300-735 : Automating Cisco Security Solutions (SAUTO) : Part 04
-
You want to use ASDM to create an inspection rule that will drop and log SHOUTcast media streams.
Which of the following inspection rules should you configure to achieve your goal? (Select the best answer.)
- H.323 H.225
- H.323 RAS
- HTTP
- RTSP
- IM
Explanation:
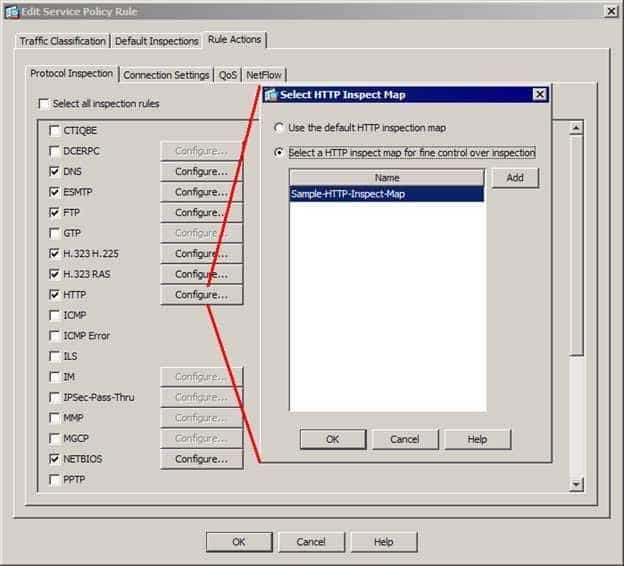
You should configure a Hypertext Transfer Protocol (HTTP) inspection rule to drop and log SHOUT cast media streams on a Cisco Adaptive Security Appliance (ASA). When HTTP inspection is enabled in a service policy, such as the global service policy, you can opt to use the default inspection rules or you can customize the inspection rules by applying an HTTP inspect map. You can select a custom HTTP inspect map from the Select HTTP Inspect Map dialog box, as shown below:
300-735 Part 04 Q01 019 You can modify the configuration of an HTTP inspect map from the Configuration > Firewall > Objects > Inspect Maps > HTTP pane of Cisco Adaptive Security Device Manager (ASDM). This pane enables you to add, delete, and modify HTTP inspect maps. To modify an existing map, you should first click the Customize button, which opens the Edit HTTP Inspect Map dialog box, as shown in the following exhibit:
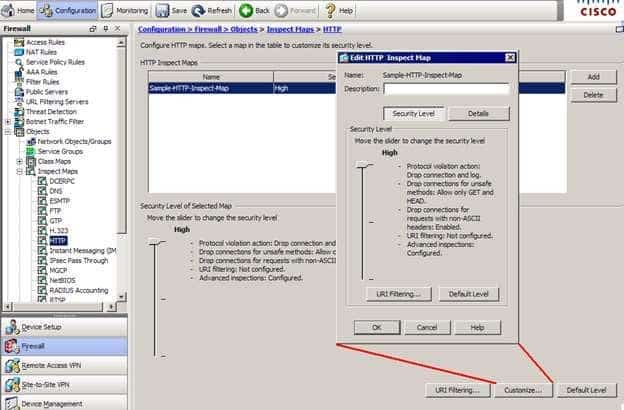
300-735 Part 04 Q01 020 You can reset the inspection map to its default security level by clicking the Default Level button, or you can slide the Security Level slider to select a predefined setting. Alternatively, you can click the Details button to expand the Edit HTTP Inspect Map dialog box into a larger window with more options, as shown below:
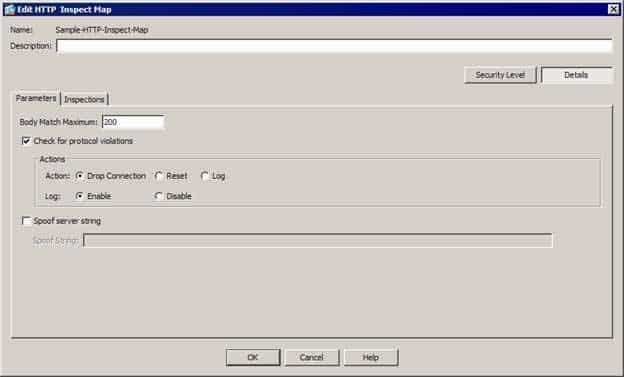
300-735 Part 04 Q01 021 You can use the Parameters tab of the expanded Edit HTTP Inspect Map dialog box to enable protocol violation checks and to select the actions that the ASA should take if protocol violations are found. You can also use the tab to configure server string spoofing and the maximum body length for HTTP request and response searches. The Inspections tab of the expanded Edit HTTP Inspect Map dialog box displays the details of the inspection map, as shown in the exhibit below:

300-735 Part 04 Q01 022 The Inspections tab displays the inspection rules that apply to the current inspect map. The Match Type column indicates whether traffic must match or not match the criterion specified in the remaining columns. The Criterion column specifies what type of inspection is being performed. If the traffic is being inspected for a value, that value is indicated in the Value column. The Action column indicates what action will be applied to sessions that meet the rules requirements, and the Log column indicates whether the action triggers a system log (syslog) message. If you wanted to add an inspection rule that dropped and logged SHOUT cast media streams, you could click the Add button to open the Add HTTP Inspect dialog box and then select the _default_shout cast tunneling protocol item from the HTTP Traffic Class dropdown list box, as shown in the following exhibit:
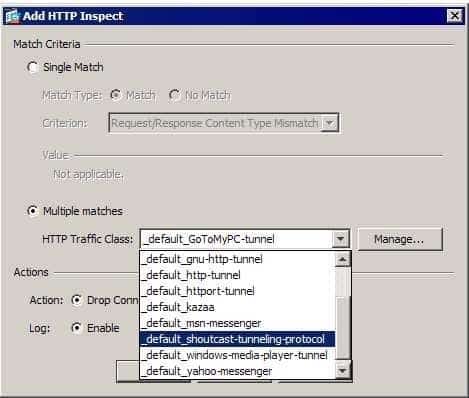
300-735 Part 04 Q01 023 The items listed in the dropdown list are class maps that have been defined on the ASA. Names that begin with _default are predefined in the system default configuration and can be referenced directly from ASDM or by the class command in a policy map. The _default_shoutcasttunnelingprotocol class map is a predefined class map that can identify SHOUTcast media streams by their HTTP metadata, as shown in the following exhibit:
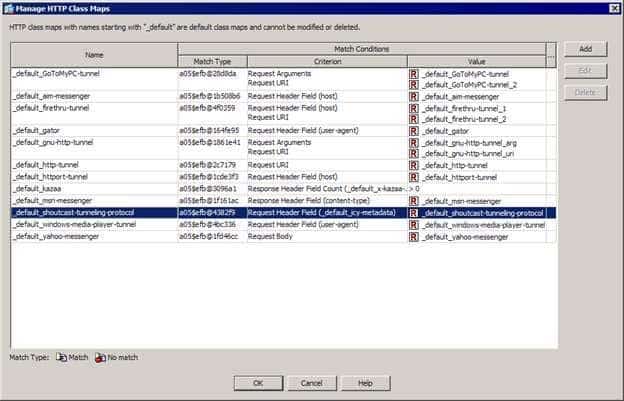
300-735 Part 04 Q01 024 You cannot configure H.323 H.225; H.323 Registration, Admission, and Status (RAS); Instant Messaging (IM); or RealTime Streaming Protocol (RTSP) inspection rules to drop and log SHOUTcast media streams on an ASA. SHOUTcast media streams use HTTP, not H.323 or H.225. H.323 H.225 and H.323 RAS inspection rules provide support for International Telecommunication Union (ITU) H.323compliant applications such as Cisco CallManager. IM inspection rules provide the ASA with the ability to enforce security policies for a variety of mainstream IM applications. RTSP inspection rules enable an ASA to process media streams that are commonly produced by RealAudio, Apple QuickTime, and Cisco IP television (IPTV) connections.
