300-735 : Automating Cisco Security Solutions (SAUTO) : Part 06
-
Which of the following EAP authentication protocols requires both a client and a server digital certificate? (Select the best answer.)
- LEAP
- PEAP
- EAP-FAST
- EAP-TLS
Explanation:
Extensible Authentication Protocol (EAP)Transport Layer Security (TLS) requires both a client and a server digital certificate. EAPTLS is an authentication protocol that can be used for pointtopoint connections and for both wired and wireless links. EAPTLS performs mutual authentication to secure the authentication process. When EAPTLS is used, a digital certificate must be installed on the authentication server and each client that must authenticate with the server. The digital certificate used on clients and the server must be obtained from the same certificate authority (CA).
Protected EAP (PEAP) does not require that clients be configured with digital certificates. When EAPPEAP is used, only servers are required to be configured with digital certificates. Clients can use alternative authentication methods, such as onetime passwords (OTPs).
Lightweight EAP (LEAP) does not require either the server or the client to be configured with a digital certificate. When LEAP is used, the client initiates an authentication attempt with a Remote Authentication DialIn User Service (RADIUS) server. The RADIUS server responds with a challenge response. If the challenge/response process is successful, the client then validates that the RADIUS server is correct for the network. If the RADIUS server is validated, the client will connect to the network.
Similar to LEAP, EAPFlexible Authentication via Secure Tunneling (FAST) does not require either the server or the client to be configured with a digital certificate. When EAPFAST is used, Protected Access Credentials (PACs) are used to authenticate users. The EAPFAST authentication process consists of three phases. The first phase, which is optional and is considered phase 0, consists of provisioning a client with a PAC, which is a digital credential that is used for authentication. A PAC can be manually configured on a client, in which case phase 0 is not required. The second phase, which is referred to as phase 1, involves creating a secure tunnel between the client and the server. The final phase, which is referred to as phase 2, involves authenticating the client. If the client is authenticated, the client will be able to access the network. -
The system software on a Cisco Catalyst 3750 series switch was corrupted during a failed upgrade, and now the switch no longer passes the POST on restart. You want to use the Xmodem Protocol to recover the system software.
To which of the following ports on the switch could you connect? (Select the best answer.)
- an Ethernet port in the management VLAN
- the auxiliary port
- the console port
- the highest numbered Ethernet port on the switch
- the lowest numbered Ethernet port on the switch
Explanation:
You should connect to the console port of a Cisco Catalyst 3750 series switch to use the Xmodem Protocol for system software recovery. Xmodem is a simple, errorcorrecting transfer protocol that can be used to transfer an IOS software image from a PC to Cisco switch or router through its console port. When the system software image on a switch or router becomes corrupted, the system will fail the poweron self-test (POST) when it reloads and it will typically halt in an administrative mode, which is commonly called readonly memory (ROM) monitor (ROMmon) mode. You can identify this mode on a switch or router by the command prompt that is displayed at the console: switch: on a switch and rommon1> on a router. When in ROMmon mode, a switch or router will no longer forward packets and thus can no longer be reached through traditional inband management methods, such as through a management virtual LAN (VLAN) or an active network interface. Instead, you must use an outofband management method to access a switch or router in ROMmon mode. The only outofband access method available on a Cisco 3750 series switch that supports Xmodem for system software recovery is the console port.
On a Cisco router, you could use either the console port or the auxiliary (AUX) port for outofband access if the router is in ROMmon mode. The AUX port on a Cisco router is typically capable of supporting most of the features available on a console port. Cisco switches either do not have AUX ports or do not support certain features, such as system recovery, on their AUX ports if they have them. -
Which of the following security functions is associated with the control plane? (Select the best answer.)
- device configuration protection
- device resource protection
- traffic accounting
- traffic filtering
Explanation:
Device resource protection is a security function that is associated with the control plane. Cisco devices are generally divided into three planes: the control plane, the management plane, and the data plane. Each plane is responsible for different operations, and each plane can be secured by implementing various security methods.
The control plane is responsible for the creation and maintenance of structures related to routing and forwarding. These functions are heavily dependent on the CPU and memory availability. Therefore, control plane security methods protect against unauthorized traffic destined for the router, which can modify route paths and consume excessive resources. Path modification can be caused by manipulating the traffic generated by routing protocols, VLAN Trunking Protocol (VTP), and Spanning Tree Protocol (STP). Path modification attacks can be mitigated by implementing routing protocol authentication and filtering, VTP authentication, and STP protection features. In addition, excessive CPU and memory consumption can be caused by control plane flooding. Resource consumption attacks can be mitigated by implementing control plane filtering and rate limiting with Control Plane Policing (CoPP) and Control Plane Protection (CPPr).
Traffic accounting and traffic filtering are security features that are associated with the data plane. The data plane is responsible for traffic passing through the router, which is referred to as transit traffic. Therefore, data plane security protects against unauthorized packet transmission and interception. Threats such as IP spoofing, Media Access Control (MAC) address spoofing, Address Resolution Protocol (ARP) spoofing, Dynamic Host Configuration Protocol (DHCP) spoofing, unauthorized traffic interception, and unauthorized network access can be mitigated and monitored by implementing features such as the following:
-ARP inspection
– Antispoofing access control lists (ACLs)
– DHCP snooping – Port ACLs (PACLs)
– Private virtual LANs (VLANs)
– Unicast Reverse Path Forwarding (uRPF)
– VLAN ACLs (VACLs)Device configuration protection is associated with the management plane. Management plane security protects against unauthorized device access and configuration. Unauthorized access can be mitigated by implementing a strong Authentication, Authorization, and Accounting (AAA) solution and by implementing Management Plane Protection (MPP), which creates protected management channels over which administrators must connect in order to access device administration features. Management traffic can be encrypted by implementing Secure Shell (SSH). You can mitigate unauthorized configuration of a device by implementing RoleBased Access Control (RBAC), whereby administrators are limited to using only the features they need to accomplish their jobs. Detection and logging of management plane access can be performed by implementing Simple Network Management Protocol version 3 (SNMPv3) and Syslog servers.
