300-735 : Automating Cisco Security Solutions (SAUTO) : Part 10
-
Which of the following statements is not true regarding an IPS device? (Select the best answer.)
- An IPS requires that at least one interface be in promiscuous mode.
- Singlepacket attacks can be mitigated by an IPS.
- Traffic leaves an IPS on a different interface than it entered.
- An IPS cannot route to destinations on different subnets.
Explanation:
An Intrusion Prevention System (IPS) does not require that at least one interface be in promiscuous mode. An IPS sits inline with the flow of traffic, thus actively monitoring network traffic and blocking malicious traffic, such as an atomic or singlepacket attack, before it spreads onto the network. An IPS requires at least two interfaces for each monitored network: one interface listens to traffic entering the IPS, and the other listens to traffic leaving the IPS. In addition, an IPS acts similarly to a Layer 2 bridge in that it can pass traffic through to destinations on the same subnet? an IPS cannot route to destinations on a different subnet. Because all monitored traffic must pass through the IPS, it can add latency to traffic flows on the network.
By contrast, an Intrusion Detection System (IDS) typically has one promiscuous network interface attached to each monitored network, with no IP address assigned to the monitoring interface. An IDS is a network monitoring device that does not sit inline with the flow of network traffic? an IDS passively monitors a copy of network traffic, not the actual packet. Since an IDS analyzes a copy of network traffic, an IDS can support asymmetric traffic flows in which the original traffic may use a different return path than it used to arrive at its original destination. Because monitored traffic does not pass through an IDS, it does not add latency to the traffic flow. -
Which of the following statements is true regarding a split ACS deployment? (Select the best answer.)
- Cisco recommends using a dedicated log collector instead of the primary or secondary server.
- The split configuration has the drawback of making an administrator less aware of the functional status of each server.
- The AAA load is divided between the primary and secondary servers, which produces a lessthanoptimal AAA flow.
- The primary and secondary servers can be used for different, specialized operations such as network admission and device administration.
Explanation:
In a split Cisco Secure Access Control System (ACS) deployment, the primary and secondary servers can be used for different, specialized operations such as network admission and device administration. ACS is an Authentication, Authorization, and Accounting (AAA) server that uses Remote Authentication DialIn User Service (RADIUS) and Terminal Access Controller Access Control System Plus (TACACS+) to provide AAA services for users, hosts, and network infrastructure devices such as switches and routers. An ACS deployment typically consists of a cluster containing a primary server and one or more secondary servers. In a split ACS deployment, the AAA load is distributed between the primary and secondary server. This distribution provides a more optimal AAA flow than a traditional smallscale deployment in which the secondary server functions only as a backup if the primary server fails.
The split ACS deployment offers a few other advantages over a traditional smallscale deployment. For example, an administrator will be more aware of the status of the primary and secondary servers because they are both operational in a split ACS deployment. By contrast, in a traditional smallscale deployment, an administrator will be less aware of the status of the secondary server because it is not actively involved in the AAA process. In addition, because both servers are active, each server can be dedicated to a specialized operation. For example, the primary server could be dedicated to device administration operations and the secondary server could be dedicated to network admission operations. If either server fails, the remaining server could take over the full load of AAA operations until the failed server is restored. -
For which of the following traffic types is stateful inspection not supported in a ZFW configuration? (Select the best answer.)
- DNS
- ICMP
- IGMP
- NetBIOS
- Sun RPC
Explanation:
Stateful inspection of Internet Group Management Protocol (IGMP) is not supported in a zonebased policy firewall (ZFW) configuration. ZFW is the latest iteration of Cisco’s stateful firewall implementation, which was formerly called ContextBased Access Control (CBAC). With ZFW, virtual security zones are specified and then interfaces are assigned to the appropriate zone. By default, all traffic is implicitly permitted to flow between interfaces that have been assigned to the same zone? however, all traffic between zones is blocked. In addition, all traffic to and from an interface is implicitly blocked by default when the interface is assigned to a zone, but there are a few exceptions. Traffic to or from other interfaces in the same zone is permitted as is traffic to or from the router itself.
In order for traffic to flow between zones, stateful packet inspection policies must be configured to explicitly permit traffic between zones. The basic process is as follows:
1. Define the required zones.
2. Create zonepairs for zones that will pass traffic between themselves.
3. Define class maps to match the appropriate traffic for each zonepair.
4. Define policy maps to specify the actions that should be performed on matching traffic.
5. Apply the policy maps to the zonepairs.
6. Assign interfaces to their appropriate zones.Inspection rules can be created for a large number of traffic types, including the following:
– Domain Name System (DNS)
– Internet Control Message Protocol (ICMP)
– Network Basic Input/Output System (NetBIOS)
– Sun Remote Procedure Call (RPC)However, stateful inspection of multicast traffic, such as IGMP, is not supported by ZFW and must be handled by other security features, such as Control Plane Policing (CoPP).
-
Which of the following commands is not available to a user with a privilege level of 0? (Select the best answer.)
