200-901 : DevNet Associate (DEVASC) : Part 04
-
Which of the following statement is true regarding MAC address?
- It is a network interface hardware address
- It is the component serial number
- It is serial number of the manufacturers code
- It is a unique IP address
-
Which git command will create a working copy of a local repository?
- git clone /path/to/repository
- git copy /path/to/repository
- git branch /path/to/repository
- git cp /path/to/repository
-
How can Cisco Advanced Malware protection be used to protect user devices and other systems on the network?
- It installs antivirus program on user devices
- it infects system files and then sit there to detect any external threat
- It employs API to obtain a list of vulnerable software on user devices
- It can be used to detect ransomware and neutralize it using an array of tools
-
Which type of HTTP method is used by the Meraki and Webex Teams APIs to send webhook notifications? (Choose two).
- It is used by meraki API to send webhook notifications
- It is used by REST API to send a payload to destination address
- It is used by Cisco switches to send alerts
- It is used by Webex teams API to send webhook notifications
-
How can status code be used as an element of response when building an application using REST API?
- as a response in conditional check
- as a response in json format
- as an alert for coding errors
- as a source of element in REST API
-
What happens when a load balancer fails and causes service disruption that can be experienced from various clients connected to the server?
- Automation script fails to connect to an internal server as it is executed
- The server sends an alert to a predefined email address
- Client devices fail to connect to the remote server
- all devices on the network fail to get data from the server
-
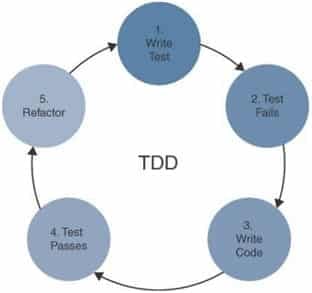
Which of the following is the correct order of steps performed during test-driven development?
- Write test, write code, test passes, test fails, refactor
- Refactor, write code, write test, test passes, test fail
- Write code, write test, test fails, test passes, refactor
- Write test, test fails, write code, test passes, Refactor
Explanation:
-
In what type of API call does the callback function used to process the response from an API call
- reverted
- synchronous
- asynchronous
- RESTful
-
What command do you use to launch an nginx container on port 80 of the host file system?
- docker image build -p 80 nginx
- docker start -it -d nginx -p 80|80
- docker container run -p 80:80 -d nginx
- docker container run -p 8080 -d
-
Which protocols are supported by yang-notif-native transport protocol? (Choose two).
- kvGPB
- gNMI
- gPRC
- RESTCONF
- NETCONF
-
Which of the following command allows client to connect to NETCONF ssh sub-system?
- $ ssh -p 830 cisco@clus1 -s netconf
- $ ssh -p netconf
- $ssh -i 830 cisco@clus1 -s netconf
- $ ssh -t 830 cisco@clus1 -s netconf
-
Devices that implement the RESTCONF protocol should expose a resource called __________ in order to enable the discovery of the REST API root resource programmatically.
- /discover/restconf
- /.well-known/restconf
- /.well-known/host-meta
- /discover/root
-
With seek pagination, after_id and before_id queries, constraints of filters and sorting can be removed. What is the downside of seek pagination?
- It can stabilize state enums and category names
- It doesn’t address cardinality fields
- It cannot bring back removed constraints
- it is challenge to create custom sort orders
-
What type of attack occurs when a web page is loaded, and malicious code copies the user’s cookies. The system then sends an HTTP request to an attacker’s web server, with the
stolen cookies in the body of the request. The attacker can then use cookies to access sensitive data?
- Malware attack
- Denial-of-service-attack
- cross-site scripting
- injection
-
Which APIs are used build a custom captive portal for mobile apps along with the ability to configure network devices via Dashboard API?
- REST APIs
- Meraki APIs
- RESTful API
- Finesse APIs
-
How can a developer access webex APIs during the authentication procedure? (Choose three).
- Teams
- Room
- Integrations
- Messages
- Bots
- Guest Issuers
-
In Software-defined architecture, which network plane provides a router to route packets faster by using techniques such as fast switching or CEF switching?
- network plane
- data plane
- I/O plane
- control plane
-
In which phase of CI/CD pipeline installing the new binaries in new servers, either physical or
virtual, and reconfiguring the load balancers to point to the new servers and monitor the environment to ensure that the new version worked as expected is achieved?
- Deployment phase
- Development phase
- Testing phase
- Building phase
-
pyATS is easily integrated in day-to-day DevOps activities and CI/CD automation pipelines. Which of the following are use cases of pyATS? (Choose two.)
- screen scrape and parse different proprietary CLI outputs
- automating configuration changes and monitoring devices
- configuring change validation
- Taking snapshot of configuration status and operational data of the network
- parse interpreted data
-
Refer to the exhibit.
#git init newrepo
Initialized empty Git repository in
/Users/chrijack/Documents/
GitHub/newrepo/.git/
#newrepo git:(master)Which command should you use to create an empty file?
- newrepo git:(slave) add newfile
- newrepo git:(master) branch newfile
- newrepo git: touch newfile
- newrepo git:(master) touch newfile
Subscribe
0 Comments
Newest