300-735 : Automating Cisco Security Solutions (SAUTO) : Part 05
-
The Serial 0/0 interfaces on Router1 and Router2 are directly connected on the 192.168.51.48/30 network. You issue the following commands on Router1:
interface serial 0/0 ip ospf messagedigestkey 1 md5 b0s0n router ospf 1routerid 1.1.1.1 network 10.10.10.0 0.0.0.255 area 1 network 192.168.51.48 0.0.0.3 area 0 area 0
authenticationYou issue the following commands on Router2:
interface serial 0/0 ip ospf authenticationkey b0s0n router ospf 2routerid 2.2.2.2 network 10.10.20.0 0.0.0.255 area 2 network 192.168.51.48 0.0.0.3 area 0 area 0 authentication
Router1 and Router2 do not form an OSPF adjacency.
Which of the following is most likely the problem? (Select the best answer.)
- an OSPF area mismatch
- an OSPF authentication mismatch
- an OSPF process ID mismatch
- an OSPF router ID mismatch
Explanation:
Of the available choices, a mismatched authentication type is most likely to be the cause of the problem in this scenario. A mismatched authentication key or a mismatched authentication type could cause two Open
Shortest Path First (OSPF) routers to not form an adjacency. In this scenario, the Serial 0/0 interface on Router1 is configured to use a Message Digest 5 (MD5) authentication key of b0s0n. The Serial 0/0 interface on Router2, on the other hand, is configured to use a plaintext authentication key of b0s0n. If the correct authentication type were configured between the Serial 0/0 interfaces on the routers, OSPF authentication would succeed and an adjacency would be formed.
A mismatched process ID will not prevent an OSPF router from establishing an adjacency with a neighbor. An OSPF process ID is used to identify the OSPF process only to the local router. In this scenario, the router ospf 1 command has been issued on Router1, which configures Router1 with an OSPF process ID of 1. The router ospf 2 command has been issued on Router2, which configures Router2 with an OSPF process ID of 2. An OSPF area mismatch is not the reason that Router1 and Router2 do not form an adjacency in this scenario. In order to establish an adjacency, OSPF routers must be configured with the same area ID, Hello timer value, Dead timer value, and authentication password. In this scenario, the Serial 0/0 interface on Router1 has been configured to operate in area 0, which is also known as the backbone area. Similarly, the Serial 0/0 interface on Router2 has been configured to operate in area 0.
OSPF router IDs should never match between routers. A router ID is a unique 32bit identifier that resembles an IP address. A router ID conflict could cause routers to not form an adjacency. If you do not manually configure a router ID on an OSPF router, then the router ID is the highest IP address configured among loopback interfaces on the router, even if a physical interface is configured with a higher IP address. Cisco recommends using a loopback interface instead of a physical interface for the router ID? a loopback interface is never in the down state, thus OSPF is considered to be more stable when the router ID is configured from the IP address of a loopback interface. In this scenario, the router IDs on Router1 and Router2 have been manually configured by using the routerid ipaddresscommand. -
In which of the following authentication protocols is support for TLS 1.2 specifically required? (Select the best answer.)
- EAPFASTv1
- EAPFASTv2
- EAPMD5
- EAPTLS
- EAPPEAP
Explanation:
Of the available choices, only Extensible Authentication ProtocolFlexible Authentication via Secure Tunneling Version 2 (EAPFASTv2) is specifically required to support Transport Layer Security (TLS) 1.2. EAPFAST is an authentication protocol that can be used for pointtopoint connections and for both wired and wireless links. EAPFAST Version 1 (EAPFASTv1) supported TLS 1.0 and higher. However, EAPFASTv2 made support of TLS 1.2 a requirement, thereby providing EAPFASTv2 with a stronger encryption algorithm than EAPFASTv1.
EAPTransport Layer Security (EAPTLS) does not specifically require support for TLS 1.2, although EAPTLS is designed to support TLS 1.0 and higher. EAPTLS is an Internet Engineering Task Force (IETF) standard that is defined in Request for Comments (RFC) 5216.
Protected EAP (PEAP) does not specifically require support for TLS 1.2. PEAP is an open standard developed by Cisco, Microsoft, and RSA. PEAP and other later variants of EAP, such as EAPTLS, and EAPTunneled TLS (EAPTTLS), are replacing Lightweight EAP (LEAP). PEAP supports TLS 1.0 and higher.
EAP Message Digest 5 (EAPMD5) does not specifically require support for TLS 1.2. EAPMD5 uses an MD5 hash function to provide security and is therefore considered weak when compared to later methods. EAP is an IETF standard that was originally defined in RFC 2284. It does not support TLS at all. -
Router2 is configured to obtain time from three different NTP servers. You want to determine from which of the three servers Router2 is currently synchronizing time.Which of the following commands would not achieve your goal? (Select the best answer.)
