300-735 : Automating Cisco Security Solutions (SAUTO) : Part 03
-
Which of the following features are supported on a Cisco ASA operating in multiple context mode? (Select 2 choices.)
- RIP
- active/active failover
- active/standby failover
- QoS
- multicast routing
Explanation:
Active/active failover and active/standby failover are supported on a Cisco Adaptive Security Appliance (ASA) operating in multiple context mode. In multiple context mode, you can divide a single ASA into multiple security contexts, which function as individual virtual devices with unique policies, even though they reside on a single piece of hardware. Multiple context mode enables the separation of different departments or business units that share a single physical ASA. When an ASA operating in transparent firewall mode is placed into multiple context mode, each context will also operate in transparent mode.
The following features are not supported when an ASA is operating in multiple context mode:
– Routing Information Protocol (RIP)
– Open Shortest Path First version 3 (OSPFv3)
– Threat detection
– Multicast routing
– Unified Communication Services
– Quality of Service (QoS)
In an active/standby configuration, one ASA serves as the active unit and forwards traffic for network clients. A second ASA functions as a standby unit, which monitors the status of the active unit but does not forward traffic for network clients. If a failover event is triggered, the standby unit takes on the role of the active unit. By contrast, an active/active failover configuration enables both ASAs to forward traffic for a select group of security contexts. With active/active failover, two failover groups exist on each ASA. When a failover event is triggered, the corresponding failover group on a standby unit can become active or the entire standby unit can become the new active unit. The type of failover resolution depends on the nature of the failover event.
In multiple context mode, as in single context mode, an ASA can also be configured to run in either routed firewall mode or transparent firewall mode. In routed mode, the firewall acts as a Layer 3 device by routing traffic between different subnets. In transparent mode, the firewall acts as a Layer 2 bridge by passing traffic through to destinations on the same subnet but not routing traffic to a destination on a different subnet. In addition to the unsupported features listed above, the following features are not supported on an ASA operating in transparent firewall mode:
– Dynamic Domain Name System (DNS)
– Dynamic Host Configuration Protocol (DHCP) relay -
Refer to the following partial sample output from the show crypto ipsec sa command:
<output omitted>
interface: FastEthernet0/0
Crypto map tag: aesmap, local addr 10.10.10.2
protected vrf: (none)
local ident (addr/mask/prot/port):
(192.168.1.0/255.255.255.0/0/0) remote ident
(addr/mask/prot/port): (172.16.17.0/255.255.255.0/0/0)
current_peer 10.20.20.2 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 2, #pkts encrypt: 2, #pkts digest: 2
#pkts decaps: 2, #pkts decrypt: 2, #pkts verify: 2
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 10.10.10.2, remote crypto endpt.:
10.20.20.2 path mtu 1500, ip mtu 1500, ip mtu idb
FastEthernet0/0 current outbound spi:
0x82E64150(2196128080)
PFS (Y/N): N, DH group: none
<output omitted>Which of the following statements is true? (Select the best answer.)
- There is a configuration mismatch between the local peer IP address and the local subnet address.
- No DH group is configured in the IKE policy.
- All encrypted traffic will be tagged with the value “aesmap”.
- At least one IPSec SA is established and operational.
Explanation:
The following partial output from the show crypto ipsec sa command indicates that at least one IP Security (IPSec) security association (SA) is established and operational:
<output omitted>interface: FastEthernet0/0 Crypto map tag: aesmap, local addr 10.10.10.2 protected vrf: (none) local ident (addr/mask/prot/port):
(192.168.1.0/255.255.255.0/0/0) remote ident
(addr/mask/prot/port): (172.16.17.0/255.255.255.0/0/0)
current_peer 10.20.20.2 port 500
PERMIT, flags={origin_is_acl,}#pkts encaps: 2243, #pkts encrypt: 2243, #pkts digest: 2243 #pkts decaps: 2210, #pkts decrypt: 2210, #pkts verify: 2210
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0 #send errors 0, #recv errors 0
local crypto endpt.: 10.10.10.2, remote crypto endpt.:
10.20.20.2 path mtu 1500, ip mtu 1500, ip mtu idb
FastEthernet0/0
current outbound spi: 0x82E64150(2196128080)
PFS (Y/N): N, DH group: none
<output omitted>
The show crypto ipsec sa command displays detailed information about IPSec SAs, including the IP addresses of the crypto endpoints (IPSec peers), the number of packets encrypted and decrypted, the security protocol, and the corresponding Security Parameter Indices (SPIs). In this scenario, the partial command output indicates that the router should use the outbound SPI with a value of 0x82E64150 (2196128080) when sending encrypted packets from the local peer, 10.10.10.2, to the remote peer 10.20.20.2. The SPI is one of the components used to uniquely identify an IPSec SA.
Each IPSec SA is uniquely identified by its corresponding IPSec peer address, security protocol, and SPI. Because IPSec SAs are unidirectional, two SAs are required between active IPSec peers: an inbound SA and an outbound SA. The SPI associated with the outbound SA is generated by the local peer during phase
2 of the Internet Key Exchange (IKE) negotiation process and is used by the remote peer as the inbound SPI associated with this SA. Likewise, the SPI associated with the inbound SA on the local peer corresponds to the outbound SPI that was generated by the remote peer during its portion of phase 2 negotiations. Once phase 2 negotiations are complete and at least one IPSec SA is operational, the router can begin sending and receiving encrypted traffic. In this scenario, the partial command output indicates that 2,243 packets have been encrypted and 2,210 packets have been decrypted since IKE phase 2 negotiations completed and the IPSec SA was created.
