200-301 : Cisco Certified Network Associate (CCNA) : Part 09
-
Which command is used to view the entire routing table?
- show route-map
- show ip mroute
- show ip route
- show ip protocols
Explanation:
The show ip route command is used to view the entire routing table. The output of this command consists of codes, gateway of last resort, directly connected networks, and routes learned through different protocols working on the network. The syntax of the show ip route command is as follows:show ip route [address [mask] [longer-prefixes]] | [protocol [process-id]]
The parameters of the show ip route command are as follows:
– address: Specifies the address for which the routing information should be displayed.
– mask: Specifies the subnet mask.
– longer-prefixes: Specifies the combination of mask and address.
– protocol: Specifies the name of the routing protocols such as Routing Information Protocol (RIP), or Open Shortest Path First (OSPF).
– protocol-id: Specifies the protocol ID used to identify a process of a particular protocol.The show route-map command is incorrect because this command is used to view the route-maps configured on the router.
The show ip mroute command is incorrect because this command is used to view the contents of the IP multicast routing table.
The show ip protocols command is incorrect because this command is used to view the routing protocols parameters, and the current timer values.
Objective:
Routing Fundamentals
Sub-Objective:
Interpret the components of routing table -
DRAG DROP
Click and drag the VLAN Trunking Protocol (VTP) mode descriptions on the left to their corresponding VTP modes on the right. (The descriptions on the left can be used more than once.)

200-301 Part 09 Q02 084 Question 
200-301 Part 09 Q02 084 Answer Explanation:
VTP server mode is the default VTP mode.VTP is a proprietary Cisco protocol used to share VLAN configuration information between Cisco switches on trunk connections. VTP allows switches to share and synchronize their VLAN information, which ensures that your network has a consistent VLAN configuration.
In VTP server mode:
– Switch can create, modify, or delete VLANs.
– Switches send/forward advertisements.
– Switches synchronize VTP information.
– VLAN information is saved in Non-Volatile RAM (NVRAM).In VTP Client mode:
– Switches forward advertisements.
– Switches synchronize VTP information.
– VLAN information is not saved in NVRAM.In VTP Transparent mode:
– Switch can create, modify, or delete VLANs.
– Switches forward advertisements.
– Does not synchronize VTP information.
– VLAN information is saved in NVRAM.Objective:
Routing Fundamentals
Sub-Objective:
Configure, verify, and troubleshoot inter-VLAN routing -
The conference room has a switch port available for use by the presenter during classes. Each presenter uses the same PC attached to the port. You would like to prevent any other PCs from using that port. You have completely removed the former configuration in order to start anew.
Which of the following steps are required to prevent any other PCs from using that port?
- make the port a trunk port
- enable port security
- make the port an access port
- assign the MAC address of the PC to the port
- make the port a sticky port
- set the maximum number of MAC addresses on the port to 1
Explanation:
You should create the port as an access port, enable port security, and statically assign the MAC address of the PC to the port. Creating the port as an access port ensures that the PC can use the port and port security can be enabled on the port. The second step is to enable port security, which is required to use the third command. The third command sets the MAC address of the PC as the statically assigned address on that port, meaning that only that address can send and receive on the port.You should not make the port a trunk port. There is no need to make this a trunk port because it will not be carrying multiple VLAN traffic, only the traffic of the PC.
You should not make the port a sticky port. The sticky keyword, when used with switchport port-security command, is used to allow a port to dynamically learn the first MAC address it sees in the port, add it to the MAC address table, and save it to the running configuration of the switch. It will not limit the MAC addresses allowed on the port to that of the PC.
You should not set the maximum number of MAC addresses on the port to 1. That would prevent the attachment of a hub or switch to the port, but would not restrict the MAC addresses allowed on the port to the MAC address of the PC.
Objective:
Infrastructure Security
Sub-Objective:
Configure, verify, and troubleshoot port security -
You are configuring Open Shortest Path First (OSPF) protocol for IPv6 on Router5. The router has two interfaces, which have been configured as follows:
S0/0 - 192.168.5.1/24 S0/1 - 10.0.0.6/8
You would like OSPF to route for IPv6 only on the S0/0 network. It should not route for IPv6 on the S0/1 network. The process ID you have chosen to use is 25. You do not want to apply an IPv6 address yet.
