200-301 : Cisco Certified Network Associate (CCNA) : Part 07
-
Which command can be issued at the following prompt?
Router(config-router)#
- show interface
- network
- interface
- ip default-gateway
Explanation:
The network command can be issued at the Router(config-router)# prompt, which also indicates that the router is in router configuration mode. The network command is used to configure the network upon which a routing protocol is functioning. The router configuration mode is accessed by issuing the router command in the global configuration mode along with a parameter indicating the routing protocol to be configured. For example:R4(config)#router eigrp 1
changes the prompt to:
R4(config-router)#
which then allows you to specify the network as follows:
R4(config-router)#network 192.18.5.0
All other options are incorrect as these commands can be issued only in the global configuration command mode (which would be indicated by the R4(config)# prompt.
Objective:
Infrastructure Management
Sub-Objective:
Configure and verify initial device configuration -
Which Cisco Internetwork Operating System (IOS) command would be used to set the privileged mode password to “cisco”?
-
router(config)# enable password cisco -
router# enable secret cisco
-
router(config)# line password cisco
-
router(config-router)# enable password cisco
Explanation:
The enable password command is used to set the local password to control access to privileged levels. This command is executed on the global configuration mode, as in router(config)# enable password cisco. The syntax of the command is:
router(config)# enable password [level level] {password | [encryption-type] encrypted-password}The parameters of the command are as follows:
– level level: An optional parameter to set the privilege level at which the password applies. The default value is 15.
– password: Specifies the password that is used to enter enable mode.
– encryption-type: An optional parameter to specify the algorithm used to encrypt the password.
– encrypted-password: Specifies the encrypted password that is copied from another router configuration.The router# enable secret cisco command is incorrect because the enable secret command must be executed from global configuration mode, not privileged EXEC mode. In fact, this is the password for which you will be prompted when you attempt to enter privilege exec mode.
The line password command is incorrect because this command is not a valid Cisco IOS command.
The router(config-router)# enable password cisco command is incorrect because the enable password command must be entered in global configuration mode.
Objective:
Infrastructure Security
Sub-Objective:
Configure, verify, and troubleshoot basic device hardening -
-
Which of the following is NOT managed by the cloud provider in an IaaS deployment?
- virtualization
- servers
- storage
- operating system
Explanation:
Operating systems are not managed by the cloud provider in an Infrastructure as a service (IaaS) deployment. Only storage, virtualization, servers, and networking are the responsibility of the provider. The customer is responsible for the following with IaaS:
– Operating systems
– Data
– Applications
– Middleware
– RuntimeIn a Platform as a Service (PaaS) deployment, the provider is responsible for all except the following, which is the responsibility of the customer:
– Applications
– DataIn Software as a Service (SaaS) deployment, the provider is responsible for everything.
Objective:
Network Fundamentals
Sub-Objective:
Describe the effects of cloud resources on enterprise network architecture -
What command produced the following as a part of its output?
1 14.0.0.2 4 msec 4 msec 4 msec 2 63.0.0.3 20 msec 16 msec 16 msec 3 33.0.0.4 16 msec * 16 msec
- Ping
- Traceroute
- Tracert
- Extended ping
Explanation:
The output displayed is a part of the output from executing the traceroute command. The traceroute command finds the path a packet takes while being transmitted to a remote destination. It is also used to track down routing loops or errors in a network. Each of the following numbered sections represents a router being traversed and the time the packet took to go through the router:1 14.0.0.2 4 msec 4 msec 4 msec 2 63.0.0.3 20 msec 16 msec 16 msec 3 33.0.0.4 16 msec * 16 msec
The output would not be displayed by the ping command. This command is used to test connectivity to a remote ip address. The output from the ping command is as follows:
router1# ping 10.201.1.11 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.201.1.11, timeout is 2 seconds: ..... Success rate is 0 percent (0/5)
The ping in this output was unsuccessful, as indicated by the Success rate is 0 percent output.
The output would not be displayed by the tracert command. The tracert command is used by Microsoft Windows operating systems, not the Cisco IOS command line interface. However, the purpose of the tracert command is similar to the Cisco traceroute utility, which is to test the connectivity or “reachability” of a network device or host. The tracert command uses Internet Control Message Protocol (ICMP).