-
On which of the following screens in ASDM can you enable users to select which connection profile they will use when they establish a clientless SSL VPN connection? (Select the best answer.)
- the Edit User Account dialog box for each user who should be able to select a connection profile
- the Edit Internal Group Policy dialog box for each group policy that is associated with the clientless SSL VPN connection profiles
- the main Connection Profiles pane
- the main Group Policies pane
- the main Local Users pane
Explanation:
You can enable users to select which connection profile they will use on the portal login page on the main Connection Profiles pane for clientless Secure Sockets Layer (SSL) virtual private network (VPN) connections in Cisco Adaptive Security Device Manager (ASDM). When you configure a clientless SSL VPN connection, you can require that a user use a specific connection profile or you can allow users to select the connection profile to use on the login page of the clientless SSL VPN portal. You can select the Allow user to select connection profile, identified by its alias, on the login page option on the Connection Profiles pane in ASDM to allow users to select which connection profile they will use. This option is shown in the following exhibit:

300-735 Part 04 Q02 025 When this option is selected, a dropdown list will be displayed on the login page of the clientless SSL VPN portal. The dropdown list will contain a list of the connection profiles from which the user can select.
You cannot configure the main Group Policies pane or the main Local Users pane to enable users to select connection profiles on the clientless SSL VPN portal. On these panes, you can view a basic summary of information for any configured group policies or user accounts, respectively. To configure group policy or user account information, you must select a group policy or a user account and click the Edit button to configure them. The resulting configuration dialog boxes-Edit User Account for users and Edit Internal Group Policy for group policies-enable you to make configuration changes, but neither of these dialog boxes contains an option for enabling users to select the connection profile on the clientless SSL VPN portal. -
Which of the following can be configured on the General screen of the Add Internal Group Policy dialog box in ASDM when creating a group policy for clientless SSL VPN users? (Select 3 choices.)
- a banner message for VPN clients
- the bookmark list to apply to VPN clients
- the tunneling protocols that clients can use to establish a VPN connection
- the name of the group policy
- a group URL that VPN users can access
- the portal customization object to apply to VPN connections
Explanation:
Of the choices available, you can configure a banner message for virtual private network (VPN) clients, the tunneling protocols that clients can use to establish VPN connections, and the name of the group policy on the General screen of the Add Internal Group Policydialog box in Cisco Adaptive Security Device Manager (ASDM) when creating a group policy for clientless Secure Sockets Layer (SSL) VPN users. You can create a group policy on a Cisco Adaptive Security Appliance (ASA) to specify security policies and network settings that are used when remote VPN users log in to the ASA. To create a group policy for clientless SSL VPN users in ASDM, you should click Configuration, click the Remote Access VPN button, expand Clientless SSL VPN Access, and click Group Policies. You can then create a new group policy by clicking Add, which will open the Add Internal Group Policy dialog box. The dialog box opens to the General screen, on which you can configure general properties for the group policy, including the name of the group policy, a banner message to be displayed to VPN users, the tunneling protocols that clients can use to establish a VPN connection, the VPN access hours, a web access control list (ACL), the number of simultaneous logins, a virtual LAN (VLAN) restriction, the connection profile to use for the connection, the maximum connect time, and the idle timeout time. The General screen of the Add Internal Group Policy dialog box, with the name, banner message, and tunneling protocols configured, is shown in the following exhibit:
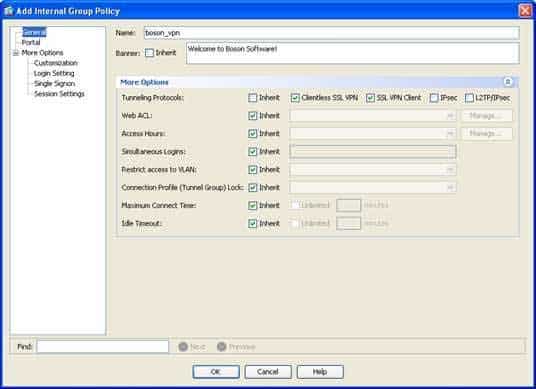
300-735 Part 04 Q03 026 The bookmark list to apply to VPN clients is not configured on the General screen of the Add Internal Group Policy dialog box. You can specify the bookmark list on the Portalscreen of the Add Internal Group Policy dialog box.
The portal customization object to apply to VPN clients is not configured on the Generalscreen of the Add Internal Group Policy dialog box. You can specify the portal customization object on the Customization screen of the Add Internal Group Policydialog box.
A group Uniform Resource Locator (URL) that VPN users can access is not configured on the General screen of the Add Internal Group Policy dialog box. You configure a group URL in a connection profile, not in a group policy. To configure a group URL, you should access the SSL VPN screen of the Add SSL VPN Connection Profile dialog box in ASDM. -
Which of the following show clock command output symbols indicates that time reported by the software clock is authoritative but not synchronized with the configured time source? (Select the best answer.)
- #
- *
- ~
- .
- +
Explanation:
The period (.) is the show clock command output symbol that indicates that time reported by the software clock is authoritative but not synchronized with the configured time source. The show clock command displays the current time as reported by the system software clock. The time can be configured manually or derived from an external time source, such as a Network Time Protocol (NTP) server. If the software clock is configured to use an external time source and that source becomes unreachable, the time might become unsynchronized due to clock drift. When this happens, the show clockcommand uses the . symbol to indicate that the time is still considered authoritative but is no longer guaranteed to be synchronized with the external time source. The following command output indicates that the software clock is authoritative but not synchronized with its time source:
.10:06:40.603 UTC Tue Jan 13 2015
The asterisk (*) is displayed in the output of the show clock command to indicate that time reported by the software clock is not authoritative. If the software clock is not set by a timing source, the system will flag the time as not authoritative and the output of the show clock command will indicate the flag with the * symbol, as shown in the following command output:
*10:06:40.603 UTC Tue Jan 13 2015
By contrast, if the time is set by a timing source and is synchronized with that source, the time is considered authoritative and the output of the show clock command will not display any additional symbols. For example, the absence of additional symbols in the following command output indicates that the software clock is authoritative and synchronized with its time source:
10:06:40.603 UTC Tue Jan 13 2015
The pound sign (#), tilde (~), and plus sign (+) are displayed in the output of the show ntp associations command, not the show clock command. The output of the show ntp associations command shows the IP addresses of configured NTP servers and their respective clock sources, strata, and reachability statistics. For example, in the following command output, the NTP server at IP address 128.227.205.3 is a stratum 1 server that uses a global positioning system (GPS) time source as its time source:
address ref clock st when poll reach delay offset disp
*~128.227.205.3 .GPS. 1 17 64 377 0.000 0.000 0.230
~71.40.128.157 204.9.54.119 2 18 64 377 0.000 321 1.816
~184.22.97.162 132.163.4.101 2 5 64 377 0.000 314 1.134
* sys.peer, # selected, + candidate, outlyer, x falseticker, ~ configured
The * next to the IP address in the command output indicates that this server is an NTP master time source to which the Cisco device is synched. A # next to the IP address indicates that the server is an NTP master time source to which the Cisco device is not yet synched. A + next to the IP address indicates that the server is an NTP master time source that is selected for synchronization but the synchronization process has not yet begun. A ~next to an IP address indicates that the address was manually configured. -
Which of the following statements are true regarding policies in Cisco Security Manager? (Select 2 choices.)
