300-735 : Automating Cisco Security Solutions (SAUTO) : Part 13
-
Which of the following can be used by Cisco IPS devices to report intrusion alerts? (Select 2 choices.)
- SDEE
- SNMPv1
- SNMPv2
- SNMPv3
- Syslog
Explanation:
Cisco Intrusion Prevention System (IPS) devices can use either Security Device Event Exchange (SDEE) or Syslog to report intrusion alerts. SDEE is a protocol that was designed for reporting security events by using an encrypted and authenticated session between devices. For example, Cisco IPS Manager Express (IME) can monitor up to 10 security sensors by using the SDEE protocol.
The Syslog protocol is used to transmit logging information, including security events, from a device to a syslog server. However, data sent using Syslog is typically sent as plain text. An attacker could intercept the messages and view the contents of the messages. By default, when User Datagram Protocol (UDP) is used, Syslog data is sent over UDP port 514, and when Transmission Control Protocol (TCP) is used, Syslog data is sent over TCP port 1468.
Cisco IPS devices do not use Simple Network Management Protocol (SNMP) to report intrusion alerts.
SNMP is used to monitor and manage network devices by collecting statistical data about those devices. Three versions of SNMP currently exist. SNMP version 1 (SNMPv1) and SNMPv2 do not provide encryption? password information, known as community strings, is sent as plain text with messages. If an attacker intercepts the message, the attacker can view the password information. SNMPv3 improves upon SNMPv1 and SNMPv2 by providing encryption, authentication, and message integrity to ensure that the messages are not tampered with during transmission. Thus, whenever possible, you should use SNMPv3 instead of SNMPv1 or SNMPv2. SNMP uses UDP port 161 for SNMP control traffic and UDP port 162 for SNMP trap traffic. -
You are using ASDM to verify a VPN configuration made by another administrator on an ASA. Please click exhibit to examine the network configuration.
Exhibit:

300-735 Part 13 Q02 115 A user accesses the VPN by typing https://203.0.113.1/BosonUsers in a browser’s location bar. Which interface will accept the connection? (Select the best answer.)
- the DMZ interface
- the inside interface
- the outside interface
- the mgmt interface
Explanation:
The outside interface will accept the connection when a user accesses the virtual private network (VPN) by typing https://203.0.113.1/BosonUsers in a browser’s location bar. In this scenario, the user is accessing the clientless Secure Sockets Layer (SSL) VPN, which enables VPN connectivity by using a browser instead of a VPN client. In Cisco Adaptive Security Device Manager (ASDM), you can determine the interface on which the clientless SSL VPN is listening by navigating to Configuration > Remote Access VPN >
Clientless SSL VPN Access > Connection Profiles. The Enable interfaces for clientless SSL VPN access area contains check boxes that indicate the interfaces that are allowed access to the clientless SSL VPN. In this scenario, only the outside interface is selected, as shown in the following exhibit:
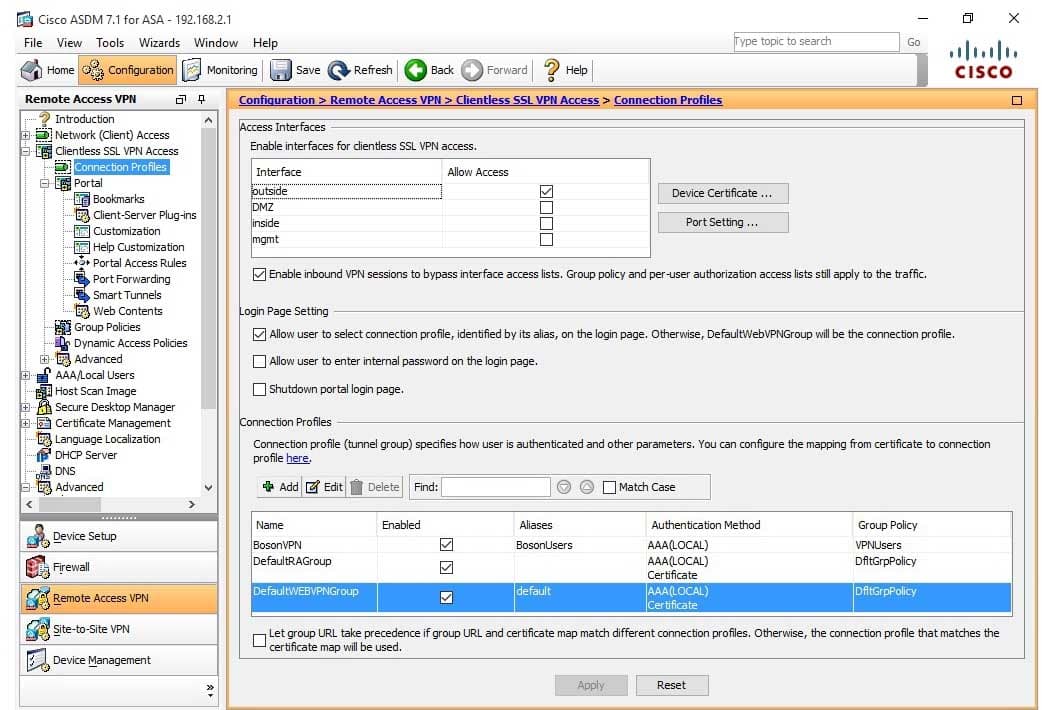
300-735 Part 13 Q02 116 -
You are using ASDM to verify a VPN configuration made by another administrator on an ASA. Please click exhibit to examine the network configuration.
