300-735 : Automating Cisco Security Solutions (SAUTO) : Part 07
-
You have been asked to add a key to an existing keychain. You issue the following commands to enter key chain key configuration mode:
RouterA(config)#key chain chain1
RouterA(configkeychain)#key 2
RouterA(configkeychainkey)#keystring key2
The new key should be valid for three hours, and the router should begin sending the key at 9 a.m. on January 13, 2015.
Which of the following commands should you issue next to achieve your goal? (Select the best answer.)- accep-tlifetime 09:00:00 Jan 13 2015 duration 3
- accep-tlifetime 09:00:00 Jan 13 2015 duration 180
- send-lifetime 09:00:00 Jan 13 2015 duration 180
- send-lifetime 09:00:00 Jan 13 2015 duration 10800
Explanation:
You should issue the send-lifetime 09:00:00 Jan 13 2015 duration 10800 command to specify that the key in this scenario should be valid for three hours and that the router should begin sending the key at 9 a.m. on January 13, 2015. The send-lifetime command is used to specify the period of time during which a key should be sent by a router for authentication. The syntax for this command is send-lifetime starttime {infinite | endtime | duration seconds}, where starttime specifies the date and time that the key should start being sent. By default, keys are valid indefinitely? however, you can use the durationkeyword to specify a duration value between 1 and 2,147,483,646 seconds. In this scenario, the duration is 10800 seconds, which is three hours, and the start time is 09:00:00 Jan 13 2015, which corresponds to 9 a.m. on January 13, 2015.
You should not issue the sendlifetime 09:00:00 Jan 13 2015 duration 180command, because the key duration is incorrectly specified as 180 seconds, which is three minutes, instead of 10,800 seconds, or three hours.
You should not issue the accept-lifetime 09:00:00 Jan 13 2015 duration 3 command or the accept-lifetime 09:00:00 Jan 13 2015 duration 180 command. The accept-lifetime command specifies the time period during which a received key is considered valid. By default, received keys are valid indefinitely. If no send-lifetime command has been issued, the accept-lifetime command will limit the period of time in which the received key is valid, but it will have no effect on the period of time during which the router sends the key for authentication. -
Which of the following can be mitigated by installing a personal firewall on a laptop? (Select the best answer.)
- a SYN flood attack
- a crosssite scripting attack
- a portscanning attack
- a sessionhijacking attack
Explanation:
Installing a personal firewall on a laptop can mitigate a portscanning attack. In a portscanning attack, an attacker uses a portscanning application to probe a computer to determine which ports are open and vulnerable to an attack. After determining which ports are open, the attacker can attempt to access the computer through an open port. With a personal firewall, you can protect a host from malicious traffic by permitting or denying specific applications or network ports access to the host or its network interface. Typically, a personal firewall provides sufficient granularity to specify the direction of a particular flow of traffic. For example, you could permit outbound web traffic but deny all inbound traffic that does not correspond to established outbound connections.
Installing a personal firewall on a laptop would not mitigate a sessionhijacking attack. A sessionhijacking attack requires that the attacker determine the Initial Sequence Number (ISN) for a new Transmission Control Protocol (TCP) session. The ISN is used during the TCP threeway handshake to synchronize the states of the sending and receiving hosts. If an attacker can guess the ISN or any subsequent sequence number for a connection, the attacker can hijack the session. Typically, an attacker will disrupt the connection by forcing one of the hosts to become unsynchronized and will then assume the identity of the unsynchronized host by spoofing its IP address. Session hijacking relies on the attacker being able to determine the correct sequence number for any given segment in a TCP session. Because some hosts use incremental ISNs and random sequence numbers, an attacker can determine the ISN for a new connection on a vulnerable host by first initiating a connection to the host and determining the current ISN.
Installing a personal firewall on a laptop would not mitigate a crosssite scripting (XSS) attack. An XSS attack takes advantage of weaknesses within a web application to insert malicious code into input fields on a web form. If the attack is successful, the attacker might be able to inject code into the webpage, which could allow the attacker to perform a variety of malicious tasks, such as redirecting visitors to another website or harvesting cookies from the victim’s computer. Serverside input validation can be used to mitigate XSS attacks performed on web forms. However, other types of XSS attacks, such as a link in an email to lure victims to a webpage containing malicious script, are not mitigated by input validation.
Installing a personal firewall on a laptop would not mitigate a SYN flood attack. A SYN flood attack sends a large volume of SYN segments to a target host in an attempt to saturate the target’s TCP connection table. The SYN flood attack exploits the TCP threeway handshake by sending TCP SYN segments from spoofed IP addresses. When the target host replies to the spoofed IP addresses, the target’s packets are ignored because the spoofed hosts do not have corresponding entries in their TCP connection tables. The target host will continue to wait for responses from the spoofed hosts until the TCP handshake times out. With a sufficient number of SYN requests, the target’s TCP connection table can become full. Once the TCP connection table is full, the target host will be unable to accept new TCP connections. -
When a switch is configured with private VLANs, which of the following ports can an isolated port communicate with? (Select the best answer.)
- ports within the same community
- ports within a different community
- other isolated ports
- promiscuous ports
Explanation:
An isolated port can communicate with promiscuous ports when a switch is configured with private virtual
LANs (VLANs). Private VLANs can be configured on a switch to help isolate traffic within a VLAN. Private VLANs can provide Layer 2 separation between ports that belong to the same VLAN. Because the separation exists at Layer 2, the hosts can exist on the same IP subnet. The VLAN to which the hosts belong is called the primary VLAN. To create a private VLAN, you must create secondary VLANs and associate them with the primary VLAN. There are two types of secondary VLANs: community VLANs and isolated VLANs. Ports that belong to a community VLAN can communicate with promiscuous ports and with other ports that belong to the same community. However, they cannot communicate with isolated ports or with ports that belong to other communities. Ports that belong to an isolated VLAN can communicate only with promiscuous ports.
After configuring the private VLAN, you can configure ports to participate in the private VLAN. When configuring a port to participate in a private VLAN, you must configure the port by issuing the switchport mode privatevlan {promiscuous | host} command. The promiscuous keyword configures the port to communicate with any secondary VLAN. Consequently, devices that should be reachable from any secondary VLAN should be connected to promiscuous ports. For example, a router, a firewall, or a gateway that any host should be able to reach should be connected to a promiscuous port. By contrast, devices connected to isolated or community VLANs should be connected to host ports, which are configured by using the host keyword. -
Which of the following statements is not true regarding the IaaS service model? (Select the best answer.)
- The consumer has control over the configuration of the OS running on the physical infrastructure in the cloud.
