice and be assessed on the following skills:
Configuration of OSPFv2 routing
Customization of OSPF.
Configuration of static NAT.
Configuration of dynamic NAT with PAT.
Configuration of various types of ACLs.
Configuration of a router with NTP as a system time source.
Backing up an IOS image to a TFTP server.
Instructions
Part 1: Configure OSPF
Step 1: Activate OSPF.
Use process ID 10 for OSPF activation on all routers.
- Activate OSPF by configuring the interfaces of the network devices in the [[Net1Name]] network, where required.
- Activate OSPF using network statements and inverse masks on the routers in the [[Net2Name]] network.
Note: For the purposes of this assessment, please enter the network statements in the following order:
1) On [[R4Name]]
the Serial0/1/1 network
the Serial0/2/0 network
the Serial0/1/0 network
2) On [[R5Name]]
the Serial0/1/1 network
the Serial0/1/0 network
the GigabitEthernet0/0/0 network
3) On [[R6Name]]
the Serial0/1/0 network
the Serial0/1/1 network
the GigabitEthernet0/0/0 network
the GigabitEthernet0/0/1 network
Step 2: Configure router IDs.
Configure router IDs on the multiaccess network routers as follows:
[[R1Name]]: 9.9.9.9
[[R2Name]]: 8.8.8.8
[[R3Name]]: 7.7.7.7
Step 3: Customize OSPF operation.
- Configure router [[R1Name]] with the highest OSPF interface priority so that it will always be the designated router of the multiaccess network.
- On router [[R1Name]], configure a default route to the ISP cloud using the exit interface command argument.
- Automatically distribute the default route to all routers in the network.
- Configure the hello and dead timer values on the interfaces that connect [[R1Name]] and [[R4Name]] to be twice the default values.
- Configure the OSPF routers so that the default cost value for all Gigabit Ethernet interfaces will be 10 and the cost value for Fast Ethernet will be 100.
- Configure the OSPF cost value of [[R4Name]] interface Serial0/1/1 to 50.
- Configure OSPF so that routing updates are not sent into networks where OSPF updates are not required.
Part 2: Configure NAT
In this part of the practice skills assessment, you will configure static and dynamic NAT at the network edge.
Step 1: Configure static NAT
Configure static NAT to translate the address of the [[IntServerName]] on LAN 1 to the public address of 192.0.2.115. Verify that the translations are occurring.
Step 2: Configure dynamic PAT.
- Create access list 1 to allow all addresses in the 192.168.0.0/16 network to be translated.
- Create a NAT pool named POOL-1. It should use address in the range 192.0.2.116 -192.0.118.
- Configure NAT to dynamically use the addresses in the pool for all traffic entering and exiting the company network. Remember that it is likely that more than three hosts will be accessing traffic on the Internet.
Part 3: Configure ACLs
Configure access control lists to meet the following requirements.
Note: Use host and any keywords whenever possible. Always explicitly configure the default deny condition when it is to be used as part of the ACL functionality so that it can be logged when the condition is met. You do not need to specify the default deny condition if it is counteracted with permit ip any any for this assessment. All ACLs should be placed in the most efficient location possible according to the guidelines specified in the curriculum.
- Create a named standard access list to explicitly prevent all external traffic accessing the telnet lines on R1. Name the list VTY-BLOCK. All addresses on the 192.168.0.0/16 network only should be allowed to access the VTY lines. Verify that the list works as specified.
- Create a numbered standard ACL to prevent all hosts on LAN 1 from accessing LAN 2. Use 10 as the number for the list.
- Create an extended numbered ACL that will prevent traffic from the LAN 4 network from accessing the HTTP service that is running on [[WGServerName]]. All other traffic from LAN 4 hosts should be able to access the network. Number the list 101.
Part 4: Manage Network Devices
Step 1: Configure NTP
Configure router [[R5Name]] to use [[WGServerName]] as its time source.
Step 2: Backup IOS to Server
Backup the IOS image file on router [[R5Name]] to [[WGServerName]].