-
Which of the following statements are true regarding IDS devices? (Select 2 choices.)
- They can send alerts.
- They do not sit inline with the flow of network traffic.
- They can directly block a virus before it infiltrates the network.
- They can detect malicious traffic only by signature matching.
- They function identically to IPS devices.
Explanation:
Intrusion Detection System (IDS) devices can send alerts and do not sit inline with the flow of network traffic. An IDS is a network monitoring device that passively monitors network traffic and actively sends alerts to a management station when it detects malicious traffic. An IDS typically has one promiscuous network interface attached to each monitored network. Because traffic does not flow through the IDS, the IDS is unable to directly block malicious traffic? however, an IDS can do any of the following:
– Request that another device block a connection
– Request that another device block a particular host
– Reset TCP connectionsAn IDS can prevent further instances of previously detected malicious traffic from passing onto the network by creating access control lists (ACLs) on routers in the traffic path or by configuring other security devices that reside in the flow of traffic. Although signaturebased pattern matching is the primary method used by an IDS to detect malicious traffic, an IDS can also consider policy definitions and historical traffic behavior when analyzing network packets.
By contrast, an Intrusion Prevention System (IPS) typically sits inline with the flow of traffic and can therefore block malicious traffic before it passes onto the network. An inline IPS can perform the following actions:
– Block traffic from a particular host
– Block a particular connection
– Modify traffic
– Reset TCP connections
However, if an IPS sits inline with traffic, a failed IPS device can cause all traffic to be dropped. Analyzing all of the traffic that passes through the IPS can cause latency and jitter. Alternatively, an IPS can be configured to operate in promiscuous mode, which would make it functionally similar to an IDS. Typically, an IPS is configured to use signaturebased pattern matching to block traffic that has been definitively marked as malicious. Traffic that is suspect but has not been confirmed as malicious is referred to as gray area traffic and is not discarded by an IPS. If an IDS is used in conjunction with an IPS, the IDS can be configured to monitor the gray area traffic in greater detail without affecting the flow of traffic through the IPS. -
Which of the following statements are true regarding TACACS+? (Select 2 choices.)
- It encrypts the entire body of a packet.
- It combines authorization and authentication functions.
- It provides router command authorization capabilities.
- It uses UDP for packet delivery.
- It was developed as an IETF standard protocol.
Explanation:
Terminal Access Controller Access Control System Plus (TACACS+) encrypts the entire body of a packet and provides router command authorization capabilities. TACACS+ is a Ciscoproprietary protocol that uses Transmission Control Protocol (TCP) for transport during Authentication, Authorization, and Accounting (AAA) operations. TACACS+ provides more security and flexibility than other authentication protocols, such as Remote Authentication DialIn User Service (RADIUS), which is an open standard protocol commonly used as an alternative to TACACS+. Because TACACS+ can be used to encrypt the entire body of a packet, users who intercept the encrypted packet cannot view the user name or contents of the packet. In addition, TACACS+ provides flexibility by separating the authentication, authorization, and accounting functions of AAA. This enables granular control of access to resources. For example, TACACS+ gives administrators control over access to configuration commands? users can be permitted or denied access to specific configuration commands. Because of this flexibility, TACACS+ is used with Cisco Secure Access Control Server (ACS), which is a software tool that is used to manage user authorization for router access.
RADIUS, not TACACS+, was developed as an Internet Engineering Task Force (IETF) standard protocol.
Like TACACS+, RADIUS is a protocol used with AAA operations. However, RADIUS uses User Datagram Protocol (UDP) for packet delivery and is less secure and less flexible than TACACS+. RADIUS encrypts only the password of a packet? the rest of the packet would be viewable if the packet were intercepted by a malicious user. With RADIUS, the authentication and authorization functions of AAA are combined into a single function, which limits the flexibility that administrators have when configuring these functions.
Furthermore, RADIUS does not provide router command authorization capabilities. -
Which of the following protocols can IPSec use to provide the integrity component of the CIA triad? (Select 2 choices.)
- GRE
- AH
- AES
- ESP
- DES
Explanation:
IP Security (IPSec) can use either Authentication Header (AH) or Encapsulating Security Payload (ESP) to provide the integrity component of the confidentiality, integrity, and availability (CIA) triad. The integrity component of the CIA triad ensures that data is not modified in transit by unauthorized parties. AH and ESP are integral parts of the IPSec protocol suite and can be used to ensure the integrity of a packet. Data integrity is provided by using checksums on each end of the connection. If the data generates the same checksum value on each end of the connection, the data was not modified in transit. In addition, AH and ESP can authenticate the origin of transmitted data. Data authentication is provided through various methods, including user name/password combinations, preshared keys (PSKs), digital certificates, and onetime passwords (OTPs). Although AH and ESP perform similar functions, ESP provides additional security by encrypting the contents of the packet. AH does not encrypt the contents of the packet.