The output would not be displayed by the extended version of the ping command. This command can be issued on the router to test connectivity between two remote routers. A remote execution means that you are not executing the command from either of the two routers you are interested in testing, but from a third router.
To execute an extended ping, enter the ping command from the privileged EXEC command line without specifying the target IP address. The command takes the router into configuration mode, where you can define various parameters, including the destination and target IP addresses. An example is below:
Protocol [ip]: Target IP address: 10.10.10.1 Repeat count [5]: Datagram size [100]: Timeout in seconds [2]: Extended commands [n]: y Source address or interface: 12.1.10.2 Type of service [0]: Set DF bit in IP header? [no]: Validate reply data? [no]: Data pattern [0xABCD]: Loose, Strict, Record, Timestamp, Verbose[none]: Sweep range of sizes [n]: Type escape sequence to abort.
Each line is a menu question allowing you to either accept the default setting (in parenthesis) of the ping or apply a different setting. The real value of this command is that you can test connectivity between two remote routers without being physically present at those routers, as would be required with the standard version of the ping command.
Objective:
Routing Fundamentals
Sub-Objective:
Troubleshoot basic Layer 3 end-to-end connectivity issues -
From which of the following attacks can Message Authentication Code (MAC) shield your network?
- DoS
- DDoS
- spoofing
- SYN floods
Explanation:
Message Authentication Code (MAC) can shield your network from spoofing attacks. Spoofing, also known as masquerading, is a popular trick in which an attacker intercepts a network packet, replaces the source address of the packets header with the address of the authorized host, and reinserts fake information which is sent to the receiver. This type of attack involves modifying packet contents. MAC can prevent this type of attack and ensure data integrity by ensuring that no data has changed. MAC also protects against frequency analysis, sequence manipulation, and ciphertext-only attacks.MAC is a secure message digest that requires a secret key shared by the sender and receiver, making it impossible for sniffers to change both the data and the MAC as the receiver can detect the changes.A denial-of-service (DoS) attack floods the target system with unwanted requests, causing the loss of service to users. One form of this attack generates a flood of packets requesting a TCP connection with the target, tying up all resources and making the target unable to service other requests. MAC does not prevent DoS attacks. Stateful packet filtering is the most common defense against a DoS attack.
A Distributed Denial of Service attack (DDoS) occurs when multiple systems are used to flood the network and tax the resources of the target system. Various intrusion detection systems, utilizing stateful packet filtering, can protect against DDoS attacks.
In a SYN flood attack, the attacker floods the target with spoofed IP packets and causes it to either freeze or crash. A SYN flood attack is a type of denial of service attack that exploits the buffers of a device that accept incoming connections and therefore cannot be prevented by MAC. Common defenses against a SYN flood attack include filtering, reducing the SYN-RECEIVED timer, and implementing SYN cache or SYN cookies.
Objective:
Infrastructure Security
Sub-Objective:
Configure, verify, and troubleshoot basic device hardening -
In the diagram below, when a packet sent from the PC at 10.0.1.3 to the PC at 10.1.1.3 leaves the Fa0/1 interface of R1, what will be the source and destination IP and MAC addresses?
