300-735 : Automating Cisco Security Solutions (SAUTO) : Part 09
-
Which of the following web application threats is not typically mitigated by installing a WAF? (Select the best answer.)
- exploits related to uncloaked error messages
- exploits against known vulnerabilities
- exploits related to directory traversal vulnerabilities
- exploits against unknown vulnerabilities
- exploits related to viruses in file uploads
Explanation:
Of the available choices, exploits related to unknown vulnerabilities are not typically mitigated by installing a web application firewall (WAF). A WAF sits between a web application and the end user in order to protect the application from malicious activity and known vulnerabilities. Therefore, by installing a WAF, it is possible to protect a vulnerable web application without modifying the application code.
WAFs are not typically capable of protecting a web application against unknown vulnerabilities. WAFs can protect against known or common unpatched web application vulnerabilities by using techniques such as cloaking to protect against information leakage related to uncloaked error messages, encrypting Uniform Resource Locators (URLs) to protect against exploits related to directory traversal, and checking file uploads for viruses. -
Which of the following is a set of rules to which a Cisco IPS appliance can compare network traffic to determine whether an attack is occurring? (Select the best answer.)
- anomaly detection
- global correlation
- reputation filtering
- a signature definition
- a threat rating
Explanation:
A signature definition is a set of rules to which a Cisco Intrusion Prevention System (IPS) appliance can compare network traffic to determine whether an attack is occurring. If the network activity matches a signature definition, IPS can trigger a specific response from other defined event action rule sets, such as denying traffic from a host or alerting an administrator. IPS administrators can manually configure signature definitions in Cisco IPS Device Manager (IDM) or use the Signature Wizard to create custom signature definitions.
Global correlation is not a set of rules to which a Cisco IPS appliance can compare network traffic to determine whether an attack is occurring. Global correlation enables IPS sensors to allow or deny traffic based on the reputation of the sending device. When you enable global correlation, IPS devices will periodically receive updates that include information about known malicious devices on the Internet from the Cisco Sensor Base Network. In addition, global correlation will send statistical information about attacks against your company’s network to the Cisco Sensor Base Network. Cisco uses that information to detect threat patterns on the Internet.
Reputation filtering is not a set of rules to which a Cisco IPS appliance can compare network traffic to determine whether an attack is occurring. Reputation filtering denies packets from hosts that are considered to have a malicious reputation based on the global correlation information that is available from the Cisco Sensor Base Network. Reputation filtering is different from global correlation inspection in that reputation filtering denies traffic before the traffic is compared to any signature definitions. In addition, reputation filtering does not generate alerts.
Anomaly detection is not a set of rules to which a Cisco IPS appliance can compare network traffic to determine whether an attack is occurring. Anomaly detection enables IPS to learn what type of network activity is normal activity for the network that is being protected. If a network starts to become congested by traffic that is generated by a worm or if a host that is infected with a worm connects to the network and attempts to infect other hosts, the anomaly detection feature can trigger a specific response, such as denying traffic from the infected host or alerting an administrator.
A threat rating is not a set of rules to which a Cisco IPS appliance can compare network traffic to determine whether an attack is occurring. A threat rating is an event action risk rating that has been lowered because of a specific action taken by IPS. A risk rating is a numerical representation of the risk presented to a network by a specific attack. Risk ratings can range from 0 through 100. Depending on the actions IPS has taken in response to an event, IPS will subtract a value from the threat rating of the event. For example, if IPS responds to a specific event by issuing a request to block the attacking host, a value of 20 will be subtracted from the threat rating. -
Which of the following describes the primary difference between PGP and S/MIME? (Select the best answer.)
- PGP can be used to encrypt disk drives, but S/MIME cannot.
- PGP can use SHA1 for data integrity, but S/MIME cannot.
- S/MIME can be used to encrypt email messages, but PGP cannot.
- S/MIME can use RSA for digital signatures, but PGP cannot.
Explanation:
The primary difference between Pretty Good Privacy (PGP) and Secure/Multipurpose Internet Mail Extensions (S/MIME) is that PGP can be used to encrypt not only email messages, but also files and entire disk drives. PGP is software that uses an asymmetric encryption method to encrypt information. To encrypt a file or a message by using PGP, you must use the recipient’s public key. The recipient will then use his or her private key to decrypt the file or message.
Although PGP is an application and S/MIME is a standardsbased protocol, both can be used to provide confidentiality, integrity, and nonrepudiation for email messages. Confidentiality is provided by an encryption method, such as Triple Data Encryption Standard (3DES or TDES). Integrity is provided by a hashing algorithm, such as Secure Hash Algorithm 1 (SHA1). Nonrepudiation is provided by creating digital signatures with an asymmetric encryption method, such as RSA.
Many modern operating systems (OSs) offer their own builtin support for filelevel and disklevel encryption. Therefore, thirdparty software is often no longer necessary for encrypting files. -
Which of the following failover link configurations can leave an ASA vulnerable to replay attacks? (Select the best answer.)
