200-301 : Cisco Certified Network Associate (CCNA) : Part 06
-
What is the purpose of frame tagging in Virtual LAN (VLAN) configurations?
- inter-VLAN routing
- encryption of network packets
- frame identification over trunk links
- frame identification over access links
Explanation:
Frame tagging is used when VLAN traffic travels over a trunk link. Trunk links carry frames for multiple VLANs. Therefore, frame tags are used for identification of frames from different VLANs. Inter Switch Link (ISL) and Institute of Electrical and Electronics Engineers (IEEE) 802.1q are the two frame tagging methods supported on Cisco devices. The purpose of frame tagging is not inter-VLAN routing. A Layer 3 device, such as a router or multilayer switch, is used for inter-VLAN routing. To configure inter-VLAN routing a logical or subinterface for each VLAN must be created on the single physical interface used to connect to the switch. An IP address is NOT applied to the physical interface; instead, each subinterface is configured with an IP address that will become the default gateway of all devices residing in that VLAN. Consequently, each subinterface and its VLAN devices must reside a different subnet as well. If a subinterface on the router is NOT configured with an IP address that resides in the same network as the hosts that reside in the VLAN that the subinterface serves, the hosts in that VLAN will be isolated from the other VLANs. The hosts in the VLAN served by the subinterface should also use this address as their default gateway, or the hosts in the VLAN will likewise be isolated form the other VLANsTo verify the IP address of the subinterface, execute the show interfaces subinterface ID command. As shown below, the IP address will appear in line 3 of the output. Compare this IP address will the IP address set as the default gateway of each host in the VLAN served by the subinterface. They should be the same, and the IP address of the hosts should be in the same subnet as this address as well.
router# show interfaces fastEthernet 0/0.1 FastEthernet0/0.1 is up, line protocol is up Hardware is AmdFE, address is 0003.e36f.41e0 (bia 0003.e36f.41e0) Internet address is 10.10.10.1/24 MTU 1500 bytes, BW 100000 Kbit, DLY 100 usec, reliability 255/255, txload 1/255, rxload 1/255 Encapsulation ISL Virtual LAN, Color 1. ARP type: ARPA, ARP Timeout 04:00:00
Frame tagging does not provide encryption of network packets. Packets are transmitted unencrypted unless the network device or the application uses an additional encryption mechanism. A Virtual Private Network (VPN) is a popular solution for providing encrypted network communication.
An access link is a connection between a switch and an end-user computer with a normal Ethernet Network Interface Card (NIC). On these links, Ethernet frames are transmitted without frame tagging.
Objective:
LAN Switching Fundamentals
Sub-Objective:
Configure, verify, and troubleshoot VLANs (normal/extended range) spanning multiple switches -
The output of the show ip route command is given:
Router# show ip route Gateway of last resort is 10.119.254.240 to network 10.140.0.0 O 172.16.0.0 [110/5] via 10.19.24.6, 0:01:00, Ethernet2 B 172.17.12.0 [200/128] via 10.19.24.24, 0:02:22, Ethernet2 O 172.71.13.0 [110/5] via 10.19.24.6, 0:00:59, Ethernet2 O 10.13.0.0 [110/5] via 10.19.24.6, 0:00:59, Ethernet2
What does the value 110 in the output represent?