Exhibit:
300-735 Part 13 Q03 117 A user accesses the VPN by typing https://203.0.113.1/BosonUsers in a browser’s location bar. How will the user be authenticated to the VPN? (Select the best answer.)
- by a RADIUS server
- by a TACACS+ server
- by HTTP credentials
- by the local database
- by a certificate
Explanation:
The user will be authenticated to the virtual private network (VPN) by the local database when the user accesses the VPN by typing https://203.0.113.1/BosonUsers in a browser’s location bar. In this scenario, the location BosonUsers is an alias for the Cisco Adaptive Security Appliance (ASA) connection profile named BosonVPN, as shown in the following exhibit:

300-735 Part 13 Q03 118 By navigating to Configuration > Remote Access VPN > Clientless SSL VPN Access> Connection Profiles, you can also determine that the authentication method for the connection profile named BosonVPN is AAA(LOCAL), which indicates that users will be authenticated by using the local Authentication, Authorization, and Accounting (AAA) database instead of a AAA server or a certificate. Although multiple authentication methods can be configured for a single connection profile, in this scenario only the AAA(LOCAL)method is configured for the BosonVPN connection profile. If you were to select the BosonVPN connection profile, you could modify the way in which BosonVPN users authenticate to the VPN, as shown in the following exhibit:
-
You are using ASDM to verify a VPN configuration made by another administrator on an ASA. Please click exhibit to examine the network configuration.
Exhibit:
300-735 Part 13 Q04 120 A user prefers to access the BosonVPN by some means other than a browser. Which of the following should you tell the user? (Select the best answer.)
- The user must use clientless SSL VPN access at this time.
- The user will need to install the SSL VPN client.
- The user can connect by using IPsec instead.
- The user can connect by using L2TP instead.
Explanation:
You should tell the user that the user must use clientless Secure Sockets Layer (SSL) virtual private network (VPN) access at this time, because that is the only method that is currently enabled for the Cisco Adaptive Security Appliance (ASA) BosonVPN connection profile in this scenario. You can determine which types of VPN tunneling protocols are enabled for a given connection profile by navigating to Configuration > Remote Access VPN > Clientless SSL VPN Access > Group Policies in Cisco Adaptive Security Device Manager (ASDM), as shown in the following exhibit:

300-735 Part 13 Q04 121 In the exhibit above, only the sslclientless tunneling protocol is enabled for VPN users who are associated with the connection profiles named BosonVPN and bsnadmin. You can modify which tunnel protocols are available for a given profile by selecting the appropriate group policy.
-
You are using ASDM to verify a VPN configuration made by another administrator on an ASA. Please click exhibit to examine the network configuration.
Exhibit:
300-735 Part 13 Q05 122 A user accesses the VPN by typing https://203.0.113.1/default in a browser’s location bar. Which of the following methods will authenticate the user? (Select 2 choices.)
- a RADIUS server
- a TACACS+ server
- the HTTP credentials
- the local database
- a certificate
Explanation:
A user who accesses the virtual private network (VPN) by typing https://203.0.113.1/default in a browser’s location bar will be authenticated by using both the Cisco Adaptive Security Appliance (ASA) Authentication, Authorization, and Accounting (AAA) local database and by using a certificate. In this scenario, the defaultalias is associated with the Default WEB VPN Group connection profile. You can determine which profile uses the alias by navigating to Configuration > Remote Access VPN > Clientless SSL VPN Access > Connection Profiles in Cisco Adaptive Security Device Manager (ASDM), as shown in the following exhibit:

300-735 Part 13 Q05 123 Based on the exhibit above, you can determine that the Default WEB VPN Group connection profile is configured with two authentication methods: AAA(LOCAL) and Certificate. Although multiple AAA servers can be configured for a single connection profile, in this scenario only the AAA(LOCAL) AAA server is configured for the Default WEB VPN Group connection profile. If you were to select the Default WEB VPN Group connection profile, you could modify the way in which default users authenticate to the VPN, as shown in the following exhibit:

300-735 Part 13 Q05 124 The AAA Server Group dropdown menu enables you to select a different AAA authentication server if one has been configured. If a server other than LOCAL is selected, you can select the Use LOCAL if Server Group fails check box to use the local database as a backup authentication method for whatever AAA server is in use.
-
You are using ASDM to verify a VPN configuration made by another administrator on an ASA. Please click exhibit to examine the network configuration.
A user accesses the VPN by typing https://203.0.113.1/default in a browser’s location bar.
