200-301 : Cisco Certified Network Associate (CCNA) : Part 21
-
Which of the following statements are true when discussing link state and distance vector routing protocols? (Choose all that apply.)
- After convergence, routing advertisements are only triggered by changes in the network with distance vector protocols
- Packets are routed based upon the shortest path calculated by an algorithm with link state protocols
- Only one router in an OSPF area can represent the entire topology of the network
- Distance vector protocols send the entire routing table to a neighbor
- Distance vector protocols send updates regarding the status of their own links to all routers in the network
- Link-state protocols place a high demand on router resources running the link-state algorithm
- Distance vector protocols require a hierarchical IP addressing scheme for optimal functionality
- Link-state protocols use hello packets and LSAs from other routers to build and maintain the topological database
- Link-state protocols require a hierarchical IP addressing scheme for optimal functionality.
Explanation:
The following statements are true of link-state and distance vector routing protocols:
– Packets are routed based upon the shortest path calculated by an algorithm with link state protocols.
– Distance vector protocols send the entire routing table to a neighbor.
– Link-state protocols place a high demand on router resources running the link-state algorithm.
– Link-state protocols use hello packets and LSAs from other routers to build and maintain the topological database.
– Link-state protocols require a hierarchical IP addressing scheme for optimal functionality.Link state protocols like OSPF use the Shortest Path First algorithm to calculate the shortest path based on a metric called cost, while distance vector protocols like RIP consider only hop count when determining the best route. Running the algorithm places a high demand on router resources. Distance vector protocols are required to send the entire routing table with each update, while link state protocols only send updates when required by changes in the network. Therefore, less traffic is created with link state protocols.
Sending routing advertisements after convergence only when changes occur in the network is a characteristic of link state protocol’s not distance vector protocols. With distance vector protocols, updates occur regularly and include the entire routing table.
All routers in an OSPF area can represent the entire topology of the network, not just one.
Distance vector protocols do not send updates regarding the status of their own links to all routers in the network. Updating link status is a characteristic of link state protocols. Distance vector protocols send the entire routing table.
Distance vector protocols do NOT require a hierarchical IP addressing scheme for optimal functionality. Link-state protocols do require this for optimal functionality, as it supports more efficient route aggregation or summarization. This reduces the number of routes in the table and the number of calculations required by the SPF algorithm, thereby lowering router resource demand.
Objective:
Routing Fundamentals
Sub-Objective:
Compare and contrast distance vector and link-state routing protocols -
In the given exhibit, which combination shows the components of a bridge ID used for Spanning Tree Protocol (STP)?

200-301 Part 21 Q02 186 - 1
- 2
- 3
- 4
Explanation:
The bridge ID, also known as the switch ID, is used to elect the root bridge in a redundant network topology. The bridge ID has two components:
– Switch’s priority number: Configured as 32768 on Cisco switches by default
– Switch’s Media Access Control (MAC) address: The burnt-in hardware address of the network interface card (NIC)The switch with the lowest bridge ID is elected as the root bridge. If the same priority number is configured on two or more switches in the network, the switch with the lowest MAC address will become the root.
Bridge Protocol Data Units (BPDUs) communicate the details of the switch with the lowest bridge ID in the network. The election process for the root bridge takes place every time there is a topology change in the network. A topology change may occur due to the failure of a root bridge or the addition of a new switch in the network. The root bridge originates BPDUs every two seconds, which are propagated by other switches throughout the network. BPDUs are used as keepalives between switches. If a switch stops receiving BPDUs from a neighboring switch for ten intervals (20 seconds), it will assume a designated role for the network segment.
The combinations of the remaining options are incorrect because Virtual LAN (VLAN) numbers and serial numbers are not components of a bridge ID.
Objective:
LAN Switching Fundamentals
Sub-Objective:
Configure, verify, and troubleshoot STP protocols -
Which of the following commands configures an SNMP host to authenticate a user by username and send clear text notifications, the receipt of which will be acknowledged by the receiver?
-
Router(config)# snmp-server host 192.168.5.5 informs version 3 noauth public -
Router(config)# snmp-server host 192.168.5.5 traps version 3 auth public
-
Router(config)# snmp-server host 192.168.5.5 informs version 2c public
-
Router(config)# snmp-server host 192.168.5.5 informs version 3 authpriv public
Explanation:
The command snmp-server host 192.168.5.5 informs version 3 noauth CISCO will configure the host to authenticate a user by username and send clear text notifications. The receiver will then acknowledge receipt of the notification. The keyword informs indicates that an inform message type will be used. Unlike a trap, an inform message is acknowledged by the receiver.The version 3 keyword indicates that version 3 is in use, which is the ONLY version that supports authentication and encryption. Finally, the noauth keyword specifies authentication by username only and no encryption.