Which of the following command sets would enable OSPF for IPv6 as required?
-
Router5(config)#ipv6 ospf 25 Router5(config)# network 192.168.5.0
-
Router5(config)#ipv6 ospf 25 Router5(config)#router-id 192.168.5.1
-
Router5(config)#ipv6 unicast-routing Router5(config)#ipv6 router ospf 25 Router5(config-rtr)#router-id 1.1.1.1 Router5(config)#interface S0/0 Router5(config-if)#ipv6 ospf 25 area 0 -
Router5(config)#ipv6 unicast-routing Router5(config)#ipv6 ospf 25 Router5(config-rtr)#router-id 1.1.1.1
Explanation:
The correct command sequence would be as follows:Router5(config)# ipv6 unicast-routing Router5(config)# ipv6 router ospf 25 Router5(config-rtr)# router-id 1.1.1.1 Router5(config)# interface S0/0 Router5(config-if)# ipv6 ospf 25 area 0
The first line enables IPv6 routing with the ipv6 unicast-routing command. The second line enables OSPF routing for IPv6 with the ipv6 router ospf command. The third assigns a necessary router ID (which was chosen at random) with the router-id command. The last two lines enable OSPF for area 0 on the proper interface.
The following command set is incorrect because it does not enable OSPF routing for IPv6, assign a necessary router ID, or enable OSPF for area 0 on the proper interface:
Router5(config)# ipv6 ospf 25 Router5(config)# network 192.168.5.0
This command set also displays incorrect use of the network command. The network command would be used with OSPF v2.
The following command set fails to enable OSPF routing for IPv6, assign a necessary router ID, or enable OSPF for area 0 on the proper interface:
Router5(config)# ipv6 ospf 25 Router5(config)# router-id 192.168.5.1
It also assigns the router ID under global configuration mode, rather than under router ospf 25 configuration mode as required.
The following command set fails to enable OSPF for area 0 on the proper interface:
Router5(config)# ipv6 unicast-routing Router5(config)# ipv6 ospf 25 Router5(config-rtr)# router-id 1.1.1.1
Objective:
Routing Fundamentals
Sub-Objective:
Configure, verify, and troubleshoot single area and multi-area OSPFv3 for IPv6 (excluding authentication, filtering, manual summarization, redistribution, stub, virtual-link, and LSAs) -
-
What is the significance of the following BECN packet statistics?

200-301 Part 09 Q05 085 - The router is experiencing congestion in sending frames.
- The router is experiencing congestion in receiving frames.
- The Frame Relay mapping table is missing an entry.
- The Frame Relay mapping table is corrupt.
Explanation:
When frames arrived at a router with the Backwards Explicit Congestion Notification (BECN) bit set, congestion was encountered in the opposite direction from which the frame was traveling. This bit is set by the Frame Relay switch. If an incoming packet has the BECN bit set, then this indicates congestion in outgoing packets, so the router will experience congestion in sending frames.When a Frame Relay switch encounters congestion, it will mark packets being sent in both directions on a PVC with either the Forward Explicit Congestion Notification (FECN) or the BECN bit set. It will set the BECN bit on packets headed in the opposite direction of the congestion and FECN in the same direction as the congestion. When a packet with the FECN bit is received by a router, it means there will be congestion when the receiving router receives packets.
A third type of marking is the Discard Eligibility (DE) bit. When this bit is set on a packet, it ensures that if congestion occurs and packets need to be discarded, the packet with the DE bit set should be discarded first. ALL packets in excess of the committed information rate (CIR) are marked with the DE bit.
Frame Relay mapping tables have nothing to do with congestion in the Frame Relay network.
Objective:
WAN Technologies
Sub-Objective:
Describe basic QoS concepts -
In the following partial output of the show ip route command, what does the letter D stand for?