- connecting the active and standby units directly with a crossover cable
- connecting the active and standby units to a dedicated VLAN on a switch
- sharing a regular data interface with the stateful failover link
- sharing the LAN failover link with the stateful failover link
- using a dedicated Ethernet interface as the stateful failover link
Explanation:
Sharing a regular data interface with the stateful failover link on a Cisco Adaptive Security Appliance (ASA) can leave the ASA vulnerable to replay attacks. A replay attack is a type of maninthemiddle attack in which the attacker uses a packet sniffer to capture legitimate network data, such as authentication tokens and preshared keys, and then replays the data to a target. In addition, the attacker might delay or modify the captured data before directing it to the target. On an ASA, all LAN failover and stateful failover information is transmitted as clear text by default. Therefore, sharing the stateful failover link with a regular data interface can unnecessarily expose virtual private network (VPN) configuration information, such as user names, passwords, and preshared keys (PSKs) to malicious users on the shared network segment. You can mitigate this risk by configuring a failover key on both the active unit and the standby unit to protect failover information. Cisco strongly recommends using a dedicated Ethernet interface or sharing a LAN failover link instead of sharing the stateful failover link with a regular data interface.
ASAs can be configured to participate in either a stateless or a stateful failover implementation. In a stateless failover implementation, the active unit and standby unit use a dedicated LAN link, known as a LAN failover link, for failover traffic. The LAN failover link can use any unnamed Ethernet interface and can connect the failover pair directly, with either a straightthrough or crossover Ethernet cable, or through a switch, with no other devices on the same network segment or virtual LAN (VLAN) as the failover pair. Although all failover traffic is sent as clear text by default, a LAN failover link does not leave an ASA vulnerable to replay attacks because the failover pair are either directly connected or connected through a dedicated VLAN.
By contrast, the failover link between two ASAs in a stateful failover implementation can use a dedicated Ethernet link, a shared LAN failover link, or a shared regular data interface. If a dedicated Ethernet link is used for stateful failover, it must follow the same connectivity guidelines as a LAN failover link: it can be either a direct connection or a dedicated VLAN on a switch. Like a LAN failover link, a stateful failover link using either a dedicated Ethernet link or a shared LAN failover link does not leave an ASA vulnerable to replay attacks because the failover pair are either directly connected or connected through a dedicated VLAN. -
Which of the following fields make up the header of an ESP packet? (Select 2 choices.)
- Next Header
- Pad Length
- Padding
- Security Parameter Index
- Sequence Number
Explanation:
The Security Parameter Index (SPI) and Sequence Number fields make up the header of an Encapsulating Security Payload (ESP) packet. ESP is an IP Security (IPSec) protocol that provides data integrity and confidentiality for IP traffic. The ESP header is always part of the authenticated data in an ESP packet, but the ESP header itself is never encrypted. By contrast, the ESP trailer, which is made up of the Padding, Pad Length, and Next Header fields, is always part of the authenticated data and is always encrypted. The following diagram illustrates the ESP packet format:
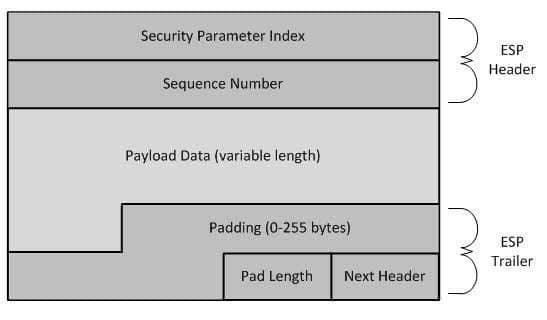
300-735 Part 09 Q05 082 ESP can operate in transport mode or tunnel mode. In transport mode, ESP encrypts only the original payload data and the resultant ESP trailer, leaving the original IP header unencrypted. The following diagram illustrates the components of an ESP packet in transport mode:

300-735 Part 09 Q05 083 In tunnel mode, ESP encrypts the entire packet, including the original IP header, the original payload data, and the resultant ESP trailer. The following diagram illustrates the components of an ESP packet in tunnel mode:
-
You want to use the authentication event noresponse action authorize vlan 101 command to ensure that network devices incapable of using 802.1X authentication are automatically placed into VLAN 101, which is the guest VLAN.
Which of the following VLAN types can you specify as an 802.1X guest VLAN? (Select the best answer.)
- a primary private VLAN
- a secondary private VLAN
- a voice VLAN
- an RSPAN VLAN
Explanation:
Of the choices available, you can configure a secondary private virtual LAN (VLAN) as an 802.1X guest VLAN with the authentication event noresponse action authorize vlan 101 command. The authentication event noresponse action authorize vlancommand specifies the VLAN into which a switch should place a port if it does not receive a response to the 802.1X Extensible Authentication Protocol over LAN (EAPoL) messages it sends on that port. The VLAN ID must be a number from 1 through 4094. The VLAN ID can specify any active VLAN except for a Remote Switch Port Analyzer (RSPAN) VLAN, a primary private VLAN, or a voice VLAN. In addition, a guest VLAN can be configured on only access ports, not on routed ports or trunk ports.