The command snmp-server host 192.168.5.5 traps version 3 auth public configures the host to send traps rather than informs.
The command snmp-server host 192.168.5.5 informs version 2c public specifies version 2c, which only support community string-based authentication.
The command snmp-server host 192.168.5.5 informs version 3 authpriv public specifies the keyword authpriv, which indicates encryption will be used and authentication based on HMAC-MD5 or HMAC-SHA algorithms.
Objective:
Infrastructure Management
Sub-Objective:
Configure and verify device-monitoring protocols -
-
What configuration is needed to span a user defined Virtual LAN (VLAN) between two or more switches?
- A VTP domain must be configured.
- VTP pruning should be enabled.
- The VTP mode of operation should be server.
- A trunk connection should be set up between the switches.
Explanation:
To span a user defined VLAN between two or more switches, a trunk connection must be established. Trunk connections can carry frames for multiple VLANs. If the link between switches is not trunked, by default only VLAN 1 information will be switched across the link.A VLAN trunking protocol (VTP) domain is not necessary to span VLANs across multiple switches. VTP is used to have consistent VLAN configuration throughout the domain.
VTP pruning is used to detect whether a trunk connection is carrying unnecessary traffic for VLANs that do not exist on downstream switches. By default, all trunk connections carry traffic from all VLANs in the management domain. However, a switch does not always need a local port configured for each VLAN. In such situations, it is not necessary to flood traffic from VLANs other than the ones supported by that switch. VTP pruning enables switching fabric to prevent flooding traffic on trunk ports that do not need it.
VTP server mode is not required for a server to span multiple switches. In VTP server mode of operation, VLANs can be created, modified, deleted, and other VLAN configuration parameters can be modified for the entire VTP domain. VTP messages are sent over all trunk links, and configuration changes are propagated to all switches in the VTP domain.
Objective:
LAN Switching Fundamentals
Sub-Objective:
Configure, verify, and troubleshoot VLANs (normal/extended range) spanning multiple switches -
Which two are NOT features of Cisco NAT implementation? (Choose two.)
- overload
- override
- overrule
- static NAT
- dynamic NAT
Explanation:
Override and overrule are NOT features of Cisco’s Network Address Translation (NAT) implementation. NAT translates internal IP address to external IP address and vice versa. NAT is typically used by firewalls or routers.The following are some of the characteristics of NAT:
– It can act as an address translator between Internet and the local network.
– It conserves IP addresses and simplifies the process of IP address allocation.
– It allows the local network to connect to Internet using unregistered IP addresses.
– It can present only one address for the entire network to the outside world when using dynamic NAT.
– It enhances network security, as it does not disclose internal network addresses to the outside world.All of the other options are incorrect because they are valid NAT features.
With static NAT, translation mappings are created statically and are placed in the translation tables whether or not there is traffic flowing. In this case, no registered addresses are saved because a registered address is still required for each mapping.
With dynamic NAT, the translation table is populated as the required traffic flows through NAT-enabled devices. In this case, a single address or multiple public addresses can be used multiple times to represent multiple private addresses.
The overload keyword allows the ip nat inside command to translate multiple devices in the internal network to the single address in the IP address pool. This process is also called overloading in that the same public IP address is mapped to all private addresses from inside the network. Since the router performing the NAT overload function will use the unique TCP source port from each host for identification, while mapping all of them to the same public IP address, it is sometimes referred to as Port Address Translation or PAT.
For example:
ip nat pool test 172.28.15.1 172.28.15.1 prefix 24
In this example, the NAT pool named “test” only has a range of one address.
Another variant of this command is given below, which configures NAT to overload on the address assigned to the serial 0 interface:
ip nat inside source list 3 interface serial 0 overload
When this variation is used, the command uses a list named 3 to determine the addresses in the pool.
Objective:
Infrastructure Services
Sub-Objective:
Configure, verify, and troubleshoot inside source NAT -
Which classful protocols perform an automatic summarization of routes when routers send updates across major classful network boundaries? (Choose two.)