The command output in this scenario does not indicate that a DiffieHellman (DH) group is not configured in the IKE policy. Although the output contains a field named DH groupwith a value of none, this field corresponds to the DH group configured for perfect forward secrecy (PFS), not to the DH group configured in an IKE policy. PFS is used to optionally encrypt IKE keying data during phase 1 negotiations. The PFS (Y/N): N field in the partial output indicates that PFS has not been configured and thus no corresponding DH can be found.
The command output does not indicate that all encrypted traffic will be tagged with the value “aesmap”. The Crypto map tag: aesmap field in the partial command output indicates the name of the IPSec crypto map that is associated with the displayed interface. A crypto map describes which traffic should be encrypted, the remote peer IP address, and the transform set that should be used to encrypt the data. -
Which of the following statements is true regarding a HIDS? (Select the best answer.)
- It can monitor the network for port scans.
- It can identify spoofing attacks.
- It can analyze OSspecific protocols, such as SMB.
- It can delay packets during reassembly.
Explanation:
A Hostbased Intrusion Detection System (HIDS) can analyze operating system (OS)specific protocols, such as Server Message Block (SMB). Intrusion Detection Systems (IDSs) are primarily used for monitoring network traffic and do not sit inline with traffic flow. Because IDS devices do not sit inline, they do not delay the flow of packets during reassembly and analysis. A HIDS can be used to monitor traffic on a single host, whereas a Networkbased IDS (NIDS) can be used to monitor all network traffic.
A hostbased solution, such as a HIDS or a Hostbased Intrusion Preventions System (HIPS), has direct access to the host OS and can typically understand OSspecific protocols and applications based on the behavior identified in kernellevel audit trails. By contrast, a networkbased solution, such as a NIDS or a Networkbased IPS (NIPS), has limited information about the host OS and its applications.
The detailed information about a particular host, its applications, and its behaviors enables a HIDS to implement policies that can be tailored to the host and that can be much more restrictive than policies implemented by a NIDS, most of which implement policies that impact the entire network. In addition, a HIDS can analyze traffic from encrypted sessions that are initiated by or terminated on the host.
By contrast, a NIDS does not have access to OSspecific information and cannot analyze OSspecific protocols and applications. However, because a NIDS is not installed on a single host, it can gather intelligence about threats such as port scans and spoofing attacks, which can affect multiple hosts throughout the network. In addition, because a NIDS is not installed on a host, it is immune to attacks that might compromise a host and its HIDS. -
Which of the following statements is true regarding OWASP? (Select the best answer.)
- It is exclusively a North American nonprofit organization.
- It endorses products from HP and Symantec.
- It releases security materials under FLOSS licenses.
- It requires membership to download security tools such as ZAP.
Explanation:
The Open Web Application Security Project (OWASP) releases security materials under Free/Libre and Open Source Software (FLOSS) licenses. OWASP is a multinational, notforprofit organization that provides frameworks, documentation, tools, and community forums with a focus on application security. For example, one of the OWASP Flagship projects is the Software Assurance Maturity Model (SAMM), which is an open framework used to guide an organization in making software security decisions that are in alignment with the organization’s risk profile. Like all OWASP documentation, the SAMM is licensed under the Creative Commons AttributionShare Alike 3.0 License, which is a common FLOSS license that allows redistribution and modification of the original content with the appropriate attribution and the requirement to distribute the derivative work under the same license as the original.
Although OWASP has many financial supporters, including Adobe, Akamai, HP, and Symantec, it does not endorse any particular company or product. According to the code of ethics published in its bylaws, OWASP must maintain and affirm its objectivity and reject inappropriate pressure from the technology industry. Therefore, OWASP strives to avoid affiliation with any technology company and to maintain its presence as an unbiased source of information about application security.
OWASP offers several different membership levels, each of which offers various benefits, such as reduced advertising costs, discounted conference sponsorship rates, and the ability to vote in OWASP elections. However, membership is not required to access or download any of the documentation or tools offered by OWASP, including Flagship projects such as the OWASP Zed Attack Proxy (ZAP). ZAP is an integrated penetration testing tool for web applications. -
Which of the following best describes a MAC spoofing attack? (Select the best answer.)
- using GARP messages to associate an attacker’s MAC address with the IP address of a valid host on the network
- sending forged frames with the intention of overwhelming a switch’s CAM table
- replacing the IP address of a legitimate website with the IP address of a malicious website
- using the MAC address of another host on the network in order to bypass port security measures
Explanation:
Of the choices available, using the Media Access Control (MAC) address of another host on the network in order to bypass port security measures best describes a MAC spoofing attack. Normally, the MAC address associated with a host corresponds to the unique, burnedin address (BIA) of its network interface. However, in a MAC spoofing attack, a malicious user virtually modifies the BIA to match the MAC address of the legitimate host on the network. Mimicking the MAC address of a known host can be used to overcome simple security measures such as Layer 2 access control lists (ACLs).
Using gratuitous Address Resolution Protocol (GARP) messages to associate an attacker’s MAC address with the IP address of a valid host on the network best describes an ARP poisoning attack, not a MAC spoofing attack. In an ARP poisoning attack, the attacker sends GARP messages to a host. The GARP messages associate the attacker’s MAC address with the IP address of a valid host on the network. Subsequently, traffic sent to the valid host address will go through the attacker’s computer rather than directly to the intended recipient.
