300-410 : Implementing Cisco Enterprise Advanced Routing and Services (ENARSI) : Part 03
-
Examine the following diagram:

300-410 Part 03 Q01 028 Routing updates are not being received on Router A from Router D. The partial output of the show run command for Router B and Router C is shown below:
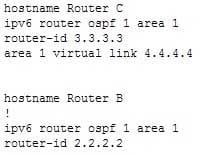
300-410 Part 03 Q01 029 What commands should you run to ensure that routing updates are getting to Router A from Router D? (Choose all that apply.)
-
routerC(config-router)# area 1 virtual-link 2.2.2.2
-
routerC(config-router)# no area 1 virtual-link 4.4.4.4 routerC(config-router)# area 0 virtual-link 2.2.2.2
-
routerB(config-router)# area 0 virtual-link 3.3.3.3
-
routerB(config-router)# area 1 virtual-link 3.3.3.3 -
routerC(config-router)# no area 1 virtual-link 4.4.4.4 routerC(config-router)# area 1 virtual-link 2.2.2.2 -
routerB(config-router)# area 1 virtual-link 4.4.4.4
-
routerB(config-router)# no area 1 virtual-link 4.4.4.4
Explanation:
The problem is that the virtual link that provides a connection from area 2 to area 0 is misconfigured on Router C, and is missing entirely from Router B. The current configuration on Router C uses the router ID 4.4.4.4 in the virtual link statement, but the neighbor that is on the other end of the link (Router B) has an ID of 2.2.2.2. Therefore, you must remove the incorrect statement with this command:routerC(config-router)# no area 1 virtual-link 4.4.4.4
Then, you would recreate it correctly with the following command:
routerC(config-router)# area 1 virtual-link 2.2.2.2
The configuration of the virtual link on Router B is missing completely. To add it, you would use the area 1 virtual-link command and configure the neighbor as Router C at 3.3.3.3:
routerB(config-router)# area 1 virtual-link 3.3.3.3
You should not run the following command on Router C:
routerC(config-router)# area 1 virtual-link 2.2.2.2
This would apply a correct statement, but leave in the incorrect statement.
You should not run any of the following sets of commands:
routerC(config-router)# no area 1 virtual-link 4.4.4.4 routerC(config-router)# area 0 virtual-link 2.2.2.2
or
routerB(config-router)# area 0 virtual-link 3.3.3.3
These commands all incorrectly include the area 0 syntax. The area in the command should be the area being transited to get to area 0, which is area 1.
You should not run the routerB(config-router)# area 1 virtual-link 4.4.4.4 command on Router B. This command uses an incorrect router ID. The neighbor for Router B should be Router C, 3.3.3.3
You should not run the routerB(config-router)# no area 1 virtual-link 4.4.4.4 command on Router B. There is no virtual link to remove from Router B.
Objective:
Layer 3 Technologies
Sub-Objective:
Configure and verify network types, area types, and router types -
-
Router10 is an area system border router (ASBR). The interfaces on Router 10 are configured as below:
S 0/0 10.0.0.0/8
S0/1 172.16.0.0/8
Fa0/0 192.168.5.0/24
Fa0/1 192.168.6.0/24You would like Router 10 to advertise the 192.168.5.0/24 and the 192.168.6.0/24 networks over OSPF in its Type 5 link-state advertisements (LSAs).
What command set would instruct the router to do this?
-
RTA10(config)# router ospf 1 RTA10(config-router)# redistribute static
-
RTA10(config)# router ospf 1 RTA10(config-router)# redistribute connected
-
RTA10(config)# router ospf 1 RTA10(config)# redistribute connected
-
RTA10(config)# router ospf 1 RTA10(config-router)# network 192.168.5.0 0.0.0.0 area 1 RTA10(config-router)# network 192.168.6.0 0.0.0.0 area 1
Explanation:
By default, Type 5 link-state advertisements (LSAs) do not include directly connected networks. To alter this behavior, you must execute the redistribute connected command in OSPF configuration mode. This command instructs the router to include these local interfaces in its advertisements, as follows:RTA10(config)# router ospf 1
RTA10(config-router)# redistribute connectedYou should not execute the command set that includes the redistribute static command. This instructs the router to advertise any statically defined routes that have been configured, instead of those that are local to the router.You should not execute the command set that includes RTA10(config)# redistribute connected. The redistribute connected command is shown being executed at the wrong command prompt, and will generate an error message. It must be executed in the OSPF configuration mode and not global configuration mode.You should not execute the following command set:RTA10(config)# router ospf 1
RTA10(config-router)# network 192.168.5.0 0.0.0.0 area 1
RTA10(config-router)# network 192.168.6.0 0.0.0.0 area 1The network commands will cause the networks to receive updates from the router, but do not allow them to be advertised in Type 5 LSAs.Objective:
Layer 3 Technologies
Sub-Objective:
Configure and verify redistribution between any routing protocols or routing sources -
-
Refer to the following partial output of the show ip bgp neighbors command:

300-410 Part 03 Q03 030 Which of the following can NOT be determined from the given output? (Choose all that apply.)
