200-201 : Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) : Part 04
-
Which of the following represents an attack source?
- threat actor
- attack vector
- action on objectives
- host file
Explanation:
A threat actor is anyone posing a threat through malicious activity. Some well-known threat actors globally are:– APT10 – a Chinese group that has been around since early 2009. Their primary mission seems to be targeting defense contractors around the world.
– Turla – a popular Russian group most known for targeting government agencies around the world.
– Gosya – A popular Russian hacker who has been spotted selling the infamous Nuke Bot.
– Darkhotel – obtained their name from compromising hotel Wifi systems.
– Mr. Po Panda – This actor’s primary focus has been to deface company websites.
– ||JackSparrow|| – This actor is a member of a hacktivist group called Turk Hack. They try to claim themselves as researchers but have been known to conduct website defacements unexpectedly.A host file is a file on a Windows machine that can contain manual IP address to name mappings.
The attack vector is not the individual. It is the method used by the threat actor. Attack vectors include:
– viruses
– e-mail attachments
– Web pages
– pop-up windows
– instant messages
– chat roomsAction on objectives refers to the goal of the hacker. For example, it might be to deliver a ransomware letter.
-
Which of the following is NOT an element of the NIST.SP800-61 r2 incident response plan?
- organizational mission
- organizational approach
- siloed approach to communication
- strategies and goals
Explanation:
Rather than a siloed approach, the incident response approach should encourage and specify communication between the team and the organization and other organizations. In a siloed approach, the team has little communication with the organization and other organizations during the response.NIST SP 800-61 v2 is the Computer Security Incident Handling Guide. According to this publication, the four major phases of the incident response lifecycle are:
1. Preparation
2. Detection and analysis
3. Containment, eradication, and recovery
4. Post incident analysisThe NIST’s incident response plan elements are:
– Incident response plan’s mission
– Strategies and goals of the incident response plan
– Senior management approval of the incident response plan
– Organizational approach to incident response
– How the incident response team will communicate with the rest of the organization and with other organizations
– Metrics for measuring the incident response capability and its effectiveness
– Roadmap for maturing the incident response capability
– How the program fits into the overall organization -
Which of the following Cisco tools makes retrospective analysis possible?
- Cisco AMP
- Cisco Ironport
- Cisco Talos
- Cisco ASA
Explanation:
Cisco Advanced Malware Protection (AMP) comes in a Network version and an Endpoint version. It can use threat intelligence to perform retrospective (looking back in time) analysis. This would allow an administrator to do something like determine when malware entered your network, as in many cases it enters long before you discover it.Cisco Advanced Security Appliance (ASA) is the standard Cisco firewall product and does not do retrospective analysis.
Cisco Ironport comes in a web version and email version, and is designed to protect those types of systems. It does not perform retrospective analysis.
Although Cisco Talos feeds are sometimes used in the process of performing retrospective analysis, it is not the component that does it. Cisco Talos is the threat intelligence sharing system that Cisco uses for all customers of the feature. The Talos team protects data, and infrastructure. Its researchers, data scientists, and engineers collect information about existing and developing threats. They then deliver protection against attacks and malware. Talos underpins the entire Cisco security ecosystem.
-
What is the first step in establishing an internal CSIRT?
- Defining the CSIRT constituency
- Developing the process and policies for the CSIRT
- Making sure that the proper budget is allocated
- Deciding where the CSIRT will reside within the organization’s hierarchy
Explanation:
Establishing a CSIRT involves the following steps:Step 1. Define the CSIRT constituency
Step 2. Ensure management and executive support
Step 3. Allocate the proper budget
Step 4. Decide where the CSIRT will reside within the Organization’s hierarchy
Step 5. Determine whether the team will be central, distributed, or virtual
Step 6. Develop the process and policies for the CSIRT -
Which section of the IP header defines the entire packet size in bytes, including header and data?
- Identification
- Total length
- IP address
- Version
Explanation:
The total length field in the IP header indicates the entire packet size in bytes, including header and data. While this is not the most useful field in intrusion analysis, it is good to know what it describes.The first header field in an IP packet is the four-bit version field. For Pv4, this is always equal to 4. The source and destination IP address fields contain the source and destination IP addresses. The identification field is primarily used for uniquely identifying the group of fragments of a single IP datagram.
-
In the HTTP header, which of the following header fields indicates the domain name of the server (for virtual hosting) and the TCP port number on which the server is listening?
