200-201 : Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS) : Part 06
-
Which of the following would provide cybersecurity training and incident response to both a federal executive branch agency and foreign company?
- National CSIRT
- Coordination center
- Internal CSIRT
- PSIRT
-
Which of the following would help multiple CSIRTS facilitate incident handling?
- MSSP
- national CSIRT
- Coordination center
- Analysis center
-
Which of the following represents a step in the second normal form in the process of normalization?
- Create a separate table for each set of related data.
- Eliminate repeating groups in individual tables.
- Create separate tables for sets of values that apply to multiple records.
- Eliminate fields that do not depend on the key.
-
Which of the following is the second step in incident handling, according to NIST.SP 800-61 r2?
- detection and analysis
- post incident analysis
- preparation
- containment, eradication, and recovery
-
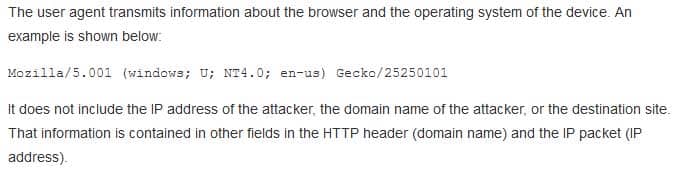
What information can be discovered from the user agent field in an HTTP packet?
- IP address of attacker
- domain name of attacker
- browser version
- destination site
-
In which stage of incident is the environment returned to a secure state?
- remediation
- Identification
- containment
- lesson-based hardening
Explanation:
Returning the environment to a secure state occurs during the remediation stage. There are six steps in the incident:
– Identification – determining whether there is an incident
– Scoping – determining the extent of the incident and identifying the attackers
– Containment – halting the spread of the incident and minimizing the impact
– Remediation – returning the environment to secure state
– Lesson-based hardening preventing future incidents
– Reporting – documenting the incident and reporting it -
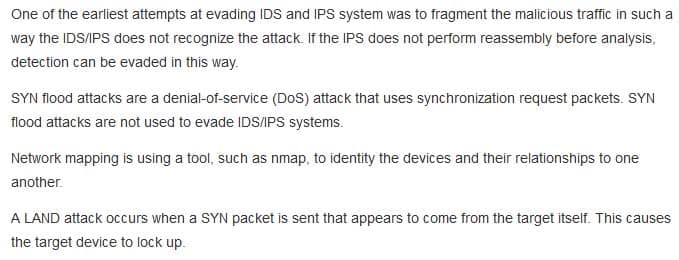
What is the term for any evasion attempt where the attacker splits malicious traffic to avoid detection or filtering?
- fragmentation
- SYN flood
- LAND attack
- network mapping
-
Actors and actions are part of which VERIS schema category?
- discovery and response
- incident tracking
- victim demographics
- incident description
-
When discontinuous free space is created by the adding and removing of data on a hard drive, what has occurred?
- steganography
- alternative data streams
- forking
- fragmentation
-
Which process is used to increase data accuracy and integrity and to support data visualization?
- data aggregation
- data warehousing
- data normalization
- data mapping
-
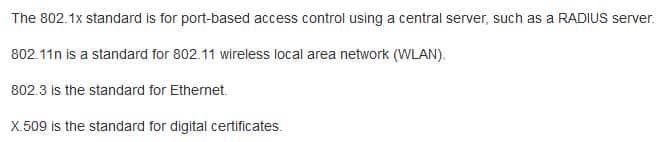
Which of the following is a standard for port-based access control?
- X.509
- 802.11n
- 802.3
- 802.1x
-
You discover several client machines are infected with malware that begins to make outbound calls (connection attempts) to a remote server after infection. You run a malware analysis tool.
What information could you derive from any domain names and host IP addresses in the malware analysis report?
- the next machine that will be infected
- destination of the callouts
- signature of the malware
- the first machine infected
-
Which of the following Wireshark filters excludes an IP address?
- gateway host <host>
- !ip.addr ==192.168.1.2
- eth.addr == 00:60:0e:53:13:d5
- ip.addr==192.168.1.0/24
-
What is the main purpose of data normalization?
- synchronize of time stamps
- duplicate data streams
- eliminate redundancy
- aggregate data
-
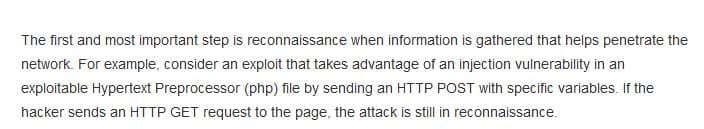
What is the first step in the Cyber Kill Chain framework?
- exploitation
- weaponization
- reconnaissance
- installation
-
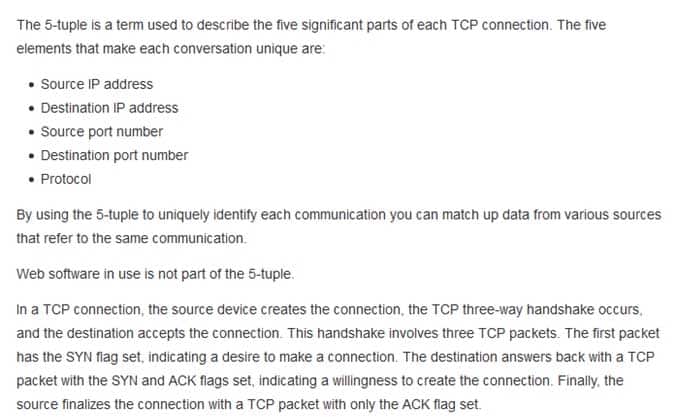
Which of the following is part of the 5 tuple?
- web software
- NetFlow record ID
- source IP address
- operating system
- device name
-
When an email with a malicious attachment is delivered to a mailbox, what step in the Cyber Kill Chain framework has occurred?
- Reconnaissance
- Exploitation
- Weaponization
- Delivery
-
Which of the following is NOT of interest during server profiling?
- Applications
- Logged-in Users/Service Accounts
- Running Processes
- Closed ports
-
According to NIST.SP800-61 r2, which of the following is NOT a question to ask during post mortem?
- Exactly what happened and at what time?
- How could information sharing with other organizations be improved?
- Whose fault was the attack?
- Were any steps or actions taken that might have inhibited the recovery?
Explanation:
Blame placing is not port o the post mortem.
Subscribe
0 Comments
Newest