Which of the following is true? (Select the best answer.)
Exhibit:
300-735 Part 13 Q06 125 - The local database will be used to authenticate only if RADIUS fails.
- The group policy named DfltGrpPolicy will be applied.
- The user’s DNS server will be boson.com.
- The session will fail because Clientless SSL VPN is not enabled.
Explanation:
The group policy named DfltGrpPolicy will be applied if the user accesses the virtual private network (VPN) by typing https://203.0.113.1/default in a browser’s location bar. In this scenario, the default alias is associated with the Cisco Adaptive Security Appliance (ASA) connection profile named Default WEB VPN Group. You can determine which aliases are associated with which connection profiles by navigating to Configuration > Remote Access VPN > Clientless SSL VPN Access > Connection Profiles in Cisco Adaptive Security Device Manager (ASDM), as shown in the following exhibit:

300-735 Part 13 Q06 126 You can determine which group policy will be applied by examining the value in the Group Policy column of the connection profile’s entry in the Connection Profiles area of the Connection Profiles screen. If you wanted to modify the group policy value in ASDM, you would select the appropriate connection profile. The Group Policy dropdown menu will then enable you to select the group policy that should be applied to the connection profile, as shown in the following exhibit:
-
Your corporate network uses MobileIron as an MDM for ISE. You have been informed that a user has lost his phone and that you must perform a selective wipe on the device.
Which of the following will not be removed from the device during the selective wipe? (Select the best answer.)
- the MobileIron app
- the CA certificate for the WiFi profile installed by ISE
- corporate applications installed by MDM
- the MDM profile and all of its subprofiles
Explanation:
The certificate authority (CA) certificate for the WiFi profile installed by Cisco Identity Services Engine (ISE) is not removed when you perform a selective wipe. ISE is a nextgeneration Authentication, Authorization, and Accounting (AAA) platform with integrated posture assessment, network access control, and client provisioning. ISE integrates with a number of Mobile Device Management (MDM) frameworks, such as MobileIron and AirWatch. From ISE, you can easily provision network devices with native supplicants available for Microsoft Windows, Mac OS X, Apple iOS, and Google Android. The supplicants act as agents that enable you to perform various functions on the network device, such as installing software or locking the screen with a personal identification number (PIN) lock.
For devices like phones, ISE relies on MDM servers to carry out the specific administrative actions selected in ISE. For example, when a selective wipe is selected for a device in ISE, a request is made to the appropriate MDM server to carry out the action. The MDM server communicates with its corresponding agent and removes all corporate applications and installed profiles, including any subprofiles. The selective wipe also removes the MDM agent, which in this scenario is the MobileIron App. Through an MDM server, ISE can perform a full wipe, a selective wipe, or a PIN lock depending on the severity of the security risk of the lost phone.
An administrator can also initiate a selective wipe if an employee is terminated. However, the administrator should also take steps to blacklist the device within ISE and remove the user accounts privileges so that the user cannot reenroll the device. The administrator can then force the user’s device to attempt an immediate reauthentication against ISE by revoking the user certificate on the CA server. This will cause the device to match the blacklist upon its attempt to reenroll. -
Which of the following statements is true regarding security contexts on a new Cisco ASA in multiple context mode? (Select the best answer.)
- You cannot delete the current admin context.
- You can delete a single security context with the clear configure context command.
- You can delete all security contexts with the no context command.
- You cannot delete a security context from the active unit in a failover configuration.
- You can delete a security context only by editing the system configuration.
Explanation:
You can delete a security context only by editing the system configuration on a new Cisco Adaptive Security Appliance (ASA). Security contexts divide a single ASA into multiple virtual devices with unique policies. This division enables a single physical ASA to provide security services for different departments while keeping the departments logically separated. The system configuration contains the startup configuration and resides in the system execution space, which is also called the system context. You can add, modify, and delete security contexts from the system execution space. You can issue the contextcommand from configuration mode to create a new security context and to enter context configuration mode, which is used to edit an existing security context. Conversely, you can issue the no context command from configuration mode to delete a single security context. For example, you can issue the no context CTX1 command to delete a context named CTX1.
You cannot issue the no context command to delete the current admin context. You can delete the current admin context only if you delete all of the configured security contexts on the ASA. You can issue the clear configure context command from the system context to remove all security contexts from the system configuration of an ASA. You can issue the show context command to determine the name of the current admin context and to display a list of the security contexts currently configured on an ASA. Sample output from the show context command is shown below:

300-735 Part 13 Q08 128 The current admin context can be identified by the * character to the left of the context name in the output of the show context command.
You can delete a security context from the active unit in a failover configuration. When you issue the no context command on the active unit of a failover pair, the security context will also be deleted from the standby unit after the configuration synchronization is complete. Cisco warns that the synchronization process can take a few seconds to complete and that any error messages related to the deleted context are likely due to synchronization delay and should therefore be ignored. -
Which of the following commands can be used to determine the SPI that a router will use to reach an active IPSec peer? (Select the best answer.)
