300-735 : Automating Cisco Security Solutions (SAUTO) : Part 08
-
You are using ASDM to verify an IPSec VPN configuration made by another administrator on an ASA.
Please click exhibit to answer the following questions.Exhibit:
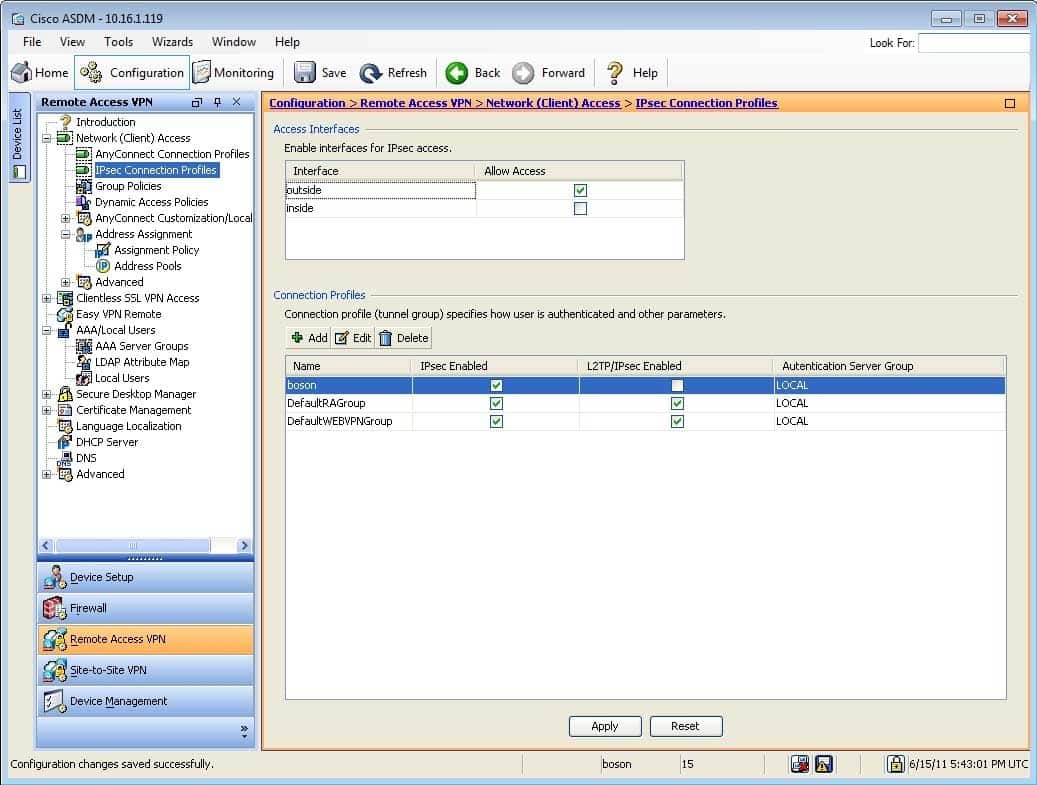
300-735 Part 08 Q01 074 Which of the following group policies will be based when a user establishes a VPN connection by using the boson connection profile? (Select the best answer.)
- internal
- temporary
- DfltGrpPolicy
- boson
Explanation:
The boson connection profile will use the boson group policy. When creating an IP Security (IPSec) connection profile in Cisco Adaptive Security Device Manager (ASDM), you can specify a number of parameters. For example, you can specify the type of authentication to use and the default group policy to use for VPN connections made by using the connection profile. This information can be configured or modified on the Add or Edit IPsec Remote Access Connection Profile dialog box in ASDM. To access this dialog box in ASDM, you should click Configuration, click the Remote Access VPN button, expand Network (Client) Access, click IPsec Connection Profiles, and then doubleclick the connection profile that you want to view. The Edit IPsec Remote Access Connection Profile dialog box for the boson connection profile is shown in the following exhibit:
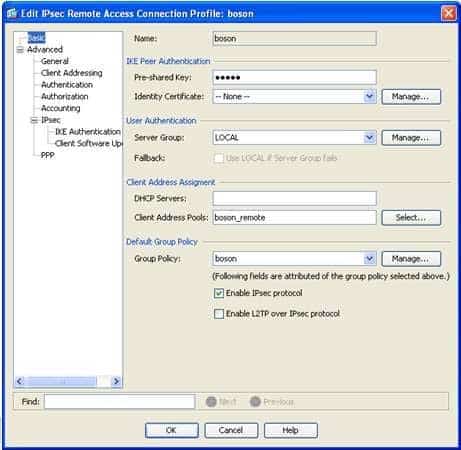
300-735 Part 08 Q01 075 On the Basic pane, you can determine that the Group Policy setting is configured to use the boson group policy. Thus the boson connection profile will not use the DfltGrpPolicy, the internal, or the temporary group policies.
-
You are using ASDM to verify an IPSec VPN configuration made by another administrator on an ASA. Please click exhibit to answer the following questions.
