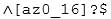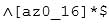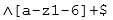200-201 : Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) : Part 05
-
Which of the following activities would be a part of retrospective analysis?
- scanning for vulnerabilities with NESSUS
- using historical data to identify an infected host
- using nmap to determine open ports
- attempting to exploit a vulnerability you found
Explanation:
Whenever you use historical data from logs to help identify a breach of any sort, you are engaged in retrospective analysis. A retrospective analysis is permed when the outcome of an event is already known, such as attempting to discover when identified malware first entered your system. GigaStor Security Forensics is another example of a tool that performs retrospective analysis.Using nmap to determine open ports is a part of network discovery stage of a penetration test. by identifying the open ports, potential attacks may be identified before they occur.
Scanning for vulnerabilities with NESSUS is a part of a vulnerability test. Attempting to exploit a vulnerability is a later stage in the penetration test.
-
What is the term for an operation that purges redundant data while maintaining data integrity?
- modularization
- aggregation
- warehousing
- normalization
Explanation:
Normalization is the process of eliminating redundancy and protecting integrity of the data. When data normalization is utilized with IPS systems, the IPS manages multiple incoming streams of data and ensures that all data exists only in one form. This eliminates redundant data. Normalization is the part of the security analysis process that reduces the sheer amount of data and makes the process cleaner and more efficient.Modularization is the breaking of a process into modules. A great example is the OSI model, which breaks the communication process down into seven modules or layers.
Aggregation is the process of taking data from multiple sources, such as IPS, firewall and router, and combining into a single integrated log file. A Security Information and Event (SIEM) system collects data from the different security devices in the system, such as firewalls and IPSs, and then aggregates the log files for analysis.
Data warehousing is the combination of data from multiple data sources or databases into a single repository for analysis and manipulation.
-
Which statement is FALSE with respect to listening ports?
- Port 443, when set to default, is encrypted.
- Ports can be numbered 1 to 65535.
- The port number does not always identify the service.
- They are closed.
Explanation:
Ports can be open, closed, or filtered. When they are open, they are said to be listening. When closed, they are not listening. While ports do have default port numbers, it is possible to run a service on a non-default port number.Software ports can be numbered from 1 to 65535. The first 1024 or so are called well-known. Some of these well-known port numbers as their defaults are:
– TCP 20 and 21: File transfer Protocol (FTP)
– TCP 22: Secure Shell (SSH)
– TCP 23: Telnet
– TCP 25: Simple mail Transfer Protocols (SMTP)
– TCP and UDP 53: Domain Name System (DNS)
– UDP 69: Trivial File Transfer Protocol (TFTP)
– TCP 79: Finger
– TCP 80: Hypertext Transfer Protocol (HTTP)
– TCP 110: Post Office Protocol v3 (POP3)
– TCP 119: Network News Protocol (NNTP)
– UDP 161 and 162: Simple Network Management Protocol (SNMP)
– UDP 443: Secure Sockets Layer over HTTP (HTTPS)Port 443 is SSL over HTTP, which is encrypted.
-
Which evidence is always considered the best evidence?
- hearsay
- indirect
- direct
- corroborative
Explanation:
Direct evidence is always considered the best because it does not require any reasoning or inference to arrive at the conclusion to be drawn from the evidence. An eyewitness account is direct evidence.Hearsay is never admissible in court. This is when someone testifies they heard someone else say something they witnessed (also called second hand). Corroborative evidence is that which supports other evidence. For example, is someone testifies they saw it raining and another said they heard rain, that is considered corroborative evidence. Indirect evidence suggests but does not prove anything. For example, if a man is accused of gambling and has been seen with gamblers, that is indirect evidence.
-
Which of the following offers incident handling services for a fee to other organizations?
- Coordination centers
- MISSP
- PSIRT
- national CSIRT
Explanation:
Managed Security Service Providers (MSSPs) provide incident response and managed security services to their customers. The Cisco Incident Response Service is an example. Another example is Cisco Active Threat Analysis.Coordination centers around the world also help with the coordination of security vulnerability disclosures to vendors, hardware and software providers, and security researchers. One of the best examples is the CERT Division of the Software Engineering Institute (SEI).
Product security incident response teams (PSIRTs) handle the investigation, resolution, and disclosure of security vulnerabilities in their products and services. National CSIRTS provide incident handling for a country. Examples include the US-CERT.