- The administrative distance of the information source
- The metric to the route
- The type of route
- The port number of the remote router
Explanation:
The value 110 in the output represents the administrative distance (AD) of the information source. Administrative distance is used by Cisco routers to select the most trustworthy source of routing information for a particular route. Every routing protocol has a default administrative distance, and if more than one routing protocol is providing route information about a route, the protocol with the lowest AD will be selected to populate the routing table. The following table shows the AD values for different routing protocols:
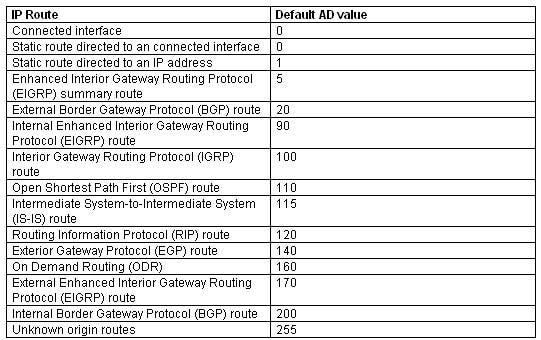
200-301 Part 06 Q02 062 The following is the sample output for the show ip route command:
Router# show ip route Gateway of last resort is 10.119.254.240 to network 10.140.0.0 O 172.16.0.0 [110/5] via 10.19.24.6, 0:01:00, Ethernet2 B 172.17.12.0 [200/128] via 10.19.24.24, 0:02:22, Ethernet2 O 172.71.13.0 [110/5] via 10.19.24.6, 0:00:59, Ethernet2 O 10.13.0.0 [110/5] via 10.19.24.6, 0:00:59, Ethernet2
The following are the fields in the output:
– O: Indicates that the route was discovered using Open Shortest Path First (OSPF).
– B: Indicates that the route was discovered using Border Gateway Protocol (BGP).
– 172.16.0.0: Indicates the address of the remote network.
– 110: Indicates the administrative distance of the route.
– 128: Indicates the metric for the route.
– Via 10.19.24.6: Specifies the address of the next router in the remote network.
– 0:02:22: Indicates the last time the route was updated.
– The metric for the route is also called the cost. In the case of the OSPF routes above, the cost is 5.The administrative distance for any particular protocol can be changed if you would like to use a routing protocol that is normally not the preferred provider. For example, if you prefer that RIP routes be installed in the routing table rather than OSPF routes, you could change the administrative distance of RIP to a lower value than OSPF (110), as shown below.
Router(config)# router rip Router(config)# distance 100
All the other options are incorrect because they do not represent the administrative distance.
Objective:
Routing Fundamentals
Sub-Objective:
Interpret the components of routing table -
Which set of Cisco Internetwork Operating System (IOS) commands is used on Cisco routers to set a password for Telnet lines?
-
router(config-router)# line vty 0 4 router(config-line)# login router(config-line)# password password
-
router(config)# line telnet 0 4 router(config-line)# login router(config-line)# password password
-
router(config)# line aux 0 router(config-line)# login router(config-line)# password password
-
router(config)# line vty 0 4 router(config-line)# login router(config-line)# password password
Explanation:
The following commands are used on Cisco routers to set a password for Telnet lines:router(config)# line vty 0 4 router(config-line)# login router(config-line)# password password
An explanation of the commands is below:
router(config)# line vty 0 4: Enters line configuration mode for virtual terminal lines 0 to 4.
router(config-line)# login: Ensures that any remote access is prompted for a password.
router(config-line)# password password: Sets a password of “password” for VTY lines.Assigning a password to the VTY lines is required for remote connections to the device to be possible. If a password has not been configured the following error message will be generated when the connection is attempted:
Password required but not set [Connection to foreign host 106.5.5.1 closed by foreign host]
Configuring a VTY password and requiring the password (accomplished with the login command) is good first step in securing Telnet access to the device. Another step that can enhance the security of remote access to the device would be to apply an access list to the VTY lines with the access-class command.
The command sequence which begins with router(config-router)# line vty 0 4 is incorrect because the line vty 0 4 command should be executed in global configuration mode, not routing protocol configuration mode.
The line telnet 0 4 command is incorrect because this is not a valid Cisco IOS command.
The line aux 0 command is incorrect because this allows you to configure the properties of the Auxiliary port, as opposed to the incoming Telnet (VTY) lines.
Objective:
Infrastructure Management
Sub-Objective:
Configure and verify device management -
-
In which of the following networks does the address 192.168.54.23/27 reside?