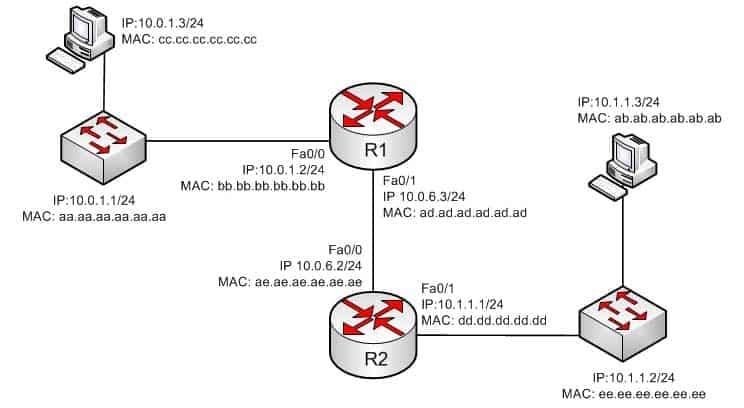
200-301 Part 07 Q06 070 - source IP 10.1.1.2 destination IP 10.1.1.3
Source MAC ad.ad.ad.ad.ad.ad destination MAC ab.ab.ab.ab.ab.ab - source IP 10.1.1.1 destination IP 10.1.1.3
Source MAC ad.dd.dd.dd.dd.dd.dd destination MAC ab.ab.ab.ab.ab.ab - source IP 10.0.1.3 destination IP 10.1.1.3
Source MAC ad.ad.ad.ad.ad.ad destination MAC ae.ae.ae.ae.ae.ae - source IP 10.0.6.3 destination IP 10.1.1.3
Source MAC ad.ad.ad.ad.ad.ad destination MAC ae.ae.ae.ae.ae.ae
Explanation:
The source IP address will be 10.0.1.3 and the destination IP address will be 10.1.1.3. The source MAC address will be ad.ad.ad.ad.ad.ad and the destination MAC address will be ae.ae.ae.ae.ae.ae. The source and destination IP addresses never change as the packet is routed across the network. The MAC address will change each time a router sends the packet to the next router or to the ultimate destination. The switches do not change either set of addresses in the header; they just switch the frame to the correct switch port according to the MAC address table. Therefore, when the packet leaves R1, the source MAC address will be that of R1 and the destination MAC address will be that of the Fa0/0 interface of R2. The IP addresses will be those of the two workstations, 10.0.1.3 and 10.1.1.3.When the workstation at 10.0.1.3 starts the process, it will first determine that the destination address is in another subnet and will send to its default gateway (10.0.1.2). It will perform an ARP broadcast for the MAC address that goes with 10.0.1.2, and R1 will respond with its MAC address, bb.bb.bb.bb.bb.bb.
After R2 determines the next-hop address to send to 10.0.1.3 by parsing the routing table, it will send the packet to R1 at 10.0.6.2. When R2 receives the packet, R2 will determine that the network 10.0.1.0/24 is directly connected and will perform an ARP broadcast for the MAC address that goes with 10.0.1.3. The workstation at 10.0.1.3 will respond with its MAC address, ab.ab.ab.ab.ab.ab.
Objective:
Routing Fundamentals
Sub-Objective:
Describe the routing concepts - source IP 10.1.1.2 destination IP 10.1.1.3
-
Which are among the valid steps in the process of recovering a password on a Cisco router? (Choose all that apply.)
- Restart the router.
- Configure the enable secret password.
- Enter the router diagnostic mode.
- Enter user mode.
- Answer the security question to recover the password.
Explanation:
Three of the steps that should be performed while recovering a password on a Cisco router are to restart the router in ROMMOM mode, enter ROMMON mode (router diagnostic mode) and reset the enable secret password. The complete password recovery process on a Cisco Router is as follows: Configure the router so that it starts without reading the non-volatile random access memory (NVRAM). This is also referred to as the system test mode, which you enter by changing the configuration register. You must first restart the router and within 60 seconds press Break on the terminal keyboard. Then the router will skip normal reading of the startup configuration file and will go to the ROMMON prompt (shown below this text section). At this command prompt, type confreg 0x2142 to instruct the router to boot to flash memory at the next reboot. When it does, it will ignore the startup configuration file again and will behave as if it had no configuration, as a new router would.rommon 1> confreg 0x2142
Type reset to reboot the router.
Enter enable mode through the test system mode.
View the existing password (if it can be viewed, it may be encrypted), configure a new password, or delete the configuration.
Configure the router to start by reading the NVRAM, which is done by resetting the configuration register to its normal value. Run these commands:Router#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#config Router(config)#config-register 0x2102
Restart the router.
You will proceed through user mode but to make any changes you make must be at the global configuration prompt.
Finally, there is no way to recover a password by answering a security question.
Objective:
Infrastructure Management
Sub-Objective:
Use Cisco IOS tools to troubleshoot and resolve problems -
Which of the following is NOT a characteristic of private Internet Protocol (IP) addressing?
- These addresses are not routable through the public Internet.
- These addresses are publicly registered with the Internet Network Information Center (InterNIC).
- These addresses are reserved by the Internet Assigned Numbers Authority (IANA).