- The consumer has control over the physical infrastructure in the cloud.
- The consumer has control over the allocation of processing, memory, storage, and network resources within the cloud.
- The consumer has control over development tools or APIs in the cloud running on the physical infrastructure in the cloud.
Explanation:
In the Infrastructure as a Service (IaaS) service model, the consumer does not have control over the physical infrastructure in the cloud. The National Institute of Standards and Technology (NIST) defines three service models in its definition of cloud computing: Software as a Service (SaaS), IaaS, and Platform as a Service (PaaS).
The SaaS service model enables its consumer to access applications running in the cloud infrastructure but does not enable the consumer to manage the cloud infrastructure or the configuration of the provided applications. A company that licenses a service provider’s office suite and email service that is delivered to end users through a web browser is using SaaS. SaaS providers use an Internet enabled licensing function, a streaming service, or a web application to provide end users with software that they might otherwise install and activate locally. Webbased email clients, such as Gmail and Outlook.com, are examples of SaaS.
The PaaS service model provides its consumer with a bit more freedom than the SaaS model by enabling the consumer to install and possibly configure provider supported applications in the cloud infrastructure. A company that uses a service provider’s infrastructure, programming tools, and programming languages to develop and serve cloudbased applications is using PaaS. PaaS enables a consumer to use the service provider’s development tools or Application Programmer Interface (API) to develop and deploy specific cloudbased applications or services. Another example of PaaS might be using a third party’s MySQL database and Apache services to build a cloudbased customer relationship management (CRM) platform.
The IaaS service model provides the greatest degree of freedom by enabling its consumer to provision processing, memory, storage, and network resources within the cloud infrastructure. The IaaS service model also enables its consumer to install applications, including operating systems (OSs) and custom applications. However, with IaaS, the cloud infrastructure remains in control of the service provider. A company that hires a service provider to deliver cloudbased processing and storage that will house multiple physical or virtual hosts configured in a variety of ways is using IaaS. For example, a company that wanted to establish a web server farm by configuring multiple Linux Apache MySQL PHP (LAMP) servers could save hardware costs by virtualizing the farm and using a provider’s cloud service to deliver the physical infrastructure and bandwidth for the virtual farm. Control over the OS, software, and server configuration would remain the responsibility of the organization, whereas the physical infrastructure and bandwidth would be the responsibility of the service provider. -
Which of the following emailrelated FirePOWER preprocessors can extract and decode attachments in clienttoserver traffic? (Select the best answer.)
- only the IMAP preprocessor
- only the POP3 preprocessor
- only the SMTP preprocessor
- only the POP3 and SMTP preprocessors
- only the IMAP and SMTP preprocessors
- the IMAP, POP3, and SMTP preprocessors
Explanation:
On a Cisco FirePOWER Intrusion Prevention System (IPS), the Internet Message Access Protocol (IMAP), Post Office Protocol version 3 (POP3), and Simple Mail Transfer Protocol (SMTP) preprocessors can extract and decode attachments in clienttoserver traffic. The FirePOWER IMAP, POP3, and SMTP preprocessors are Application layer inspection engines with the capability to decode email traffic and to normalize the resulting data prior to forwarding the traffic to the intrusion rules engine for analysis.
In addition to generating an event when they observe anomalous traffic, the FirePOWER emailrelated preprocessor engines can inspect the commands that pass between a client and a server to ensure that they are compliant with the relevant Request for Comments (RFC). For example, the IMAP preprocessor can generate an event when either a client command or a server response does not comply with RFC 3501, which is the RFC that defines the IMAP protocol, and the POP3 preprocessor can do the same for commands that do not comply with RFC 1939, which is the RFC that defines the POP3 protocol. By contrast, the SMTP preprocessor provides the ability to normalize all, none, or a specific set of SMTP commands, although a base set of commands will always be considered as part of the custom valid set if normalization is enabled. -
Which of the following authentication methods is not used with OSPFv3? (Select the best answer.)
- plaintext
- MD5
- SHA1
- IPv6 IPSec
Explanation:
Plaintext authentication is not used with Open Shortest Path First version 3 (OSPFv3), which is also called OSPF for IP version 6 (IPv6). OSPFv3 uses IPv6 IP Security (IPSec) authentication, which in turn uses either Message Digest 5 (MD5) or the Secure Hash Algorithm 1 (SHA1). Although plaintext authentication is not used by OSPFv3, you can configure OSPFv3 either to encrypt the MD5 or SHA1 hash that is used by IPv6 IPSec or to leave the hash unencrypted. Encrypting the hash provides an extra layer of security but requires additional processing that could introduce latency. You can issue either the ospfv3 authentication command or the ipv6 ospf authentication command to configure authentication for OSPFv3 on an interface.
MD5 and plaintext authentication are supported by OSPF version 2 (OSPFv2), which is the IPv4 version of OSPF. By default, no authentication method is used with OSPFv2. To configure a router for MD5 authentication, you should first configure the authentication password by issuing the ip ospf authenticationkey password command in interface configuration mode. Then you should configure MD5 authentication for an OSPF interface by issuing the ip ospf authentication messagedigest command in interface configuration mode. Because plaintext authentication is notoriously insecure, Cisco recommends using MD5 authentication for OSPFv2 instead of plaintext authentication. -
You have configured a Cisco Catalyst switch to store its binding table on a local TFTP server.
Which of the following commands can you issue to verify the URL that the agent will use to store the binding table on the TFTP server? (Select the best answer.)
- show ip dhcp snooping
- show ip dhcp snooping database
- show ip dhcp snooping binding
- show ip dhcp snooping statistics
Explanation:
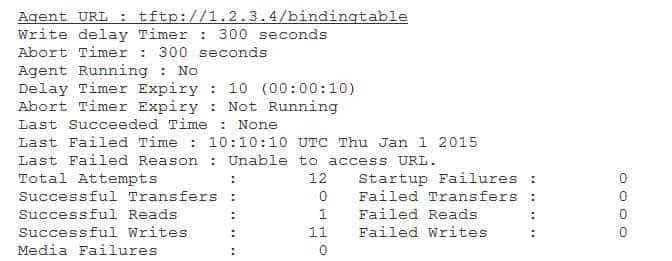
You can issue the show ip dhcp snooping database command to verify the Uniform Resource Locator (URL) that the agent will use to store the binding table when Dynamic Host Configuration Protocol (DHCP) snooping is configured on a Cisco Catalyst switch to store the binding table on a local Trivial File Transfer Protocol (TFTP) server. DHCP snooping ensures that DHCP servers reside on trusted switch interfaces and that all DHCP traffic from untrusted interfaces is verified before being forwarded. When a switch is configured to use DHCP snooping, the switch tracks client Media Access Control (MAC) addresses and their associated DHCP client hardware addresses in the DHCP snooping binding database, which is also known as the binding table. If the switch receives DHCP packets that do not match entries in the binding table, the switch drops the packets. The binding table can be stored locally or it can be stored on a remote server.
