300-735 : Automating Cisco Security Solutions (SAUTO) : Part 14
-
Which of the following statements is true regarding traditional stateful packetfiltering firewalls? (Select the best answer.)
- They are more efficient than stateless packetfiltering firewalls.
- They can operate at Layers 3, 4, 5, and 7 of the OSI model.
- They prevent more types of attacks than Application layer firewalls do.
- They can defend against DoS attacks.
Explanation:
Stateful packetfiltering firewalls can defend against Denial of Service (DoS) attacks. Stateful packetfiltering firewalls use a state table to track session information. Session information is maintained and tracked by stateful packetfiltering firewalls in order to determine whether packets should be permitted or blocked. For example, when monitoring Transmission Control Protocol (TCP) traffic, the stateful packet filter adds an entry to the state table when a TCP session is permitted. Subsequent packets are verified against the state table to ensure that the packets belong to an established connection. If the TCP packet does not belong to an established connection, the packets are dropped. Thus, if an attacker attempts to send a flood of packets to the network, the packets will be dropped if they do not match a connection in the table.
By contrast, a stateless packetfiltering firewall, which is also referred to as a static packetfiltering firewall, evaluates and either blocks or allows individual packets based on the Layer 3 and Layer 4 information in the packet header. Specifically, stateless packetfiltering firewalls can use the source and destination IP addresses, source and destination port numbers, and protocol type listed in the packet header? these values are commonly known as the 5tuple. Because a stateless packetfiltering firewall allows all traffic from an approved IP address, stateless packetfiltering firewalls are susceptible to IP spoofing attacks, which is a type of attack wherein an attacker uses the source IP address of a trusted host to send messages to other computers. In addition, because a stateless packetfiltering firewall does not maintain a table of active connections, it is more efficient than a stateful packetfiltering firewall.
Traditional stateful packetfiltering firewalls can operate at Layers 3, 4, and 5 of the Open Systems Interconnection (OSI) model but not at Layer 7. Application inspection firewalls, also known as application proxies, can operate at Layer 7-the Application layer-as well as at Layers 3, 4, and 5. This enables application inspection firewalls to prevent more types of attacks than traditional stateful packetfiltering firewalls do. Because they can operate at the Application layer, application inspection firewalls can be used to prevent applicationspecific traffic. -
You are analyzing recent intrusion events in FireSIGHT Defense Center and notice several events with blue icons.
To which of the following vulnerability classifications do the blue icons correspond? (Select the best answer.)
- unknown target
- vulnerable
- potentially vulnerable
- not vulnerable
Explanation:
A blue icon is used in intrusion event records by Cisco FireSIGHT Defense Center to classify a vulnerability as an unknown target. An unknown target classification indicates that either the source or target host is on a monitored network but has no corresponding entry in the network map. FireSIGHT uses impact levels to describe the potential severity of attacks. In the FireSIGHT system, managed devices, like Cisco FirePOWER Intrusion Prevention Systems (IPSs), respond to an intrusion event by flagging the event with an impact level and sending the event to the FireSIGHT Defense Center. The impact level is based on accumulated intrusion data, network discovery data, and vulnerability information. The aggregated intrusion event data typically contains contextual information about the event and includes a copy of the packet that triggered the event.
The following table provides a summary of the FireSIGHT impact levels and their meaning:

300-735 Part 14 Q02 131 -
Which of the following SNMP actions are used by an NMS to extract information from an SNMP agent? (Select 2 choices.)
