200-301 : Cisco Certified Network Associate (CCNA) : Part 04
-
Which of the following commands would instruct OSPF to advertise ONLY the 192.168.10.0/24 network in Area 0?
-
Router(config)# router ospf 1 Router(config-router)# network 192.168.10.0 0.0.0.255 area 0 -
Router(config)# router ospf 1 Router(config-router)# network 192.168.11.0 0.0.0.255 area 0
-
Router(config)# router ospf 1 Router(config-router)# network 192.168.10.0 255.255.255.0 area 0
-
Router(config)# router ospf 1 Router(config-router)# network 192.168.10.0 0.0.255.255 area 0
Explanation:
The command Router(config-router)# network 192.168.10.0 0.0.0.255 area 0 would instruct OSPF to advertise the 192.168.10.0 network in Area 0. It is executed in OSPF process 1 configuration mode, as indicated by the prompt Router(config-router)#. This command correctly states the network as 192.168.10.0 and uses the proper wildcard mask of 0.0.0.255.The command Router(config-router)# network 192.168.11.0 0.0.0.255 area 0 is incorrect because it advertises the 192.168.11.0/24 network instead of the 192.168.10.0/24 network.The command Router(config-router)# network 192.168.10.0 255.255.255.0 area 0 is incorrect because it uses a regular mask instead of a wildcard mask.
The wildcard mask in OSPF network statements must be expressed inversely, and not as a regular subnet mask. If the network you are configuring for OSPF operation is 192.168.10.0/24, then the inverse version of a /24 mask (or 255.255.255.0) would be 0.0.0.255. The correct command, Router(config-router)# network 192.168.10.0 0.0.0.255 area 0,will configure OSPF to run over any local interfaces assigned an IP address beginning with 192.168.10, since the inverse mask dictates that the first three octets must be a match.
The command Router(config-router)# network 192.168.10.0 0.0.255.255 area 0 is incorrect because it uses an improper wildcard mask. This mask would instruct OSPF to advertise any network with a prefix longer than the 192.168.0.0/16 network.
When routing does not seem to be working correctly, one of the first things to check is whether OSPF is operating on the proper interfaces. OSPF is enabled by network statements. To verify the network statements that were entered, you should execute the show run command and examine the output. If the network statement is configured so that the interface on the router is not in that network, OSPF will not operate on that interface. For example, suppose that Router A has an interface of 192.168.5.1/30 and the show run command produces the following output:
<output omitted> router ospf 2 area 0 network 192.168.5.0 0.0.0.4
In this case, OSPF will not operate on the interface because the router interface is not in the network indicated by the network statement. The problem is not the network address but the wildcard mask. For a 30-bit mask, the wildcard should be 0.0.0.3, not 0.0.0.4. The wildcard mask can be determined by subtracting the regular mask value in the last octet (252) from 255, which is 3. The solution would to remove the incorrect statement and enter the correct statement as follows:
routerA(config)# router ospf 2 area 0 no network 192.168.5.0 0.0.0.4 area 0 network 192.168.5.0 0.0.0.3 area 0
Objective:
Routing Fundamentals
Sub-Objective:
Configure, verify, and troubleshoot single area and multi-area OSPFv2 for IPv4 (excluding authentication, filtering, manual summarization, redistribution, stub, virtual-link, and LSAs) -
-
You are the network administrator for your company. You have a Class B address range and are planning for a network that allows 150 hosts per subnet and at least 164 subnets.
Which subnet mask should you use to accomplish the task?
- 255.255.192.0
- 255.255.255.192
- 255.255.255.0
- 255.255.255.252
Explanation:
You should use 255.255.255.0 as the subnet mask to allow 150 hosts per subnet and at least 164 subnets. The formulas used to calculate the number of subnets and hosts are:Number of subnets = 2number-of-subnet-bits
Number of hosts per subnet = 2number-of-host-bits – 2Subnet mask in decimal: 255.255.255.0
Subnet mask in binary: 11111111.11111111.11111111.00000000
Number of subnet bits: 8 (binary 1s in the subnet octet of the subnet mask)
Number of host bits: 8 (binary 0s in the subnet mask)In this scenario, we find that for 255.255.255.0:
Subnets that can be used: 28 = 256
Hosts that can be used: 28 – 2 = 254The other options do not allow 150 hosts per subnet and at least 164 subnets.
If you use 255.255.192.0 as the subnet mask, then the total number of hosts that can be connected per subnet is 16382 (214 – 2 = 16382). However, there will be 4 subnets (22 = 4).
If you use 255.255.255.192 as the subnet mask, there will be 62 hosts (26 – 2 = 62).
If you use 255.255.255.252 as the subnet mask, there will be two hosts per subnet (22 – 2 = 2).
Note: This mask is frequently used for a subnet that connects two routers. In that case, there are two interfaces in the subnet, and thus it is most efficient use of the addressing space. This is also the most efficient way to address a point-to-point serial link.
A note about the formulas: You will always subtract 2 from the number of hosts (2number-of-host-bits – 2) because the all-zeroes bit address is reserved for the network address and the all-ones bit address is reserved for the broadcast address.