Exhibit:
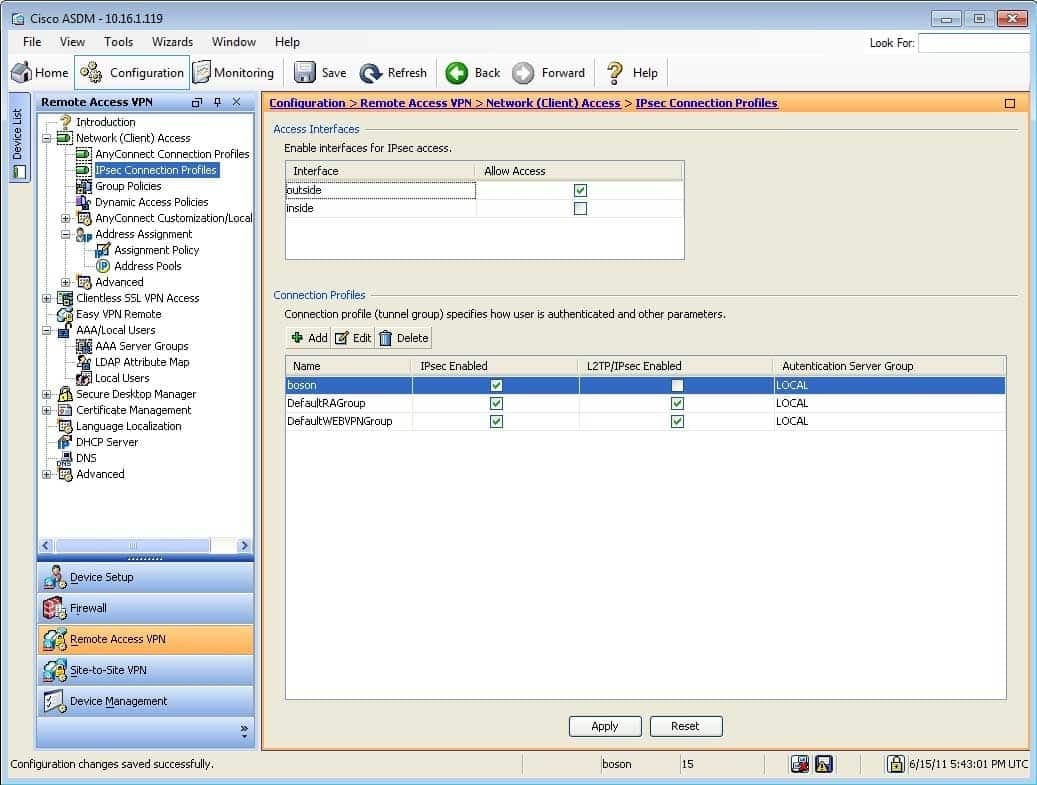
300-735 Part 08 Q02 076 Which of the following will occur when a user attempts to establish a VPN connection to the ASA by using the boson connection profile and the boson user account? (Select the best answer.)
- The user will be unable to establish a VPN connection.
- A banner will be displayed that states “Welcome to Boson Software!”
- The internal group policy will be applied to the connection.
- The VPN traffic will be sent by using only VLAN 2.
Explanation:
Of the choices available, a banner will be displayed that states “Welcome to Boson Software!” when a user attempts to establish a virtual private network (VPN) connection to the Cisco Adaptive Security Appliance (ASA) by using the boson connection profile and the boson user account. You can configure a banner message to be displayed when users establish a VPN connection. This information is configured in the group policy that is associated with the connection profile used to create the connection.
In this scenario, the boson connection profile is associated with the boson group policy. The boson group policy is configured to inherit the banner settings from the default group policy, DfltGrpPolicy. You can view the banner settings by clicking Configuration, clicking the Remote Access VPN button, expanding Network (Client) Access, clicking Group Policies, and double clicking the boson group policy, which will open the Edit Internal Group Policy dialog box, as shown in the following exhibit:

300-735 Part 08 Q02 077 Therefore, to determine whether a banner message will be displayed, you should view the details of the DfltGrpPolicy group policy. By viewing the details of the default group policy, you can determine that a banner message has been configured that states “Welcome to Boson Software!” The following exhibit displays the details of the DfltGrpPolicy group policy:
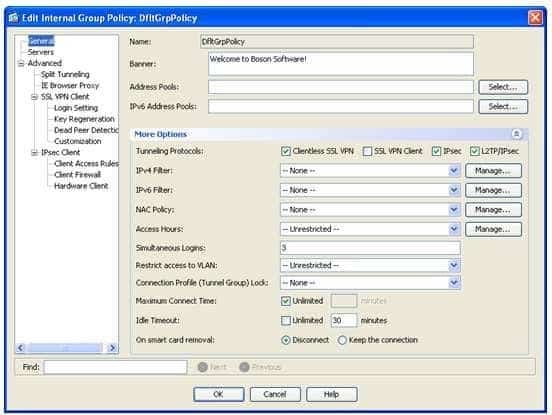
300-735 Part 08 Q02 078 Because the boson group policy inherits the Banner setting, VPN connections made by using connection profiles that use the boson group policy will display the “Welcome to Boson Software!” banner message.
The boson user will be able to establish a VPN connection. There is nothing in the boson user’s profile settings that would prevent the user from making a VPN connection. Moreover, the user will also be able to establish a management session with the ASA, because the boson user has been granted administrative access to the device.
The internal group policy will not apply to a VPN connection made by using the boson connection profile and the boson user account. The boson connection profile is associated with the boson group policy, not the internal group policy.
The VPN traffic will not be sent by using only virtual LAN (VLAN) 2 when a user makes a VPN connection by using the boson connection profile and the boson user account. Although you can configure VLAN restrictions for a group policy, none have been configured in this scenario. -
You are using ASDM to verify an IPSec VPN configuration made by another administrator on an ASA.
Please click exhibit to answer the following questions.