D 192.1.2.0/24 via 5.1.1.71 [w:0 m:0] C 192.8.1.1/32 directly connected to loopback 0
- This is a default route
- This is an EIGRP route
- This is static route
- This is a directly connected route
Explanation:
The letter D indicates that it was a route learned by the EIGRP routing protocol. In the output of the show ip route command, each route will have a letter next to it that indicates the method by which the route was learned. At the beginning of the output will be a legend describing the letters as shown below:

200-301 Part 09 Q06 086 The letter does not indicate that it is a default route. The default route (if configured) will appear at the end of the legend as follows:
Gateway of last resort is 10.119.254.240 to network 10.140.0.0
The letter does not indicate that it is a static route. Static routes will have an “S” next to them.
The letter does not indicate that it is a directly connected route. Directly connected routes will have a “C” next to them.
Objective:
Routing Fundamentals
Sub-Objective:
Interpret the components of routing table -
Which command would you use to see which switch interface is associated with a particular MAC address?
- show interface mac
- show mac
- show mac-address-table
- show ip interface
Explanation:
The show mac-address-table command displays a table of every learned MAC address, and the switch port associated with the MAC address. Sample output is as follows:
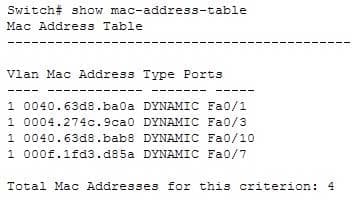
200-301 Part 09 Q07 087 This output indicates that four MAC addresses have been learned by this switch, and the last column indicates the switch port over which each MAC address was learned, and for which frames destined for each MAC address will be forwarded. The MAC address table is built dynamically by examining the source MAC address of received frames. If the switch receives a MAC address not listed in this table, it will send the frame out all ports except the one from which it was originated.
The show ip interface command is a router command, and displays no information on MAC address tables.
The show interface mac and show mac commands are incorrect because they are not valid Cisco IOS commands.
Objective:
LAN Switching Fundamentals
Sub-Objective:
Describe and verify switching concepts -
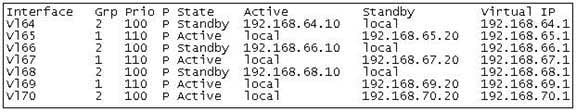
What command would provide the output displayed in the exhibit? (Click on the Exhibit(s) button.)
200-301 Part 09 Q08 088 -
switch# show hsrp
-
switch# show standby
-
switch# show interface vlan
-
switch# show standby brief
Explanation:
The command show standby brief displays the output in the exhibit. It is used to display a summary of the HSRP groups of which the switch is a member. The summary information it provides includes the group number, priority, state, active device address, standby address, and group address. In the exhibit, the interface VLAN 64 is a member of HSRP group 2. Its priority in the group is 100 and it is currently the standby switch. Since preemption is configured (as indicated by the P following the priority), we know that the priority of this switch must be lower than the priority of the active device. The active device has an IP address of 192.168.64.10 and the group IP address is 192.168.64.1.The command show standby can be used to display detailed information about HSRP groups of which a switch is a member. It does not provide the quick summary display of the exhibit. This command displays information about HSRP on all configured interfaces and for all HSRP groups. It also displays hello timer information and the expiration timer for the standby switch. The command syntax is show standby [type number [group]].
Below is an example of this command’s output:
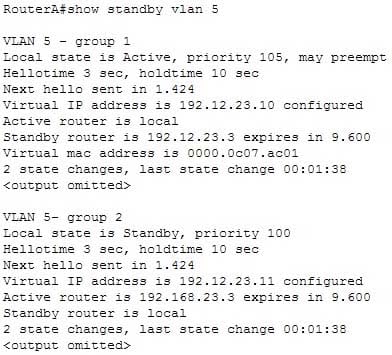
200-301 Part 09 Q08 089 In the above output, Router A is load-sharing traffic for VLAN 5. It is active for group 1 and standby for group 2. The router at address 192.168.23.3 is active for group 2 and standby for group 1. This allows traffic to be sent to both routers while still allowing for redundancy. Router A was also configured with the standby 1 preempt command (results seen in line 1), which allows it to resume its role as active for group 1 if it comes back up from an outage.