Before Cisco IOS Software Release 12.0, it was common practice to subtract 2 from the networks formula (2number-of-subnet-bits) to exclude the all-ones subnet and subnet zero. Today that range is usable, except with some legacy systems. On certain networks with legacy software, you may need to use the previous formula (2number-of-subnet-bits – 2) to calculate the number of valid subnets.
Objective:
Network Fundamentals
Sub-Objective:
Apply troubleshooting methodologies to resolve problems -
When the copy running-config startup-config command is issued on a router, where is the configuration saved?
- Random access memory (RAM)
- Flash
- Non-volatile random access memory (NVRAM)
- Read-only memory (ROM)
Explanation:
When the copy running-config startup-config command is issued on a router, the configuration is saved in the non-volatile random access memory (NVRAM) memory. The copy startup-config running-config command copies the version in RAM to NVRAM. Note: For the copy startup-config running-config command to function, there must be a configuration already residing in RAM. For example, a brand-new router with no configuration created would have no startup configuration in RAM. If you attempted to execute the copy startup-config running-config command in that case, you would receive the following error message%% non-volatile memory configuration is invalid or not present
In addition to storing the running configuration in the NVRAM, you can also store it on a Trivial File Transfer Protocol (TFTP) server. When a router boots in the absence of a startup configuration, the router will look for a valid configuration on a TFTP server. In the case that the TFTP server also does not have a valid router configuration or is unreachable, the router will enter the setup dialog and prompt the user to provide initial configuration inputs.
The router does not store the startup configuration in random access memory (RAM). RAM only holds the running configuration that is loaded from the NVRAM or TFTP server during the boot process.
The router does not store the configuration in flash or read-only memory (ROM). ROM contains the bootstrap code, while flash memory contains the IOS image.
Objective:
Infrastructure Management
Sub-Objective:
Perform device maintenance -
In the network exhibit, the routers are running OSPF and are set to the default configurations. (Click the Exhibit(s) button.)
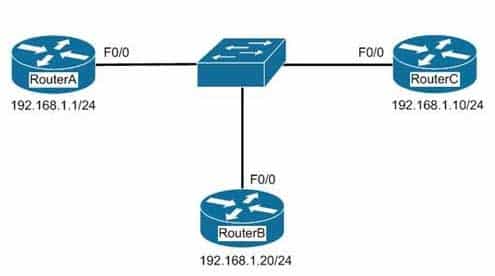
200-301 Part 04 Q04 032 What would be the effect of configuring a loopback interface on RouterA with an address of 192.168.1.50/24?
- Router B would become the DR
- Router A would become the DR
- Router C would become the DR
- Router A would become the BDR
Explanation:
Configuring a loopback interface on RouterA with an address of 192.168.1.50/24 would cause Router A to become the designated router (DR). The designated router (DR) is determined by the router with the highest interface priority number. If the priority numbers are tied, then the router with the highest router ID (RID) becomes the DR. The default priority number is 1, and can be configured as high as 255. Changing the priority to 0 would make the router ineligible to become the DR or the backup designated router (BDR). The ip ospf priority # command is used to manually configure a priority on a specific interface.Router IDs are determined first by the highest loopback IP address, followed by the highest IP address on an active physical interface. Thus, in the case of a priority tie, the router with the highest loopback IP address will have the highest RID, and will become the DR for the network segment.
The current Router ID for a router can be determined by executing the show ip interface brief command. In the sample output of the show ip interface brief command below, the RID will be 10.108.200.5.
Router# show ip interface brief Interface IP-Address OK? Method Status Protocol Ethernet0 10.108.00.5 YES NVRAM up up Ethernet1 unassigned YES unset administratively down down Loopback0 10.108.200.5 YES NVRAM up up Serial0 10.108.100.5 YES NVRAM up up Serial1 10.108.40.5 YES NVRAM up up Serial2 10.108.100.5 YES manual up up Serial3 unassigned YES unset administratively down down
Neither Router B nor C will be the DR because the IP addresses on their physical interfaces are lower than 192.168.1.50/24.
Router A will not be the backup designated router. Since it is the DR, it cannot also be the BDR.
Router C will not be the BDR because its IP address is lower than that of Router B. Router B will be the BDR.
Objective:
Routing Fundamentals
Sub-Objective:
Configure, verify, and troubleshoot single area and multi-area OSPFv2 for IPv4 (excluding authentication, filtering, manual summarization, redistribution, stub, virtual-link, and LSAs) -
Which of the following NAT terms refers to a registered address that represents an inside host to an outside network?
- inside global
- outside global
- inside local
- outside local
Explanation:
An inside global address is the registered or public address assigned by the NAT server to an inside host. To the outside world it is only address seen for the host. The real (private) address, called the inside local, remains hidden. The outside global address is the public address of a host that is outside the network connecting to the network. It the NAT server is also translating incoming addresses as well as outgoing addresses the address it assigns to the external host is called the outside local address.The inside local address is the private IP address assigned to a host inside the network. The outside local is the address of a host outside the network as seen by hosts inside the network.
For example, in the diagram below, PC1 is sending a packet to the Web server. R1 is operating in NAT overload mode, which means that it maps all internal private IP addresses to a single public IP address.