- The ASN of rtrA
- The ASN of 172.161.81.7
- The best paths between rtrA and the 172.161.81.7 neighbor
- The RID of the 172.161.81.7 neighbor
- The status of the connection between rtrA and 172.161.81.7
Explanation:
The autonomous system number (ASN) of rtrA and the best paths between rtrA and the 172.161.81.7 neighbor cannot be determined from the given output.The show ip bgp neighbors command displays the TCP and BGP connections from a given router to its neighbors. This command is executed in EXEC mode. You can use various optional keywords to view different aspects of the neighbors. For example, this command can display the details about a given neighbor, routes advertised to or received from neighbors, and the prefix-list received by neighbors.In this case, the command is used to show the details about a specific neighbor of rtrA. The IP address (172.161.81.7) of the neighbor is provided in the command. The text BGP neighbor is 172.161.81.7 indicates the IP address of the neighbor. The text remote AS 151 indicates that the neighbor is in the ASN 151. It can also be determined from the text external link that the neighbor is an eBGP neighbor. For iBGP neighbors, the text internal link will appear. The router ID (RID) of the neighbor can be determined from the text remote router ID 10.8.22.4.The output also provides details about the state of the BGP connection, which is Established in this case. Furthermore, the duration for which the connection has been established, the duration for which BGP maintains neighbor relationship in the absence of messages, and the keepalive duration are also displayed.The state of the connection between the local router (rtrA) and the given neighbor (172.161.81.7) can be any of the following:
Idle Indicates that the local router does not accept any connection from its neighbor
Idle (admin) Indicates that the connection between the two routers has been shut down administratively by using the neighbor shutdown command
Connect Indicates that the local router has already sent an connection request to its neighbor
Active Indicates that the local router is listening for connection requests from the neighbor
OpenSent Indicates that the local router has sent an OPEN message to its neighbor
OpenConfirm Indicates that the local router has received a KEEPALIVE or UPDATE message from its neighbor
Established Indicates that a BGP connection has been successfully created between the local router and its neighborThe status of the connection between two BGP neighbors can also be viewed by using the show ip bgp summary command, as shown below:
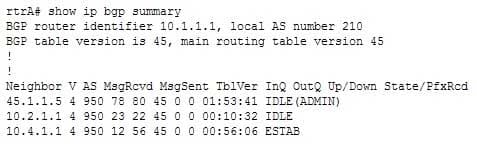
300-410 Part 03 Q03 031 In the above output, it can be determined that the command router bgp 210 was executed on rtrA because the local AS is 210 in the output. It can be determined that the command neighbor 45.1.1.5 shutdown was issued on rtrA because the state of the neighbor relationship with the router at 45.1.1.5 is listed as IDLE(ADMIN).
All the other options are incorrect because the respective details are displayed by the show ip bgp neighbors command.
Objective:
Layer 3 Technologies
Sub-Objective:
Configure and verify eBGP (IPv4 and IPv6 address families) -
Examine the exhibit.
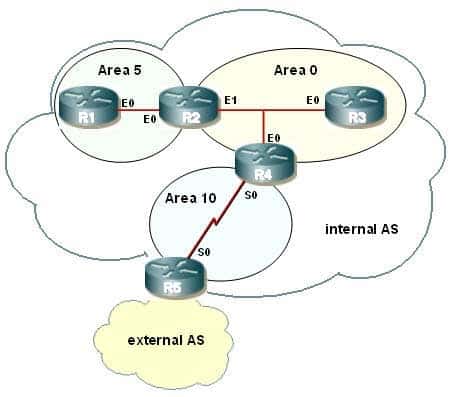
300-410 Part 03 Q04 032 You are asked to configure the routers R1, R2, R3, and R4. (Refer to the IP addressing table below.) Which configuration command series is required to ensure that router R1 will NOT be receiving Type 3, 4, or 5 LSAs?
R1 interface E0 - 172.31.200.1/21 R2 interface E0 - 172.31.200.2/21 R2 interface E1 - 172.31.208.2/21 R3 interface E0 - 172.31.208.3/21
-
R1(config)# router ospf 5 R1(config-router)# area 5 stub R1(config-router)# network 172.31.200.0 0.0.7.255 area 5
-
R2(config)# router ospf 5 R2(config-router)# area 5 stub no-summary R2(config-router)# network 172.31.200.0 0.0.7.255 area 5 R1(config)# router ospf 5 R1(config-router)area 5 stub R1(config-router)# network 172.31.200.0 0.0.7.255 area 5
-
R1(config)# router ospf 10 R1(config-router)# area 5 stub R1(config-router)# network 172.31.200.0 255.255.248.0 area 5
-
R2(config)# router ospf 10 R2(config-router)# area 5 stub no-summary R2(config-router)# network 172.31.200.0 255.255.248.0 area 5
Explanation:
At the area border router (ABR), router R2, the no-summary keyword is required with the area stub command to create a totally stubby area. All other routers in area 5 will require the stub command without the no summary keyword. The following commands are required to configure R2:R2(config)# router ospf 5 R2(config-router)# area 5 stub no-summary R2(config-router)# network 172.31.200.0 0.0.7.255 area 5
R1 will require:
R1(config)# router ospf 5 R1(config-router)# area 5 stub R1(config-router)# network 172.31.200.0 0.0.7.255 area 5
All routers within a stub area must be configured as stub, or adjacencies will not form. Besides the command to enable OSPF and the command to identify the area, the only other required command identifies the area as a stub. A totally stubby area does not accept any external network LSAs (Type 5) or any inter-area summary LSAs (Types 3 and 4) from entering the area.
Use the area stub command with the no-summary keyword to configure a totally stubby area. The diagram below shows the commands that should be executed on R1 and R2.
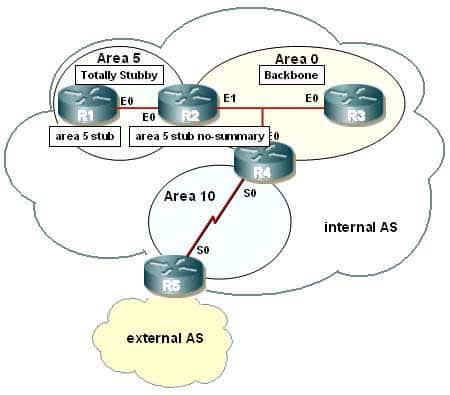
300-410 Part 03 Q04 033 The correct syntax for the area stub command is shown below:
Router(config-router)# area area-id stub [no-summary]
Note that the optional no-summary keyword is used only on area border routers (ABRs) to block summary link advertisements into the stub area. This option creates a totally stubby area. It is very important to configure the command consistently on all routers within the area. OSPF sends its stub status (on or off) in its hello packets. If two neighbors have conflicting stub status, they will not form an adjacency, and you end up with no OSPF communication over that link.