When a guest VLAN is configured, the switch will grant non802.1Xcapable clients access to the guest VLAN? however, if an 802.1Xcapable device is detected, the switch will place the port into an unauthorized state and will deny access to all devices on the port. You can use the authentication event fail action command to specify how the switch should react if an 802.1X client is detected and the client fails to authenticate. There are two configurable parameters: nextmethod and authorize vlanid. The authorize vlanid parameter configures a restricted VLAN, which is functionally similar to the guest VLAN. The nextmethod parameter configures the switch to attempt authentication by using the next authentication method specified in the authentication order command. For example, if the authentication order 802.1X mab webauth command has been configured and 802.1X authentication fails, the switch will attempt to use Media Access Control (MAC) Authentication Bypass (MAB) to authenticate the client based on its MAC address? if MAB fails, the switch will attempt webbased authentication. If the nextmethod parameter is configured, the switch will indefinitely cycle through authentication methods unless Web Authentication (WebAuth) is configured. If WebAuth is configured, the authentication process will not loop back to other authentication methods and the switch will ignore EAPoL messages on the port. -
Which of the following statements is true about network traffic event logging in Cisco FireSIGHT Management Center? (Select the best answer.)
- Beginningofconnection events contain less information than endofconnection events.
- Performance is optimized by logging both beginningofconnection events and end ofconnection events.
- You can log only beginningofconnection events for encrypted connections handled by an SSL policy.
- You can log only endofconnection events for blocked traffic.
Explanation:
In Cisco FireSIGHT Management Center, beginningofconnection events contain less information than endofconnection events. Cisco FireSIGHT Management Center, which was formerly called Sourcefire Defense Center, can log beginningofconnection and endofconnection events for various types of network traffic.
Although most network traffic will generate both kinds of events, blocked or blacklisted traffic is typically denied without further processing and therefore only generates beginningofconnection events. Beginningofconnection events contain a limited amount of information because they are generated based on the information contained in the first few packets of a connection.
By contrast, endofconnection events are generated when a connection closes, times out, or can no longer be tracked because of memory constraints. Endofconnection events contain significantly more information than beginningofconnection events because they can draw upon data collected throughout the course of a connection. This additional information can be used to create traffic profiles, generate connection summaries, or graphically represent connection data. In addition, the data can be used for detailed analysis or to trigger correlation rules based on session data. Endofconnection events are also required to log encrypted connections that are handled by a Secure Sockets Layer (SSL) policy because there is not enough information in the first few packets to indicate that a connection is encrypted. -
Which of the following are asymmetric algorithms? (Select 3 choices.)
- DH
- AES
- 3DES
- ECC
- RC4
- RSA
Explanation:
DiffieHellman (DH), Elliptical Curve Cryptography (ECC), and RSA are asymmetric algorithms. DH is an asymmetric key exchange method. DHA and ECC are asymmetric encryption algorithms. Asymmetric encryption, also known as public key encryption, uses a public key to encrypt data and a different, yet mathematically related, private key to decrypt data. Public key infrastructure (PKI) uses a certificate authority (CA) to tie a public key to a user ID to further ensure the confidentiality of data. Asymmetric encryption algorithms use more complex mathematical functions than symmetric encryption algorithms. As a result, asymmetric encryption algorithms take longer to encrypt and decrypt data than symmetric encryption algorithms. Other examples of asymmetric encryption algorithms include Digital Signature Algorithm (DSA) and ElGamal.
Advanced Encryption Standard (AES), RC4, and Triple Data Encryption Standard (3DES) are examples of symmetric encryption algorithms. When symmetric encryption algorithms are used, the same encryption key is used to encrypt and decrypt data. Two types of symmetric algorithms exist: block ciphers and stream ciphers. Block ciphers derive their name from the fact that they encrypt blocks of data. For example, AES encrypts 128bit blocks of data. By contrast, stream ciphers are typically faster than block ciphers because stream ciphers encrypt text of variable length depending on the size of the frame to be encrypted? stream ciphers are not limited to specific block sizes. For example, RC4, a stream cipher, can encrypt data in streams of 8 through 2,048 bits. Other examples of symmetric encryption algorithms include International Data Encryption Algorithm (IDEA), Skipjack, and Blowfish. -
Which of the following statements are true regarding class maps on a Cisco ASA? (Select 2 choices.)
- QoS traffic shaping is not available for all class maps.
- Class maps apply specific security measures on a persession basis.
- By default, no class maps are defined on an ASA.
- Class maps must use an ACL to match traffic.
- Class maps can match traffic based on application protocols.
- Class maps identify the interface to which a policy map is applied.
Explanation:
Class maps can match traffic based on application protocols, and Quality of Service (QoS) traffic shaping is not available for all class maps on a Cisco Adaptive Security Appliance (ASA). A class map is one of the three basic components of Modular Policy Framework (MPF)? policy maps and service policies are the other two components. MPF is a Cisco ASA feature that provides a flexible method of enabling security policies on an interface. A class map identifies a specific flow of traffic, a policy map determines the action that will be performed on the traffic, and a service policy ties this action to a specific interface. Generally, each class map can contain only a single match statement, and a packet can match only a single class map within the policy map of a particular feature type. For example, if a packet matched a class map for File Transfer Protocol (FTP) inspection and a class map for traffic policing, the ASA would apply both policy map actions to the packet. However, if a packet matched a class map for FTP inspection and a second, different class map that included FTP inspection, the ASA would apply only the actions of the first matching policy map. By default, two class maps are defined on an ASA? the classdefault and inspection_default class maps are part of the default configuration of an ASA.
