300-735 : Automating Cisco Security Solutions (SAUTO) : Part 11
-
Which of the following examples best describes the SaaS service model? (Select the best answer.)
- A company moves all companywide policy documents to an Internetbased virtual file system hosted by a service provider.
- A company hires a service provider to deliver cloudbased processing and storage that will house multiple virtual hosts configured in a variety of ways.
- A company licenses an office suite, including email service, that is delivered to the end user through a web browser.
- A company obtains a subscription to use a service provider’s infrastructure, programming tools, and programming languages to develop and serve cloudbased applications.
Explanation:
A company that licenses an office suite, including email service, that is delivered to the end user through a web browser is an example of the Software as a Service (SaaS) service model. The National Institute of Standards and Technology (NIST) defines three service models in its definition of cloud computing: SaaS, Infrastructure as a Service (IaaS), and Platform as a Service (PaaS).
The SaaS service model enables its consumer to access applications running in the cloud infrastructure but does not enable the consumer to manage the cloud infrastructure or the configuration of the provided applications. A company that licenses a service provider’s office suite and email service that is delivered to end users through a web browser is using SaaS. SaaS providers use an Internet enabled licensing function, a streaming service, or a web application to provide end users with software that they might otherwise install and activate locally. Webbased email clients, such as Gmail and Outlook.com, are examples of SaaS.
The PaaS service model provides its consumer with a bit more freedom than the SaaS model by enabling the consumer to install and possibly configure providersupported applications in the cloud infrastructure. A company that uses a service provider’s infrastructure, programming tools, and programming languages to develop and serve cloudbased applications is using PaaS. PaaS enables a consumer to use the service provider’s development tools or Application Programmer Interface (API) to develop and deploy specific cloudbased applications or services. Another example of PaaS might be using a third party’s MySQL database and Apache services to build a cloudbased customer relationship management (CRM) platform.
The IaaS service model provides the greatest degree of freedom by enabling its consumer to provision processing, memory, storage, and network resources within the cloud infrastructure. The IaaS service model also enables its consumer to install applications, including operating systems (OSs) and custom applications. However, with IaaS, the cloud infrastructure remains in control of the service provider. A company that hires a service provider to deliver cloudbased processing and storage that will house multiple physical or virtual hosts configured in a variety of ways is using IaaS. For example, a company that wanted to establish a web server farm by configuring multiple Linux Apache MySQL PHP (LAMP) servers could save hardware costs by virtualizing the farm and using a provider’s cloud service to deliver the physical infrastructure and bandwidth for the virtual farm. Control over the OS, software, and server configuration would remain the responsibility of the organization, whereas the physical infrastructure and bandwidth would be the responsibility of the service provider.
A company that moves all companywide policy documents to an Internetbased virtual file system hosted by a third party is using cloud storage. Cloud storage is a term used to describe the use of a service provider’s virtual file system as a document or file repository. Cloud storage enables an organization to conserve storage space on a local network. However, cloud storage is also a security risk in that the organization might not have ultimate control over who can access the files. -
You have issued the logging enable command on an ASA with the default configuration.
Which of the following statements is true regarding the syslog messages that will be generated on this ASA by default? (Select the best answer.)
- The ASA will generate syslog messages that include a date.
- The ASA will generate syslog messages that include a time.
- The ASA will not generate syslog messages with a severity of 0.
- The ASA will not generate syslog messages with a severity of 7.
- The ASA will send syslog messages to only the console.
Explanation:
A Cisco Adaptive Security Appliance (ASA) with a default configuration and logging enabled will not generate system log (syslog) messages with a severity of 0. This value correlates with the severity of the event that caused the message to be generated? higher values indicate a less severe event. Level 0 is an emergency severity level and denotes that the system is unusable. Although an ASA will not generate syslog messages with a severity level of 0, severity level 0 is supported on the ASA to ensure compatibility with the UNIX syslog feature. The following table lists the syslog severity levels that can be generated by an ASA:

300-735 Part 11 Q02 097 When an ASA is configured to direct syslog messages to a specific output location, it will include all messages with a severity level value less than or equal to the severity level value configured for that particular location. For example, if an ASA is configured to output syslog messages with a severity of 7 to the console, the ASA will also output syslog messages with a severity less than 7 to the console. Therefore, the higher the severity level configured on the ASA, the more syslog messages generated and transmitted to the configured logging destinations.
An ASA with a default configuration and logging enabled will not send syslog messages to only the console.
Although syslog messages for all supported severity levels are generated once logging has been enabled, they are not directed to a destination until an output location has been configured on the ASA. Syslog messages can be directed to several different locations, including the ASA’s console port? a syslog server? a Simple Network Management Protocol (SNMP) server? an email address? or a remote session, such as a Telnet session, a Secure Shell (SSH) session, or a Cisco Adaptive Security Device Manager (ASDM) session. When configuring a target location for syslog messages, you must also specify the severity level for the syslog messages that should be directed to the target location. Because directing syslog messages to the console can degrade system performance, Cisco recommends configuring the internal buffer as a destination for syslog messages and then using the show logging command to manually view the buffered messages.
An ASA with a default configuration and logging enabled will not generate syslog messages that include a date or time. Although the timestamp is not included by default, you can configure the syslog to include a timestamp by issuing the logging timestamp command. In addition, you can configure the syslog to include a device ID by issuing the logging deviceid command. The syntax for the logging deviceid command is logging deviceid [contextname | hostname | ipaddress interfacename | string text]. -
According to Cisco best practices, which of the following is true about the ideal application of an extended access list? (Select the best answer.)
- It should be applied in the inbound direction on the interface that is as close to the destination aspossible.
- It should be applied in the outbound direction on the interface that is as close to the destination aspossible.
- It should be applied in the inbound direction on the interface that is as close to the source as possible.
- It should be applied in the outbound direction on the interface that is as close to the source as possible.
Explanation:
According to Cisco best practices, extended access control lists (ACLs) should be applied in the inbound direction on the interface that is as close to the source as possible. ACLs are used to identify traffic. Once identified, the traffic can then be filtered, analyzed, forwarded, or influenced in various ways. ACLs can be identified by an access list number or an access list name. Numbered ACLs ranging from 1 through 99 are standard ACLs and can identify traffic based on only the source IP address. Numbered ACLs ranging from 100 through 199 are extended ACLs and can identify traffic based on source and destination IP addresses as well as traffic type.
ACLs can consist of multiple access list statements, which are also known as access control entries (ACEs). Packets are compared to each statement in sequence until a match is found. The permit and deny keywords are used to indicate whether matching packets should be forwarded or dropped, respectively. If the packet does not match any of the access list statements, the packet is dropped. This is called the implicit deny rule? all traffic is dropped unless it is matched by one of the access list statements that is configured with the permit keyword.