- show clock detail
- show ntp associations
- show ntp associations detail
- show ntp status
Explanation:
Of the available choices, only the show clock detail command would not enable you to determine from which of the three Network Time Protocol (NTP) servers Router2 is synchronizing time. The show clock detail command displays the date and time as it is configured on the device and general information about the source of the configuration. However, this command does not reveal the IP address or NTP peer status of an NTP source. The following is sample output from the show clock detail command:
Router2#show clock detail
09:12:20.299 UTC Sat Jul 4 2015
Time source is NTP
The show ntp associations command and the show ntp associations detail command would both enable you to determine from which of the three NTP servers Router2 is synchronizing time. The show ntp associations command displays both the address of the NTP server from which the client obtains its time and the address of the reference clock to which the NTP server is synchronized. When issued with the detail keyword, you can additionally determine the IP address of the NTP peer from which time was synchronized, the NTP source authentication status, the NTP hierarchical status of the server from which time was obtained, whether the NTP peer passes basic sanity checks, whether NTP believes the time is valid, and the stratum of the NTP peer. The following is sample output from both the show ntp associations command and the show ntp associations detail command:
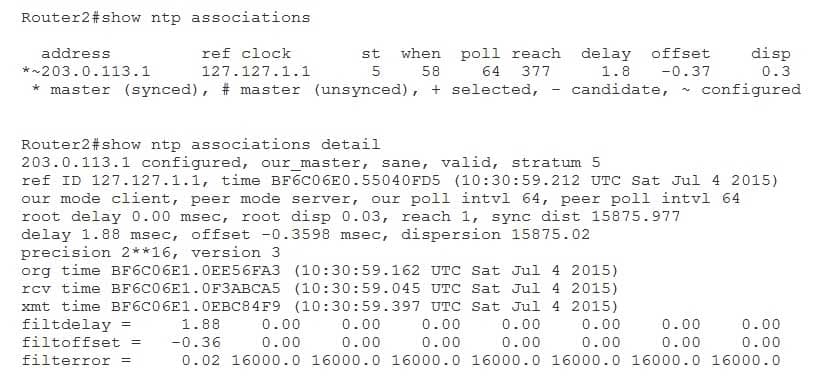
300-735 Part 05 Q03 044 The presence of our_master in the output of the show ntp associations detail command indicates the status of the device at the NTP peer IP address of 203.0.113.1. Similarly, the asterisk (*) in the output of the show ntp associations command indicates that Router2’s NTP master is the device with the IP address of 203.0.113.1.
The show ntp status command would enable you to determine from which of the three NTP servers Router2 is synchronizing time. The show ntp status command displays no information when NTP is not running on a device. When NTP is running, the show ntp status command provides information about whether the local clock is synchronized, the local clock’s stratum level, and the IP address of the NTP peer that the local device is using as a reference clock. The following is sample output from the show ntp status command: -
Which of the following indicates that aggressive mode ISAKMP peers have created SAs? (Select the best answer.)
- AG_NO_STATE
- MM_NO_STATEC. AG_AUTH
- MM_KEY_AUTH
- QM_IDLE
Explanation:
Of the available choices, the AG_NO_STATE state is most likely to indicate that aggressive mode Internet
Security Association and Key Management Protocol (ISAKMP) peers have created security associations (SAs). The show crypto isakmp sa command displays the status of current IKE SAs on the router. The following states are used during aggressive mode:
– AG_NO_STATE – The peers have created the SA.
– AG_INIT_EXCH – The peers have negotiated SA parameters and exchanged keys.
– AG_AUTH – The peers have authenticated the SA.The MM_NO_STATE state is the first transaction to occur when setting up Internet Key Exchange (IKE) SAs in main mode MM_NO_STATE indicates that the ISAKMP peers have created their SAs. However, an exchange that does not move past this stage indicates that main mode has failed. The following states are used during main mode:
– MM_NO_STATE – The peers have created the SA.
– MM_SA_SETUP – The peers have negotiated SA parameters.
– MM_KEY_EXCH – The peers have exchanged DiffieHellman (DH) keys and have generated a shared secret.
– MM_KEY_AUTH – The peers have authenticated the SA.
Quick mode is used during IKE phase 2. The only state in quick mode is QM_IDLE, which indicates that IKE phase 1 has completed successfully and that there is an active IKE SA between peers. - Which of the following is least likely to be considered an advanced persistent threat? (Select the best answer.)
- Operation Aurora
- Heartbleed
- the 2011 RSA breach
- Stuxnet
Explanation:
Of the available options, Heartbleed is least likely to be considered an advanced persistent threat. An advanced persistent threat is an intrusion in which the attacker has advanced knowledge of intrusion tools and techniques, is fully intent on using the intrusion to achieve a specific mission or goals, and has organizational backing, funding, and motivation. For example, an attacker who obtains access to an organization’s network and remains there for an extended period of time to collect data that can then be used to the attacker’s advantage can be considered an advanced persistent threat.
Heartbleed is a vulnerability, not an advanced persistent attack. Heartbleed is the OpenSSL vulnerability that could allow an attacker to obtain approximately 64 kilobytes (KB) of information from a web server’s memory at regular intervals. The Heartbleed bug, which was discovered in 2014, was a memoryhandling bug present in OpenSSL from version 1.0.1 through version 1.0.1f. OpenSSL 1.0.1g was the first version to fix the bug. By exploiting this vulnerability, an attacker can obtain a server’s private key, which could in turn allow the attacker to decrypt communications with the server or perform maninthemiddle attacks against the server. Although Heartbleed could be used as a component of an attack in an advanced persistent threat, it is not itself an advanced persistent threat.
Operation Aurora could be considered an advanced persistent threat. Operation Aurora was a monthslong attack in 2009 that was carried out against multiple companies, including Google and Adobe? it began with a targeted email spear phishing attack. The email delivered malware that was capable of exploiting an Internet Explorer vulnerability to obtain access to the contents of partially freed memory. After compromising company workstations, the attackers used those workstations to obtain access to other company resources and information, which eventually resulted in the loss of intellectual property. The attack was eventually traced to two Chinese education facilities that were thought to have ties to a Google competitor in China.
The 2011 RSA breach could be considered an advanced persistent threat. The RSA breach was an attack against RSA’s SecurID twofactor authentication system. Similar to Operation Aurora, the 2011 RSA breach began with a targeted phishing email that contained a Microsoft Excel attachment. The Excel attachment contained a zeroday exploit that was able to install a back door on a user’s workstation. From there, the attacker compromised other workstations in what appeared to be an effort to retrieve information related to SecurID, such as source code or customer information.