Sending forged frames with the intention of overwhelming a switch’s content addressable memory (CAM) table best describes a MAC flooding attack, not a MAC spoofing attack. In a MAC flooding attack, a malicious user generates thousands of forged frames with the intention of overwhelming the switch’s CAM table, which stores learned MAC addresses. Once this table is flooded, the switch can no longer make intelligent forwarding decisions and all traffic is flooded. This allows the attacker to view all data sent through the switch because all traffic will be sent out each port. Implementing port security can help mitigate MAC flooding attacks.
Replacing the IP address of a legitimate website with the IP address of a malicious website best describes a Domain Name System (DNS) poisoning attack, not a MAC spoofing attack. DNS poisoning is an attack that modifies the DNS cache by providing invalid information. In a DNS poisoning attack, a malicious user attempts to exploit a DNS server by replacing the IP addresses of legitimate hosts with the IP address of one or more malicious hosts. Because the DNS cache of the attacked server is poisoned, it will reply to DNS requests with the IP address of the malicious hosts rather than the IP address of the legitimate hosts. -
You issue the show zone security command on a Cisco router and receive the following command output:
RouterA#show zone security
zone self
Description: System defined zone
zone inside
Member Interfaces:
FastEthernet0/0
FastEthernet0/1
zone outside
Member Interfaces:
Serial0/0/0zone dmz
Member Interfaces:
Serial0/0/1Based on the command output, to which zones can the S0/1/0 interface send traffic? (Select the best answer.)
- S0/1/0 can send traffic to the dmz zone.
- S0/1/0 can send traffic to the outside zone.
- S0/1/0 can send traffic to the inside zone, but only in response to traffic initiated from the inside zone.
- S0/1/0 can send traffic to any zone.
- S0/1/0 cannot send traffic to any configured zones.
Explanation:
In this scenario, the S0/1/0 interface cannot send traffic to any configured zones. S0/1/0 is not a member of any zones, as shown by the following output from the show zone security command:
RouterA# show zone security
zone self
Description: System defined zone
zone inside
Member Interfaces:
FastEthernet0/0
FastEthernet0/1
zone outside
Member Interfaces:
Serial0/0/0zone dmz
Member Interfaces:
Serial0/0/1Traffic cannot flow between an interface that does not belong to a security zone and an interface that does belong to a security zone. Therefore, S0/1/0 cannot send traffic to Fa0/0, Fa0/1, S0/0/0, or S0/0/1. However, S0/1/0 can send traffic to S0/1/1 because S0/1/1 is not a member of any security zone.
Even if S0/1/0 were a member of the outside zone, S0/1/0 would not be able to send traffic to the inside zone or dmz zone. When no zone pair exists for a pair of zones, traffic is blocked by default. Traffic is allowed to pass freely between interfaces within the same zone.
If S0/1/0 were a member of the dmz zone, S0/1/0 would be able to send traffic to the inside zone only in response to traffic initiated from the inside zone. RouterA is configured to allow Telnet traffic and traffic sent to 10.2.2.3 from the inside zone to the dmz zone and to allow return traffic from the dmz zone to the inside zone for these sessions. -
Which of the following features can cause a switch port to enter the errdisable state? (Select the best answer.)
- BPDU guard
- PortFast
- root guard
- loop guard
Explanation:
The BPDU guard feature can cause a switch port to enter the errdisable state. The BPDU guard feature should be enabled on PortFast enabled ports so that BPDU guard can prevent a rogue switch from modifying the Spanning Tree Protocol (STP) topology and becoming the root bridge. When such a port receives a bridge protocol data unit (BPDU), BPDU guard immediately puts that port into the errdisable state and shuts down the port. The port must then be manually reenabled, or it can be recovered automatically through the errdisable timeout function. BPDU guard should not be enabled on ports that are connected to other switches.
PortFast is a feature that should be used only on switch ports that are connected to end devices, such as user workstations or print devices. Because PortFast immediately transitions a port to the STP forwarding state, skipping over the listening and learning states, steps should be taken to ensure that a switch that is inadvertently or intentionally connected to the port cannot influence the STP topology.
The root guard feature, when enabled on a port, prevents superior BPDUs received on a neighbor switch connected to that port from becoming the root bridge. If superior BPDUs are received on a port enabled with root guard, the port enters the rootinconsistent state and no data will flow through that port until the port stops receiving superior BPDUs.
The loop guard feature prevents nondesignated ports from inadvertently forming bridging loops if the steady flow of BPDUs is interrupted. When the port stops receiving BPDUs, loop guard puts the port into the loopinconsistent state, which keeps the port in a blocking state. After the port starts receiving BPDUs again, loop guard enables the port to transition through the normal STP states. -
Which of the following are not considered NGE cryptographic algorithms and should be avoided according to Cisco? (Select 2 choices.)
- DH768
- SHA256
- ECDH384
- SHA512
- DH1024
Explanation:
DiffieHellman (DH) with a 768bit modulus (DH768) and DH with a 1,024bit modulus (DH1024) are not considered Next Generation Encryption (NGE) cryptographic algorithms and should be avoided according to Cisco. NGE algorithms are a collection of cryptographic technologies that are efficient, scalable, and expected to provide reliable security for at least the next decade. Because of recent advances in computing power, many cryptographic algorithms no longer provide adequate security. DH768 and DH1024 do not provide a level of security that is likely to meet the confidentiality requirements of the enterprise over the next decade.