Objective:
Layer 3 Technologies
Sub-Objective:
Configure and verify network types, area types, and router types -
-
You instructed your assistant to configure load balancing on a router. The router currently has two routes to network A. One route has a cost of 15, and the other has a cost of 30.
What command should the assistant execute to instruct the router to treat the two routes as equal without including any other routes in the load balancing?
-
routerA(config)# variance 2
-
routerA(config-router)# variance 2 -
routerA(config)# variance 3
-
routerA(config-router)# variance 3
Explanation:
The correct command to instruct the router to treat the two routes as equal is variance 2. It must be entered in EIGRP configuration mode, as evidenced by the routerA(config-router)# prompt. The number that comes after the command is called the multiplier. A multiplier of two tells the router that any route that is within twice the metric of the best route will be considered equal to the best route.The default setting for variance is one, which indicates that the routes must be equal to be considered for load balancing. An additional requirement of load balancing is that the alternate route’s feasible distance must not be higher than the advertised distance of the route, which could indicate a routing loop.The assistant should not execute the variance 2 command at the routerA(config)# prompt, which is global configuration mode. The variance command must be entered in EIGRP configuration mode at the routerA(config-router)# prompt.The assistant should not use the variance 3 command in either mode because that would direct the router that any route within three times the cost of the best route (in this scenario, a cost of 45) would be considered equal to the cost of the best route. The scenario requires that two routes be load balanced. Because one route has a cost of 15 and the other has a cost of twice 15 (30), the variance multiplier must be two.Objective:
Layer 3 Technologies
Sub-Objective:
Configure and verify EIGRP load balancing -
-
Examine the exhibit.
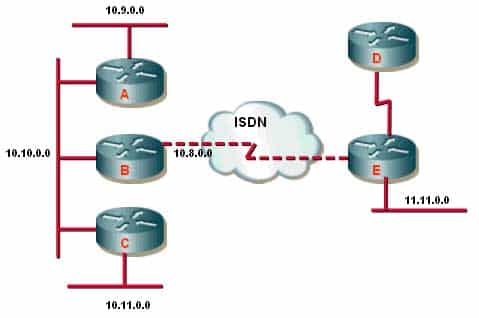
300-410 Part 03 Q06 034 The router labeled “B” has been configured by using the following configuration commands:
RouterB(config)# router eigrp 100 RouterB(config-router)# network 10.0.0.0 RouterB(config-router)# distribute-list 10 in bri 0 RouterB(config)# access-list 10 deny 11.11.0.0 0.0.255.255 RouterB(config)# access-list 10 permit any
Which statement best describes the effects of this configuration?
- Only network 11.11.0.0 will be advertised to routers A and C.
- Advertisements received by router A will include router D networks.
- Advertisements to router C will not include the router D and E networks.
- Traffic from network 11.11.0.0 hosts will be discarded because of ACL 10.
Explanation:
The router will scan the access list specified by a distribute list. If a match to a permit statement is found, the route entry is permitted; if a match is found to a deny statement, the route is discarded. In this question, the permit statement in ACL 10 provides a permit match to all routes advertised from router D except for network 11.11.0.0.Distribute lists are used to filter inbound, outbound, or redistributed routing updates. Instead of using the passive-interface command, distribute lists enable you to selectively control which routes are processed.If a distribute list is associated with an interface, the routing update is compared to the access list that was specified in the distribute list. If a match is found to a permit statement, then the packet is forwarded. If a match is found to a deny statement, the packet is discarded. If no match is found, the implicit deny statement at the end of the access list will drop the packet. For example, if the access list in the above example were missing the line access-list 10 permit any, all updates would be denied, not just the one specified by the deny statement.If no distribute list is associated with the interface, the routing update packets are processed as normal.Distribute lists can reference multiple access lists if required to obtain the desired result. For example, examine the following configuration from a partial output of show run:router eigrp
distribute-list 2 out ethernet 0
distribute-list 1 out
!
access-list 1 permit 10.0.0.0 0.255.255.255
access-list 2 permit 10.0.1.0 0.0.0.255By using two access lists and two distribute lists, you accomplish the following:- Only routes matching 10.0.0.0/8 will be advertised out interfaces other than E0
- Only routes matching 10.0.1.0/24 will be advertised out E0
Network 11.11.0.0 will not be the only network advertised to routers A and C. In this question, the permit statement in ACL 10 provides a permit match to all routes advertised from router D except for network 11.11.0.0.
The option advertisements to Router C will not include the router D and E networks is incorrect because although the 11.11.0.0/16 network will be denied, any other networks attached to either Router C or Router D will be permitted.
Traffic from network 11.11.0.0 hosts will NOT be discarded because of ACL 10. If the access list were applied to the interface with the access-group command instead of the distribute-list command, this would be the case, but a distribute list blocks routing updates, not normal traffic.
Objective:
Layer 3 Technologies
Sub-Objective:
Configure and verify filtering with any protocol -
Which EIGRP packet type is sent as a multicast when a new route is discovered, and sent as a unicast to synchronize topology tables when neighbors initialize?