Stuxnet is more likely than Heartbleed to be considered an advanced persistent threat. Stuxnet exploited vulnerabilities in both the printer spooler service and the processing of .lnk files. Stuxnet was used in an act of cyber warfare against Iranian industrial control systems (ICSs). It was written to target specific ICSs by modifying code on programmable logic controllers (PLCs). Stuxnet initially exploited vulnerabilities in the printer spooler service? however, later variants exploited a vulnerability in the way that Windows processes shortcuts (.lnk files). Research from Symantec published in 2011 indicated that at the time, over 60% percent of the Stuxnetaffected hosts had been in Iran. Symantec analyzed Stuxnet and its variants and discovered that five organizations were the primary targets of infection and that further infections were likely collateral damage from the aggressive manner in which the worm spreads throughout the network. Given the considerable cost in resources and manhours that would have been required to craft the Stuxnet worm, it was theorized that it was likely intended to sabotage highvalue targets such as nuclear materials refinement facilities. -
Which of the following best describes the purpose of SNMP? (Select the best answer.)
- to manage network devices
- to send email
- to create VPNs
- to transfer files
Explanation:
Simple Network Management Protocol (SNMP) is used to manage network devices. SNMP can be used to remotely monitor and configure a wide variety of network devices, such as routers, switches, and network printers. SNMP version 1 (SNMPv1) and SNMPv2 use community strings to provide authentication. However, neither SNMPv1 nor SNMPv2 uses encryption? all data and community strings are sent in clear text. A malicious user can sniff an SNMP community string and use it to access and modify network devices. SNMPv3 is an enhancement to the SNMP protocol that uses encryption to provide confidentiality, integrity, and authentication.
SNMP is not used to send email. Simple Mail Transfer Protocol (SMTP) is used to send email. Post Office Protocol 3 (POP3) and Internet Message Access Protocol 4 (IMAP4) are used to receive email.
SNMP is not used to create virtual private networks (VPNs). To create a VPN, you would typically use a protocol that can encrypt the data on the virtual network, such as IP Security (IPSec). A VPN is often used when it is necessary to connect two locations that are separated by a public network, such as the Internet.
SNMP is not used to transfer files. To transfer files between computers, you should use File Transfer Protocol (FTP), Trivial FTP (TFTP), or Secure FTP (SFTP). -
You create a static pointtopoint VTI tunnel on RouterA. Afterward, you issue the show runningconfig command and receive the following output:
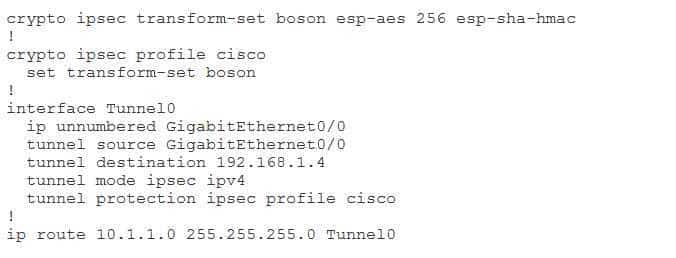
300-735 Part 05 Q07 046 Which of the following is the authentication transform that will be used by the static VTI tunnel? (Select the best answer.)
- ESP with 128bit AES
- ESP with 256bit AES
- ESP with 56bit DES
- ESP with 168bit 3DES
- ESP with MD5
- ESP with SHA
- AH with MD5
- AH with SHA
Explanation:
The static virtual tunnel interface (VTI) tunnel will use Encapsulating Security Payload (ESP) with Secure Hash Algorithm (SHA) as the authentication transform, as indicated by the crypto ipsec transformset command. The syntax of the crypto ipsec transformset command is crypto ipsec transformset transformname transform1 [transform2] [transform3] [transform4]. Up to four transforms can be specified in an IP Security (IPSec) transform set: one ESP authentication transform, one authentication header (AH) transform, one ESP encryption transform, and one IP compression transform.
ESP can use the Message Digest 5 (MD5) and SHA algorithms for authentication. The following keywords can be used to specify the ESP authentication transform:
– espmd5hmac
– espshahmacAH can also use the MD5 and SHA algorithms for authentication. The following keywords can be used to specify the AH transform:
– ahmd5hmac– uses AH with MD5
– ahshahmac
– uses AH with SHAESP can use the following encryption methods:
-128bit, 192bit, and 256bit Advanced Encryption Standard (AES)
– 56bit Data Encryption Standard (DES)
– 168bit Triple DES (3DES)
-160bit Softwareoptimized Encryption ALgorithm (SEAL)
-Null encryptionThe following keywords can be used to specify the ESP encryption transform:
– espies
– espaes 192
– espaes 256
– espdes
– esp3des
– espseal
– espnullThe LempelZivStac (LZS) algorithm is the only IP compression method that can be used in an IPSec transform set. To configure a transform set to use LZS IP compression, you should use the complzs keyword.
-
To ease administrative overhead, you want to add a third party feed to a Security Intelligence device so that the IP addresses of known malicious hosts are automatically blacklisted. However, you have not determined whether the feed is valid. Which of the following are you most likely to do? (Select the best answer.)
- Implement the feed, and add IP addresses to a custom whitelist as necessary.
- Enforce Security Intelligence filtering by Security Zone.
- Configure the monitor-only setting, and examine the logs.
- Configure a custom blacklist that contains only malicious IP addresses.
Explanation:
Most likely, you will configure the monitor-only setting and examine the logs if you want to add a thirdparty feed to a Security Intelligence device but you have not determined whether the feed is valid. Security Intelligence devices, such as a Cisco Sourcefire Intrusion Prevention System (IPS), are capable of accepting manually imported lists of network addresses or feeds from third parties. Such devices can block IP addresses or networks based on their reputation, which mitigates device overhead that comes from having to analyze traffic from those networks.
The monitor-only setting enables traffic from networks that are listed within a given feed to be analyzed by the Security Intelligence device but also logs the fact that the given network matches the thirdparty feed. This enables an administrator to review the logs and the analysis of traffic from networks on the feed to determine the validity of the feed.