- urgent pointer
- referrer
- authorization
- date
- host
Explanation:
The host field indicates the domain name of the server (for virtual hosting) and the TCP port number on which the server is listening.Other examples of HHTP header fields are:
– Accept – Media type(s) that is (/are) acceptable for the response
– Content-Length – The length of the request body in octets (8-bit bytes)
– From – The email address of the user making the request
– Referrer – the address of the previous web page from which a link to the currently requested page was followed
– Host – The domain name of the server (for virtual hosting), and the TCP port number on which the server is listening
– Date – The date and time that the message was originated
– Authorization – Authorization credentials for HTTP authenticationThere is no urgent pointer field in an HTTP header. This field is found in TCP headers. The following lists the fields found in a TCP header:
– Urgent Pointer: Refers to the first urgent data byte in the packet.
– Sequence Number: Refers to the first byte of data in the current message. This field helps TCP to reassemble the packets in the correct order. For example, when data is transferred between an FTP server and FTP client, the receiver uses this field to reassemble the packets into the original file.
– Data Offset: Refers to the number of 32-bit words in the TCP header.
– Windows: Refers to the size of the available space for the incoming data.
– Source Port and Destination Port: Refer to the point where upper-layer source and destination processes receive TCP services. Both TCP and UDP packets contain these fields.
– Acknowledgement Number: Refers to the sequence number of the next byte of data that the sender will receive.
– Reserved: Reserved for future use.
– Flags: Contains control information, such as the SYN and ACK bits which are used to establish and acknowledge communication, and the FIN bit which is used to terminate the connection.
– Checksum: An indicator of any damage to the header while being in transit. Both TCP and UDP packets contain this field.
– Options: Used to specify TCP options. Only TCP packets this field.
– Data: has upper-layer information. -
The IDS alerted you there was an attack when there was none.