The command show interface vlan is not a complete command. A VLAN number must follow the command. When provided with a VLAN number, the output would display the status of the SVI, but no HSRP information.
The command show hsrp is not a valid command due to incorrect syntax.
Objective:
Infrastructure Services
Sub-Objective:
Configure, verify, and troubleshoot basic HSRP -
-
Which of the following fields are in a Transmission Control Protocol (TCP) header? (Choose three.)
- Length
- Sequence Number
- Data Offset
- Type-of-Service
- Window
Explanation:
– Sequence Number, Data Offset, and Window are the fields found in a TCP header. TCP hosts create a connection-oriented session with one another. The following are the fields found in a TCP header:
– Sequence Number: Refers to the first byte of data in the current message. This field helps TCP to reassemble the packets in the correct order. For example, when data is transferred between an FTP server and FTP client, the receiver uses this field to reassemble the packets into the original file.
– Data Offset: Refers to the number of 32-bit words in the TCP header.
– Window: Refers to the size of the available space for the incoming data.
– Source Port and Destination Port: Refer to the point where upper-layer source and destination processes receive TCP services. Both TCP and UDP packets contain these fields.
– Acknowledgment Number: Refers to the sequence number of the next byte of data which the sender will receive.
– Reserved: Reserved for future use.
– Flags: Contains control information, such as the SYN and ACK bits which are used to establish and acknowledge communication, and the FIN bit which is used to terminate the connection.
– Checksum: An indicator of any damage to the header while being in transit. Both TCP and UDP packets contain this field.
– Urgent Pointer: Refers to the first urgent data byte in the packet.
– Options: Used to specify TCP options. Only TCP packets contain this field.
– Data: Has upper-layer information.TCP is used for unicast transmissions and provides connection -oriented services for upper layer protocols. It will establish a state of connection between two devices before any data is transferred; for example, before a workstation can exchange HTTP packets with Web server, a TCP connection must be established between the workstation and the Web server.
The Length field is found in a User Datagram Protocol (UDP) header, where it specifies the length of the UDP header and data. UDP headers contain the Source Port, Destination Port, Length, and Checksum fields.
Sequence number, acknowledgment number, and windows size are fields not found in a UDP header because UDP provides none of the services that require use of these fields. That is, UDP cannot re-sequence packets that arrive out of order, nor does UDP acknowledge receipt (thus the term non-guaranteed to describe UDP). Furthermore, since UDP does not acknowledge packets, there is no need to manage the window size, which refers to the number of packets that can be received without an acknowledgment.
The Type-of-Service field is found in an Internet Protocol (IP) header, where it specifies the handling of a current datagram by an upper-layer protocol.
Objective:
Network Fundamentals
Sub-Objective:
Compare and contrast TCP and UDP protocols -
Which Cisco IOS command disables Cisco Discovery Protocol Version 2 (CDPv2) advertisements?
- no cdp advertise-v2
- no cdp v2-advertise
- no cdp run
- no cdp enable
Explanation:
The no cdp advertise-v2 command disables CDPv2 advertisements. It is the reverse of the cdp advertise-v2 command, which enables CDPv2 advertisements on a device.The no cdp v2-advertise command is not a valid Cisco IOS command.
The no cdp run command disables CDP, not CDPv2 advertisements.
The no cdp enable command disables CDP on an interface.
Objective:
LAN Switching Fundamentals
Sub-Objective:
Configure and verify Layer 2 protocols -
Which of the following statements are TRUE regarding EIGRP operation? (Choose two.)
- A successor is a backup route, and is installed in both the routing and topology tables.
- A successor is a primary route, and is installed in both the routing and topology tables.
- A successor is a primary route, and is installed only in the routing table.
- A feasible successor is a backup route, and is installed in both the routing and topology tables.
- A feasible successor is a primary route, and is only installed in the routing table.