Although you could implement the feed and add IP addresses to a custom whitelist as necessary, doing so might increase administrative overhead if the feed turns out to be invalid. On Security Intelligence devices, whitelists can be used to override blacklisted IP addresses. Whitelists can thus be used to enable communication with legitimate IP addresses that are listed on third-party feeds or other blacklists that might be too broadly defined. From an administrative overhead standpoint, you are more likely to validate the feed, then implement the feed, and finally add IP addresses or networks to the whitelist as necessary.
You are less likely to enforce Security Intelligence filtering by Security Zone than configure the monitor only setting in this scenario, because doing so would neither validate nor invalidate the IP addresses that are contained on the third-party feed. Enforcing blacklisting by security zone can be used to enhance the performance of a Security Intelligence device by limiting the blacklisting to the specific security zones that process the given traffic. For example, the blacklisting of IP addresses that send email traffic could be restricted to a Security Zone that handles only email traffic.
You are not likely to configure a custom blacklist that contains only malicious IP addresses, because doing so defeats the purpose of easing administrative overhead in this scenario. Security Intelligence devices allow the creation of custom blacklists so that you can manually block specific IP addresses or networks. However, compiling and validating such a list would require more administrative overhead in this scenario than simply validating a third-party feed prior to implementing it. -
Which of the following is primarily true of SEM systems? (Select the best answer.)
- They perform real-time analysis and detection.
- They focus on policy and standards compliance.
- They consolidate logs to a central server.
- They analyze log data and report findings.
Explanation:
Security Event Management (SEM) systems perform realtime analysis and detection. SEM systems typically analyze log data from a number of sources. Some systems also incorporate incident handling tools that enable administrators to more effectively mitigate threats when they occur.
Security Information Management (SIM) systems, on the other hand, are focused more on the collection and analysis of logs in a nonrealtime fashion. For example, a SIM system might centralize logging on a single device for review and analysis. Some SIM systems also provide assessment tools that can flag potentially threatening events.
A Security Information and Event Management (SIEM) system combines both the realtime aspects of a SEM system and the indepth analysis and timeline generation of a SIM system. Therefore, a SIEM system is a hybrid of a SIM system and a SEM system. -
You want to configure Cisco ISE as a SCEP proxy to a Microsoft Windows 2008 R2 Server root CA. Which of the following also needs to be configured? (Select the best answer.)
- AD on the CA
- a root CA on the Cisco ISE
- a manually installed certificate on the connecting BYOD device
- NDES on a CA or domain member server
Explanation:
Microsoft Network Device Enrollment Service (NDES) on a certificate authority (CA) or domain member server also needs to be configured if you want to configure Cisco Identity Services Engine (ISE) as a Simple Certificate Enrollment Protocol (SCEP) proxy to a Microsoft Windows 2008 R2 Server root CA.
Implementing ISE as a SCEP proxy enables bring your own device (BYOD) users to register their devices on their own, without administrative overhead from the IT department.
You are not required to configure a root CA on the Cisco ISE. Configuring ISE as a SCEP proxy indicates that ISE communicates with the CA on the behalf of its client devices. However, the ISE does need to be configured with a SCEP CA profile. When configured with a SCEP CA profile, the ISE will contain a SCEP NDES server registration authority (RA) certificate in the Certificate Store. RAs verify requests for certificates and enable the CA to issue them.
You are not required to configure Active Directory (AD) on the CA. AD is typically configured on domain controllers, although member servers and workstations can connect to the AD domain.
You are not required to manually install a certificate on the connecting BYOD device. Manually installing a client certificate on the BYOD device would defeat the purpose of configuring the ISE as a SCEP proxy, because administrative intervention would be required. -
You issue the following commands on a Cisco router:
tacacsserver host ts1 single-connection timeout 20
tacacsserver timeout 30Which of the following are true about how the Cisco router communicates with the TACACS+ server? (Select 2 choices.)
- The router will maintain an open TCP connection.
- The router will maintain an open TCP connection for no more than 20 seconds.
- The router will maintain an open TCP connection for no more than 30 seconds.
- The router will wait 20 seconds for the server to reply before declaring an error.
- The router will wait 30 seconds for the server to reply before declaring an error.
Explanation:
The router will maintain an open Transmission Control Protocol (TCP) connection. In addition, the router will wait 20 seconds for the server to reply before declaring an error. The tacacsserver host ts1 single connection timeout 20 command in this scenario configures a router to connect to a Terminal Access Controller Access Control System Plus (TACACS+) server named ts1. The single connection keyword configures the router to maintain an open connection to the TACACS+ server. The timeout 20 keyword configures the router to wait 20 seconds for the TACACS+ server to reply before declaring an error with the connection.
The router will not wait 30 seconds for the server to reply before declaring an error. The tacacsserver host ts1 single connection timeout 20 command in this scenario configures the router to wait only 20 seconds for the server to reply before declaring an error. If the timeout 20 keyword had not been specified in this scenario, the tacacsserver timeout 30 command would have configured the router to wait 30 seconds for the server to reply before declaring an error. The timeout 20 keyword in this scenario overrides the value assigned by the tacacsserver timeout command.
The router will maintain an open connection for an indeterminate amount of time, not for a 20second or 30second interval. When the single connection keyword is not configured, a Cisco router will open and close a TCP connection to the TACACS+ server each time it needs to perform an operation. When the single connection keyword is configured, the router connects to the TACACS+ server and maintains that connection even when it is not performing an operation. This setting enhances the efficiency of the communications between the router and the TACACS+ server because the router is not having to constantly close and open connections. -
You want to implement a VPN with an alwayson fail close policy for Cisco AnyConnect clients. Which of the following does Cisco recommend that you do? (Select the best answer.)