- show crypto ipsec sa
- show crypto session
- show crypto isakmp sa active
- show crypto ipsec securityassociation
Explanation:
The show crypto ipsec sa command can be used to determine the Security Parameter Index (SPI) that a router will use to reach an active IP Security (IPSec) peer. Each IPSec security association (SA) is uniquely identified by its corresponding IPSec peer address, security protocol, and SPI. Because IPSec SAs are unidirectional, two SAs are required between active IPSec peers: an inbound SA and an outbound SA. The SPI associated with the outbound SA is generated by the local peer during phase 2 of the Internet Key
Exchange (IKE) negotiation process and is used by the remote peer as the inbound SPI associated with this SA. Likewise, the SPI associated with the inbound SA on the local peer corresponds to the outbound SPI that was generated by the remote peer during its portion of phase 2 negotiations.
The show crypto ipsec sa command displays detailed information about IPSec SAs, including the IP addresses of the crypto endpoints (IPSec peers), the number of packets encrypted and decrypted, the security protocol, and the corresponding SPIs. For example, the following partial command output shows the SPIs associated with the SAs between the local peer, 10.10.10.2, and the remote peer 10.20.20.2 on interface FastEthernet 0/0:

300-735 Part 13 Q09 129 The show crypto session command displays a summary of all current IKE SAs and their corresponding IPSec SAs? however, the command does not display the SPI that a router will use to reach an active IPSec peer. Sample output from the show crypto sessioncommand is shown below:
The show crypto isakmp sa active command displays active IKE SAs, not configuration and operational details of an IPSec connection. SA information is displayed in a summarized format, as shown below:
dst src state connid slot status
10.20.20.2 10.10.10.2 QM_IDLE 1 0 ACTIVE
For each SA, the dst field displays the IP address of the remote IKE peer, whereas the src field reveals the IP address of a local interface. An active IKE SA is typically in the QM_IDLE state, as indicated by the state field. The state field indicates the IKE negotiation state of an SA. An SA in the QM_IDLE state indicates that phase 1 negotiations have completed and that the SA is ready for quick mode negotiation of an IPSec SA. Because multiple SAs can exist between a particular source and destination, each SA is assigned a unique connection ID, as shown in the connid field. You should issue the show crypto isakmp sa command without the active keyword to display all current IKE SAs.
The show crypto ipsec securityassociation command displays the SA lifetime configured for an existing IPSec SA. You can issue the crypto ipsec security association lifetime seconds seconds command from global configuration mode to configure the SA lifetime. The command output below displays a default SA lifetime configuration:
Security association lifetime: 4608000 kilobytes/3600 seconds -
Which of the following can be installed on a host to analyze and prevent malicious traffic on that host? (Select the best answer.)
- a HIDS
- a HIPS
- a NIPS
- a NIDS
Explanation:
A Hostbased Intrusion Prevention System (HIPS) can be installed on a host to analyze and prevent malicious traffic on that host. An Intrusion Prevention System (IPS) can be used to actively monitor, analyze, and block malicious traffic before it infects devices. Typically, an IPS is configured to block only traffic that has been definitively marked as malicious. Traffic that is suspect but has not been confirmed as malicious is referred to as gray area trafficand is not discarded by an IPS.
HIPS software can be installed on a host computer in conjunction with a hostbased firewall to protect the computer and the data it holds against malicious traffic. Because HIPS software is installed on a host computer, it can directly access the host operating system (OS) as well as encrypted traffic on the host. By contrast, a Networkbased IPS (NIPS) device is a standalone platform that can be installed in conjunction with networkbased firewalls to monitor and prevent malicious traffic from being sent to any device on the network.
An Intrusion Detection System (IDS) is similar to an IPS, but IDS devices do not sit inline with traffic. Thus IDS devices are primarily used for monitoring traffic and hosts rather than actively preventing attacks. If malicious activity is discovered, an IDS device can send an alert to a management station. However, because the IDS does not sit inline with traffic, the traffic will have already affected the network or host by the time the alert is sent. A Hostbased IDS (HIDS) can be used to monitor activity on a single host? a HIDS can monitor traffic being sent to and from a host and can monitor OS files for suspicious changes. By contrast, a Networkbased IDS (NIDS) can be used to monitor all network traffic. -
Which of the following is an open framework used to guide an organization in making software security decisions that are in alignment with the organization’s risk profile? (Select the best answer.)
- SAMM
- ZAP
- WTE
- OWTF
Explanation:
The Software Assurance Maturity Model (SAMM) is an open framework used to guide an organization in making software security decisions that are in alignment with the organization’s risk profile. The SAMM is published by the Open Web Application Security Project (OWASP), which is a multinational, notforprofit organization that provides frameworks, documentation, tools, and community forums with a focus on application security. Like all OWASP documentation, the SAMM is licensed under the Creative Commons AttributionShare Alike 3.0 License, which is a common Free/Libre and Open Source Software (FLOSS) license that allows redistribution and modification of the original content with the appropriate attribution and the requirement to distribute the derivative work under the same license as the original.