- A feasible successor is a backup route, and is only installed in the topology table.
- If the successor route fails and no feasible successor route exists, the router will send an update with the route marked with an unreachable metric of 16.
Explanation:
In EIGRP operations, primary or active routes are known as successors. These routes are maintained in both the routing and topology tables. The routing table is the list of network paths that are currently used by the router.EIGRP also has the ability to maintain backup routes to destination networks. These backup routes are known as feasible successors. If a feasible successor is discovered by EIGRP, it will be maintained only in the topology table, since it is not currently being used to route traffic. In the event of a successor failure, the backup feasible successor will become the successor, and will be installed in the routing table automatically. If the successor route fails and no feasible successor route exists, the router will send queries to all neighbors until a new successor is found.
EIGRP maintains three dynamic tables in RAM:
– Neighbor table, which is a list of all neighboring EIGRP routers on shared subnets
– Topology table, which contains all discovered network paths in the internetwork
– Routing table, which contains the best path (based on lowest metric) to each destination networkA successor is not a backup route. A successor is a primary or active route, and it is stored in both the routing and topology tables.
A feasible successor is not a primary route. It is a backup route, and it is stored only in the topology table.
If the successor route fails and no feasible successor route exists, the router will not send an update with the route marked with an unreachable metric of 16. EIGRP does not send an update with the route marked with an unreachable metric, and even if it did, 16 is not an unreachable metric in EIGRP as it is in RIP. Instead it sends a multicast query packet to all adjacent neighbors requesting available routing paths to the destination network.
Objective:
Routing Fundamentals
Sub-Objective:
Configure, verify, and troubleshoot EIGRP for IPv4 (excluding authentication, filtering, manual summarization, redistribution, stub) -
Which two are NOT valid Cisco IOS commands used for Cisco Discovery Protocol (CDP)? (Choose two.)
- show cdp
- show cdp entry *
- show cdp neighbor entries
- show cdp neighbors detail
- show cdp devices
Explanation:
The show cdp neighbor entries command and the show cdp devices command are not valid Cisco IOS commands.The Cisco IOS commands used for CDP are as follows:
show cdp: This command is used to view global CDP information, such as timer and hold time.
show cdp entry *: This command is used to view information regarding all neighboring devices.
show cdp neighbors detail: This command is used to view the details regarding the neighboring devices which are discovered by the CDP. This command is used to view details such as network address, enabled protocols, and hold time. The complete syntax of this command is:show cdp neighbors [type number] [detail]
Objective:
LAN Switching Fundamentals
Sub-Objective:
Configure and verify Layer 2 protocols -
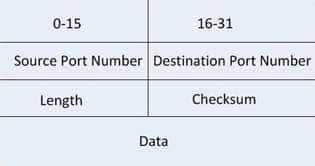
What data structure is pictured in the graphic?
200-301 Part 09 Q13 090 - TCP segment
- UDP datagram
- IP header
- Http header
Explanation:
The data structure pictured in the graphic is an UDP datagram. It uses a header (not shown) that contains the source and destination MAC address. It has very little overhead as compared to the TCP segmented (shown later in this explanation) as any transmission that uses UDP is not provided the services of TCP.It is not a TCP segment, which has much more overhead (shown below). The TCP header contains fields for sequence number, acknowledgment number, and windows size, fields not found in a UDP header because UDP provides none of the services that require use of these fields. That is, UDP cannot re-sequence packets that arrive out of order, nor does UDP acknowledge receipt (thus the term non-guaranteed to describe UDP). Furthermore, since UDP does not acknowledge packets there is no need to manage the window size (the window size refers to the number of packets that can be received without an acknowledgment.

200-301 Part 09 Q13 091 It is not an IP header. An IP header contains fields for the source and destination IP address. The IP header, like the UDP segment, does not contain fields for sequence number, acknowledgment number, and windows size, fields not found in a TCP header because TCP provides none of the services that require use of these fields. IP provides best-effort user data. This does not cause a delivery problem, however, as IP relies on TCP to provide those services when the transmission is a unicast.