You can use the match command from class map configuration mode to identify traffic based on specified
characteristics. The keywords you can use to identify traffic in a class map are closely tied to their respective characteristics. The match command supports the following key words: accesslist, port, defaultinspectiontraffic, dscp, precedence, rtp, tunnelgroup, and any.
For example, you could issue the following commands to create a class map named CLASSMAP that identifies traffic using Transmission Control Protocol (TCP) port 8080:asa(config)#classmap CLASSMAP asa(configcmap)#match port tcp eq 8080
Once traffic has been identified by a class map, the associated policy map can take action on that traffic. A policy map typically contains references to one or more class maps and defines actions that should be performed on traffic matched by the specified class maps. If traffic matches multiple class maps for different actions within a policy map-for instance, if traffic matches a class map for application inspection as well as a class map for priority queuing-the actions of both class maps will be applied to the traffic. To continue the example from above, you could issue the following commands to configure a policy map named POLICYMAP that matches traffic specified by the class map named CLASSMAP and then processes the traffic with the Hypertext Transfer Protocol (HTTP) inspection engine:
asa(config)#policymap POLICYMAP asa(configpmap)#class CLASSMAP asa(configpmapc)#inspect http
A policy map does not act on traffic until the map has been applied to an interface by a service policy. A service policy identifies the interface to which a policy map is applied? a service policy can be applied globally to all interfaces, which will apply application inspection to only traffic entering the appliance. Alternatively, a service policy can be applied to a single interface, which will apply application inspection to traffic entering and exiting the interface. An interface service policy overrides a global service policy: if traffic matches both an interface policy and a global policy, only the interface policy will be applied to that particular traffic flow. To complete the example, you could issue the following commands to apply the POLICYMAP policy map to the inside interface:
asa(config)#servicepolicy POLICYMAP interface inside QoS traffic shaping is available for only the classdefault class map.
Class maps do not apply specific security measures on a persession basis? dynamic access policies (DAPs) can apply specific security measures on a persession basis. Configuring a DAP allows you to resolve complications presented by the frequently inconsistent nature of a virtual private network (VPN). For example, users might access your network from different remote locations, with each location having a different configuration, thus presenting a variety of security issues for each individual situation. With a DAP, you can apply specific security measures for each specific situation on a persession basis. Depending on the circumstances of the next connection from a remote location, a different DAP may be applied if the variables have changed.
-
Which of the following is true regarding the EAPFAST authentication process? (Select the best answer.)
- A digital certificate is required only on the client.
- A digital certificate is required only on the server.
- Digital certificates are required on both the client and the server.
- Digital certificates are not required on the client or the server.
Explanation:
Digital certificates are not required on the client or the server during the Extensible Authentication Protocol (EAP)Flexible Authentication via Secure Tunneling (FAST) authentication process? instead, EAPFAST uses Protected Access Credentials (PACs). EAPFAST is an authentication protocol that can be used for pointtopoint connections and for both wired and wireless links. The EAPFAST authentication process consists of three phases. The first phase, which is optional and is considered phase 0, consists of provisioning a client with a PAC, which is a digital credential that is used for authentication. A PAC can be manually configured on a client, in which case phase 0 is not required. The second phase, which is referred to as phase 1, involves creating a secure tunnel between the client and the server. The final phase, which is referred to as phase 2, involves authenticating the client. If the client is authenticated, the client will be able to access the network.
Other EAP methods exist that do rely on digital certificates for authentication. For example, EAPTransport Layer Security (TLS) requires both a client and a server digital certificate, whereas Protected EAP (PEAP) requires only servers to be configured with digital certificates. With PEAP, clients can use alternative authentication methods, such as onetime passwords (OTPs).
Similar to EAPFAST, Lightweight EAP (LEAP) does not require either the server or the client to be configured with a digital certificate. When LEAP is used, the client initiates an authentication attempt with a Remote Authentication DialIn User Service (RADIUS) server. The RADIUS server responds with a challenge response. If the challenge/response process is successful, the client then validates that the RADIUS server is correct for the network. If the RADIUS server is validated, the client will connect to the network. -
Which of the following security functions is associated with the data plane? (Select 2 choices.)
- device configuration protection
- signaling protection
- traffic conditioning
- traffic filtering
Explanation:
Traffic conditioning and traffic filtering are security features that are associated with the data plane. Cisco devices are generally divided into three planes: the control plane, the management plane, and the data plane. Each plane is responsible for different operations, and each plane can be secured by implementing various security methods.