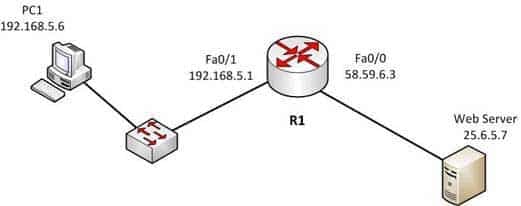
200-301 Part 04 Q05 033 Below is a listing of the names assigned to certain addresses in the diagram:
Inside local 192.168.5.6
Inside global 58.59.6.3
Outside local 192.168.5.1
Outside global 25.67.5.7Objective:
Infrastructure Services
Sub-Objective:
Configure, verify, and troubleshoot inside source NAT -
Which commands would you use to determine the IP address and hostname of a directly connected switch from which you received VLAN information? (Choose two. Each correct answer is part of the solution.)
- show vtp status
- show cdp neighbors detail
- show cdp neighbor status
- show vtp counters
- show cdp neighbor
Explanation:
The VLAN Trunking Protocol (VTP) is used to synchronize VLANs between switches, and the question implies that VTP is being used in this environment. The show vtp status command will display the IP address of the switch that last updated your VLAN database. The output of this command is as follows:
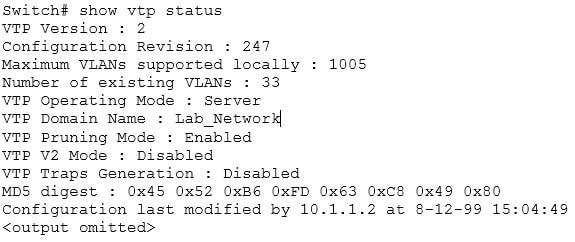
200-301 Part 04 Q06 034 The “Configuration last modified by 10.1.1.2” output reveals the IP address of the switch from which you received VLAN information. Once you know the IP address of the switch, you can use the show cdp neighbors detail command to determine the hostname associated with this IP address. The output of this command is as follows:
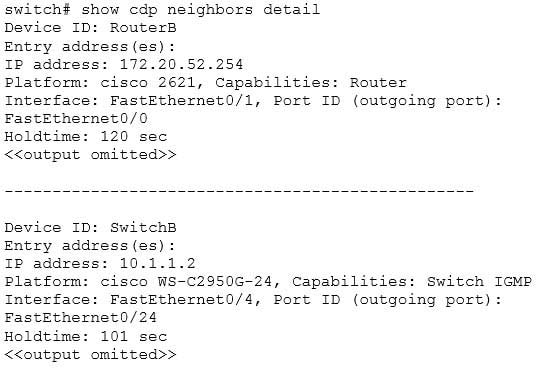
200-301 Part 04 Q06 035 The show cdp neighbors detail command provides detailed information about directly connected Cisco devices. The detail option is required to provide the IP address of the neighboring devices, and indicates here that IP address 10.1.1.2 is assigned to Device ID: SwitchB, which is the hostname for this device. SwitchB is the switch from which you received VLANs.
Although not offered as an option, the show cdp entry* command will also display all directly connected devices and will indicate the hostname and the IP address and platform, but will not indicate from which device VTP information was received. Its output is shown below:
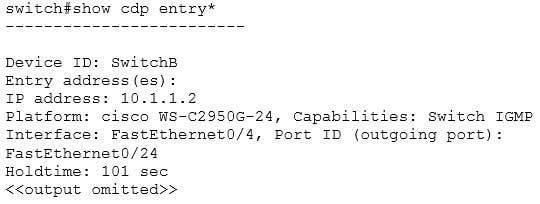
200-301 Part 04 Q06 036 This command displays the same information as the show cdp neighbor detail command. It includes:
– The IP address of the neighbor (in this case 10.1.1.2)
– The port on which the CDP information was received (in this case FastEthernet0/4)
– The platform (in this case a Cisco WS-C2950G-24 Switch)The show vtp counters command is incorrect because it does not display information about neighboring devices, nor information regarding from which switch VLANs were received.
The show cdp neighbor command is incorrect because the detail option is required to display the IP addresses of neighboring devices.
The show cdp neighbor status command is incorrect because this is not a valid Cisco IOS command.
Objective:
LAN Switching Fundamentals
Sub-Objective:
Configure, verify, and troubleshoot VLANs (normal/extended range) spanning multiple switches -
Which command produced the following output?
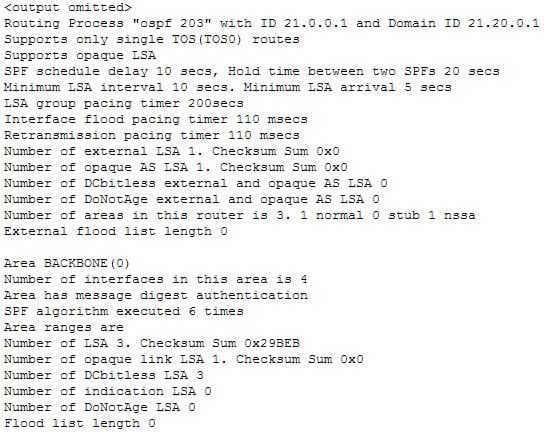
200-301 Part 04 Q07 037 - show ip ospf database
- show ip ospf statistics
- show ip ospf
- show ip ospf traffic
Explanation:
The output was produced by the show ip ospf command. The show ip ospf command is used to view information about the OSPF routing processes. The syntax of the command is as follows:Router# show ip ospf [process-id]
The process-id parameter of the command specifies the process ID.