An HTTP header does not include fields for HTTP requests and responses.
Objective:
Network Fundamentals
Sub-Objective:
Compare and contrast TCP and UDP protocols -
Which of the following excerpts from the output of the show ip eigrp topology command include EIGRP learned routes or pairs of routes that will be included in the routing table? (For excerpts that include multiple routes, do not include the entry unless BOTH routes will be included in the routing table.)
- P 172.16.16.0/24, 1 successors, FD is 284244
via 172.16.250.2 (284244/17669856), Serial0/0
via 172.16.251.2 (12738176/27819002), Serial0/1 - P 172.16.250.0/24, 1 successors, FD is 2248564
via Connected, Serial0/0 - P 172.16.10.0/24 2 successors, FD is 284244
via 172.16.50.1 (284244/17669856), Serial1/0
via 172.16.60.1 (284244/17669856), Serial1/1 - P 172.16.60.0/24, 1 successors, FD is 2248564
via Connected, Serial1/1
Explanation:
The following excerpt indicates two successor routes, and they will both be included:P 172.16.10.0/24 2 successors, FD is 284244
via 172.16.50.1 (284244/17669856), Serial1/0
via 172.16.60.1 (284244/17669856), Serial1/1Both of these routes will be included because they have identical metrics (284244/17669856). Only the EIGRP successor routes will appear in the routing table, as these are considered the best-path routes to each remote network.
The route for 172.16.16.0/24 via 172.16.251.2 (12738176/27819002) will not be included because only successor routes are included, and this route is a feasible successor. Feasible successor routes are routes that are used only as a backup if the successor route(s) becomes unavailable. If you examine the output of each option, it will indicate how many successor routes are in the entry. The entry shows that there is only one successor to this route:
P 172.16.16.0/24, 1 successors, FD is 284244
via 172.16.250.2 (284244/17669856), Serial0/0
via 172.16.251.2 (12738176/27819002), Serial0/1The first listed is the successor and the second is the feasible successor. The first has the best or lowest metric (284244/17669856), which is the criterion used for selection.
These entries indicate successor routes, but they also indicate they are via Connected, which means they are networks directly connected to the router.
P 172.16.250.0/24, 1 successors, FD is 2248564
via Connected, Serial0/0and
P 172.16.60.0/24, 1 successors, FD is 2248564
via Connected, Serial1/1Therefore, they are not EIGRP learned routes.
Objective:
Routing Fundamentals
Sub-Objective:
Configure, verify, and troubleshoot EIGRP for IPv4 (excluding authentication, filtering, manual summarization, redistribution, stub) - P 172.16.16.0/24, 1 successors, FD is 284244
-
Which of the following statements is TRUE about trunk ports?
- A trunk port connects an end-user workstation to a switch.
- A trunk port uses 802.1q to identify traffic from different VLANs.
- A trunk port supports a single VLAN.
- A trunk port uses a straight-through Ethernet cable when connecting two switches.
Explanation:
A switch port can operate as an access port or a trunk port. An access port is used to connect to an end-user device, such as a workstation, server, or printer, while a trunk port is used to connect to neighboring switches or routers. The trunk link is responsible for carrying data between workstations connected to different switches, or a switch and a router configured for inter-VLAN routing. For example, in the diagram below where VLANs are in use on both switches and inter-VLAN routing is configured, the interfaces will operate as follows:
– SW1 – Fa0/1 and Fa0/2 are trunk links, Fa0/0 is an access link
– SW2 – Fa0/0 is trunk link and Fa0/1 is an access link
– RTR – Fa0/2 is a trunk link
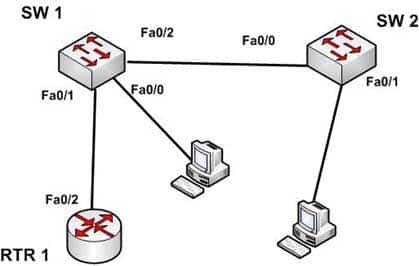
200-301 Part 09 Q15 092 With the exception of frames traveling on the native VLAN, data frames crossing a trunk link must be frame tagged over the link to identify the VLAN that sourced the frame. The receiving switch sees the VLAN ID, and uses this information to forward the frame appropriately. 802.1q and ISL are the two possible frame tagging methods between Cisco switches. In summary, some facts about access and trunk ports:
Access ports:
– Carry traffic for a single VLAN
– Connect end user workstations to the switch
– Use a straight-through cable to connect to the deviceTrunk ports:
– Facilitate inter-VLAN communication when connected to a Layer 3 device
– Carry traffic from multiple VLANs
– Use 802.1q to identify traffic from different VLANsWhen a new trunk link is created on a switch, all VLANs are allowed to use the trunk, by default.