Increasing the modulus size used by an algorithm can provide a higher level of security? however, if the algorithm is inherently inefficient, the increased modulus size can adversely affect the performance of the device using the algorithm. For maximum security without using an NGE, Cisco recommends using DH with a 3,072bit modulus (DH3072)? however, because DH is not particularly efficient when configured with a large modulus, Cisco considers a 2,048 bit modulus as an acceptable compromise between security and efficiency. Any modulus size less than 2,048 bits, such as 1,024 bits or 758 bits, is not considered to provide an acceptable level of security.
ECDH384, Secure Hash Algorithm (SHA) with a 256bit digest (SHA256), and SHA with a 512bit digest (SHA512) are all considered NGE cryptographic algorithms according to Cisco. SHA256 and SHA512 are components of the set of cryptographic algorithms known as SHA2. -
You want to configure a router so that networkbased CLI access is limited to SSH connections that are received on a specified interface.Which of the following Cisco IOS features should you configure to achieve your goal? (Select the best answer.)
- CoPP
- CPPr
- MPP
- uRPF
Explanation:
You should configure Management Plane Protection (MPP) on a Cisco router to ensure that networkbased commandline interface (CLI) access is limited to Secure Shell (SSH) connections that are received on a specified interface. MPP enables you to specify one or more interfaces as management interfaces. A management interface is an interface that is permitted to receive management traffic, which is traffic from a specific set of network protocols that is destined for the router. Once MPP is enabled, only specified types of management traffic are permitted on their respective management interfaces. For example, you could configure a router’s FastEthernet 0/0 interface to permit SSH and Secure Hypertext Transfer Protocol (HTTPS) traffic and its FastEthernet 0/1 interface to permit Trivial File Transfer Protocol (TFTP) traffic. Without MPP, you would need to create the appropriate access control lists (ACLs) and apply them in the inbound direction to every interface on the router if you wanted to limit access to one or more interfaces and management protocols.
You should not configure Control Plane Policing (CoPP). CoPP is a Quality of Service (QoS) feature that can be used to limit the type and amount of traffic that reaches the control plane. Control plane traffic is traffic that is destined to the router and that requires CPU intervention for processing. Examples of control plane traffic are routing protocol updates, SSH sessions, and Hypertext Transfer Protocol (HTTP) connections. Because control plane traffic requires CPU intervention, it is possible to overload the CPU with a surge of traffic. When the CPU is overloaded, the router might be unable to update its routing information and transit traffic can be affected. CoPP enables you to configure QoS rates for various traffic types to ensure that sufficient processing time is available for critical protocols. CoPP policies are applied globally and cannot be limited to a single router interface.
You should not configure Control Plane Protection (CPPr). CPPr enhances the capabilities of CoPP by providing more granular control over control plane traffic. With CPPr, traffic is classified into three levels of control instead of the single level of control provided by CoPP. In addition, CPPr provides the ability to drop packets that are destined to Transmission Control Protocol (TCP) or User Datagram Protocol (UDP) router ports that are either close or not listening. CPPr can also limit the number of packets from a particular protocol that are permitted into the control plane IP input queue. Like CoPP, CPPr policies are applied globally and cannot be limited to a single router interface. You should not configure unicast Reverse Path Forwarding (uRPF). uRPF is an antispoofing mechanism that verifies that the source address of a packet is reachable from the interface on which the packet was received. If uRPF is used in conjunction with an ACL, it can cause packets to become packetswitched. Packet switching requires CPU intervention and can create a burden on the control plane. -
Which of the following describes a TPM? (Select the best answer.)
- an independent cryptographic processor embedded into computers
- a system of assigning data to various categories
- a system used to provide services on demand from remote locations
- a process of remotely initiating the deletion of data stored on a device
Explanation:
An independent cryptographic processor embedded into computers describes a Trusted Platform Module (TPM). A TPM provides hardwarebased authentication and full disk encryption services. Because the encryption keys are stored in the TPM module, any data stored on the drive cannot be decrypted once the drive is removed from the original device. TPM uses an encrypted memory module, which provides an additional security layer for properties such as passwords, digital certificates, and encryption keys.
Classification of information, also known as data classification, can be described as a system of assigning data to various categories. Each category should possess a unique policy outlining how data is to be stored, protected, accessed, and disposed of. The policy should also indicate who has permission to participate in the storage, protection, access, and disposal of the data within that category.
Cloud computing can be described as a system used to provide services on demand from remote locations. Cloud computing allows for computer processes that are typically hosted internally to be moved to an external provider, which can reduce the burden on system and network resources. When a provider cloud is used, access to applications, storage space, and other services can be provided on demand without requiring the services to be installed on individual workstations. The use of cloudbased services can simplify IT management by reducing or eliminating the time required to install, upgrade, and manage services.
A remote wipe can be described as the process of remotely initiating the deletion of data stored on a device. A remote wipe works by sending a command to the device through the Internet? after the device establishes a connection to the Internet, the device receives the command and the process of deleting the data is initiated. A user whose laptop or smart phone has been stolen may perform a remote wipe to prevent the thief from accessing confidential information. -
Which of the following are not default values in an IKE policy on an ASA running software version 8.4 or higher? (Select 2 choices.)