- RIPv1
- RIPv2
- IGRP
- OSPF
- EIGRP
- BGPv4
Explanation:
The classful routing protocols Routing Information Protocol version1 (RIPv1) and Interior Gateway Routing Protocol (IGRP) summarize routes at classful network boundaries. RIPv1 is a standard distance vector protocol that uses hop count as a metric. IGRP is a Cisco Systems proprietary distance vector routing protocol that has a composite metric based on bandwidth, delay, load, reliability, and maximum transmission unit (MTU).In classless routing protocols RIPv2, Open Shortest Path First (OSPF), Enhanced IGRP (EIGRP) and Border Gateway Protocol version 4 (BGPv4), route summarization can be controlled manually at any bit position in the IP address. Classless routing protocols transmit subnet mask along with the routes, and therefore manual summarization may be required at times to keep the routing table size in control.
It should be noted that RIPv2 and EIGRP, although classless protocols, will perform automatic summarization by default unless the no auto-summary command is configured. Once no auto-summary is configured, you can manually configure summarization on any bit position in the IP address. Since you can override auto-summarization in both RIPv2 and EIGRP, RIPv1 and IGRP are better answers to this question.
Objective:
Routing Fundamentals
Sub-Objective:
Compare and contrast interior and exterior routing protocols -
A newly implemented IP-based video conferencing application is causing the network to slow down.
Which OSI layer needs to be addressed to resolve the problem?
- Layer 1
- Layer 2
- Layer 3
- Layer 4
- Layer 5
- Layer 6
- Layer 7
Explanation:
You need to address Open System Interconnect (OSI) Layer 1, the Physical layer, to resolve the problem. IP-based video conferencing applications are bandwidth-intensive and may cause the network to slow down unless there is enough bandwidth to ensure proper network operation. To resolve bandwidth problems, you may need to switch to a higher capacity network backbone, which may require a change of cabling or media types, such as fiber optics. Cabling and network media types are defined at OSI Layer 1.The seven layers of the OSI model are as follows, in descending order from Layer 7 to Layer 1:
– Application: Interacts directly with the application. It provides application services, such as e-mail and File Transfer Protocol (FTP).
– Presentation: Enables coding and conversion functions for application layer data. The Presentation layer converts data into a format that is acceptable by the application layer. The formatting and encryption of data is done at this layer.
– Session: Creates, manages, and terminates sessions between communicating nodes. The session layer handles the service requests and responses that take place between different hosts.
– Transport: Delivers data sequentially and without errors. This layer manages data transmission between devices, a process known as flow control. The Transport layer protocols are Transmission Control Protocol (TCP) and User Datagram Protocol (UDP).
– Network: Defines the network address or the Internet Protocol (IP) address, which is then used by the routers to forward the packets.
– Data Link: Ensures the reliable delivery of data to the physical address of the destination.
– include fiber optic, wireless, and Ethernet.Objective:
Network Fundamentals
Sub-Objective:
Apply troubleshooting methodologies to resolve problems -
You have configured a router as shown in the following output:
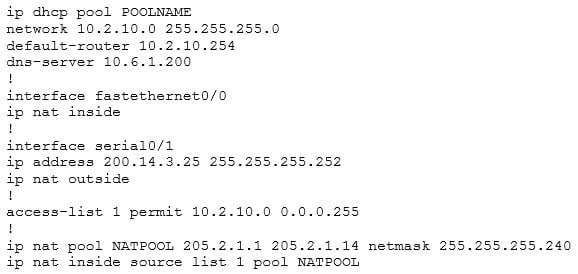
200-301 Part 21 Q08 187 Hosts on the LAN cannot receive an IP address. What is wrong?
- The IP address on the serial interface is incorrect.
- The default-router command in the DHCP pool is incorrect.
- An IP address needs to be configured on the FastEthernet interface.
- The NAT pool is not large enough.
Explanation:
An IP address needs to be configured on the FastEthernet interface. Dynamic Host Control Protocol (DHCP) is used to dynamically provide IP network configurations to workstations as they are booted up. DHCP minimizes network administration overload, allowing devices to be added to the network with little or no manual configuration.The router configuration in the scenario has created a DHCP address pool called POOLNAME. The network statement in the exhibit, network 10.2.10.0 255.255.255.0, identifies the range of IP addresses that the pool will provide to host systems (10.2.10.0 /24). However, a DHCP pool can only provide IP addresses over a subnet to which it is directly connected. Because neither of the interfaces in the exhibit has an IP address on the 10.2.10.0 /24 subnet, the solution is to assign the FastEthernet0/0 interface the IP address specified in the default-router statement, 10.2.10.254 /24.
The IP address on the serial interface has no impact on the DHCP pool.
The default-router statement is correctly providing the IP address that DHCP hosts will use as their default gateway. The problem is not with the default-router statement, but with the lack of a correct IP address assigned to the FastEthernet0/0 interface.