Trunk ports are used between switches and routers, and do not connect to end-user workstations.
Trunk ports support all VLANs known to the switch by default, so that devices in the same VLAN can communicate across multiple switches. Trunk ports are not limited to a single VLAN, as access ports are.
Trunk ports connected between switches using crossover Ethernet cables, not straight-through Ethernet cables. Trunk ports between switches and routers use straight-through cables.
Objective:
LAN Switching Fundamentals
Sub-Objective:
Configure, verify, and troubleshoot interswitch connectivity -
In which two situations would it be appropriate to issue the ipconfig command with the /release and /renew options? (Choose two.)
- When the result of running the ipconfig /all command indicates a 169.254.163.6 address
- When recent scope changes have been made on the DHCP server
- When no IP helper address has been configured on the router between the client and the DHCP server
- When the no ip directed-broadcast command has been issued in the router interface local to the client, and no IP helper address has been configured on the router between the client and the DHCP server
Explanation:
It would it be appropriate to issue the ipconfig command with the /release and /renew options when the result of running the ipconfig /all command indicates a 169.254.163.6 address, or when recent scope changes have been made on the DHCP server. When a computer has an address in the 169.254.0.0 network, it indicates that the computer has not been issued an address from the DHCP server. Instead, the computer has utilized Automatic Private IP Addressing (APIPA) to issue itself an address. If the reason for this assignment is a temporary problem with the DHCP server or some other transitory network problem, issuing the ipconfig /release command followed by the ipconfig /renew command could allow the computer to receive the address from the DHCP sever.Similarly, if changes have been made to the settings on the DHCP server, such as a change in the scope options (such as gateway or DNS server), issuing this pair of commands would update the DHCP client with the new settings when his address is renewed.
These commands will have no effect when no IP helper address has been configured on the router between the client and the DHCP server. An IP helper address can be configured on the local interface of a router when no DHCP server exists on that subnet and you would like to allow the router to forward DHCP DISCOVER packets to the DHCP server on a remote subnet. DHCP DISCOVER packets are broadcast, and routers do not pass on broadcast traffic by default.
These commands also will be of no benefit if the no ip directed-broadcast command has been issued in the router interface local to the client and no IP helper address has been configured on the router between the client and the DHCP server. The no ip directed-broadcast command instructs the router to deny broadcast traffic (which is the default). Under those conditions, the command will not result in finding the DHCP server or receiving an address.
Objective:
Infrastructure Services
Sub-Objective:
Troubleshoot client- and router-based DHCP connectivity issues -
Which of the following characteristics are NOT shared by RIPv1 and RIPv2?
- They share an administrative distance value
- They use the same metric
- They both send the subnet mask in routing updates
- They have the same maximum hop count
Explanation:
RIPv1 and RIPv2 do NOT both send the subnet mask in routing updates. RIPv1 is classful, while RIPv2 is classless. This means the RIPv1 does not send subnet mask information in routing updates, while RIPv2 does.Both versions have the same administrative distance of 120.
Both versions have the same metric, which is hop count.
Both versions have the same maximum hop count, which is 15.
Objective:
Routing Fundamentals
Sub-Objective:
Configure, verify, and troubleshoot RIPv2 for IPv4 (excluding authentication, filtering, manual summarization, redistribution) -
Which Enhanced Interior Gateway Routing Protocol (EIGRP) packet is NOT sent reliably over the network?