- PSKbased authentication method
- 168bit DES encryption algorithm
- 1024bit DH group
- MD5 hash algorithm
- 14,400second lifetime
Explanation:
The Message Digest 5 (MD5) algorithm and a 14,400second lifetime are not default values in an Internet Key Exchange (IKE) policy on a Cisco Adaptive Security Appliance (ASA) running software version 8.2. Virtual private network (VPN) peers establish a connection through a series of negotiations and authentications. Initially, the VPN peers negotiate an IKE security association (SA) and establish a tunnel for key management and authentication. This initial phase is referred to as IKE phase 1. The key management tunnel is used to protect the subsequent negotiation of IP Security (IPSec) SAs. This secondary negotiation phase is referred to as IKE phase 2.
Each VPN peer defines a collection of security parameters in an IKE policy. These parameters are used to negotiate the creation of the key management tunnel in IKE phase 1. There are six required parameters in an IKE policy:
– Policy priority – specifies the order in which policies are negotiated with a peer
– Authentication method – indicates whether a preshared key (PSK) or an RSA digital certificate is used to verify the identity of an IKE peer
– Encryption algorithm – indicates the data protection method used to secure IKE traffic
– Hashbased Message Authentication Code (HMAC) algorithm – indicates the data integrity method used to verify the integrity of IKE traffic
– DiffieHellman (DH) group – specifies how keying material is generated between IKE peers
-Lifetime – specifies the length of time that a key is considered valid? the default is 86,400 seconds, or 24 hoursIf an IKE policy does not specify a parameter and its associated value, the ASA will use the default value. The default IKE policy settings are shown below:
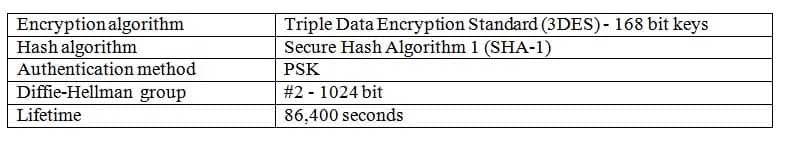
300-735 Part 03 Q11 017 The default IKE policy settings are combined with the configuration parameters specified in the running configuration. For example, because the following block of commands does not specify an HMAC algorithm, an ASA running software revision 8.4 or higher would use the default value, which is SHA1:
ASA(config)#crypto ikev1 policy 1
ASA(configikev1policy)#authentication rsasig
ASA(configikev1policy)#encryption aes 192
ASA(configikev1policy)#group 1
ASA(configikev1policy)#lifetime 14400
In order for VPN peers to successfully negotiate a key management tunnel during IKE phase 1, the peers must agree on security parameters. For example, when ASA1 sends an IKE policy proposal to ASA2, the IKE policy is compared with the IKE policies defined on ASA2. The proposed policy must be an exact match to one of ASA2’s locally defined policies? otherwise, it will be rejected. The one exception to this rule is the value of the IKE lifetime parameter. An IKE lifetime is considered a match if the value specified by the remote peer is less than or equal to the IKE lifetime defined in the local policy. If the IKE lifetime value is less than that of the local policy, the ASA will use the lesser of the two values. -
Which of the following is specifically filtered by a URL filtering subscription service on a Cisco router? (Select the best answer.)
- traffic sent from specific domains
- traffic that contains specific keywords
- traffic that contains malicious software
- traffic that matches predefined categories
Explanation:
On a Cisco router, traffic that matches predefined categories is filtered by a Uniform Resource Locator
(URL) filtering subscription service. URL filtering inspects Hypertext Transfer Protocol (HTTP) requests and blocks access to websites that match certain criteria. Subscription based URL filtering services, which are offered by Trend Micro, Websense, and Secure Computing, assign websites to categories, which are used by administrators to limit or block access to these sites. URL filtering is commonly configured on perimeter routers to prevent users from inadvertently accessing URLs that have been deemed inappropriate or identified as containing malware.
Although a URL filtering subscription service does not specifically filter traffic that contains malicious software as a payload, you can configure the local URL filtering service so that access to websites known to distribute malicious software is filtered. For example, if a particular URL is known to harbor malware, you could filter that specific URL or the entire domain. However, to filter traffic that contains malicious software as a payload, you should install an Intrusion Prevention System (IPS). -
Which of the following actions could you take to mitigate VLAN hopping attacks? (Select the best answer.)
- Implement sticky MAC addresses.
- Change the native VLAN on trunk ports to an unused VLAN.
- Implement DAI.
- Limit the number of MAC addresses permitted on a port.
Explanation:
You should change the native virtual LAN (VLAN) on trunk ports to an unused VLAN to mitigate VLAN hopping attacks. In a VLAN hopping attack, an attacker sends doubletagged 802.1Q frames over a trunk link. A doubletagged frame is an Ethernet frame containing two distinct 802.1Q headers. Although doubletagging can be used as a legitimate way to tunnel traffic through a network and is commonly used by service providers, it can also be used by an attacker to circumvent security controls on an access switch. In a VLAN hopping attack, the attacker attempts to inject packets into other VLANs by accessing the native VLAN on a trunk and sending doubletagged 802.1Q frames to the switch. The switch strips the outer 802.1Q header from the received frame and then forwards the frame, which still includes an 802.1Q header, across a trunk port to the VLAN of the target host. A successful VLAN hopping attack enables an attacker to send unidirectional traffic to other VLANs without the use of a router.
Implementing sticky secure Media Access Control (MAC) addresses can help mitigate MAC spoofing attacks. In a MAC spoofing attack, an attacker uses the MAC address of another known host on the network in order to bypass port security measures. MAC spoofing can also be used to impersonate another host on the network.