- Start with a fail open policy, and implement fail close in phases.
- Start with the fail close policy, and implement fail open as necessary.
- Implement always-on, and leave the failure policy at the default setting.
- Implement always-on with a fail open policy, and enable the Disconnect button.
Explanation:
Cisco recommends that you start with a fail open policy and implement fail close in phases if you want to implement a virtual private network (VPN) with an always on fail close policy. The always on feature enables Cisco AnyConnect clients to establish a VPN session automatically whenever the client detects that the host is connected to an untrusted network. For example, a laptop that is used both on a corporate LAN and for remote work might be configured to automatically connect to the corporate VPN whenever the laptop is not directly connected to the corporate LAN. However, any number of problems could prevent the client from actually establishing a connection to the VPN.
There are two types of connect failure policies that you can enable for Cisco AnyConnect always on clients. The fail open policy allows the client to complete a connection to the local network for access to the Internet or local resources. However, because a VPN session has not been established, the security of the AnyConnect device that is connected to the remote network could be compromised.
The fail closed policy, on the other hand, prevents all network access from the Cisco AnyConnect client except to local devices and devices that are available by using split tunneling. This extra layer of security could prevent the user from accessing the Internet and thus could compromise productivity if the user relies on Internet access to complete work related tasks. Because the fail closed policy is so restrictive, Cisco recommends implementing it by using a phased approach that includes initially implementing fail open and surveying user activity for AnyConnect issues that might prevent seamless connections.
There is no need to enable the Disconnect button, because the button is enabled by default when the always on feature is enabled. The Disconnect button enables users to manually disconnect from a VPN session that has been automatically established by the AnyConnect client. The Disconnect button can be disabled by an administrator.
Cisco does not recommend leaving the failure policy at the default setting if you want to implement a fail close policy. The fail close policy is the default failure policy when connect failure policies are enabled. -
Your company is using a shopping cart web application that is known to be vulnerable to a code injection attack. Your company has no support agreement for the application, and the application is no longer updated by its author. Modifying the code would require the hiring of additional help and an extensive interview process.
Which of the following should your company do in the meantime to most quickly mitigate the threat? (Select the best answer.)
- Use the grep command to examine web logs for evidence of an attack.
- Shut down the site.
- Replace the shopping cart application with a different one.
- Implement a WAF.
Explanation:
Your company should implement a web application firewall (WAF) to mitigate the shopping cart web application threat. A WAF sits between a web application and the end user in order to protect the application from malicious activity and known vulnerabilities. Therefore, by installing a WAF, it is possible to protect a vulnerable web application without modifying the application code.
Although you should issue the grep command to examine web application logs for evidence of an attack, doing so would not quickly mitigate the threat posed by the unpatched vulnerability. Searching for evidence of an attack takes time. Even if evidence of an attack were found in the log, discovering that evidence does not mitigate the threat.
Although you should consider replacing the shopping cart application with a different one that is supported and regularly updated, doing so would not be the quickest way to mitigate the threat. Depending on the complexity of the data and the availability of conversion tools, it could take many weeks or months to successfully migrate a shopping cart from one web application to another.
You should not shut down the site. Shutting down the site would cause a severe business interruption because users would no longer be able to purchase products by using the shopping cart. -
Which of the following is a Cisco IPS appliance feature that analyzes normal network activity to detect hosts that are infected with worms? (Select the best answer.)
- anomaly detection
- global correlation
- reputation filtering
- a signature definition
- a threat rating
Explanation:
Anomaly detection is a Cisco Intrusion Prevention System (IPS) appliance feature that analyzes normal network activity to detect hosts that are infected with worms. The IPS anomaly detection feature enables IPS to learn what type of network activity is normal activity for the network that is being protected. If a network starts to become congested by traffic that is generated by a worm or if a host that is infected with a worm connects to the network and attempts to infect other hosts, the anomaly detection feature can trigger a specific response, such as denying traffic from the infected host or alerting an administrator.
Signature definitions do not analyze normal network activity to detect hosts that are infected with worms. A signature definition is a set of rules to which a Cisco IPS appliance can compare network traffic to determine whether an attack is occurring. If the network activity matches a signature definition, IPS can trigger a specific response from other defined event action rule sets, such as denying traffic from a host or alerting an administrator. IPS administrators can manually configure signature definitions in Cisco IPS Device Manager (IDM) or use the Signature Wizard to create custom signature definitions.
Global correlation does not analyze normal network activity to detect hosts that are infected with worms. Global correlation enables IPS sensors to allow or deny traffic based on the reputation of the sending device. When you enable global correlation, IPS devices will periodically receive updates that include information about known malicious devices on the Internet from the Cisco Sensor Base Network. In addition, global correlation will send statistical information about attacks against your company’s network to the Cisco Sensor Base Network. Cisco uses that information to detect threat patterns on the Internet.
Reputation filtering does not analyze normal network activity to detect hosts that are infected with worms. Reputation filtering denies packets from hosts that are considered to have a malicious reputation based on the global correlation information that is available from the Cisco Sensor Base Network. Reputation filtering is different from global correlation inspection in that reputation filtering denies traffic before the traffic is compared to any signature definitions. In addition, reputation filtering does not generate alerts.
Threat ratings do not analyze normal network activity to detect hosts that are infected with worms. A threat rating is an event action risk rating that has been lowered because of a specific action taken by IPS. A risk rating is a numerical representation of the risk presented to a network by a specific attack. Risk ratings can range from 0 through 100. Depending on the actions IPS has taken in response to an event, IPS will subtract a value from the threat rating of the event. For example, if IPS responds to a specific event by issuing a request to block the attacking host, a value of 20 will be subtracted from the threat rating. -
Which of the following can be used to encrypt email messages, files, and disk drives? (Select the best answer.)