The NAT configuration in the exhibit has no impact on the DHCP pool. If the NAT pool were not large enough, the result would be that some of the hosts would be able to get to the Internet and others would not. For example, the output from the diagram shown below indicates that there are fourteen addresses in the pool (205.2.1.1 to 205.2.1.14). If the network contained 30 computers, only fourteen would be able to use the Internet at the same time because of the number of public addresses in the pool:
ip nat pool NATPOOL 205.2.1.1 205.2.1.14 netmask 255.255.255.240 ip nat inside source list 1 pool NATPOOL
Objective:
Infrastructure Services
Sub-Objective:
Configure and verify DHCP on a router (excluding static reservations) -
Which of the following commands could you use to verify the type of serial cable you are connected to (DCE or DTE)?
- show interfaces
- show controllers
- show ip interface
- show interface dce
- show interface switchport
Explanation:
The show controllers command provides hardware-related information used to troubleshoot and diagnose issues with Cisco router interfaces. The output of the command is as follows:routerA# show controllers serial 0 HD unit 1, idb = 0x1C44E8, driver structure at 0x1CBAC8 buffer size 1524 HD unit 1 V.35 DTE cable, clock rate 64000
The preceding output indicates that a V.35 DTE cable is currently connected to interface Serial 0, and that a clock rate of 64000 bps has been detected from the DCE (the other side of the serial link). When the other end is a CSU/DSU, as is usually the case, the clock rate is provided by the CSU/DSU. The clocks stopped portion of the following output would indicate that a clock rate has not been detected from the DCE:
routerA# show controllers serial 0 HD unit 1, idb = 0x1C44E8, driver structure at 0x1CBAC8 buffer size 1524 HD unit 1 V.35 DTE cable, clocks stopped
This condition would be rectified by configuring a clock rate on the DCE router.
The show interfaces, show ip interface, and show interface switchport commands do not display any hardware-related information, such as connected cable types.
The show interface dce command is incorrect because this is not a valid Cisco IOS command.
Objective:
WAN Technologies
Sub-Objective:
Describe WAN access connectivity options -
You are the network administrator for your company. You have been assigned the task of configuring an appropriate IP addressing scheme in the network.
Assuming that the network address is 192.16.100.0/28, what will be the number of hosts per network in this scenario?
- 2
- 6
- 14
- 30
Explanation:
In this scenario, there will be 14 hosts per network. The formula for calculating the number of hosts on a subnet is 2n – 2, where n is the number of host bits in the summary mask. The n can be calculated by subtracting host bits from the total number of bits in a subnet mask (32). In this case, n would be 32 – 28 = 4. Therefore, the formula to calculate the number of bits in this scenario would be:2(32 -28) – 2 = 24 – 2 = 14 hosts
You always subtract 2 from 2n because the all-zero-bit address is reserved for the network address (called the network ID) and the all-one-bit address is reserved for the broadcast address.
The 192.16.100.0/28 network address would not have 30 hosts per network. The 192.16.100.0/27 network address would actually yield 30 hosts per network. In this case, n would be 32 – 27 = 5, so the number of host bits in the subnet mask would be 32 – 2, which is equal to 30.
The 192.16.100.0/28 network address would not have 6 hosts per network. The 192.16.100.0/29 network address would yield 6 hosts per network. In this case, n would be 32 – 29 = 3, so the number of host bits in the subnet mask would be 8 – 2, which is equal to 6.
The 192.16.100.0/28 network address would not have 2 hosts per network. The 192.16.100.0/30 network address would yield 2 hosts per network. In this case, n would be 32 – 30 = 2, so the number of host bits in the subnet mask would be 4 – 2, which is equal to 2.
Objective:
Network Fundamentals
Sub-Objective:
Configure, verify, and troubleshoot IPv4 addressing and subnetting -
What is the HSRP virtual router MAC address for the virtual router for HSRP group 31?
- 0000.0c07.ac1f
- ac1f
- 0c07
- 07.ac
Explanation:
The Hot Standby Router Protocol (HSRP) virtual MAC address for the virtual router for HSRP group 31 is 0000.0c07.ac1f. A Media Access Control (MAC) address is a 6-byte value that is unique for every networked device. MAC addresses are typically written in hexadecimal notation. The address 0000.0c07.ac1f is a MAC address for an HSRP virtual router; this address can also be written as 00-00-0c-07-ac-1f or 00.00.0c.07.ac.1f. Hexadecimal letters can be written as either lowercase or uppercase letters.The MAC address for an HSRP virtual router consists of the vendor ID, the HSRP code and the group ID. The vendor ID corresponds to the first three bytes of the MAC address. A vendor ID of 0000.0c indicates that the device was manufactured by Cisco. The HSRP code corresponds to the fourth and fifth bytes of the MAC address. The HSRP code for a virtual router is always equal to 07.ac. Finally, the group ID corresponds to the last byte of the MAC address. For example, a group ID of 1f, when converted to decimal, indicates that the virtual router belongs to HSRP group 31.