The show ip ospf database command is incorrect because this command is used to view the OSPF database for a specific router. The following is sample output from the show ip ospf database command when no arguments or keywords are used:
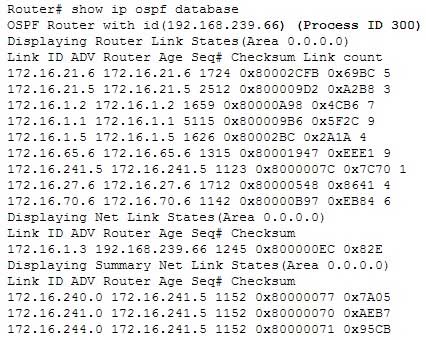
200-301 Part 04 Q07 038 The show ip ospf statistics command is incorrect because this command is used to view the OSPF calculation statistics. The following is sample output from the show ip ospf statistics command that shows a single line of information for each SPF calculation:

200-301 Part 04 Q07 039 The show ip ospf traffic command is incorrect because this is not a valid command.
Objective:
Routing Fundamentals
Sub-Objective:
Compare and contrast interior and exterior routing protocols -
Which Cisco command keeps unauthorized users from viewing passwords in the router configuration file?
- enable secret
- enable password
- enable encryption
- service encryption
- service password-encryption
Explanation:
The service password-encryption global configuration mode command keeps unauthorized users from viewing passwords in the router configuration file. The service password-encryption command encrypts all current and future passwords configured on the router, including the line password, virtual terminal password, console password, user name password, routing protocol passwords such as BGP neighbor passwords, the privileged command password, and authentication key passwords. Moreover, it encrypts any future passwords created on the router. The encryption process occurs whenever the current configuration is built or a password is configured. The service password-encryption command will cause the router configuration file to display encrypted characters instead of passwords when the running-configuration or startup-configuration files are viewed.The enable password command creates a password that will be required to enter privileged EXEC mode, but the password will not be encrypted.
The enable secret command provides encryption to the enable mode passwords but does not apply globally to all passwords configured on the router. It also does not encrypt any future passwords created on the router.
The enable encryption and service encryption commands are invalid.
Objective:
Infrastructure Security
Sub-Objective:
Configure, verify, and troubleshoot basic device hardening -
Which of the following statements are TRUE regarding carrier sense multiple access collision detection (CSMA/CD)? (Choose three.)
- Networks are segmented into multiple collision domains using switches for CSMA/CD networks.
- Networks are segmented into multiple broadcast domains using switches for CSMA/CD networks.
- CSMA/CD networks normally operate on half-duplex mode.
- CSMA/CD networks normally operate on full-duplex mode.
- Gigabit Ethernet uses CSMA/CD as the media access control method.
- Gigabit Ethernet uses carrier sense multiple access with collision avoidance (CSMA/CA) as the media access control method.
Explanation:
The following statements are true:
– Networks are segmented into multiple collision domains using switches for CSMA/CD networks
– CSMA/CD networks normally operate on half-duplex mode
– Gigabit Ethernet uses CSMA/CD as its media access control methodCSMA/CD is a Local Area Network (LAN) access method used in Ethernet. In CSMA/CD, if a device or a node wants to send a packet in the network, it first determines if the network is free. If the network is not free, then the node will wait before sending the packet into a network. If the network is free, then the node sends the packet; if another device sends a packet simultaneously, their signals or packets collide. When the collision is detected, both packets wait for a random amount of time before retrying.The option stating that networks are segmented into multiple broadcast domains using switches for CSMA/CD networks is incorrect because networks are segmented into multiple broadcast domains using routers for CSMA/CD networks.
The option stating that CSMA/CD networks normally operate on full-duplex mode is incorrect; these networks normally operate on half-duplex mode.
The option stating that gigabit Ethernet uses CSMA/CA as the media access control method is incorrect because gigabit Ethernet uses CSMA/CD as the media access control method.
Objective:
LAN Switching Fundamentals
Sub-Objective:
Describe and verify switching concepts -
You are the Cisco administrator for NationalAct Incorporated. One of your assistants is preparing to introduce a new switch to the network. Before doing so, you execute the show vtp status command on OldSwitch and NewSwitch, respectively, and receive the following output:
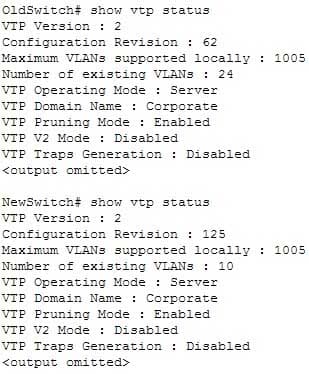
200-301 Part 04 Q10 040 If NewSwitch is introduced to the network, which of the following will be true?
- NewSwitch will delete its current VTP data.
- There will be 10 VLANs in the network.
- OldSwitch will retain its current VTP data.
- There will be 24 VLANs in the network.