- Update
- Query
- Reply
- Acknowledgement
Explanation:
Acknowledgement packets are sent unreliably over the network, and there is no guaranteed delivery of acknowledgement packets between neighboring routers.Acknowledgement packets are a special type of hello packets that do not contain data and have a non-zero acknowledgement number. These are sent as a unicast.
Update, Query, and Reply packets use Reliable Transport Protocol (RTP), which ensures guaranteed delivery of packets between neighboring devices. The RTP mechanism ensures loop-free synchronized network.
Objective:
Routing Fundamentals
Sub-Objective:
Configure, verify, and troubleshoot EIGRP for IPv4 (excluding authentication, filtering, manual summarization, redistribution, stub) -
You recently implemented SNMPv3 to increase the security of your network management system. A partial output of the show run command displays the following output that relates to SNMP:
<output omitted> snmp-server group TECHS v3 noauth read TECHS write TECHS
Which of the following statements is true of this configuration?
- It provides encryption, but it does not provide authentication
- It provides neither authentication nor encryption
- It provides authentication, but it does not provide encryption
- It provides both authentication and encryption
Explanation:
It provides neither authentication nor encryption. In SMNPv3, there are three combinations of security that can be used:
– noAuthNoPriv- no authentication and no encryption; includes the noauth keyword in the configuration
– AuthNoPriv – messages are authenticated but not encrypted; includes the auth keyword in the configuration
– AuthPriv – messages are authenticated and encrypted; includes the priv keyword in the configurationIn this case, the keyword noauth in the configuration indicates that no authentication and no encryption are provided. This makes the implementation no more secure than SNMPv1 or SNMPv2.
In SNMPv1 and SNMPv2, authentication is performed using a community string. When you implement SNMP using the noauth keyword, it does not use community strings for authentication. Instead it uses the configured user or group name (in this case TECHS). Regardless, it does not provide either authentication or encryption.
Objective:
Infrastructure Management
Sub-Objective:
Configure and verify device-monitoring protocols -
You are the network administrator for your company. You want to upgrade the network, which is currently running on IPv4, to a fully functional IPv6 network. During the transition, you want to ensure that hosts capable only of IPv6 can communicate with hosts capable only of IPv4 on the network.
Which solution should you implement to accomplish the task in this scenario?
- IPv6 over IPv4 tunnels
- IPv6 over dedicated Wide Area Network (WAN) links
- Dual-Stack Backbones
- Protocol translation
Explanation:
The protocol translation deployment model should be used to accomplish the task in this scenario. It is the only offered solution that does not require at least one end of the communication solution to support both IPv6 and IPv4.The following deployment models are available for IPv4 to IPv6 migration:
– IPv6 over IPv4 tunnels: IPv6 traffic is encapsulated into IPv4 packets. Then these packets are transferred over IPv4 WAN. This model eliminates the need to create separate circuits to connect to the IPv6 networks. This model increases protocol overhead because of the IPv6 headers and requires the edge router at each end be capable of both protocols.
– Protocol translation: A method allowing an IPv6 host to communicate with an IPv4 host. This is accomplished with the help of Network Address Translation – Protocol Translation (NAT-PT) used to configure translation between IPv6 and IPv4 hosts. NAT-PT allows communication between IPv6 hosts and applications, and native IPv4 hosts and applications.
– IPv6 over dedicated WAN links: A new deployment of IPv6 is created. In this model, IPv6 hierarchy, addressing, and protocols are used by all nodes. However, this model involves cost for creating IPv6 WAN circuits. This solution is not designed for LAN translation but rather communication over WAN links.
– Dual-Stack Backbones: A hybrid model in which backbone routers have dual-stack functionality, which enables them to route both IPv4 and IPv6 packets. It is suitable for an enterprise that uses both IPv4 and IPv6 applications. Running IPv6 and IPv4 together in a network is known as dual-stack routing.Objective:
Network Fundamentals
Sub-Objective:
Identify the appropriate IPv6 addressing scheme to satisfy addressing requirements in a LAN/WAN environment