Objective:
Infrastructure Services
Sub-Objective:
Configure, verify, and troubleshoot basic HSRP -
You manage the EIGRP subnet in your organization. You have enabled EIGRP for IPv6 on all the routers in the EIGRP AS 260 using the following commands on all the routers:

200-301 Part 21 Q12 188 During verification, you discover that EIGRP for IPv6 is not running on the routers.
Which of the following should be done to fix the issue?
- The ipv6 address command should be executed in interface configuration mode.
- The ipv6 address command should be executed in router configuration mode.
- The eigrp router-id command should be executed in interface configuration mode.
- The eigrp router-id command should be executed in router configuration mode.
Explanation:
The eigrp router-id command should be executed in router configuration mode to fix the issue. This command specifies a fixed router IPv4 address to the router. If this command is missing or incorrectly configured on the router, EIGRP for IPv6 will not run properly.Another command that you should perform so that EIGRP for IPv6 runs on the routers is the no shutdown command. You should execute this command in interface configuration mode. The no shutdown command is necessary because all the interfaces with EIGRP for IPv6 enabled on them are in a shutdown state by default.
A sample configuration to implement EIGRP for IPv6 on a router is as follows:
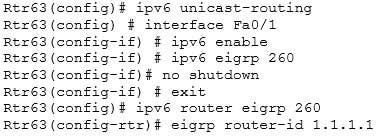
200-301 Part 21 Q12 189 The two options stating that the ipv6 address command should be executed on the routers are incorrect. EIGRP for IPv6 can be configured on router interfaces without explicitly specifying a global unicast IPv6 address. If you specify the ipv6 enable command, as in this scenario, then the IPv6 address command is not required.
The option stating that the eigrp router-id command should be executed in interface configuration mode is incorrect. This command should be executed in router configuration mode instead of interface or global configuration modes.
Objective:
Routing Fundamentals
Sub-Objective:
Configure, verify, and troubleshoot EIGRP for IPv6 (excluding authentication, filtering, manual summarization, redistribution, stub) -
You have multiple departments sharing a common network. You are concerned about network traffic from one department reaching another department.
What would be a solution for isolating the departments? (Choose all that apply.)
- Configure separate VLANs for each department.
- Assign a unique VTP domain for each department.
- Put each department in a separate collision domain.
- Configure trunk links between departmental switches.
- Configure separate subnets for each department
Explanation:
You could either configure separate VLANs for each department or configure separate subnets for each department. Either approach has the effect of restricting each department’s traffic to its local subnet or VLAN, unless you configure and allow inter-VLAN routing.VLANs logically divide a switched network into multiple independent broadcast domains. Broadcast traffic within one VLAN will never be sent to hosts in other VLANs. In this respect, VLANs operate exactly as subnets do. The only way for hosts in different VLANs to communicate is through a router or multilayer switch configured to perform inter-VLAN routing between the VLANs.
The VLAN Trunking Protocol (VTP) is used to synchronize VLAN databases across multiple switches, and is not a method for isolating departmental traffic.
Collision domains cannot be used to isolate traffic between departments. Multiple departments cannot share a collision domain when using switches. Every port on a switch is a separate collision domain, which allows the switch to forward more than one frame at a time. This also reduces collisions, since each host is therefore in a separate collision domain. The switch processes data based only on MAC addresses, and has no knowledge of which host is in which IP subnet or department.
Trunk links are used to connect switches to other switches and to routers for the purpose of carrying traffic from multiple VLANs, and are not a method of isolating traffic between different departments.
Objective:
LAN Switching Fundamentals
Sub-Objective:
Configure, verify, and troubleshoot VLANs (normal/extended range) spanning multiple switches -
During the process of connecting four switches to the central router and implementing VLANS between the devices, it becomes apparent that there was a misunderstanding about which encapsulation protocol to use on the links between the switches and the router.
If there is mismatch between the encapsulation types used on the router interface and the type used on the connected switch port, what will be the result?
- The relevant switch ports will be green.
- The relevant switch ports will be amber.
- The relevant switch ports will be neither green nor amber.
- The relevant switch ports will be green and flashing.