The data plane is responsible for traffic passing through the router, which is referred to as transit traffic. Therefore, data plane security protects against unauthorized packet transmission and interception. Threats such as IP spoofing, Media Access Control (MAC) address spoofing, Address Resolution Protocol (ARP) spoofing, Dynamic Host Configuration Protocol (DHCP) spoofing, unauthorized traffic interception, and unauthorized network access can be mitigated and monitored by implementing features such as the following:
– ARP inspection
– Antispoofing access control lists (ACLs)
– DHCP snooping
– Port ACLs (PACLs)
– Private virtual LANs (VLANs)
– Unicast Reverse Path Forwarding (uRPF)
– VLAN ACLs (VACLs)The control plane is responsible for the creation and maintenance of structures related to routing and forwarding. These functions are heavily dependent on the CPU and memory availability. Therefore, control plane security methods protect against unauthorized traffic destined for the router, which can modify route paths and consume excessive resources. Path modification can be caused by manipulating the traffic generated by routing protocols, VLAN Trunking Protocol (VTP), and Spanning Tree Protocol (STP). Path modification attacks can be mitigated by implementing routing protocol authentication and filtering, VTP authentication, and STP protection features. In addition, excessive CPU and memory consumption can be caused by control plane flooding. Resource consumption attacks can be mitigated by implementing control plane filtering and rate limiting with Control Plane Policing (CoPP) and Control Plane Protection (CPPr).
Device configuration protection is associated with the management plane. Management plane security protects against unauthorized device access and configuration. Unauthorized access can be mitigated by implementing a strong Authentication, Authorization, and Accounting (AAA) solution and by implementing Management Plane Protection (MPP), which creates protected management channels over which administrators must connect in order to access device administration features. Management traffic can be encrypted by implementing Secure Shell (SSH). You can mitigate unauthorized configuration of a device by implementing RoleBased Access Control (RBAC), whereby administrators are limited to using only the features they need to accomplish their jobs. Detection and logging of management plane access can be performed by implementing Simple Network Management Protocol version 3 (SNMPv3) and Syslog servers. -
Which of following capabilities do an IDS and IPS have in common? (Select the best answer.)
- blocking a particular connection
- blocking traffic from a particular host
- modifying traffic
- resetting TCP connections
Explanation:
An Intrusion Detection System (IDS) and an Intrusion Prevention System (IPS) can both reset Transmission Control Protocol (TCP) connections. An IDS is a network monitoring device that passively monitors network traffic and actively sends alerts to a management station when it detects malicious traffic. An IDS typically has one promiscuous network interface attached to each monitored network. Because traffic does not flow through the IDS, the IDS is unable to directly block malicious traffic? however, an IDS can do any of the following:
– Request that another device block a connection
– Request that another device block a particular host
– Reset TCP connectionsAn IDS can prevent further instances of previously detected malicious traffic from passing onto the network by creating access control lists (ACLs) on routers in the traffic path or by configuring other security devices that reside in the flow of traffic.
By contrast, an IPS typically sits inline with the flow of traffic and can therefore block malicious traffic before it passes onto the network. An inline IPS can perform the following actions:
– Block traffic from a particular host
– Block a particular connection
– Modify traffic
– Reset TCP connectionsHowever, if an IPS sits inline with traffic, a failed IPS device can cause all traffic to be dropped. Analyzing all of the traffic that passes through the IPS can cause latency and jitter. Alternatively, an IPS can be configured to operate in promiscuous mode, which would make it functionally similar to an IDS.
-
Which of the following statements are true regarding RADIUS? (Select 2 choices.)
- It encrypts only the password in AccessRequest packets.
- It combines authorization and authentication functions.
- It provides more flexible security options than TACACS+.
- It uses TCP port 49.
- It is a Ciscoproprietary standard protocol.
Explanation:
Remote Authentication DialIn User Service (RADIUS) combines authentication and authorization into a single function and encrypts only the password in AccessRequest packets. RADIUS is an Internet Engineering Task Force (IETF) standard protocol for Authentication, Authorization, and Accounting (AAA) operations. RADIUS uses User Datagram Protocol (UDP) for packet delivery. Because RADIUS encrypts only the password of a packet, the rest of the packet would be viewable if the packet were intercepted by a malicious user. RADIUS has fewer flexible security options than Terminal Access Controller Access Control System Plus (TACACS+), because RADIUS combines the authentication and authorization functions of AAA into a single function and does not provide router command authorization capabilities.
By contrast, TACACS+ is a Ciscoproprietary protocol that uses Transmission Control Protocol (TCP) for transport during AAA operations. TACACS+ provides more security and flexibility than RADIUS because TACACS+ encrypts the entire body of a packet and separates the authentication, authorization, and accounting functions of AAA. This separation enables granular control of access to resources. For example, TACACS+ gives administrators control over access to configuration commands? users can be permitted or denied access to specific configuration commands. Because of this flexibility, TACACS+ is used with Cisco Secure Access Control Server (ACS), which is a software tool that is used to manage user authorization for router access. -
Which of the following protocols can IPSec use to provide the confidentiality component of the CIA triad? (Select 2 choices.)