Answer Configurations
R1 possible names: BD-1; RTR-1; RTR-A
———————————
ena
conf t
!
interface GigabitEthernet0/0/0
ip ospf priority 255
ip ospf 10 area 0
ip nat inside
!
interface Serial0/1/0
ip ospf hello-interval 20
ip ospf dead-interval 80
ip ospf 10 area 0
!
interface Serial0/1/1
ip nat outside
!
router ospf 10
router-id 9.9.9.9
auto-cost reference-bandwidth 10000
default-information originate
!
access-list 1 permit 192.168.0.0 0.0.255.255
!
ip nat pool POOL-1 192.0.2.116 192.0.2.118 netmask 255.255.255.248
ip nat inside source list 1 pool POOL-1 overload
ip nat inside source static 192.168.11.100 192.0.2.115
ip route 0.0.0.0 0.0.0.0 Serial0/1/1
!
ip access-list standard VTY-BLOCK
permit 192.168.0.0 0.0.255.255
deny any
!
line vty 0 4
access-class VTY-BLOCK in
!
ntp server 192.168.11.100
!
end
R2 possible names: BD-2; RTR-2; RTR-B
———————
enable
conf t
!
access-list 100 deny tcp any host 192.168.11.100 eq www
access-list 100 permit ip any any
!
interface GigabitEthernet0/0/0
ip ospf 10 area 0
!
interface GigabitEthernet0/0/1
ip ospf 10 area 0
ip access-group 100 in
!
router ospf 10
router-id 8.8.8.8
passive-interface GigabitEthernet0/0/0
auto-cost reference-bandwidth 10000
!
end
R3 possible names: BD-3; RTR-3; RTR-C
—————–
enable
conf t
!
access-list 10 deny 192.168.11.0 0.0.0.255
access-list 10 permit any
!
interface GigabitEthernet0/0/0
ip ospf 10 area 0
!
interface GigabitEthernet0/0/1
ip ospf 10 area 0
ip access-group 10 in
!
router ospf 10
router-id 7.7.7.7
passive-interface GigabitEthernet0/0/0
auto-cost reference-bandwidth 10000
!
end
R4 possible names: PP-1; RTR-A; RTR-1
————–
ena
conf t
!
interface Serial0/1/1
ip ospf cost 50
!
interface Serial0/2/0
ip ospf hello-interval 20
ip ospf dead-interval 80
no cdp enable
!
router ospf 10
auto-cost reference-bandwidth 1000
network 10.10.0.240 0.0.0.3 area 0
network 10.10.0.236 0.0.0.3 area 0
network 10.10.0.248 0.0.0.3 area 0!
end
R5 possible names: PP-2; RTR-B; RTR-2
—————
ena
conf t
!
router ospf 10
log-adjacency-changes
passive-interface GigabitEthernet0/0/0
auto-cost reference-bandwidth 1000
network 10.10.0.240 0.0.0.3 area 0
network 10.10.0.244 0.0.0.3 area 0
network 192.168.33.0 0.0.0.15 area 0
!
ntp server 192.168.3.14
!
end
====backup IOS image to tftp
You will need to copy the IOS image to the server. The command will give you a series of prompts. I have provided you with the prompts and the correct answers. You can select the answers that come after the first two prompts and paste them in after the prompt on the router. The last prompt, you just press the <Enter> key. The process of copying the file takes some time. You can move on to another device while the command completes execution.
Enter the interactive command:
copy flash tftp
Source filename []? isr4300-universalk9.03.16.05.S.155-3.S5-ext.SPA.bin
Address or name of remote host []? 192.168.33.14
Destination filename [isr4300-universalk9.03.16.05.S.155-3.S5-ext.SPA.bin]? Press <Enter>
R6 possible names: PP-3; RTR-C; RTR-3
—————–
ena
conf t
!
access-list 101 deny tcp any host 192.168.33.14 eq www
access-list 101 permit ip any any
!
interface GigabitEthernet0/0/0
ip access-group 101 in
!
router ospf 10
passive-interface GigabitEthernet0/0/0
passive-interface GigabitEthernet0/0/1
auto-cost reference-bandwidth 1000
network 10.10.0.248 0.0.0.3 area 0
network 10.10.0.244 0.0.0.3 area 0
network 192.168.44.0 0.0.0.255 area 0
network 192.168.55.0 0.0.0.255 area 0
!
end