- get
- getNext
- set
- inform
- trap
Explanation:
The get and getNext actions are used by a network management station (NMS) to extract information from a Simple Network Management Protocol (SNMP) agent. SNMP is a protocol that an NMS can use to communicate with an agent in the same community. If the NMS and the agent do not share the same community string, the NMS is not permitted to communicate with the agent. SNMP communities can be configured to be either readonly or readwrite. Readonly communities enable an NMS to retrieve Management Information Base (MIB) data from a community, whereas readwrite communities enable an NMS to modify and retrieve MIB data. If the NMS is authorized to communicate with the agent of a readonly community, the NMS can take any of the following actions:
– get – request a particular item from the MIB
– getNext – request the next sequential item from the MIB
– getBulk – request several sequential items from the MIB
By contrast, if the NMS is authorized to communicate with the agent of a readwrite community, the NMS can take any of the following actions:
– get – request a particular item from the MIB
– getNext – request the next sequential item from the MIB
– getBulk – request several sequential items from the MIB
– set – modify an item in the MIBThe SNMP agent typically accumulates statistical data regarding the number and type of SNMP requests and responses it has processed. For example, on Cisco routers, you can use the show snmp command to display the accumulated SNMP statistics, as shown in the following sample output:
Chassis: 4279256517
1230 SNMP packets input
2 Bad SNMP version errors
5 Unknown community name
4 Illegal operation for community name supplied
0 Encoding errors
0 Number of requested variables
0 Number of altered variables
680 Getrequest PDU
479 Getnext PDUs
60 Setrequest PDUs
0 Input queue packet drops (Maximum queue size 1000)
1230 SNMP packets output
0 Too big errors (Maximum packet size 1500)
No such name errors
Bad values errors
0 General errors
762 Response PDUs 0 Trap PDUs
SNMP logging: disabled
The sample output indicates the number of get, getNext, and set requests that have been received by the router as well as statistics on the number of various types of SNMP packets the router has sent in response to NMS queries. For example, the Illegal operation for community name supplied field in the sample output indicates that four SNMP packets requested an operation that was not allowed for the associated community, such as a set request for a community that permits only get requests. In addition, the Unknown community name field indicates that five SNMP packets were received with unknown community strings.
The trap and inform actions are not used by an NMS to extract information from an SNMP agent. Instead, the trap and inform actions are used by an SNMP agent to alert an NMS when a particular threshold has been exceeded:
– trap – send to the NMS an alert that does not require an acknowledgment
– inform – send to the NMS an alert that requires an acknowledgment
Although the inform action is more reliable than the trap action, the inform action can consume additional resources. The inform action can be sent multiple times until the NMS acknowledges it. In addition, the agent stores the data from the inform action in local memory until the NMS acknowledges the receipt of the notification. -
Which of the following statements is true regarding stateful firewalls? (Select the best answer.)
- Their primary purpose is to hide the source of a network connection.
- They operate at the Application layer of the OSI model.
- They allow traffic into a network only if a corresponding request was sent from inside the network.
- They can block traffic that contains specific web content.
Explanation:
Stateful firewalls allow traffic into a network only if a corresponding request was sent from inside the network. A stateful firewall makes filtering decisions based on previous packets that have been sent. It does so by keeping track of the state of each session. When an outbound session is initiated, the stateful firewall will create an entry in the firewall’s state table and dynamically allow the return traffic in the inbound direction. Inbound traffic from other sources will be blocked unless there is a corresponding outbound session listed in the state table. Stateful firewalls are more secure than packet filtering firewalls, which make filtering decisions based on each packet individually without regard to session state.
The primary purpose of a stateful firewall is not to hide the source of a network connection. If you want to hide the source of a network connection, you should use a proxy firewall or implement Network Address Translation (NAT) or Port Address Translation (PAT). A proxy firewall terminates the connection with the source device and initiates a new connection with the destination device, thereby hiding the true source of the traffic. When the reply comes from the destination device, the proxy firewall forwards the reply to the original source device. NAT is used to translate private addresses used on an internal network to public addresses that are routable over the Internet. Because NAT performs address translation between private and public addresses, NAT effectively hides the address scheme used by the internal network, which can increase security. NAT also reduces the number of public IP addresses that a company needs to allow its devices to access Internet resources, thereby conserving IP version 4 (IPv4) address space.
Stateful firewalls do not operate at the Application layer of the Open Systems Interconnection (OSI) model. Both stateful firewalls and packet filtering firewalls operate at the Network layer and the Transport layer of the OSI model. Stateful firewalls and packet filtering firewalls do not understand Application layer data, so they cannot filter traffic based on that data. For example, a stateful firewall cannot block traffic that contains specific web content, because the stateful firewall does not understand Hypertext Transfer Protocol (HTTP) data. -
Which of the following statements is true regarding the autocommand keyword when used with the username command on Cisco routers? (Select the best answer.)