- The ranges of private IP addressing are 10.0.0.0 to 10.255.255.255, 172.16.0.0 to 172.31.255.255, and 192.168.0.0 to 192.168.255.255.
Explanation:
It is NOT correct to state that private IP addresses are publicly registered with the Internet Network Information Center (InterNIC). Only public IP addresses are registered with the InterNIC. The following characteristics are TRUE regarding private IP addressing:
– Private addresses are not routable through the public Internet.
– Private addresses are reserved by the Internet Assigned Numbers Authority (IANA).
– The ranges of private IP addressing are 10.0.0.0 to 10.255.255.255, 172.16.0.0 to 172.31.255.255 and 192.168.0.0 to 192.168.255.255.
– The use of private IP addressing conserves the use of the public IPv4 address spacePrivate addresses cannot be registered publicly.
Private IP addresses conserve public addressing space and can improve network security.
Objective:
Network Fundamentals
Sub-Objective:
Describe the need for private IPv4 addressing -
You are the network administrator for your company. You have implemented VLAN Trunking Protocol (VTP) in your network. However, you have found that VTP is not synchronizing VLAN information.
Which of the following items should be verified to resolve the problem? (Choose three.)
- Ensure that switches in the VTP domain are configured with VTP version 1 and version 2.
- Ensure that VLANs are active on at least one switch on the VTP domain.
- Ensure that all of the ports that interconnect switches are configured as trunks and are trunking properly.
- Ensure that the VTP domain name is the same on all switches in the domain.
- Ensure that identical passwords are configured on all VTP switches.
Explanation:
The following is a list of the steps to take if VTP fails to exchange VLAN information:
– Ensure that all of the ports that interconnect switches are configured as trunks and are trunking properly.
– Ensure that VLANs are active in all the devices.
– Ensure that at least one switch is acting as a VTP server in the VTP domain.
– Ensure that the VTP domain name is the same for all switches in the domain. The VTP domain name is case-sensitive.
– Ensure that the VTP password is the same for all switches in the domain.
– Ensure that the same VTP version is used by every switch in the domain. VTP version 1 and version 2 are not compatible on switches in the same VTP domain. You should not ensure that switches are configured with VTP version 1 and version 2 in the domain, because VTP version 1 and version 2 are incompatible. VTP version 1 is the default on all Cisco switches.You should not ensure that VLANs are active on at least one switch in the VTP domain, because VLANs should be active in all of the devices in a VTP domain.
Objective:
LAN Switching Fundamentals
Sub-Objective:
Configure, verify, and troubleshoot VLANs (normal/extended range) spanning multiple switches -
Which of the following is NOT a possible component of Enhanced Interior Gateway Routing Protocol’s (EIGRP) composite metric?
- Cost
- Load
- Delay
- Bandwidth
Explanation:
Cost is not a component of EIGRP’s composite metric. The cost, or efficiency, of a path is used as a metric by the Open Shortest Path First (OSPF) routing protocol. Enhanced IGRP (EIGRP) is Cisco Systems’ proprietary routing protocol. It can use bandwidth, delay, load, reliability, and maximum transmission unit (MTU) to calculate the metric. Of these five metrics, by default, only minimum bandwidth and delay are used to compute the best path.The metric for EIGRP can be calculated with this formula:
Metric = [K1 * Bandwidth + (K2 * Bandwidth) / (256-load) + K3*Delay] * [K5 / (reliability + K4)]
The default constant values for Cisco routers are K1 = 1, K3 = 1, and K2 = 0, K4 = 0, K5 = 0. In the default setting, K1 and K3 have non-zero values, and therefore, by default, the metric is dependent on bandwidth and delay.
Objective:
Routing Fundamentals
Sub-Objective:
Configure, verify, and troubleshoot EIGRP for IPv4 (excluding authentication, filtering, manual summarization, redistribution, stub) -
Which show interfaces command output indicates that the link may not be functional due to a Data Link layer issue, while the Physical layer is operational?