What is called?
- True negative
- False positive
- False negative
- True positive
Explanation:A false positive means the IDS mistakenly (False) identified an attack (positive). A true positive means the IDS correctly (True) detected an issue positive). A false negative means the system made a mistake (False) and missed (negative) an issue. A true negative means the IDS correctly (True) did not detect an issue (negative).
-
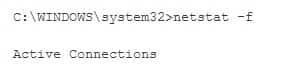
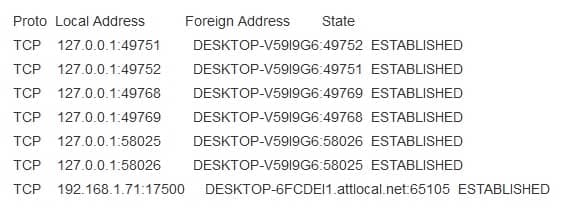
Which netstat command displays Ethernet statistics?
- netstat –a
- netstat –b
- netstat –f
- netstat –e
Explanation:
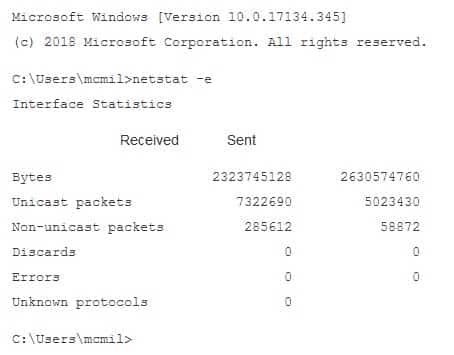
The netstat –e command displays Ethernet statistics. An example output is shown below:
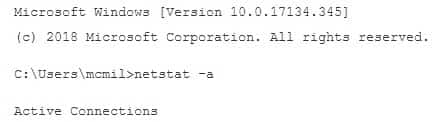
200-201 Part 04 Q08 003 The netstat –a command shows all connections and listening ports:
200-201 Part 04 Q08 004 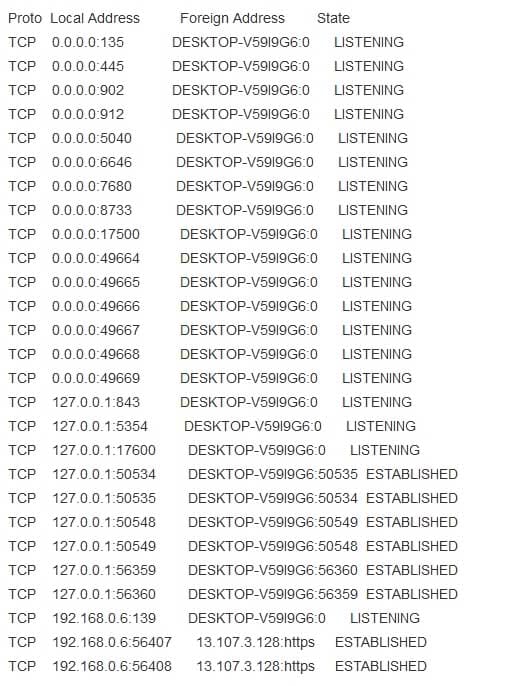
200-201 Part 04 Q08 005 The netstat –b command displays the executable involved in creating the connection
200-201 Part 04 Q08 006 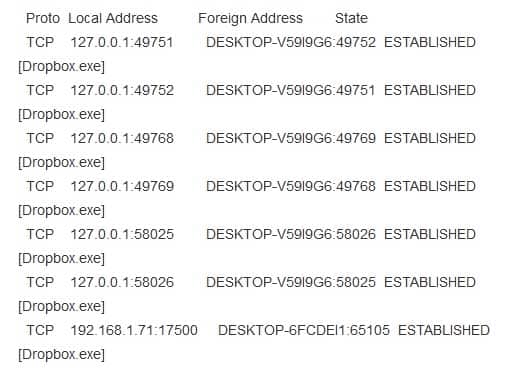
200-201 Part 04 Q08 007 The netstat –f command displays fully qualified domain names for foreign addresses.
-
What application protocol is in use in this capture?
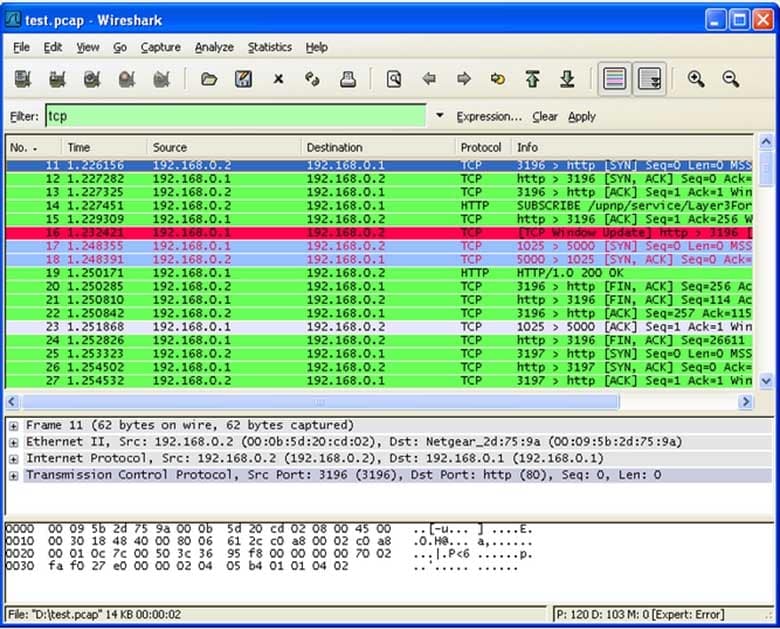
200-201 Part 04 Q09 010 - HTTP
- DHCP
- SSL
- DNS
Explanation:
The application protocol is indicated in the details section as the destination port of 80, which is HTTP.The application protocol is not DHCP. Were that the case, the destination port numbers in the details section would be 67 and 68.
DNS is not the protocol in use. Were it in use, the destination port number in the details section would be 53.
If SSL were the application protocol, the destination would have been port 443.
You should be familiar with the following common protocols and their ports:
– FTP 20,21
– SSH, SFTP 22
– TELNET 23
– SMTP 25
– DNS 53
– DHCP 67,68
– TFTP 69
– HTTP 80
– POP3 110
– NTP 123
– NetBIOS 137, 139
– IMAP 143
– SNMP 161
– LDAP 389
– SSL and HTTPS 443
– LDAPS 636
– MS SQL Server 1433 -
You suspect there is a threat against your DNS server that makes use of the query process.
What type of traffic should you monitor?