- 192.168.54.0
- 192.168.54.8
- 192.168.54.4
- 192.168.54.16
Explanation:
When a class C address such as 192.168.54.0 is subnetted with a /27 mask, the subnet mask in dotted decimal format is 255.255.255.224. This means that the interval between the network IDs of the resulting subnets is 32. The resulting network IDs are as follows:192.168.54.0
192.168.54.32
192.168.54.64
192.168.54.92 and so on.Therefore, the address 192.168.54.23 resides in the 192.168.54.0 subnet. The address 192.168.54.0 is called a network ID or, alternately, a subnet address. It represents the subnet as a group and will be used in the routing tables to represent and locate the subnet.
Neither the first address (192.168.54.0, the network ID) nor the last address (192.168.54.31, the broadcast address) in any resulting subnet can be used. Therefore, the addresses in this range are 192.168.54.1 through 192.168.54.30, which includes the 192.168.54.23 address.
192.168.54.8 would only be a network ID if the mask were /29, which would result in an interval of 8 between network IDs. However, even if a /29 mask were used, the 192.168.54.23 address would not fall in its range. The address range for a /29 mask would be 192.168.54.9 through 192.168.54.14.
Similarly, 192.168.54.4 would only be a network ID for a /30 mask, which would result in an interval of 4 between network IDs. But even if a /30 mask were used, the 192.168.54.23 address would not fall in its range. The address range for a /30 mask would be 192.168.54.5 through 192.168.54.6.
192.168.54.16 could be a network ID if the mask were /28, /29 or /30, but not with a /27 mask.
Objective:
Network Fundamentals
Sub-Objective:
Apply troubleshooting methodologies to resolve problems -
What is the primary benefit of the Virtual Local Area Network (VLAN) Trunking Protocol (VTP)?
- broadcast control
- frame tagging
- inter-VLAN routing
- consistent VLAN configuration across switches in a domain
Explanation:
VTP manages configured VLANs across a switched network and maintains consistency of VLAN information throughout a VTP domain. When an administrator adds, deletes, or renames VLANs, VTP propagates this information to all other switches in the VTP domain. This makes the process of VLAN changes a plug-and-play activity. This protocol was developed by, and remains proprietary to Cisco Systems. Broadcast control is not the primary benefit of VTP. Broadcast control is achieved by using VLANs. VLANs segment the network into logical broadcast domains. This helps in the reduction of unnecessary traffic over the network and optimizes the available bandwidth use. VTP pruning helps reduce broadcast and unknown unicast over VLAN trunk links. However, this is not the primary benefit of VTP.Frame tagging is required for VLAN identification as frames traverse trunk links in a switch fabric. Inter-Switch Link (ISL) and IEEE 802.1q are the two methods of frame tagging available on Cisco devices. ISL is proprietary to Cisco, whereas IEEE 802.1q is a standard method. VTP is not a frame tagging method.
Inter-VLAN routing is achieved by an Open Systems Interconnect (OSI) Layer 3 device (Router). Inter-VLAN routing is not a benefit of VTP.
Objective:
LAN Switching Fundamentals
Sub-Objective:
Configure, verify, and troubleshoot VLANs (normal/extended range) spanning multiple switches -
Which of the following is NOT a feature offered by Enhanced Interior Gateway Routing Protocol (EIGRP)?
- variable length subnet masks (VLSM)
- partial updates
- neighbor discovery mechanism
- multiple vendor compatibility
Explanation:
EIGRP is a Cisco-proprietary routing protocol, and does not support multiple vendor environments. EIGRP is a classless routing protocol, and thus supports variable length subnet masks (VLSM).EIGRP routers build a neighbor table in memory, and use a multicast-based neighbor discovery mechanism.
EIGRP routers send partial updates when there are network events.
The following are features offered by EIGRP:
– Fast convergence
– Partial updates
– Neighbor discovery mechanism
– VLSM
– Route summarization
– ScalabilityObjective:
Routing Fundamentals
Sub-Objective:
Compare and contrast distance vector and link-state routing protocols -
You are the network administrator for your company and have configured Cisco Discovery Protocol (CDP) in your network. You recently noticed that when devices send large numbers of CDP neighbor announcements, some devices are crashing. You decide to disable CDP on the router.