Explanation:
If NewSwitch is introduced to the network, there will be 10 VLANs. The VLAN database of the new switch will overwrite the VLAN databases of the production switches because it is operating in server mode and has a higher VLAN configuration revision number.VLAN Trunking Protocol (VTP) is used to synchronize VLANs between different switches. The VTP configuration revision number is used to determine which VTP switch has the most current version of the VLAN database, and is incremented whenever a VLAN change is made on a VTP server switch. The Configuration Revision: 125 output indicates that NewSwitch has a configuration revision number of 125, which will be compared to other switches in the same VTP domain, including OldSwitch, which has a revision number of 62. If the production switches have lower configuration revision numbers than the new switch, their VLAN databases will be replaced with the VLAN database of the new switch. Any switch ports that had been assigned to be removed from VLANs in the configuration database of the new switch will be disabled, possibly resulting in catastrophic network failure. All VTP switches in the same VTP domain should have a domain password defined, which will protect against a rogue switch being added to the network and causing VLAN database corruption.NewSwitch will not delete its current VTP data. If the production switches have lower configuration revision numbers than the new switch, their VLAN databases will be replaced with the VLAN database of the new switch.
The number of VLANs will not remain 24. The 24 VLANs indicated by the Number of existing VLANs: 24 output will be overwritten with the 10 VLANs in the NewSwitch VLAN database.
OldSwitch will not retain its current VTP data. It will be replaced with the VLAN database of the new switch.
Objective:
LAN Switching Fundamentals
Sub-Objective:
Configure, verify, and troubleshoot VLANs (normal/extended range) spanning multiple switches -
Which of the following is a frame tagging method for identifying Virtual LAN (VLAN) memberships over trunk links?
- STP
- RIP
- CDP
- 802.1q
Explanation:
802.1q is a frame tagging method for identifying Virtual LAN (VLAN) memberships over trunk links. Frame tagging ensures identification of individual VLAN frames over a trunk link that carries frames for multiple VLANs. This frame tagging method is a standardized protocol developed by The Institute of Electrical and Electronics Engineers (IEEE). Cisco has also developed a proprietary frame tagging method, known as Inter-Switch Link (ISL).When configuring a trunk link between a router and a switch, you must configure the physical interface on the router with one subinterface for each VLAN, and you must configure the physical ports on the router and the switch with the same encapsulation type, whether 802.1q or ISL.Spanning Tree Protocol (STP) is not a frame tagging method, but a protocol used to remove switching loops in redundantly configured switched environments and create a single active Layer 2 path between any two network segments. Whenever a network segment can be handled by more than one switch, STP will elect one switch to take responsibility, and the other switches will be placed into a blocking state for the ports connected to that segment. In this way, only one switch receives and forwards data for this segment, removing the potential for generating multiple copies of the same frame. The benefits of STP include:
– Prevention of broadcast storms
– Prevention of multiple frame copies
– Media Access Control (MAC) address database stabilityRouting Information Protocol (RIP) is not a frame tagging method, but a distance vector routing protocol. It populates routing tables dynamically about the topology changes.
Cisco Discovery Protocol is not a frame tagging method, but a Cisco proprietary protocol used to collect hardware and protocol information for directly connected Cisco devices. CDP has nothing to do with VLANs.
Objective:
LAN Switching Fundamentals
Sub-Objective:
Configure, verify, and troubleshoot VLANs (normal/extended range) spanning multiple switches -
A packet is received with a destination IP address of 10.2.16.10.
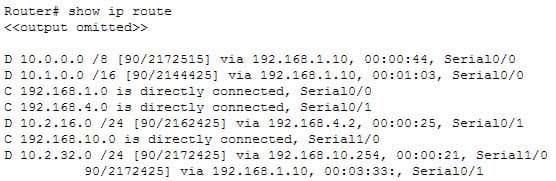
200-301 Part 04 Q12 041 What would the next hop IP address be for this packet?
- 192.168.1.10
- 192.168.4.2
- 192.168.10.254
- None; the packet will be dropped.
Explanation:
The packet will be routed to the next hop IP address of 192.168.4.2, since this routing table entry is the most specific match for the remote network. Packets are routed according to the most specific, or “longest,” match in the routing table. The packet in the scenario has a destination IP address of 10.2.16.10, which matches two entries in the routing table.
– 10.0.0.0 /8: this matches based on the /8 mask, where only the first byte has to match. The destination IP address of 10.2.16.10 has a first byte matching 10. If this were the only matching route table entry, it would be selected.
– 10.2.16.0 /24: The first 24 bits of this entry match the first 24 bits of the destination IP address of 10.2.16.10.Therefore, the 10.2.16.0 /24 entry is selected for routing this packet because it most specifically matches the destination IP address, or has the longest number of matching bits.
The next hops of 192.168.1.10 and 192.168.10.254 will not be used, as these routes are not the most specific matches for the destination IP address of the packet.
It is interesting to note that packets that are destined for the 10.2.32.0 network will be load balanced across both serial 0/0 and serial 0/1 because the cost (2172425) is the same for both paths.
The packet will not be dropped because there is at least one routing table entry that matches the destination IP address of the packet.