- disable
- enable
- exit
- login
- logout
Explanation:
The login command is not available to a user with a privilege level of 0. Privilege levels can be used to limit the IOS commands that a user can access. The disable, enable, exit, help, and logout commands are available to a user with a privilege level of 0. Because the default privilege level for a newly created local user account is 1, a newly created user will always have access to the basic commands necessary to escalate their privilege level or access the help system. You can assign a user one of 16 privilege levels, some of which are used by default by the IOS. For example, privilege levels 1 and 15 are default IOS privilege levels. Privilege level 1 allows a user to issue any command that is available at the user EXEC > prompt. Privilege level 15 allows a user to issue any command that is available at the privileged EXEC # prompt.
Each privilege level is associated with a list of commands that are available at that level. Users assigned to a privilege level have access to all of the commands at that privilege level and all lower privilege levels. Changing the commands that are available to a privilege level might provide access to a user who should not be allowed access to the command, or it might restrict access to another user who should be allowed access to the command. Peruser privilege levels can sometimes conflict with the privilege levels set for virtual terminal (VTY) interfaces. In the event of a conflict, peruser privileges override the privileges configured for the VTY line causing the conflict. -
Which of the following is most likely to cause the greatest amount of disruption on a router? (Select the best answer.)
- spyware
- a Trojan horse
- a worm
- a DDoS attack
Explanation:
Of the available choices, a Distributed Denial of Service (DDoS) attack is most likely to cause the greatest amount of disruption on a router. A DDoS attack is a coordinated Denial of Service (DoS) attack that uses multiple attackers to target a single host. For example, a large number of zombie hosts in a botnet could flood a target device with packets. Because the flood of packets originates from multiple hosts and typically targets public services, such as the web service, the target device might not detect the attack. If enough packets are sent to the target device within a short period of time, the target will be unable to respond to legitimate packets because it is waiting for a response to each of the requests originated by the attacker.
A Trojan horse does not cause the greatest amount of disruption on a router. A Trojan horse is a type of malicious software that appears to be legitimate software. Because a Trojan horse appears to be legitimate, users often load the Trojan horse unknowingly. The Trojan horse can then affect the computer in several ways. Some Trojan horses cause advertising popups to be displayed intermittently. Other Trojan horses can cause more harm by deleting or damaging data. Because a router runs only Ciscoproprietary software, there is little chance that a Trojan horse could inadvertently be installed.
Likewise, a worm does not cause the greatest amount of disruption on a router. A worm is a specific type of standalone, malicious software that has the ability to selfpropagate. A worm typically exploits vulnerabilities in an operating system (OS) to compromise a computer and to install copies of itself onto the infected device. Because a router runs only Ciscoproprietary software, there is little chance that a worm could exploit a vulnerability in its OS and infect the router. Although excessive network traffic caused by worm propagation could negatively affect the performance of a router, it is unlikely that this traffic would be comparable to the impact of a DDoS attack.
Spyware does not cause the greatest amount of disruption on a router. Spyware is a type of unwanted software that can record a user’s actions and personal information. Because a router runs only Ciscoproprietary software, there is little chance that spyware could inadvertently be installed. -
The following partial command output is from the running configuration of an ASA that has been configured to authorize VPN users based on their group membership in AD:
ldap attributemap ExampleMap mapname memberOf GroupPolicy mapvalue memberOf CN=Managers,CN=Users,OU=bsnsw,DC=boson,DC=com Group5 mapvalue memberOf CN=Marketing,CN=Users,OU=bsnsw,DC=boson,DC=com Group4 mapvalue memberOf CN=Employees,CN=Users,OU=bsnsw,DC=boson,DC=com Group3 mapvalue memberOf CN=Engineers,CN=Users,OU=bsnsw,DC=boson,DC=com Group2 mapvalue memberOf CN=Finance,CN=Users,OU=bsnsw,DC=boson,DC=com Group1An LDAP authorization query for a VPN user returns the following values:
memberOf: value = CN=Managers,CN=Users,OU=bsnsw,DC=boson,DC=com
memberOf: value = CN=Marketing,CN=Users,OU=bsnsw,DC=boson,DC=com
memberOf: value = CN=Employees,CN=Users,OU=bsnsw,DC=boson,DC=com
memberOf: value = CN=Finance,CN=Users,OU=bsnsw,DC=boson,DC=com
Which group policy will the ASA assign to the user in this scenario? (Select the best answer.)- Group1
- Group2
- Group3
- Group4
- Group5
Explanation:
In this scenario, the Cisco Adaptive Security Appliance (ASA) will assign the group policy named Group1 to the virtual private network (VPN) user. Lightweight Directory Access Protocol (LDAP) attribute maps are used to authorize VPN users based on specified Active Directory (AD) attributes, such as group membership or department name. The following sample output from the running configuration defines five group policy mappings:
ldap attributemap ExampleMap mapname memberOf GroupPolicy mapvalue memberOf CN=Managers,CN=Users,OU=bsnsw,DC=boson,DC=com Group5 mapvalue memberOf CN=Marketing,CN=Users,OU=bsnsw,DC=boson,DC=com Group4 mapvalue memberOf CN=Employees,CN=Users,OU=bsnsw,DC=boson,DC=com Group3 mapvalue memberOf CN=Engineers,CN=Users,OU=bsnsw,DC=boson,DC=com Group2 mapvalue memberOf CN=Finance,CN=Users,OU=bsnsw,DC=boson,DC=com Group1