Explanation:
If there is a mismatch between the encapsulation types used on the router interface and the type used on the connected switch port, the link will not be functional and there will be neither an amber nor a green light. The same outcome will be produced when there is a bad cable, an incorrect cable type, or a lack of signal. An example of a cable mismatch would be the use of a straight-through cable when the situation required a crossover cable, or vice versa.When connecting switch ports to routers, there are two possible encapsulation types: the default Interswitch Link (ISL) and the 802.1q standard. ISL is a Cisco proprietary technology; therefore, it can only be used between Cisco products. 802.1q is an industry standard that can be used between Cisco and non-Cisco products. If the same type is not configured on each end, the link will not work.
The relevant switch ports will not be green. Green indicates normal operation with no activity.
The relevant switch ports will not be amber. Amber indicates the link is administratively down. The amber light is usually flashing as well.
The relevant switch ports will not be green and flashing. This display indicates normal operation with activity on the line.
Objective:
LAN Switching Fundamentals
Sub-Objective:
Troubleshoot interface and cable issues (collisions, errors, duplex, speed) -
You know that Router2 is configured for RIP. Which Cisco Internetwork Operating System (IOS) command is used to view the current state of all active routing protocols?
- show ip arp
- debug ip rip
- show ip protocols
- show ip routing process
- show arp
- show interfaces
Explanation:
The show ip protocols command is used to view the current state of active routing protocols. This command is issued from Privileged EXEC mode. The syntax of the command is as follows:Router2# show ip protocols
Output of the command would resemble the following:
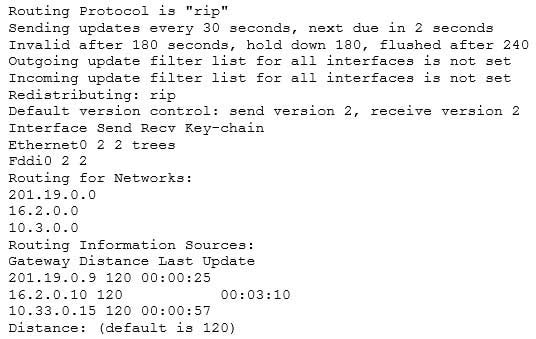
200-301 Part 21 Q15 190 This command shows additional information about individual protocols. The version number of RIP being used is shown on the seventh line of the output. This output also indicates on lines 12-14 that it is routing for three networks: 201.19.0.0, 16.2.0.0, and 10.3.0.0. This means that the router will be sending and receiving RIP updates on any interfaces that have IP addresses in those networks.
Also note that the router at 16.2.0.10 has not sent an update in 3 minutes and 10 seconds. If an update is not received in 50 seconds (for a total of 4 minutes), the route-flush timer (240 seconds from the last valid update) will have expired, causing the local router to remove all networks learned from the router at 16.2.0.10 from the routing table.
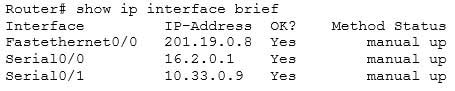
For more specific information about those interfaces, in terms such as S0 or Fa0/0, you could execute the show ip interface brief command as shown below. The output displays the addresses of the interfaces, which would indicate which interfaces were enabled for RIP and thus sending and receiving updates.
200-301 Part 21 Q15 191 The show ip arp command is incorrect because this command is executed on a router to determine the IP and MAC addresses of hosts on a LAN connected to the router.
The debug ip rip command is incorrect because this command is used to capture RIP traffic between the routers in real time. This command could also be used to determine the version of RIP being used as shown in line 2 of the partial output of the command below:
Router2#debug ip rip RIP protocol debugging is on
*Mar 3 02:11:39.207:RIP:received packet with text authentication 234
*Mar 3 02:11:39.211:RIP:received v1 update from 122.108.0.10 on Serial0
*Mar 3 02:11:39.211:RIP: 79.0.0.0/8 via 0.0.0.0 in 2 hops
*Mar 3 02:11:40.212:RIP: ignored v2 packet from 192.168.5.6 (illegal version)In the above output Router 2 has received a version 1 update from a router at 122.108.0.10 which indicates that a ping to that router should succeed. It also shows what was learned from the router at 122.108.0.10, which is the router to network 79.0.0.0/8 via 0.0.0.0. The 0.0.0.0 indicates that the next hop for that route is the router that sent this advertising (the router at 122.108.0.10).
The output also shows that a RIP router at 192.168.5.6 sent a version 2 update that was ignored by Router 2, which is using version 1. This mismatch of versions will prevent Router 2 from forming an adjacency with the router at 192.168.5.6.