Which command should you use to achieve the objective?
- no cdp run
- set cdp disable
- no cdp enable
- no cdp advertise-v2
Explanation:
You should use the no cdp run command to disable CDP on the router. Due to a known vulnerability regarding the handling of CDP by Cisco routers and switches when devices send large numbers of CDP neighbor announcements, some devices can crash or cause abnormal system behavior. To overcome this problem, you can disable CDP for the entire router by using the no cdp run command. You cannot use the set cdp disable command to disable CDP on the router. This command disables CDP on an entire Catalyst switch.You cannot use the no cdp enable command to disable CDP on the router. This command disables CDP on a specific interface.
You cannot use the no cdp advertise-v2 command to disable CDP on the router. This command disables CDPv2 advertisements.
Objective:
LAN Switching Fundamentals
Sub-Objective:
Configure and verify Layer 2 protocols -
Which of the following topologies is used in Wide Area Networks (WANs)?
- FDDI
- CDDI
- SONET
- Token Ring
Explanation:
Synchronous Optical NETwork (SONET) is the standard topology for fiber optic networks. Developed in 1980s, SONET can transmit data at rates of up to 2.5 gigabits per second (Gbps). All other options are incorrect because they are LAN topologies, not WAN topologies.Fiber Distributed Data Interface (FDDI) specifies a 100-Mbps dual-ring fiber optics-based token-passing LAN. FDDI is typically implemented for high-speed LAN backbones because of its support for high bandwidth.
Copper Distributed Data Interface (CDDI) is copper version of FDDI. They differ only in that FDDI can span longer distances than CDDI due to the attenuation characteristics of copper wiring.
Token Ring/IEEE 802.5 LAN technology was developed by IBM in 1970. Token-ring LAN technology is based on token-passing, in which a small frame, called a token, is passed around the network. Possession of the token grants the node the right to transmit data. Once the data is transmitted, the station passes the token to the next end station.
Objective:
Network Fundamentals
Sub-Objective:
Compare and contrast network topologies -
Two catalyst switches on a LAN are connected to each other with redundant links and have Spanning Tree Protocol (STP) disabled.
What problem could occur from this configuration?
- It may cause broadcast storms.
- All ports on both switches may change to a forwarding state.
- It may cause a collision storm.
- These switches will not forward VTP information.
Explanation:
The configuration in the scenario may cause broadcast storms. When there are redundant links between two switches, it is recommended that you enable Spanning Tree Protocol to avoid switching loops or broadcast storms. Loops occur when there is more than one path between two switches. STP allows only one active path at a time, thus preventing loops. A broadcast storm occurs when the network is plagued with constant broadcasts. When the switches have redundant links, the resulting loops would generate more broadcasts, eventually resulting in a complete blockage of available bandwidth that could bring the complete network down. This situation is referred to as a broadcast storm. The option stating that all ports on both switches may change to a forwarding state is incorrect. Forwarding is a port state that is available when using STP. When STP is disabled, the switch cannot change the STP states of its ports.The option stating that the switches will not forward VLAN Trunking Protocol (VTP) information is incorrect. Enabling or disabling STP does not have a direct effect on VTP messages.
The term collision storm is not a valid term.
Objective:
LAN Switching Fundamentals
Sub-Objective:
Configure, verify, and troubleshoot interswitch connectivity -
Users on the LAN are unable to access the Internet. How would you correct the immediate problem?

200-301 Part 06 Q10 063 Router# show ip interface brief
Interface IP-Address OK? Method Status Protocol
FastEthernet 0/0 unassigned YES unset down down
FastEthernet 0/1 172.16.1.254 YES NVRAM up up
Serial0/0 200.16.4.25 YES NVRAM administratively down down
Serial0/1 unassigned YES unset down down- Configure a bandwidth on the serial interface.
- Perform a no shutdown command on the serial interface.
- Configure a private IP address on the Fastethernet0/0 LAN interface.