The ldap attributemap ExampleMap command creates an LDAP attribute map named ExampleMap. The LDAP attribute map contains a mapname statement, which maps the AD memberOf attribute to the ASA GroupPolicy attribute, and a series of mapvaluecommands, which map matching LDAP response strings to ASA attributes. The mapvalue commands specify the mapping between AD group membership attributes in an LDAP response and the ASA group policy to which they should be applied. When the ASA receives a reply to an LDAP authorization query for the VPN user in this scenario, the following multiattribute response is compared to the mapvalue statements in the LDAP attribute map:memberOf: value = CN=Managers,CN=Users,OU=bsnsw,DC=boson,DC=com
memberOf: value = CN=Marketing,CN=Users,OU=bsnsw,DC=boson,DC=com
memberOf: value = CN=Employees,CN=Users,OU=bsnsw,DC=boson,DC=com
memberOf: value = CN=Finance,CN=Users,OU=bsnsw,DC=boson,DC=comIf an LDAP query returns a multivalued attribute, the ASA will match only one of the returned values to the appropriate group policy. The ASA will select the matching group policy with the least number of characters in the name and that starts with the lowest alphanumeric character. In this scenario, four of the five configured mapvalue statements will match the LDAP query response. Because the group policies in the matched statement have names of identical length, the ASA will select the name based on its alphabetical preference. Alphabetically, the name Group1 comes before any of the other matching group policy names: Group3, Group4, and Group5.
-
Which of the following descriptions most accurately describes split tunneling? (Select the best answer.)
- It enables traffic to exit the same interface through which it entered.
- It enables traffic to flow between interfaces that share the same security level.
- It enables a VPN tunnel to form through a firewall or NAT device.
- It enables a VPN tunnel to determine which traffic flows should be encrypted.
Explanation:
Split tunneling enables a virtual private network (VPN) tunnel to determine which traffic flows should be encrypted. Without split tunneling, all traffic that passes through a remote VPN router is encrypted and forwarded through a tunnel to the VPN server, which is an inefficient use of the bandwidth and processing power of the VPN server and the remote VPN router. Traffic that is destined for the Internet or another unprotected network does not need to be encrypted or forwarded to the VPN server. Split tunneling uses an access control list (ACL) to determine which traffic flows are permitted to pass through the encrypted tunnel. Traffic destined for a protected network at the VPN server site is encrypted and allowed to pass through the tunnel, whereas all other traffic is processed normally. This method reduces both the processing load on the router and the amount of traffic that passes through the encrypted tunnel. Split tunneling can also be applied to traffic from remote access VPN clients.
Transparent tunneling, not split tunneling, enables a VPN tunnel to form through a firewall or Network Address Translation (NAT) device. When transparent tunneling is enabled on a VPN client, encrypted packets are encapsulated in Transmission Control Protocol (TCP) or User Datagram Protocol (UDP) packets prior to transmission through the firewall or NAT device.
The samesecuritytraffic permit intrainterface command enables traffic on a Cisco Adaptive Security Appliance (ASA) to exit the same interface through which it entered, which is also known as hairpinning. By default, an ASA does not allow packets to enter and exit through the same physical interface. However, because multiple logical virtual LANs (VLANs) can be assigned to the same physical interface, it is sometimes necessary to allow a packet to enter and exit through the same interface. The samesecuritytraffic permit intrainterface command allows packets to be sent and received from the same interface even if the traffic is protected by IP Security (IPSec) security policies. Another scenario for which you would need to use the samesecuritytraffic permit intrainterface command is if multiple users need to connect via VPN through the same physical interface. These users will not be able communicate with one another unless the samesecuritytraffic permit intrainterface command has been issued from global configuration mode.
Likewise, the samesecuritytraffic permit interinterface command enables traffic to flow between interfaces that share the same security level. Typically, interfaces with the same security level are not allowed to communicate. -
Which of the following IPS detection types does not require regularly updated definition files? (Select the best answer.)
- patternbased
- profilebased
- signaturebased
- reputationbased
Explanation:
Profilebased detection methods, which are also known as anomalybased detection methods, do not require regularly updated definition files. Profilebased detection methods detect abnormal behavior on a network. Traffic is classified as normal or abnormal based on information that is dynamically learned or manually programmed. The benefit of anomalybased detection is that anything that is not specified as normal is classified as abnormal? therefore, anomalybased detection can typically detect a wide range of threats. One drawback of anomalybased detection is that new traffic patterns are required on a regular basis on all but the smallest of networks, which leads to a lot of false positives. Another drawback is the memory and processing power required to handle profiles for each user.