In addition to data authentication and data integrity, IPSec can provide confidentiality, which is another component of the CIA triad. IPSec uses encryption protocols, such as Advanced Encryption Standard (AES) or Data Encryption Standard (DES), to provide data confidentiality. Because the data is encrypted, an attacker cannot read the data if he or she intercepts the data before it reaches the destination. IPSec does not use either AES or DES for data authentication or data integrity.
Generic Routing Encapsulation (GRE) is a protocol designed to tunnel any Layer 3 protocol through an IP transport network. Because the focus of GRE is to transport many different protocols, it has very limited security features. By contrast, IPSec has strong data confidentiality and data integrity features, but it can transport only IP traffic. GRE over IPSec combines the best features of both protocols to securely transport any protocol over an IP network. However, GRE itself does not provide data integrity or data authentication. -
RouterA is configured to establish an IKE tunnel with RouterB. You issue the show crypto isakmp sa command on RouterA and receive the following output:
dst src state connid slot
10.1.2.3 10.1.2.4 MM_SA_SETUP 1 0
Which of the following statements is true? (Select the best answer.)
- RouterA has negotiated ISAKMP SA parameters with RouterB.
- RouterA has exchanged keys with RouterB.
- RouterA has generated a shared secret.
- RouterA uses three transactions to negotiate an ISAKMP SA.
- RouterA has established an active IKE SA.
Explanation:
RouterA has negotiated Internet Security Association and Key Management Protocol (ISAKMP) security association (SA) parameters with RouterB. The show crypto isakmp sa command displays the status of current Internet Key Exchange (IKE) SAs on the router. The MM_SA_SETUP state indicates that the IKE peers are using main mode for phase 1 negotiations and that they have successfully negotiated security parameters. IKE has two modes for phase 1 security negotiation: main mode and aggressive mode. The following states are used during main mode:
– MM_NO_STATE – The peers have created the SA.
– MM_SA_SETUP – The peers have negotiated SA parameters.
– MM_KEY_EXCH – The peers have exchanged DiffieHellman (DH) keys and have generated a shared secret.
– MM_KEY_AUTH – The peers have authenticated the SA.
The following states are used during aggressive mode:
– AG_NO_STATE – The peers have created the SA.
– AG_INIT_EXCH – The peers have negotiated SA parameters and exchanged keys.
– AG_AUTH – The peers have authenticated the SA.Quick mode is used during IKE phase 2. The only state in quick mode is QM_IDLE, which indicates that IKE phase 1 has completed successfully and that there is an active IKE SA between peers.
Because RouterA is using main mode, RouterA requires six transactions, not three, to negotiate an ISAKMP SA. Main mode requires six transactions for IKE peers to negotiate security parameters, generate a shared secret, and mutually authenticate. Aggressive mode requires only three transactions to negotiate security parameters, establish a key management tunnel, and mutually authenticate.
RouterA has not yet exchanged keys with RouterB or generated a shared secret. Key exchange and shared secret generation occurs during the MM_KEY_EXCH state. -
Which of the following worms was used in an act of cyber warfare against Iranian ICSs? (Select the best answer.)
- Blaster
- Nachi
- Stuxnet
- Welchia
Explanation:
The Stuxnet worm was used in an act of cyber warfare against Iranian industrial control systems (ICSs). Stuxnet is a Microsoft Windows worm that was discovered in the wild as early as 2008. It was written to target specific ICSs by modifying code on programmable logic controllers (PLCs). Stuxnet initially exploited vulnerabilities in the printer spooler service? however, later variants exploited a vulnerability in the way that Windows processes shortcuts. Research from Symantec published in 2011 indicated that at the time, more than 60% percent of the Stuxnetaffected hosts had been in Iran. Symantec analyzed Stuxnet and its variants and discovered that five organizations were the primary targets of infection and that further infections were likely collateral damage from the aggressive manner in which the worm spreads throughout the network. Given the considerable cost in resources and manhours that would have been required to craft the Stuxnet worm, it was theorized that it was likely intended to sabotage highvalue targets such as nuclear materials refinement facilities.
Blaster is a worm that targeted a vulnerability in the Distributed Component Object Model (DCOM) Remote Procedure Call (RPC) service on Microsoft Windows hosts. The worm carried a destructive payload that configured the target host to engage in Denial of Service (DoS) attacks on Microsoft update servers.
Like Blaster, Welchia is a worm that targeted a vulnerability in the DCOM RPC service. In fact, Welchia exploited the exact same vulnerability as the Blaster worm. Welchia was developed to scan the network for vulnerable machines, infect them, and then remove the Blaster worm if present. It was even designed to download and install the appropriate patch from Microsoft to fix the vulnerability that it and Blaster initially exploited to infect the target machine. However, despite the goodnatured design intentions of the Welchia worm, its networkscanning component inadvertently caused DoS attacks on several large networks, including those of the United States armed forces. Welchia was also referred to by the name Nachi. -
Which of the following statements is true regarding the Cisco IOS Resilient Configuration feature? (Select the best answer.)
- Extra space is not required to secure the primary IOS image file.
- Image or configuration mismatches are not automatically detected.
- Only remote storage can be used for securing configuration files.
- The feature can be disabled remotely.