- L2TP
- PEM
- PGP
- S/MIME
Explanation:
Pretty Good Privacy (PGP) is software that can be used to encrypt email messages, files, and disk drives. PGP can be used to provide confidentiality, integrity, and nonrepudiation. PGP uses an asymmetric encryption method to encrypt information. To encrypt a file or a message by using PGP, you must use the recipient’s public key. The recipient will then use his or her private key to decrypt the file or message. Many modern operating systems (OSs) offer their own builtin support for file level and disk level encryption. Therefore, third-party software is often no longer necessary for encrypting files.
Privacy Enhanced Mail (PEM) and Secure/Multipurpose Internet Mail Extensions (S/MIME) can be used to encrypt email messages, but they cannot be used to encrypt files or disk drives. PEM is defined in Requests for Comments (RFCs) 1421 through 1424 but was never widely used. S/MIME, which was created by RSA Data Security, is now an RFC standard defined in RFCs 3369, 3370, 3850, and 3851.
Although Layer 2 Tunneling Protocol (L2TP) can be used along with an encryption protocol to encrypt files and email messages while they are sent over a virtual private network (VPN), L2TP is not used to encrypt disk drives. L2TP does not offer any security on its own but provides the tunnel by which IP packets encapsulated in User Datagram Protocol (UDP) packets can travel. -
Refer to the exhibit:
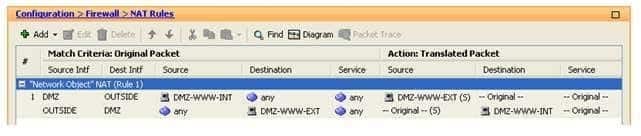
300-735 Part 05 Q16 047 You have created a network object NAT rule in ASDM to translate the real IP address of a DMZ web server, DMZWWWINT, to an IP address in the OUTSIDE network, DMZWWWEXT. The DMZ interface has a
security level of 50, and the OUTSIDE interface has a security level of 0. In addition, the ASA is running system software version 8.4.
Which of the following statements are true regarding the ACL that will be required to enable hosts in the OUTSIDE network to communicate with the DMZ web server? (Select 2 choices.)- The ACL should be applied to the OUTSIDE interface.
- The ACL should be applied to the DMZ interface.
- The ACL should reference the DMZWWWEXT object as its source address.
- The ACL should reference the DMZWWWEXT object as its destination address.
- The ACL should reference the DMZWWWINT object as its destination address.
Explanation:
In this scenario, the access control list (ACL) should be applied to the OUTSIDE interface and should reference the DMZWWWINT object as its destination address. The Network Address Translation (NAT) rule in this scenario creates a static mapping between the address of the web server in the DMZ network, which has been defined as an object named DMZWWWINT, and an address in the OUTSIDE network, which has been defined as an object named DMZWWWEXT. This static mapping enables hosts on the outside network to communicate with the DMZ web server by using the DMZWWWEXT address. However, the Cisco Adaptive Security Appliance (ASA) will deny inbound traffic from the OUTSIDE interface by default unless it is return traffic from an existing connection or an ACL exists which explicitly permits the traffic.
You can view, edit, and add ACLs from the Configuration > Firewall > Access Rules pane in Adaptive Security Device Manager (ASDM). By default, the Access Rules pane contains implicit rules that permit traffic from higher security interfaces to lower security interfaces and that deny all traffic that has not been otherwise permitted, as shown in the following exhibit:

300-735 Part 05 Q16 048 You can click the Add button in the Access Rules pane to create a new ACL. When you click the Add button, ASDM will display the Add Access Rule dialog box, as shown in the following exhibit:
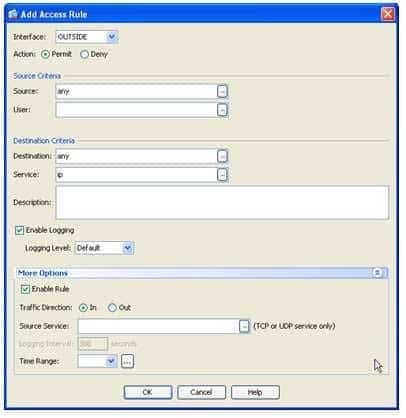
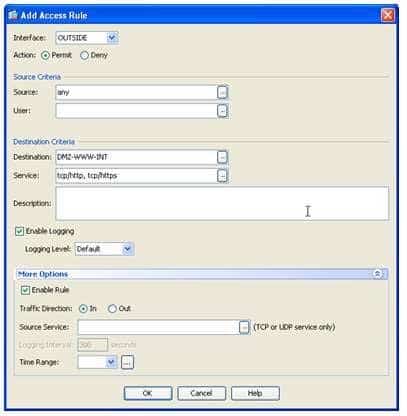
300-735 Part 05 Q16 049 In the Add Access Rule dialog box, you should click the Interface dropdown and select the OUTSIDE interface if it is not already selected. The ACL should be applied to the OUTSIDE interface? otherwise, the traffic from the OUTSIDE network would be denied before reaching any of the other ASA interfaces. You should ensure that the Permit radio button is selected in order to permit the traffic specified by the ACL. The Source Criteria section of the Add Access Rule dialog box can maintain its default values because traffic from any source and user should be permitted to access the DMZ web server. The network object corresponding to the DMZ web server should be specified in the Destination field of the Destination Criteria section. Because the ASA is running a system software revision that is greater than or equal to version 8.3, the ACL required for this scenario must use the object named DMZWWWINT as its destination and not the object named DMZWWWEXT, as would be the case for system software revisions less than version 8.3. Finally, the Service field should be used to specify the protocols that will be permitted by the ACL. By default, all IP traffic is permitted? however, as this rule will apply to a web server, it is more secure to limit the permitted protocols to Hypertext Transfer Protocol (HTTP) and Secure HTTP (HTTPS). You can either type the protocol object names into the field, or click the browse button to select protocols from a list. By default, the Add Access Rules dialog box enables the rule in the inbound direction, which is precisely what is needed in this scenario. The following exhibit shows the Add Access Rules dialog box with sample values that would be suitable for this scenario:
300-735 Part 05 Q16 050 When you click the OK button, the Access Rules pane will automatically update to display the newly created ACL, as shown in the following exhibit:

300-735 Part 05 Q16 051 You would not apply an ACL to the DMZ interface. Although you could apply a similar ACL to the DMZ interface in the outbound direction, traffic from the OUTSIDE interface would be denied by the implicit Global policy before it had a chance to reach the DMZ interface. There is no need to apply an ACL to the DMZ interface in the inbound direction because traffic from higher security interfaces is permitted to lower security interfaces by default. You would not need to supply a source address to the ACL in this scenario, because all traffic passing through the OUTSIDE interface in the inbound direction is specified instead. Although you could specify individual hosts or subnets in a similar ACL, it is significantly more efficient to specify any traffic on the OUTSIDE interface. Typically, the OUTSIDE interface of an ASA connects to the greatest number of additional networks, such as the Internet, and it would quickly become impractical to specify all permitted hosts or subnets.