By contrast, patternbased detection methods, which are also called signaturebased methods, require regularly updated definition files. Patternbased detection methods use specific strings of text to detect malicious traffic. Many signaturebased detection methods can also use protocols and port numbers to further specify malicious traffic patterns. The benefit of signaturebased detection methods is that the number of false positives generated is typically low. However, the drawback is that a modified attack cannot be detected by old signature definition files? the modified attack will not be detected until a new signature is added for the modified attack. Therefore, Cisco recommends updating signature files, including antivirus signatures, every time a new update is available.
Reputationbased detection methods use information collected from a global network of security devices to detect malicious traffic. Because the information available is constantly being updated, reputationbased systems require frequent updates to their definition files. The primary advantage to these frequent updates is that many attacks can be detected and prevented based on information gathered from other systems that have already experienced the same attack. -
Which of the following statements is true regarding the sendlifetime command? (Select the best answer.)
- The default duration for sending keys is infinite.
- You cannot specify a duration based on a specific start and end time.
- The duration must be specified in oneminute increments.
- The earliest start time value is January 1, 1970.
Explanation:
When using the sendlifetime command, the default duration for sending keys is infinite. The sendlifetime command is used to specify the period of time during which a key should be sent by a router for authentication. The syntax for this command is sendlifetime starttime {infinite | endtime | duration seconds}, where starttime specifies the date and time that the key should start being sent. The earliest valid start time is January 1, 1993.
By default, keys are valid indefinitely? however, you can use the duration keyword to specify a duration value between 1 and 2,147,483,646 seconds. For example, the sendlifetime 19:00:00 Feb 24 2015 duration 3600 command specifies that a key should be valid for 3,600 seconds, which is one hour, and that the router should begin sending the key at 19:00:00 Feb 24 2015, which corresponds to 7 p.m. on February 24, 2015.
You can specify the duration as a specific start and end time. For example, you could issue the sendlifetime 19:00:00 Feb 24 2015 20:00:00 Feb 24 2015 command to achieve the same onehour duration as the sendlifetime 19:00:00 Feb 24 2015 duration 3600 command. -
Which of the following is a show ntp associations command output symbol that indicates that an IP address is an NTP master and the router is synchronized with the master? (Select the best answer.)
- #
- *
- .
- ~
- +
Explanation:
The asterisk (*) is a show ntp associations command output symbol that indicates that an IP address is a Network Time Protocol (NTP) master and the router is synchronized with the master. The output of the show ntp associations command displays the IP addresses of configured NTP servers as well as their respective clock sources, strata, and reachability statistics. For example, in the following command output, the NTP server at IP address 128.227.205.3 is a stratum 1 server that uses a global positioning system (GPS) time source as its time source:
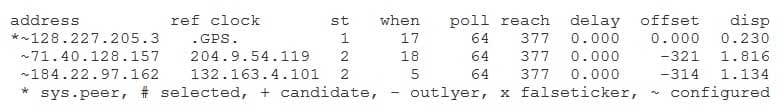
300-735 Part 10 Q10 087 The * next to the IP address in the command output indicates that this server is an NTP master time source to which the Cisco device is synched. The pound sign (#) next to the IP address indicates that this server is an NTP master time source to which the Cisco device is not yet synched. The plus sign (+) next to the IP address indicates that this server is an NTP master time source that is selected for synchronization but the synchronization process has not yet begun. A tilde (~) next to an IP address indicates that the address was manually configured.
The period (.) is a symbol displayed in the output of the show clock command, not the show ntp associations command. If the time is set by a timing source and is not synchronized with that source, the time is still considered authoritative but the . symbol is displayed in the output of the show clock command to indicate the lack of time synchronization. The following command output indicates that the software clock is authoritative but not synchronized with its time source:
.10:06:40.603 UTC Tue Jan 13 2015
The show clock command displays the current time as reported by the system software clock. If the software clock is not set by a timing source, such as NTP, the system will flag the time as not authoritative and the output of the show clock command will indicate the flag with the * symbol, as shown in the following command output:
*10:06:40.603 UTC Tue Jan 13 2015
By contrast, if the time is set by a timing source and is synchronized with that source, the time is considered authoritative and the output of the show clock command will not display any additional symbols. For example, the absence of additional symbols in the following command output indicates that the software clock is authoritative and synchronized with its time source:
10:06:40.603 UTC Tue Jan 13 2015 -
Which of the following impact levels is used by FireSIGHT to indicate that either the source or target host is on a monitored network but has no corresponding entry in the network map? (Select the best answer.)
- 0
- 1
- 2
- 3
- 4
Explanation:
The impact level 4 is used by Cisco FireSIGHT Defense Center to indicate that either the source or target host is on a monitored network but has no corresponding entry in the network map. FireSIGHT uses impact levels to describe the potential severity of attacks. In the FireSIGHT system, managed devices, like Cisco FirePOWER Intrusion Prevention Systems (IPSs), respond to an intrusion event by flagging the event with an impact level and sending the event to the FireSIGHT Defense Center. The impact level is based on accumulated intrusion data, network discovery data, and vulnerability information. The aggregated intrusion event data typically contains contextual information about the event and includes a copy of the packet that triggered the event.