Explanation:
Extra space is not required to secure the primary IOS image file with the Cisco IOS Resilient Configuration feature. The Resilient Configuration feature is designed to protect system and configuration files from tampering and accidental deletion. You can issue the following block of commands to enable the Resilient Configuration feature:Router#configure terminal Router(config)#secure boot-image Router(config)#secure boot-config
When the feature is enabled, the primary system image file and associated running configuration are securely archived in local persistent storage? you cannot select a remote storage location. The secure bootimage command enables the image resilience component of the Resilient Configuration feature and effectively hides the system image from the directory structure. This means that the system image will no longer be displayed when the dir command is issued from the command prompt of an EXEC shell? you can issue the show secure bootset command to verify that the system image has been archived. In addition, because the system image file is not copied to a secure location, extra storage is not required to secure it. By contrast, the secure bootconfig command creates a hidden copy of the running configuration file. The secured versions of the system image and running configuration are referred to as the primary bootset.
You can restore either or both components of the primary bootset at any time. The system image can be restored from readonly memory (ROM) monitor (ROMmon) mode and the running configuration can be restored from the global configuration mode by using the restore parameter of the secure bootconfig command. Once the system image and running configuration have been secured, the router will track version mismatches and produce a console message if the system image or running configuration have mismatched versions. Once the Resilient Configuration feature is enabled, it can only be disabled from the console. -
Which of the following can be installed on a host to analyze and prevent malicious traffic on that host? (Select the best answer.)
- antivirus software
- a HIPS
- a personal firewall
- a proxy server
Explanation:
A Hostbased Intrusion Prevention System (HIPS) can be installed on a host to analyze and prevent malicious traffic on that host. An Intrusion Prevention System (IPS) can be used to actively monitor, analyze, and block malicious traffic before it infects devices. HIPS software can be installed on a host computer to protect that computer against malicious traffic. By contrast, a Networkbased IPS (NIPS) is an independent operating platform, often a standalone appliance or a hardware module installed in a chassis. A NIPS device can be installed inline on a network to monitor and prevent malicious traffic from being sent to other devices on the network. One advantage of using a NIPS over a HIPS is that a NIPS can detect lowlevel network events, such as the scanning of random hosts on the network? a HIPS can only detect scans for which it is the target. A HIPS and a NIPS can be used together to provide an additional layer of protection.
Although you could install a personal firewall to protect a host from malicious traffic, a personal firewall does not perform traffic analysis. However, a personal firewall can work in conjunction with other software, such as a HIPS or a NIPS, to protect a host from a wider array of malicious activities. For example, Cisco Advanced Malware Protection (AMP) for Endpoints can work in conjunction with a personal firewall to provide threat protection and advanced analytics.
You could not install antivirus software to analyze and prevent malicious traffic on that host. Antivirus software monitors the file system and memory space on a host for malicious code. Although the antivirus software might protect the host from malicious file execution, it would be unable to protect the host from malicious traffic. Some antivirus vendors offer integrated security suites, which feature personal firewall, HIPS, antivirus, and antimalware components.
You could not install a proxy server on a host to analyze and prevent malicious traffic on that host. A proxy server is typically an application layer gateway that provides resource caching and traffic filtering for a particular class of traffic, such as web content. Although you could install a proxy server locally on a host, it would not have a significant effect on malicious traffic directed at the host nor would it be able to analyze its content. -
Which of the following traffic types can be detected by the FirePOWER ratebased prevention preprocessor engine? (Select the best answer.)
- Back Orifice traffic
- distributed port scan traffic
- port sweep traffic
- SYN flood traffic
Explanation:
The FirePOWER ratebased prevention preprocessor engine can detect SYN flood traffic. A FirePOWER Intrusion Prevention System (IPS) has several predefined preprocessor engines that can be used in network policies to detect specific threats? the preprocessors focus on detecting Back Orifice attacks, detecting port scan attacks, preventing ratebased attacks, and detecting sensitive data. The ratebased prevention preprocessor detects traffic abnormalities based on the frequency of certain types of traffic. The following traffic patterns can trigger ratebased attack prevention:-Traffic containing excessive incomplete Transmission Control Protocol (TCP) connections
-Traffic containing excessive complete TCP connections
-Excessive rule matches for a particular IP address or range of IP addresses
-Excessive rule matches for one particular rule regardless of IP addressDistributed port scan traffic and port sweep traffic can be detected by the portscan detection preprocessor. Port scanning traffic can be an indicator that an attacker is conducting network reconnaissance prior to an attack. Although legitimate port scanning traffic can periodically exist on a network, the portscan detection preprocessor can distinguish between legitimate scanning and potentially malicious traffic based on the activity patterns found in the analysis of port scanning traffic.
The FirePOWER IPS has a preprocessor dedicated to Back Orifice traffic. Back Orifice and its variants exploit a vulnerability in Microsoft Windows hosts to gain complete administrative control of the host. Back Orifice traffic can be identified by the presence of a specific token, known as a magic cookie, in the first eight bytes of a User Datagram Protocol (UDP) packet. -
Which of the following commands should you issue to allow a packet to exit an ASA through the same interface through which it entered the ASA? (Select the best answer.)
- samesecuritytraffic permit interinterface
- samesecuritytraffic permit intrainterface
- securitylevel 0
- securitylevel 100
- established
Explanation:
To allow a packet to exit a Cisco Adaptive Security Appliance (ASA) through the same interface through which it entered, which is also known as hairpinning, you should issue the samesecuritytraffic permit intrainterface command. By default, an ASA does not allow packets to enter and exit through the same physical interface. However, because multiple logical virtual LANs (VLANs) can be assigned to the same physical interface, it is sometimes necessary to allow a packet to enter and exit through the same interface. The samesecuritytraffic permit intrainterface command allows packets to be sent and received from the same interface even if the traffic is protected by IP Security (IPSec) security policies. Another scenario for which you would need to use the samesecuritytraffic permit intrainterface command is if multiple users need to connect via virtual private network (VPN) through the same physical interface. These users will not be able communicate with one another unless the samesecuritytraffic permit intrainterface command has been issued from global configuration mode.