- ACK
- Hello
- Update
- Replies
- Queries
Explanation:
EIGRP update packets are sent as a multicast when a new route is discovered, and sent as a unicast to synchronize topology tables when a neighboring router initializes.Whenever EIGRP only needs to communicate with a single neighbor, it sends a unicast to that neighbor instead of the standard multicast. In this case, it unicasts a packet to update a new EIGRP router on the network with the information that all other routers on that network already know.Hellos for neighbor discovery and maintenance are always multicasts.ACKs are hellos without data, and are always unicast.Queries are always multicast.Replies to queries are always unicast.Objective:
Layer 3 Technologies
Sub-Objective:
Describe EIGRP packet types -
Your company has a policy of creating all configurations in text files, checking the files, and then applying the configurations to the devices. Your assistant has presented you with the following partial configuration that she plans to execute on a router:interface S0/0/1ipv6 address 2001:610:FFFF:1::1/64ipv6 ospf 100 area 0ipv6 router ospf 100
router-id 10.1.1.6The configuration is supposed to accomplish the following:Enable IPv6 routing
Assign a router ID
Assign an IPv6 address to the interface
Place the interface in OSPF area 0
Which step does this configuration NOT complete?
- Enable IPv6 routing
- Assign a router ID
- Assign an IPv6 address to the interface
- Place the interface in OSPF area 0
Explanation:
The configuration indicates all steps are complete except for globally enabling IPv6 routing. If that had been done, the configuration output would have reflected it under the interface as follows:interface S0/0/1
ipv6 address 2001:610:FFFF:1::1/64
ipv6 ospf 100 area 0
ipv6 enableipv6 router ospf 100
router-id 10.1.1.6Prior to configuring OSPFv3 on an interface, it must be enabled globally. OSPFv3 is an OSPF version specific to IPv6. The following commands will globally enable OSPF v3. It will then be reflected by the ipv6 enable statement under the interface when viewing the configuration as shown in the fourth line of the output above.Router5(config)# ipv6 unicast-routing
Router5(config)# ipv6 ospf 100
Router5(config-rtr)# router-id 10.1.1.6The problem is not the router ID. The configuration in the scenario does assign a router ID, as indicated by these lines:ipv6 router ospf 100
router-id 10.1.1.6The problem is not the IPv6 address. The configuration does assign an IPv6 address to the interface, as indicated by these lines:interface S0/0/1
ipv6 address2001:610:FFFF:1::1/64OSPF area 0 is not the problem. The configuration does place the interface in OSPF area 0, as indicated by these lines:interface S0/0/1
ipv6 ospf 100 area 0Objective:
Layer 3 Technologies
Sub-Objective:
Configure and verify OSPF for IPv6 -
Which show command displays entries in a router’s Border Gateway Protocol (BGP) table?
- show ip bgp
- show ip bgp table
- show ip bgp topology
- show ip bgp summary
Explanation:
The correct command is show ip bgp.The BGP table lists all the paths that the BGP router has learned. Each destination network listed might have multiple possible paths listed. Given that the criteria are met for each destination network, BGP will choose a path to put in the IP routing table.The BGP table is in many ways analogous to EIGRP’s topology table in that it lists many known paths, not just the best path. Below is an example partial output of the show ip bgp command:

300-410 Part 03 Q09 035 The following facts can be determined from this output:
All of the routes were redistributed into BGP from an IGP. In the status column (located to the left of the Network column and to right of the column where some lines have a > symbol) is a column that is either blank or has an i symbol. In this case, all of the columns are blank. If the status column is blank, then BGP learned the route from an external peer. If it has an i symbol, an iBGP neighbor advertised this path to the router. It was learned from an Interior Gateway Protocol (IGP) and was advertised as a result of executing a network statement on the neighbor under the router bgp context as shown below adding the 30.0.0.0 network under BGP 100.R4(config)#router bgp 100 R4(config-router)#network 30.0.0.0
Four routes will be installed in the routing table. These routes have both an * symbol and a > symbol.
l in the status column. The * symbol indicates that the next hop is valid and the > symbol indicates that this is the best route.The output is slightly different if you specify the network that you are interested in, as shown below in the show ip bgp 214.5.98.0 command output:
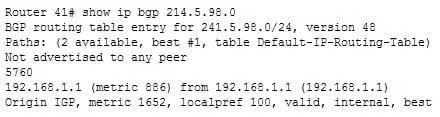
300-410 Part 03 Q09 036 This output focuses solely on the route to the network 214.5.98.0 and provides the following pieces of information:
The neighbor that sent this route is at 192.168.1.1
The AS of the network where 214.5.98.0 is located is 5760
The IGP metric to reach the neighbor that sent this route is 886, as shown by the text 192.168.1.1 (metric 886)
The complete metric to 214.5.98.0 is 1652, as shown in the last line by Origin IGP, metric 1652The commands show ip bgp table and show ip bgp topology are not valid Cisco commands.
The show ip bgp summary command displays the status of BGP connections.
Objective:
Layer 3 Technologies
Sub-Objective:
Explain BGP attributes and best-path selection -
You have enabled RIPng on one of the interfaces of a router with the basic configuration. You have assigned an address to that interface using the ipv6 address command.
Which of the following statements should appear in the output of the show running-config command executed on the router? (Choose all that apply.)
- ipv6 unicast-routing
- ipv6 enable
- ipv6 rip enable
- ipv6 router rip
- ipv6 unnumbered
- ipv6 prefix-list
Explanation:
The ipv6 unicast-routing and ipv6 rip enable statements should appear in the output of the show running-config command.The ipv6 unicast-routing command is one of the basic IPv6 commands that needs to be executed on any router for IPv6 processing. This command is executed in the global configuration mode to allow IPv6 packet forwarding on the router. When it has been executed the ipv6 unicast-routing statement will appear in the output of the show run command.The ipv6 rip enable command allows you to enable RIPng on a router interface. You should execute this command to create a RIPng routing process. When it has been executed the ipv6 rip enable statement will appear in the output of the show run command.The ipv6 router rip command allows you to work with RIPng routing process by entering the router configuration mode for RIPng. It will only appear if modifications have been made to the RIPng routing process, which is not mentioned in this case.The commands to configure a router with RIPng is as follows:rtrA(config)# ipv6 unicast-routing rtrA(config)# interface Fa0/1 rtrA(config-if)# ipv6 rip rip process enable rtrA(config-if)# ipv6 address 2001:1:1:1::1/64
Important note: in the command set above, the command that enables the RIP process on interface Fa0/1 is executed before the command assigning the IPv6 address. The order of execution of those two commands does not matter. However, if a configuration file is copied and pasted into a router, then the order in which the statements appear does matter.