Note: Before running any debug command you should execute the show processes command and verify that the CPU utilization on the router is low enough to handle the effects of running the debug command.
The show ip routing process command is incorrect because it is not a valid Cisco IOS command.
The show arp command is used to identify the IP address to MAC address mappings the router has leaned through the ARP broadcast process. It is helpful when you have identified errors associated with a MAC address and you need to learn the IP address or vice versa. Sample output is below.
router# show arp Protocol Address Age (min) Hardware Addr Type Interface Internet 10.0.0.3 0 0004.dd0c.ffcb ARPA Ethernet01 Internet 10.0.0.1 - 0004.dd0c.ff86 ARPA Ethernet0
The difference between the show arp command and the show ip arp command is that show arp will also include mappings learned through non-IP protocols such as when inverse ARP is used to learn and map DLCIs to IP addresses.
The show interface command can also be used to identify IP addresses from MAC addresses and vice versa, but also indicates the state of the interface; IP addresses MTU and much more about each interface. Sample output is below.
router# show interfaces Ethernet 0 is up, line protocol is up Hardware is MCI Ethernet, address is 0000.0c00.750c(bia 0000.0c00.750c) Internet address is 10.108.28.8, subnet mask is 255.255.255.0 MTU 1500 bytes, BW 10000 Kbit, DLY 100000 usec, rely 255/255, load 1/255
Objective:
Routing Fundamentals
Sub-Objective:
Compare and contrast distance vector and link-state routing protocols -
You are the network administrator for your company. You want to implement a routing protocol that can support hierarchical routing, multiple vendor environments, and authentication, and provides fast convergence.
Which routing protocol will you implement?
- Enhanced Interior Gateway Routing Protocol (EIGRP)
- Open Shortest Path First (OSPF)
- Routing Information Protocol version 2 (RIPv2)
- Interior Gateway Routing Protocol (IGRP)
Explanation:
Open Shortest Path First (OSPF) is the routing protocol that accomplishes this task. The following are characteristics of OSPF:
– Conveges very quickly.
– Uses cost to detemine the best route.
– Uses Internet Protocol (IP) protocol 89.
– Has a default administrative distance of 110.
– Is an industry standard protocol (non Cisco-proprietary).
– Supports Non-Broadcast Multi-Access (NBMA) networks such as frame relay, X.25, and Asynchronous Transfer Mode (ATM). The default hello interval for NBMA networks is 30 seconds.
– Supports point-to-point and point-to-multipoint connections.
– Supports authentication.
– Uses 224.0.0.6 as multicast address for ALLDRouters.
– Uses 224.0.0.5 as multicast address for ALLSPFRouters.
– Uses link-state updates and SPF calculation that provides fast convergence.
– Recommended for large networks due to good scalability.
– Uses cost as the default metric.
– Supports VLSM.
– Create minimal overhead due to its hierarchical design.In OSPF networks, a hierarchical IP addressing design and the use of areas yields the following benefits:
– Faster convergence
– Reduced routing overhead
– Confinement of network instability to a single area of the networkElecting a designated router (DR) in each area reduces update traffic because all updates occur through the DR. The DR election is based on the router ID. This is the highest IP address of the active interfaces when no loopback interface is configured. When a loopback address is present, its address is used for the purposes of DR election. In either case, the router with highest router ID becomes the DR.
EIGRP and IGRP are incorrect because they are Cisco-proprietary routing protocols, and thus do not support multiple vendor environments. They also do not support hierarchical routing. IGRP is no longer being supported by Cisco.
RIPv2 is incorrect because it does not support hierarchical routing or provide fast convergence.
Objective:
Routing Fundamentals
Sub-Objective:
Compare and contrast distance vector and link-state routing protocols -
Which feature is NOT provided by flow control?
- buffering
- windowing
- full duplex transmission
- source-quench messaging
Explanation:
The full duplex mode of transmission is not provided by flow control. Full duplex transmission is an Ethernet concept where hosts are able to send and receive at the same time. There are no collisions in a full-duplex Ethernet network. A dedicated switch port is required for each node in a full-duplex Ethernet network. Both the host’s NIC and the switch port must be capable of operating in full-duplex mode. When full duplex is implemented, no collisions will occur on the link between the switch and the device. That will be one error condition that can be removed from consideration when troubleshooting a full duplex link.Flow control is a function that prevents network congestion. It does so by ensuring that the transmitting device does not flood the receiving device with data. The following statements are true regarding flow control:
– Controls the amount of data which the sender can send to the receiver.