An ACL does not perform an action until it is applied to an interface. Only one ACL can be configured per interface per direction. This means that a particular interface can be configured for one inbound and one outbound ACL. According to Cisco best practices, extended IP ACLs should be placed as close as possible to the source of traffic because extended ACLs have the ability to specify a destination IP address and port. By contrast, standard ACLs should be placed as close to the destination network as possible because they can filter addresses based on only the source IP address. If a standard ACL is placed too close to the source network, it is possible that the limited granularity of the standard ACL could unintentionally cause legitimate traffic to be filtered. -
Which of the following statements is true regarding network object NAT on an ASA? (Select the best answer.)
- A single NAT rule can apply to both a source and destination address.
- A network object or group is a parameter of the NAT configuration.
- Network object NAT is more scalable than twice NAT.
- Network object NAT can use network object groups to specify real and mapped addresses.
- Network object NAT is easier to configure than twice NAT.
Explanation:
Network object Network Address Translation (NAT) is easier to configure than twice NAT on a Cisco Adaptive Security Appliance (ASA) configuration. You can implement NAT in two ways on an ASA: network object NAT and twice NAT. With network object NAT, NAT is a parameter of a network object and the network object serves as the real address for the translation. Network object NAT can apply to either a source or destination address? however, two separate NAT rules would be required to translate both a source and destination address. Because of these restrictions and limitations, network object NAT is easier to configure than twice NAT.
By contrast, twice NAT can use network objects and groups to represent real and mapped addresses. The network objects or groups in a twice NAT configuration are parameters of the NAT configuration and can represent source real, source mapped, destination real, and destination mapped addresses. In addition, service objects can be used to represent real and mapped source and destination network ports. Twice NAT can specify both source and destination addresses in a single NAT rule, which makes it more scalable than network object NAT. However, the additional capabilities of twice NAT make it more difficult to configure than network object NAT. -
Upon which of the following languages is the Cisco FlexConfig scripting engine based? (Select the best answer.)
- Java
- JavaScript
- ActionScript
- Bourne Again Shell
Explanation:
The Cisco FlexConfig scripting engine is based on the Java programming language. The FlexConfig scripting engine uses a subset of the commands from the Apache Velocity Template engine, which is an opensource templating engine that can be used to create and reference dynamic configuration objects. With FlexConfig, an administrator can create policies and objects to extend the capabilities of Cisco Security Manager (CSM) to include configuration features that are not otherwise supported. For example, you could use a FlexConfig script to loop through a specified group of phone numbers and assign a portion of them to plain old telephone service (POTS) ports and the remainder to IP addresses for Voice over IP (VoIP) operation.
The FlexConfig scripting engine is not based on the Bourne Again Shell (bash) command language. The Cisco IOS commandline interface (CLI) is based on the bash command interpreter and, on some platforms, includes all of the standard bash interpreter features in addition to a set of Ciscospecific commands.
The FlexConfig scripting engine is not based on the ActionScript or JavaScript programming languages.
Although many webbased management platforms, such as CSM or Cisco Configuration Professional (CCP), rely on ActionScript or JavaScript for all or even part of their general implementation, the FlexConfig scripting engine is a fully Javabased templating engine and is not dependent on other programming languages or command interpreters. -
Refer to the exhibits:
300-735 Part 11 Q06 098 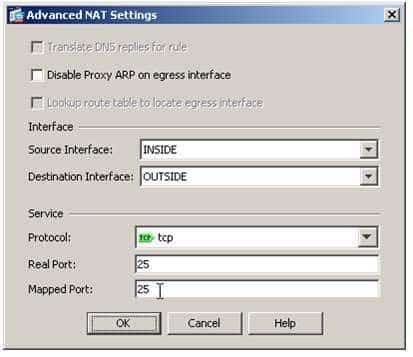
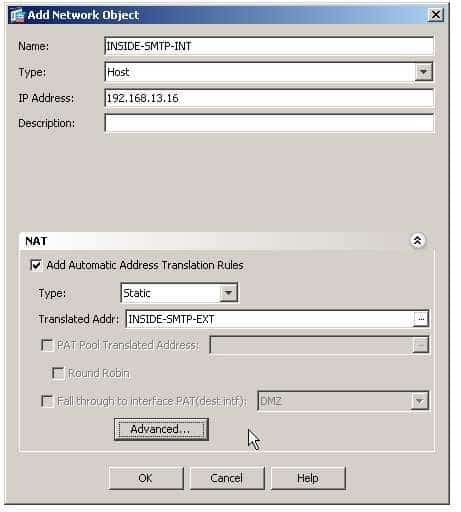
300-735 Part 11 Q06 099 You want to use ASDM to create a static network object NAT rule which will enable users on the OUTSIDE network to reach an SMTP server on the INSIDE network by using the IP address defined by the INSIDESMTPEXT object.