The show ip dhcp snooping database command can be used to display the status of the DHCP snooping binding table agent and statistics regarding the status of the binding table, such as the URL where the binding table can be found and how many successful writes have been committed to the table. For example, the following sample output indicates that the binding table is stored in a file named bindingtable on the TFTP server with an IP address of 1.2.3.4:
300-735 Part 07 Q07 055 The show ip dhcp snooping command displays general information regarding the DHCP snooping configuration on a switch, such as the virtual LANs (VLANs) for which DHCP snooping is enabled and the trusted state of each interface. For example, the following sample output indicates that DHCP snooping is enabled for VLANs 101, 201, and 301:

300-735 Part 07 Q07 056 The show ip dhcp snooping binding command displays the dynamic entries in the binding table. You must use the show ip source binding command to view both static and dynamic binding table entries. For example, the following sample output from the show ip dhcp snooping binding command indicates that two DHCP clients from VLAN 101 have entries in the binding table:

300-735 Part 07 Q07 057 The show ip dhcp snooping statistics command displays statistical information regarding the number of frames that have been forwarded or dropped by the DHCP snooping configuration on a switch. You can use the detail keyword to display expanded statistics, which include the number of packets dropped for each denial category, such as binding mismatches or exceeded rate limits. For example, the following sample output from the show ip dhcp snooping statistics command indicates that 1,450 packets were forwarded and 105 packets were dropped from untrusted ports:
Packets Forwarded = 1450
Packets Dropped = 118
Packets Dropped From untrusted ports = 105 -
You have configured a CoPP policy to mitigate the effects of DoS attacks on the router.
Which of the following packet types does the CoPP policy affect? (Select the best answer.)
- packets originating from the control plane
- packets destined to the control plane
- packets originating from the data plane
- packets destined to the data plane
Explanation:
The Control Plane Policing (CoPP) policy in this scenario affects packets that are destined to the control plane of a router. Packets destined to the control plane are typically packets intended to create or perform network operations on a router, such as packets from dynamic routing protocols or Address Resolution Protocol (ARP) packets. These packets cannot be handled by Cisco’s normal fastpath switching mechanisms, such as Cisco Express Forwarding (CEF), because they require special handling by the router’s CPU, which is also known as the route processor. CoPP is a Cisco IOS feature that protects the route processor of a router or switch from malicious traffic, such as Denial of Service (DoS) attacks.
The control plane is one of the four logical components that collectively define a router? the remaining components are the data plane, the management plane, and the services plane. The control plane is the home of the route processor and is essential to the forwarding of packets because routing protocol operation, network management, and processbased switching all involve the control plane. CoPP filters the types of packets that enter or exit the control plane and controls the rate at which permitted packets enter or exit the control plane. Because traffic must pass through the control plane to reach the management plane, CoPP protects the management plane as well.
The CoPP policy in this scenario does not affect packets that originate from the control plane of a router. DoS attacks that target a router use packets either that are destined to the router itself or that require special handling by the router’s route processor. Because packets originating from the control plane have already passed through the route processor, a CoPP policy that affects packets exiting the control plane would not mitigate the effects of a DoS attack.
Cisco considers all packets that pass through a router without any interaction from the route processor as data plane traffic, which is also known as transit traffic. Because DoS attacks on a router target the route processor, a CoPP policy that protects a router from DoS attacks would not affect packets originating from or destined to the data plane. -
Which of the following is the most likely reason for an organization to implement an extranet? (Select the best answer.)
- to provide customers with largescale computer services
- to provide internal departments with independent security policies
- to provide internal users with a customized website
- to provide customers with access to the company’s internal network
Explanation:
A company can implement an extranet to provide customers with access to the company’s internal network. An extranet is a portion of a company’s internal network that is accessible to specific people outside of the company, such as business partners, suppliers, or customers. By creating an extranet, a company can provide a location for sharing information with external users. For example, a consulting company could create an extranet for external customers to view and comment on the consulting company’s progress on various projects. In many extranet implementations, the external customer network shares a bilateral connection with the company’s internal network. This bilateral connection not only enables the external customer to access portions of the company’s internal network, but it also enables portions of the company’s internal network to access the portions of the external customer’s network.
An extranet is not implemented to provide customers with largescale computer services. A company could implement a cloud computing infrastructure to provide largescale computer services over a vast network, such as the Internet. Cloud computing allows for access to applications, storage space, and other services on demand without requiring that the services be installed locally. Cloud computing can be used to replace or supplement highly utilized local systems. The use of cloudbased services can simplify IT management by reducing or eliminating the amount of time needed to install, upgrade, and manage services.
An extranet is not implemented to provide internal departments with independent security policies. A company could implement security contexts on a firewall, such as the Cisco Adaptive Security Appliance (ASA), to provide internal departments with independent security policies. Security contexts divide a single ASA into multiple virtual devices with unique policies that can be managed by separate administrative domains. This division enables a single physical ASA to provide security services for different departments while keeping the departments logically separated.
An extranet is not implemented to provide internal users with a customized website. Instead, an intranet can be created to provide internal users with their own website. An intranet provides a location for sharing information among members of the company. Unlike an extranet, an intranet is typically available only to internal users. -
Which of the following is the default connection profile that is applied to clientless SSL VPN connections? (Select the best answer.)
- DefaultRAGroup
- DefaultWEBVPNGroup
- DefaultSSLVPNGroup
- DefaultL2LGroup
Explanation:
The DefaultWEBVPNGroup connection profile is the default connection profile that is applied to clientless Secure Sockets Layer (SSL) virtual private network (VPN) connections. Connection profiles are used to separate remote VPN users into groups. For example, you can use one connection profile for contractors and another connection profile for managers, with each profile providing access to different resources. If no connection profile is associated with a particular user or if the user did not select a connection profile when the user initiated the VPN connection, the default connection profile will be used. For SSL VPN connections, the default connection profile is the Default WEB VPN Group profile. You can edit the default connection profiles, but you cannot delete them.
The Default RAGroup connection profile is not the default connection profile for clientless SSL VPN connections. This profile is the default profile used for full tunneling IP Security (IPSec) VPN connections.
The DefaultL2LGroup connection profile is not the default connection profile for clientless SSL VPN connections. This profile is the default profile used for IPSec LANtoLAN VPN connections.