The Offensive Web Testing Framework (OWTF), Zed Attack Proxy (ZAP), and Web Testing Environment (WTE) are not open frameworks used to guide an organization in making software security decisions that are in alignment with the organization’s risk profile. OWTF is a penetration testing tool designed to automate some of the lower level and tedious parts of the penetration testing process. Its aim is to provide the penetration tester with more time to analyze and investigate complex vulnerabilities. ZAP is an integrated penetration testing tool for web applications. It provides automated scanning tools and a suite of tools that can be used to manually probe for vulnerabilities. WTE is a consolidated testing environment that can be distributed as a virtual machine, a bootable image, or as individual Linux packages. WTE aims to provide a sandbox in which testers, developers, and trainers can interact with security tools provided by OWASP and other FLOSS developers. WTE is based on the OWASP Live CD Project. -
Which of the following attacks involves overwhelming a switch’s CAM table? (Select the best answer.)
- ARP poisoning
- ARP spoofing
- MAC flooding
- MAC spoofing
Explanation:
A Media Access Control (MAC) flooding attack involves overwhelming a switch’s content addressable memory (CAM) table. Switches and bridges store learned MAC addresses in the CAM table, which is also known as the MAC address table. When the CAM table becomes full, no more MAC addresses can be learned. If a switch receives traffic destined for a MAC address that is not in its MAC address table, the switch floods the traffic out every port except the port that originated the traffic. Consequently, in a MAC flooding attack, an attacker attempts to fill the CAM table so that any further traffic will be sent to all ports. Then, because traffic is flooded out every interface, the attacker can view any traffic that is sent to the switch.
A MAC spoofing attack involves using the MAC address of a legitimate host on the network in order to bypass port security measures, not overwhelming a switch’s CAM table. Normally, the MAC address associated with a host corresponds to the unique, burnedin address (BIA) of its network interface. However, in a MAC spoofing attack, a malicious user virtually modifies the BIA to match the MAC address of the legitimate host on the network. Mimicking the MAC address of a known host can be used to overcome simple security measures such as Layer 2 access control lists (ACLs).
An Address Resolution Protocol (ARP) poisoning attack, which is also known as an ARP spoofing attack, involves sending gratuitous ARP (GARP) messages to a target host. The GARP messages associate the attacker’s MAC address with the IP address of a valid host on the network. Subsequently, traffic sent to the valid host address will go to the attacker’s computer rather than to the intended recipient. -
Which of the following statements are true regarding a ZFW? (Select 2 choices.)
- A zone can contain more than one interface.
- An interface can reside in more than one zone.
- The firewall can operate in transparent mode.
- Stateful packet inspection is supported for multicast traffic.
- Stateful packet inspection is supported for IPv6 traffic.
Explanation:
With a zonebased policy firewall (ZFW), a zone can contain more than one interface and the firewall can operate in transparent mode. ZFW is the latest iteration of Cisco’s stateful firewall implementation, which was formerly called ContextBased Access Control (CBAC). With ZFW, virtual security zones are specified and then interfaces are assigned to the appropriate zone. A zone may contain more than one interface? however, an interface may not be assigned to more than one zone.
By default, all traffic is implicitly permitted to flow between interfaces that have been assigned to the same zone? however, all traffic between zones is blocked. In addition, all traffic to and from an interface is implicitly blocked by default when the interface is assigned to a zone, but there are a few exceptions. Traffic to or from other interfaces in the same zone is permitted, as is traffic to or from the router itself.
In order for traffic to flow between zones, stateful packet inspection policies must be configured to explicitly permit traffic between zones. Inspection rules can be created for a large number of traffic types, including the following:
– Domain Name System (DNS)
– Internet Control Message Protocol (ICMP)
– Network Basic Input/Output System (NetBIOS)
– Sun Remote Procedure Call (RPC)
However, stateful inspection of IP version 6 (IPv6) traffic and multicast traffic, such as Internet Group Management Protocol (IGMP), is not supported by a ZFW and must be handled by other security features, such as Control Plane Policing (CoPP).
A ZFW can operate in transparent mode or in routed mode. In transparent mode, a ZFW operates as a Layer 2 firewall, bridging traffic between interfaces and filtering traffic at Layer 3 through Layer 7. The trusted and untrusted interfaces of the firewall are connected to the same IP subnet, and the firewall bridges traffic between the interfaces. By contrast, a ZFW in routed mode operates as a Layer 3 firewall, routing traffic between interfaces and filtering traffic at Layer 3 through Layer 7. The trusted and untrusted interfaces of the firewall are on different IP subnets, and the firewall routes traffic between the interfaces. -
Which of the following is true regarding loop guard? (Select the best answer.)
- Loop guard should be used in conjunction with root guard.
- Loop guard should be used in conjunction with PortFast.
- Loop guard places inconsistent ports into the blocking state.
- Loop guard is used to disable ports that receive BPDUs.