Which of the following samples of the Configuration > Firewall > NAT Rules pane corresponds to the resulting configuration after you create the NAT rule? (Select the best answer.)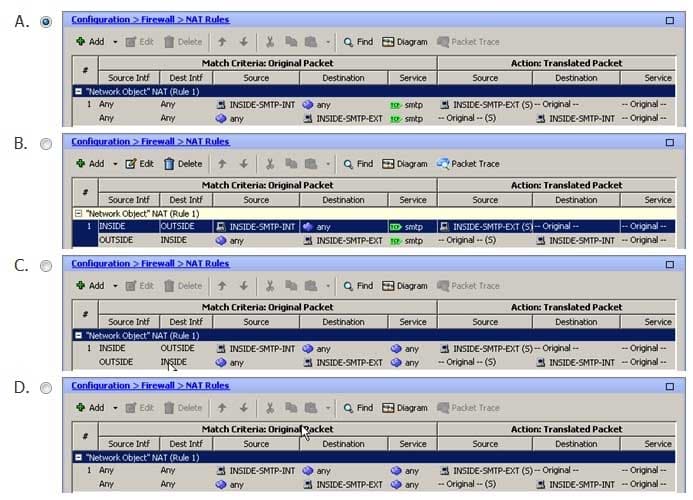
300-735 Part 11 Q06 100 - Option A
- Option B
- Option C
- Option D
Explanation:
The following sample of the Configuration > Firewall > NAT Rules pane corresponds to the resulting configuration after you create the static Network Address Translation (NAT) rule in this scenario:
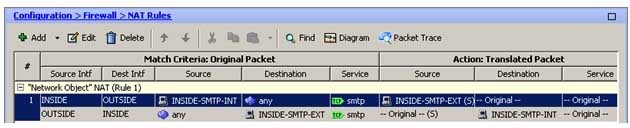
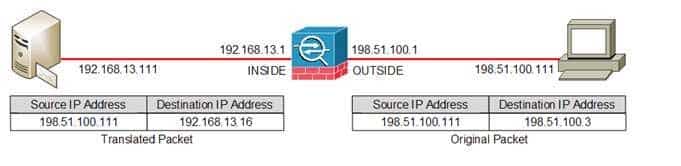
300-735 Part 11 Q06 101 The network object NAT rule in this scenario creates a static NAT rule which will enable users on the OUTSIDE network to reach a Simple Mail Transfer Protocol (SMTP) server on the INSIDE network by using the IP address specified by the INSIDESMTPEXT network object, which is 198.51.100.3. The following diagram illustrates the static rule by using a sample packet from a host with an IP address of 198.51.100.111:
300-735 Part 11 Q06 102 You can configure a network object NAT rule from the Configuration > Firewall > NAT Rules pane in Adaptive Security Device Manager (ASDM) by clicking the Add dropdown list, and selecting the Add “Network Object” NAT rule to open the Add Network Object dialog box. The following sample Add Network Object dialog box corresponds to the dialog box in this scenario:
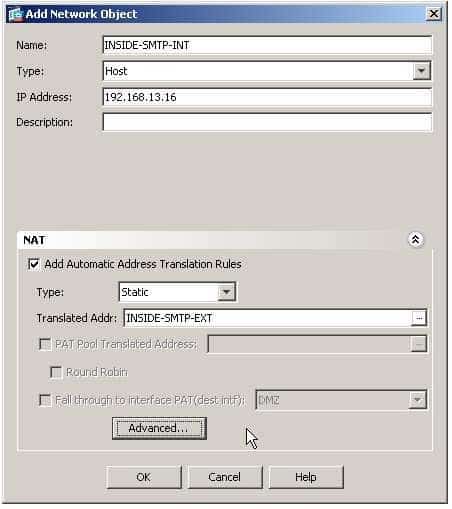
300-735 Part 11 Q06 103 The Name field in the Add Network Object dialog box specifies the name of the network object to which the NAT rule will apply. The NAT rule will affect the source IP address of the specified network object. The Type dropdown list specifies the type of network object that is being configured. A network object can be a single IP address, a range of IP addresses, a network subnet, or a Fully Qualified Domain Name (FQDN). In this scenario, the NAT rule is being configured for a single SMTP server, so the Host type is selected from the dropdown list box in the dialog box. Because the Host type is selected, the IP Address field is displayed in the dialog box. If something else had been selected, the appropriate fields would be displayed instead. For example, if the Range type had been selected, the Start Address and End Address fields would have been displayed instead of the IP Address field. The IP Address field specifies the IP Address that corresponds to the network object; in this scenario, it refers to the real IP address of the SMTP server.
The NAT section of the Add Network Object dialog box is where NAT parameters can be configured. The Add Automatic Address Translation Rules checkbox enables NAT for the object and creates the NAT rules displayed in the Configuration > Firewall > NAT Rules pane of ASDM. The Type dropdown list in the NAT section specifies the type of NAT that will be performed for the network object’s source IP address. You can configure static NAT, dynamic NAT, and dynamic Port Address Translation (PAT). In this scenario, a static NAT rule is required to translate the SMTP server’s real IP address to a mapped IP address on the OUTSIDE network. The Translated Addr field specifies the mapped address that will be used as the source of translated packets. In this scenario, the INSIDE SMTPEXT network object defines the IP address of the SMTP server on the OUTSIDE network and is specified in the Translated Addr field. Because static NAT has been selected as the translation type, none of the other fields in the dialog box are available. Fields such as the PAT Pool Translated Address field become available only when a relevant translation type is specified. The Advanced button is used to open the Advanced NAT Settings dialog box, as shown in the following sample dialog box: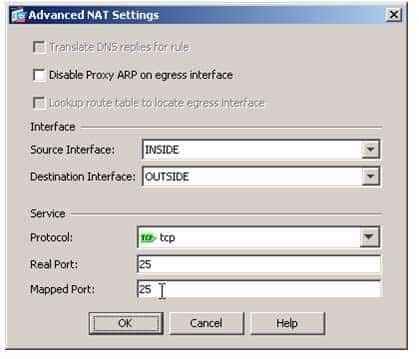
300-735 Part 11 Q06 104 The Advanced NAT Settings dialog box can be used to specify additional translation parameters, such as the source and destination interfaces. In addition, you can specify port translation for a network service. In this scenario, we specify the INSIDE interface as the Source Interface, the OUTSIDE interface as the Destination interface, and we specify Transmission Control Protocol (TCP) port 25, which is the port used by SMTP, as both the real port and mapped port. Specifying the network service limits the static NAT rule to only packets with the appropriate network port.
The following sample of the Configuration > Firewall > NAT Rules pane does not correspond to the resulting configuration after you create the static NAT rule in this scenario, because no network service has been specified for the original packets: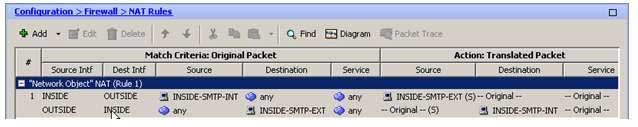
300-735 Part 11 Q06 105 The following sample of the Configuration > Firewall > NAT Rules pane does not correspond to the resulting configuration after you create the static NAT rule in this scenario, because no source or destination interfaces have been specified for the original packets:

300-735 Part 11 Q06 106 The following sample of the Configuration > Firewall > NAT Rules pane does not correspond to the resulting configuration after you create the static NAT rule in this scenario, because neither a network service nor source and destination interfaces have been specified for the original packets:
-
One of your company’s headquarters routers is not forwarding packets to a branch location. The router is housed in a locked room onsite. A junior administrator has remotely connected to the router to troubleshoot the problem. You have been asked for assistance in interpreting some of the configuration output.
Which of the following methods are you least likely to use to connect to the router? (Select the best answer.)
- Telnet
- SSH
- a console port
- a serial port
- an auxiliary port
Explanation:
Of the available choices, you are least likely to use a serial port to connect to the router. Serial ports and Ethernet ports are used to directly connect Cisco routers to other network devices. For example, you might use a serial port to directly connect a Cisco router to other data terminal equipment (DTE) or data communications equipment (DCE) devices. You would also use a serial port to connect a router to a Channel Service Unit/Data Service Unit (CSU/DSU).
You are likely to use inband tools, such as Telnet or Secure Shell (SSH), to connect to the router in this scenario because the router is remotely accessible from your company’s network. Management applications and administrators who want to manage a Cisco device when it is operating in its normal state could connect to the device by using virtual terminal (VTY) application protocols such as Telnet or SSH. The use of VTY lines typically allows multiple administrators or management applications to concurrently access a device from more than one location.