- Rule-based policies can contain hundreds of rules containing values for the same set of parameters.
- Settings-based policies can define only one set of parameters for each settings based policy defined on a device.
- Local policies are well-suited to smaller networks and to devices requiring standard configurations.
- Any changes that you make to a shared policy are not automatically applied to all the devices to which it is assigned.
- The Default section of a shared policy contains rules that cannot be overridden by local rules.
Explanation:
In Cisco Security Manager (CSM), rulebased policies can contain hundreds of rules containing values for the same set of parameters and settingsbased policies can define only one set of parameters for each settingsbased policy defined on a device. CSM is a graphicsbased management application that can be used to configure a wide variety of Cisco devices, such as routers, switches, firewall appliances, Intrusion Prevention System (IPS) appliances, and Catalyst service modules. One of the advantages of CSM is its ability to centralize the administration of security policies across a large number of Cisco devices. CSM categorizes policies into two general types: rulebased policies and settingsbased policies. Rulesbased policies, such as access control lists (ACLs) and inspection rules, are stored in a tabular fashion and can contain many different values for the same set of parameters. These policies are processed in order and the first matching table entry will be applied, even if there are other matching table entries farther down the table. Because of the nature in which rulesbased policies are processed, they can contain hundreds of rules with values for the same set of parameters. By contrast, settingsbased policies can define only a single set of parameters for each settingsbased policy defined on a device. Settingsbased policies, such as Quality of Service (QoS) policies and IP Security (IPSec) policies, contain a set of parameters that, as a whole, define a particular hardware or security configuration feature.
CSM policies can be either local or shared. A local policy is specific to a particular device, and any changes affect only its associated device. By contrast, a shared policy is applicable to a group of devices and any changes are automatically applied to all of its associated devices. Because local policies are specific to individual devices, it can become cumbersome to manage the policies in a network with a large number of devices? therefore, local policies are better suited to smaller networks and shared policies are better suited to larger networks.
Shared policies use an inheritance hierarchy to determine which policy rules are implemented on a particular device. There are two kinds of shared policy rules: mandatory and default. Mandatory rules cannot be overridden by either child policy rules or local rules. By contrast, default rules can be overridden by both child policy rules and local rules. Inheritance enables you to nest multiple shared rules and ensure that certain policies cannot be overridden while still maintaining the flexibility to override some default settings. -
Which of the following authentication methods are supported by both RADIUS and TACACS+ server groups on a Cisco ASA firewall? (Select 3 choices.)
- ASCII
- CHAP
- MSCHAPv1
- MSCHAPv2
- PAP
Explanation:
Remote Authentication DialIn User Service (RADIUS) and Terminal Access Controller Access Control
System Plus (TACACS+) server groups on a Cisco Adaptive Security Appliance (ASA) support Challenge
Handshake Authentication Protocol (CHAP), Microsoft CHAP version 1 (MSCHAPv1), and Password Authentication Protocol (PAP). A Cisco ASA supports a number of different Authentication, Authorization, and Accounting (AAA) server types, such as RADIUS, TACACS+, Lightweight Directory Access Protocol (LDAP), Kerberos, and RSA Security Dynamics, Inc. (SDI) servers.
When authenticating with a TACACS+ server, a Cisco ASA can use the following authentication protocols:
– ASCII
– PAP
– CHAP
– MSCHAPv1
When authenticating with a RADIUS server, a Cisco ASA can use the following authentication protocols:
– PAP
– CHAP
– MSCHAPv1
– MSCHAPv2
– Authentication Proxy Mode (for example, RADIUS to RSA/SDI, RADIUS to Active Directory, and others) -
Which of the following statements is true regarding ZFW traffic action characteristics? (Select the best answer.)
- The pass action is bidirectional and automatically permits return traffic.
- The inspect action is unidirectional and can be used to maintain state information.
- The drop action silently discards packets and does not generate ICMP host unreachable messages.
- The pass action can provide an audit trail including session start, stop, and duration values.
Explanation:
The drop action in a zonebased policy firewall (ZFW) configuration silently discards packets and does not generate Internet Control Message Protocol (ICMP) host unreachable messages. ZFWs include many of the features of previous firewall versions, including stateful packet inspection and Uniform Resource Locator (URL) filtering. However, several new firewall features are also included, such as the ability to create security zones to which security policies can be applied. With ZFWs, policies are applied to a security zone pair rather than to an interface. This provides for more granular implementation of firewall policies? different policies can be applied to hosts connected to the same interface. Before a policy can be applied to an interface, the interface must be added to a zone. To permit traffic from one zone to another, you must create a zone pair between the zones. Once you have configured zones and zone pairs, you can apply one of three actions, pass, drop, or inspect, to the traffic between the zones.
The drop action is the default action that is applied to traffic sent from one zone to another on a router that is configured with a ZFW. Unless a policy has been configured to allow traffic to be sent between two zones, the traffic will be dropped.
The pass action can be applied to permit traffic from one zone to another. However, because the pass action is unidirectional, no return traffic will be allowed by the pass action. Another policy would need to be applied in the destination zone to allow return traffic to the originating zone.
The inspect action can be used to maintain state information for a connection sent through a ZFW. Consequently, unlike the pass action, the inspect action is bidirectional and will allow return traffic to the zone from the destination. For example, if a ZFW is used in between an internal network and the Internet, the inspect action can be used to allow the internal hosts to retrieve information from the Internet. That is, data from the Internet will be permitted by the inspect action. In addition, the inspect action can provide an audit trail including session start time, stop time, duration, quantity of data transferred, and source and destination IP addresses. -
You have configured an ASA to accept SSL VPN connections. DTLS and DPD are configured on the ASA.Which of the following is most likely to occur if a Cisco AnyConnect client that is not configured for DTLS attempts to connect to the ASA? (Select the best answer.)
- The client will be unable to establish a connection to the ASA.
- The client will still be able to connect by using DTLS and will be able to communicate on the remote network.
- The client will be able to connect by using TLS and will be able to communicate on the remote network.
- The client will be able to establish a connection to the ASA but will be unable to communicate on the remote network.