- Ethernet 0/0 is up, line protocol is up
- Ethernet 0/0 is up, line protocol is down
- Ethernet 0/0 is down, line protocol is up
- Ethernet 0/0 is down, line protocol is down
Explanation:
The first or left-hand column (Ethernet 0/0 is up) indicates the Physical layer state of the interface, while the second or right-hand column (line protocol is down) indicates the Data Link layer state of the interface. The following command output excerpt indicates that the link is not functional due to a Data Link layer (or “line protocol”) issue, while the Physical layer is operational:Ethernet 0/0 is up, line protocol is downIf the problem were at the Data Link layer while the Physical layer is operational, the show interfaces command output will indicate that the interface is up, but the line protocol is down.
In the normal operation mode, when both Physical layer and Data Link layer are up, the show interfaces output will display the following message:
Ethernet0/0 is up, line protocol is up
The message Ethernet 0/0 is down, line protocol is up is not a valid output.
The message Ethernet 0/0 is down, line protocol is down indicates that both the Physical layer and the Data Link layer are down. Therefore, this is an incorrect option.
Objective:
LAN Switching Fundamentals
Sub-Objective:
Troubleshoot interface and cable issues (collisions, errors, duplex, speed) -
Which of the following topologies is used in Wide Area Networks (WANs)?
- FDDI
- CDDI
- SONET
- Token Ring
Explanation:
Synchronous Optical NETwork (SONET) is the standard topology for fiber optic networks. Developed in 1980s, SONET can transmit data at rates of up to 2.5 gigabits per second (Gbps). All other options are incorrect because they are LAN topologies, not WAN topologies.Fiber Distributed Data Interface (FDDI) specifies a 100-Mbps dual-ring fiber optics-based token-passing LAN. FDDI is typically implemented for high-speed LAN backbones because of its support for high bandwidth.
Copper Distributed Data Interface (CDDI) is copper version of FDDI. They differ only in that FDDI can span longer distances than CDDI due to the attenuation characteristics of copper wiring.
Token Ring/IEEE 802.5 LAN technology was developed by IBM in 1970. Token-ring LAN technology is based on token-passing, in which a small frame, called a token, is passed around the network. Possession of the token grants the node the right to transmit data. Once the data is transmitted, the station passes the token to the next end station.
Objective:
Network Fundamentals
Sub-Objective:
Compare and contrast network topologies -
Which of the following is the correct command to define a default route using a gateway address of 172.16.0.254?
- ip default-route 172.16.0.254 255.255.0.0
- ip route 0.0.0.0 0.0.0.0 172.16.0.254
- default-gateway 172.16.0.254
- ip route default 172.16.0.254
Explanation:
The ip route command is used to manually define a static route to a destination network. The syntax of the command is as follows:ip route [destination_network] [mask] [next-hop_address or exit interface] [administrative_distance] [permanent]The attributes of the command are as follows:
– destination_network: Defines the network that needs to be added in the routing table.
– mask: Defines the subnet mask used on the network.
– next-hop_address: Defines the default gateway or next-hop router that receives and forwards the packets to the remote network.
– administrative_distance (AD): States the administrative distance. Static routes have an AD of 1, which can be changed to change the priority of the route.Creating a default route is accomplished by substituting 0.0.0.0 for both the [destination_network] and [mask] fields, yielding the following command to create a default route through host 172.16.0.254:
router(config)# ip route 0.0.0.0 0.0.0.0 172.16.0.254
Any route configured manually is considered a static route. Another example of a command that creates a non-default route is shown below:
router(config)# ip route 192.168.12.0 255.255.255.0 172.65.3.1
This command would instruct the router on which the command was executed to send any traffic for the 192.168.12.0/24 network to the router located at 172.65.3.1.
You can also affect the route by changing the administrative distance of the route. By default, all static routes have an AD of 1, making them preferable to routes learned from routing protocols. However, you can add the AD parameter at the end of the command as shown below, making the static route less desirable than one learned from a routing protocol such as RIP:
router(config)# ip route 192.168.12.0 255.255.255.0 172.65.3.1 150
One reason to configure the routes this way could be to make the static route a backup route to the route learned by RIP, such as when the static route is a less desirable route through a distant office.
Once the ip route command has been used to add either a static route or a static default route to a router, the routes should appear in the routing table. They will be indicated with an S next to a static route and an S* for a default static route. The first two examples from the explanation above would appear in the routing table as follows:
S*0.0.0.0/0 [1/0] via 172.16.0.254 S 192.168.12.0/24 [1/0] via 172.65.3.1
The ip default-route, default-gateway, and ip route default commands are incorrect because they are not valid Cisco IOS commands.