You might use a console port or an auxiliary (AUX) port to connect to the router in this scenario, although doing so is not necessary because the router is remotely accessible. In addition, connecting by either of these methods requires you to be in the same room as the device. You are most likely to use either an AUX port or a console port to manage a Cisco router outofband, such as when the router is in readonly memory (ROM) monitor (ROMmon) mode. The AUX port on a Cisco router is typically capable of supporting most of the features available on a console port. Cisco switches either do not have AUX ports or do not support certain features, such as system recovery, on their AUX ports if they have them.
ROMmon is a management mode that Cisco routers and switches revert to when the system cannot find a software image, the software image is corrupted, or the configuration register has been set to manually enter ROMmon mode. Because ROMmon is an outofband management method, it can be used to recover system software images, passwords, or other configuration data even when the router or switch is in a state where it can no longer forward packets. -
You are troubleshooting IPSec VPN connectivity between two sites. From the local router, you are able to ping the remote tunnel endpoint.
Which of the following steps should you perform next? (Select the best answer.)
- Issue the traceroute command to trace the route to the tunnel endpoint.
- Verify that the IKE policies match on both peers.
- Verify that the peers successfully authenticate one another.
- Reboot both devices.
Explanation:
If you are able to ping the remote tunnel endpoint, you should verify that the Internet Key Exchange (IKE) policies match on both peers. Issuing the show crypto isakmp policycommand will display the IKE phase 1 policy settings that are configured on the router, including the encryption algorithm, hash algorithm, authentication method, DiffieHellman (DH) key exchange mechanism, and security association (SA) lifetime. The following displays sample output from the show crypto isakmp policy command:
RouterA#show crypto isakmp policy
Global IKE policy
Protection suite of priority 20
encryption algorithm: AES Advanced Encryption Standard (128 bit keys)
hash algorithm: Secure Hash Standard
authentication method: PreShared Key
DiffieHellman group: #14 (2048 bit)
lifetime: 3600 seconds, no volume limitYou can also issue the debug crypto isakmp command to determine whether an IKE phase 1 policy mismatch is occurring. The debug error message 1d00h: ISAKMP (0:1): atts are not acceptable. Next payload is 0 will appear when there is a phase 1 policy mismatch between the peers. To configure IKE phase 1 policy parameters, issue the crypto isakmp policy priority command to enter ISAKMP policy configuration mode, where you can issue the following commands:
– authentication
– encryption
– group
– hash
– lifetime
If the IKE phase 1 policies match, you should issue the debug crypto isakmp command to verify that the SA authenticates. If there is a preshared key (PSK) mismatch between the peers, you will see the 1d00h:% CRYPTO4IKMP_BAD_MESSAGE: IKE message from 10.11.12.13 failed its sanity check or is malformed debug error message. If a PSK is missing on one of the peers, you will see the 1d00h:#CRYPTO4IKMP_NO_PRESHARED_KEY: Preshared key for remote peer at 10.11.12.13 is missing debug error message. To create a PSK, issue the crypto isakmp key key {address | ipaddress [mask] | hostname name} [noxauth] command.
If you can ping the remote tunnel endpoint, there is no need to issue the traceroutecommand to trace the route to the tunnel endpoint. A successful ping indicates that connectivity between the peers exists. If the ping is not successful, you can issue the traceroute command to see where the fault is occurring along the path between the two peers.
Rebooting peer routers should not be among the first actions you perform when troubleshooting IP Security (IPSec) virtual private network (VPN) connectivity between two sites. If you have performed the other troubleshooting steps but are still unable to establish a VPN connection, you might consider rebooting the routers. However, rebooting is not likely to solve the connectivity problems. -
Which of the following is not a method of mitigating false positives on a Sourcefire device? (Select the best answer.)
- disabling unnecessary Snort rules
- suppressing event notifications
- reporting false positives to Cisco Technical Support
- configuring an Allow action without inspection
- configuring a Block action
Explanation:
Configuring a Block action is not a method of mitigating false positives on a Sourcefire device. A false positive occurs when an intrusion detection system (IDS) or intrusion prevention system (IPS) identifies nonmalicious traffic as malicious. Sourcefire devices are commercial Cisco IDSs based on the opensource IDS known as Snort. The Block action simply blocks traffic and does not perform any type of inspection. Although the Block action might prevent notifications from false positives, it would also drop legitimate traffic.
Configuring an Allow action without inspection is a method of mitigating false positives on a Sourcefire device. A Sourcefire device can match traffic based on a number of conditions, including security zones, networks, virtual LAN (VLAN) tags, source or destination ports, applications, Uniform Resource Locators (URLs), or users. The Sourcefire is also capable of handling traffic matching a given condition by applying an action, or rule, to the traffic. The actions that are supported by a Sourcefire include all of the following:
– Monitor
– Trust
– Block
– Interactive Block
– Allow
A Sourcefire can inspect and log traffic that is passed by the Allow action. Sourcefire inspection occurs when an Intrusion Policy is applied to this action. Applying an action without an Intrusion Policy performs the given action when traffic matches a condition but does not inspect the traffic. Therefore, you could apply an Allow action without an Intrusion Policy to allow all traffic matching a given condition and prevent that traffic from generating a false positive. Conversely, you might apply an Allow action with an Intrusion Policy to permit all but malicious traffic that matches a given condition.
Disabling unnecessary Snort rules is a method of mitigating false positives on a Sourcefire device. Unnecessary rules include rules that are designed to prevent the exploitation of vulnerabilities that have been fixed, rendering the rule obsolete. Disabling such rules prevents them from generating alerts based on matching traffic.
Reporting false positives to Cisco Technical Support is a method of mitigating false positives on a
Sourcefire device. Default Sourcefire Snort rules that trigger notifications might need to be modified by Cisco’s Vulnerability Research Team (VRT) if the rule is causing legitimate traffic to be dropped.
Suppressing event notifications by using the Sourcefire Suppression feature is a method of mitigating false positives on a Sourcefire device. The Suppression feature will prevent the Sourcefire device from sending event notifications. However, the Suppression feature does not prevent the Sourcefire from processing traffic. Therefore, the generation of false positives might still be a drain on device resources. Also, legitimate traffic could be silently dropped. -
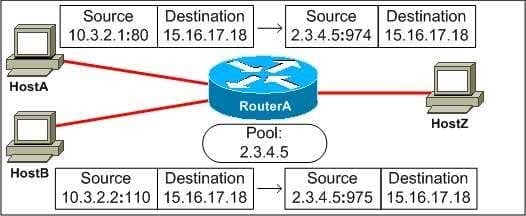
Which of the following actions is performed by dynamic NAT? (Select the best answer.)