Limiting the number of MAC addresses permitted on a port can help mitigate MAC flooding attacks. In a MAC flooding attack, an attacker generates thousands of forged frames every minute with the intention of overwhelming the switch’s MAC address table. Once this table is flooded, the switch can no longer make intelligent forwarding decisions and all traffic is flooded. This allows the attacker to view all data sent through the switch because all traffic will be sent out each port. A MAC flooding attack is also known as a content addressable memory (CAM) table overflow attack.
Implementing Dynamic ARP Inspection (DAI) can help mitigate Address Resolution Protocol (ARP) poisoning attacks. In an ARP poisoning attack, which is also known as an ARP spoofing attack, the attacker sends a gratuitous ARP (GARP) message to a host. The GARP message associates the attacker’s MAC address with the IP address of a valid host on the network. Subsequently, traffic sent to the valid host address will go through the attacker’s computer rather than directly to the intended recipient. -
Which of the following devices typically sits inline? (Select the best answer.)
- a HIDS
- a HIPS
- a NIDS
- a NIPS
Explanation:
A Networkbased Intrusion Prevention System (NIPS) typically sits inline, which means that all traffic from the external network must flow through and be analyzed by the NIPS before the traffic can enter the internal network. Therefore, a NIPS can detect and drop malicious traffic, which prevents malicious traffic from infiltrating the internal network. A NIPS can work in conjunction with a network firewall? however, Cisco recommends deploying a NIPS on the inside interface of the firewall in order to prevent the NIPS from wasting resources by analyzing traffic that will ultimately be blocked by the firewall. This enables the NIPS to efficiently analyze the traffic that the firewall permits onto the network, rather than processing every inbound packet.
A Hostbased Intrusion Prevention System (HIPS) is software that is installed on a host device and analyzes traffic that enters the host. Any traffic that is suspected to be malicious is blocked before it can affect the host device. Many modern, hostbased firewall applications include components that provide HIPS functionality.
A Networkbased Intrusion Detection System (NIDS) typically does not sit inline in the flow of traffic. Instead, a NIDS merely sniffs the network traffic by using a promiscuous network interface. Because network traffic does not flow through a NIDS, the NIDS can detect malicious traffic but cannot prevent it from infiltrating the network. When a NIDS detects malicious traffic, it can alert other network devices in the traffic path so that further traffic can be blocked. In addition, a NIDS can be configured to send a Transmission Control Protocol (TCP) reset notification or an Internet Control Message Protocol (ICMP) unreachable message to the source and destination addresses.
A Hostbased Intrusion Detection System (HIDS) is software that is installed on a host device and analyzes changes made to the device. The primary difference between a HIDS and a HIPS is that a HIPS can detect and block malicious traffic before the traffic can affect the host? a HIDS can detect a threat only after it has already affected the host. Two examples of HIDS applications are Tripwire and OSSEC. Tripwire monitors the integrity of critical files and sends alerts if changes are made to them. OSSEC is an opensource application that monitors logs, registries, and critical files. In addition, OSSEC can detect rootkits, which are malware processes that actively hide their presence from the host operating system. -
Which of the following statements is true regarding a stateless packetfiltering firewall? (Select the best answer.)
- It can operate at Layer 4 of the OSI model.
- It is more secure than a stateful packetfiltering firewall.
- It tracks packets as a part of a stream.
- It is not susceptible to IP spoofing attacks.
Explanation:
A stateless packetfiltering firewall can operate at Layer 4 of the Open Systems Interconnection (OSI) model.
A stateless packetfiltering firewall, which is also referred to as a static packetfiltering firewall, evaluates and either blocks or allows individual packets based on the Layer 3 and Layer 4 information in the packet header. Specifically, stateless packetfiltering firewalls can use the source and destination IP addresses, source and destination port numbers, and protocol type listed in the packet header? these values are commonly known as the 5tuple. Because a stateless packetfiltering firewall allows all traffic from an approved IP address, stateless packetfiltering firewalls are susceptible to IP spoofing attacks? an IP spoofing attack is a type of attack wherein an attacker uses the source IP address of a trusted host to send messages to other computers. This allows the attacker to send messages that appear to come from legitimate hosts on the network. In addition, because a stateless packetfiltering firewall evaluates packets individually, it cannot evaluate data streams or track connections.
By contrast, stateful packetfiltering firewalls traditionally operate at Layers 3, 4, and 5 of the OSI model. Stateful packetfiltering firewalls are more secure than stateless packetfiltering firewalls and are commonly used because of their versatility and ability to dynamically monitor and filter packets. Session information is maintained and tracked by stateful packetfiltering firewalls in order to determine whether packets should be permitted or blocked. For example, when monitoring Transmission Control Protocol (TCP) traffic, the stateful packet filter adds an entry to the state table when a TCP session is permitted. Subsequent packets are verified against the state table to ensure that the packets are in the expected sequence. If the TCP packet sequence numbers are not in the expected range, the packets are dropped. -
An SNMP readonly community named READONLY is configured on a Cisco router. Which of the following fields in the output of the show snmp command on the router will increment if an NMS makes a set request to the READONLY community? (Select the best answer.)