-
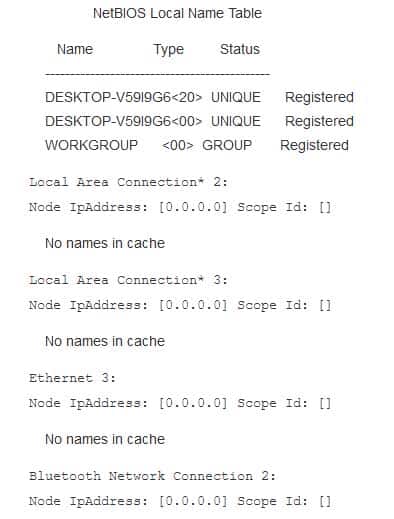
You have been asked to collect all the usernames from an access log. According to policy, usernames must be at least six characters and no more than sixteen characters. Usernames can only include lowercase letters, numbers, underscores, and hyphens, such as the following:
200-201 Part 05 Q06 012 Which regular expression will locate all valid usernames?
Explanation:
The regular expression Щ[a-z0-9_-]{6,16}$ will locate all valid usernames. The Щ and $ indicate the beginning and end of the pattern, respectively. The characters inside of the square brackets [] specify what is allowable, being a lowercase letter (a-z), number (0-9), underscore (_), or hyphen (-). The values in the curly braces {} specifies the minimum number of occurrences, being at least six, but no more than sixteen characters.The regular expression Щ[az0_16]?$ only finds usernames with a single characters a, z, 0, 1, _, or 6. Also, the question mark (?) will match these characters zero or one time, returning empty matches.
The regular expression Щ[a-z1-6]+$ will locate only usernames that contain one or more lowercase letters or the digits 1 through 6. The plus sign (+) will match one or more occurrence.
The regular expression Щ[az0_16]*$ will locate only usernames that contain the characters 1, z, 0, _, 1 or 6. Also, the asterisk (*) will match zero or more occurrences, returning empty matches.
-
After compromising a host and escalating privileges, the attacker installs a remote access Trojan (RAT).
What step of the Cyber Kill Chain framework has just occurred?
- Reconnaissance
- Exploitation
- Installation
- Weaponization
Explanation:
It is the installation step. Installation comes after exploitation and involves the installation tools and resources the hacker will use. These tools allow the attacker to maintain persistence while plotting the next step. Installation of a remote access Trojan (RAT) would be part of the installation step.It is not the reconnaissance step when information is gathered. For example, consider an exploit takes advantage of an injection vulnerability in an exploitable php by sending an HTTP POST with specific variables. If the hacker sends an HTTP GET request the page, the attack is still in reconnaissance.
It is not the weaponization step. Weaponization occurs when the attacker turns some utility or function into a weapon he can use in the attack. It occurs after reconnaissance. Using Metasploit to craft an exploit is an example.
It is not the exploitation step. Exploitation comes after the attacker creates a weapon and delivers the weapon. It occurs when the weapon executes. Were the user to execute the attachment we would be in the exploitation stage.
-
Which of the following represents the software that is acting on behalf of a user?
- representative agent field
- cookie
- type field
- host field
- user agent
Explanation:
The user agent is an HTTP header inside the software that is acting on behalf of a user. For example, it might indicate the browser type and capability. The User-Agent (UA) string is intended to identify devices requesting online content, which helps with intrusion analysis.The host field indicates the domain name of the server (for virtual hosting), and the TCP port number on which the server is listening.
– Other examples of HTTP header fields are:
– Accept – Media type(s) that is(are) acceptable for the response
– Content-Length – The length of the request body in octets (8-bit bytes)
– From – The email address of the user making the request
– Referrer – The address of the previous web page from which a link to the currently requested page was followed
– Host – The domain name of the server (for virtual hosting), and the TCP port number on which the server is listening
– Date – The date and time that the message was originated
– Authorization – Authentication credentials for HTTP authenticationCookies are text files with information with stored information about the user. They are not HTTP header fields. There is no representative agent field in the HTTP header. There is no type field in the HTTP header. The type field is the first field in an Internet Control Message Protocol (ICMP) header, and is used to indicate the function or purpose of the communication. A control message is the function or purpose of the ICMP communication.