- The specified command cannot exceed 255 characters.
- The autocommand keyword must be the username command’s last argument.
- The specified command cannot contain embedded spaces.
- The user session is not terminated if the autocommand keyword fails to execute its specified command.
Explanation:
When the autocommand keyword is used with the username command on a Cisco router, it must be the last command line argument specified. The username command creates and configures entries in a router’s local authentication database. The username command requires a user name as its main argument? the user name must be a single string of text without blank spaces or quotation marks. There are a number of keywords that can be used with the username command to customize user characteristics, such as passwords, privilege levels, and automatic commands. The autocommand keyword configures a command that will execute immediately after a user successfully logs in to a Cisco router. The command specified by the autocommand keyword can be of any length and can contain embedded spaces. Because the command can be of any length, the autocommand keyword must be the username command’s last argument. The username command can accept multiple arguments, such as the password and privilege keywords, on a single command line. Alternatively, each keyword can be specified with the username command on its own line. For example, the username boson password cisco privilege 15 autocommand show process cpu historycommand is equivalent to the following block of commands:RouterA(config)#username boson password cisco
RouterA(config)#username boson privilege 15
RouterA(config)#username boson autocommand show process cpu historyThe sample command block configures a user name of boson with a password of cisco, configures a privilege level of 15, and causes the EXEC shell to execute the show process cpu history command after the user successfully logs in to the router. If the command is successful, the output will be displayed on the user’s terminal and then the session will be automatically disconnected. However, if the command fails to execute, only an error message will be displayed on the user’s terminal before the session is automatically disconnected. Because the user session is disconnected by default after the output from the autocommand keyword is displayed, you must use the nohangup keyword if you intend to change the default behavior and leave the user session intact.
-
Refer to the exhibit.

300-735 Part 14 Q06 132 The network you administer consists of the devices shown in the exhibit. Each link is 100 megabits per second (Mbps) and is connected to a FastEthernet port. Switch S1 is the root bridge. You enable root guard on Fa0/0 on switch S2 and switch S3 by issuing the spanningtree guard root command in interface configuration mode on both switch ports. You also enable the UplinkFast feature on S2 and S3 by issuing the spanningtree uplinkfast command in global configuration mode on both switches.
Which of the following statements best describes what will occur if the link between S1 and S2 is broken? (Select the best answer.)- Traffic will follow its normal path from Host2 to S1.
- The Fa0/0 port on both switches will be put into the rootinconsistent (blocked) state.
- Only Fa0/0 on S2 will be put into the rootinconsistent (blocked) state.
- Only Fa0/0 on S3 will be put into the rootinconsistent (blocked) state.
Explanation:
If the link between S1 and S2 is broken, the Fa0/0 port on S2 will be placed into the rootinconsistent state. When root guard is enabled on a port, it prevents a port from becoming a root port. Normally, a port that receives a superior bridge protocol data unit (BPDU) will become the root port. However, if a port configured with root guard receives a superior BPDU, the port transitions to the rootinconsistent state and the port will be blocked until it stops receiving superior BPDUs. As a result, root guard can be used to influence the placement of the root bridge on a network by preventing other switches from propagating superior BPDUs throughout the network and becoming the root bridge.
When the root bridge detects the broken link, it will send out BPDUs to converge the network topology. Since root guard was enabled on Fa0/0 on S2, the interface will be placed into the rootinconsistent state when it receives superior BPDUs from Fa0/0 on S3. Thus root guard prevents Fa0/0 on S2 from being selected as a root port. The port will remain in the rootinconsistent state until it stops receiving superior BPDUs from Fa0/0 on S3.
Fa0/0 on S3 will not be placed into the rootinconsistent state, because it will not receive superior BPDUs from S2. S3 will continue to receive superior BPDUs from S1.