- Unknown community name
- Illegal operation for community name supplied
- Input queue packet drops
- No such name errors
Explanation:
In this scenario, the Illegal operation for community name supplied field in the output of the show snmp command on the router will increment if a network management station (NMS) makes a Simple Network Management Protocol (SNMP) set request to the READONLY community. SNMP communities can be configured to be either readonly or readwrite. Readonly communities enable an NMS to retrieve Management Information Base (MIB) data from a community, whereas readwrite communities enable an NMS to modify and retrieve MIB data. The show snmp command displays accumulated SNMP statistics, as shown in the following sample output:
Chassis: 42792565171230
SNMP packets input
2 Bad SNMP version errors
5 Unknown community name
4 Illegal operation for community name supplied
0 Encoding errors
0 Number of requested variables
0 Number of altered variables 680 Getrequest PDU
479 Getnext PDUs
60 Setrequest PDUs
0 Input queue packet drops (Maximum queue size 1000)
1230 SNMP packets output
0 Too big errors (Maximum packet size 1500)
No such name errors
Bad values errors
0 General errors
762 Response PDUs
0 Trap PDUs
SNMP logging: disabled
The Illegal operation for community name supplied field in the sample output indicates that four SNMP packets requested an operation that was not allowed for the associated community, such as a set request for a community that permits only get requests. The Unknown community name field indicates that five SNMP packets were received with unknown community strings. The Input queue packet drops field indicates that no packets were dropped because the input queue had reached its maximum size. The No such name errors field indicates that five SNMP packets were received for MIBs that did not exist on the router. The sample output also indicates the number of get, getNext, and set requests that have been received by the router as well as statistics on the number of various types of SNMP packets the router has sent in response to NMS queries. -
Which of the following statements is true of all firewalls? (Select the best answer.)
- They maintain a state table.
- They hide the source of network connections.
- They operate at Layer 7 of the OSI model.
- They are multihomed devices.
Explanation:
All firewalls are multihomed devices. A multihomed device is a device that connects to more than one network segment. The purpose of a firewall is to block undesired network traffic and to allow desired network traffic to pass from one network interface to another.
Some firewalls, such as proxy firewalls, can be configured to hide the source of network connections. However, stateful firewalls and packet filtering firewalls are not typically configured to hide the source of network connections. A proxy firewall terminates the connection with the source device and initiates a new connection with the destination device, thereby hiding the true source of the traffic. When the reply comes from the destination device, the proxy firewall forwards the reply to the original source device. Network Address Translation (NAT) and Port Address Translation (PAT) can also be used to hide the source of network connections.
Some firewalls, such as stateful firewalls, maintain a state table. However, other firewalls, such as packet filtering firewalls, do not. A stateful firewall makes filtering decisions based on the state of each session. When an outbound session is initiated, the stateful firewall will create an entry in the firewall’s state table and dynamically allow the return traffic in the inbound direction. Inbound traffic from other sources will be blocked unless there is a corresponding outbound session listed in the state table.
A packet filtering firewall makes simple filtering decisions based on each individual packet. As a result, packet filtering firewalls are not particularly flexible. For example, if you want to configure traffic on a port to flow inbound as well as outbound, you must open up the port in both directions. However, doing so might expose the internal network to undesirable inbound traffic on that port. Therefore, stateful firewalls are more secure than packet filtering firewalls.
Some firewalls, such as applicationlevel proxy firewalls, operate at Layer 7 of the Open Systems Interconnection (OSI) model, which is called the Application layer. However, stateful firewalls and packet filtering firewalls operate at the Network and Transport layers. An applicationlevel proxy firewall can make filtering decisions based on Application layer data. However, to do so, the firewall must be able to understand the corresponding Application layer protocol. As a result, applicationlevel proxy firewalls are often designed to filter data for a particular Application layer protocol, such as Hypertext Transfer Protocol (HTTP) or File Transfer Protocol (FTP). For example, an HTTP proxy can block malicious or otherwise undesirable web traffic, but it might not be able to block malicious FTP traffic. -
You issue the following block of commands on a Cisco router:
RouterA(config)#privilege exec level 10 show users RouterA(config)#username boson password cisco RouterA(config)#username boson privilege 15 RouterA(config)#username boson autocommand show users
RouterA(config)#line vty 0 4
RouterA(configline)#login local
RouterA(configline)#privilege level 7
Which of the following statements accurately describes what happens when the user boson successfully initiates a Telnet session to RouterA? (Select the best answer.)
- The autocommand command fails, and the user is disconnected.
- The autocommand command fails, and the user is not disconnected.
- The autocommand command succeeds, and the user is disconnected.
- The autocommand command succeeds, and the user is not disconnected.
Explanation:
When the user boson successfully initiates a Telnet session to RouterA in this scenario, the autocommand command succeeds and the user is disconnected from the router. When issued with the username command, the autocommand keyword can execute a specific command immediately after a user successfully logs in to a Cisco router. In this scenario, the autocommand specifies that the show users command should execute immediately after the user logs in. The command output is displayed to the user terminal, and then the user’s session is terminated. You can prevent the user session from being terminated either by using the nohangup keyword or by issuing the no username username autocommand command to remove the autocommand keyword. However, the no username username autocommand command will delete both the autocommandkeyword and the specified user name from the local database? therefore, you will need to issue the username username password password again to recreate the user entry. By contrast, the nohangup keyword does not affect the autocommand keyword but instead changes the default behavior so that the user session is not disconnected.