You should not issue the samesecuritytraffic permit interinterface command to allow a packet to exit through the same interface through which it entered. The samesecuritytraffic permit interinterface command is used to allow communication between different interfaces that share the same security level. Typically, interfaces with the same security level are not allowed to communicate with each other.
You should not issue either the securitylevel 0 command or the securitylevel 100command to allow a packet to exit through the same interface through which it entered. The securitylevel command is used to set the security level on a physical interface. Security level 0 should be used to achieve the lowest security level possible, whereas security level 100 should be used to achieve the highest security level available.
You should not issue the established command to allow a packet to exit through the same interface through which it entered. The established command is used to allow inbound traffic on any interface that has already established an outbound connection with the ASA. For example, you could issue the established tcp 4567 0 command to configure the ASA to allow an external host to initiate a connection through the ASA to an internal host after the internal host has first established a Transmission Control Protocol (TCP) connection to port 4567 on the external host. The established command is often used to support protocols such as streaming media protocols that negotiate the ports for return traffic. -
Which of the following devices requires that a physical interface be in promiscuous mode in order to monitor network traffic? (Select the best answer.)
- an IPS
- a firewall
- a router
- an IDS
- an ASA
Explanation:
An Intrusion Detection System (IDS) requires that a physical interface be in promiscuous mode in order to monitor network traffic. An IDS is a network monitoring device that does not sit inline with the flow of network traffic? an IDS passively monitors a copy of network traffic, not the actual packet. Typically, an IDS has one promiscuous network interface attached to each monitored network. A promiscuous device listens to all data flowing past it regardless of the destination. Because traffic does not flow through the IDS, the IDS cannot mitigate singlepacket attacks and is unable to directly block malicious traffic, like a virus, before it passes onto the network. However, an IDS can actively send alerts to a management station when it detects malicious traffic.
An Intrusion Prevention System (IPS) sits inline with the flow of traffic, thus actively monitoring network traffic and blocking malicious traffic, such as an atomic or singlepacket attack, before it passes onto the network. Blocking an attack inline can prevent the attack from spreading further into the network. An IPS requires at least two interfaces for each monitored network: one interface listens to traffic entering the IPS, and the other listens to traffic leaving the IPS. In addition, an IPS acts similarly to a Layer 2 bridge in that it passes traffic through to destinations on the same subnet? an IPS cannot route to destinations on a different subnet. An interface of an IPS can be put in promiscuous mode? when this happens, the device operates as an IDS on that interface. However, an IPS does not require that a physical interface be in promiscuous mode in order to monitor network traffic.
A firewall is a network security device that protects a trusted network from an untrusted network, such as the Internet. Firewalls can operate in either routed mode or transparent mode. In routed mode, the firewall acts as a Layer 3 device that can perform Network Address Translation (NAT) and route traffic between virtual LANs (VLANs) on different subnets. In transparent mode, the firewall acts as a Layer 2 bridge in that it can pass traffic through to destinations on the same subnet but cannot route to destinations on a different subnet. Although a firewall is a security appliance that permits or denies traffic on a network, a firewall does not require that a physical interface be in promiscuous mode in order to monitor network traffic.
A router is a device that connects multiple subnets of the same or different networks and passes information between them. The functionality of a router can vary depending on the size of the network on which it is deployed. For example, a Cisco IPS Advanced Integration Module (AIM) can be installed in a router to integrate IPS functionality at the hardware level. Alternatively, an IOS feature set with IPS capabilities can be installed to provide IPS functionality at the software level. A router operating as an IPS or IDS can serve as a part of the network security structure as well as a bridge between two segments of the network. Although a router can function as an IPS or IDS, a router does not require that a physical interface be in promiscuous mode in order to monitor network traffic.
The Cisco Adaptive Security Appliance (ASA) is a multifunction appliance that can provide firewall, virtual private network (VPN), intrusion prevention, and content security services. The Cisco ASA is based on the framework of the Private Internet Exchange (PIX) firewall appliance. If used as an IPS device in IDS mode, or promiscuous mode, the Cisco ASA can have a physical interface in promiscuous mode? however, Cisco ASA does not require that a physical interface be in promiscuous mode in order to monitor network traffic. -
Which of the following is typically implemented in a cluster configuration? (Select the best answer.)
- ACS
- CSA
- CTA
- SSC
Explanation:
Cisco Secure Access Control System (ACS) is typically implemented in a cluster configuration. ACS is an
Authentication, Authorization, and Accounting (AAA) server that uses Remote Authentication DialIn User Service (RADIUS) and Terminal Access Controller Access Control System Plus (TACACS+) to provide AAA services for users, hosts, and network infrastructure devices such as switches and routers. An ACS deployment typically consists of a primary server responsible for configuration, authentication, and policy enforcement and one or more secondary servers serving as a backup in case the primary server fails. In largescale deployments, the primary server’s function is typically relegated to configuration and synchronization services, whereas the secondary servers provide AAA services to the network clients.