Traffic would not follow its normal path from Host2 to the root bridge if the link between S1 and S2 were broken. When the link between S1 and S2 is up, traffic from Host2 travels from S4 to S2 to S1. This is based on the root path cost. The root path cost is an accumulation of path costs from bridge to bridge. A Fast Ethernet link has a path cost of 19. There are two 100megabits per second (Mbps) paths, so the root path cost from S4 to S2 to S1 equals 38. The root path cost from S4 to S3 to S1 also equals 38. If the root path cost is identical, the bridge ID (BID) is used to determine the path. In this scenario, S2 has a priority of 32768, as does S3. However, the Media Access Control (MAC) address for S2, 000000000002, is lower than the MAC address for S3, 000000000003, making S2 the designated bridge. If the link between S1 and S2 breaks, the path for traffic coming from Host2 will be rerouted from its normal path to the S4 to S3 to S1 path. -
Which of the following is a Cisco AMP for Endpoints feature that can prevent specific programs from running on managed endpoints? (Select the best answer.)
- file reputation
- device trajectory
- file trajectory
- outbreak control
Explanation:
The outbreak control feature of Cisco Advanced Malware Protection (AMP) for Endpoints can prevent specific programs from running on managed endpoints. AMP for Endpoints is a hostbased malware detection and prevention platform that runs on Microsoft Windows, Mac OS X, Linux, and Google Android. Like many other antimalware packages, AMP for Endpoints monitors network traffic and application behavior to protect a host from malicious traffic. However, unlike many of its competitors, AMP for Endpoints continues its analysis after a disposition has been assigned to a file or traffic flow. When malware is detected, the outbreak control feature of AMP for Endpoints can use application blocking to ensure that a compromised application does not spread the infection. Outbreak control provides for granular control over which applications are blocked and can use whitelists to ensure that missioncritical software continues to run even during an outbreak.
File reputation, file trajectory, and device trajectory are not AMP for Endpoints features that prevent specific programs from running on managed endpoints. File reputation uses information collected from a global network of security devices to analyze and detect malicious traffic. File trajectory tracks the spread of suspicious files throughout the network, which can reduce the analysis time if a suspicious file is determined to be malicious. Likewise, device trajectory tracks file and network activity on endpoints to reduce the overall analysis time when malicious software is detected. -
You have been asked to use ASDM to change the global application inspection settings on an ASA at the edge of your network.
Which of the following panes in the firewall configuration navigation tree can you use to achieve this task? (Select the best answer.)
- Access Rules
- Service Policy Rules
- Filter Rules
- Advanced
Explanation:
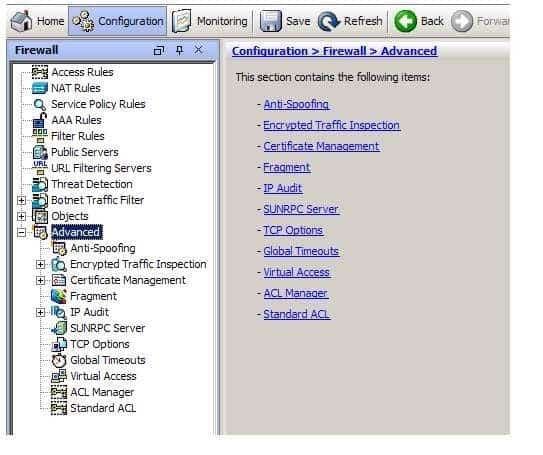
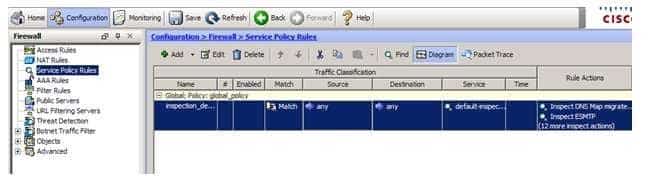