-
According to the branch location ACL design guidelines in the Cisco BYOD Design Guide, which protocols should not be permitted by the default ACL that is applied to the access ports of a Layer 2 switch? (Select 2 choices.)
- BOOTP
- DNS
- HTTP
- HTTPS
- ICMP
- TFTP
Explanation:
According to the branch location access control list (ACL) design guidelines in the Cisco Bring Your Own Device (BYOD) Design Guide, Hypertext Transfer Protocol (HTTP) and Secure HTTP (HTTPS) should not be permitted by the default ACL that is applied to the access ports of a Layer 2 switch. In a BYOD environment, 802.1X, Web Authentication (WebAuth), or Media Access Control (MAC) Authentication Bypass (MAB) are used to authenticate and authorize the user and the user’s associated device for network access. Once a wired device authenticates with the Cisco Identity Services Engine (ISE), a downloadable ACL (dACL) is typically applied to the appropriate access port on the Layer 2 switch to which the device is attached. HTTP and HTTPS traffic should be permitted by an ACL that is used to redirect web traffic to the ISE for browserbased authentication if 802.1x or MAB authentication are unavailable. Cisco recommends denying Domain Name System (DNS) traffic or specifically excluding the IP address of the ISE to prevent redirection loops. For example, the following ACL denies DNS traffic and permits HTTP and HTTPS traffic for redirection to the ISE:switch(config)#ip accesslist extended REDIRECT-ACL switch(configextnacl)#deny udp any any eq domain switch(configextnacl)#permit tcp any any eq www switch(configextnacl)#permit tcp any any eq 443
Cisco recommends applying a default ACL to the access ports of Layer 2 switches to mitigate against situations where a configuration error might prevent a dACL from being applied to the appropriate access port during the authorization/authentication process. The default ACL should permit Bootstrap Protocol (BOOTP), DNS, Trivial File Transfer Protocol (TFTP), and Internet Control Message Protocol (ICMP). In addition, the default ACL should explicitly deny and log all other IP traffic. For example, the following ACL complies with Cisco’s best common practices (BCP) as outlined in the BYOD Design Guide:
switch(config)#ip accesslist extended DEFAULT-ACL switch(configextnacl)#permit icmp any any switch(configextnacl)#permit udp any eq bootpc any eq bootps switch(configextnacl)#permit udp any any eq domain switch(configextnacl)#permit udp any any eq tftp switch(configextnacl)#deny ip any any log
-
You have issued the following commands to modify the 802.1X configuration on a switch port:
switch(configif)#authentication order mab dot1x switch(configif)#authentication priority dot1x mab switch(configif)#authentication event fail action nextmethod switch(configif)#authentication event noresponse action authorize vlan 1313
A new host is attached to the switch port. The host’s MAC address is in the authentication database, but the host’s certificate for 802.1X authentication is expired.
Which of the following statements is true regarding the host in this scenario? (Select the best answer.)- MAB will authorize the host for network access, and the switch port will ignore the host’s 802.1X authentication attempts.
- MAB will authorize the host for network access? however, the host will lose network access when it attempts to authenticate with 802.1X.
- The host will fail 802.1X authentication and will be assigned to VLAN 1313.
- The host will fail 802.1X authentication, and the switch will place the port into an unauthorized state.
Explanation:
In this scenario, Media Access Control (MAC) Authentication Bypass (MAB) will authorize the host for network access? however, the host will lose network access when it attempts to authenticate with 802.1X. A switch port can be configured to use 802.1X, MAB, or Web Authentication (WebAuth) to authenticate clients. The authentication order command is used to specify the order in which the switch should attempt the configured authentication methods. By default, a switch will attempt 802.1X authentication before other authentication methods. The authentication order mab dot1x command configures the switch to first use MAB to authenticate a client based on its MAC address. If the client’s MAC address is not in the authentication database, the switch will then attempt to authenticate the client with 802.1X. In this scenario, the client’s MAC address is in the authentication database and MAB will authorize the client for network access.