Cisco Trust Agent (CTA) is responsible for ascertaining the status of security applications and management tools that are installed on a client. As client software, CTA communicates host posture information back to a network access device on a Cisco Network Admission Control (NAC) framework. NAC is a Cisco feature that prevents hosts from accessing the network if they do not comply with organizational requirements, such as containing an updated antivirus definition file. When NAC is configured on an access device, such as a router or switch, the NAC device intercepts connections from hosts that are not yet registered on the network. When a host attempts to connect to the network, the access device queries the CTA running on the host for the host’s security status. The access device then sends this information to the ACS, which determines whether the host is in compliance with organizational security policies. If the host is in compliance, it is allowed to access the network? if the host is not in compliance, it can be denied access, quarantined, or allowed limited network access.
Cisco Secure Services Client (SSC) is client security software that facilitates the use of one authentication framework for connecting to both wired and wireless devices on a Cisco Unified Wireless Network. SSC makes use of the Extensible Authentication Protocol (EAP), WiFi Protected Access (WPA), and WPA2 standards to control network access and enforce security policies for clients using Microsoft Windows platforms. Cisco SSC is not typically implemented in a cluster configuration.
Cisco Security Agent (CSA) is a Hostbased Intrusion Prevention System (HIPS) that can be installed on host computers, servers, and pointofsale (POS) computers. CSA can help protect these devices from malicious network traffic, such as zeroday attacks. In addition, CSA can provide local firewall services, antivirus services, and security policy enforcement. CSA is not typically implemented in a cluster configuration. -
Which of the following traffic types are blocked by default in a zone-based policy firewall configuration? (Select 2 choices.)
- traffic to or from the self zone
- traffic between interfaces in the same zone
- traffic between interfaces in a zone and interfaces not assigned to any zone
- traffic between interfaces in different zones
- traffic directly to or received from the router
Explanation:
In a zonebased policy firewall (ZFW) configuration, all traffic between interfaces in different zones is blocked by default. In addition, all traffic between interfaces that have been assigned to a zone and interfaces that are not assigned to any zone is blocked by default. ZFW is the latest iteration of Cisco’s stateful firewall implementation, which was formerly called ContextBased Access Control (CBAC). With ZFW, virtual security zones are specified and then interfaces are assigned to the appropriate zone. By default, all traffic is implicitly permitted to flow between interfaces that have been assigned to the same zone? however, all traffic between zones is blocked. In addition, all traffic to and from an interface is implicitly blocked by default when the interface is assigned to a zone, but there are a few exceptions. Traffic to or from other interfaces in the same zone is permitted, as is traffic to or from the router itself. When ZFW is configured, a special zone called the self zone is automatically created and contains the IP addresses of all the router interfaces. By default, all traffic to or from the self zone is implicitly permitted? this implicit permission ensures that management access to the router is not lost when ZFW is configured.
In order for traffic to flow between userconfigured zones, stateful packet inspection policies must be configured to explicitly permit traffic between the zones. The basic process is as follows:
1. Define the required zones.
2. Create zonepairs for zones that will pass traffic between themselves.
3. Define class maps to match the appropriate traffic for each zonepair.
4. Define policy maps to specify the actions that should be performed on matching traffic.
5. Apply the policy maps to the zonepairs.
6. Assign interfaces to their appropriate zones.
Although inspection rules can be created for a large number of traffic types, stateful inspection of multicast traffic is not supported by ZFW and must be handled by other security features, such as Control Plane Policing (CoPP). -
An inside host has initiated a TCP connection through a Cisco ASA to an outside server. The outside server has responded with a SYN/ACK segment? however, the inside host has not yet responded with an ACK segment.
Which of the following lines of output from the show conn command best represents the state of the connection in this scenario? (Select the best answer.)
- TCP outside 192.0.2.51:22 inside 10.1.1.18:12113 idle 0:00:00, bytes 0, flags SaAB
- TCP outside 192.0.2.51:22 inside 10.1.1.18:12113 idle 0:00:00, bytes 0, flags saA
- TCP outside 192.0.2.51:22 inside 10.1.1.18:12113 idle 0:00:00, bytes 0, flags aB
- TCP outside 192.0.2.51:22 inside 10.1.1.18:12113 idle 0:00:00, bytes 0, flags A
- TCP outside 192.0.2.51:22 inside 10.1.1.18:12113 idle 0:00:00, bytes 0, flags U
- TCP outside 192.0.2.51:22 inside 10.1.1.18:12113 idle 0:00:00, bytes 0, flags UIO
Explanation:
The following line of output from the show conn command on a Cisco Adaptive Security Appliance (ASA) best represents the state of a connection that is waiting on only the ACK segment from an inside host:
TCP outside 192.0.2.51:22 inside 10.1.1.18:12113 idle 0:00:00, bytes 0, flags AThe output of the show conn command uses connection flags to indicate the status of each entry in the ASA connection database. The connection database is used by the stateful firewall feature of the ASA to track the state of each network connection that passes through it. The flags that an ASA uses to track a connection entry are dependent on the interface that initiated the connection. Typically, each connection entry has corresponding inside and outside interfaces. In terms of the connection database, the inside interface for the entry is the interface with the higher security level, whereas the outside interface for the entry is the interface with the lower security level. In addition, a data flow from the inside interface to the outside interface is considered to be moving in the outbound direction and a data flow from the outside interface to the inside interface is considered to be moving in the inbound direction.