Common examples of Types are:
– 8 for Echo Request
– 0 for Echo Reply
– 11 for Timeout Exceeded
– 3 for Destination UnreachableThere are about sixteen formally defined Types for ICMP. The remaining fields in the ICMP header are Code, Checksum, and Rest of Header. The Code field is used to define or reference a sub-type (i.e., a more specific sub-meaning of the indicated control message). The Checksum field is used to verify that the ICMP communication was not corrupted in transit. The Rest of Header field may hold values when needed based on the Type, or is set to all zeros when unused. For example, a Type 5 Redirect will place an IP address in the Rest of Header field.
-
According to SP 800-86, which of the following is NOT an important factor when prioritizing potential data sources if evidence?
- volatility
- time involved
- likely value
- effort required
Explanation:
The amount of time involved in the collection is NOT one of the three considerations covered by SP 800-86. They are (quoted directly from SP 800-86):– Likely Value. Based on the analysts understanding of the situation and previous experience in similar situations, the analyst should be able to estimate the relative likely value of each potential data source.
– Volatility. Volatile data refers to data on a live system that is lost after a computer is powered down or due to the passage of time. Volatile data may also be lost as a result of other actions performed on the system. In many cases, acquiring volatile data should be given priority over non-volatile data. However, non-volatile may also be somewhat dynamic in nature (e.g., log files that are overwritten as new events occur).
– Amount of Effort Required. The amount of effort required to acquire different data sources may vary widely. The effort involves not only the time spent by analyst and others within the organization (including legal advisors) but also the cost of equipment and services (e.g., outside experts). For example, acquiring data from a network router would probably require much less effort than acquiring data from an ISP. -
Which statement is true with regard to evidence collection?
- Allow full access to the crime scene.
- Always shut the computer down first.
- Always call police.
- Always protect the integrity of the evidence.
Explanation:
You should always protect the confidentiality and the integrity of all evidence collected and ensure that a proper chain of custody is maintained. You should never shut the computer down until all volatile (memory) evidence is collected. You should tightly control access to the crime scene. You should always consider calling the police carefully as they will take control of the investigation.In summary, guidelines for evidence collection are:
– Upon seizing digital evidence, actions taken should not change that evidence.
– When it is necessary for a person to access original digital evidence, that person must be forensically competent.
– All activity relating to the seizure, access, storage, or transfer of digital evidence must be fully documented, preserved, and available for review.
– An individual is responsible for all actions taken with respect to digital evidence while the digital evidence is in their possession.
– Any agency that is responsible for seizing, accessing, storing, or transferring digital evidence is responsible for compliance with these principles. -
Which of the following is NOT reconnaissance?
- scanning without completing the three way handshake
- installation of a RAT
- searching for the robots.txt file
- communicating over social media
Explanation:
Installation comes after exploitation and involves the installation of additional tools and resources the hacker will use. These tools allow the attacker to maintain persistence while plotting the next step.The first and most important step is reconnaissance when information is gathered that helps penetrate the network. For example, consider an exploit takes advantage of an injection vulnerability in an exploitable Hypertext Preprocessor php file by sending an HTTP POST with specific variables. If the hacker sends an HTTP GET request to the page, the attack is still in reconnaissance.
Other examples of reconnaissance include obtaining IP blocks, researching social media accounts and obtaining DNS records.
The seven steps in the kill chain are:
– Reconnaissance is the attacker gathers information to aid in penetrating the network
– Weaponization is the attacker turns a legitimate utility or function into a weapon that can be used in the attack
– Delivery is the attacker transmits the crafted exploit to the target
– Exploitation is the exploit is executed
– Installation is the hacker installs additional tools and resources on the target device or in the target network
– Command and control is the attacker takes remote control of the target device from the Command and Control server
– Actions on objectives is the attacker takes action (deletes data, steals data, defaces website) -
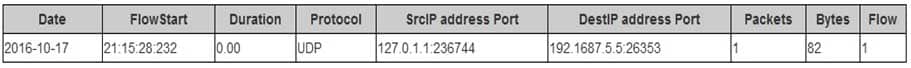
Examine the following NetFlow entry:

200-201 Part 05 Q12 017 Which statement is FALSE?
- The destination port is 236744.
- The bytes are 82.
- This is a single packet.
- The protocol is UDP
-
In which stage of incident handling is the extent of the incident determined?
- lessons learned
- containment
- scoping
- identification
Explanation:
Determining the extent of the incident involves determining how widespread it is and what devices are involved. There are six steps in the incident handling process:– Identification – determining whether there is an incident
– Scoping – determining the extent of the incident and identifying the attackers
– Containment – halting the spread of the incident and minimizing the impact
– Remediation – returning the environment to secure state
– Lesson-based hardening preventing future incidents
– reporting – documenting the incident and reporting it -
Which of the following is NOT one of the 5 tuples?