To ensure that no packets are dropped, even if there is no matching route in the routing table, a default route could be configured as follows (next hop picked at random for illustration):
Router(config)# ip route 0.0.0.0 0.0.0.0 192.168.1.1
This configuration would instruct the router to send any packets that do match the existing routes to 192.168.1.1. For example, a packet destined for 201.50.6.8/24 would not match any routes in the table, and would thus be forwarded to 192.168.1.1.
If you understand how routing tables and routing advertisements work, it is relatively simple to describe the contents of a router’s routing table without seeing the table directly. To do so, you would view the router’s configuration and the configuration of its neighbors using show run, along with a diagram of its network connections. For example, examine the diagram of the two routers shown below along with their respective configurations:

200-301 Part 04 Q12 042 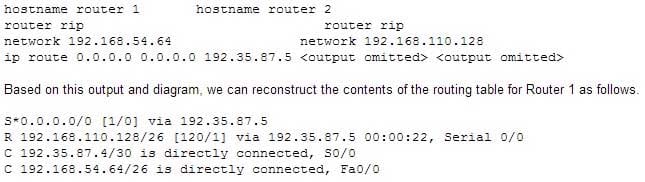
200-301 Part 04 Q12 043 It will contain S*0.0.0.0/0 [1/0] via 192.35.87.5 because of the static default route indicated in line 4 of its configuration output.
It will contain R 192.168.110.128/26 [120/1] via 192.35.87.5 00:00:22, Serial 0/0 because Router 2 has a network 192.168.110.128 statement indicating that it will advertise this network to its neighbors.
It will contain the two routes C 192.35.87.4/30 is directly connected, S0/0 and C 192.168.54.64/26 is directly connected, Fa0/0 because all directly connected routes are automatically placed in the table.
Objective:
Routing Fundamentals
Sub-Objective:
Interpret the components of routing table -
Which cable can suffer attenuation if it is bent beyond the minimum bend radius?
- UTP
- STP
- Co-axial
- Fiber optic
Explanation:
Fiber-optic cables can suffer attenuation if they are bent beyond the minimum bend radius. Fiber-optic cables work on the principle of total internal reflection. The fiber optic cable uses a laser and glass tubes with refractive internal coating to achieve total internal reflection. If a light ray travelling in the tube is bent at a certain angle, the light ray will be reflected inside the medium instead of passing through the medium. If the fiber optic cables are bent beyond the minimum bend radius, the signal will be lost and the cable will suffer attenuation. Fiber cables are expensive and are typically used for outdoor campus backbone. However, as the fiber cables use light to carry signals, they are not affected by the electro-magnetic interference (EMI) generated by electric cables. Another advantage of fiber optic cabling is its applicability to situations where electrical issues may exist in the environment. Even in situations where the length of the cable run is well within the attenuation limits of STP (for example 55 meters), voltage differences between buildings can cause issues. That is a problem that can be solved by using fiber on the run, which is not impacted by electrical issue.All other cables typically use copper to carry low voltage signals and are not affected by normal bending. However, even copper cables may suffer some signal loss if there are bends in the cable.
Objective:
Network Fundamentals
Sub-Objective:
Select the appropriate cabling type based on implementation requirements -
Which type of network connection requires a straight-through cable?
- host to host
- switch to router
- switch to switch
- host to router’s Ethernet port
Explanation:
A switch to router connection requires a straight-through cable. Straight-through cables are also used for host to switch communication. A crossover cable is used to connect “like” devices, and a straight through cable is used when connecting “unlike” devices. The one exception to this rule is when connecting a computer NIC to an Ethernet port on a router, a crossover cable is used. In summary, the following list describes when to use crossover and straight through cables:– Host to host Crossover
– Host NIC to router Crossover
– Host to switch Straight through
– Switch to Switch Crossover
– Switch to router Straight throughThe difference between straight-through and crossover lies in the location of the wire termination on the two ends of an RJ-45 cable. If the unshielded twisted-pair (UTP) cable wire connects Pin 1 of one side to Pin 1 of other side and Pin 2 to 2 through all eight Pins of the RJ-45 connector, the cable is said to be straight-through.
On the other hand, if the Pin 1 of one side RJ-45 cable connected to Pin 3 of other end and Pin 2 connects to Pin 6 of other side, it is called as crossover cable. The cable type to be used depends upon circuit connection on the hardware. Some devices have ports that are capable of identifying the cable type and automatically adjusting the port setting to be a standard or uplink port.
Host-to-host, switch-to-switch, and host-to-Ethernet-port would all use a crossover cable to connect in the network. The following figure shows the pin layout for a crossover cable:

200-301 Part 04 Q14 044 Objective:
Network Fundamentals
Sub-Objective:
Select the appropriate cabling type based on implementation requirements -
What command would you run to determine which switch is the root bridge for a particular VLAN?