When an ASA receives the first packet from a Transmission Control Protocol (TCP) connection, it creates an entry in the connection database. The ASA immediately adds the B flag to the entry if the connection was initiated from the outside. The ASA then uses various flags to indicate the progress of the TCP threeway handshake. For example, if a connection is initiated from the inside, the ASA will add the saA flags to the entry, as shown in the following command output:TCP outside 192.0.2.51:22 inside 10.1.1.18:12113 idle 0:00:00, bytes 0, flags saA
The s flag indicates that the ASA is awaiting a SYN segment from the outside host, and the a flag indicates that the ASA is waiting for an ACK response segment to the SYN that was initiated from the inside host. When the corresponding SYN/ACK segment is received from the outside host, it will satisfy both of these flags and the ASA will clear the flags from the entry, as shown in the following command output:
TCP outside 192.0.2.51:22 inside 10.1.1.18:12113 idle 0:00:00, bytes 0, flags AThe remaining A flag indicates that the ASA is awaiting an ACK segment from the inside host. When the host on the inside responds to the SYN/ACK segment with the corresponding ACK segment, the ASA will clear the A flag and will mark the connection with the U flag, as shown in the following command output:
TCP outside 192.0.2.51:22 inside 10.1.1.18:12113 idle 0:00:00, bytes 0, flags UThe U flag indicates that the threeway handshake is complete and that the TCP session is established. Once the TCP session is established, the host can begin to exchange data. In this example, the inside host has established a Secure Shell (SSH) session to an outside server. When the outside server sends data to the inside host, the ASA will add the I flag to the entry to indicate that data has passed through the session in the inbound direction. Likewise, the ASA will add the O flag to the entry to indicate that data has passed through the session in the outbound direction. Thus a normal TCP session should have flags similar to those shown in the following command output:
TCP outside 192.0.2.51:22 inside 10.1.1.18:12113 idle 0:00:00, bytes 0, flags UIOBy contrast, if the connection were initiated from the outside, the ASA would have added the SaAB flags to the entry, as shown in the following command output:
TCP outside 192.0.2.51:22 inside 10.1.1.18:12113 idle 0:00:00, bytes 0, flags SaABThe S flag indicates that the ASA is awaiting a SYN segment from the inside host, and the A flag indicates that the ASA is waiting for an ACK response segment to the SYN that was initiated from the outside host. When the corresponding SYN/ACK segment is received from the inside host, it will satisfy both of these flags and the ASA will clear the flags from the entry, as shown in the following command output:
TCP outside 192.0.2.51:22 inside 10.1.1.18:12113 idle 0:00:00, bytes 0, flags aBThe remaining a flag indicates that the ASA is awaiting an ACK segment from the outside host. When the host on the outside responds to the SYN/ACK segment with the
-
Which of the following is an IOS privilege level that provides the highest level of access on a Cisco router? (Select the best answer.)
- 0
- 1
- 15
- 16
Explanation:
The highest level of access on a Cisco router is provided by IOS privilege level 15. Privilege levels can be used to limit the IOS commands that a user can access. However, you are limited to 16 privilege levels, some of which are used by default by the IOS. For example, privilege levels 1 and 15 are default IOS privilege levels. Privilege level 1 allows a user to issue any command that is available at the user EXEC > prompt. Privilege level 15 allows a user to issue any command that is available at the privileged EXEC # prompt.
Each privilege level is associated with a list of commands that are available at that level. Users assigned to a privilege level have access to all of the commands at that privilege level and all lower privilege levels. Changing the commands that are available to a privilege level might provide access to a user who should not be allowed access to the command, or it might restrict access to another user who should be allowed access to the command.
Because the default privilege level for a newly created local user account is 1, a newly created user will always have access to the disable, enable, exit, help, and logout commands? these commands are associated with privilege level 0. However, per user privilege levels can sometimes conflict with the privilege levels set for virtual terminal (VTY) interfaces. In the event of a conflict, per user privileges override the privileges configured for the VTY line causing the conflict.
Although there are 16 distinct privilege levels that can be assigned on a Cisco router, 16 is not a valid value for a privilege level. Valid values for user assigned privilege levels are whole numbers ranging from 0 through 15. -
Which of the following statements is true regarding LDAP attribute maps on an ASA? (Select the best answer.)
- There is a defined limit on the number of LDAP attribute maps you can configure.
- There is a defined limit on the number of attributes that can be mapped in each LDAP attribute map.
- There is a defined limit on the number of LDAP servers to which an LDAP attribute map can be applied.
- There is a defined limit on the number of AD multivalued attributes matched by an LDAP attribute map.
Explanation:
When using Lightweight Directory Access Protocol (LDAP) attribute maps on a Cisco Adaptive Security Appliance (ASA), there is a limit on the number of Active Directory (AD) multivalued attributes matched by an LDAP attribute map. LDAP attribute maps are used to authorize virtual private network (VPN) users based on specified AD attributes, such as group membership or department name. If an LDAP query returns a multivalued attribute, such as the list of groups of which a user is a member, the ASA will match only one of the returned values to the appropriate group policy. The ASA will select the matching group policy with the least number of characters in the name and that starts with the lowest alphanumeric character.
There is no defined limit on the number of LDAP attribute maps you can configure on an ASA. Because LDAP attribute maps are dynamically allocated as they are needed, configuring a large number of attribute maps does not unnecessarily burden the ASA during normal operations. Likewise, there is no defined limit on the number of attributes that can be mapped in each LDAP attribute map.
There is no defined limit on the number of LDAP servers to which an LDAP attribute map can be applied. When an LDAP attribute map is applied to a server, the ASA only verifies that the specified attribute map exists. The same LDAP attribute map can be applied to multiple, different servers. -
Which of the following can be determined from the Route Details tab of the VPN Client Statistics dialog box shown above? (Select the best answer.)