- mapping an inside local IP address to a specific global IP address
- mapping an inside local IP address to a global IP address chosen from a pool
- mapping an inside local IP address and port to a global IP address with a specific port
- mapping an inside local IP address and port to a global IP address with a randomly selected port
Explanation:
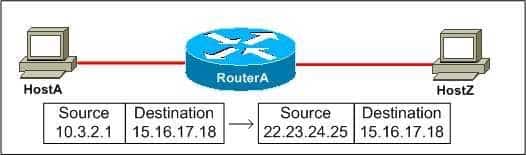
Dynamic Network Address Translation (NAT) maps an inside local IP address to a global IP address chosen from a pool. This is often done to enable inside hosts with private, nonroutable IP addresses to use a globally routable IP address so that the inside hosts can communicate over the Internet. The following exhibit shows an example of dynamic NAT:

300-735 Part 11 Q10 108 Static NAT maps an inside local IP address to a specific global IP address. This is often used to enable outside hosts to connect to a device on the inside network, such as a web server, when port translation is not required. The following exhibit shows an example of static NAT:
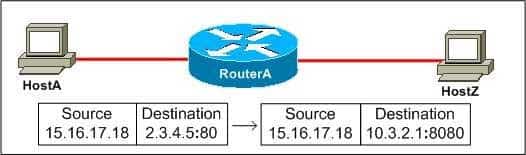
300-735 Part 11 Q10 109 Static Port Address Translation (PAT), which is also called port forwarding, maps an inside local IP address and port to a global IP address with a specific port. This is often used to enable outside hosts to connect to a specific service on a device located on the inside network, such as a web server. The following exhibit shows an example of static PAT:
300-735 Part 11 Q10 110 Dynamic PAT, which is also called NAT overloading, maps an inside local IP address and port to a global IP address with a randomly selected port. This is often done to enable multiple inside hosts with private, nonroutable IP addresses to share a single globally routable IP address so that the inside hosts can communicate over the Internet. The PAT router keeps track of each inside host by assigning a random port number to the client for the duration of the communication.
However, dynamic PAT is capable of mapping internal source addresses to more than one routable IP address. Some security appliances could mistake a large number of packets from a single IP address as a DoS attack attempt. Therefore, dynamic PAT supports the use of roundrobin to enable internal IP source addresses to map to more than just one routable IP source address. By using dynamic PAT’s roundrobin assignment of IP addresses, the risk of misidentification of large amounts of traffic as a DoS attack can be mitigated.
The following exhibit shows an example of dynamic PAT: -
You are configuring auto NAT on a Cisco Firepower device. The network object contains rules of both static and dynamic types from internal subnets. You have configured the rules in the following order:
1. Dynamic NAT: 172.16.1.0/28
2. Static NAT: 192.168.51.8/29
3. Static NAT: 10.10.10.0/24
4. Dynamic NAT: 192.168.32.0/24
5. Static NAT: 10.10.11.1/32The Firepower receives internal traffic from the 192.168.51.8/29 subnet.
Which of the rules in this scenario will be processed? (Select 2 choices.)- 1
- 2
- 3
- 4
- 5
Explanation:
Of the auto Network Address Translation (NAT) rules configured in this scenario, only the static NAT rule for the 10.10.11.1/32 network and the static NAT rule for the 192.168.51.8/29 network will be processed. Auto NAT rules are automatically ordered by the device. Regardless of the order in which you configured the rules in the network object, auto NAT will always attempt to match static rules before dynamic rules. In addition, auto NAT will always attempt to match the longest address prefix first, meaning that the rule that contains the smallest quantity of real IP addresses will be processed before rules containing a larger quantity of real IP addresses. Therefore, a static NAT mapping that matches 10.10.10. 0/24 will be processed before a dynamic NAT mapping that matches 10.10.10.10/32, even though the 10.10.10.10/32 address has a longer prefix.
In this scenario, auto NAT will first attempt to match the traffic to the static NAT rule with the 10.10.11.1/32 address. This is because that rule is the static rule with the longest prefix. Next, auto NAT will attempt to match the traffic to the static rule with the second longest prefix, which is 192.168.51.8/29. Because the traffic matches this rule, the device will not process any of the other auto NAT rules.
If the traffic in this scenario did not match the static 192.168.51.8/29 rule, the device would have continued processing the auto NAT rules in the following order:
– Static NAT: 10.10.10.0/24
– Dynamic NAT: 172.16.1.0/28
– Dynamic NAT: 192.168.32.0/24There are two methods of implementing NAT on a Cisco Firepower device: manual NAT and auto NAT. Of the two methods, auto NAT is the simplest to configure because NAT rules are configured as components of a network object. Both source and destination addresses are compared to the rules within the object. Manual NAT, on the other hand, enables you to specify both the source address and the destination address of a mapping in a single rule. Therefore, you can configure more granular mapping rules by using manual NAT.
Both manual NAT rules and auto NAT rules are stored in the same translation table. The table is divided into three sections. Section 1 and Section 3 contain manual NAT rules, with Section 1 containing the most specific manual NAT rules and Section 3 containing the most general NAT rules. Section 2 contains auto NAT rules.
When the Firepower matches traffic to the NAT translation table, manual NAT rules in Section 1 are processed first and in the order in which they were configured. Manual NAT rules are added to Section 1 by default. If a match is found, rules in Section 2 and Section 3 are ignored. If the traffic does not match any of the manual NAT rules in Section 1, the auto NAT rules in Section 2 are processed.
If the traffic matches one of the auto NAT rules, rules in Section 3 are ignored. If the traffic does not match any of the auto NAT rules, the device will next attempt to match the traffic to the Section 3 manual NAT rules.
Similar to Section 1, the manual NAT rules in Section 3 are processed in the order that they appear in the configuration. However, you must specifically place manual NAT rules in this section because the device will not automatically place manual NAT rules there. Cisco recommends that the most general manual NAT rules be placed in this section, with the most specific of those general rules configured first. -
Which of the following fields make up the trailer of an ESP packet? (Select 3 choices.)
- Next Header
- Pad Length
- Padding
- Security Parameter Index
- Sequence Number
Explanation:
The Encapsulating Security Payload (ESP) trailer is made up of the Padding, Pad Length, and Next Header fields. ESP is an IP Security (IPSec) protocol that provides data integrity and confidentiality for IP traffic. The
ESP trailer is always part of the authenticated data and is always encrypted. By contrast, the Security Parameter Index (SPI) and Sequence Number fields make up the header of an ESP packet. The ESP header is always part of the authenticated data in an ESP packet, but the ESP header itself is never encrypted. The following diagram illustrates the ESP packet format:

300-735 Part 11 Q12 112 ESP can operate in transport mode or tunnel mode. In transport mode, ESP encrypts only the original payload data and the resultant ESP trailer, leaving the original IP header unencrypted. The following diagram illustrates the components of an ESP packet in transport mode:

300-735 Part 11 Q12 113 In tunnel mode, ESP encrypts the entire packet, including the original IP header, the original payload data, and the resultant ESP trailer. The following diagram illustrates the components of an ESP packet in tunnel mode:
-
You have issued the following commands to modify the 802.1X configuration on a switch port:
switch(configif)#authentication event fail action next-method switch(configif)#authentication order mab dot1x switch(configif)#authentication priority dot1x mab switch(configif)#authentication event noresponse action authorize vlan 1313
A new host is attached to the switch port. The host’s MAC address is not in the authentication database. In addition, the host does not support 802.1X.