You can use the Service Policy Rules pane in the firewall configuration navigation tree of Cisco Adaptive Security Device Manager (ASDM) to change the global application inspection settings on a Cisco Adaptive Security Appliance (ASA) at the edge of your network. Application inspection is one of the actions that can be applied to traffic with a policy map. Services that embed IP addresses in the packet or that utilize dynamically assigned ports for secondary channels require deep packet inspection, which is provided by Application layer protocol inspection. Some traffic, such as Internet Control Message Protocol (ICMP) traffic, might be dropped if inspection for that protocol is not enabled. You can use ASDM to make changes to the global policy by navigating to the Service Policy Rules pane, highlighting the inspection policy, and clicking Edit, as shown in the following exhibit:
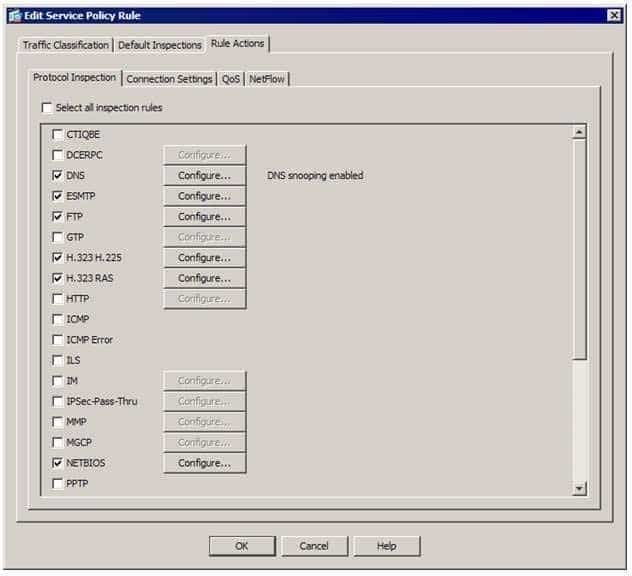
300-735 Part 14 Q08 133 From the Edit Service Policy Rule dialog box, click the Rule Actions tab, where you will find the protocol inspection configurations for the global policy. For example, you could select the check box next to the ICMP field in the following exhibit to enable the ASA to inspect ICMP traffic so that ICMP replies from valid ICMP requests are not inadvertently dropped:
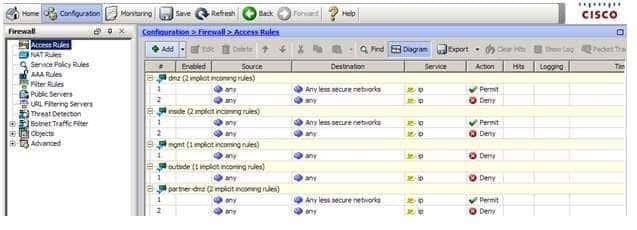
300-735 Part 14 Q08 134 The Access Rules pane in ASDM cannot be used to change the global application inspection settings on an ASA at the edge of your network. The Access Rules pane is used to configure security policies related to controlling access to your network. All inbound traffic must pass through the firewall? by default, no traffic can pass unless an access rule is configured to permit it. The Access Rules pane is shown in the following exhibit:
300-735 Part 14 Q08 135 The Filter Rules pane in ASDM cannot be used to change the global application inspection settings on an
ASA at the edge of your network. The Filter Rules pane is used to configure Uniform Resource Locator (URL) filtering, which prevents inappropriate Internet usage on a secure network. Typically, URL filtering is not handled directly by the ASA but by some other server that must be enabled via the URL Filtering Servers pane before you can add filter rules. When a user makes a request for content from an outside address, the ASA sends a message to the filtering server; if the response from the filtering server indicates that there is no filter prohibiting access to that URL, the ASA will allow the requested content. The Filter Rules pane is shown in the following exhibit:
300-735 Part 14 Q08 136 The Advanced pane in ASDM cannot be used to change the global application inspection settings on an ASA at the edge of your network. From the Advanced pane, you are able to configure several advanced firewall protection features, such as encrypted traffic inspection, IP audit, and fragment size. The Advanced pane is shown in the following exhibit:
-
Which of the following configuration parameters is not displayed on the Connection Profiles pane for clientless SSL VPN connections in ASDM? (Select the best answer.)