Explanation:
The client will be able to connect by using Transport Layer Security (TLS) and will be able to communicate on the remote network. Datagram TLS (DTLS) is the default transport method for Secure Sockets Layer (SSL) virtual private network (VPN) connections on Cisco Adaptive Security Appliance (ASA) devices. However, if DTLS is not enabled on the VPN client, TLS can be used as a fallback method for data transport. In such a scenario, the client will establish a TLS connection and will be able to communicate on the remote network, provided that the user has access to the client network. In order for an ASA to fall back to TLS, Dead Peer Detection (DPD) must be enabled on the ASA. DPD is a feature that can determine whether the other end of a link is not responding and the connection has failed. If DPD determines that the client is not responding, the connection will revert to using TLS as the transport method. -
Refer to the exhibit.
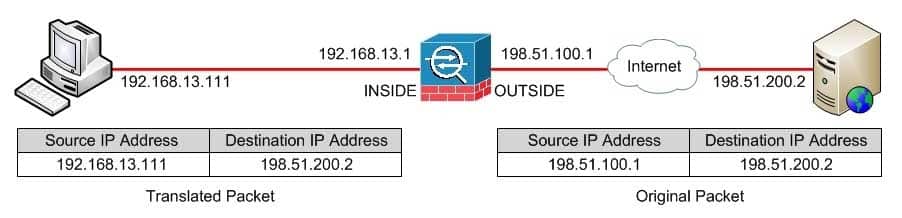
300-735 Part 04 Q09 027 You want to use network object NAT to configure the ASA to perform PAT on traffic that originates from the 192.168.13.0/24 network attached to the INSIDE interface and that is destined to any networks connected to OUTSIDE interface.
Which of the following blocks of commands should you issue to achieve your goal? (Select the best answer.)-
asa(config)#object network INSIDENetwork asa(confignetworkobject)#subnet 192.168.13.0 255.255.255.0 asa(confignetworkobject)#nat (INSIDE,OUTSIDE) dynamic interface
-
asa(config)#object network OUTSIDENetwork asa(confignetworkobject)#subnet 198.51.100.0 255.255.255.0 asa(confignetworkobject)#nat (any,INSIDE) dynamic interface
-
asa(config)#object network INSIDENetwork asa(confignetworkobject)#subnet 192.168.13.0 255.255.255.0 asa(confignetworkobject)#nat (OUTSIDE,INSIDE) dynamic interface
-
asa(config)#object network INSIDENetwork asa(confignetworkobject)#subnet 192.168.13.0 255.255.255.0 asa(confignetworkobject)#nat (any,OUTSIDE) dynamic interface
Explanation:
You should issue the following block of commands to achieve your goal in this scenario:
asa(config)#object network INSIDENetwork
asa(confignetworkobject)#subnet 192.168.13.0 255.255.255.0
asa(confignetworkobject)#nat (INSIDE, OUTSIDE) dynamic interfaceWhen the nat command is issued from network object configuration mode, it is referred to as the nat (object) command and it can be used to configure network object Network Address Translation (NAT) on the Cisco Adaptive Security Appliance (ASA). Network object NAT enables you to easily specify a mapping for the source address in a packet. The command block in this scenario configures a network object named INSIDENetwork, defines a subnet IP address and network mask for the INSIDENetwork object, and specifies that the real source IP address of packets from the INSIDE interface should be dynamically translated to the mapped IP address corresponding to the IP address assigned to the OUTSIDE interface. The effect of the translation on matching packets is illustrated by the following graphic:
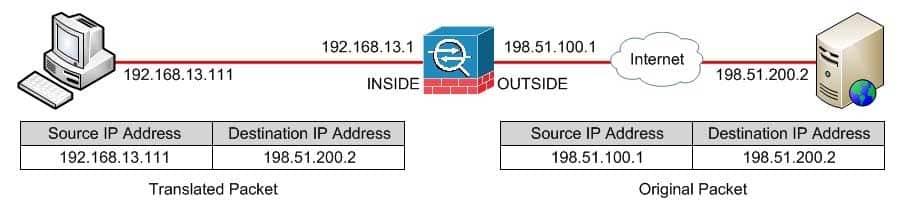
300-735 Part 04 Q09 028 The nat (object) command can be used to create a dynamic NAT rule which translates traffic for a particular network object. The abbreviated syntax to create a dynamic NAT rule with the nat (object) command is nat (real_interface,mapped_interface) dynamic {mapped_object | mapped_ host_IP | interface} [fallthrough_interface], where real_interface represents the source interface of the original packet and mapped_interfacerepresents the source interface of the translated packet. The source IP address of the original packet is based on the definition of the network object? in this scenario, the network object is a network subnet. The dynamic keyword is used to specify a dynamic NAT rule and the interface parameter is used to specify a Port Address Translation (PAT) rule. An optional fallthrough interface can be specified if dynamic NAT is configured to use a pool of addresses to ensure that translation continues even if every IP address in the pool has been assigned a translation.
Alternatively, you could use Adaptive Security Device Manager (ASDM) instead of the command line to configure the network object NAT rule in this scenario. You can create a network object rule in ASDM by accessing the Configuration > Firewall > NAT Rules pane, clicking the Add dropdown list, and selecting the Add “Network Object” NAT ruleoption to open the Add Network Object dialog box. The following sample Add Network Object dialog box corresponds to the block of commands in this scenario:
300-735 Part 04 Q09 029 You should not issue the following block of commands to achieve your goal in this scenario:
asa(config)#object network INSIDENetwork
asa(confignetworkobject)#subnet 192.168.13.0 255.255.255.0
asa(confignetworkobject)#nat (any,OUTSIDE) dynamic interfaceThe nat (any,OUTSIDE) dynamic interface command in this block of commands maps the source IP address of traffic that originates from the 192.168.13.0/24 subnet, from any interface, to the IP address assigned to the OUTSIDE interface. Although this block of commands would configure the ASA to perform the required translation for traffic originating from the INSIDE interface, it would also perform the translation for any traffic from the 192.168.13.0/24 subnet originating from any other interface. Because the scenario requires the translation to occur only for traffic originating from the INSIDE interface, you should not issue this block of commands.
You should not issue the following block of commands to achieve your goal in this scenario:asa(config)#object network INSIDENetwork asa(confignetworkobject)#subnet 192.168.13.0 255.255.255.0 asa(confignetworkobject)#nat (OUTSIDE, INSIDE) dynamic interface
The nat (OUTSIDE, INSIDE) dynamic interface command maps the source IP address of traffic that originates from the 192.168.13.0/24 subnet, from only the OUTSIDE interface, to the IP address assigned to the INSIDE interface. Because the 192.168.13.0/24 network is directly connected to the INSIDE interface and not the OUTSIDE interface, this translation rule would not achieve the requirements of the scenario.
You should not issue the following block of commands to achieve your goal in this scenario:asa(config)#object network INSIDENetwork asa(confignetworkobject)#subnet 192.168.13.0 255.255.255.0 asa(confignetworkobject)#nat (OUTSIDE, INSIDE) dynamic interface
This block of commands creates a network object that corresponds to the network directly connected to the OUTSIDE interface. The nat (any,INSIDE) dynamic interface command maps the source IP address of traffic that originates from the 198.51.100.0/24 subnet, from any interface, to the IP address assigned to the INSIDE interface.