Objective:
Routing Fundamentals
Sub-Objective:
Configure, verify, and troubleshoot IPv4 and IPv6 static routing -
Which of the following statements is true with regard to SDN?
- It combines the control plane and the data plane
- It separates the data plane and the forwarding plan
- It implements the control plane as software
- It implements the data plane as software
Explanation:
In Software-defined networking (SDN), the control plane is separated from the data (or forwarding) plane and is implemented through software. The data plane remains on each physical device but the control plane is managed centrally for all devices though software. SDN does not combine the data and control plane. Instead it decouples them.SDN does not separate the data plane and the forwarding plan. These are both names for the same plane; that is, a data plane is a forwarding plane.
SDN does not implement the data plane as software. The data plane remains on each physical device.
Objective:
Infrastructure Management
Sub-Objective:
Describe network programmability in enterprise network architecture -
Which Cisco Internetwork Operating System (IOS) command is used to save the running configuration to non-volatile random access memory (NVRAM)?
- copy startup-config running-config
- move startup-config running-config
- copy running-config startup-config
- move startup-config running-config
Explanation:
The copy running-config startup-config command is used to save the running configuration to NVRAM. This command will should always been run after making changes to the configuration. Failure to do so will result in the changes being discarded at the next restart of the router. When the router is restarted, the startup configuration file is copied to RAM and becomes the running configuration. The copy startup-config running-config command is incorrect because this command is used to copy the startup configuration to the running configuration. The command would be used to discard changes to the configuration without restarting the router.The move startup-config running-config and move startup-config running-config commands are incorrect because these are not valid Cisco IOS commands. There is no move command when discussing the manipulation of configuration files.
Objective:
Infrastructure Management
Sub-Objective:
Perform device maintenance -
DRAG DROP
Click and drag the features on the left to their corresponding frame tagging method on the right.

200-301 Part 07 Q16 071 Question 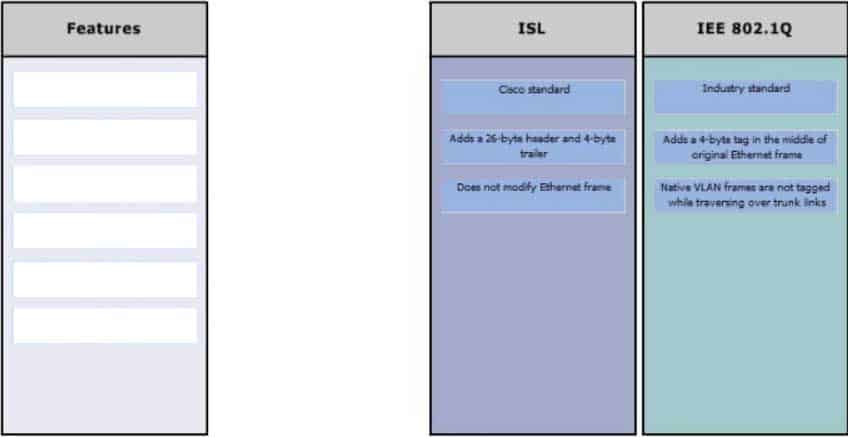
200-301 Part 07 Q16 071 Answer Explanation:
ISL and IEEE 802.1Q are VLAN frame tagging methods.
ISL:
– Is Cisco proprietary
– Adds a 26-byte header and 4-byte trailer
– Does not modify Ethernet frameIEEE 802.1Q frame tagging method:
– Is a standard method
– Adds a 4-byte tag in the middle of original Ethernet frame
– Has a concept called native VLAN. Native VLAN frames are not tagged while traversing over a trunk link.Objective:
LAN Switching Fundamentals
Sub-Objective:
Configure, verify, and troubleshoot interswitch connectivity -
Which option lists the given applications in the correct sequence of increasing bandwidth consumption?