The following table provides a summary of the FireSIGHT impact levels and their meaning:
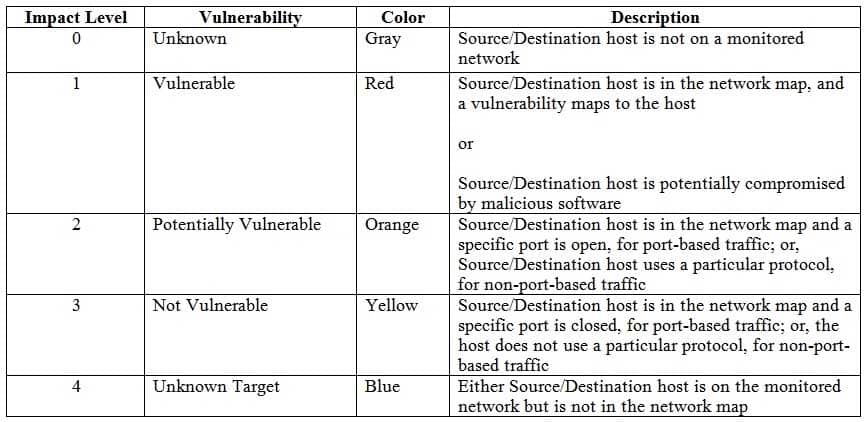
300-735 Part 10 Q11 088 -
Which of the following can the FirePOWER IMAP preprocessor extract in clienttoserver traffic? (Select the best answer.)
- attachments
- file names
- addresses
- header data
Explanation:
On a Cisco FirePOWER Intrusion Prevention System (IPS), the Internet Message Access Protocol (IMAP) preprocessors can extract and decode attachments in clienttoserver traffic. The FirePOWER IMAP preprocessor is an Application layer inspection engine with the capability to decode email traffic and to normalize the resulting data prior to forwarding the traffic to the intrusion rules engine for analysis. Cisco also provides Post Office Protocol version 3 (POP3) and Simple Mail Transfer Protocol (SMTP) preprocessors.
In addition to generating an event when they observe anomalous traffic, the FirePOWER emailrelated preprocessor engines can inspect the commands that pass between a client and a server to ensure that they are compliant with the relevant Request for Comments (RFC). For example, the IMAP preprocessor can generate an event when either a client command or a server response does not comply with RFC 3501, which is the RFC that defines the IMAP protocol, and the POP3 preprocessor can do the same for commands that do not comply with RFC 1939, which is the RFC that defines the POP3 protocol.
By contrast, the SMTP preprocessor provides the ability to normalize all, none, or a specific set of SMTP commands, although a base set of commands will always be considered as part of the custom valid set if normalization is enabled. In addition, the SMTP preprocessor can extract email file names, addresses, and header data. -
Which of the following routing protocols does not support MD5 authentication for secure route updates? (Select the best answer.)
- BGP
- OSPF
- RIPv1
- RIPv2
- EIGRP
Explanation:
Routing Information Protocol version 1 (RIPv1) does not support Message Digest 5 (MD5) authentication for secure route updates. Routing protocol spoofing can inject false routes into routing tables, which can influence path selection through a routed network. You can mitigate routing table modification by implementing routing protocol authentication and filtering. RIPv1 does not support any form of authentication? however, its successor, RIP version 2 (RIPv2), supports either plaintext authentication or MD5 authentication.
Border Gateway Protocol (BGP), Open Shortest Path First (OSPF), RIPv2, Enhanced Interior Gateway Routing Protocol (EIGRP) all support MD5 authentication for secure route updates. Although many of these protocols, such as OSPF, support plaintext authentication as an alternative to MD5, Cisco recommends using MD5 for authentication because it is considerably more secure than plaintext authentication.
Alternatively, you can disable all dynamic routing protocols and use static routes to ensure that routes are updated securely. However, static routes work well only on small, reliable networks. Static routes are not scalable, because changes made on one router are not propagated to the other routers on the network? each router must be modified manually. -
Which of the following is displayed by the show ip dhcp snooping databasecommand? (Select the best answer.)