Which of the following statements is true regarding the host in this scenario? (Select the best answer.)
- MAB will learn the new host’s MAC address and authorize the host for network access, and the switch port will ignore the host’s 802.1X authentication attempts.
- MAB will authorize the host for network access? however, the host will lose network access when it attempts to authenticate with 802.1X.
- The host will be assigned to VLAN 1313.
- The host will fail MAB authentication, and the switch will place the port into an unauthorized state.
Explanation:
In this scenario, the host will be assigned to virtual LAN (VLAN) 1313 because the authentication event noresponse action authorize vlan 1313 command has been issued and the host does not support 802.1X authentication. A switch port can be configured to use 802.1X, Media Access Control (MAC) Authentication Bypass (MAB), or Web Authentication (WebAuth) to authenticate clients. The authentication event noresponse action authorize vlan 1313 command specifies the VLAN into which a switch should place a port if it does not receive a response to the Extensible Authentication Protocol over LAN (EAPoL) messages it sends on that port. This enables devices that do not support 802.1X to be assigned to a guest VLAN. When a guest VLAN is configured, the switch will grant non802.1Xcapable clients access to the guest VLAN? however, if an 802.1Xcapable device is detected, the switch will place the port into an unauthorized state and will deny access to all devices on the port.
The authentication order command is used to specify the order in which the switch should attempt the configured authentication methods. By default, a switch will attempt 802.1X authentication before other authentication methods. The authentication order mab dot1x command configures the switch to first use MAB to authenticate a client based on MAC address. If the client’s MAC address is not in the authentication database, the switch will then attempt to authenticate the client with 802.1X. In this scenario, the client’s MAC address is not in the authentication database? therefore, MAB will not authorize the client for network access. Normally, the configured authentication order is mirrored by the priority of each authentication method? however, you can use the authentication priority command to change the priority. If the priority mirrored the authentication order in this scenario, the switch would ignore EAPoL messages if the client was authenticated by MAB and the client would continue to have authorized network access. However, the authentication priority dot1x mab command changes the default priority behavior and assigns a higher priority to 802.1X authentication than it does to MAB. This enables a client to use 802.1X authentication even if it has successfully been authenticated by MAB. Unfortunately, the client is not an 802.1X client.
The authentication event fail action command specifies how the switch should react if an 802.1X client is detected and the client fails to authenticate. There are two configurable parameters: nextmethod and authorize vlanid. The authorize vlanid parameter configures the port to a specific restricted VLAN. The nextmethod parameter configures the switch to attempt authentication by using the next authentication method specified in the authentication order command. If the nextmethod parameter is configured, the switch will indefinitely cycle through authentication methods unless WebAuth is configured. If WebAuth is configured, the authentication process will not loop back to other authentication methods and the switch will ignore EAPoL messages on the port. -
Your supervisor asks you to configure a local CA to help secure digital communications.
Which of the following best describes what your company is most likely implementing? (Select the best answer.)
- a PKI
- symmetric encryption
- asymmetric encryption
- a oneway hash algorithm
Explanation:
Of the available choices, your company is most likely implementing a public key infrastructure (PKI) if you have been asked to configure a local certificate authority (CA) to help secure digital communications. A PKI enables encrypted communication by using a combination of a public and a private key pair. A certificate is bound to a user’s public key, which is the key that is made available to anyone who wishes to send a message to the owner of the key pair. The private key is a secret key that is not shared. If a private key becomes compromised or is no longer needed, the associated CA should be notified immediately so that the certificate revocation list (CRL) can be updated. Certificates typically contain information, such as the owner’s name and contact information, the public key, the key validity period, the digital signature of the certificate, and the location where the CRL can be retrieved.
Although asymmetric encryption is used in a PKI infrastructure, in this scenario you are more specifically implementing a PKI. DiffieHellman (DH), Elliptical Curve Cryptography (ECC), and RSA are asymmetric algorithms. DH is an asymmetric key exchange method. ECC and RSA are asymmetric encryption algorithms. Asymmetric encryption, also known as public key encryption, uses a public key to encrypt data and a different, yet mathematically related, private key to decrypt data. PKI uses a certificate authority to tie a public key to a user ID to further ensure the confidentiality of data. Asymmetric encryption algorithms use more complex mathematical functions than symmetric encryption algorithms. As a result, asymmetric encryption algorithms take longer to encrypt and decrypt data than symmetric encryption algorithms. Other examples of asymmetric encryption algorithms include Digital Signature Algorithm (DSA) and ElGamal.
Your company is not implementing symmetric encryption. Advanced Encryption Standard (AES), RC4, and Triple Data Encryption Standard (3DES) are examples of symmetric encryption algorithms. When symmetric encryption algorithms are used, the same encryption key is used to encrypt and decrypt data. Two types of symmetric algorithms exist: block ciphers and stream ciphers. Block ciphers derive their name from the fact that they encrypt blocks of data. For example, AES encrypts 128bit blocks of data. By contrast, stream ciphers are typically faster than block ciphers because stream ciphers encrypt text of variable length depending on the size of the frame to be encrypted? stream ciphers are not limited to specific block sizes. For example, RC4, a stream cipher, can encrypt data in streams of 8 through 2,048 bits. Other examples of symmetric encryption algorithms include International Data Encryption Algorithm (IDEA), Skipjack, and Blowfish.Your company is not implementing a oneway hash algorithm. Oneway hash algorithms, such as Message Digest 5 (MD5) can be used to create checksums that represent every bit of data that is stored in a file. Future hashes created from the same file can then be compared to the original hash to determine whether anything has changed. Secure Hash Algorithm 1 (SHA1) is another hash algorithm that produces a fixedlength value that corresponds to the content being parsed. -
Which of the following authentication methods were invented by Cisco? (Select 2 choices.)
- PEAP
- EAPFAST
- EAPTLS
- EAPMD5
- LEAP
Explanation:
Lightweight Extensible Authentication Protocol (LEAP) and Extensible Authentication Protocol (EAP)Flexible Authentication via Secure Tunneling (FAST) are both authentication methods that were invented by Cisco.
LEAP is a wireless security method based on 802.1X. The Institute of Electrical and Electronics Engineers (IEEE) 802.1X standard specifies an authentication mechanism using EAP. The 802.1X standard can use digital certificates for authentication. Therefore, it is important to maintain an uptodate public key infrastructure (PKI) configuration. LEAP was developed by Cisco to enable wireless authentication with support for Authentication, Authorization, and Accounting (AAA) protocols, such as Remote Authentication DialIn User Service (RADIUS).