- an interactive Telnet session on a server running an SAP application
a voice conversation between PC-based VoIP services
a voice conversation between two IP phones while accessing an online video site - a voice conversation between two IP phones while accessing an online video site
an interactive Telnet session on a server running an SAP application
a voice conversation between PC-based VoIP services - a voice conversation between PC-based VoIP services
a voice conversation between two IP phones while accessing an online video site
an interactive Telnet session on a server running an SAP application - an interactive Telnet session on a server running an SAP application
a voice conversation between two IP phones while accessing an online video site
a voice conversation between PC-based VoIP services
Explanation:
The correct sequence of increasing bandwidth consumption in the given scenario would be, from lowest to highest:
1. an interactive Telnet session on a server running an SAP application
2. a voice conversation between PC-based VoIP services
3. a voice conversation between two IP phones while accessing an online video siteAn interactive Telnet session uses the least amount of bandwidth of the three application examples because it mainly involves the transfer of text.A voice conversation between IP phones, also known as voice over IP (VoIP) traffic, requires more bandwidth than Telnet. Voice traffic is delay-sensitive and benefits from Quality of Service (QoS) to ensure service quality.
A voice conversation between two IP phones while accessing an online video site would consume the most bandwidth. A voice conversation with real-time video exchange is the equivalent of real-time video traffic. Video traffic is real-time and benefits from dedicated bandwidth with QoS implementation to ensure quality.
Objective:
WAN Technologies
Sub-Objective:
Describe basic QoS concepts - an interactive Telnet session on a server running an SAP application
-
Consider the following output of the show ip interface brief command:

200-301 Part 07 Q18 072 You have a single area OSPF network. What command should you execute on R1 so that OSPF is operational on the E0, S1, and S2 interfaces ONLY?
-
R1(config-router)#network 192.168.12.64 0.0.0.127 area 0
-
R1(config-router)#network 192.168.12.64 0.0.0.63 area 0 -
R1(config-router)#network 192.168.12.64 0.0.0.66 area 0
-
R1(config-router)#network 192.168.12.64 255.255.255.192 area 0
-
R1(config-router)#network 192.168.12.64 0.0.0.63 area1
Explanation:
The command R1(config-router)#network 192.168.12.64 0.0.0.63 area 0 would ensure that OSPF is operational on the E0, S1, and S2 interfaces only. When executing the network command in OSPF, a wildcard mask in combination with the network ID used in the command determines which interfaces will participate in OSPF. Any interfaces that are included in the network created by the network ID and the mask will participate in OSPF. Wildcard masks in OSPF network statements are expressed inversely, and not as a regular subnet masks. For example, if the network you are configuring for OSPF operation is 192.168.10.0/24, then the inverse version of a /24 mask (or 255.255.255.0) would be 0.0.0.255.The network ID is the starting point and the wildcard mask specifies where the network will end or the range of the network. In this case, the network begins at 192.168.12.64. The value in the last octet of the mask indicates the number of values (including 64) that will be included in the network, which means that it will range from 192.168.12.64 – 192.168.12.127. 64 to 127 equals 64 values if you include the endpoints 64 and 127.
The network, and therefore the operation of OSPF, includes the interfaces E0 (192.168.12.65), S1 (192.168.12.125), and S2 (192.168.12.121) because these three IP addresses lie within the range 192.1268.12.64 – 192.168.12.127.
The command R1(config-router)#network 192.168.12.64 0.0.0.127 area 0 is incorrect because the resulting network would range from 192.168.12.64 – 192.168.12.191. This would include all of the required interfaces, but would also include E1 (192.168.12.129) and S0 (192.18.12.187), which is not desired.
The command R1(config-router)#network 192.168.12.64 0.0.0.66 area 0 is incorrect because the resulting network would range from 192.168.12.64 – 192.168.12.129. This would include all of the required interfaces, but would also include E1 (192.168.12.129).
The command R1(config-router)#network 192.168.12.64 255.255.255.192 area 0 is incorrect because the mask, while correct in its breadth and the exact inverse of the wild card mask 0.0.0.63, is not stated in wildcard mask format.
The command R1(config-router)#network 192.168.12.64 0.0.0.63 area 1 is incorrect because it specifies area 1. At least one area of an OSPF network must be area 0 and since this is a single area OSPF network, the command must specify area 0.