- show spantree vlan
- show spanning tree
- show vlan spantree
- show spanning-tree vlan
- show spanning-tree interface
Explanation:
The show spanning-tree vlan command provides Spanning Tree Protocol (STP) information on the root switch, including the bridge ID, root path, and root cost, as well as information on the local switch. The output of the command is as follows:
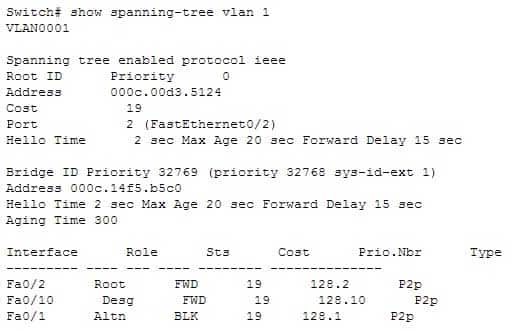
200-301 Part 04 Q15 045 This output indicates the following:
The root switch has a bridge ID (Priority + MAC Address) of 0-000c.00d3.5124, while the local switch has a bridge ID of 32769-000c.14f5.b5c0. This indicates that the local switch is not the root switch for VLAN 1. Additional evidence that the local switch is not the root switch is the fact that the Fa0/1 port is blocking with a role listed as Altn. Only non- root bridges have blocking ports.
For this switch, Fa0/1 represents the redundant link that needs to be blocked to prevent a switching loop.
Interface Fa0/2 is the root port (the interface with the shortest path to the root switch).
All three links have a cost of 19, which is the default cost of a single FastEthernet link.
802.1d is enabled in this switch, as indicated by the output Spanning tree enabled protocol ieee in line 2.The show spanning-tree interface command will indicate the port role and state that a particular interface plays in each VLAN, but does not indicate the root bridge for a particular VLAN. Below is sample output from the show spanning-tree interface fastethernet0/1 command. In this example, RSTP is in use rather than 802.1d.
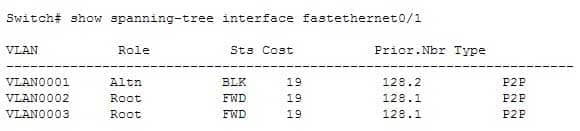
200-301 Part 04 Q15 046 In the above output, the Fa0/1 interface is not the root bridge for any of the three VLANs. It is the root port for VLANs 2 and 3. Root bridges have only designated ports. It is the alternate port for VLAN1, which means that Fa0/1 has a higher cost path to the root bridge than another interface in the topology, and will be in a blocking state as long as that other path is available.
The other options are incorrect because they are not valid Cisco IOS commands. The correct syntax would be show spanning-tree, not show spanning tree or show spantree.
Objective:
LAN Switching Fundamentals
Sub-Objective:
Configure, verify, and troubleshoot STP protocols -
Which of the following statements describes split horizon?
- The router learns from its neighbor that a route has gone down, and the router sends an update back to the neighbor with an infinite metric to that route.
- For a period of time, the router will ignore any route advertisements with a lower metric to a downed route.
- A router will not send route information back out the same interface over which it was learned.
- The moment a router determines a route has gone down, it will immediately send a route update with an infinite metric to that route.
- The packets are flooded when a topology change occurs, causing network routers to update their topological databases and recalculate routes.
Explanation:
Split horizon is used to prevent routing loops in distance vector routing environments. It prevents a router from advertising a network back in the direction of the router from which it was learned. In this sense, route advertisements flow “downstream” (away from the route), but never “upstream” (back towards the advertised route).Poison reverse describes when a router learns that a network has gone down, and the router sends an update back to the neighbor with an infinite metric.Holddown describes when a router ignores any route advertisements that have a lower metric to a downed route.
Triggered updates describe when a router immediately sends a route update with an infinite metric, as opposed to waiting for its next regularly scheduled routing update.
Link State Advertisements (LSA) are packets that are flooded when a topology change occurs, causing network routers to update their topological databases and recalculate routes.
Objective:
Routing Fundamentals
Sub-Objective:
Compare and contrast distance vector and link-state routing protocols -
Which of the following loop avoidance mechanisms drives the requirement to create subinterfaces for each point-to-point connection in a partially meshed frame relay network?
- split horizon
- poison reverse
- maximum hop count
- feasible successor
Explanation:
Split horizon is the loop avoidance mechanism that drives the requirement to create sub interfaces for each point-to-point connection in a partially meshed frame relay network. Frame relay is a non-broadcast multi-access (NBMA) network and obeys the rules of split horizon. This mechanism prohibits a routing protocol from sending updates out the same physical interface on which it was received. When the same physical interface is used to host multiple frame relay connections, this will prevent an update arriving from remote network A on the physical interface from being sent out the same interface to remote network B.By creating a subinterface for each frame relay connection and assigning IP addresses to the subinterfaces rather than the physical interface, and by placing the subinterfaces into different subnets, split horizon will not see the “virtual” interfaces as the same interface and will allow these routing updates to be sent back out the same physical interface on which they arrived. It is important to map each subnet (or subinterface) to a remote Data Link Connection Identifier (DLCI) so that traffic to a remote network can be sent out the correct subinterface.To summarize this discussion:
– Subinterfaces solve the NBMA split horizon issues.
– There should be one IP subnet mapped to each DLCIPoison reverse is not the mechanism driving the requirement to create subinterfaces for each point-to-point connection in a partially meshed frame relay network. This mechanism requires a router to send an unreachable metric to the interface on which a network was discovered when it is learned from another interface that the network is no longer available.