Explanation:
Loop guard places inconsistent ports into the blocking state. Loop guard prevents a switch port from transitioning to the forwarding state when it stops receiving bridge protocol data units (BPDUs)? this prevents switching loops from occurring. A port configured with loop guard that stops receiving BPDUs will be put into the loopinconsistent state, as shown in the following output:%SPANTREE4LOOPGUARDBLOCK: No BPDUs were received on port 0/1 in vlan 4. Moved to loop inconsistent state
After the port starts receiving BPDUs again, loop guard enables the port to transition through the normal Spanning Tree Protocol (STP) states.
Loop guard should not be used in conjunction with root guard. Root guard is used to prevent newly introduced switches from being elected the new root. This allows administrators to maintain control over which switch is the root. When STP is used, the device with the lowest bridge priority is elected the root. If an additional device is added to the network with a lower priority than the current root, it will send superior BPDUs and be elected the new root. However, this could cause the network to reconfigure in unintended ways. To prevent this, root guard can be applied. If root guard is enabled on a loop guard-enabled port, loop guard will be automatically disabled.
Loop guard should not be used in conjunction with PortFast. PortFast reduces convergence time by immediately placing edge ports into a forwarding state. PortFast is recommended for ports that connect to enduser devices, such as desktop computers. In addition, PortFast cannot be used with loop guard. If PortFast is enabled on a loop guard-enabled port, loop guard will be automatically disabled.
Loop guard is not used to disable ports that receive BPDUs. Instead, BPDU guard is used to disable ports that erroneously receive BPDUs. BPDU guard is applied to edge ports that have PortFast enabled. Because PortFast automatically places ports into a forwarding state, a switch that has been connected to a PortFastenabled port could cause switching loops. However, when BPDU guard is applied, the receipt of a BPDU on a port with BPDU guard enabled will result in the port being placed into an errdisable state, which prevents loops from occurring. -
What is the minimum DH modulus size recommended by Cisco to provide acceptable security when DH must be used instead of an NGE algorithm? (Select the best answer.)
- 768 bits
- 1,024 bits
- 2,048 bits
- 3,072 bits
Explanation:
The minimum DiffieHellman (DH) modulus size recommended by Cisco to provide acceptable security when DH must be used instead of a Next Generation Encryption (NGE) algorithm is 2,048 bits. NGE algorithms are a collection of cryptographic technologies that are efficient, scalable, and expected to provide reliable security for at least the next decade. Because of recent advances in computing power, many cryptographic algorithms no longer provide adequate security. DH algorithms with a smaller modulus size do not provide a level of security that is likely to meet the confidentiality requirements of the enterprise over the next decade.
Increasing the modulus size used by an algorithm can provide a higher level of security? however, if the algorithm is inherently inefficient, the increased modulus size can adversely affect the performance of the device using the algorithm. For maximum security without using an NGE, Cisco recommends using DH with a 3,072bit modulus (DH3072)? however, because DH is not particularly efficient when configured with a large modulus, Cisco considers a 2,048 bit modulus as an acceptable compromise between security and efficiency. Any modulus size less than 2,048 bits, such as 1,024 bits or 758 bits, is not considered to provide an acceptable level of security.
Ideally, standard DH should be replaced with an NGE such as Elliptical Curve DH with a 384bit modulus (ECDH384) for improved security without a negative impact on performance or a loss of scalability. Other examples of NGE algorithms are Advanced Encryption Standard (AES) in Galois/Counter Mode (GCM) and Secure Hash Algorithm 2 (SHA2), which includes SHA with a 256bit digest (SHA256) and SHA with a 512bit digest (SHA512). -
Which of the following is a QoS feature that can apply policies to individual controlplane subinterfaces? (Select the best answer.)
- CoPP
- CPPr
- MPP
- uRPF
Explanation:
Control Plane Protection (CPPr) is a Quality of Service (QoS) feature that can apply policies to individual controlplane subinterfaces. Control plane traffic is traffic that is destined to the router and that requires CPU intervention for processing. Because control plane traffic requires CPU intervention, it is possible to overload the CPU with a surge of traffic. When the CPU is overloaded, the router might be unable to update its routing information and transit traffic can be affected. With CPPr, traffic from the aggregate control plane interface is classified into one of three control plane subinterfaces: host, transit, or Cisco Express Forwarding (CEF) exception. QoS policies can then be applied to each of the subinterfaces individually.
Like CPPr, Control Plane Policing (CoPP) is a QoS feature that can be used to limit the type and amount of traffic that reaches the control plane. However, CoPP policies are applied to the aggregate control plane interface and not to the individual control plane subinterfaces.
Management Plane Protection (MPP) is a security feature that can specify one or more interfaces as management interfaces, not a QoS feature that can apply policies to individual control plane subinterfaces. A management interface is an interface that is permitted to receive management traffic, which is traffic from a specific set of network protocols that is destined for the router. Once MPP is enabled, only specified types of management traffic are permitted on their respective management interfaces. MPP simplifies the configuration of management plane security policies because it reduces the number of configuration steps required to restrict management access to the router. Without MPP, you would need to create the appropriate access control lists (ACLs) and apply them in the inbound direction to every interface on the router if you wanted to limit access to one or more interfaces and management protocols.