For example, if the partial configuration below were pasted into a router, the IPv6 RIP process 56 would not be enabled on Fa0/0:
ip unicast routing
interface Fa0/0
ipv6 rip 56 enable
ipv6 address 2001:1:1:1::1/64The system would reject the ipv6 rip 56 enable command because an IPv6 address is not yet present. If the commands were reversed in the file, the system would accept the ipv6 rip 56 enable command.
In the scenario, the ipv6 enable command does not appear in the show running-config output. This command enables IPv6 routing on a router interface that has not been assigned an IPv6 address. In this case, an IPv6 address is explicitly assigned to the router interface by using the ipv6 address command. Therefore, the ipv6 enable command is not required.
The ipv6 unnumbered interface type command does not appear in the show running-config output. This command will allow you to enable IPv6 without assigning an IPv6 address to a router interface.
Objective:
Layer 3 Technologies
Sub-Objective:
Describe RIPng -
Company A recently acquired Company B and the network infrastructures are being merged. Both organizations used non-overlapping globally unique network addressing but different Interior Gateway Protocols (IGPs). Initially, multiple WAN links will connect the two organizations. Company A will maintain its core routing protocol, and Company B’s routing protocol will be the edge routing protocol. Two-way redistribution will be used to ensure full network routing capability.What additional routing configuration should be performed to prevent routing loops and suboptimal routing?
- Manually configure static routes.
- Manually configure default routes.
- Manually adjust the administrative distances.
- Manually adjust the local preference attribute.
Explanation:
When routes are being redistributed from the core into the edge and from the edge into the core, the administrative distance (AD) associated with external routes should be modified. This lessens the possibility of sub-optimal routing when multiple routing protocols advertise different paths to the same network. The AD associated with the externally advertised routes should be higher than the internal IGP’s AD. To change the AD for an entire routing protocol, use the distance command. An example and the command syntax are shown below:router(config)#router rip router(config-router)#distance 125
The complete syntax of the distance command is:
distance weight [address mask [ access-list-number | name]
The weight parameter is the AD, which can be a number from 10 to 255. Note that distances 0 through 9 are reserved for system use.
To change only the AD for selected networks, use an access list with the distance command as shown below:
router(config)# access-list 5 permit 10.0.0.0 255.0.0.0 router(config)# access-list 5 permit 11.0.0.0 255.0.0.0 router(config)# access-list 5 permit 12.0.0.0 255.0.0.0 router(config)# router rip router(config-router)# distance 220 0.0.0.0 255.255.255.255 5
The 0.0.0.0 255.255.255.255 portion included with the distance command could hold an address/mask combination for a single address, but it is more common to use an access list.
Objective:
Layer 3 Technologies
Sub-Objective:
Configure and verify redistribution between any routing protocols or routing sources -
Which of the following commands will enable the DHCP and relay services on a Cisco router?
-
RouterA(config)# service dhcp -
RouterA(config)# dhcp enable
-
RouterA(config)# enable dhcp
-
RouterA(config-if)# dhcp enable
-
RouterA(config-if)# service dhcp
Explanation:
Using the service dhcp command at global configuration mode will enable the DHCP and relay services on a Cisco router. By default, these services are already enabled on the router, but they can be disabled using the no service dhcp command. Before the DHCP service can actually function, a pool of addresses must be created and any statically defined addresses (such as the router itself) must be excluded. If the router has two interfaces and needs to issue addresses on both interfaces two pools and two exclusion statements must be present.Below is an example of a complete configuration taken from a partial output of the show run command. This router has two interfaces 10.0.0.1/24 and 192.168.5.1/24, creating the need for two pools and two exclusion statements. It excludes the address ranges 10.0.0.1-10.0.0.5 from the 10.0.0.0/24 pool and excludes 192.168.5.1-192.168.5.5 from the 192.168.5.0/24 pool, and creates a pool for 10.0.0./24 and 192.168.5.0/24.

300-410 Part 03 Q12 037 The commands RouterA(config)# dhcp enable and RouterA(config)# enable dhcp are incorrect because the syntax is incorrect.
The command RouterA(config-if)# dhcp enable is incorrect because the syntax is incorrect and because it is executed in interface configuration mode. Enabling DHCP is done at the global prompt.
The command RouterA(config-if)# service dhcp is incorrect because it is executed in interface configuration mode. Enabling DHCP is done at the global prompt
Objective:
Layer 3 Technologies
Sub-Objective:
Identify, configure, and verify IPv4 addressing and subnetting -
-
You are configuring a DHCP server to service a group of clients that are located on a different subnet than the DHCP server itself. What else must you configure to ensure a successful setup?l
- Relay agent
- Multicast routing
- Unicast routing
- Access list
Explanation:
If a DHCP server needs to service clients in a different subnet, you will need to configure a relay agent. The relay agent service is enable by default but does not function unless you provide the IP address of the remote DHCP server, which is done by executing the ip helper address command on the interface where the address needs to be announced.The fact that the clients are on a different subnet indicates that there is a router between the DHCP server and the clients. The DHCP discover packet that a client sends out is in the form of a broadcast. Routers do not forward broadcast traffic from one segment to the other. Without a relay agent, the DHCP server would never receive the requests.A relay agent resides on the same segment as the clients. When a client sends out a discover packet, the relay agent takes the request, converts it to a unicast packet, and forwards the request to the DHCP server on the other network segment.The relay agent can also be activated on the router that separates the two network segments. To enable the relay agent service on a Cisco router where 172.16.10.2 is the IP address of the DHCP server, use the following command:Router(config-if)# ip helper-address 172.16.10.2A relay agent can also be used to assist in the auto configuration of a switch. Auto configuration is a process whereby:- A switch boots up.