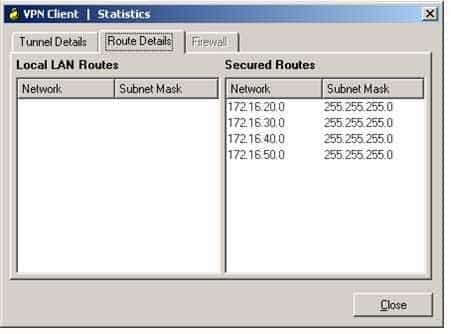
300-735 Part 06 Q19 052 - The VPN client cannot access devices on the local LAN.
- The VPN client is configured to use split tunneling.
- The VPN client is configured to use transparent tunneling.
- The VPN client cannot access devices on the 172.16.20.0/24 network.
Explanation:
The Route Details tab of the VPN Client Statistics dialog box displayed below indicates that the virtual private network (VPN) client is configured to use split tunneling:
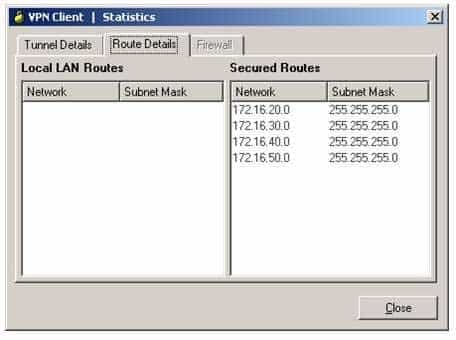
300-735 Part 06 Q19 053 By default, all traffic from a VPN client is passed through an encrypted tunnel to the VPN server. However, with split tunneling, only traffic destined for a protected subnet is passed through the encrypted tunnel? all other traffic is processed normally. You can define protected subnets on the VPN server by entering the network address of each protected subnet on the Split Tunneling tab of the Group Policy window or by specifying an access control list (ACL) that includes each protected subnet. When a client establishes a VPN session, the list of protected subnets is passed from the VPN server to the VPN client as part of the session configuration parameters.
Alternatively, the VPN client can be configured to pass all nonlocal traffic through an encrypted tunnel to the VPN server. If the group policy on the VPN server permits local LAN access and the VPN client is configured to allow local LAN access, all traffic that is not destined to the local LAN is sent through the encrypted tunnel. For example, if the VPN client had a locally configured route to the 192.168.13.0/24 network, packets destined for that network would be processed normally. However, any packets destined for a network not in the VPN client’s routing table, such as the Internet, would pass through the encrypted tunnel to the VPN server. This configuration is represented on the Route Details tab of the VPN Client Statistics dialog box shown below:
300-735 Part 06 Q19 054 The VPN Client Statistics dialog box does not indicate that the client cannot access devices on the 172.16.20.0/24 network. Because the 172.16.20.0/24 network is listed in the Secured Routes pane, traffic destined for the 172.16.20.0/24 network will pass through the encrypted tunnel to the VPN server. However, traffic destined for a network not in the Secured Routes pane, such as the Internet or the local LAN, will not pass through the tunnel and will be processed normally.
Likewise, the VPN Client Statistics dialog box does not indicate that the client cannot access devices on the local LAN. Because the router is configured for split tunneling, only traffic destined for a network in the Secured Routes pane is passed through an encrypted tunnel to the VPN server. All other traffic, including local LAN traffic, is processed normally.
You cannot determine from the Route Details tab of the VPN Client Statistics dialog box whether the client is configured to use transparent tunneling. The Tunnel Details tab of the VPN Client Statistics dialog box indicates whether the client is configured to use transparent tunneling. Transparent tunneling facilitates the creation of IP Security (IPSec) tunnels through a firewall or Network Address Translation (NAT) device. When transparent tunneling is enabled on the client, encrypted packets are encapsulated in Transmission Control Protocol (TCP) or User Datagram Protocol (UDP) packets prior to transmission through the firewall or NAT device. -
Which of the following IPS detection methods is a string pattern-based detection method? (Select the best answer.)
- anomalybased detection
- profilebased detection
- signaturebased detection
- policybased detection
Explanation:
Signaturebased detection is a string patternbased detection method. Patternbased detection methods use specific strings of text to detect malicious traffic. Many signaturebased detection methods can also use protocols and port numbers to further specify malicious traffic patterns. The benefit of signaturebased detection methods is that the number of false positives generated is typically low. However, the drawback is that a modified attack cannot be detected by an old signature? the modified attack will not be detected until a new signature is added for the modified attack. Therefore, Cisco recommends updating signature files, including antivirus signatures, every time a new update is available.
Anomalybased detection methods and profilebased detection methods detect abnormal behavior on a network. Traffic is classified as normal or abnormal based on information that is dynamically learned or manually programmed. The benefit of anomalybased detection is that anything that is not specified as normal is classified as abnormal? therefore, anomalybased detection can typically detect a wide range of threats. One drawback of anomalybased detection is that new traffic patterns are required on a regular basis on all but the smallest of networks, which leads to a lot of false positives. Another drawback is the memory and processing power required to handle profiles for each user.
Policybased detection methods use algorithms to detect patterns in network traffic. The benefit of policybased detection methods is that they can often detect when a coordinated attack, such as a Distributed Denial of Service (DDoS) attack, is happening, whereas a signaturebased detection method might detect only a collection of individual Denial of Service (DoS) attacks.