– Uses buffering, transmitting source-quench messages, and windowing to handle network congestion.
– Determines the rate at which the data is transmitted between the sender and receiver.
– Types of flow control include windowing, buffering, and congestion avoidance.Flow control generally operates at the Transport layer in the OSI model. The Transport layer is responsible for error-free and sequential delivery of data. This layer is used to manage data transmission between devices.
Buffering is a method by which network devices use to save temporary overflows of excess data into the memory. The data is stored in the memory until it is processed.
Source-quench messages are used by the devices that receive the data to avoid buffer overflow.
Windowing is a scheme in which an acknowledgement is required by the source device from the destination after the transmission of a fixed number of packets.
Objective:
Network Fundamentals
Sub-Objective:
Compare and contrast OSI and TCP/IP models -
Which device creates broadcast domains and enables communication across separate broadcast domains?
- router
- switch
- hub
- access points
Explanation:
A router allows communication across separate broadcast domains. A broadcast domain is group of hosts and network devices in which a broadcast frame sent by one host can be received by all of the other hosts in the broadcast domain. A router determines the path to other destination networks, and forwards data packets to the next hop along this path. A router operates at Layer 3 of the Open System Interconnect (OSI) layered communication model and uses an Internet Protocol (IP) address hierarchy to identify and route data through source and destination devices.A switch does not allow communication across separate broadcast domains. A switch creates collision domains and enables communications across different collision domains. A collision domain is a logical group of hosts and network devices where packets can potentially collide with one another, causing a communications disruption. Switches forward broadcasts so they do not form a separate broadcast domain unless Virtual LANs (VLANs) are created.
A hub does not allow communication across separate broadcast domains. A hub transmits frames, which means that they neither form separate collision or broadcast domains nor allow communication across these domains. Hubs are multiport devices that allow consolidation of various LAN segments and amplify signals that pass through them. Hubs operate at OSI Layer 1.
An access point does not allow communication across separate broadcast domains. Access points (APs) are OSI Layer 2 wireless hubs that allow client hosts to connect to the backbone network wirelessly.
Objective:
Network Fundamentals
Sub-Objective:
Describe the impact of infrastructure components in an enterprise network -
Which of the following is NOT a dynamic table maintained by a router running the EIGRP routing protocol?
- topology table
- CAM table
- routing table
- neighbor table
Explanation:
All are tables maintained by a router running the EIGRP routing protocol except a Content Addressable Memory (CAM) table. This table is only present on a switch. It is used to maintain the two MAC addresses involved in a conversation between computers so that the conversation can be routed once and then switched thereafter which is a much faster process.EIGRP maintains three dynamic tables in RAM:
– Neighbor table, which is a list of all neighboring EIGRP routers on shared subnets
– Topology table, which contains all discovered network paths in the internetwork
– Routing table, which contains the best path (based on lowest metric) to each destinationObjective:
Routing Fundamentals
Sub-Objective:
Configure, verify, and troubleshoot EIGRP for IPv4 (excluding authentication, filtering, manual summarization, redistribution, stub) -
Which of the following protocols is responsible for negotiating upper-layer protocols that will be carried across a Point-to-Point Protocol (PPP) connection?
- LCP
- NCP
- LMI
- ISDN
Explanation:
Network Control Protocol (NCP) is responsible for negotiating upper-layer protocols that will be carried across the PPP connection. NCP defines how the two PPP peers negotiate with the network layer protocols, such as IP and IPX, which will be used across the PPP connection.Link Control protocol (LCP) is not responsible for negotiating upper-layer protocols that will be carried across a PPP connection. Link Control protocol (LCP) has the primary responsibility of negotiating and maintaining the PPP connection. LCP, defined in Request for Comments (RFCs) 1548 and 1570, has the primary responsibility to establish, configure, authenticate, and test a PPP connection. LCP negotiates the following when setting up a PPP connection:
– Authentication method used (PAP or CHAP), if any
– Compression algorithm used (Stacker or Predictor), if any
– Callback phone number to use, if defined
– Multilink; other physical connections to use, if configuredLocal Management Interface (LMI) is not responsible for negotiating upper-layer protocols that will be carried across the PPP connection. LMI is a characteristic of a frame relay connection. There are three types of LMIs supported by Cisco routers:
– Cisco
– ANSI Annex D
– Q933-A Annex ALMI has nothing to do with PPP connections.
Integrated Services Digital Network (ISDN) is a type of WAN connection and has nothing to do with PPP connections.
Objective:
WAN Technologies
Sub-Objective:
Configure and verify PPP and MLPPP on WAN interfaces using local authentication