- AES
- AH
- DES
- MD5
- SHA
Explanation:
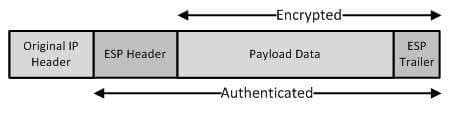
Of the choices available, IP Security (IPSec) can use either Advanced Encryption Standard (AES) or Data Encryption Standard (DES) to provide the confidentiality component of the confidentiality, integrity, and availability (CIA) triad. The confidentiality component of the CIA triad ensures that transmitted data cannot be read by an unauthorized party if the data is intercepted before it reaches its destination. Depending on the amount of confidentiality desired, IPSec can use AES or DES with Encapsulating Security Payload (ESP) in either transport mode or tunnel mode. In transport mode, ESP uses AES or DES to encrypt only the original payload data and the resultant ESP trailer, leaving the original IP header unencrypted. The following diagram illustrates the components of an ESP packet in transport mode:
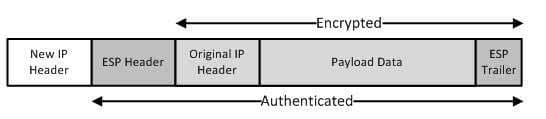
300-735 Part 09 Q14 085 In tunnel mode, ESP uses AES or DES to encrypt the entire packet, including the original IP header, the original payload data, and the resultant ESP trailer. The following diagram illustrates the components of an ESP packet in tunnel mode:
300-735 Part 09 Q14 086 IPSec can use Authentication Header (AH) and ESP to provide the integrity component of the CIA triad, not the confidentiality component. The integrity component of the CIA triad ensures that unauthorized parties have not modified data as it was transmitted over the network. Data integrity is provided by using algorithms such as Message Digest 5 (MD5) or Secure Hash Algorithm (SHA) to produce checksums on each end of the connection. If the data generates the same checksum value on each end of the connection, the data was not modified in transit. In addition, AH and ESP can authenticate the origin of transmitted data. Data authentication is provided through various methods, including user name/password combinations, preshared keys (PSKs), digital certificates, and onetime passwords (OTPs).
-
You issue the following commands on a Cisco ASA with no other configured interfaces:
asa(config)#interface gigabitethernet 0/1
asa(configif)#speed 1000 asa(configif)#duplex full asa(configif)#nameif inside asa(configif)#ip address 10.1.1.1 255.255.255.0 asa(configif)#no shutdown asa(configif)#exit asa(config)#telnet 10.1.1.0 255.255.255.0 inside asa(config)#telnet timeout 30
Which of the following statements is true regarding the resulting configuration? (Select the best answer.)
- Telnet sessions will time out after 30 seconds of inactivity.
- The ASA will assign the interface a security level of 0.
- The ASA will assign the interface a security level of 100.
- Telnet sessions will be denied until a security level is manually assigned.
Explanation:
In this scenario, the Cisco Adaptive Security Appliance (ASA) will assign the GigabitEthernet 0/1 interface a security level of 100. The block of commands in this scenario configures the GigabitEthernet 0/1 interface to operate in fullduplex mode at a speed of 1,000 megabits per second (Mbps), names the interface “inside”, and assigns an IP address 10.1.1.1 with a network mask of 255.255.255.0. In addition, the no shutdown command enables the interface. The telnet commands define a network range that is permitted to Telnet to the inside interface and configure a Telnet idletimeout value. Because no security level is manually assigned to the interface, the ASA will automatically assign the interface a security level. The default security level on an ASA is 0? however, the inside interface is an exception to this rule because it is automatically assigned a security level of 100 if a security level is not explicitly configured. An interface can be assigned any integervalued security level from 0 through 100.
Telnet sessions will not be denied to the GigabitEthernet 0/1 interface until a security level is manually assigned. Normally, Telnet traffic is not permitted to the interface with the lowest security. However, if there is only one configured interface and it has been configured with a security level of 100, Telnet traffic is permitted even though the interface simultaneously has the highest security and the lowest security. Because the ASA automatically assigns a security level of 100 to the inside interface, Telnet sessions will be able to access the interface. If there were other active interfaces on the ASA, a Telnet session would be permitted to the interface with the lowest security only if that session was protected by a virtual private network (VPN) tunnel terminating on the interface. Although there are several methods for working around Telnet access restrictions of the ASA, Cisco recommends disabling Telnet and using more secure methods for management access, such as Secure Shell (SSH) or Secure Hypertext Transfer Protocol (HTTPS) instead? neither HTTPS nor SSH is restricted by the security level of an interface.
Telnet sessions will not time out after 30 seconds of activity. The telnet timeout 30 command specifies an inactivity timeout length of 30 minutes, not 30 seconds. The telnet timeout command accepts an integer value from 1 through 1440 to specify the number of minutes a Telnet session can remain idle before the ASA closes the connection. -
Which of the following vulnerabilities did the Blaster worm exploit on target hosts? (Select the best answer.)
- a buffer overflow vulnerability in the DCOM RPC service
- a buffer overflow vulnerability in IIS software
- a buffer overflow vulnerability in Microsoft SQL Server
- a remote code execution vulnerability in the printer spooler service
- a remote code execution vulnerability in the processing of .lnk files
Explanation:
The Blaster worm exploited a buffer overflow vulnerability in the Distributed Component Object Model (DCOM) Remote Procedure Call (RPC) service on Microsoft Windows hosts. The worm carried a destructive payload that configured the target host to engage in Denial of Service (DoS) attacks on Microsoft update servers. Before Microsoft released a patch, several other worms exploited the vulnerability. For example, the Welchia worm targeted the same vulnerability. Welchia was developed to scan the network for vulnerable machines, infect them, and then remove the Blaster worm if present. It was even designed to download and install the appropriate patch from Microsoft to fix the vulnerability that it and Blaster initially exploited to infect the target machine. However, despite the goodnatured design intentions of the Welchia worm, its networkscanning component inadvertently caused DoS attacks on several large networks, including those of the United States armed forces.