Objective:
Routing Fundamentals
Sub-Objective:
Configure, verify, and troubleshoot single area and multi-area OSPFv2 for IPv4 (excluding authentication, filtering, manual summarization, redistribution, stub, virtual-link, and LSAs) -
-
Which command would be used to establish static translation between an inside local address 192.168.144.25 and an inside global address 202.56.63.102?
- router(config)#ip nat inside source static 192.168.144.25 202.56.63.102
- router(config)#ip source nat inside static local-ip 192.168.144.25 global-ip 202.56.63.102
- router(config)#ip nat static inside source 192.168.144.25 202.56.63.102
- router(config)#ip nat inside static source 192.168.144.25 202.56.63.102
Explanation:
To establish a static translation between an inside local address 192.168.144.25 and an inside global address 202.56.63.102, you would use the ip nat inside source static 192.168.144.25 202.56.63.102 command executed in global configuration mode. The correct format of the command is:ip nat inside source static local-ip global-ipThis static configuration can be removed by entering the global no ip nat inside source static command.
Simply executing the ip nat inside source command will not result in NAT functioning. The NAT process also has to be applied correctly to the inside and outside interfaces. For example if, in this scenario the Fa0/0 interface hosted the LAN and the S0/0 interface connected to the Internet the following commands would complete the configuration of static NAT.
Router(config)#interface F0/0 Router(config-if)#ip nat inside Router(config-if)#exit Router(config)#interface S0/0 Router(config-if)#ip nat outside
The other options are incorrect because they are not valid Cisco IOS configuration commands. They all contain syntax errors.
Objective:
Infrastructure Services
Sub-Objective:
Configure, verify, and troubleshoot inside source NAT -
How many IP addresses can be assigned to hosts in subnet 192.168.12.64/26?
- 32
- 62
- 128
- 256
Explanation:
Subnet 192.168.12.64/26 has 62 IP addresses that can be assigned to hosts. The formula to calculate the available number of hosts is:2n – 2 = x
Where n = the number of host bits in the subnet mask and x = the number of possible hosts.
You will subtract 2 from the hosts calculation to remove the first address (the network ID) and the last address (the broadcast ID) from the valid hosts range. These addresses are reserved as the network ID and the broadcast address, respectively, in each subnet.
An IP address has 32 available bits divided into four octets. In this scenario, the /26 indicates that the subnet mask is 26 bits long, or that 26 bits are reserved for the network portion of the address. This leaves 6 bits for the host addresses (32 – 26 = 6). The number of host addresses would be calculated as follows:
Number of hosts = 26 – 2
Number of hosts = 64 – 2 = 62Another simple way of determining the number of hosts in a range, when the subnet mask extends into the last octet, is to determine the decimal value of the last bit in the subnet mask after converting it to binary notation. This process only works when the subnet extends into the last octet, meaning that the subnet is greater than /24. The /26 subnet mask equals 26 network bits and 6 hosts bits, written as follows:
11111111.11111111.1111111.11000000
The 1s represent network bits and the 0s represent host bits.
In this example, the 26th bit (read from left to right) has a decimal value of 64, indicating that this subnet has 64 addresses. Subtract 2 to represent the network and broadcast addresses (64 – 2 = 62). This shows that this subnet range can be used to address 62 hosts.
Network address: 192.168.12.0
Subnet Mask in decimal: 255.255.255.192
Subnet Mask in binary: 11111111.11111111.11111111.11000000
Hosts: 64 – 2 = 62For subnet 192.168.12.64, the valid host range will start from 192.168.12.65 to 192.168.12.126. For the next subnet 192.168.12.128, the valid host range will start from 192.168.12.129 to 192.168.12.190.
To construct a subnet that would contain 32 addresses would require using a mask of 255.255.255.224. This mask would leave 5 host bits, and 25 – 2 = 32.
To construct a subnet that would contain 128 addresses would require using a mask of 255.255.255.128. This mask would leave 7 host bits, and 27 – 2 = 128.
To construct a subnet that would contain 256 addresses would require using a mask of 255.255.255.0. This mask would leave 8 host bits, and 2(8) – 2 = 256.
Objective:
Network Fundamentals
Sub-Objective:
Configure, verify, and troubleshoot IPv4 addressing and subnetting