- source port number
- source Ip address
- destination IP address
- netflow record ID
Explanation:
The Netflow ID appears in the NetFlow header when using NetFlow to capture what is called a flow. This compromises all packets that are part of the same conversation as defined by the 5-tuple that all packets share. However, the NetFlow ID is not one of the five tuples.By using the 5-tuple uniquely identify each communication you can match up data from various sources that refer to the same communication.
The 5 tuple is a term to describe the 5 significant parts of each TCP connection. These 5 elements which make each conversation unique are:
– Source IP address
– Destination IP address
– Source port number
– Destination port number
– ProtocolThe source device created the connection and the destination accepts the connection following the TCP three way handshake. this handshake involves three TCP packets. The forst packet has the SYN flag set, indicating a desire to make a connection. The destination answers back with TCP packet with the SYN and ACK flags set, indicating a willingness to create the connection. Finally, the source finalizes the connection with a TCP packet with only the ACK flag set.
-
According to NIST, what goal are you supporting when you hash both evidence data and backup of the data and compare the hashes?
- integrity
- availability
- confidentiality
- authentication
Explanation:
Hashing is used to prove integrity or prove that the data has not changed since the original hash values were generated. Confidentiality is proved by applying access controls or encryption. The goal is to prevent unauthorized viewing of data.Availability is provided by redundancy. The goal is to maintain access to the data at all times.
Authentication is provided by assessing credentials. The goal is to only allow credentialed entities to log in. -
You are investigating suspicious communication between two devices in your environment. The source socket is 205.16.3.74:5696 and the destination socket is 192.168.5.3:53.
What service should you suspect is under attack?
- DHCP
- NTP
- DNS
- HTTP
Explanation:
You should suspect a DNS attack, mist likely an at attempt at an unauthored zone transfer. The destination port is port 53. Unless there is a non-default service running on that port, that port is used for DNS.You should not suspect DHCP. By default, DHCP uses ports 67 and 68, not 53.
You should not suspect HTTP. By default, HTTP uses port 80.
You should not suspect NTP. By default, NTP uses port 123. -
You have discovered a vulnerability to your web service that if leveraged would cause data to be changed in the attack.
Which CVSS metric will increase if this attack is realized?
- complexity
- confidentiality
- Availability
- integrity
Explanation:
The integrity metric increases when data is changed in the attack.When a service is rendered unable to do its job as in this case, its availability has been decreased resulting in an increase in the availability metric. The confidentiality metric increases when there is a data disclosure or breach.
Attack vector describe the nature of the vulnerability. The new version of CVSS (3.0) set the possible values for the confidentiality, integrity and availability metrics to none, low, and high. These are explained below for integrity:

200-201 Part 05 Q17 019 The complexity metric is a measure of the difficulty of succeeding in the attack. Low and high are values for attack complexity, which has replaced access complexity in version 3.0, and measures the difficulty of the attack. It has two possible values:
Low (L) – the attacker can perform the attack at will
High (H) – the attack depends on conditions beyond the control of the attacker -
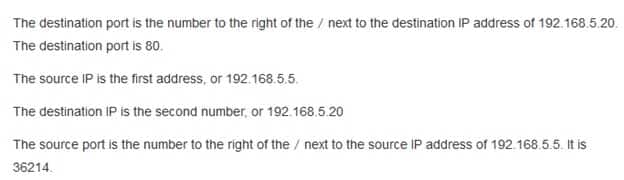
Examine the following ASA system message:
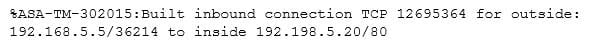
200-201 Part 05 Q18 020 Which statement is FALSE?
- The destination port is 302015.
- The destination IP is 192.168.5.20
- The source IP is 192.168.5.5
- The source port is 36214.
-
What statement is FALSE about probabilistic analysis?
- The answer is not definitive.
- All data is known beforehand.
- It is used in decision-making scenarios.
- It indicates how likely the event is.