- Change the IP address on the serial interface.
Explanation:
The output indicates that the serial interface leading to the Internet is administratively down. All router interfaces are disabled by default due to the presence of a shutdown command in the running configuration. The no shutdown command removes this configuration, and the interface becomes active. The command sequence is:Router(config)# interface serial0/0 Router(config-if)# no shutdown
Although it was not the problem in the scenario, the S0/0 interface could also cause an error if it is configured as shown in this output:
Interface IP-Address OK? Method Status Protocol
Serial0/0 200.16.4.25 YES NVRAM up down
In this example, the S0/0 interface has been enabled, and while there is Layer 1 connectivity (the Status column), Layer 2 is not functioning (the Protocol column). There are two possible reasons for this result:
– Interface S0/0 is not receiving a clock signal from the CSU/DSU (if one is present).
– The encapsulation type configured on S0/0 does not match the type configured on the other end of the link (if the other end is a router).Configuring a bandwidth on the serial interface is incorrect because the output indicates the interface is administratively down, which does not pertain to bandwidth.
Configuring a private IP address on the Fastethernet0/0 LAN interface is incorrect because the output indicates the problem is with the disabled serial interface.
The IP address on the serial interface may or may not be valid, but it is not the immediate cause of the connectivity problem. The serial interface is disabled.
Objective:
LAN Switching Fundamentals
Sub-Objective:
Troubleshoot interface and cable issues (collisions, errors, duplex, speed) -
Which two statements are TRUE of Internet Protocol (IP) addressing? (Choose two.)
- Public addresses are registered with the Internet Assigned Numbers Authority (IANA).
- These addresses are publicly registered with the Internet Service Provider (ISP).
- Through a public IP address, you can access another computer on the Internet, such as a Web server.
- The ranges of public IP addressing are 10.0.0.0 to 10.255.255.255, 172.16.0.0 to 172.31.255.255, and 192.168.0.0 to 192.168.255.255.
- Private addresses are allocated by the Internet Assigned Numbers Authority (IANA).
Explanation:
Public addresses are publicly registered with the Internet Assigned Numbers Authority (IANA). Through a public IP address, you can access an Internet computer like a Web server. The following statements are true of public IP addressing:
– These addresses are publicly registered with the Internet Assigned Numbers Authority (IANA)
– Through a public IP address, you can access another Internet computer, such as a Web server.
– Other people on the Internet can obtain information about or access to your computer via a public IP address.
– Public IP addresses are visible to the public.The option stating that public IP addresses are publicly registered with the Internet Service Provider (ISP) is incorrect. Public IP addresses are registered with the Internet Assigned Numbers Authority (IANA). Since 1998, InterNIC has been primarily responsible for allocating domain names and IP addresses under the governance of the Internet Corporation for Assigned Names and Numbers (ICANN) body, a U.S. non-profit corporation that was created to oversee work performed by the Internet Assigned Numbers Authority (IANA).
The option stating that 10.0.0.0 to 10.255.255.255, 172.16.0.0 to 172.31.255.255, and 192.168.0.0 to 192.168.255.255 are the range of public IP addressing is incorrect. These ranges belong to private IP addressing.
The option stating that private addresses are allocated by the IANA is incorrect. Private IP address are not managed, but are used by private organizations as they see fit.. The IANA is governed by ICANN, and its primarily role is to allocate overseas global IP addresses from the pools of unallocated addresses, as well as DNS root zone management.
Objective:
Network Fundamentals
Sub-Objective:
Describe the need for private IPv4 addressing -
Which type of network uses Carrier Sense Multiple Access with Collision Detection (CSMA/CD) as an access method?
- Token Ring
- LocalTalk
- 100VG-AnyLan
- Ethernet
Explanation:
Ethernet networks use CSMA/CD as an access method. In CSMA/CD, if a device wants to send a frame in the network, it first determines if the network is free. If the network is not free, the node will wait before sending the frame into a network. If the network is free, it sends the frame; if another device sends a frame simultaneously then their signals or frames collide. When the collision is detected, both packets wait for a random time before retrying. The following statements are true regarding CSMA/CD:
– CSMA/CD is required for shared collision domains, such as when hosts are connected via hubs. (Hubs are Layer 1 devices, and thus do not create collision domains.)