The Default SSL VPN Group connection profile is not the default connection profile for clientless SSL VPN connections. This is not a default profile that is provided by Cisco. You can create a connection profile named Default SSL VPN Group, but it will not be used by default for clientless SSL VPN connections. -
You are configuring a connection profile for Cisco AnyConnect SSL VPN users. You have accessed the Add SSL VPN Connection Profile dialog box in ASDM. You want to configure a group URL for the connection profile.
On which of the following screens of this dialog box will you be able to accomplish your goal? (Select the best answer.)
- the Basic screen
- the General screen
- the Authorization screen
- the SSL VPN screen
Explanation:
You can configure a group Uniform Resource Locator (URL) for the connection profile that you are configuring for Cisco AnyConnect Secure Sockets Layer (SSL) virtual private network (VPN) users on the SSL VPN screen of the Add SSL VPN Connection Profiledialog box in Cisco Adaptive Security Device
Manager (ASDM). If you configure a group URL for SSL VPN users, the users can connect to the group URL and will not be required to select a tunnel group when they establish a connection. In such a scenario, the user is presented with only user name and password fields on the login screen. The Cisco Adaptive Security Appliance (ASA) examines the URL from which the user is connecting and automatically applies the connection profile associated with the URL. Configuring a group URL can help improve security because the user is not presented with a list of available connection profiles.
To configure a group URL for a new SSL VPN connection profile in ASDM, you should click Configuration, expand Network (Client) Access, click AnyConnect Connection Profiles, and click Add under Connection Profiles, which will open the Add SSL VPN Connection Profile dialog box. In the Add SSL VPN Connection Profile dialog box, expand Advanced and click SSL VPN to open the SSL VPN screen, which is shown in the following exhibit:
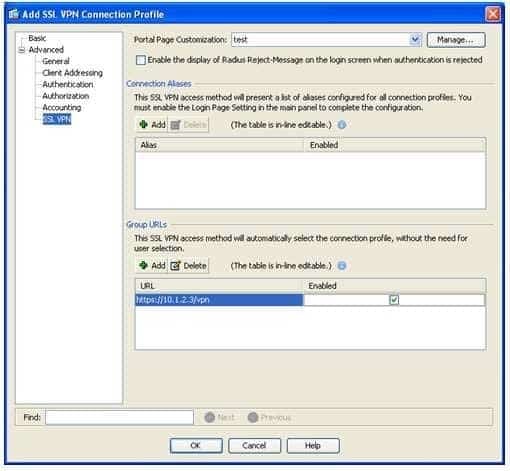
300-735 Part 07 Q11 058 You cannot configure a group URL on the Basic screen of the Add SSL VPN Connection Profile dialog box in ASDM. On the Basic screen, you can configure the connection profile name, the Authentication, Authorization, and Accounting (AAA) server group, the default group policy, and client addressing information, such as Dynamic Host Configuration Protocol (DHCP) servers and IP address pools.
You cannot configure a group URL on the General screen of the Add SSL VPN Connection Profile dialog box in ASDM. On the General screen, you can enable password management and configure password expiration notification options.
You cannot configure a group URL on the Authorization screen of the Add SSL VPN Connection Profile dialog box in ASDM. On the Authorization screen, you can configure an authorization server group and user name certificate mapping. -
You are configuring a connection profile for clientless SSL VPN connections. You have accessed the Add Clientless SSL VPN Connection Profile dialog box in ASDM.
Which of the following authentication methods can you configure in this dialog box? (Select the best answer.)
- only AAA
- only OTP
- only digital certificates
- both AAA and OTP
- both AAA and digital certificates
Explanation:
You can configure Authentication, Authorization, and Accounting (AAA) and digital certificate authentication on the Add Clientless SSL VPN Connection Profile dialog box in Cisco Adaptive Security Device Manager (ASDM). Connection profiles are used to separate remote virtual private network (VPN) users into groups. For example, you can use one connection profile for contractors and another connection profile for managers, with each profile providing access to different resources.
You can configure a new connection profile by using ASDM. To configure a new connection profile for clientless Secure Sockets Layer (SSL) VPN connections by using ASDM, you should click Configuration, click the Remote Access VPN button, expand Clientless SSL VPN Access, and click Connection Profiles, which will open the Connection Profiles configuration pane. From this pane, you can view a list of existing connection profiles and you can create new connection profiles. You should click the Add button under Connection Profiles in the Connection Profiles screen to create a new connection profile and to open the Add Clientless SSL VPN Connection Profile dialog box, which is shown in the following exhibit:
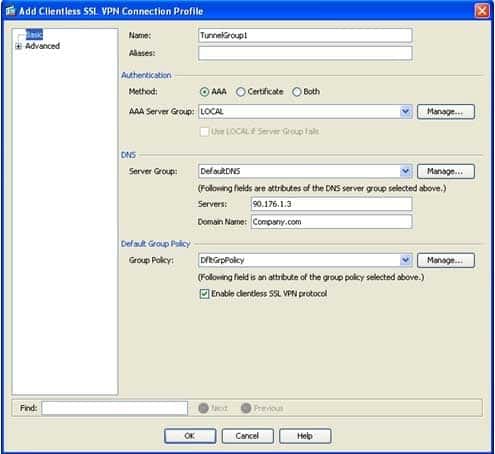
300-735 Part 07 Q12 059 In this dialog box, you can configure the connection profile details, including the authentication method to use, the Domain Name System (DNS) server to use, and the group policy to apply to the connection profile. There are two authentication methods that are supported: AAA and Certificate. You can configure the connection profile to use either or both of the methods.
You cannot configure onetime passwords (OTPs) as an authentication method for connection profiles on the Add Clientless SSL VPN Connection Profile dialog box in ASDM. OTP is a two factor user authentication method that typically uses a personal identification number (PIN) in conjunction with code generated by a hardware or software token. The token is synchronized with a central server and periodically generates a code. The code is only valid until the next code is generated, which typically occurs in less than 60 seconds. -
Which of the following can you mitigate by implementing DAI? (Select the best answer.)
- ARP poisoning attacks
- MAC spoofing attacks
- MAC flooding attacks
- VLAN hopping attacks
Explanation:
Implementing Dynamic ARP Inspection (DAI) can help mitigate Address Resolution Protocol (ARP) poisoning attacks. In an ARP poisoning attack, which is also known as an ARP spoofing attack, the attacker sends a gratuitous ARP (GARP) message to a host. The GARP message associates the attacker’s Media Access Control (MAC) address with the IP address of a valid host on the network. Subsequently, traffic sent to the valid host address will go through the attacker’s computer rather than directly to the intended recipient.