Exhibit: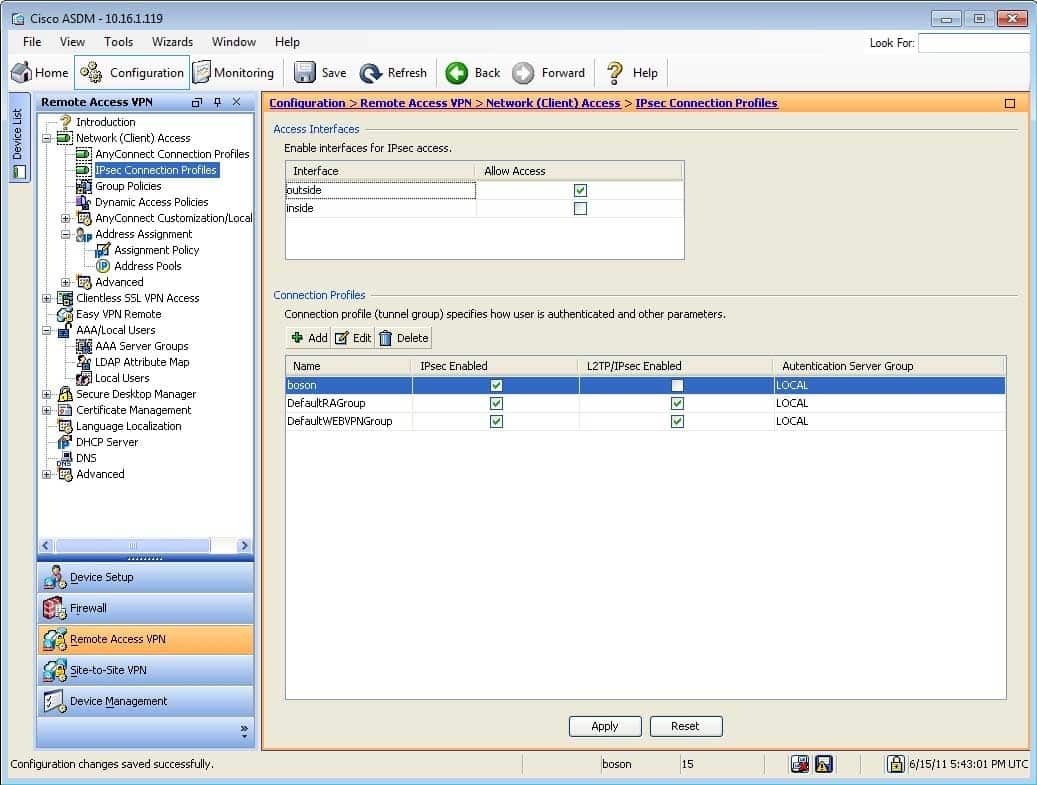
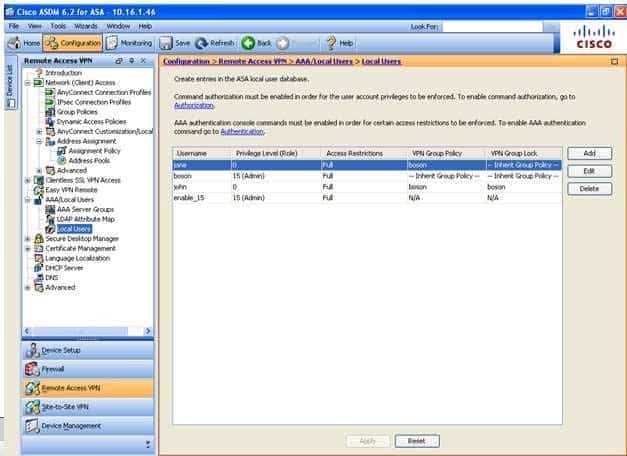
300-735 Part 08 Q03 079 Which of the following users have been assigned to use the boson group policy? (Select the best answer.)
- only jane
- only john
- only boson
- both john and jane
- john, jane, and boson
Explanation:
Both the john and jane user accounts have been configured to use the boson group policy. When configuring a user account, you can specify the group policy to associate with the user account. This is configured on the VPN Policy pane of the Add or Edit User Account dialog box. You can access the Add or Edit User Account dialog box in Cisco Adaptive Security Device Manager (ASDM) by clicking Configuration, clicking the Remote Access VPN button, expanding AAA/Local Users, clicking Local Users, double clicking the user, and clicking VPN Policy, as shown in the following exhibit:
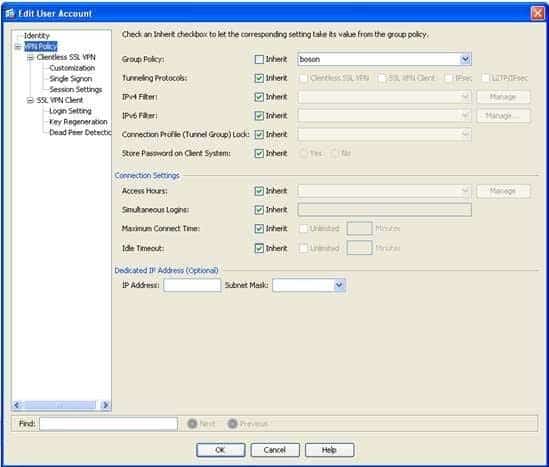
300-735 Part 08 Q03 080 For both the john and jane user accounts, the Group Policy setting is configured to use the boson group policy. You can also view the group policy configuration for all users on the Local Users pane in ASDM. For example, in the following exhibit, the VPN Group Policy column indicates that only the john and jane user accounts are configured to use the boson group policy:
-
You manage your company’s Cisco devices by using Telnet. Your supervisor is concerned about eavesdropping over inband device management and has asked you to recommend a solution that would allow you to disable the Telnet servers on each device.
Which of the following are you most likely to recommend as a replacement? (Select the best answer.)
- SNMPv3
- SSH
- SFTP
- SCP
Explanation:
Most likely, you will recommend Secure Shell (SSH) as a replacement for Telnet as a method of inband management on your company’s Cisco devices. SSH is a virtual terminal (VTY) protocol that can be used to securely replace Telnet. Telnet is considered to be an insecure method of remote connection because it sends credentials over the network in clear text. Therefore, you should replace Telnet with an encrypted application, such as SSH, where possible. Encryption is a method of encoding network traffic so that it cannot be read intransit. Thus encryption can be used to defeat eavesdropping attacks.