- UDP
- ARP
- TCP
- HTTP
Explanation:
You should monitor UDP traffic. DNS servers communicate queries using UDP. In one example of a DNS attack type that makes use of UDP (but not the only one), a malicious individual queries your DNS server for a record unknown to the DNS server. The server then does that it is designed to do, which is forward that query to the domain name listed in the record. In this attack, the listed domain is a malicious domain, and the malicious DNS server responds with a record, but within the record is hidden malware that infects the DNS server.Using DNS server logs, you can identify this type of communication by performing retrospective analysis to determine when the malware file entered the network.
Many security products maintain a list of communication by performing retrospective analysis to determine when the malware file entered the network.
Many security products maintain a list of known problematic DNS domains. They scan the DNS records (which can be huge in size) for matches and alert you to any communication with a known problem domain.
TCP is not used by DNS for queries. Query traffic will fit into a UDP packet. Because UDP is much faster than TCP, it was chosen as the transport protocol for queries. Reliability is provided by DNS at the application layer.
ARP is used to resolve IP addresses to MAC addresses. It is not a protocol used in DNS query communication.
HTTP is a protocol used by web servers and would be of no use in mapping to find a threat actor that involves DNS servers. However, HTTP headers can be used to map HTTP attacks to their source.
HTTP logs and DNS logs can be correlated to one another. The DNS log will show the domain name and IP address and by matching those to the HTTP log we can identify the contents of the HTTP header to identify the attack type.
-
Which statement is FALSE with respect to open ports?
- If it is listening, it is open
- Ports use values that range between 1 and 65535.
- Port 23 is FTP
- If you send a TCP packet with the SYN flag set, you will receive one with the SYN and ACK flags back.
Explanation:
Port 23 is not used by FTP. It is used by Telnet. Although port numbers do have defaults set for well-known services, you can always change the port on which a service is running.An open port is also called listening port in some instances. Open or listening ports have an available service running on them. It may or may not be the default service for that port. if the port is closed, it means a service is not available on that port.
Ports use values that range between 1 and 65535.
If you send a TCP packet with the SYN flag set, you will receive one with the SYN and ACL flags back if it is open. If it is closed, you will receive a packet with the RST flag set. If you receive no response, the port is filtered or blocked on the firewall.
-
Which of the following CVSS scores measures the extent to which the information resource can be changed due to an attack?
- Availability
- Confidentiality
- Integrity
- Attack vector
Explanation:
Integrity is the extent to which the information resource can be changed due to an attack.Confidentiality is the secrecy of an information resource managed by a software component due to an exploited vulnerability.
Availability measures the extent to which availability is at risk due to an attack.
Attack vector describe the nature of the vulnerability. Version 3.0 of CVSS sets the possible values for the confidentiality, integrity, and availability metrics to none, low, and high. These are explained below for integrity:
-
You are assessing application or service availability with a port scan. All services use default ports.
This is an example of what type of exploit analysis?
- deterministic
- predictive
- probabilistic
- intuitive
Explanation:
In deterministic analysis, all data used for analysis is known beforehand. An example of this type of analysis is port scanning because we clearly understand the rules of the TCP three-way handshake beforehand and we know the default port numbers.In probabilistic analysis don’t have all data beforehand and works on probabilities. Predictive analysis is not a term that is used when describing exploit analysis. Intuitive is also not a term used when describing exploit analysis.
-
Which action would be supportive of the concept of volatile data collection as describe in SP 800-86?
- collect memory data first
- collect volatile data after rebooting
- collect malware data
- collect hard drive data first
Explanation:
According to the concept of volatile data collection as covered in NIST 800-86, volatile data, meaning data that is gone after rebooting, should be collected first as it is fragile. Memory data should be collected first.All volatile data should be collected before, not after, rebooting while it still exists. You should not collect hard drive data first. This is not volatile data. The concept of data does not concern itself with data content, such as malware data. It is only concerned with the volatile data.
-
Which of the following is NOT one of the five tuples?
- source Ip address
- source port number
- destination IP address
- device name
Explanation:
The 5-tuple is a term used to describe the five significant parts of each TCP connection. The five elements which make each conversation unique are:– Source IP address
– Destination IP address
– Source port number
– Destination port number
– ProtocolBy using the 5-tuple to uniquely identify each communication, you can map data from various sources that refer to the same communication.
In a TCP connection, the source device creates the connection, the TCP three-way handshake occurs, and the destination accepts the connection. This handshake involves three TCP packets. The first packet has the SYN flag set, indicating a desire to make a connection. The destination answers back with a TCP packet with the SYN and ACK flags set, indicating a willingness to create the connection. Finally, the source finalizes the connection. Finally, the source finalizes the connection with a TCP packet with only the ACK flag set.