Maximum hop count is not the mechanism driving the requirement to create sub interfaces for each point-to-point connection in a partially meshed frame relay network. Each routing protocol has a maximum hop count, which is the maximum number of hops allowed to a remote network before the network is considered “unreachable”.
Feasible successor is not the mechanism driving the requirement to create sub interfaces for each point-to-point connection in a partially meshed frame relay network. This is a concept unique to EIGRP that represents a secondary route to a network that is considered the “best” route of possible backup routes.
Objective:
LAN Switching Fundamentals
Sub-Objective:
Configure and verify Layer 2 protocols -
How is load balancing achieved when implementing HSRP?
- By configuring multiple gateways on the routers
- By using multiple HSRP groups
- By configuring the same priority on all HSRP group members
- By configuring multiple virtual router addresses
Explanation:
When implementing Hot Standby Router Protocol (HSRP), load balancing is achieved by using multiple HSRP groups. Routers configured for HSRP can belong to multiple groups and multiple VLANs. By configuring one group to be active for Router A and standby for Router B, and the second group to be active for Router B and standby for Router A, both routers A and B can be used to pass traffic, as opposed to one sitting idle.Load balancing cannot be achieved by configuring multiple gateways on the routers. The routers have one IP address. Each group will have a virtual IP address. In the configuration below, line 4 configures the virtual IP address, and is therefore the address that clients will use as their gateway:interface fastethernet 0/1 no switchport ip address 192.168.5.5 255.2555.255.0 standby 1 ip 192.168.5.10
Load balancing cannot be achieved by configuring the same priority on all HSRP group members. If that were done, one of the routers would become active and the others would remain inactive standbys. The active router will be the one with the highest IP address.
Load balancing cannot be achieved by configuring multiple virtual router addresses. Each HSRP group can only have one virtual address.
Objective:
Infrastructure Services
Sub-Objective:
Configure, verify, and troubleshoot basic HSRP -
Which Cisco IOS command would produce the preceding menu-based prompt for additional information?
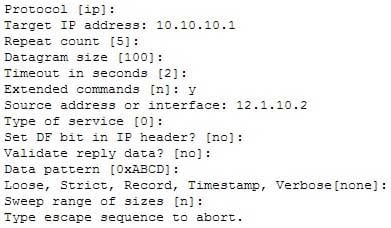
200-301 Part 04 Q19 047 - tracert 10.10.10.1
- traceroute 12.1.10.2
- ping 10.10.10.1
- ping
Explanation:
This menu-based prompt for additional information shown would be generated by the Cisco IOS ping command when issued without a target IP address. This is also known as issuing an extended ping. This command can be issued on the router to test connectivity between two remote routers. To execute an extended ping, enter the ping command from the privileged EXEC command line without specifying the target IP address. It takes the command into configuration mode, where various parameters, including the destination and target IP addresses, can be defined. Note: You can only perform an extended ping at the privileged EXEC command line, while the normal ping works in both user EXEC mode and privileged EXEC mode.The tracert command is incorrect because the tracert command is used by Microsoft Windows operating systems, not Cisco devices. This command cannot be run via the Cisco IOS command line interface. However, Microsoft’s tracert utility is similar to Cisco’s traceroute utility, which is to test the connectivity or “reachability” of a network device or host. The tracert command uses Internet Control Message Protocol (ICMP) to list all of the ‘hops” or routers traversed to a destination.
The traceroute command is incorrect because this command uses Internet Control Message Protocol (ICMP) to list all of the ‘hops” or routers traversed to a destination. It is also used to find routing loops or errors within a network.
The ping 10.10.10.1 command is incorrect because you when you issue this command you will either receive a reply from the destination or a destination unreachable message. It will not prompt for additional information as shown
Objective:
Routing Fundamentals
Sub-Objective:
Configure, verify, and troubleshoot IPv4 and IPv6 static routing -
On a Cisco 2950 switch, which status LED and color combination indicates a Power On Self-Test (POST) failure?
- system LED: no color
- system LED: solid red
- system LED: solid amber
- stat LED: no color
- stat LED: green
Explanation:
A POST failure is indicated by a solid amber color on the system LED. The switch automatically runs POST which is a series of self-tests to verify proper functioning, after the power is connected. The system LED is off (no color) at the time that POST begins. The LED will turn green if POST is successful, or it will turn amber if POST fails. The system LED will not be colorless. The system LED will show no color at the beginning of the POST cycle, not after a POST failure.The system LED will not be solid red after a POST failure. Cisco LEDs do not have a red color mode.
The Stat LED indicates the status of each port. If it is amber there is a signal but the port is not forwarding, either because of an address violation or it has been disabled. If it is colorless, there is no signal. In this case:
– Ensure the switch has power
– Ensure the proper cable type is in use (for a switch to switch connection use a crossover cable: for a switch to host and or switch to router connection use a straight through)
– Ensure a good connection by reseating all cablesIf it is green, the port has a signal and is functional. Green means:
– Layer 1 media is functioning between the switch and the device on the other end of the cable
– Layer 2 communication has been established between the switch and the device on the other end of the cable
200-301 Part 04 Q20 048 Objective:
LAN Switching Fundamentals
Sub-Objective:
Configure, verify, and troubleshoot interswitch connectivity