- The switch obtains an IP address, subnet mask, and gateway address (optional).
- The switch uses the DNS server to locate the TFTP server.
- The switch connects to the TFTP server, downloads the configuration file, and applies it.
When the switch must broadcast to locate the DHCP, DNS, or TFTP server, IP helper addresses can be provided for all of these. When the switch broadcasts, a unicast will be sent to all of these addresses.
In following illustration, the FastEthernet0 interface of the router is connected to the subnet containing the switch and the FastEthernet1 interface of the router is connected to the subnet containing the DHCP, DNS, and TFTP servers. The addresses involved are:
- Switch – 10.2.2.2
- Router – F0 10.2.21, F2 20.2.2.2
- DHCP – 20.2.2.5
- DNS – 20.2.2.6
- TFTP – 20.2.2.7
The router that is located between the subnet containing the switch and the subnet containing the DHCP, DNS, and TFTP servers should be configured as shown below:
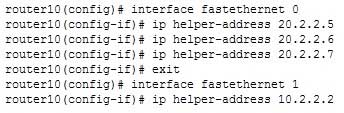
300-410 Part 03 Q13 038 Regardless of whether the ip helper-address command has been used to aid in the DHCP configuration of a switch utilizing auto configuration, or to aid DHCP clients in a different subnet from the DHCP server, the DHCP relay service will provide relay services for the following UDP protocols by default:
Trivial File Transfer Protocol (TFTP) (port 69)
Domain Naming System (DNS) (port 53)
Time service (port 37)
NetBIOS Name Server (port 137)
NetBIOS Datagram Server (port 138)
Boot Protocol (BOOTP) client and server packets (ports 67 and 68)
TACACS service (port 49)
IEN-116 Name Service (port 42)This default behavior can be altered with the IP forward-protocol udp command executed in global configuration mode.
Multicast routing, unicast routing and access lists do not aid in the DHCP communication process.
Objective:
Layer 3 Technologies
Sub-Objective:
Identify, configure, and verify IPv4 addressing and subnetting -
You have two autonomous systems connected by more than one ASBR.
Which strategy does Cisco recommend in this situation?
- Use two-way redistribution.
- Use a default route in both directions.
- Allow routes to be exchanged in one direction, and use a default route in the other direction.
- Manually configure routes in all ASBRs, and update the configuration each time there is a change in either AS.
Explanation:
If there is a single autonomous system border router (ASBR) connecting two autonomous systems (AS), Cisco generally recommends full two-way route redistribution. But when there are multiple ASBRs, as in this scenario, two-way route redistribution may result in routing loops. One solution is to use a default route in one direction and allow routes to be exchanged in the other direction.Default routes in both directions will almost certainly cause routing loops.Manual configuration of static routes would work, but the administrative maintenance necessary when there are changes would be considerable.Objective:
Layer 3 Technologies
Sub-Objective:
Configure and verify redistribution between any routing protocols or routing sources -
Which command can you use to verify that interfaces have been configured in the correct areas and to show timer intervals and neighbor adjacencies for OSPF?
- show ip ospf
- show ip route
- show ip protocol
- show ip ospf database
- show ip ospf interface
Explanation:
The correct answer is show ip ospf interface. This command displays all of the important OSPF parameters that relate to each of the interfaces. Information can be displayed on a per-interface basis if an interface is specified. If none is specified, all interfaces running OSPF will be displayed.
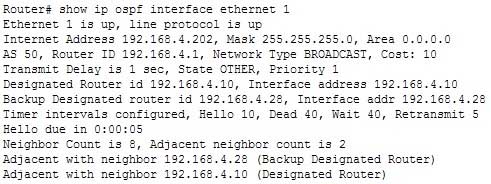
300-410 Part 03 Q15 039 The following commands can be used to monitor and verify OSPF operation:
show ip ospf – displays the number of times the SPF algorithm has run and the default LSU interval, but does not show neighbor adjacencies.
show ip route – displays known routes and how they were discovered, but not timers and neighbor adjacencies.
show ip protocol – displays information about timers, filters, metric, etc. for the entire router, but not OSPF neighbor adjacencies.
show ip ospf database – displays the router ID, the OSPF process ID, and the contents of the topological database, but not adjacencies information or timer values.Objective:
Layer 3 Technologies
Sub-Objective:
Configure and verify OSPF neighbor relationship and authentication -
Refer to the following table:
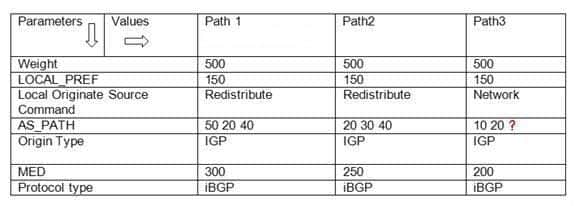
300-410 Part 03 Q16 040 Path1, Path2, and Path3 are the available routes between routers A and B. The bgp always-compare med command is executed for all three routes.What should be the value for the missing ASN (represented by a question mark in the table) so that Path3 becomes the best path between routers A and B based on their MED values?