Device name is not one of the five tuples.
-
According to SP 800-86, which of the following is NOT volatile data?
- hibernation file
- slack space
- network configuration
- network connections
Explanation:
Hibernation files are created when a system hibernates or sleeps and are still there after rebooting. Slack space in memory where no data is located normally but can contain evidence. It goes way when rebooting. When a host received dynamic network configurations (DHCP) these configurations are lost when rebooting.
-
Which organizational stakeholders are responsible for installing anti-malware software?
- System and network administrators
- CEO
- CISO
- CSIRT team
Explanation:
The proper way to address malware, according to the NIST SP800-61 r2, is to install anti-malware software. The stakeholder group responsible for that is the system and network administrators. It is part of their duties to keep it up to date.It is not the responsibility of the Computer Security Incident Response Team (CSIRT). Their job is to identify and handle security incidents. It is not the responsibility of the Chief Information Security Officer. This role’s job is to manage security from a much higher level and to support all security efforts.
It is not the responsibility of the Chief Executive Officer. His job is to manage the entire organization, although this role’s support of all security efforts is critical.
-
Cisco Active Threat Analysis is an example of which of the following?
- MSSP
- PSIRT
- Coordination centers
- National CSIRT
Explanation:
Managed Security Service Providers (MSSPs) provide incident response and managed security services to their customers. The Cisco Incident Response Service is an example. Another example is Cisco Active Threat Analysis.Coordination centers around the world also help CSIRTS coordinate incident handling. They also help coordinate security vulnerability disclosures to vendors, hardware and software providers, and security researchers. One of the best examples is the CERT Division of the Software Engineering Institute (SEI).
Product security incident response teams (PSIRTs) handle the investigation, resolution, and disclosure of security vulnerabilities in their products and services.
A national Computer Security Incident Response Team (national CSIRT) provides cybersecurity protection to an entire country or a significant portion of a national economy, which would include protecting federal civilian or executive branch agencies. CSIRTs provide incident handling capabilities as well as training and coordination of vulnerability databases. Two well-known national CSIRTs are the Industrial Control Systems Cyber Emergency Readiness Team (ICS-CERT) and the United States Cyber Emergency Readiness Team (US-CERT).
-
What is the final step in the Cyber Kill Chain framework?
- exploitation
- command and control
- action on objectives
- installation
Explanation:
During the action on objectives step, the attacker achieves the long term goal. For example, it could be defacing a website or it could be stealing money. Exploitation comes after the attacker creates a weapon and delivers the weapon. It occurs when the weapon executes.Installation comes after exploitation and involves the installation of additional tools and resources the hacker will use. These tools allow the attacker to maintain persistence while plotting the next step. Installation of a remote access Trojan (RAT) would be part of the installation step.
Communication with well-known malicious IP address is part of the Command and Control step, since the remote device is quite likely a command and control server.
The seven steps in the kill chain are:
Reconnaissance is the attacker gathers information to aid in penetrating the network
Weaponization is the attacker turns a legitimate utility or function into a weapon that can be used in the attack
Delivery is the attacker transmits the crafted exploit to the target
Exploitation is the exploit is executed
Installation is the hacker installs additional tools and resources on the target device or in the target network
Command and control is the attacker takes remote control of the target device from the Command and Control server
Actions on objectives is the attacker takes action (deletes data, steals data, defaces website) -
Which of the following is the latest Linux file system?
- ext3
- ext2
- ext4
- ext5
Explanation:
Ext4 is the latest Linux file system. One of the improvements over ext3 is support for unlimited subdirectories. Ext4 modifies important data structures of the filesystem, such as the ones destined to store the file data. The result is a filesystem with an improved design, better performance, reliability, and features. Other improvements are:– Supports volumes with sizes up to 1 exibyte (EiB) and files with sizes up to 16 terabytes (TiB)
– Supports extens
– Is backwards compatible with ext3 and ext2
– Uses extents to replace the traditional block mapping scheme used by ext2 and ext3Ext2 was the first commercial-grade file system for Linux. It is no longer in use. The ext2 filesystem does not support journaling, which would help in recovery after a crash. Ext3 is the second version of the file system. The journaling feature in filesystems helps in recovery after a crash. The ext3 filesystem provides journaling capability.
There is no Ext5.