Digital certificates are not required on the client or the server during the EAPFAST authentication process? instead, EAPFAST uses Protected Access Credentials (PACs). EAPFAST is an authentication protocol that can be used for pointtopoint connections and for both wired and wireless links. The EAPFAST authentication process consists of three phases. The first phase, which is optional and is considered phase 0, consists of provisioning a client with a PAC, which is a digital credential that is used for authentication. A PAC can be manually configured on a client, in which case phase 0 is not required. The second phase, which is referred to as phase 1, involves creating a secure tunnel between the client and the server. The final phase, which is referred to as phase 2, involves authenticating the client. If the client is authenticated, the client will be able to access the network.EAPTransport Layer Security (TLS) was not invented by Cisco. EAPTLS is an Internet Engineering Task
Force (IETF) standard that is defined in Request for Comments (RFC) 5216. In addition, Protected EAP
(PEAP) was not invented by Cisco alone. PEAP is an open standard developed by Cisco, Microsoft, and RSA. PEAP and other later variants of EAP, such as EAPTLS, and EAPTunneled TLS (EAPTTLS), are replacing LEAP.
EAPMessage Digest 5 (MD5) was not invented by Cisco. EAPMD5 uses an MD5 hash function to provide security and is therefore considered weak when compared to later methods. EAP is an IETF standard that was originally defined in RFC 2284. -
You have configured antispoofing ACLs and DHCP snooping.
Which of the following are you most likely securing? (Select the best answer.)
- the control plane
- the management plane
- the data plane
- every network plane
Explanation:
Most likely, you are securing the data plane if you have configured antispoofing access control lists (ACLs) and Dynamic Host Configuration Protocol (DHCP) snooping. The data plane is responsible for traffic passing through the router, which is referred to as transit traffic. Therefore, data plane security protects against unauthorized packet transmission and interception. Threats such as IP spoofing, Media Access Control (MAC) address spoofing, Address Resolution Protocol (ARP) spoofing, DHCP spoofing, unauthorized traffic interception, and unauthorized network access can be mitigated and monitored by implementing features such as the following:
– ARP inspection
– Antispoofing ACLs
– DHCP snooping
– Port ACLs (PACLs)
– Private virtual LANs (VLANs)
– Unicast Reverse Path Forwarding (uRPF)
– VLAN ACLs (VACLs)You are securing the control plane if you have configured Control Plane Policing (CoPP), Control Plane Protection (CPPr), routing protocol authentication, and filtering. The control plane is responsible for the creation and maintenance of structures related to routing and forwarding. These functions are heavily dependent on the CPU and memory availability. Therefore, control plane security methods protect against unauthorized traffic destined for the router, which can modify route paths and consume excessive resources. Path modification can be caused by manipulating the traffic generated by routing protocols, VLAN Trunking Protocol (VTP), and Spanning Tree Protocol (STP). Path modification attacks can be mitigated by implementing routing protocol authentication and filtering, VTP authentication, and STP protection features. In addition, excessive CPU and memory consumption can be caused by control plane flooding. Resource consumption attacks can be mitigated by implementing control plane filtering and rate limiting with CoPP and CPPr.
You are securing the management plane if you have configured Authentication, Authorization, and Accounting (AAA) solutions and Management Plane Protection (MPP). Device configuration protection is associated with the management plane. Management plane security protects against unauthorized device access and configuration. Unauthorized access can be mitigated by implementing a strong AAA solution and by implementing MPP, which creates protected management channels over which administrators must connect in order to access device administration features. Management traffic can be encrypted by implementing Secure Shell (SSH). You can mitigate unauthorized configuration of a device by implementing RoleBased Access Control (RBAC), whereby administrators are limited to using only the features they need to accomplish their jobs. Detection and logging of management plane access can be performed by implementing Simple Network Management Protocol version 3 (SNMPv3) and Syslog servers. -
You issue the following commands on a Cisco ASA. No other interfaces have been configured.
asa(config)#interface gigabitethernet 0/1 asa(configif)#speed 1000 asa(configif)#duplex full asa(configif)#securitylevel 0 asa(configif)#nameif inside asa(configif)#ip address 10.1.1.1 255.255.255.0 asa(configif)#no shutdownasa(configif)#exit asa(config)#telnet 10.1.1.0 255.255.255.0 inside asa(config)#telnet timeout 30
Which of the following statements is true regarding the resulting configuration? (Select the best answer.)
- Telnet sessions will time out after 30 seconds of inactivity.
- The ASA will deny SSH connections to the interface.
- The ASA will reassign the interface a security level of 100.
- Telnet sessions will be denied because a security level is manually assigned.
Explanation:
In this scenario, the Cisco Adaptive Security Appliance (ASA) will deny Telnet sessions to the
GigabitEthernet 0/1 interface because a security level is manually assigned. Normally, Telnet traffic is not permitted to the interface with the lowest security. However, if there is only one configured interface and it has been configured with a security level of 100, Telnet traffic is permitted even though the interface is simultaneously the interface with the lowest security and the highest security. Because the interface in this scenario has been manually assigned the lowest security level of 0, the Telnet session will be denied. If there were other active interfaces on the ASA, a Telnet session would be permitted to the interface with the lowest security only if that session was protected by a virtual private network (VPN) tunnel terminating on the interface.
The ASA will not deny Secure Shell (SSH) connections to the interface. Although there are several methods for working around Telnet access restrictions of the ASA, Cisco recommends disabling Telnet and using more secure methods for management access, such as SSH or Secure Hypertext Transfer Protocol (HTTPS) instead? neither HTTPS nor SSH is restricted by the security level of an interface.
The block of commands in this scenario configures the GigabitEthernet 0/1 interface to operate in full duplex mode at a speed of 1000 megabits per second (Mbps), assigns the interface a security level of 0, names the interface “inside”, and assigns an IP address 10.1.1.1 with a network mask of 255.255.255.0. In addition, the no shutdown command enables the interface. The telnet commands define a network range that is permitted to Telnet to the inside interface and configure a Telnet idletimeout value. The default security level on an ASA is 0? however, the inside interface is an exception to this rule because it is automatically assigned a security level of 100 if a security level is not explicitly configured. An interface can be assigned any integervalued security level from 0 through 100.
Telnet sessions will not time out after 30 seconds of activity. The telnet timeout 30 command specifies an inactivity timeout length of 30 minutes, not 30 seconds. The telnet timeout command accepts an integer value from 1 through 1440 to specify the number of minutes a Telnet session can remain idle before the ASA closes the connection. -
Which of the following vulnerabilities did the Stuxnet worm exploit on target hosts? (Select 2 choices.)