Unicast Reverse Path Forwarding (uRPF) is an antispoofing mechanism that verifies that the source address of a packet is reachable from the interface on which the packet was received, not a QoS feature that can apply policies to individual controlplane subinterfaces. If uRPF is used in conjunction with an ACL, it can cause packets to become packetswitched. Packet switching requires CPU intervention and can create a burden on the control plane. -
Which of the following is an independent cryptographic processor that provides hardwarebased authentication services for PCs? (Select the best answer.)
- TPM
- TNC
- MTM
- TMI
Explanation:
A Trusted Platform Module (TPM) is an independent cryptographic processor that provides hardwarebased authentication and full disk encryption services for personal computers (PCs). TPM uses an encrypted memory module, which provides an additional security layer for properties such as passwords, digital certificates, and encryption keys. Because the encryption keys are stored in the TPM module, any data stored on an associated encrypted drive cannot be decrypted once the drive is removed from the original device.
A Mobile Trusted Module (MTM) is the TPMequivalent for mobile phones. With an integrated MTM, a mobile phone can have a hardwarebased root of trust. A hardwarebased root of trust ensures the integrity of the mobile phone, including any stored keys or certificates, and can facilitate secure transactions, such as enterprise access or online banking.
Trusted Network Connect (TNC) is a vendorneutral standard to enforce endpoint integrity and network access policies. TNC can be implemented in the device that an endpoint uses for network access or within the existing network infrastructure. TNC is intended to support interoperability between a variety of vendors of endpoints and network infrastructure devices.
Trusted MultiTenant Infrastructure (TMI) is an open framework that defines reference models for trusted cloud or shared infrastructures. Because of the recent rise in cloudbased computing, the Trusted Computing Group (TCG) has published the TMI framework as a first step toward implementing trustbased models in shared, multiprovider infrastructures. -
Which of the following statements is true regarding the SA lifetime specified in a matching IKE policy? (Select the best answer.)
- The value specified by the remote peer must be equal to the value specified by the local peer.
- The value specified by the remote peer must be less than or equal to the value specified by the local peer.
- The value specified by the remote peer must be greater than or equal to the value specified by the local peer.
- The value specified by the remote peer must be less than the value specified by the local peer.
- The value specified by the remote peer must be greater than the value specified by the local peer.
Explanation:
In an Internet Key Exchange (IKE) policy, the security association (SA) lifetime specified by the remote peer must be less than or equal to the value specified by the local peer. Virtual private network (VPN) peers establish a connection through a series of negotiations and authentications. Initially, the VPN peers negotiate an IKE SA and establish a tunnel for key management and authentication. This initial phase is referred to as IKE phase 1. The key management tunnel is used to protect the subsequent negotiation of IP Security (IPSec) SAs. This secondary negotiation phase is referred to as IKE phase 2.
Each VPN peer defines a collection of security parameters in an IKE policy. These parameters are used to negotiate the creation of the key management tunnel in IKE phase 1. There are six required parameters in an IKE policy:
Policy priority – specifies the order in which policies are negotiated with a peer
Authentication method – indicates whether a preshared key or an RSA digital certificate is used to verify the identity of an IKE peer
Encryption algorithm – indicates the data protection method used to secure IKE traffic
Hashbased Message Authentication Code (HMAC) algorithm – indicates the data integrity method used to verify the integrity of IKE traffic
DiffieHellman (DH) group – specifies how keying material is generated between IKE peers
Lifetime – specifies the length of time that a key is considered valid? the default is 86,400 seconds, or 24 hoursIf an IKE policy does not specify a parameter and its associated value, the VPN peer will use the default value by default. For example, the default IKE policy settings for a Cisco Apative Security Appliance (ASA) running software revision 8.4 or higher are shown below:
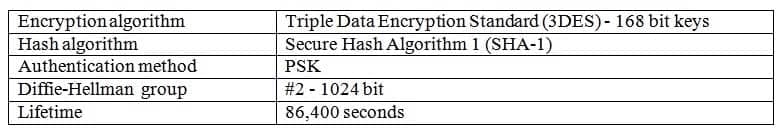
300-735 Part 13 Q18 130 The default IKE policy settings are combined with the configuration parameters specified in the running configuration. For example, because the following block of commands does not specify an HMAC algorithm, the ASA would use the default value, which is SHA1:
ASA(config)#crypto ikev1 policy 1 ASA(configikev1policy)#authentication rsasig ASA(configikev1policy)#encryption aes 192 ASA(configikev1policy)#group 1 ASA(configikev1policy)#lifetime 14400
In order for VPN peers to successfully negotiate a key management tunnel during IKE phase 1, the peers must agree on security parameters. For example, when ASA1 sends an IKE policy proposal to ASA2, the IKE policy is compared with the IKE policies defined on ASA2. The proposed policy must be an exact match to one of ASA2’s locally defined policies? otherwise, it will be rejected. The one exception to this rule is the value of the IKE lifetime parameter. An IKE lifetime is considered a match if the value is less than or equal to the IKE lifetime defined in the local policy. If the IKE lifetime value is less than that of the local policy, the router will use the lesser of the two values. For example, when ASA1 initiates a connection to ASA2, ASA1 will only consider lifetime values from ASA2’s policies as matching if they are less than or equal to 14,400 seconds.