-
-
You are using ASDM to verify a clientless SSL VPN configuration made by a junior administrator on an ASA. Please click exhibit to answer the following questions.
Exhibit: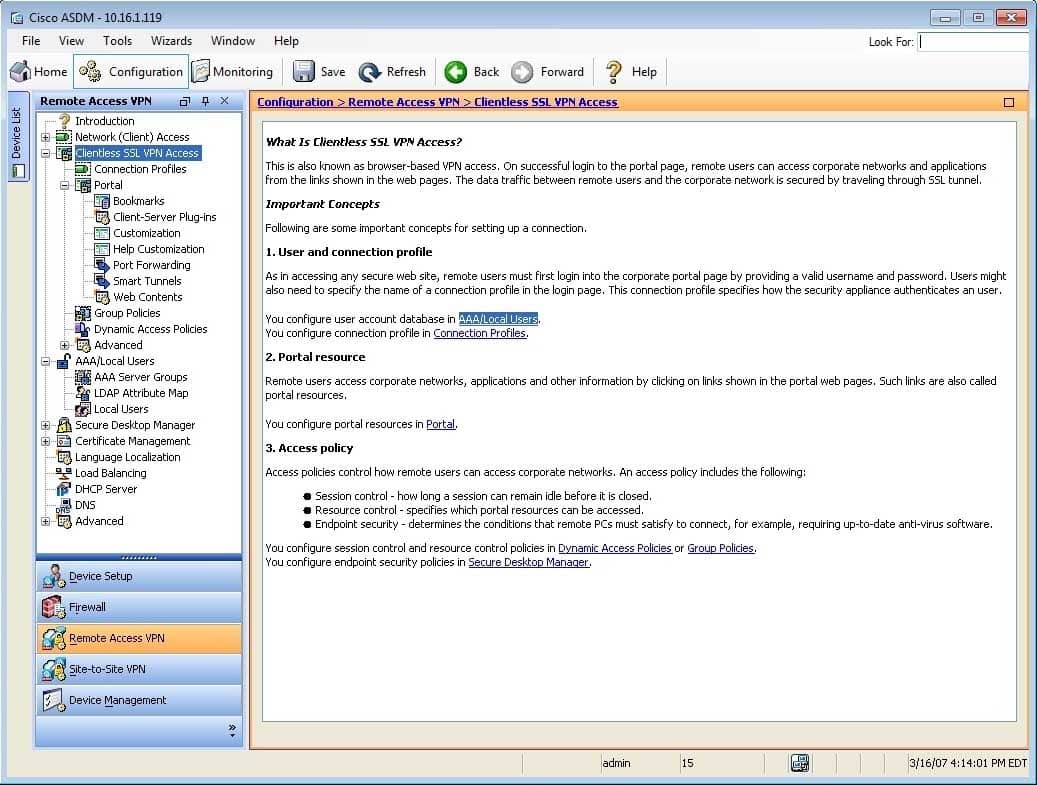
300-735 Part 04 Q10 030 When a user logs in to the clientless SSL VPN portal by using extranet tunnel group, which of the following statements is true regarding the appearance of the portal? (Select the best answer.)
- No text will be displayed in the title portion of the portal screen.
- The text “SSL VPN Service” will be displayed in the title portion of the portal screen.
- The text “Boson Extranet” will be displayed in the title portion of the portal screen.
- The text “Boson SSL VPN Service” will be displayed in the title portion of the portal screen.
Explanation:
When a user logs in to the clientless Secure Sockets Layer (SSL) virtual private network (VPN) portal by using the extranet tunnel group, the text “Boson Extranet” will be displayed in the title portion of the portal screen. When users log in to a clientless SSL VPN session, the users are presented with a portal screen that contains information and links to resources to which the user has access. You can customize the appearance of the portal by modifying the DfltCustomization customization object or by creating a new customization object and linking it to the appropriate tunnel group (s). You can then link a customization object to a specific tunnel group, which is also known as a connection profile.
To determine which customization object has been applied to a tunnel group, you should click
Configuration, click the Remote Access VPN button, expand Clientless SSL VPN Access, click Connection Profiles, and then select the appropriate connection profile from the list. For this scenario, you want to determine the customization object that will be applied to the extranet tunnel group, so you should doubleclick extranet in the list of connection profiles, expand Advanced, and click Clientless SSL VPN. The Portal Page Customization entry indicates that this connection profile uses the extranet_customization customization object, as shown in the following exhibit:

300-735 Part 04 Q10 031 To view the details of a customization object in Cisco Adaptive Security Device Manager (ASDM), you should click Configuration, click the Remote Access VPN button, expand Clientless SSL VPN Access, expand Portal, and click Customization, which will display the Customization Objects pane. In this scenario, two customization objects have been created: boson_customization and extranet_customization. To view the details of a customization object, you should doubleclick the customization object, which will open the SSL VPN Customization Editor in a browser window. To determine the text that will be displayed in the title portion of the portal screen, you should navigate to the Portal area of the SSL VPN Customization Editor by clicking the Portal tab and then click Title Panel, as shown in the following exhibit:

300-735 Part 04 Q10 032 The text that will be displayed in the title portion of the portal is displayed in the Text entry of the Title Panel pane; the Text entry contains the text “Boson Extranet”, which is the text that will be displayed in the title portion of the portal when users establish a VPN connection, as shown in the following exhibit.
300-735 Part 04 Q10 033 The text “SSL VPN Service” is the default text that will be displayed if you do not customize the Text entry of the Title Panel. In this scenario, the text has been customized, so the text “SSL VPN Service” will not be displayed.
The text “Boson SSL VPN Service” will be displayed only for tunnel groups that use the boson_customization customization object. This text will not be displayed for the extranet tunnel group. -
You are using ASDM to verify a clientless SSL VPN configuration made by a junior administrator on an ASA. Please click exhibit to answer the following questions.
Exhibit:
300-735 Part 04 Q11 034 Which of the following statements is true regarding how the on-screen keyboard will be displayed when a user establishes a clientless SSL VPN session by using the boson connection profile? (Select the best answer.)
- The on-screen keyboard will not be displayed on any pages.
- The on-screen keyboard will be displayed only on the login page.
- The on-screen keyboard will be displayed on any portal page that requires authentication.
- The on-screen keyboard will be displayed on every portal page.
Explanation:
In this scenario, the onscreen keyboard will be displayed only on the login page when a user establishes a clientless Secure Sockets Layer (SSL) virtual private network (VPN) session by using the boson connection profile. When users log in to a clientless SSL VPN session, you can configure an onscreen keyboard to be displayed in certain areas of the portal. The onscreen keyboard enables users to enter information, such as passwords, by using the onscreen keyboard instead of a physical keyboard. For example, you can configure the onscreen keyboard to be displayed on the login page, and users can use this keyboard to enter their login information. By default, the onscreen keyboard is disabled. To enable the onscreen keyboard, you should click Configuration, click the Remote Access VPN button, expand Clientless SSL VPN Access, expand Portal, and click Customization, which will display the Customization Objects pane. This pane contains an OnScreen Keyboard area that provides several options for configuring the onscreen keyboard. You can select from the following onscreen keyboard options:
– Do not show OnScreen keyboard – This option disables the onscreen keyboard.