You should change the native virtual LAN (VLAN) on trunk ports to an unused VLAN to mitigate VLAN hopping attacks. In a VLAN hopping attack, attacker sends doubletagged 802.1Q frames over a trunk link. A doubletagged frame is an Ethernet frame containing two distinct 802.1Q headers. Although doubletagging can be used as a legitimate way to tunnel traffic through a network and is commonly used by service providers, it can also be used by an attacker to circumvent security controls on an access switch. In a VLAN hopping attack, the attacker attempts to inject packets into other VLANs by accessing the native VLAN on a trunk and sending doubletagged 802.1Q frames to the switch. The switch strips the outer 802.1Q header from the received frame and then forwards the frame, which still includes an 802.1Q header, across a trunk port to the VLAN of the target host. A successful VLAN hopping attack enables an attacker to send unidirectional traffic to other VLANs without the use of a router.
Implementing sticky secure MAC addresses can help mitigate MAC spoofing attacks. In a MAC spoofing attack, an attacker uses the MAC address of another known host on the network in order to bypass port security measures. MAC spoofing can also be used to impersonate another host on the network.
Limiting the number of MAC addresses permitted on a port can help mitigate MAC flooding attacks. In a MAC flooding attack, an attacker generates thousands of forged frames every minute with the intention of overwhelming the switch’s MAC address table. Once this table is flooded, the switch can no longer make intelligent forwarding decisions and all traffic is flooded. This allows the attacker to view all data sent through the switch because all traffic will be sent out each port. A MAC flooding attack is also known as a content addressable memory (CAM) table overflow attack. -
You have configured a lawful intercept view, five CLI views, and two superviews on a Cisco router. How many additional CLI views can you create? (Select the best answer.)
- one
- two
- six
- seven
Explanation:
You can create seven additional command line interface (CLI) views on a Cisco router if you have already configured a lawful intercept view, five CLI views, and two superviews. A CLI view enables an administrator to provide granular access to IOS commands and interfaces to a specific user or group of users. CLI views can be grouped under a superview to provide access to all of the commands within each view. On hardware platforms that support it, a single lawful intercept view can be created to provide secure access to a specific set of commands pertaining to voice calls and their associated Simple Network Management Protocol (SNMP) data.
The maximum number of CLI views you can create on a Cisco router is 15. This includes one lawful intercept view and any combination of CLI views and superviews? however, this does not include the root view, which is created by default and does not count against the number of available views. In this scenario, you have created eight views: one lawful intercept view, five CLI views, and two superviews. Because you can configure a maximum of 15 views, you can create only seven more views. Each of the newly created views could be a CLI view or a superview but could not be a lawful intercept view, because one has already been created. -
Which of the following statements is true regarding the aaa new-modelcommand? (Select the best answer.)
- The aaa new-model command must be issued prior to enabling AAA accounting on a router.
- The aaa new-model command must be issued after enabling AAA authentication on a router.
- The aaa new-model command configures AAA to work only with RADIUS servers.
- The aaa new-model command configures AAA to work only with TACACS+ servers.
- The aaa new-model command has been deprecated in Cisco IOS versions 12.3 and later.
Explanation:
The aaa new-model command must be issued prior to enabling Authentication, Authorization, and Accounting (AAA) accounting on a router. AAA can be used to control access to a router or switch. Before configuring authentication, authorization, or accounting using AAA, you must first issue the aaa new-model command to enable AAA on the device? the aaa authentication, aaa authorization, and aaa accounting commands cannot be issued until the aaa new-model command is issued. When the aaa new-model command is issued, local authentication is applied immediately to all router lines and interfaces? any existing authentication methods are superseded by the aaa new-model command. All future connection attempts will be authenticated using the method defined in the aaa authentication command.
When implementing AAA, you can configure users to be authenticated against a local database, against a Remote Authentication DialIn User Service (RADIUS) server, or against a Terminal Access Controller Access Control System Plus (TACACS+) server. You are not limited to a single type of authentication with AAA.The aaa newmodel command has not been deprecated in Cisco IOS versions 12.3 and later. This command is required in these versions of Cisco IOS in order to implement AAA on a router or a switch.
-
Which of the following signature microengines typically has the greatest effect on Cisco IOS IPS performance? (Select the best answer.)
- atomic-ip
- normalizer
- service-http
- service-smb-advanced
- string-tcp
Explanation:
Of the choices provided, the stringtcp signature microengine (SME) typically has the greatest effect on Cisco IOS Intrusion Prevention System (IPS) performance. An SME compiles a specific category of signatures and loads them into the IPS regular expression table. Within each category is a number of signatures that can analyze a packet or stream of packets for a particular pattern. For example, the atomicip SME contains signatures that can recognize a pattern in a single packet, whereas the servicehttp SME contains signatures than can recognize a pattern in a stream of Hypertext Transfer Protocol (HTTP) packets. In general, the more of a packet or stream of packets that an SME needs to analyze, the greater its impact on the available memory and CPU of the router. The stringtcp SME can analyze one or more Transmission Control Protocol (TCP) packets and search for a particular string of text.
The atomicip SME can analyze the Layer 3 and Layer 4 header fields of a single packet. Because the atomicip SME signatures operate on a single packet, they cannot preserve state information between packets. However, atomicip SME signatures do not consume large amounts of memory or CPU resources like stringbased SMEs can consume.
The servicehttp and servicesmbadvanced SMEs can analyze Layer 5 through 7 information for HTTP and Server Message Block (SMB) network services, respectively. Service SMEs are typically the most complicated SMEs because they understand and implement a significant portion of the network services for which they are designed. For example, the servicehttp SME can effectively mimic the characteristics of a web server in order analyze the HTTP payload between a web server and its client. Because service SMEs have a deep knowledge of their underlying protocols, they can be optimized to decode only particular portions of a data stream, thereby reducing their impact on the memory and CPU utilization.
The normalizer SME is targeted at fragmented IP datagrams. The normalizer SME reassembles the fragmented IP datagrams and then analyzes the completed datagram before deciding whether the datagram should be forwarded or discarded. If the normalizer SME decides that a datagram should be forwarded but the datagram is too large to transmit, it will refragment the datagram prior to forwarding it. If the normalizer SME had to analyze fragmented datagrams based on the many different ways that destination devices might reassemble them, it could consume a significant amount of memory and CPU resources? however, because the normalizer SME reassembles datagrams without regard to how the target device will receive them, the process can be optimized with regard to memory and CPU utilization. -
You have configured the password management feature for a tunnel group on an ASA. The ASA is using a
Cisco Secure ACS RADIUS server for AAA authentication.