– CSMA/CD networks normally operate in half-duplex mode, since in a shared collision domain, a host cannot send and receive data at the same time.
– CSMA/CD is not required when connected to non-shared (private) collision domains, such as when hosts are connected to dedicated switch ports.
– Switches create dedicated collision domains, so devices can operate in full-duplex mode.Token Ring is incorrect because Token Ring uses token passing as the access method.
LocalTalk is incorrect because LocalTalk uses CSMA/CA (Collision Avoidance) as the access method.
100VG-AnyLan is incorrect because 100VG-AnyLan uses demand priority as the access method.
Objective:
LAN Switching Fundamentals
Sub-Objective:
Interpret Ethernet frame format -
You are advising a client on the options available to connect a small office to an ISP.
Which of the following is an advantage of using an ADSL line?
- it uses the existing cable TV connection
- it uses the existing phone line
- you receive a committed information rate (CIR) from the provider
- the upload rate is as good as the download rate
Explanation:
xDSL lines, including the ADSL variant, use the existing phone line and as such make installing only a matter of hooking up the DSL modem to the line. It does not use the use the existing cable TV connection. This is a characteristic of using a cable modem rather than ADSL.You do not receive a committed information rate (CIR) from the provider. CIR is provided with a frame relay connection.
The upload rate is NOT as good as the download rate with asynchronous DSL (ADSL). The download rate is significantly better than the upload rate. Symmetric Digital Subscriber Line (SDSL) is a version of DSL that supplies an equal upload and download rate, but that is not the case with ADSL.
Objective:
WAN Technologies
Sub-Objective:
Describe WAN access connectivity options -
Which of the following methods will ensure that only one specific host can connect to port F0/1 on a switch?
- Configure port security on F0/1 to forward traffic to a destination other than that of the MAC address of the host.
- Configure the MAC address of the host as a static entry associated with port F0/1.
- Configure port security on F0/1 to accept traffic only from the MAC address of the host.
- Configure an inbound access control list on port F0/1 limiting traffic to the IP address of the host.
- Configure port security on F0/1 to accept traffic other than that of the MAC address of the host.
Explanation:
To limit connections to a specific host, you should configure port security to accept traffic only from the MAC address of the host. By default, an unlimited number of MAC addresses can be learned on a single switch port, whether it is configured as an access port or a trunk port. Switch ports can be secured by defining one or more specific MAC addresses that should be allowed to connect, and by defining violation policies (such as disabling the port) to be enacted if additional hosts try to gain a connection. The following example secures a switch port by manually defining the MAC address of allowed connections:switch(config-if)# switchport port-security switch(config-if)# switchport port-security mac-address 00C0.35F0.8301
The first command activates port security on the interface, while the second command statically defines the MAC address of 00c0.35F0.8301 as an allowed host on the switch port.
The mac-address-table static command assigns a permanent MAC address to the port, but does not prevent any other MAC addresses from being associated with the port. . The command below would assign the MAC address 0050.3e8d.62bb to port 15 on the switch:
switch(config)# mac-address-table static 0050.3e8d.6400 interface fastethernet0/15
You should not configure port security on F0/1 to forward traffic to a destination other than that of the MAC address of the host. Traffic from other hosts should be rejected, not forwarded or accepted. For the same reason, you should not configure port security on F0/1 to accept traffic other than that of the MAC address of the host.
You cannot configure an inbound access control list on port F0/1 limiting traffic to the IP address of the host. It is impossible to filter traffic based on IP addresses on a Layer 2 switch.
Objective:
Infrastructure Security
Sub-Objective:
Configure, verify, and troubleshoot port security -
Consider the following diagram:

200-301 Part 06 Q15 064 Which of the following routing protocols could NOT be used with this design?