- a buffer overflow vulnerability in the DCOM RPC service
- a buffer overflow vulnerability in IIS software
- a buffer overflow vulnerability in Microsoft SQL Server
- a remote code execution vulnerability in the printer spooler service
- a remote code execution vulnerability in the processing of .lnk files
Explanation:
Stuxnet exploited vulnerabilities in both the printer spooler service and the processing of .lnk files. Stuxnet was used in an act of cyber warfare against Iranian industrial control systems (ICSs). It was written to target specific ICSs by modifying code on programmable logic controllers (PLCs). Stuxnet initially exploited vulnerabilities in the printer spooler service? however, later variants exploited a vulnerability in the way that Windows processes shortcuts (.lnk files). Research from Symantec published in 2011 indicated that at the time, over 60% percent of the Stuxnetaffected hosts had been in Iran. Symantec analyzed Stuxnet and its variants and discovered that five organizations were the primary targets of infection and that further infections were likely collateral damage from the aggressive manner in which the worm spreads throughout the network. Given the considerable cost in resources and manhours that would have been required to craft the Stuxnet worm, it was theorized that it was likely intended to sabotage highvalue targets such as nuclear materials refinement facilities.
The Blaster worm exploited a buffer overflow vulnerability in the Distributed Component Object Model (DCOM) Remote Procedure Call (RPC) service on Microsoft Windows hosts. The worm carried a destructive payload that configured the target host to engage in Denial of Service (DoS) attacks on Microsoft update servers. Before Microsoft released a patch, several other worms exploited the vulnerability. For example, the Welchia worm targeted the same vulnerability. Welchia was developed to scan the network for vulnerable machines, infect them, and then remove the Blaster worm if present. It was even designed to download and install the appropriate patch from Microsoft to fix the vulnerability that it and Blaster initially exploited to infect the target machine. However, despite the goodnatured design intentions of the Welchia worm, its networkscanning component inadvertently caused DoS attacks on several large networks, including those of the United States armed forces.
SQL Slammer exploited a buffer overflow vulnerability in Microsoft Structured Query Language (SQL) server software. SQL Slammer spread at a tremendous rate and was reported to have infected as many as 12,000 servers per minute. Its high scanning rate generated enough traffic on many networks to effectively produce DoS effects as collateral damage to the infection.
Code Red exploited a buffer overflow vulnerability in Microsoft Internet Information Server (IIS) software. Although not as efficient as SQL Slammer, Code Red still managed to infect as many as 2,000 hosts per minute. The initial Code Red variant failed to infect more than a single set of IP addresses? however, a later variant was reported to have affected over 350,000 hosts within the first 14 hours of its release into the wild. -
Which of the following security applications is least likely to be included in a vendor’s desktop security suite? (Select the best answer.)
- antivirus software
- a HIPS
- a personal firewall
- a proxy server
Explanation:
Of the available choices, a proxy server is least likely to be included in a vendor’s desktop security suite. A proxy server is typically an application layer gateway that provides resource caching and traffic filtering for a particular class of traffic, such as web content. Although you could install a proxy server locally on a host, it would not have a significant effect on malicious traffic directed at the host nor would it be able to analyze its content.
A Hostbased Intrusion Prevention System (HIPS) can be installed on a host to analyze and prevent malicious traffic on that host and is more likely to be included in a vendor’s desktop security suite than a proxy server. An Intrusion Prevention System (IPS) can be used to actively monitor, analyze, and block malicious traffic before it infects devices. HIPS software can be installed on a host computer to protect that computer against malicious traffic. By contrast, a Networkbased IPS (NIPS) is an independent operating platform, often a standalone appliance or a hardware module installed in a chassis. A NIPS device can be installed inline on a network to monitor and prevent malicious traffic from being sent to other devices on the network. One advantage of using a NIPS over a HIPS is that a NIPS can detect lowlevel network events, such as the scanning of random hosts on the network? a HIPS can only detect scans for which it is the target. A HIPS and a NIPS can be used together to provide an additional layer of protection.
A personal firewall is more likely to be included in a vendor’s desktop security suite than a proxy server. A personal firewall can work in conjunction with other software, such as a HIPS or a NIPS, to protect a host from a wider array of malicious activities. For example, Cisco Advanced Malware Protection (AMP) for Endpoints can work in conjunction with a personal firewall to provide threat protection and advanced analytics.
Antivirus software is more likely to be included in a vendor’s desktop security suite than a proxy server. Antivirus software monitors the file system and memory space on a host for malicious code. Although the antivirus software might protect the host from malicious file execution, it would be unable to protect the host from malicious traffic. Some antivirus vendors offer integrated security suites, which feature personal firewall, HIPS, antivirus, and antimalware components. -
Which of the following commands should you issue to allow communication between different ASA interfaces that share the same security level? (Select the best answer.)
- samesecuritytraffic permit interinterface
- samesecuritytraffic permit intrainterface
- securitylevel 0
- securitylevel 100
- established
Explanation:
You should issue the samesecuritytraffic permit interinterface command on a Cisco Adaptive Security Application (ASA) to allow communication between different interfaces that share the same security level. Typically, interfaces with the same security level are not allowed to communicate with each other.
You should not issue the samesecurity traffic permit intrainterface command to allow communication between different interfaces that share the same security level. You should issue the samesecuritytraffic permit intrainterface command to allow a packet to exit an ASA through the same interface through which it entered, which is also known as hairpinning. By default, an ASA does not allow packets to enter and exit through the same physical interface. However, because multiple logical virtual LANs (VLANs) can be assigned to the same physical interface, it is sometimes necessary to allow a packet to enter and exit through the same interface. The samesecuritytraffic permit intrainterface command allows packets to be sent and received from the same interface even if the traffic is protected by IP Security (IPSec) security policies. Another scenario for which you would need to use the samesecuritytraffic permit intrainterface command is if multiple users need to connect via virtual private network (VPN) through the same physical interface. These users will not be able communicate with one another unless the samesecuritytraffic permit intrainterface command has been issued from global configuration mode.
You should not issue either the securitylevel 0 command or the securitylevel 100 command to allow communication between different interfaces that share the same security level. The securitylevel command is used to set the security level on a physical interface. Security level 0 should be used to achieve the lowest security level possible, whereas security level 100 should be used to achieve the highest security level available.
You should not issue the established command to allow communication between different interfaces that share the same security level. The established command is used to allow inbound traffic on any interface that has already established an outbound connection with the ASA. For example, you could issue the established tcp 4567 0 command to configure the ASA to allow an external host to initiate a connection through the ASA to an internal host after the internal host has first established a Transmission Control Protocol (TCP) connection to port 4567 on the external host. The established command is often used to support protocols such as streaming media protocols that negotiate the ports for return traffic.