You are not likely to recommend any version of Simple Network Management Protocol (SNMP) as a replacement for Telnet. However, if your company were using SNMP version 1 (SNMPv1) or SNMPv2 as a means of inband management, you might recommend that your company use SNMPv3 instead. Three versions of SNMP currently exist. SNMPv1 and SNMPv2 do not provide encryption? password information, known as community strings, is sent as plain text with messages. SNMPv3 improves upon SNMPv1 and SNMPv2 by providing encryption, authentication, and message integrity to ensure that the messages are not tampered with during transmission.
You are not likely to recommend either Secure File Transfer Protocol (SFTP) or Secure Copy (SCP) as a replacement for Telnet. However, either of those applications could replace File Transfer Protocol (FTP), which is a protocol that is used to exchange files between devices. FTP transmits all data as clear text. Both SFTP and SCP transmit information in an encrypted format. -
Which of the following commands should you issue when troubleshooting basic IKE peering to determine whether PSKs are present and matching on both peers? (Select the best answer.)
- ping
- traceroute
- show crypto isakmp policy
- debug crypto isakmp
Explanation:
You should issue the debug crypto isakmp command to determine whether preshared keys (PSKs) are present and matching on both peers. If there is a PSK mismatch between the peers, you will see the 1d00h:%CRYPTO4IKMP_BAD_MESSAGE: IKE message from 10.11.12.13 failed its sanity check or is malformed debug error message. If a PSK is missing on one of the peers, you will see the 1d00h:#CRYPTO4IKMP_NO_PRESHARED_KEY: Preshared key for remote peer at 10.11.12.13 is missing debug error message. To create a PSK, issue the crypto isakmp key key {address | ipaddress [mask] | hostname name} [noxauth] command.
When troubleshooting basic Internet Key Exchange (IKE) peering, you should perform the following steps:
1. Verify that the peers can reach each other.
2. Verify that the IKE policies match on both peers.
3. Verify that the peers successfully authenticate each other.To verify that the peers can reach each other, you can issue the ping command. A successful ping indicates that connectivity between the peers exists. If the ping is not successful, you can issue the traceroute command to see where the fault is occurring along the path between the two peers.
To verify that the IKE policies match on both peers, you can issue the show crypto isakmp policy command to display the IKE phase 1 policy settings that are configured on the router, including the encryption algorithm, hash algorithm, authentication method, DiffieHellman (DH) key exchange mechanism, and security association (SA) lifetime. The following displays sample output from the show crypto isakmp policy command:RouterA#show crypto isakmp policy Global IKE policy Protection suite of priority 20 encryption algorithm: AES - Advanced Encryption Standard (128 bit keys) hash algorithm: Secure Hash Standard authentication method: PreShared Key DiffieHellman group: #14 (2048 bit) lifetime: 3600 seconds, no volume limit
To configure IKE phase 1 policy parameters, issue the crypto isakmp policy priority command to enter ISAKMP policy configuration mode, where you can issue the following commands:
– authentication – encryption
– group
– hash
– lifetime
You can issue the debug crypto isakmp command to determine whether an IKE phase 1 policy mismatch is occurring. The debug error message 1d00h: ISAKMP (0:1): atts are not acceptable. Next payload is 0 will appear when there is a phase 1 policy mismatch between the peers.To verify that the peers successfully authenticate each other, you should issue the debug crypto isakmp command. If the PSKs are present and matching on both peers, the IKE SA should establish successfully and communication between the sites should occur.
-
Your company has installed and configured a Sourcefire device. You want to reduce false positives from a trusted source.
Which of the following could you do? (Select 2 choices.)
- Configure an Allow action with an Intrusion Policy.
- Configure a Block action with an Intrusion Policy.
- Configure a Trust action.
- Configure an Allow action without an Intrusion Policy.
- Configure a Block action without an Intrusion Policy.
- Configure a Monitor action.
Explanation:
You could configure a Sourcefire Allow action without an Intrusion Policy to reduce false positives from a trusted source. Alternatively, you could configure a Trust action. A false positive occurs when an intrusion detection system (IDS) or intrusion prevention system (IPS) identifies non malicious traffic as malicious. Sourcefire devices are commercial Cisco IDSs based on the opensource IDS known as Snort.
A Sourcefire device can match traffic based on a number of conditions, including security zones, networks, virtual LAN (VLAN) tags, source or destination ports, applications, Uniform Resource Locators (URLs), or users. The Sourcefire is also capable of handling traffic matching a given condition by applying an action, or rule, to the traffic. The actions that are supported by a Sourcefire include all of the following:
– Monitor
– Trust
– Block
– Interactive Block
– Allow
Configuring actions is a step in configuring granular access control rules, which in turn is part of developing an Access Control Policy.
A Sourcefire can inspect and log traffic that is passed by the Allow action. Sourcefire inspection occurs when an Intrusion Policy is applied to this action. Applying an action without an Intrusion Policy performs the given action when traffic matches a condition but does not inspect the traffic. Therefore, you could apply an Allow action without an Intrusion Policy to allow all traffic matching a given condition and prevent that traffic from generating a false positive. Conversely, you might apply an Allow action with an Intrusion Policy to permit all but malicious traffic that matches a given condition.
The Trust action allows traffic to pass uninspected and not logged. Therefore, the Trust action can never prevent malicious traffic from passing through the Sourcefire and will never generate false positives. You cannot configure a Block action with an Intrusion Policy. In addition, you should not configure a Block action to prevent false positives in this scenario. The Block action blocks traffic and does not perform any type of inspection.
You do not need to configure a Monitor action. The Monitor action does not determine whether traffic is blocked or allowed based on a matching condition? its purpose is to track traffic from the network. This action is primarily used to log all traffic that connects to the Sourcefire. The Monitor action will log the traffic even if does not match any other condition and is not allowed to pass. -
Which of the following is a reason to use the roundrobin assignment feature of dynamic PAT addresses? (Select the best answer.)