- 10
- 20
- 30
- 40
Explanation:
The missing autonomous system number (ASN) in the AS_PATH parameter of Path3 should be 40 so that Path3 becomes the best path from A to B. BGP selects the best path by first selecting the first valid path between two routers. If other paths are available between the two routers, BGP compares values of various attributes to select the best available path. In this case, Path 2 is the current best path between routers A and B. The values of various parameters (listed in the table) are compared with Path1 and Path2.While comparing Path1 and Path2, the weight, LOCAL_PREF, local originate source command, length of AS_PATH, and origin type are same. Therefore, these parameters are not useful in determining the best path. However, the MED value of Path2 is lower than that of Path1. As a result, Path2 is selected as the best path because BGP prefers the route with the lesser MED value.BGP now compares the parameter values of Path 2 (the current best path) and Path3. The weight and LOCAL_PREF parameters are same for both routes. Path 2 and Path3 are both local routes originated by using the redistribute and the network commands, respectively. BGP prefers local routes learned by the network or redistribute commands over those that are learned by the aggregate-address command.The AS_PATH parameter specifies the list of AS numbers that comprise the route. The best path should have the shortest value for the AS_PATH parameter. In this case, both Path2 and Path3 consist of three AS numbers and are originated by an IGP. Therefore, the AS_PATH and the origin type parameters are not helpful in determining the best path.Finally, BGP compares the MED values of Path2 and Path3. The MED values are compared only when the first AS number in the AS_PATH is the same for both routes; that is, when both routes begin in the same AS. The first ASN in the AS_PATH parameter of Path2 is 40; therefore, the missing ASN for Path3 should be 40. This allows the comparison of MED values and the selection of Path3 as the best route as it has lower MED value.All the other options are incorrect because a value other than 40 disables the comparison of the MED values between Path2 and Path3. If the MED value is not considered, then BGP determines whether Path3 is an iBGP or eBGP router. BGP selects an iBGP route instead of an eBGP route.Objective:
Layer 3 Technologies
Sub-Objective:
Explain BGP attributes and best-path selection -
Refer to the following exhibit that shows four Cisco routers named rtr1, rtr2, rtr3, and rtr4:

300-410 Part 03 Q17 041 The routers rtr2, rtr3, and rtr4 are eBGP peers of rtr1. In addition, rtr3 and rtr4 are also eBGP peers.
You want to implement the following requirements on rtr1:
The first attribute to select the best path is used.
Advertisements about 10.77.22.0/24 sent by rtr4 will be chosen over the advertisements sent by rtr3.
Which of the following commands should be included in the implementation plan for rtr1 to achieve the desired results? (Each option is a part of the solution. Choose all that apply.)- neighbor 135.90.66.1 route-map set_weight out
- neighbor 135.90.66.6 route-map set_weight in
- route-map set_weight deny 10
- match ip-address 1
- set metric 100
- set weight 100
Explanation:
The following commands should be included in the implementation plan:neighbor 135.90.66.6 route-map set_weight in
match ip-address 1
set weight 100The neighbor 135.90.66.6 route-map set_weight in command specifies a route-map named set_weight for the incoming routing updates from 135.90.66.6 peer. The match ip-address 1 command specifies a criterion to match the IP address as specified in an access list. When the match criterion is met, the action specified in the set weight command is performed.The set weight 100 command sets the weight attribute, which is a Cisco-defined attribute, to 100. The weight attribute is the first to be checked when BGP selects the best path between eBGP routers. This attribute is local to the router on which it is set and cannot be advertised to other routers.The complete set of commands to achieve the desired results is as follows:
access-list 1 permit 10.77.22.0 0.0.0.255
router bgp 444
neighbor 135.90.66.3 remote-as 111
neighbor 135.90.66.1 remote-as 222
neighbor 135.90.66.6 remote-as 333
neighbor 135.90.66.6 route-map set_weight in
route-map set_weight permit 10
match ip-address 1
set weight 100The set metric 100 command should not be included in the implementation plan to achieve the desired results. This command sets the metric to 100; however, the requirement is to use the first attribute to be checked, which is the weight attribute.
The neighbor 135.90.66.1 route-map set_weight out command should not be included in the implementation plan. This command forms an eBGP neighbor relationship with rtr3. The command also uses a route map named set_weight to set the weight attribute for the routes sent by rtr1. However, the weight attribute is local to rtr1 and cannot be set for outbound routes.
The route-map set_weight deny 10 command should not be specified in the implementation plan to achieve the desired results. This command creates a route map named set_weight. The deny keyword in this command indicates that if the match criterion is satisfied, then the set action is not performed. The permit keyword should be specified instead of the deny keyword to perform the set action when a match occurs.
Objective:
Layer 3 Technologies
Sub-Objective:
Identify suboptimal routing -
Examine the exhibit.
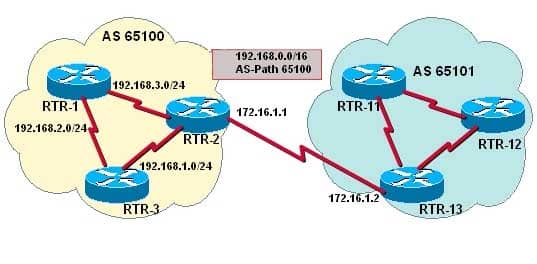
300-410 Part 03 Q18 042 You have determined that RTR2 is not advertising the CIDR summary address 192.168.0.0 to the other routers in AS 65100. Which set of configuration commands will enable the BGP router RTR2 to announce the network prefix 192.168.0.0/16 to the other routers in the AS 65100?