- RIPv1
- RIPv2
- EIGRP
- OSPF
Explanation:
The network design displayed has subnets of a major classful network located in opposite directions from the perspective of some of the individual routers. This configuration can be accommodated by any routing protocol that supports Variable Length Subnet masks (VLSM) or the transfer of subnet mask information in routing advertisements.RIPv1 supports neither of these. RIPv1 will automatically summarize routing advertisements to their classful network (in this case 192.168.1.0/24). This action will cause some of the routers to have routes to the same network with different next hop addresses, which will NOT work.EIGRP, RIPv2 and OSPF all support VLSM and can be used in the design shown in the scenario.
Objective:
Routing Fundamentals
Sub-Objective:
Compare and contrast distance vector and link-state routing protocols -
The four switches in the diagram below have default configurations. Considering the bandwidths indicated on each link and the MAC addresses indicated for each switch, which ports will be forwarding after RSTP has converged? (Choose all that apply.)
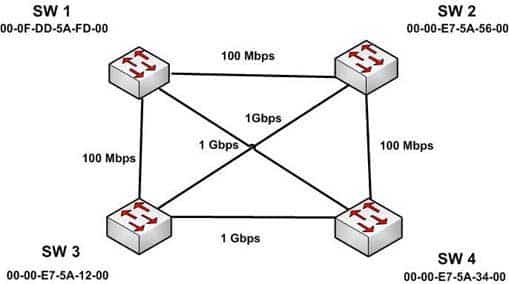
200-301 Part 06 Q16 065 - SW 1 port that connects to SW 4
- SW 1 port that connects to SW 2
- SW 1 port that connects to SW 3
- SW 2 port that connects to SW 3
- SW 2 port that connects to SW 4
- SW 3 port that connects to SW 4
- SW 3 port that connects to SW 1
- SW 3 port that connects to SW 2
-
You and your team are evaluating the use of OSPFv3 in your IPv6 network.
Which of the following statements is true of OSPFv3?
- There will be a higher demand on the processor to run the link-state routing algorithm
- Router IDs must match for adjacency formation
- Area IDs do not need to match for adjacency formation
- Area types do not need to match for adjacency formation
Explanation:
There will be a higher demand on the processor to run the link-state routing algorithm. As with OSPFv2, OSPFv3 uses the Shortest Path first (SPF) algorithm, which is processor intensive. It is one of the only downsides of using the algorithm.OSPFv3 also shares a number of other characteristics with its v2 counterpart with respect to adjacency formation. For example:
– Router IDs should not match.
– Router IDs should reflect the correct router ID for each device.
– Area IDs must match.
– Area types must match.Objective:
Routing Fundamentals
Sub-Objective:
Configure, verify, and troubleshoot single area and multi-area OSPFv3 for IPv6 (excluding authentication, filtering, manual summarization, redistribution, stub, virtual-link, and LSAs) -
You have established a console session with R1 and you are attempting to download an IOS image from the TFTP server in the diagram below.

200-301 Part 06 Q18 066 However, you are unable to make the connection to 150.140.6.5. What is the problem?
- The IP address of the management station is incorrect
- The IP address of the TFTP server is incorrect
- The interfaces between R1and R2 are not in the same subnet
- The IP address of Switch B is incorrect
Explanation:
The IP address of the TFTP server is incorrect. The TFTP server, Switch B and the Fa0/2 interface on R3 should all be in the same subnet. With a 27-bit mask (255.255.255.224) against the 150.140.0.0 classful network the resulting subnets are:150.140.0.0
150.140.0.32
150.140.0.64and so on, incrementing in intervals of 32 in the last octet until it reaches the 150.140.6.0 subnet.
150.140.6.0
150.140.6.32
150.140.6.64At this point, we can see that Switch B and the router interface are in the 150.140.6.32 subnet, while the TFTP server is in the 150.140.6.0 subnet. The IP address of the TFTP server needs to be in the 150.140.6.33-150.140.6.62 range, while avoiding the addresses already used on R1 and the switch.