- the DHCP snooping configuration for a switch
- dynamic entries in the binding table
- the status of the binding table
- detailed DHCP snooping statistics
Explanation:
The show ip dhcp snooping database command displays the status of the binding table. When Dynamic Host Configuration Protocol (DHCP) snooping is configured on a Cisco Catalyst switch, the switch tracks client Media Access Control (MAC) addresses and their associated DHCP client hardware addresses in the DHCP snooping binding database, which is also known as the binding table. If the switch receives DHCP packets that do not match entries in the binding table, the switch drops the packets. The binding table can be stored locally or it can be stored on a remote server. The show ip dhcp snooping databasecommand can be used to display the status of the DHCP snooping binding table agent and statistics regarding the status of the binding table, such as the Uniform Resource Locator (URL) where the binding table can be found and how many successful writes have been committed to the table. For example, the following sample output indicates that the binding table is stored in a file named bindingtable on the Trivial File Transfer Protocol (TFTP) server with an IP address of 1.2.3.4:
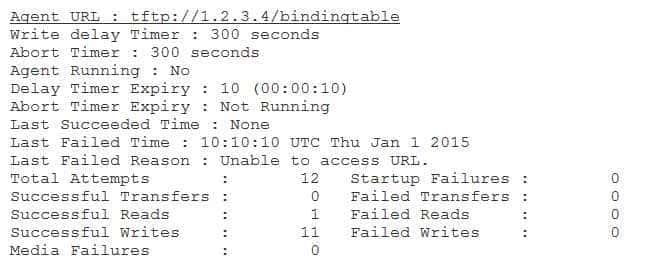
300-735 Part 10 Q14 089 The show ip dhcp snooping command displays general information regarding the DHCP snooping configuration on a switch, such as the virtual LANs (VLANs) for which DHCP snooping is enabled and the trusted state of each interface. For example, the following sample output indicates that DHCP snooping is enabled for VLANs 101, 201, and 301:

300-735 Part 10 Q14 090 The show ip dhcp snooping binding command displays the dynamic entries in the binding table. You must use the show ip source binding command to view both static and dynamic binding table entries. For example, the following sample output from the show ip dhcp snooping binding command indicates that two DHCP clients from VLAN 101 have entries in the binding table:

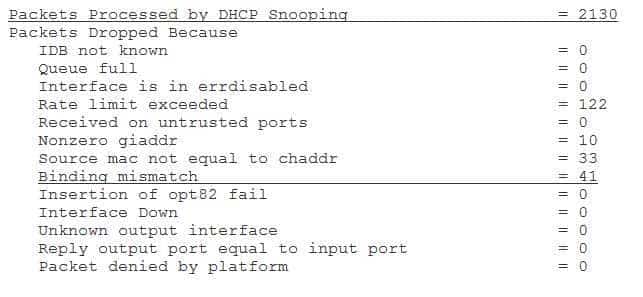
300-735 Part 10 Q14 091 The show ip dhcp snooping statistics detail command displays detailed DHCP snooping statistics, which include the number of packets dropped for each denial category, such as binding mismatches or exceeded rate limits. For example, the following sample output from the show ip dhcp snooping statistics detail command indicates that 2,130 packets were processed by DHCP snooping and 41 packets were dropped because of binding mismatches:
-
Under normal operating circumstances, which of the following planes sends the least amount of traffic to the route processor of a Cisco router? (Select the best answer.)
- the data plane
- the control plane
- the services plane
- the management plane
Explanation:
Under normal operating circumstances, the data plane sends the least amount of traffic to the route processor of a Cisco router. The data plane is one of the four logical components that collectively define a router? the remaining components are the control plane, the management plane, and the services plane. Traffic from the data plane consists primarily of usergenerated traffic that is forwarded from one interface to another on a router. This type of traffic is also referred to as transit traffic.
Cisco routers can use several different forwarding mechanisms to process transit traffic. The slowest of these Layer 3 switching mechanisms is process switching, which uses the router’s CPU, which is also known as the route processor, to determine the next hop and forwarding interface associated with the destination IP address of a received packet. Once a router has a corresponding entry in its route cache or Cisco Express Forwarding (CEF) table, all subsequent packets matching that entry’s destination can be fastswitched to the appropriate interface without involving the CPU. The fastswitching mechanism can handle significantly higher throughput than the processswitching mechanism because most, if not all, of its functions can be implemented directly by the switching fabric of the router.
By contrast, nearly all traffic from the control plane and management plane is handled by the router processor on a Cisco router. Control plane traffic typically consists of packets that are intended to create or perform network operations on a router, such as packets from dynamic routing protocols or Address Resolution Protocol (ARP) packets, whereas management plane traffic consists of packets used to administer the router, such as Telnet or Secure Shell (SSH) session traffic. These packets cannot be handled by Cisco’s normal fastpath switching mechanisms, because they require special handling by the router’s CPU.
Traffic from the services plane is a special kind of data plane traffic that requires some degree of processing by the router CPU before it can be placed into the fastswitching path. For example, Generic Routing Encapsulation (GRE) encapsulation or Quality of Service (QoS) processing might need to be applied to traffic before it is placed into the fast path. Although not all services plane traffic must be processed by the CPU, considerably more services plane traffic involves the CPU than data plane traffic does. -
Which of the following best describes an external cloud? (Select the best answer.)
- decentralized computer resources that can be accessed over the Internet
- a network zone between the Internet and a private or trusted network
- a portion of a private or trusted network that can be accessed by a business partner
- websites available only to users inside a private network
Explanation:
An external cloud is best described as decentralized computer resources that can be accessed over the Internet. An external cloud allows for computer processes that are typically hosted internally to be moved to an external provider, which can reduce the burden on system and network resources. In cloud computing, there are two accepted types of cloud infrastructure: external and internal. External clouds are managed by a service provider and are further broken down into two categories: public and private. With public clouds, the service provider controls the cloud and its infrastructure, whereas with private clouds, the service provider controls only the infrastructure. Internal clouds are similar to private clouds, except that the cloud is owned and managed by the organization that uses it and not by a thirdparty service provider.