Stuxnet is an example of a worm that exploited vulnerabilities in both the printer spooler service and the processing of .lnk files. Stuxnet was used in an act of cyber warfare against Iranian industrial control systems (ICSs). It was written to target specific ICSs by modifying code on programmable logic controllers (PLCs). Stuxnet initially exploited vulnerabilities in the printer spooler service? however, later variants exploited a vulnerability in the way that Windows processes shortcuts (.lnk files). Research from Symantec published in 2011 indicated that at the time, over 60% percent of the Stuxnetaffected hosts had been in Iran. Symantec analyzed Stuxnet and its variants and discovered that five organizations were the primary targets of infection and that further infections were likely collateral damage from the aggressive manner in which the worm spreads throughout the network. Given the considerable cost in resources and manhours that would have been required to craft the Stuxnet worm, it was theorized that it was likely intended to sabotage high value targets such as nuclear materials refinement facilities.
SQL Slammer is an example of a worm that exploited a buffer overflow vulnerability in Microsoft Structured Query Language (SQL) server software. SQL Slammer spread at a tremendous rate and was reported to have infected as many as 12,000 servers per minute. Its high scanning rate generated enough traffic on many networks to effectively produce DoS effects as collateral damage to the infection.
Code Red is an example of a worm that exploited a buffer overflow vulnerability in Microsoft Internet Information Server (IIS) software. Although not as efficient as SQL Slammer, Code Red still managed to infect as many as 2,000 hosts per minute. The initial Code Red variant failed to infect more than a single set of IP addresses? however, a later variant was reported to have affected over 350,000 hosts within the first 14 hours of its release into the wild. -
Which of the following statements is true regarding the primary bootset when the Cisco IOS Resilient Configuration feature is enabled? (Select the best answer.)
- The configuration file can be secured on a TFTP server, but the system image must be secured on local storage.
- The system image can be secured on a TFTP server, but the configuration file must be secured on local storage.
- The configuration file and the system image must both be secured on local storage.
- The configuration file and the system image must both be secured on remote storage.
Explanation:
The configuration file and the system image must both be secured on local storage when the Cisco IOS Resilient Configuration feature is enabled. The Resilient Configuration feature is designed to protect system and configuration files from tampering and accidental deletion. You can issue the following block of commands to enable the Resilient Configuration feature:Router#configure terminal Router(config)#secure bootimage Router(config)#secure bootconfig
When the feature is enabled, the primary system image file and associated running configuration are securely archived in local persistent storage? you cannot select a remote storage location. The secure bootimage command enables the image resilience component of the Resilient Configuration feature and effectively hides the system image from the directory structure. This means that the system image will no longer be displayed when the dir command is issued from the command prompt of an EXEC shell. In addition, because the system image file is not copied to a secure location, extra storage is not required to secure it. By contrast, the secure bootconfig command creates a hidden copy of the running configuration file. The secured versions of the system image and running configuration are referred to as the primary bootset.
You can restore either or both components of the primary bootset at any time. The system image can be restored from readonly memory (ROM) monitor (ROMmon) mode and the running configuration can be restored from the global configuration mode by using the restore parameter of the secure bootconfig command. Once the system image and running configuration have been secured, the router will track version mismatches and produce a console message if the system image or running configuration have mismatched versions. Once the Resilient Configuration feature is enabled, it can only be disabled from the console. -
Which of the following can be installed on a host to ensure that only specified inbound and outbound connections are permitted? (Select the best answer.)
- antivirus software
- a HIPS
- a personal firewall
- a proxy server
Explanation:
A personal firewall can be installed on a host to ensure that only specified inbound and outbound connections are permitted. A personal firewall can protect a host from malicious traffic by permitting or denying specific applications or network ports access to the host or its network interface. Typically, a personal firewall provides sufficient granularity to specify the direction of a particular flow of traffic. For example, you could permit outbound web traffic but deny inbound Internet Control Message Protocol (ICMP) messages.
A Hostbased Intrusion Prevention System (HIPS) can be installed on a host to analyze and prevent malicious traffic on that host. An Intrusion Prevention System (IPS) can be used to actively monitor, analyze, and block malicious traffic before it infects devices. HIPS software can be installed on a host computer to protect that computer against malicious traffic. By contrast, a Networkbased IPS (NIPS) is an independent operating platform, often a standalone appliance or a hardware module installed in a chassis. A NIPS device can be installed inline on a network to monitor and prevent malicious traffic from being sent to other devices on the network. One advantage of using a NIPS over a HIPS is that a NIPS can detect lowlevel network events, such as the scanning of random hosts on the network? a HIPS can only detect scans for which it is the target. HIPS and a NIPS can be used together to provide an additional layer of protection.