– Show only for the login page – This option enables the onscreen keyboard for the login page.
– Show for all portal pages requiring authentication – This option enables the onscreen keyboard for any page that requires that the user be authenticated.
In this scenario, the Show only for the login page option is selected, as shown in the following exhibit:
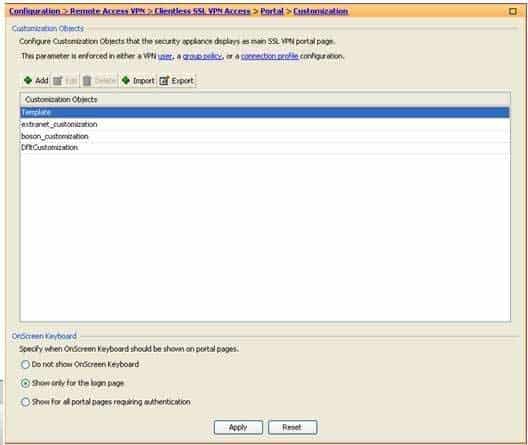
300-735 Part 04 Q11 035 This setting will apply to any customization object that you create. Therefore, selecting the Show only for the login page option will configure the onscreen keyboard to be displayed on the login page for all customization objects and for any connection profiles associated with those customization objects.
-
You are using ASDM to verify a clientless SSL VPN configuration made by a junior administrator on an ASA. Please click exhibit to answer the following questions.Exhibit:
300-735 Part 04 Q12 036 Which of the following statements are true regarding the extranet connection profile? (Select three.)
- It will use the boson_grp group policy.
- It will use the DfltGrpPolicy group policy.
- It will use the local AAA database for authentication.
- It will use digital certificates for authentication.
- It will use the DfltCustomization customization object.
- It will use the boson_customization customization object.
- It will use the extranet customization customization object.
Explanation:
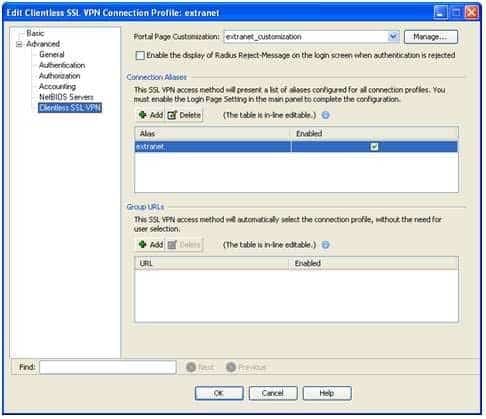
The extranet connection profile will use the DfltGrpPolicy group policy, the local Authentication, Authorization, and Accounting (AAA) database for authentication, and the extranet_customization customization object. When creating a connection profile in Cisco Adaptive Security Device Manager (ASDM), you can specify a number of parameters. For example, you can specify the type of authentication to use and the default group policy to use for VPN connections made by using the connection profile. This information can be configured or modified on the Add or Edit Clientless SSL VPN Connection Profile dialog box in ASDM. To access this dialog box in ASDM, you should click Configuration, click the Remote Access VPN button, expand Clientless SSL VPN Access, and click Connection Profiles. You can then doubleclick a connection profile to open the Edit Clientless SSL VPN Connection Profile dialog box for the selected connection profile. The Edit Clientless SSL VPN Connection Profile dialog box for the extranet tunnel group is shown in the following exhibit:
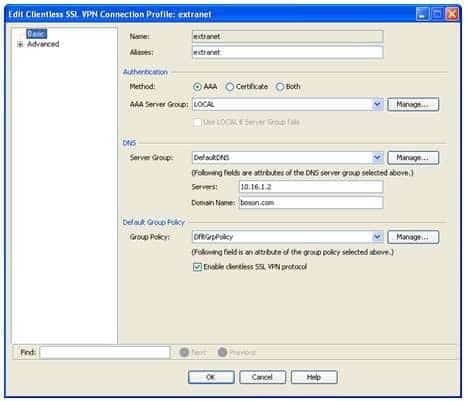
300-735 Part 04 Q12 037 The Authentication section of the Basic screen of the Edit Clientless SSL VPN Connection Profile dialog box indicates that the tunnel group will use the local AAA database for user authentication. Thus any VPN connections made by using this tunnel group will be authenticated against the AAA database.
The Default Group Policy section indicates that the DfltGrpPolicy group policy will be applied to this connection profile. That is, the settings in the DfltGrpPolicy group policy will apply to VPN users who connect by using the extranet tunnel group.
The Clientless SSL VPN screen of the Edit Clientless SSL VPN Connection Profiledialog box indicates that the extranet connection profile will use the extranet_customization customization object. This screen is shown in the following exhibit: -
You are using ASDM to verify a clientless SSL VPN configuration made by a junior administrator on an ASA. Please click exhibit to answer the following questions.Exhibit:
300-735 Part 04 Q13 039 Which of the following statements is true regarding the display of a banner message when users establish a clientless SSL VPN session by using the extranet connection profile? (Select the best answer.)
- No banner message will be displayed.
- A generic banner message will be displayed that states “Welcome to SSL VPN Service.”
- A custom banner message will be displayed that states “Welcome to Boson Software!”
- For each user, a custom banner message will be displayed for each user that states “Welcome user-name.”
Explanation:
No banner message will be displayed when users establish a clientless Secure Sockets Layer (SSL) virtual private network (VPN) session by using the extranet connection profile. You can configure a banner message to be displayed when users establish a clientless SSL VPN connection. This information is configured in the group policy that is associated with the connection profile used to create the connection.
In this scenario, you want to determine whether a banner message will be displayed when the extranet connection profile is used. The extranet connection profile uses the DfltGrpPolicy group policy, so you should view the details of that group policy. To view the details of the DfltGrpPolicy group policy, you should click Configuration, expand Clientless SSL VPN Access, and click Group Policies. You can then doubleclick DfltGrpPolicy (System Default), which will open the Edit Internal Group Policy dialog box, which is shown in the following exhibit:
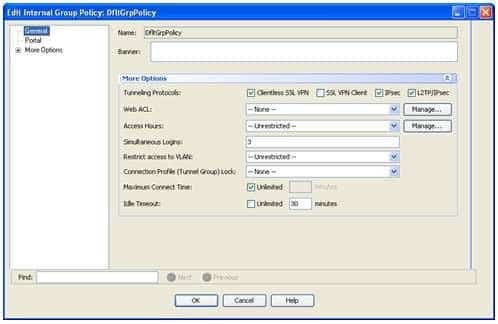
300-735 Part 04 Q13 040 The Banner entry contains no value. As a result, clientless SSL VPN connections made by using connection profiles that use the DfltGrpPolicy group policy will not display a banner to users when they establish a connection.
VPN connections made by using the boson connection profile will display the message “Welcome to Boson Software!” This message will not be displayed for connections made by using the extranet connection profile.