A portion of a private or trusted network that can be accessed by a business partner best describes an extranet, not an external cloud. An extranet is a portion of a company’s internal network that is accessible to specific people outside of the company, such as business partners, suppliers, or customers. By creating an extranet, a company can provide a location for sharing information with external users. For example, a consulting company could create an extranet for external customers to view and comment on the consulting company’s progress on various projects. In many extranet implementations, the external customer network shares a bilateral connection with the company’s internal network. This bilateral connection not only enables the external customer to access portions of the company’s internal network, but it also enables portions of the company’s internal network to access the portions of the external customer’s network.
A network zone between the Internet and a private or trusted network best describes a demilitarized zone (DMZ), not an external cloud. DMZs are typically bordered by two firewalls: one that allows information to flow between the DMZ and the Internet, and one that allows information to flow between the DMZ and the private, or trusted, network.
Websites available only to users inside a private network best describe an intranet, not an external cloud. An intranet can be created to provide internal users with their own website. An intranet provides a location for sharing information among members of the company. Unlike an extranet, which is a portion of the company’s network that is accessible by people outside the company, an intranet is typically available only to internal users. -
Which of the following statements are true regarding the DfltGrpPolicy group policy? (Select 3 choices.)
- It cannot be modified.
- It is the default policy used with the DefaultRAGroup connection profile.
- It is the default policy used with the DefaultWEBVPNGroup connection profile.
- It can be applied to user profiles.
- It should be deleted if custom group policies are created.
Explanation:
The DfltGrpPolicy group policy can be applied to user profiles and is the default policy used with both the DefaultRAGroup and the DefaultWEBVPNGroup connection profiles. Group policies are used with Cisco Adaptive Security Appliances (ASAs) to specify security policies and network settings that are used when remote virtual private network (VPN) users log in to the ASA. Cisco ASAs include the DfltGrpPolicy group policy, which is the default policy used for the default connection profiles that are included on an ASA: DefaultRAGroup and DefaultWEBVPNGroup. You can customize the DfltGrpPolicy group policy and tailor it to match your company’s requirements, and you can inherit policies from it from within custom group policies. In addition to applying this group policy to connection profiles, you can also apply it to user profiles, which you can use to create a specific set of policies for individual users.
The DfltGrpPolicy group policy cannot be deleted. You can create custom group policies, but you cannot delete the default group policy. -
Which of the following is accomplished as a result of issuing the groupurl command on an ASA? (Select the best answer.)
- A list of bookmarks will be created for clientless SSL VPN users.
- A VPN access method will be created in which the connection profile is automatically selected for VPN users.
- A webtype ACL will be created for a tunnel group.
- A list of WebVPN servers will be applied to a user account.
Explanation:
Issuing the groupurl command on a Cisco Adaptive Security Appliance (ASA) will create a virtual private network (VPN) access method in which the connection profile is automatically selected for VPN users? the groupurl command will create a group Uniform Resource Locator (URL) for Secure Sockets Layer (SSL) VPN users. If you configure a group URL for SSL VPN users, the users can connect to the group URL and will not be required to select a tunnel group when they establish a connection. In such a scenario, the user is presented with only user name and password fields on the login screen. The Cisco ASA examines the URL from which the user is connecting and automatically applies the connection profile associated with the URL. Configuring a group URL can help improve security because the user is not presented with a list of available connection profiles.
You can configure a group URL by using the groupurl command or by using Cisco Adaptive Security Device Manager (ASDM). The syntax of the groupurl command is groupurl url [enable | disable]. This command should be issued from tunnelgroupwebvpn configuration mode. To configure a group URL for a new SSL VPN connection profile in ASDM, you should click Configuration, expand Network (Client) Access, click AnyConnect Connection Profiles, and click Add under Connection Profiles, which will open the Add SSL VPN Connection Profile dialog box. In the Add SSL VPN Connection Profile dialog box, expand Advanced, and click SSL VPN to open the SSL VPN screen? on the SSL VPN screen, you can add a list of group URLs in the Group URLsarea.
Issuing the groupurl command will not create a webtype access control list (ACL) for a tunnel group. You can issue the accesslist webtype command to create a webtype ACL.
Issuing the groupurl command will not apply a list of WebVPN servers to a user account or create a list of bookmarks for SSL VPN users. You can issue the urllist command to configure a list of WebVPN servers or a list of URLs that will be applied to user profiles. -
What is the default modulus size that is used to create a selfsigned certificate for SSL authentication on a Cisco ASA? (Select the best answer.)