-
Implementing which of the following features provides a cloudbased subscription method of URL filtering that can be used with Cisco’s ZFW? (Select the best answer.)
- Websense
- Trend Micro TRPS
- Secure Computing SmartFilter
- blacklists and whitelists
Explanation:
The Trend Micro Trend Router Provisioning Server (TRPS) provides a cloudbased subscription method of Uniform Resource Locator (URL) filtering that can be used with Cisco’s zonebased policy firewall (ZFW). URL filtering inspects Hypertext Transfer Protocol (HTTP) requests and blocks access to websites that match certain criteria. For example, URL filtering is commonly configured on perimeter routers to prevent users from inadvertently accessing URLs that have been deemed inappropriate or identified as hosting malware. Subscriptionbased URL filtering services assign websites to categories, which are used by administrators to limit or block access to these sites. With a Trend Micro subscription, the Cisco firewall sends URL queries to a TRPS located on the Internet. The TRPS will reply with category information for the requested URL. The Cisco firewall will then allow or block the traffic based on the category.
Websense and Secure Computing SmartFilter provide a local serverbased method of URL filtering that can be used with Cisco’s ZFW. The Cisco firewall sends URL queries to the Websense or SmartFilter server. The server will reply with category information for the requested URL. The Cisco firewall will then allow or block the traffic based on the category. The primary difference between a Websense or SmartFilter server and a TRPS is that the Websense and SmartFilter servers are hosted on the local network? the TRPS is located on the Internet.
Blacklists and whitelists are methods of URL filtering that can be used with Cisco’s ZFW. However, they do not require a subscription? these features are included in the Cisco IOS. A blacklist contains a list of domains that you want to explicitly block, and a whitelist contains a list of domains that you want to explicitly allow. You can also block traffic that contains certain keywords in the URL. Blacklists, whitelists, and URL keyword filtering can be used in conjunction with a URL filtering subscription service. -
Which of the following best describes how an IPS is similar to an IDS? (Select the best answer.)
- They both sit in the path of network traffic.
- Neither sits in the path of network traffic.
- They both prevent malicious traffic from infiltrating the network.
- They can both use signatures to detect malicious traffic.
Explanation:
Intrusion Prevention System (IPS) and Intrusion Detection System (IDS) devices are similar in that they can both use signatures to detect malicious traffic. Patternmatching IDS and IPS devices use specific strings of text called signatures to detect malicious traffic. The primary benefit of signaturebased detection methods is that the number of false positives generated is typically low. However, signaturebased detection methods do not provide adequate protection against new attacks. Although signatures can be added as new threats are found, there is always a delay between the time a threat is released and the time a signature is developed to detect the threat.
IPS devices typically sit inline in the path of network traffic? however, IDS devices typically do not. Because traffic flows through an IPS, an IPS can detect malicious traffic as it enters the IPS device and can prevent the malicious traffic from infiltrating the network. An IPS can work in conjunction with a network firewall? however, Cisco recommends deploying an IPS on the inside interface of the firewall in order to prevent the IPS from wasting resources by analyzing traffic that will ultimately be blocked by the firewall. This enables the IPS to efficiently analyze the traffic that the firewall permits onto the network, rather than processing every inbound packet.
By contrast, an IDS device merely sniffs the network traffic by using a promiscuous network interface. Because network traffic does not flow through an IDS device, the IDS device can detect malicious traffic but cannot prevent it from infiltrating the network. When an IDS detects malicious traffic, it can alert other network devices in the traffic path so that further traffic can be blocked. In addition, an IDS can be configured to send a Transmission Control Protocol (TCP) reset notification or an Internet Control Message Protocol (ICMP) unreachable message to the source and destination addresses.
Protocolbehavior IDS and IPS devices use rules to detect protocol traffic that does not follow standard methods of operation. The rules used by protocolbehavior devices are usually based on the Request for Comment (RFC) documents that define each protocol. Although protocolbehavior devices can detect nonstandard traffic, there is no way to know for sure whether the traffic is caused by a malicious user or by a poorly coded application. Therefore, protocolbehavior devices have a higher rate of false positives.
Anomalydetection IDS and IPS devices detect abnormalities in network traffic behavior. To enable anomalydetection devices to detect abnormalities in traffic, the devices must first take a baseline reading of what normal network traffic patterns are like. Once the baseline is taken, an anomalydetection device will compare future traffic against the baseline to detect abnormal traffic flows. Anomalydetection devices have a higher false positive rate, but they are capable of detecting new attacks.