- the authentication method to use
- the login page settings to use
- the interfaces to use
- the tunneling protocols to use
Explanation:
The tunneling protocols to use are not displayed on the Connection Profiles pane for clientless Secure Sockets Layer (SSL) virtual private network (VPN) connections in Cisco Adaptive Security Device Manager (ASDM). The Connection Profiles pane displays a quick summary of information related to the connection profiles that have previously been configured. This pane also enables you to configure additional connection profiles. The type of information displayed on the Connection Profiles pane includes the interfaces on the Cisco Adaptive Security Appliance (ASA) that are enabled for VPN access, the login page settings, a list of connection profiles that have been configured, the alias associated with the connection profiles, the authentication method to use for connections made using the connection profiles, and the interfaces to use for connections made using the connection profiles. An example of the Connection Profiles pane is shown in the following exhibit:

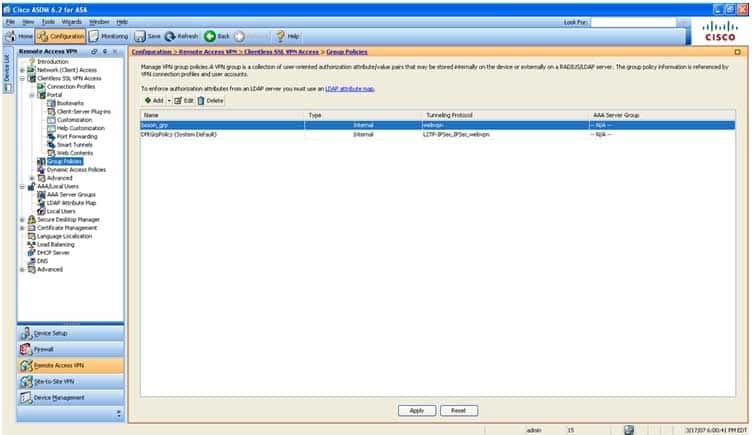
300-735 Part 14 Q09 138 The Group Policies pane for clientless SSL VPN connections in ASDM displays a quick summary of information relating to the group policies that are configured on the ASA. The type of information that is displayed on this pane includes the tunneling protocols that are enabled for each group policy, the type of each group policy, and the Authentication, Authorization, and Accounting (AAA) server group that is to be used by each group policy. An example of the Group Policies pane is shown in the following exhibit:
-
You are configuring a group policy for Cisco AnyConnect VPN connections. You have accessed the Add Internal Group Policy dialog box for the group policy.
On what pane will you be able to configure a VLAN restriction? (Select the best answer.)
- the Customization pane
- the Servers pane
- the General pane
- the SSL VPN Client pane
Explanation:
You can configure a virtual LAN (VLAN) restriction in a group policy for Cisco AnyConnect virtual private network (VPN) clients on the General pane of the Add Internal Group Policy dialog box for the group policy. You can configure a VLAN restriction so that all VPN traffic that is generated by using the associated group policy is sent to the specified VLAN. By configuring a VLAN restriction, you can control the VPN traffic.
To configure a VLAN restriction in Cisco Adaptive Security Device Manager (ASDM) for a group policy that will be used for Cisco AnyConnect clients, you should click Configuration, click the Remote Access VPN button, expand Network (Client) Access, click Group Policies, and click the Add button to create a new group policy, or you should select the group policy to modify and click the Edit button to edit an existing group policy. Depending on whether you click the Add button or the Edit button, the Add Internal Group Policy dialog box or the Edit Internal Group Policy dialog box will open. The General pane of these dialog boxes contains a list of general configuration options, including the banner to display to users, the IP address pool to use, the tunneling protocols to use, and the VLAN to which VPN traffic should be restricted. The following exhibit displays an example configuration in which VPN connections made by using the boson_grp group policy will be restricted to VLAN 10:

300-735 Part 14 Q10 140 You cannot configure a VLAN restriction on the Customization pane of the Add Internal Group Policy dialog box for a group policy for Cisco AnyConnect VPN clients. On this pane, you can configure the customization object to apply to the VPN connection, the home page Uniform Resource Locator (URL), and a custom access denied message to display to users.