The IP address of the management station does not appear to be in any of the networks listed in the diagram, but that doesn’t matter since the connection to the router is through the console cable which does not require a correct IP address.
The Fa0/2 and Fa0/1 interfaces on R1 and R2 are in the same subnet. Using a 25-bit mask against the 192.18.5.0/24 classful network yields the following subnets:
192.18.5.0
192.168.5.128Both router interfaces in question are in the 192.18.5.0 subnet.
As we have already determined, the IP address of Switch B is correct. Even if it were incorrect or missing altogether, it would have no impact on connecting to the TFTP server. Switches merely switch frames based on MAC addresses and only need an IP address for management purposes.
Objective:
Routing Fundamentals
Sub-Objective:
Troubleshoot basic Layer 3 end-to-end connectivity issues -
R1 and R2 are connected as shown in the diagram and are configured as shown in output in the partial output of the show run command.
200-301 Part 06 Q19 067 
200-301 Part 06 Q19 068 The command ping R2 fails when executed from R1. What command(s) would allow R1 to ping R2 by name?
-
R1(config)#int S1 R1(config-if)#no ip address 192.168.5.5 R1(config-if)# ip address 192.168.5.9 255.255.255.252
-
R1(config)#no ip host R1 R1(config)# ip host R2 192.168.5.6 255.255.255.252 -
R1(config)#no hostname R2 R1(config)# hostname R1
-
R2(config)#int S1 R1(config-if)#no ip address 192.168.5.5 R1(config-if)# ip address 192.168.5.9 255.255.255.0
Explanation:
Both routers have been configured with the ip host command. This command creates a name to IP address mapping, thereby enabling the pinging of the device by address. On R1, the mapping is incorrect and needs to be corrected. Currently it is configured as ip host R1 192.168.5.6. It is currently mapping its own name to the IP address of R2.To fix the problem, you should remove the incorrect IP address mapping and create the correct mapping for R2, as follows:R1(config)#no ip host R1 R1(config)# ip host R2 192.168.5.6 255.255.255.252
Once this is done, the ping on R2 will succeed.
The IP address of the S1 interface on R1 does not need to be changed to 192.168.5.9 /30. In fact, if that is done the S1 interface on R1 and the S1 interface in R2 will no longer be in the same network. With a 30-bit mask configured, the network they are currently in extends from 192.168.5.4 – 192.168.5.7. They are currently set to the two usable addresses in that network, 192.168.5.5 and 192.168.5.6.
The hostnames of the two routers do need to be set correctly using the hostname command for the ping to function, but they are correct now and do not need to be changed.
The subnet mask of the S1 interface on R2 does not need to be changed to 255.255.255.0. The mask needs to match that of R1, which is 255.255.255.252.
Objective:
Infrastructure Services
Sub-Objective:
Troubleshoot client connectivity issues involving DNS -
-
You run the following command:
switch# show ip interface brief
What information is displayed?
- A summary of the IP addresses and subnet mask on the interface
- A summary of the IP addresses on the interface and the interface’s status
- The IP packet statistics for the interfaces
- The IP addresses for the interface and the routing protocol advertising the network
Explanation:
The command show ip interface brief displays a summary of the IP address on the interface and the interface’s status. The status shows whether the interface is up. This command is useful when you are connected to a router or switch with which you are not familiar, because it allows you to obtain the state of all interfaces or switch ports. Sample output of this command is shown below:

200-301 Part 06 Q20 069 This command does not display subnet mask information. You should use other commands, such as show ip interface or show run interface, to verify the subnet mask.
IP statistics about the interface are displayed with the command show ip interface. Adding the brief keyword tells the switch to leave out everything but the state of the interface and its IP address.
To view the routing protocol advertising an interfaces network, you would use the command show ip protocol.
Objective:
LAN Switching Fundamentals
Sub-Objective:
Configure, verify, and troubleshoot interswitch connectivity