You could not install antivirus software to ensure that only specified inbound and outbound connections are permitted. Antivirus software monitors the file system and memory space on a host for malicious code. Although the antivirus software might protect the host from malicious file execution, it would be unable to protect the host from malicious traffic. Some antivirus vendors offer integrated security suites, which feature personal firewall, HIPS, antivirus, and antimalware components.
You could not install a proxy server on a host to ensure that only specified inbound and outbound connections are permitted. A proxy server is typically an application layer gateway that provides resource caching and traffic filtering for a particular class of traffic, such as web content. Although you could install a proxy server locally on a host and use it to process specified outbound connections, it would not be able to restrict outbound connections that were not configured to use the proxy nor would it be able to restrict inbound connections. -
Which of the following statements are true regarding the FirePOWER inline normalization preprocessor engine? (Select 2 choices.)
- Inline normalization can process IPv4 and ICMPv4 traffic but not IPv6 traffic.
- Inline normalization can process IPv4 and IPv6 traffic but not ICMPv4 traffic.
- Inline normalization cannot detect TCP SYN flood attacks.
- Inline normalization cannot detect TCP session hijacking attacks.
- Inline normalization takes place immediately before decoding by the packet decoder.
Explanation:
The FirePOWER inline normalization preprocessor engine cannot detect Transmission Control Protocol (TCP) SYN flood attacks or session hijacking attacks. The inline normalization preprocessor can be used by a FirePOWER Intrusion Prevention System (IPS) that is deployed in an inline configuration. Packet normalization can reduce the chances of malicious traffic evading detection. The inline normalization process takes place immediately after the IPS packet decoder decodes the packet, which ensures that packets being analyzed by the IPS are identical to the packets that will be assembled by the target host. The inline normalization preprocessor can perform normalizations on various components of Internet Control Message Protocol version 4 (ICMPv4), IP version 4 (IPv4), IPv6, and TCP packets. For example, it can reset the timetolive (TTL) value on a packet if it detects a TTL value outside of a userdefined range.
The FirePOWER ratebased prevention preprocessor engine, not the inline normalization detection preprocessor engine, can detect SYN flood traffic. The ratebased prevention preprocessor engine detects traffic abnormalities based on the frequency of certain types of traffic. The following traffic patterns can trigger ratebased attack prevention:
– Traffic containing excessive incomplete TCP connections
– Traffic containing excessive complete TCP connections
– Excessive rule matches for a particular IP address or range of IP addresses
– Excessive rule matches for one particular rule regardless of IP addressThe FirePOWER TCP stream preprocessor engine, not the inline normalization detection preprocessor, can detect session hijacking attacks. The stream preprocessor assembles the packets of a TCP data stream into a single comprehensive unit for scanning. Because the TCP stream preprocessor has access to multiple packets in a data stream, it can analyze state information, analyze payload anomalies, and identify streambased attacks that are not possible to identify based on singlepacket analysis.
-
What is the effect of the samesecuritytraffic permit intrainterface command on a Cisco ASA? (Select the best answer.)
- It allows communication between different interfaces that share the same security level.
- It allows traffic to exit the same interface through which it entered.
- It allows outbound traffic and the corresponding return traffic to pass through different ASAs.
- It allows traffic destined to unprotected subnets to bypass a VPN tunnel.
Explanation:
On a Cisco Adaptive Security Appliance (ASA), the samesecuritytraffic permit intrainterface command allows traffic to exit the same interface through which it entered, which is also known as hairpinning. By default, an ASA does not allow packets to enter and exit through the same physical interface. However, because multiple logical virtual LANs (VLANs) can be assigned to the same physical interface, it is sometimes necessary to allow a packet to enter and exit through the same interface. The samesecuritytraffic permit intrainterface command allows packets to be sent and received from the same interface even if the traffic is protected by IP Security (IPSec) security policies. Another scenario for which you would need to use the samesecuritytraffic permit intrainterface command is if multiple users need to connect via virtual private network (VPN) through the same physical interface. These users will not be able communicate with one another unless the samesecuritytraffic permit intrainterface command has been issued from global configuration mode.
The samesecuritytraffic permit interinterface command, not the samesecuritytraffic permit intrainterface command, allows communication between different interfaces that share the same security level. By default, interfaces with the same security level are not allowed to communicate with each other.
A split tunneling policy, not the samesecuritytraffic permit intrainterfacecommand, allows traffic destined to unprotected subnets to bypass an encrypted tunnel. With split tunneling, only traffic destined to protected subnets is routed through the appropriate VPN tunnel. Traffic destined to unprotected subnets, such as the Internet, can bypass the tunnel and be routed normally. You can issue the splittunnelpolicy and splittunnelnetworklist commands to configure a split tunneling policy.
Transmission Control Protocol (TCP) bypass, not the samesecuritytraffic permit intrainterface command, allows outbound traffic and the corresponding return traffic to pass through different ASAs. With TCP state bypass, an ASA will allow a specific class of traffic to pass through the ASA without the traffic class having an entry in the ASA’s state table. TCP state bypass is disabled by default. You can issue the set connection advancedoptions tcpstatebypass command to enable the TCP state bypass feature.