You cannot configure a VLAN restriction on the Servers pane of the Add Internal Group Policy dialog box for a group policy for Cisco AnyConnect VPN clients. On this pane, you can configure the Domain Name System (DNS) servers to use for the connection and the Windows Internet Name Service (WINS) servers to use for the connection.
You cannot configure a VLAN restriction on the SSL VPN Client pane of the Add Internal Group Policy dialog box for a group policy for Cisco AnyConnect VPN clients. On this pane, you can configure whether the Cisco AnyConnect VPN client installer remains on client systems, whether compression should be applied to the VPN session, the maximum transmission unit (MTU) for the connection, and the client profile to download to clients. -
Which of the following are transmitted by SDEE? (Select the best answer.)
- SDFs
- TFTP data
- IPS events
- SNMP traps
Explanation:
Intrusion Prevention System (IPS) events are transmitted by Security Device Event Exchange (SDEE) between IPSenabled clients and a centralized IPS management server. SDEE uses Secure Sockets Layer (SSL), which provides a secure communication channel between the devices, to send data. Because the channel between the devices is secure, exchanging SDEE messages is more secure than exchanging syslog messages.
Signature definition files (SDFs) are not transmitted by SDEE. By default, a router will use the builtin SDF that is hardcoded into the IOS. However, you can issue the ip ips sdf location command to specify an alternative SDF for Cisco IOS IPS to use. The SDF files can be specified as a file name located in Flash memory, on a File Transfer Protocol (FTP) server, on a Trivial FTP (TFTP) server, or on a Remote Copy Protocol (RCP) server. If the specified SDF cannot be loaded, the builtin SDF is used.
Simple Network Management Protocol (SNMP) traps are not transmitted by SDEE. SNMP is used to monitor and manage network devices by collecting statistical data about those devices. SNMP version 3 (SNMPv3) provides encryption? SNMPv1 and SNMPv2 do not.
TFTP data is not transmitted by SDEE. TFTP is a management protocol that can be used to transfer configuration files and SDFs between devices. When you use TFTP to send data, the data is sent as plain text? TFTP does not provide encryption. In addition, TFTP does not provide message integrity or authentication. -
You want to configure a WSA to permit access to a particular social media site? however, you also want to deny access to some of the features on that site, such as uploading files and liking posts.
Which of the following WSA features should you configure to achieve your goal (Select the best answer.)
- AMP
- AVC
- DCA
- DLP
Section: Content and Endpoint Security Explanation
Explanation/Reference:
You should configure the Application Visibility and Control (AVC) feature on a Cisco Web Security Appliance (WSA) if you want to permit access to a particular social media site and deny the use of some of the features on that site, such as uploading files and liking posts. A WSA is a standalone web gateway that offers features that can mitigate webbased attacks, enforce acceptable use policies, and provide detailed reporting. The AVC feature provides an administrator with granular control over a wide range of web applications, including the ability to disable application features, limit application bandwidth, and constrain application access to a particular set of users or period of time. The AVC feature is included as part of the Cisco Web Security Essentials software license, which also includes the following:
– Uniform Resource Locator (URL) filtering
– Threat intelligence using the Cisco Talos threat detection network
– Layer 4 traffic monitoring – Policy management
– Actionable reporting
– Data Loss Prevention (DLP), including thirdparty DLP integrationThe URL filtering feature on a WSA can be used to permit or deny access to a particular social media site? however, it does not provide the ability to deny access to some of the features on that site. The URL filtering feature uses a database of over 50 million URLs to protect users from sites that are known to host malicious content. The Dynamic Content Analysis (DCA) feature enhances basic URL filtering by enabling the WSA to determine whether unknown URLs post a threat. The DCA engine can scan unknown URLs and their associated content text in real time and can successfully categorize URLs with an error rate of less than 10 percent.