The privilege exec level 10 show users command in this scenario changes the required privilege level of the show users command to level 10. The default EXEC privilege level is level 1? therefore, this command removes the show users command from the EXEC shells of all users with privilege levels less than 10. The default enable privilege level is level 15? therefore, any user could enter privileged EXEC mode and execute the command. The username boson privilege 15 command in this scenario configures the user boson with a privilege level of 15. Because the user’s base privilege level is already 15, the user is not required to issue the enable command to enter privileged EXEC mode. The following block of commands configures the four default virtual terminal (VTY) interfaces on RouterA to use the local database for authentication and to assign user sessions a default privilege level of 7:
RouterA(config)#line vty 0 4
RouterA(configline)#login local
RouterA(configline)#privilege level 7
Although Telnet users are assigned a default privilege level of 7 in this scenario, peruser privileges override the privileges configured for the VTY line. Therefore, the user boson will be granted privilege level 15 when connected to a VTY line through a Telnet session. By contrast, a user without a specified privilege level will be granted privilege level 7 in this scenario. Because the show users command has been assigned a required privilege level of 10, the boson user will be able to execute the command, whereas a Telnet user with the default privilege level would be unable to execute the command without first issuing the enable command to enter privileged EXEC mode.
If the boson user was assigned a privilege level that was insufficient to execute the show users command, the autocommand keyword would still attempt to execute the command. The autocommand keyword does not verify that a user has sufficient privileges to execute the specified command. However, the command would cause the router to display an error message instead of the expected command output. The user session would be disconnected after the error message was displayed.
In no case would the user session remain connected. The nohangup keyword must be used with the username command to change the default behavior so that a user session is not disconnected after the command specified by the autocommand command is executed. -
You administer the network shown above. SwitchE is the root bridge for the network. You connect SwitchF to a port on SwitchB. SwitchF has a priority value of 0 and the MAC address 0000.0c42.0729.

300-735 Part 03 Q19 018 Which statement is most accurate regarding root bridge selection after SwitchF is connected to SwitchB? (Select the best answer.)
- SwitchB will immediately become the root bridge.
- SwitchE will remain the root bridge.
- SwitchF will immediately become the root bridge.
- SwitchE will remain the root bridge until it is powered down, and then SwitchF will become the root bridge.
Explanation:
After you connect SwitchF to a port on SwitchB, SwitchF will become the root bridge because it has the lowest possible priority value and it has a lower Media Access Control (MAC) address than any of the other switches with a priority value of 0. The root bridge is the switch with the lowest bridge ID (BID), which is composed of a 2byte bridge priority and a 6byte MAC address. The bridge priority is considered first in the determination of the lowest BID. When two or more switches have the lowest priority, the switch with the lowest MAC address will become the root bridge. Because SwitchF has a lower MAC address than SwitchE, SwitchF will become the root bridge.
SwitchE will not remain the root bridge, because SwitchF has the same priority and a lower MAC address.
When a switch is powered on, it sends out bridge protocol data units (BPDUs) that contain the switch’s BID. As soon as a switch receives a BPDU with a lower BID than the current root switch BID, the switch will consider that BPDU to be superior, replace the root switch BID with the BID from the BPDU, and recalculate the root port and port costs. This can have an undesired effect on how packets are sent through a switched network. Therefore, when connecting a switch to a switched network, you must ensure that the switch has a higher priority value than the root bridge, unless you want the switch to assume the root bridge role. This is especially true if the switch is older or contains inferior technology, such as ports that are capable of only 10megabits per second (Mbps) transmission or halfduplex operation. Alternatively, you can issue the spanningtree guard root command to enable the root guard feature. The root guard feature, when enabled on a port, prevents superior BPDUs received on a neighbor switch connected to that port from becoming the root bridge. If superior BPDUs are received on a port enabled with root guard, the port enters the rootinconsistent state and the port is blocked until the port stops receiving superior BPDUs.
SwitchB will not become the root bridge. SwitchB has a priority value of 65535, which is the highest possible priority value. The root bridge is the switch with the lowest priority value. You can set the bridge priority by issuing the spanningtree priority value command, where value is a number from 0 through 65535? the default priority is 32768.
SwitchE will not remain the root bridge until it is powered down? SwitchF will immediately replace SwitchE as the root bridge. Root bridges do not behave the same as Open Shortest Path First (OSPF) designated routers (DRs) and backup DRs (BDRs) do. A DR is not replaced by another DR even if a router with a higher OSPF priority is introduced. A DR remains the DR until it fails or is powered down? then the BDR becomes the DR and a new BDR is selected. -
Which of the following statements is true regarding the outbreak control feature of AMP for Endpoints? (Select the best answer.)
- It cannot block polymorphic malware.
- It must wait for a content update before blocking specific files.
- It cannot whitelist specific applications.
- It can use application blocking lists to contain compromised applications.
Explanation:
The outbreak control feature of Cisco Advanced Malware Protection (AMP) for Endpoints can use application blocking lists to contain compromised applications. AMP for Endpoints is a hostbased malware detection and prevention platform that runs on Microsoft Windows, Mac OS X, Linux, and Google Android. Like many other antimalware packages, AMP for Endpoints monitors network traffic and application behavior to protect a host from malicious traffic. However, unlike many of its competitors, AMP for
Endpoints continues its analysis after a disposition has been assigned to a file or traffic flow. When malware is detected, the outbreak control feature of AMP for Endpoints can use application blocking to ensure that a compromised application is contained and that it does not spread the infection. Outbreak control provides for granular control over which applications are blocked and can use whitelists to ensure that missioncritical software continues to run even during an outbreak.
The outbreak feature works in conjunction with the continuous analysis, continuous detection, and retrospective security features of AMP for Endpoints to quickly contain and control the spread of malware. Once a file or application has been detected as malicious, the outbreak control feature can use custom detection rules to quickly block the specific file or application without waiting for a signature file content update. In addition, custom signatures can be created to detect polymorphic malware, which is malicious software than can evolve its code or behavior as it propagates.