- router bgp 65100
neighbor 172.16.1.2 remote-as 65100
neighbor 192.168.3.2 remote-as 65100
network 192.168.3.0 - router bgp 65100
neighbor 172.16.1.2 remote-as 65101
neighbor 192.168.3.2 remote-as 65100
network 192.168.0.0 - router bgp 65100
neighbor 172.16.1.2 remote-as 65100
neighbor 192.168.3.2 remote-as 65100
network 192.168.0.0 mask 255.255.0.0
ip route 192.0.0.0 255.0.0.0 null 0 - router bgp 65100
neighbor 172.16.1.2 remote-as 65101
neighbor 192.168.3.2 remote-as 65100
network 192.168.0.0 mask 255.255.0.0
ip route 192.168.0.0 255.255.0.0 null 0
Explanation:
Issuing the following commands will cause RTR2 to advertise the CIDR block 192.168.0.0/16 to the other routers by using BGP:RTR2(config)# router bgp 65100 RTR2(config-router)# neighbor 172.16.1.2 remote-as 65101 RTR2(config-router)# neighbor 192.168.3.2 remote-as 65100 RTR2(config-router)# network 192.168.0.0 mask 255.255.0.0 RTR2(config-router)# ip route 192.168.0.0 255.255.0.0 null 0
The network command specifies the address that will be inserted into the BGP table. Without the mask keyword, the classful network will be assumed. Because 255.255.0.0, or /16, is not the natural mask for any Class C address, the mask keyword must also be specified. Thus, 192.168.0.0 and 255.255.0.0 identify the desired address and mask of the 192.168.0.0/16 network prefix.
The router checks the IP forwarding table for an exact match before it advertises the route. Without a matching entry in the IP forwarding table, that route will not be advertised. RTR2 must be able to advertise a CIDR block and not the individual subnets. A static route is required because BGP requires that a match of the network prefix be present in the forwarding table when using the network command with the mask keyword. Therefore, to ensure an exact match for the identified prefix exists in the IP forwarding table, and to ensure that the prefix will always be advertised, a static route for 192.168.0.0/16 to null 0 is also required.
The syntax for the network command is shown below:
network network-number [ mask network-mask ] [ route-map map-tag ]
The parameters are:
mask – This parameter is optional and identifies the network or subnetwork to advertise.
route-map – This parameter is optional and identifies a preconfigured route-map that will be used to filter specific addresses from being advertised.The following command set is missing the mask keyword in the network command and the command to create a static route to null 0. The address used in the network command is also incorrect. It should 192.168.0.0:
router bgp 65100 neighbor 172.16.1.2 remote-as 65100 neighbor 192.168.3.2 remote-as 65100 network 192.168.3.0
The following command set is missing the mask keyword in the network command and the command to create a static route to null 0:
router bgp 65100 neighbor 172.16.1.2 remote-as 65101 neighbor 192.168.3.2 remote-as 65100 network 192.168.0.0
The following command set uses an incorrect mask (255.0.0.0) in the command that creates the static route to null 0. It should be 255.255.0.0:
router bgp 65100 neighbor 172.16.1.2 remote-as 65100 neighbor 192.168.3.2 remote-as 65100 network 192.168.0.0 mask 255.255.0.0 ip route 192.0.0.0 255.0.0.0 null 0
Objective:
Layer 3 Technologies
Sub-Objective:
Describe, configure, and verify BGP peer relationships and authentication - router bgp 65100
-
Which method of advertising networks from an autonomous system into BGP can result in the most instability?
- Using the network command
- Redistributing static routes into BGP
- Redistributing dynamic routes into BGP
- Redistributing static routes into IBGP
Explanation:
Redistributing dynamic IGP routes into BGP can result in instability, and is not recommended. Dynamic routes can disappear from the routing table, and even flap up and down constantly if there are link problems, especially with WAN links. If the networks are redistributed into BGP, their flapping can result in BGP updates about the route changing status, resulting in instability for BGP. Most ISPs guard against unstable routes and might threaten to cut off your BGP connectivity if you have flapping routes that cause BGP instability in their networks. The network command and redistributed static routes, on the other hand, tend not to change state so often. As a result, they are considered much more stable from a BGP perspective.Objective:
Layer 3 Technologies
Sub-Objective:
Configure and verify manual and autosummarization with any routing protocol -
Consider the following output of the show ip bgp summary command:

300-410 Part 03 Q20 043 Which of the following neighbors have an established connection with RouterA?
- 10.1.1.1
- 10.2.1.1
- 10.3.1.1
- 10.4.1.1
- 10.5.1.1
Explanation:
The neighbor with the IP address 10.2.1.1 has an established connection with RouterA. This is because the State/PfxRcd value for this neighbor is a number, 15, which indicates the number of prefixes received by RouterA from the neighbor. The prefixes are exchanged between BGP neighbors through the update message, which can be transmitted only if an established connection exists between the neighbors. An established connection exists between two neighbors if the local router is in Open Confirm state and it receives a KEEPALIVE or an UPDATE message.The connection between RouterA and the neighbor with the IP address 10.1.1.1 is not established. This is because the State/PfxRcd value for this neighbor is OPENSENT. In this state, RouterA sends an OPEN message to a neighbor to determine the parameters for establishing a connection. The OPENSENT state occurs before the connection is established.The connection between RouterA and the neighbor with the IP address 10.3.1.1 is not established. This is because the State/PfxRcd value for this neighbor is IDLE. In this state, RouterA does not accept any incoming connections from the neighbor.The connection between RouterA and the neighbor with the IP address 10.4.1.1 is not established. This is because the State/PfxRcd value for this neighbor is ACTIVE. In this state, RouterA is attempting to establish a BGP peering session but it is not yet complete.The connection between RouterA and the neighbor with the IP address 10.5.1.1 is not established. This is because the State/PfxRcd value for this neighbor is OPENCONFIRM. In this state, RouterA waits for a KEEPALIVE or NOTIFICATION message from the neighbor.Objective:
Layer 3 Technologies
Sub-Objective:
Describe, configure, and verify BGP peer relationships and authentication