- You want to send traffic to more than one remote device.
- You want to map a single internal IP address to a single routable IP address.
- You want to prevent the misinterpretation of traffic as a DoS attack.
- You want to use a single mapped routable address.
Explanation:
You would use the roundrobin assignment feature of dynamic Port Address Translation (PAT) addresses if you want to prevent the misinterpretation of traffic as a Denial of Service (DoS) attack. Dynamic PAT is a form of Network Address Translation (NAT) that enables IP source addresses to be translated from many unique IP addresses to one of a pool of routable IP address. NAT is most often used to conserve routable IP addresses on the public side of a NAT router. When PAT is configured, an inside local address, along with a port number, is typically mapped to a single inside global address. The NAT router uses port numbers to keep track of which packets belong to each host.
Dynamic PAT is capable of mapping internal source addresses to more than one routable IP address. Some security appliances could mistake a large number of packets from a single IP address as a DoS attack attempt. Therefore, dynamic PAT supports the use of roundrobin to enable internal IP source addresses to map to more than just one routable IP source address. By using dynamic PAT’s roundrobin assignment of IP addresses, the risk of misidentification of large amounts of traffic as a DoS attack can be mitigated.
You could use PAT if you wanted to translate many internal addresses to a single routable IP address. However, you would not need to use the dynamic PAT roundrobin feature to achieve this task. Roundrobin is used to cycle through a pool of routable IP addresses instead of translating to a single routable IP address.
You would use static NAT to map a single internal IP address to a single routable IP address. Static NAT translates a single inside local IP address to a single inside global IP address? the static mapping is permanently present in the NAT translation table. It is therefore possible for someone on an outside network to access a device on an inside network by using its inside global IP address.
You would not need to use dynamic PAT if you want to send traffic to more than one remote device. PAT neither specifically enables nor specifically prevents the sending of traffic from one device to multiple remote devices. -
You are configuring manual NAT on a Cisco Firepower device.
Which of the following best describes the order in which the NAT rules will be processed? (Select the best answer.)
- on a firstmatch basis in the order that they appear in the configuration
- the most general rules first followed by the most specific rules
- static rules first followed by dynamic rules
- shortest prefix first followed by longer prefixes
Explanation:
The Firepower will process the Network Address Translation (NAT) rules on a firstmatch basis in the order that they appear in the configuration if you are configuring manual NAT. There are two methods of implementing NAT on a Cisco Firepower device: manual NAT and auto NAT. Of the two methods, auto NAT is the simplest to configure because NAT rules are configured as components of a network object. Both source and destination addresses are compared to the rules within the object. Manual NAT, on the other hand, enables you to specify both the source address and the destination address of a mapping in a single rule. Therefore, you can configure more granular mapping rules by using manual NAT.
Both manual NAT rules and auto NAT rules are stored in the same translation table. The table is divided into three sections. Section 1 and Section 3 contain manual NAT rules, with Section 1 containing the most specific manual NAT rules and Section 3 containing the most general NAT rules. Section 2 contains auto NAT rules.
When the Firepower matches traffic to the NAT translation table, manual NAT rules in Section 1 are processed first and in the order in which they were configured. Manual NAT rules are added to Section 1 by default. If a match is found, rules in Section 2 and Section 3 are ignored. If the traffic does not match any of the manual NAT rules in Section 1, the auto NAT rules in Section 2 are processed.
Auto NAT rules are automatically ordered by the device. Regardless of the order in which you configured the rules in the network object, auto NAT will always attempt to match static rules before dynamic rules. In addition, auto NAT will always attempt to match the longest address prefix first, meaning that the rule that contains the smallest quantity of real IP addresses will be processed before rules containing a larger quantity of real IP addresses. Therefore, a static NAT mapping that matches 10.10.10.0/24 will be processed before a dynamic NAT mapping that matches 10.10.10.10/32, even though the 10.10.10.10/32 address has a longer prefix. If the traffic matches one of the auto NAT rules, rules in Section 3 are ignored. If the traffic does not match any of the auto NAT rules, the device will next attempt to match the traffic to the Section 3 manual NAT rules.
Similar to Section 1, the manual NAT rules in Section 3 are processed in the order that they appear in the configuration. However, you must specifically place manual NAT rules in this section because the device will not automatically place manual NAT rules there. Cisco recommends that the most general manual NAT rules be placed in this section, with the most specific of those general rules configured first. -
Which of the following is least likely to be considered a form of malware? (Select the best answer.)
- bots
- DDoS
- Trojan horses
- viruses
Explanation:
Of the available choices, a Distributed Denial of Service (DDoS) attack is least likely to be considered a form of malware. Malware, which is a term formed from the combination of the words malicious and software, is unwanted software that is specifically designed to be malicious. Malware can damage or disrupt systems, steal information from a user, or perform other unwanted and malicious actions.
A DDoS attack is a coordinated Denial of Service (DoS) attack that uses multiple attackers to target a single host. For example, a large number of zombie hosts in a botnet could flood a target device with packets. Because the flood of packets originates from multiple hosts and typically targets public services, such as the web service, the target device might not detect the attack. If enough packets are sent to the target device within a short period of time, the target will be unable to respond to legitimate packets because it is waiting for a response to each of the requests originated by the attacker.
Bots are forms of malware. A bot is a type of automated software that can be used as a remote command and control tool to exploit a compromised system for malicious purposes. For example, a botnet is a network of bots on compromised systems that can be used to carry out coordinated attacks, such as a DDoS attack.
Viruses are forms of malware. A virus is a type of software that can make copies of itself and inject them into other software. Viruses can therefore spread across systems and networks. The level of damage that can be inflicted by a virus ranges from annoyances to destruction of data.