No group policy has been configured with a banner of “Welcome to SSL VPN Service.” In addition, no group policy has been configured with a banner of “Welcome username.” Thus no VPN connections in this scenario will display either of these banner messages. -
You are using ASDM to verify a clientless SSL VPN configuration made by a junior administrator on an ASA. Please click exhibit to answer the following questions.Exhibit:

300-735 Part 04 Q14 041 - No bookmarks will be displayed.
- The boson.com and files.boson.com bookmarks will be displayed.
- The extranet.boson.com and projects.boson.com bookmarks will be displayed.
- The boson.com, files.boson.com, extranet.boson.com, and projects.boson.com bookmarks will be displayed.
Explanation:
The extranet.boson.com and projects.boson.com bookmarks will be displayed to users who establish a clientless Secure Sockets Layer (SSL) virtual private network (VPN) session by using the extranet connection profile. You can create a bookmark list to specify a list of Uniform Resource Locators (URLs) that will be displayed to users when they establish a clientless SSL VPN connection. To configure a bookmark list, you should access the Bookmarks pane of Cisco Adaptive Security Device Manager (ASDM) by clicking Configuration, clicking the Remote Access VPN button, expanding Clientless SSL VPN Access, expanding Portal, and clicking Bookmarks. In this scenario, two bookmark lists have been created: URLs and Extranet. The URLs bookmark list contains two URLs, which are boson.com and files.boson.com. The Extranet bookmark list also contains two URLs, which are extranet.boson.com and projects.boson.com.
The bookmark list that will be applied to a tunnel group is specified in the group policy that is associated with the tunnel group. In this scenario, the extranet tunnel group is linked to the DfltGrpPolicy group policy. Thus you should view the details of this group policy to determine which links will be displayed. This is accomplished by clicking Configuration, clicking the Remote Access VPN button, expanding Clientless SSL VPN Access, selecting Group Policies, and double clicking DfltGrpPolicy (System Default). You should then click Portal, which will display the Portal pane of the Edit Internal Group Policy dialog box, as shown in the following exhibit:

300-735 Part 04 Q14 042 The Bookmark List entry indicates that the Extranet bookmark list is associated with the DfltGrpPolicy group policy. Because this list contains the extranet.boson.com and projects.boson.com URLs, you can conclude that these URLs will be displayed to users who connect by using the extranet tunnel group.
-
Which of the following are inband management tools that do not use encryption? (Select 3 choices.)
- SNMPv1
- SNMPv2
- SNMPv3
- Telnet
- SSH
Explanation:
Of the available choices, Simple Network Management Protocol version 1 (SNMPv1), SNMP version 2 (SNMPv2), and Telnet are all inband management tools that do not use encryption. Encryption is a method of encoding network traffic so that it cannot be read intransit. Thus encryption can be used to defeat eavesdropping attacks.
Simple Network Management Protocol (SNMP) is used to remotely monitor and manage network devices. Telnet is used to create a terminal connection to remote devices. When a Cisco device is operating in its normal state, another device can connect to it by using inband methods, such as virtual terminal (VTY) application protocols.
Three versions of SNMP currently exist. SNMPv1 and SNMPv2 do not provide encryption? password information, known as community strings, is sent as plain text with messages. SNMPv3 improves upon SNMPv1 and SNMPv2 by providing encryption, authentication, and message integrity to ensure that the messages are not tampered with during transmission.
Secure Shell (SSH) is a VTY protocol that can be used to securely replace Telnet. Telnet is considered to be an insecure method of remote connection because it sends credentials over the network in clear text.
Therefore, you should replace Telnet with an encrypted application, such as SSH, where possible. -
Your company’s Cisco ISE device and all of its supplicants support EAPFASTv2. A user’s authentication fails. However, the user’s device attempts to authenticate and succeeds. Which of the following is true? (Select the best answer.)
- The user will have no access.
- The user will have restricted access.
- The user will have full access.
- The device will have full access but the user will have no access.
Explanation:
The user will have restricted access if user authentication to the Cisco Identity Services Engine (ISE) fails but the user’s device authentication succeeds. Extensible Authentication Protocol (EAP)Flexible
Authentication via Secure Tunneling (FAST) with EAP chaining, which is also sometimes called EAPFAST version 2 (EAPFASTv2), enables the validation of both user and device credentials in a single EAP transaction. EAP chaining enables a Cisco security device to validate authentication credentials for both a user and the user’s device. In order to enable EAP chaining, both the Cisco security device and the supplicant device must support EAP chaining.
The Cisco ISE will assign a different level of authorization access depending on one of four success and failure possibilities, as shown in the following table:
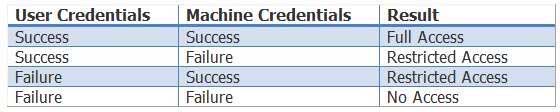
300-735 Part 04 Q16 043 EAP-FAST is an authentication protocol that can be used for pointtopoint connections and for both wired and wireless links. The EAP-FAST authentication process consists of three phases. The first phase, which is optional and is considered phase 0, consists of provisioning a client with a PAC, which is a digital credential that is used for authentication. A PAC can be manually configured on a client, in which case phase 0 is not required. The second phase, which is referred to as phase 1, involves creating a secure tunnel between the client and the server. The final phase, which is referred to as phase 2, involves authenticating the client. If the client is authenticated, the client will be able to access the network.
-
Which of the following features prevent attacks that consume CPU and memory resources? (Select 2 choices.)
- CoPP
- CPPr
- CPU Threshold Notifications
- Memory Threshold Notifications
Explanation:
Control Plane Policing (CoPP) and Control Plane Protection (CPPr) prevent attacks that consume CPU and memory resources. Both CoPP and CPPr use class maps to filter and ratelimit traffic. However, CPPr separates control plane traffic into three subinterfaces: the host subinterface, the transit subinterface, and the Cisco Express Forwarding (CEF)exception subinterface. For this reason, Cisco recommends that you use CPPr instead of CoPP whenever possible. To configure CPPr, you must perform the following steps:
– Create access control lists (ACLs) to identify traffic.
– Create a traffic class.
– Create a traffic policy, and associate the traffic class to the policy.
– Apply the policy to the specific control plane subinterface.
CoPP is similar to CPPr, except CoPP does not separate control plane traffic into three subinterfaces. To configure CoPP, you must perform the following steps:
– Create ACLs to identify traffic.
– Create a traffic class.
– Create a traffic policy, and associate the traffic class to the policy.
– Apply the policy to the control plane interface.The host subinterface contains control plane IP traffic that is destined for a router interface, including traffic from the following sources and protocols:
– Terminating tunnels
– Secure Shell (SSH)
– Simple Network Management Protocol (SNMP)
– Internal Border Gateway Protocol (iBGP)
– Enhanced Interior Gateway Routing Protocol (EIGRP)
The transit subinterface contains control plane IP traffic that is traversing the router, including the following traffic:
– Nonterminating tunnel traffic
– Traffic that is softwareswitched by the route processor
The CEFexception subinterface contains control plane traffic redirected by CEF for process switching, including traffic from the following sources and protocols:
– NonIP hosts
– Address Resolution Protocol (ARP)
– External BGP (eBGP)
– Open Shortest Path First (OSPF)
– Label Distribution Protocol (LDP)
– Layer 2 keepalivesCPU Threshold Notifications and Memory Threshold Notifications do not prevent attacks that consume CPU and memory resources. However, these features can automatically send notifications if excessive CPU or memory consumption is detected. Excessive resource consumption could occur if CoPP or CPPr protection features have been circumvented or are misconfigured. Notifications are typically sent as SNMP trap messages.