The DLP feature on a WSA can be used to prevent sensitive data from being transmitted to the web. DLP engines, which include any integrated thirdparty solutions, inspect outbound traffic for specified criteria, such as credit card numbers or customer data, and can take the appropriate action. A WSA can use the Internet Content Adaptation Protocol (ICAP) to integrate thirdparty DLP solutions to enhance its traffic inspection and analysis capabilities. The Advanced Malware Protection (AMP) feature on a WSA can be used to enable advanced malware detection, blocking, analysis, and retroactive reporting on a WSA. The AMP feature enhances the dynamic reputationbased and behaviorbased malware analysis processes available on the WSA with enhanced file reputation, file sandboxing, and retrospective file analysis. Enhanced file analysis enables the WSA to fingerprint a file and send it to the Cisco Security Intelligence Operations (SIO) for a reputation verdict. File sandboxing provides a secure environment where the behavior of a file, such as a compressed archive or a Microsoft Office document, can be analyzed. Retrospective file analysis, which is also known as file retrospection, enables the WSA to track files that were originally deemed as safe and were later determined to be a threat. This helps an administrator determine who might be at risk from those files. -
Which of the following statements are true regarding ACLs? (Select 3 choices.)
- If a packet is permitted by one entry, it cannot be denied by a more specific entry later in the ACL.
- If a packet is denied by one entry, it cannot be permitted by a more specific entry later in the ACL.
- If a packet does not match any entries in the ACL, it is permitted.
- If a packet does not match any entries in the ACL, it is denied.
- An ACL cannot contain two conflicting entries that refer to the same source address.
- An ACL cannot contain two conflicting entries that refer to the same destination address.
Explanation:
If a packet is permitted by one access control entry (ACE), it cannot be denied by a more specific entry later in the access control list (ACL). Likewise, if a packet is denied by an ACE, it cannot be permitted by a more specific entry later in the ACL. In addition, if a packet does not match any entries in the ACL, it is denied. ACLs are processed in a sequential manner, from the first entry in the list to the last entry. Because ACLs are processed from top to bottom, correct sequencing is critical to ensuring proper filtering. More specific entries should be located higher in an ACL so that they are processed before less specific entries. This helps ensure that statements located higher in an ACL do not negate the intended impact of statements located lower in the ACL.
An ACL can contain multiple entries that conflict. For example, you could inadvertently have one entry that permits traffic from a specific source or destination IP address and have another entry that denies traffic from the same source or destination IP address. You should use caution when editing ACL entries. New entries are added to the end of an ACL by default and do not override conflicting entries. Because new statements added to an existing ACL are appended to the end of the existing ACL, it might be necessary to recreate the ACL if you need to make significant changes to an ACL or add a statement that should appear at or near the top of the ACL. -
Which of the following NAT types effectively exempts one or more addresses from translation? (Select the best answer.)
- dynamic NAT
- dynamic PAT
- identity NAT
- static NAT
Explanation:
Identity Network Address Translation (NAT) is a NAT type that effectively exempts one or more addresses from translation. With identity NAT, real addresses and mapped addresses are identical for a particular NAT rule. For example, an identity rule might specify that a real address of 192.168.13.1 on the inside interface should be translated to a mapped address of 192.168.13.1 on the outside interface. Because the real and mapped addresses are identical in an identity NAT rule, any matching addresses effectively bypass NAT. A common use for identity NAT is to exempt remote access virtual private network (VPN) client addresses from the NAT rules applied to the VPN gateway interfaces.
Static NAT, dynamic NAT, and dynamic Port Address Translation (PAT) are not NAT types that effectively exempt one or more addresses from translation. Static NAT provides a bidirectional translation between real and mapped IP addresses. As the name implies, static NAT specifies a mapping between real and mapped addresses that does not change over time. Static NAT rules typically define onetoone mappings of real and mapped addresses. By contrast, dynamic NAT provides unidirectional mappings between one or more real addresses and one or more mapped addresses. The addresses are mapped on a firstcome, firstserved basis, and mappings can be initiated only by hosts with real addresses. Dynamic PAT provides mappings between one or more real addresses and a single mapped address. With dynamic PAT, the source port of each real address is used to identify the associated mapped port and address. Like dynamic NAT, dynamic PAT mappings occur on a firstcome, firstserved basis and mappings can be initiated only by hosts with real addresses.