Trojan horses are forms of malware. A Trojan horse is a malicious program that entices the user to execute it by appearing to be a legitimate application. Trojan horses can be used to annoy users, steal information, destroy data, or install back doors. -
Which of the following occurs when an IDS or IPS does not identify malicious traffic that enters the network? (Select the best answer.)
- a false positive
- a false negative
- a true positive
- a true negative
Explanation:
A false negative occurs when an intrusion detection system (IDS) or intrusion prevention system (IPS) does not identify malicious traffic that enters the network. False negatives can often lead to disastrous network security problems. To properly secure a network, you should reduce the number of false negatives as much as possible by finetuning IDS and IPS rules, even if more false positives are reported. Penetration testing can help determine when an IDS or IPS is not detecting a genuine attack.
A false positive occurs when an IDS or IPS identifies nonmalicious traffic as malicious. Tuning must be performed to minimize the number of false positives while eliminating false negatives. Not only can too many false positives overburden a router, they can also overburden a network administrator because false positives must usually be verified as harmless.
A true positive occurs when an IDS or IPS correctly identifies malicious traffic as malicious. For instance, a true positive occurs when a virus or an attack is identified and the appropriate action is taken.
A true negative occurs when an IDS or IPS correctly identifies harmless traffic as harmless. For example, a true negative occurs when an administrator correctly enters a password or when Hypertext Transfer Protocol (HTTP) traffic is sent to a web server. -
Which of the following lost or stolen device options are available to employees when MDM is integrated with ISE? (Select 3 choices.)
- report device as lost or stolen
- initiate a PIN lock
- initiate a full or corporate wipe
- quarantine the device
- revoke the device’s digital certificate
Explanation:
When Mobile Device Management (MDM) platforms are integrated with Cisco Identity Services Engine
(ISE), employees have the ability to report a device as lost or stolen, initiate a personal identification number (PIN) lock, or initiate a full or corporate wipe. A corporate wipe, which is also known as a selective wipe, removes only corporate data and applications from the device. A full wipe, which is also known as a factory reset, removes all data from the device. An employee is also capable of reinstating a device to gain access without having to reregister the device with ISE. Each of these options is available to the employee by using ISE’s My Devices portal.
ISE is a next generation Authentication, Authorization, and Accounting (AAA) platform with integrated
posture assessment, network access control, and client provisioning. ISE integrates with a number of MDM frameworks, such as MobileIron and AirWatch. From ISE, you can easily provision network devices with native supplicants available for Microsoft Windows, Mac OS X, Apple iOS, and Google Android. The supplicants act as agents that enable you to perform various functions on the network device, such as installing software or locking the screen with a PIN lock.
Only ISE administrators can quarantine a device and revoke the device’s digital certificate. However, administrators are also capable of performing wipes and PIN locks without user notification or intervention. Unlike employees, who initiate full wipes or corporate wipes by using the My Devices portal, an administrator initiates a wipe or a PIN lock by using the ISE Endpoints screen. Whether an administrator can initiate a full wipe or a corporate wipe depends on the MDM server policies and configuration. In a Bring Your Own Device (BYOD) environment, administrators will most likely be able to perform only a corporate wipe or a PIN lock on a device. If the device is a corporate device that an employee is simply allowed to use, an administrator might be able to perform a full wipe from the Endpoints screen by selecting Full Wipe from the MDM Access dropdown menu. Administrators can additionally force connected devices off the network, add devices to the Blacklist Identity Group, and disable the device’s RSA SecurID token. -
Which of the following private VLAN port types communicate only with promiscuous ports? (Select the best answer.)
- community ports
- isolated ports
- SPAN ports
- promiscuous ports
Explanation:
Isolated private virtual LAN (VLAN) ports can communicate only with promiscuous ports. Private VLANs can be configured on a switch to help isolate traffic within a VLAN. Private VLANs can provide Layer 2 separation between ports that belong to the same VLAN. Because the separation exists at Layer 2, the hosts can exist on the same IP subnet. The VLAN to which the hosts belong is called the primary VLAN. To create a private VLAN, you must create secondary VLANs and associate them with the primary VLAN.
Community private VLAN ports can communicate with promiscuous ports and with other ports that belong to the same community. However, they cannot communicate with isolated ports or with ports that belong to other communities. Promiscuous ports can communicate with all other private VLAN port types.
Switch Port Analyzer (SPAN) ports are not a private VLAN port type. SPAN is a means of monitoring traffic on a switch by copying packets from a source port to a monitored port or mirrored port. -
On which of the following layers of the hierarchical network design model should you implement PortFast, BPDU guard, and root guard? (Select the best answer.)
- only on core layer ports
- only on distribution layer ports
- only on access layer ports
- only on core and distribution layer ports
- on core, distribution, and access layer ports
Explanation:
You should implement PortFast, BPDU guard, and root guard only on access layer ports. PortFast, BPDU guard, and root guard are enhancements to Spanning Tree Protocol (STP). The access layer is the network hierarchical layer where enduser devices connect to the network. The distribution layer is used to connect the devices at the access layer to those in the core layer. The core layer, which is also referred to as the backbone, is used to provide connectivity to devices connected through the distribution layer.
PortFast reduces convergence time by immediately placing user access ports into a forwarding state.
PortFast is recommended only for ports that connect to enduser devices, such as desktop computers. Therefore, you would not enable PortFast on ports that connect to other switches, including distribution layer ports and core layer ports. To enable PortFast, issue the spanningtree portfast command from interface configuration mode.
BPDU guard disables ports that erroneously receive bridge protocol data units (BPDUs). User access ports should never receive BPDUs, because user access ports should be connected only to enduser devices, not to other switches. When BPDU guard is applied, the receipt of a BPDU on a port with BPDU guard enabled will result in the port being placed into a disabled state, which prevents loops from occurring. To enable BPDU guard, issue the spanningtree bpduguard enable command from interface configuration mode.