-
Which of the following can be detected by the Cisco ESA CASE? (Select 2 choices.)
- snowshoe spam
- phishing attacks
- DDoS attacks
- MAC spoofing attacks
- DNS poisoning attacks
Explanation:
A Cisco Email Security Appliance (ESA) is designed to protect against email threats, such as malware attachments, phishing scams, and spam. The Cisco Context Adaptive Scanning Engine (CASE) on an ESA is a contextual analysis technology that is intended to detect email threats as they are received. CASE checks the reputation of email senders, scans the content of email messages, and analyzes the construction of email messages. As part of this process, CASE submits the email sender to the Cisco SenderBase Network, which contains data on hundreds of thousands of email networks. The sender is assigned a score based on this information. The content of the email messaging is scanned because it could contain language, links, or a call to action that is indicative of a phishing scam.
Snowshoe spammers establish many false company names and identities, often with unique post office addresses and telephone numbers, so that reputation filters do not perceive the source of the spam as a threat. In addition, the spam output is spread across multiple IP addresses and domain names in order to defeat blacklists.
Phishing is a social engineering technique in which a malicious person uses a seemingly legitimate electronic communication, such as email or a webpage, in an attempt to dupe a user into submitting personal information, such as a Social Security number (SSN), account login information, or financial information. To mitigate the effects of a phishing attack, users should use email clients and web browsers that provide phishing filters. In addition, users should also be wary of any unsolicited email or web content that requests personal information. The CASE on a Cisco ESA appliance is capable of detecting phishing scams.
The Cisco ESA CASE does not protect against Distributed Denial of Service (DDoS) attacks. A DDoS attack is a coordinated Denial of Service (DoS) attack that uses multiple attackers to target a single host. For example, a large number of zombie hosts in a botnet could flood a target device with packets.
The Cisco ESA CASE does not protect against Media Access Control (MAC) spoofing attacks. A MAC spoofing attack uses the MAC address of another host on the network in order to bypass port security measures.
The Cisco ESA CASE does not protect against Domain Name System (DNS) poisoning attacks. DNS poisoning is an attack that modifies the DNS cache by providing invalid information. In a DNS poisoning attack, a malicious user attempts to exploit a DNS server by replacing the IP addresses of legitimate hosts with the IP address of one or more malicious hosts. -
You are configuring dynamic PAT on a Cisco ASA 5500 using the CLI. The ASA is running software version 8.3.Which of the following IP addresses must be configured within a network object or object group? (Select the best answer.)
- inside global
- outside global
- inside local
- outside local
Explanation:
Of the available options, an inside local address must be configured within a network object or object group if you are configuring dynamic Port Address Translation (PAT) on a Cisco Adaptive Security Appliance (ASA) 5500 using the command line interface (CLI) if the ASA is running software version 8.3. A local address is a source or destination IP address as seen from the perspective of a host on the inside network.
On a Cisco ASA, a network object is a data structure that is used in place of inline IP information. You might use a network object in place of configuring IP addresses, subnet masks, protocols, and port numbers if you must configure that same information in multiple places. If the information you configure within the object ever changes, you then need only modify the single object instead of locating and modifying each instance of the inline IP information.
An object group is simply a group of network objects. By grouping network objects, you can enable the use of a single application control engine (ACE) to make requests of multiple devices.
An inside local address is an IP address that represents an internal host to the inside network. Inside local addresses are typically private IP addresses defined by Request for Comments (RFC) 1918. When a NAT router receives a packet from a local host destined for the Internet, the router changes the inside local address to an inside global address and forwards the packet to its destination.
You can configure an inside global address inline or as part of a network object or object group on an ASA running software version 8.3. An inside global address is an IP address that represents an internal host to the outside network. Inside global addresses are typically public IP addresses assigned by the administrator of the outside network.
You would not configure an outside global address in this scenario. An outside global address is an IP address that represents an external host to the outside network. Outside global addresses are typically public IP addresses assigned to an Internet host by the host’s operator. The outside global address is usually the address registered with the Domain Name System (DNS) server that maps a host’s public IP address to a friendly name, such as www.example.com.You are not likely to configure an outside local address in this scenario. An outside local address is an IP address that represents an external host to the inside network. The outside local address is often the same as the outside global address, particularly when inside hosts attempt to access resources on the Internet. However, in some configurations, it is necessary to configure a NAT translation that allows a local address on the internal network to identify an outside host. -
Which of the following phishing techniques is most likely to occur as a result of DNS poisoning? (Select the best answer.)
- vishing
- pharming
- whaling
- dumpster diving
Explanation:
Pharming is the phishing technique that is most likely to occur as a result of Domain Name System (DNS) poisoning. Phishing is a social engineering technique in which a malicious person uses a seemingly legitimate electronic communication, such as email or a webpage, in an attempt to dupe a user into submitting personal information, such as a Social Security number (SSN), account login information, or financial information. Pharming is used to retrieve sensitive information by directing users to fake websites. Malicious users can direct users to fake websites through DNS poisoning or host file manipulation. Both DNS and host files are used to crossreference Uniform Resource Locators (URLs) and IP addresses. When a user specifies a URL, either a DNS server or the local host file converts it to an IP address so that requests can be forwarded to the correct location. Both a DNS server and a host file can be altered so that users are directed to websites that appear authentic but instead are used for malicious information gathering. These phony websites often ask users for passwords or other sensitive information. A pharming attack is not effective unless a user voluntarily provides information to the website.
Whaling is a type of spear phishing attack used to retrieve sensitive information from highranking executives of a corporation. Spear phishing is a form of phishing that targets specific individuals. Spear phishing is considered whaling when it specifically targets highranking executives of a corporation, such as chief executive officers (CEOs) or chief financial officers (CFOs). To mitigate the effects of a phishing attack, users should use email clients and web browsers that provide phishing filters. In addition, users should also be wary of any unsolicited email or web content that requests personal information.
Like whaling and pharming, vishing is another form of phishing that is used to obtain sensitive information. Vishing accomplishes its goal through the use of voice communication networks. Perpetrators of vishing attacks use a variety of methods to retrieve information. For example, an attacker might spoof phone numbers of legitimate businesses in order to deceive a victim. An attacker might also use a misleading voice or email message that instructs the potential victim to contact a phony call center that is masked as a legitimate business. After telephone communications are established, the perpetrators will attempt to coax sensitive information from users, such as credit card or bank account numbers.
Dumpster diving is an attack in which malicious users obtain information that has been thrown in the trash. Dumpster divers seek to recover discarded documents that might contain sensitive information such as account login credentials, passwords, or bank account numbers. To prevent unauthorized users from obtaining information from discarded documents, individuals and companies should shred documents containing confidential data before disposing of such documents.