Which of the following actions will occur after a remote user with an expired password attempts to establish a VPN connection? (Select the best answer.)
- The AnyConnect client will display an authentication failed dialog box and will not permit the user to establish the VPN connection until an admin unlocks the user’s account.
- The AnyConnect client will display a dialog box that prompts the user for a new password.
- The AnyConnect client will display a dialog box that prompts the user for both their old password and a new password.
- The AnyConnect client will display a dialog box notifying the user that their password has expired but will permit the user to establish the VPN connection with the expired password.
Explanation:
In this scenario, the Cisco AnyConnect virtual private network (VPN) client will display a dialog box that prompts the user for a new password after a remote user with an expired password attempts to establish a VPN connection. When a Cisco Adaptive Security Appliance (ASA) is configured to use the password management feature for a particular tunnel group, the ASA will use Microsoft Challenge Handshake
Authentication Protocol version 2 (MSCHAPv2) rather than Password Authentication Protocol (PAP) when communicating with the Remote Authentication DialIn User Service (RADIUS) server and the AnyConnect client. MSCHAPv2 supports password expiry and password change capabilities that are not inherently supported by PAP or RADIUS. This enables the ASA to understand RadiusReject messages with password expiry information instead of simply treating the messages as authentication failure messages. When the ASA receives the RadiusReject message with password expiry information, it sends a MODE_CFG message to the AnyConnect VPN client, causing it to display a dialog box that prompts the user for a new password. The ASA then forwards the new password to the RADIUS server, and if the new password meets the configured password requirements, the user is authenticated and the ASA can finish establishing the VPN connection.
The AnyConnect client will not prevent the user from establishing a VPN connection until an administrator unlocks the user’s account. Because the password management feature is enabled on the ASA, it has the capability to prompt the user to update their expired password. However, if the password management feature was not enabled on the ASA in this scenario, then RadiusReject messages received from the RADIUS server would be interpreted as an authentication failure message and users with expired passwords would be unable to establish VPN connections.
The AnyConnect client will not prompt the user for both their old password and a new password nor will it permit the user to establish the VPN connection with an expired password. -
You want to issue the following block of commands on a Cisco ASA:
ASA(config)#nat (DMZ, INSIDE) source dynamic any interface destination static INSIDESQLEXT INSIDESQLINT
You do not have CLI access to the ASA and must use ASDM instead.
Which of the following samples of the Add NAT Rule dialog box corresponds to the configuration needed to achieve your goal? (Select the best answer.)

300-735 Part 07 Q18 060 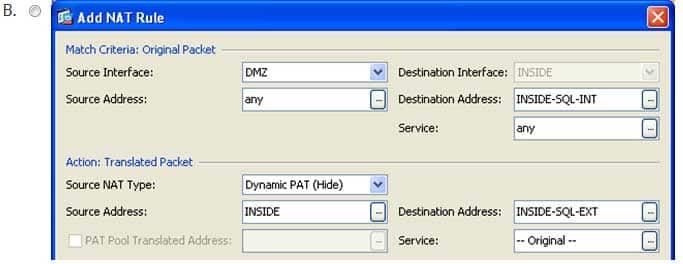
300-735 Part 07 Q18 061 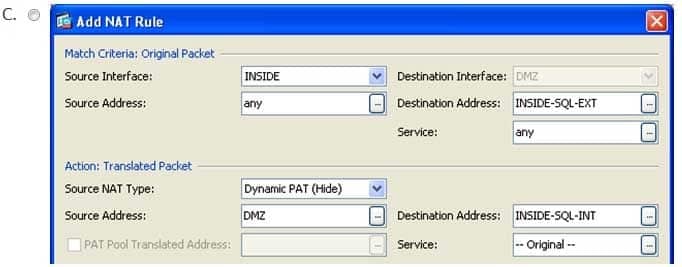
300-735 Part 07 Q18 062 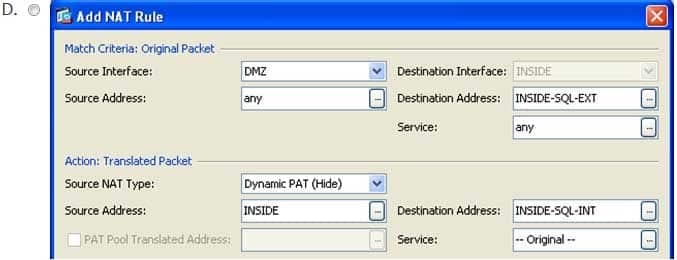
300-735 Part 07 Q18 063 - Option A
- Option B
- Option C
- Option D
Explanation:
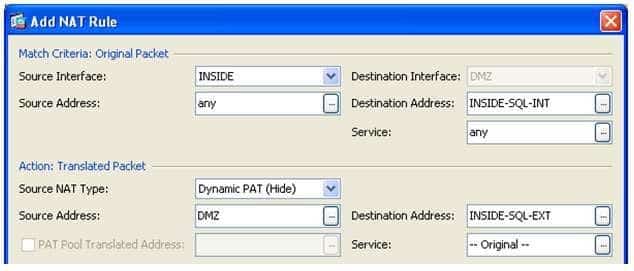
The following sample of the Add NAT Rule dialog box corresponds to the Cisco Adaptive Security Appliance (ASA) configuration needed to achieve your goal using Cisco Adaptive Security Device Manager (ASDM):
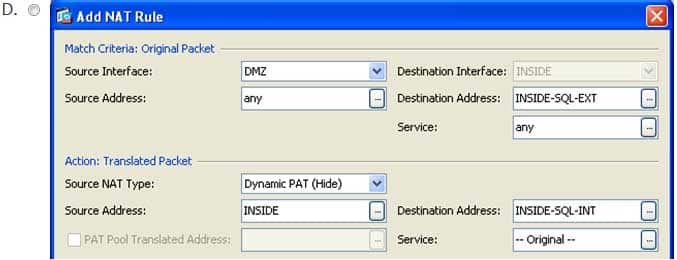
300-735 Part 07 Q18 064 In the exhibit shown above, the Match Criteria: Original Packet section of the Add NAT Rule dialog box contains fields that correspond to the interface and IP address information in a matching packet prior to translation. The Source Interface field specifies the real source interface, the Source Address field specifies the real source IP address, the Destination Interface field specifies the real destination interface, the Destination Address field specifies the real destination IP address, and the Service: field specifies the real protocol port numbers for the original packet. By contrast, the Action: Translated Packet section of the Add NAT Rule dialog box contains fields that correspond to the mapped interface and IP address information in a matching packet after translation. The Source NAT Type field specifies the type of Network Address Translation (NAT), the Source Address field specifies the mapped source IP address, the Destination Address: field specifies the mapped destination IP address, and the Service: field specifies the mapped protocol numbers for the translated packet.