Root guard is used to prevent newly introduced switches from being elected as the root. The device with the lowest bridge priority is elected the root. If an additional device is added to the network with a lower priority than the current root, it will become the new root. However, this could cause the network to reconfigure in unintended ways, particularly if an access layer switch were to become the root. To prevent this, root guard can be applied to ports that connect to other switches in order to maintain control over which switch is the root. Root guard is applied on a perport basis with the spanningtree guard root command. -
Which of the following is the man-in-the-middle attack that is most likely to be used to cause a workstation to send traffic to a false gateway IP address? (Select the best answer.)
- ARP spoofing
- DHCP spoofing
- MAC spoofing
- switch spoofing
Explanation:
Dynamic Host Configuration Protocol (DHCP) spoofing is the maninthemiddle attack that is most likely to be used to cause a workstation to send traffic to a false gateway IP address. In a DHCP spoofing attack, a rogue DHCP server is attached to the network in an attempt to intercept DHCP requests. The rogue DHCP server can then respond to the DHCP requests with its own IP address as the default gateway address so that all traffic is routed through the rogue DHCP server. DHCP snooping is a security technique that can be used to mitigate DHCP spoofing.
In an Address Resolution Protocol (ARP) poisoning attack, which is also known as an ARP spoofing attack, the attacker sends a gratuitous ARP (GARP) message to a host. The GARP message associates the attacker’s Media Access Control (MAC) address with the IP address of a valid host on the network. Subsequently, traffic sent to the valid host address will go to the attacker’s computer rather than to the intended recipient.
MAC spoofing makes network traffic from a device look as if it is coming from a different device. MAC spoofing is often implemented to bypass port security by making a device appear as if it were an authorized device. Malicious users can also use MAC spoofing to intercept network traffic that should be destined for a different device. ARP cache poisoning, content addressable memory (CAM) table flooding, and Denial of Service (DoS) attacks can all be performed by MAC spoofing.
Switch spoofing is a virtual LAN (VLAN) hopping attack that is characterized by using Dynamic Trunking Protocol (DTP) to negotiate a trunk link with a switch port in order to capture all traffic that is allowed on the trunk. In a switch spoofing attack, the attacking system is configured to act like a switch with a trunk port. This enables the attacking system to become a member of all VLANs, which enables the attacker to send and receive traffic among the other VLANs. -
On a Cisco ASA, which of the following RADIUS authentication protocols are not supported? (Select 2 choices.)
- CHAP
- EAPMD5
- PAP
- PEAP
- MSCHAPv1F. MSCHAPv2
Explanation:
Neither Extensible Authentication Protocol (EAP)Message Digest 5 (MD5) nor Protected EAP (PEAP) are supported by the Remote Authentication DialIn User Service (RADIUS) server on a Cisco Adaptive Security Appliance (ASA). RADIUS is an Authentication, Authorization, and Accounting (AAA) server that uses User Datagram Protocol (UDP) for packet delivery.
RADIUS and Terminal Access Controller Access Control System Plus (TACACS+) server groups on a
Cisco ASA support Challenge Handshake Authentication Protocol (CHAP), Microsoft CHAP version 1 (MSCHAPv1), and Password Authentication Protocol (PAP). A Cisco ASA supports a number of different AAA server types, such as RADIUS, TACACS+, Lightweight Directory Access Protocol (LDAP), Kerberos, and RSA Security Dynamics, Inc. (SDI) servers.
When authenticating with a TACACS+ server, a Cisco ASA can use the following authentication protocols:
– ASCII
– PAP
– CHAP
– MSCHAPv1
When authenticating with a RADIUS server, a Cisco ASA can use the following authentication protocols:
– PAP
– CHAP
– MSCHAPv1
– MSCHAP version 2 (MSCHAPv2)
– Authentication Proxy Mode (for example, RADIUS to RSA/SDI, RADIUS to Active Directory, and others) -
Which of the following is the best reason to enforce blacklisting by security zone on a Cisco device that uses the Security Intelligence IP Address Reputation feature? (Select the best answer.)
- to streamline performance of the IPS device
- to ensure that local hosts can communicate with a given IP address
- to validate a blacklist feed that has been obtained from a third party
- to manually control which networks are blocked by the IPS
Explanation:
Most likely, you would enforce blacklisting by security zone to streamline performance of the intrusion prevention system (IPS) device. Enforcing blacklisting by security zone can be used to enhance the performance of a Security Intelligence device by limiting the blacklisting to the specific security zones that process the given traffic. For example, the blacklisting of IP addresses that send email traffic could be restricted to a Security Zone that handles only email traffic.
You would configure the monitoronly setting if you wanted to validate a blacklist feed that has been obtained from a third party. Security Intelligence devices, such as a Cisco Sourcefire IPS, are capable of accepting manually imported lists of network addresses or feeds from third parties. Such devices can block IP addresses or networks based on their reputation, which mitigates device overhead that comes from having to analyze traffic from those networks. The monitoronly setting enables traffic from networks that are listed within a given feed to be analyzed by the Security Intelligence device, but also logs the fact that the given network matches the thirdparty feed. This enables an administrator to review the logs and the analysis of traffic from networks on the feed to determine the validity of the feed.
You would add IP addresses to a custom whitelist to ensure that local hosts can communicate with a given IP address. On Security Intelligence devices, whitelists can be used to override blacklisted IP addresses. Whitelists can thus be used to enable communication with legitimate IP addresses that are listed on thirdparty feeds or other blacklists that might be too broadly defined. From an administrative overhead standpoint, you should first validate the feed, then implement the feed, and finally add IP addresses or networks to the whitelist as necessary.
You would configure a custom blacklist to manually control which networks are blocked by the IPS. Security Intelligence devices allow the creation of custom blacklists so that you can manually block specific IP addresses or networks. -
Which of the following is not true of SIM systems? (Select the best answer.)