-
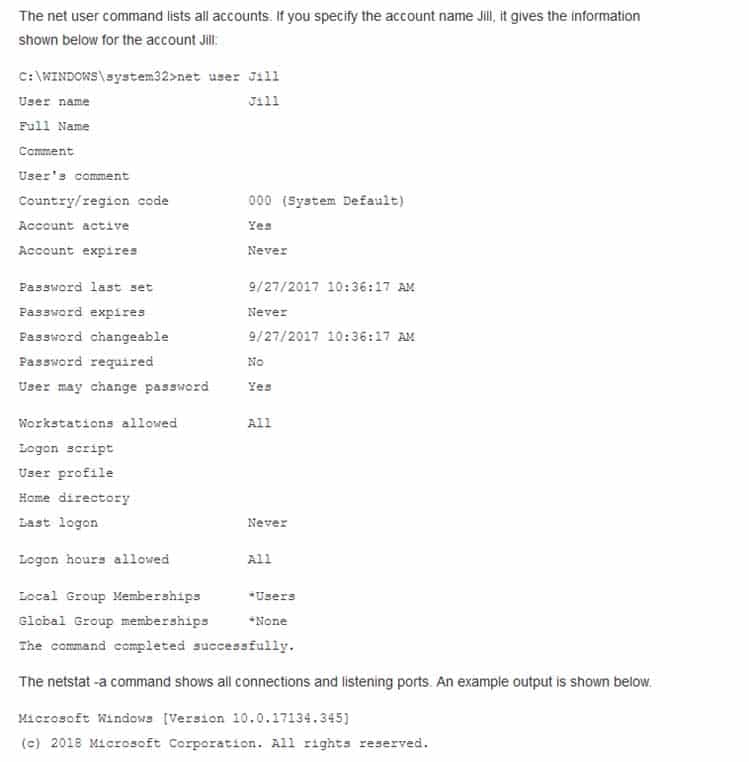
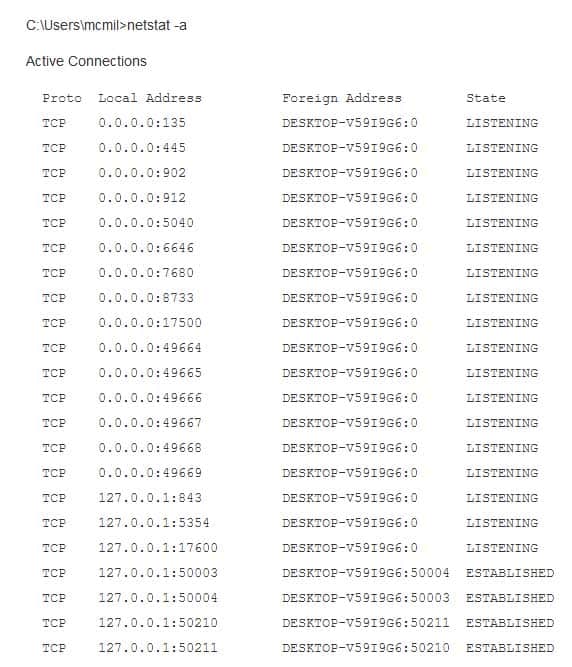
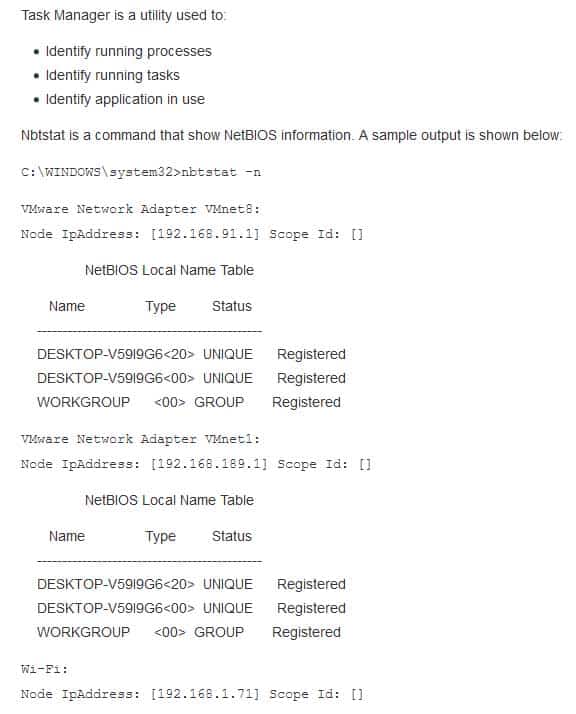
What tool or command can be used to determine details of a used account?
- nbtstat
- Task Manager
- netstat –a
- net user