The sample Add NAT Rule dialog box configures the ASA to map the real source IP address traffic from any network attached to the DMZ network to the IP address assigned to the INSIDE interface. In addition, the mapped destination IP address defined in the INSIDESQLEXT object is mapped to the real destination IP address defined in the INSIDESQLINT object. The following diagram depicts the translation of the addresses within matching packets where INSIDESQLEXT has an IP address of 192.168.15.2 and INSIDESQLINT has an IP address of 192.168.13.2:
300-735 Part 07 Q18 065 You could use the nat (DMZ, INSIDE) source dynamic any interface destination static INSIDESQLEXT INSIDESQLINT command from global configuration mode to configure the same dynamic NAT rule as shown in the sample. Add NAT Rule dialog box. When the nat command is issued from global configuration mode, it is referred to as the nat (global) command and it can be used to configure twice NAT on the ASA. Twice NAT enables you to specify a mapping for both the source address and destination address in a packet. The nat (global) command in this scenario can be used to create a dynamic NAT rule which translates traffic between the DMZ and INSIDE interfaces of the ASA. The abbreviated syntax to create a dynamic NAT rule with the nat (global) command is nat (real_interface, mapped_interface) source dynamic {real_object | any} {mapped_object | interface} destination static {mapped_object | interface} {real_object| any}.
The following sample of the Add NAT Rule dialog box corresponds to the nat (DMZ, INSIDE) source dynamic any interface destination static INSIDESQLINT INSIDESQLEXT command: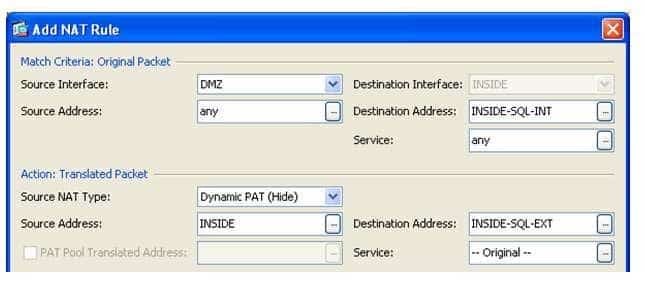
300-735 Part 07 Q18 066 The following sample of the Add NAT Rule dialog box corresponds to the nat (INSIDE, DMZ) source dynamic any interface destination static INSIDESQLEXT INSIDESQLINT command:
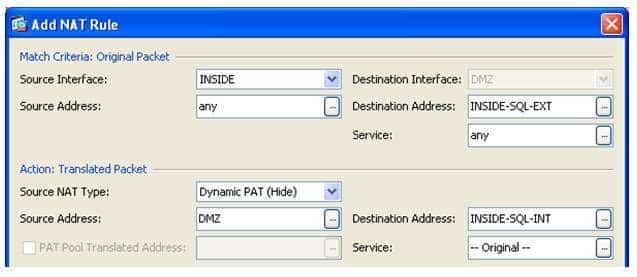
300-735 Part 07 Q18 067 The following sample of the Add NAT Rule dialog box corresponds to the nat (INSIDE, DMZ) source dynamic any interface destination static INSIDESQLINT INSIDESQLEXT command:
-
You are using ASDM to verify an IPSec VPN configuration made by another administrator on an ASA. Please click exhibit to answer the following questions.
Exhibit:
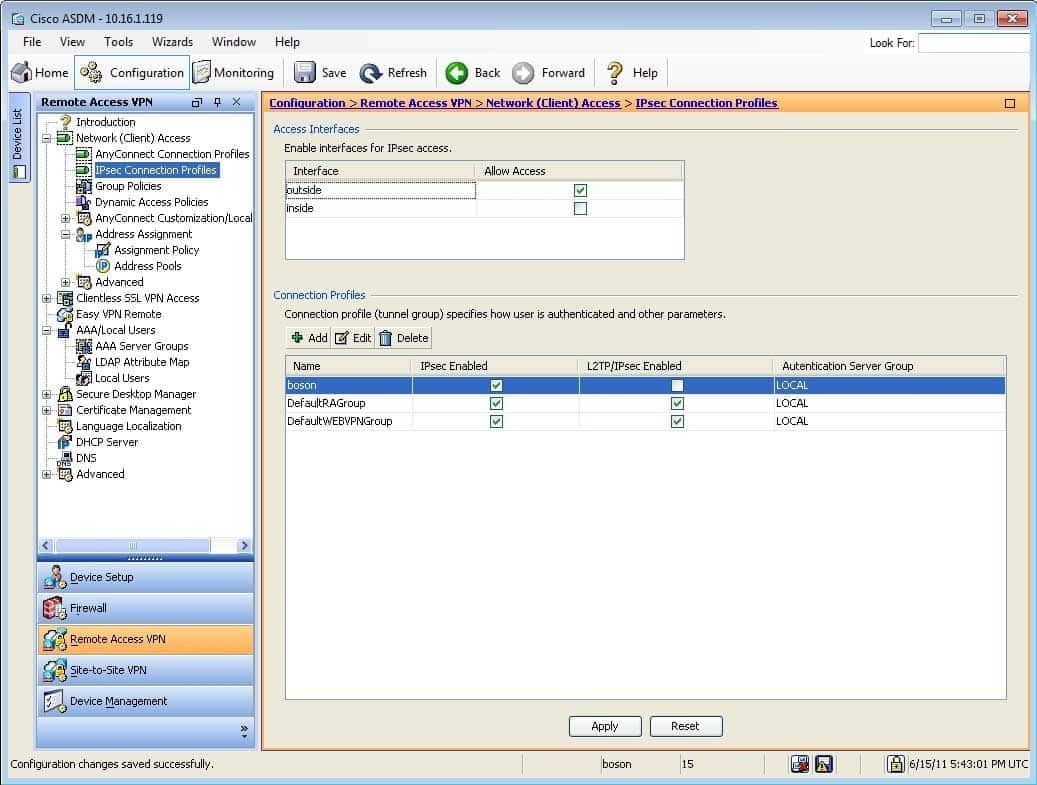
300-735 Part 07 Q19 069 Which of the following tunneling protocols are supported by the boson group policy? (Select the best answer.)