- They perform realtime threat detection.
- They focus on policy and standards compliance.
- They consolidate logs to a central server.
- They analyze log data and report findings.
Explanation:
Security Information Management (SIM) systems do not perform realtime analysis and detection. SIM systems are focused more on the collection and analysis of logs in a nonrealtime fashion. For example, a SIM system might centralize logging on a single device for review and analysis. Some SIM systems also provide assessment tools that can flag potentially threatening events.
Security Event Management (SEM) systems perform realtime analysis and detection. SEM systems typically analyze log data from a number of sources. Some systems also incorporate incident handling tools that enable administrators to more effectively mitigate threats when they occur.
A Security Information and Event Management (SIEM) system combines both the realtime aspects of a SEM system and the indepth analysis and timeline generation of a SIM system. Therefore, a SIEM system is a hybrid of a SIM system and a SEM system. -
In the Cisco ISE GUI, you click Administration > Certificates > Certificate Store and notice that a SCEP NDES server RA certificate is installed on the ISE node.
Which of the following best describes the reason the certificate is there? (Select the best answer.)
- The ISE is a SCEP proxy for a Windows CA.
- The ISE is a CA for the Windows AD domain.
- The ISE has been compromised, and the CA chain has been altered.
- The ISE requires the CA in order to mitigate a Windows Server SCEP bug.
Explanation:
The Cisco Identity Services Engine (ISE) is a Simple Certificate Enrollment Protocol (SCEP) proxy for a Windows certificate authority (CA) if you notice that a SCEP Network Device Enrollment Service (NDES) server registration authority (RA) certificate is installed in the ISE’s Certificate Store. Implementing ISE as a SCEP proxy enables bring your own device (BYOD) users to register their devices on their own, without administrative overhead from the IT department.
The ISE is not a CA for the Windows Active Directory (AD) domain. When configured with a SCEP CA profile, the ISE will contain a SCEP NDES server RA certificate in the Certificate Store. RAs verify requests for certificates and enable the CA to issue them.
The ISE does not require the CA in order to mitigate a Windows Server SCEP bug. However, configuring ISE as a SCEP proxy to a Microsoft Windows 2008 R2 Server does require the installation of some Microsoft SCEP implementation hotfixes.
There is nothing in this scenario to indicate that the ISE has been compromised. In addition, there is no reason to suspect that the CA chain has been altered. -
You issue the following commands on a Cisco router:
tacacsserver host ts1 timeout 30 tacacsserver timeout 20
Which of the following is true about how the Cisco router communicates with the TACACS+ server? (Select the best answer.)
- The router will maintain an open TCP connection.
- The router will maintain an open TCP connection for no more than 20 seconds.
- The router will wait 20 seconds for the server to reply before declaring an error.
- The router will wait 30 seconds for the server to reply before declaring an error.
Explanation:
The router will wait 30 seconds for the server to reply before declaring an error. The tacacsserver host ts1 timeout 30 command in this scenario configures a router to connect to a Terminal Access Controller Access Control System Plus (TACACS+) server named ts1. The timeout 30 keyword in this command configures the router to wait 30 seconds for the server to reply before declaring an error.
The router will wait 30 seconds, not 20 seconds, for the server to reply before declaring an error. If the timeout 30 keyword had not been specified in this scenario, the tacacsserver timeout 20 command would have configured the router to wait 20 seconds for the server to reply before declaring an error. The timeout 30 keyword in this scenario overrides the value assigned by the tacacsserver timeout command.
The router will not maintain an open Transmission Control Protocol (TCP) connection, because the singleconnection keyword has not been issued in this scenario. The singleconnection keyword configures the router to maintain an open connection to the TACACS+ server. When the singleconnection keyword is not configured, a Cisco router will open and close a TCP connection to the TACACS+ server each time it needs to perform an operation. When the singleconnection keyword is configured, the router connects to the TACACS+ server and maintains that connection even when it is not performing an operation. This setting enhances the efficiency of the communications between the router and the TACACS+ server because the router does not have to constantly close and open connections. -
You are configuring VPN access for Cisco AnyConnect clients. You finish the configuration by establishing a fail open policy.
Which of the following is true of AnyConnect clients that fail to establish a VPN session? (Select the best answer.)
- They are granted full access to the local network, but without security.
- They are granted full access to the local network, including security.
- They are denied full network access, except for local resources.
- They are denied full network access, including local resources.
Explanation:
Cisco AnyConnect clients that fail to establish a virtual private network (VPN) session under a fail open policy are granted full access to the local network, but without the security provided by the Cisco
AnyConnect VPN service. Connect failure policies are typically applied when the Cisco AnyConnect alwayson feature is configured. The alwayson feature enables Cisco AnyConnect clients to establish a VPN session automatically whenever the client detects that the host is connected to an untrusted network. For example, a laptop that is used both on a corporate LAN and for remote work might be configured to automatically connect to the corporate VPN whenever the laptop is not directly connected to the corporate LAN. However, any number of problems could prevent the client from actually establishing a connection to the VPN.
There are two types of connect failure policies that you can enable for Cisco AnyConnect alwayson clients. The fail open policy allows the client to complete a connection to the local network for access to the Internet or local resources. However, because a VPN session has not been established, the security of the AnyConnect device that is connected to the remote network could be compromised.
The fail closed policy, on the other hand, prevents all network access from the Cisco AnyConnect client except to local devices and devices that are available by using split tunneling. This extra layer of security could prevent the user from accessing the Internet and thus could compromise productivity if the user relies on Internet access to complete workrelated tasks. Because the fail closed policy is so restrictive, Cisco recommends implementing it by using a phased approach that includes initially implementing fail open and surveying user activity for AnyConnect issues that might prevent seamless connections.