- 512 bits
- 768 bits
- 1,024 bits
- 2,048 bits
Explanation:
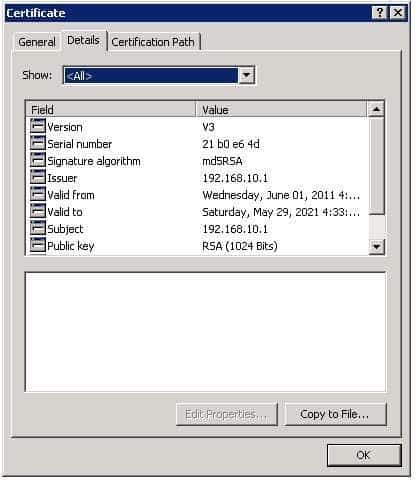
The default modulus size that is used to create a selfsigned certificate for Secure Sockets Layer (SSL) authentication on a Cisco Adaptive Security Appliance (ASA) is 1,024 bits. If no trust point has been configured, an ASA dynamically generates a selfsigned certificate when an SSL connection is first established. For example, when a Secure Hypertext Transfer Protocol (HTTPS) or a Cisco Adaptive Security Device Manager (ASDM) connection is made to the ASA, a selfsigned certificate is used to authenticate the ASA to the browser or ASDM client. You can view selfsigned certificates in ASDM by opening the Configuration > Remote Access VPN > Certificate Management > Identity Certificates pane. You can identify a selfsigned certificate in the Identity Certificatespane by looking for a certificate with identical values in the Issued To and Issued Byfields. After selecting a certificate, you can click the Show Details button to display detailed information about the certificate. Below, you can see a selfsigned certificate associated with ASDM_Trustpoint0 and with a modulus of 1,024 bits:

300-735 Part 10 Q19 093 Alternatively, you can examine a certificate by using a modern web browser. When a web browser or ASDM session is presented with a selfsigned certificate, it will issue a warning to indicate that it cannot verify the certificate with a root certificate authority (CA). Below, you can see an example of the warning information presented by a browserbased HTTPS session that receives a selfsigned certificate:
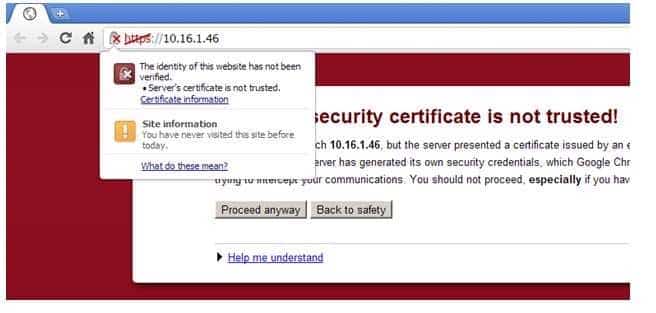
300-735 Part 10 Q19 094 You can view the details of the certificate by clicking the Certificate information link, which will display the information about the contents of the certificate. You can determine that a certificate is selfsigned by noting that the Issued to and Issued by fields in the certificate contain the same value, as shown in the example below:

300-735 Part 10 Q19 095 You can click the Details tab to view the contents of the certificate. Because this example is from an ASA with a default configuration, you can see in the following exhibit that the modulus size in the Public key field is 1,024 bits:
-
Which of the following statements is true regarding private VLANs? (Select the best answer.)
- Isolated ports can communicate only with other isolated ports in the same isolated VLAN.
- Only a single community VLAN can be associated with a primary VLAN.
- Community VLANs can send traffic to isolated ports but cannot receive traffic from them.
- Every port in a private VLAN is a member of the primary VLAN.
Explanation:
Every port in a private virtual LAN (VLAN) is a member of the primary virtual LAN (VLAN). Private VLANs can be configured on a switch to help isolate traffic and provide Layer 2 separation between ports that belong to the same VLAN. Because the separation exists at Layer 2, the hosts can exist on the same IP subnet. The VLAN to which the hosts belong is called the primary VLAN. To create a private VLAN, you must create one or more secondary VLANs and associate the secondary VLANs with the primary VLAN. There are two types of secondary VLANs: community VLANs and isolated VLANs.
When configuring a port to participate in a private VLAN, you must configure the port by issuing the switchport mode privatevlan {promiscuous | host} command. The promiscuous keyword configures the port to communicate with any secondary VLAN. Consequently, devices that should be reachable from any secondary VLAN should be connected to promiscuous ports. For example, a router, a firewall, or a gateway that any host should be able to reach should be connected to a promiscuous port. By contrast, devices connected to isolated or community VLANs should be connected to host ports, which are configured by using the host keyword.
You can configure a primary VLAN by issuing the privatevlan primary command, and you can configure secondary VLANs by issuing the privatevlan {isolated | community} command. Devices connected to a community VLAN can communicate with other devices on the community VLAN as well as with the primary VLAN. However, no devices on the community VLAN can communicate with a device that is connected to an isolated port.
Ports that belong to an isolated VLAN can communicate only with promiscuous ports. Any traffic received from isolated ports is forwarded only to promiscuous ports? thus isolated ports cannot communicate directly with each other.