- only clientless SSL VPN
- only SSL VPN Client
- only IPSec
- both clientless SSL VPN and SSL VPN Client
- both clientless SSL VPN and IPSec
- clientless SSL VPN, SSL VPN Client, and IPSec
Explanation:
The boson group policy supports only IP Security (IPSec) as a tunneling protocol. You can specify the tunneling protocols that can be used to establish a connection to a tunnel group, which is also known as a connection profile, either in a group policy or within a user account, depending on whether the tunneling protocol configuration should be applied to a group or to a single user. When you configure a tunneling protocol, you can specify one or more of the following four options: Clientless SSL VPN, SSL VPN Client, IPSec, or L2TP/IPSec.
In this scenario, you can view the tunneling protocols that are configured for the boson group policy user account by accessing the group policy information in Cisco Adaptive Security Device Manager (ASDM) by clicking Configuration, clicking the Remote Access VPN button, expanding Network (Client) Access, clicking Group Policies, and double clicking the boson group policy, which will open the Edit Internal Group Policy dialog box. The More Options section on the General pane displays the Tunneling Protocols entry. This entry for the boson group policy is configured with the IPsec option, which means that the boson group policy supports only IPSec connections. The following exhibit displays the General pane of the Edit Internal Group Policy dialog box for the boson group policy:

300-735 Part 07 Q19 070 -
You are using ASDM to verify an IPSec VPN configuration made by another administrator on an ASA. Please click exhibit to answer the following questions.
Exhibit:
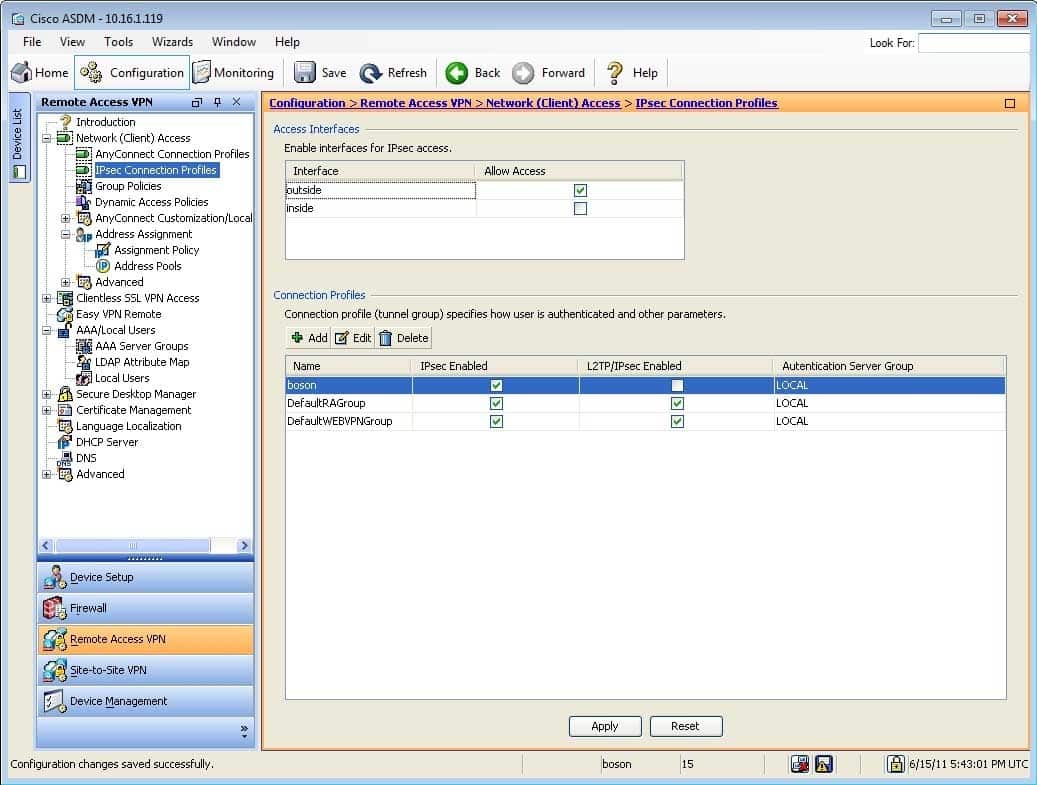
300-735 Part 07 Q20 071 Which of the following IP address ranges will be used to assign address to VPN clients who connect by using the boson connection profile? (Select the best answer.)
- 10.1.1.50 through 10.1.1.75
- 10.1.10.50 through 10.1.10.75
- 192.168.0.100 through 192.168.0.125
- 192.168.10.100 through 192.168.10.125
Explanation:
Virtual private network (VPN) clients who connect by using the boson connection profile will be assigned an
IP address in the range from 10.1.1.50 through 10.1.1.75. You can create a local IP address pool on a Cisco Adaptive Security Appliance (ASA) to deploy IP addresses to remote VPN clients. The IP address pool can then be applied to Cisco AnyConnect or IP Security (IPSec) connection profiles. To view the IP address pool that is associated with the boson connection profile in Cisco Adaptive Security Device Manager (ASDM), you should click Configuration, click the Remote Access VPN button, expand Network (Client) Access, click IPsec Connection Profiles, and then double click boson, which will open the Edit IPsec Remote Access Connection Profile dialog box, as shown in the following exhibit:
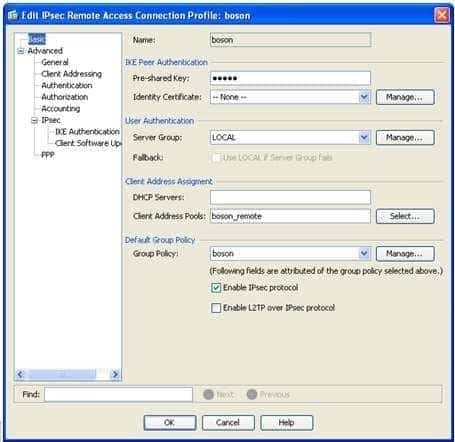
300-735 Part 07 Q20 072 The Client Address Pools entry indicates that the boson_remote address pool has been configured for this connection profile. To view the IP addresses associated with this address pool, you should expand Address Assignment under Network (Client) Access and then click Address Pools, which will display the Address Pools pane, as shown in the following exhibit:

300-735 Part 07 Q20 073 On this pane, you can determine that the boson_remote address pool will distribute IP addresses in the range from 10.1.1.50 through 10.1.1.75.
The boson_internal address pool will distribute IP addresses in the range from 10.1.10.50 through
10.1.10.75. The boson_extranet address pool will distribute IP addresses in the range from 192.168.0.100 through 192.168.0.125. The temporary address pool will distribute IP addresses in the range from
192.168.10.100 through 192.168.10.125. The boson_remote address pool will not distribute IP addresses in any of these ranges.