Normally, the configured authentication order is mirrored by the priority of each authentication method? however, you can use the authentication priority command to change the priority. If the priority mirrored the authentication order in this scenario, the switch would ignore Extensible Authentication Protocol over LAN (EAPoL) messages after the client was authenticated by MAB and the client would continue to have authorized network access. However, the authentication priority dot1x mab command changes the default priority behavior and assigns a higher priority to 802.1X authentication than it does to MAB. This enables a client to use 802.1X authentication even if it has successfully been authenticated by MAB. Unfortunately, the client will lose network access when it attempts 802.1X authentication because its certificate is expired.The authentication event fail action command specifies how the switch should react if an 802.1X client is detected and the client fails to authenticate. There are two configurable parameters: nextmethod and authorize vlanid. The authorize vlanid parameter configures the port to a specific restricted virtual LAN (VLAN). The nextmethod parameter configures the switch to attempt authentication by using the next authentication method specified in the authentication order command. If the nextmethod parameter is configured, the switch will indefinitely cycle through authentication methods unless WebAuth is configured. If WebAuth is configured, the authentication process will not loop back to other authentication methods and the switch will ignore EAPoL messages on the port.
The authentication event noresponse action authorize vlan 1313 command specifies the VLAN into which a switch should place a port if it does not receive a response to the EAPoL messages it sends on that port. This enables devices that do no support 802.1X to be assigned to a guest VLAN. When a guest VLAN is configured, the switch will grant non802.1Xcapable clients access to the guest VLAN? however, if an 802.1Xcapable device is detected, the switch will place the port into an unauthorized state and will deny access to all devices on the port. -
Which of the following are symmetric encryption algorithms? (Select 3 choices.)
- AES
- RC4
- 3DES
- ECC
- DH
- DSA
Explanation:
Advanced Encryption Standard (AES), RC4, and Triple Data Encryption Standard (3DES) are symmetric encryption algorithms. When symmetric encryption algorithms are used, the same encryption key is used to encrypt and decrypt data. In addition, because symmetric encryption algorithms use less complex mathematics than asymmetric encryption algorithms when encrypting and decrypting data, they often perform faster than asymmetric encryption algorithms.
Two types of symmetric encryption algorithms exist: block ciphers and stream ciphers. Block ciphers derive their name from the fact that they encrypt fixedlength blocks of data. For example, AES encrypts 128bit blocks of data. By contrast, stream ciphers are typically faster than block ciphers because stream ciphers can encrypt text of variable length depending on the size of the frame to be encrypted? stream ciphers are not limited to specific block sizes. For example, RC4, a stream cipher, can encrypt data in streams of 8 through 2,048 bits. Other examples of symmetric encryption algorithms include International Data Encryption Algorithm (IDEA), Skipjack, and Blowfish.
DiffieHellman (DH), Digital Signature Algorithm (DSA), and Elliptical Curve Cryptography (ECC) are asymmetric algorithms. DH is an asymmetric key exchange method. DSA and ECC are asymmetric encryption algorithms. Asymmetric encryption, also known as public key encryption, uses a public key to encrypt data and a different, yet mathematically related, private key to decrypt data. Public key infrastructure (PKI) uses a certificate authority (CA) to tie a public key to a user ID to further ensure the confidentiality of data. Other examples of asymmetric encryption algorithms include RSA and ElGamal. -
Which of the following statements is correct regarding the traffic types that can be matched in a class map on a Cisco ASA? (Select the best answer.)
- A class map can match traffic by TCP port number but not by UDP port number.
- A class map can match traffic by UDP port number but not by IP precedence.
- A class map can match traffic by TCP port number but not by IP precedence.
- A class map can match traffic by UDP port number but not by TCP port number.
- A class map can match traffic by TCP port number, by UDP port number, and by IP precedence.
Explanation:
A class map can match traffic by Transmission Control Protocol (TCP) port number, by User Datagram Protocol (UDP) port number, and by IP precedence on a Cisco Adaptive Security Appliance (ASA). A class map is one of the three basic components of Modular Policy Framework (MPF)? policy maps and service policies are the other two components. MPF is a Cisco ASA feature that provides a flexible method of enabling security policies on an interface. A class map identifies a specific flow of traffic, a policy map determines the action that will be performed on the traffic, and a service policy ties this action to a specific interface. Generally, each class map can contain only a single match statement, and a packet can match only a single class map within the policy map of a particular feature type. For example, if a packet matched a class map for File Transfer Protocol (FTP) inspection and a class map for traffic policing, the ASA would apply both policy map actions to the packet. However, if a packet matched a class map for FTP inspection and a second, different class map that included FTP inspection, the ASA would apply only the actions of the first matching policy map.
You can use the match command from class map configuration mode to identify traffic based on specified characteristics. The keywords you can use to identify traffic in a class map are closely tied to their respective characteristics. The match command supports the following key words: accesslist, port, defaultinspectiontraffic, dscp, precedence, rtp, tunnelgroup, and any.
For example, you could issue the following commands to create a class map named CLASSMAP that identifies traffic using TCP port 25:asa(config)#classmap CLASSMAP asa(configcmap)#match port tcp eq 25
Once traffic has been identified by a class map, the associated policy map can take action on that traffic. A policy map typically contains references to one or more class maps and defines actions that should be performed on traffic matched by the specified class maps. If traffic matches multiple class maps for different actions within a policy map-for instance, if traffic matches a class map for application inspection as well as a class map for priority queuing-the actions of both class maps will be applied to the traffic. To continue the example from above, you could issue the following commands to configure a policy map named POLICYMAP that matches traffic specified by the class map named CLASSMAP and then processes the traffic with the Hypertext Transfer Protocol (HTTP) inspection engine:
asa(config)#policymap POLICYMAP asa(configpmap)#class CLASSMAP asa(configpmapc)#inspect http
A policy map does not act on traffic until the map has been applied to an interface by a service policy. A service policy can be applied globally to all interfaces, which will apply application inspection to only traffic entering the appliance? alternatively, a service policy can be applied to a single interface, which will apply application inspection to traffic entering and exiting the interface. An interface service policy overrides a global service policy: if traffic matches both an interface policy and a global policy, only the interface policy will be applied to that particular traffic flow. To complete the example, you could issue the following commands to apply the POLICYMAP policy map to the inside interface:
asa(config)#servicepolicy POLICYMAP interface inside
