350-401 : Implementing Cisco Enterprise Network Core Technologies (ENCOR) : Part 01
-
You issue the following commands on a Cisco router:
RouterA#debug condition interface serial 0/0 RouterA#debug condition interface serial 0/1 RouterA#debug condition username RouterB RouterA#debug ppp authentication
Which of the following PPP authentication debugging messages will be displayed on RouterA? (Select the best answer.)
- only messages that contain the RouterB user name
- only messages that arrive on the Serial 0/0 interface
- only messages that arrive on the Serial 0/1 interface
- messages that contain the RouterB user name or that arrive on either specified interface
Explanation:
Debug messages that contain the RouterB user name and that arrive on either the Serial 0/0 interface or the Serial 0/1 interface would be displayed if you were to issue the commands in this scenario on a Cisco router. The debug condition command is used to enable restrictions on the data that the debugging process displays. If no conditions are specified, all output from enabled debugging commands will be displayed. You can configure a series of debug conditions, any one of which will cause debug messages to display when a match occurs. In order to display the output, the debugging process need only match one of the specified conditions, not all of them.
The debug condition interface interface command limits debug messaging output to only enabled debugging that applies to the specified interface. For example, if you were to issue the debug condition interface serial 0/0 command followed by the debug ppp authentication command in this scenario, the debug output would consist of PointtoPoint Protocol (PPP) authentication messages, but only if those messages also apply to the router’s Serial 0/0 interface.
The debug output will not be limited to only one interface on RouterA in this scenario. Configuring a series of debug condition interface interface commands limits debug message output to the series of specified interfaces. The debug output need match only one of the interface conditions to be displayed. For example, you could issue the following commands on RouterA to ensure that PPP authentication debug messages that apply to either the Serial 0/0 interface or the Serial 0/1 interface are displayed on the router:
RouterA#debug condition interface serial 0/0 RouterA#debug condition interface serial 0/1 RouterA#debug ppp authentication
After issuing the commands above, you could further limit the PPP authentication debug output by issuing the no debug condition interface interface command. For example, issuing the no debug condition interface serial 0/0 command would remove the Serial 0/0 interface condition from the debugging output, which means that only PPP authentication messages that apply to the Serial 0/1 interface would be displayed. You can remove all interface conditions from debugging output by issuing the no debug condition interface all command. After that command is issued, all PPP authentication debugging messages would be displayed unless you also issued the no debug ppp authentication command or the no debug all command.
The debug output will not be limited to the user name RouterB, because you have also issued debug condition interface interface commands in this scenario. The debug condition {username username | called dialstring | callerdialstring} command enables you to limit the output of debugging messages by user name, calling party number, or called party number. Applying only one of those conditions to debugging output stops the output of debug messages on all interfaces. The router will then monitor each interface for a condition match. If a match occurs, debug messages will be displayed for that match. In this scenario, the debug condition username RouterB command will display output when an interface sends or receives a PPP authentication packet that contains the user name RouterB. However, because you have also issued the debug condition interface serial 0/0 command and the debug condition interface serial 0/1 command, PPP authentication messages that apply to either of those interfaces will be displayed even if the RouterB user name is not matched.
You can determine which debug conditions are configured and which have been met on a Cisco device by issuing the show debug condition command from privileged EXEC mode. For example, the following output indicates that three conditions have been enabled on the router, but only the last two conditions have been matched so far: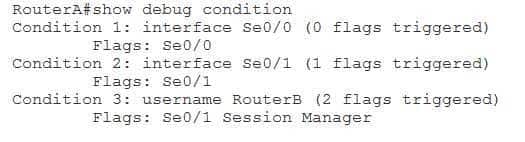
350-401 Part 01 Q01 001 Based on the output above, you can determine that PPP authentication has occurred on RouterA’s Serial 0/1 interface and that the user name RouterB was used to perform the authentication. In addition, the user name RouterB triggered flags both on the Serial 0/1 interface and by the PPP session manager, possibly indicating that after debugging was configured, the connection between RouterA and RouterB went down and was then restored.
-
Which of the following ping command options should be enabled if you want to determine the MTU size that a given connection supports? (Select the best answer.)
- the IPv4 donotfragment bit
- a number of pings greater than five
- a datagram size greater than 1,500 bytes
- a timeout value greater than two seconds
Explanation:
The IP version 4 (IPv4) donotfragment bit, or DF bit, is the ping command option that should be enabled if you want to determine the maximum transmission unit (MTU) size that a given connection supports. By default, packet fragmentation is used to enable oversized packets to traverse the network in chunks that are smaller than the configured MTU. The DF bit configures the ping command to attempt to send packets of a given size without fragmentation. By repeatedly pinging a destination device with smaller and smaller datagram sizes, you can determine the MTU.
The ping command supports the ability to modify the size of the datagram that it transmits as well as the ability to enable the DF bit, which is disabled by default. You can configure extended ping features either by issuing the ping command without parameters, which causes the ping command to display a series of configuration prompts, or by specifying parameters on the command line along with the ping command. For example, the ping 192.168.1.1 size 1500 dfbit command configures an extended ping with a destination IP address of 192.168.1.1, a datagram size of 1,500 bytes, and an enabled DF bit. On a connection with an MTU of 1,500 bytes, this ping succeeds, as shown in the following output:

350-401 Part 01 Q02 002 Based on the output, you can determine that the ping succeeded. You can also determine that the DF bit is, indeed, enabled. However, issuing the ping 192.168.1.1 size 1501 dfbit command on the same device results in a failure, as shown in the following output:

350-401 Part 01 Q02 003 In the output above, issuing the ping 192.168.1.1 size 1501 dfbit command results in a ping failure because the MTU is configured to 1,500 bytes and the DF bit is set. If you were to issue the same command without the dfbit parameter, the ping would succeed because the ping command is allowing the datagram to be fragmented, as shown in the following output:

350-401 Part 01 Q02 004 You do not need to explicitly set the datagram size to 1,500 bytes in this scenario. By default, Cisco devices are configured with a system MTU of 1,500 bytes. Therefore, the ping might succeed, providing no indication of a configured MTU. In order to test the MTU, you should set the DF bit and test a high MTU. You should then methodically lower the datagram size that you test with the DF bit enabled until the ping succeeds.
You do not need to adjust the number of pings from the default value of five. In addition, you do not need to adjust the default timeout value of two seconds. Neither of these values help you determine the configured MTU.
-
You issue the debug ppp authentication command on RouterA. RouterA’s Serial 0/0 interface is connected to RouterB. RouterA’s Serial 0/1 interface is connected to RouterC. You issue the no shutdown command on all interfaces and note that every interface has entered the up state.
Next, you issue the show debug condition command on RouterA and receive the following output:

350-401 Part 01 Q03 005 Which of the following statements is true? (Select the best answer.)
- A debug condition has been met on the Serial 0/0 interface.
- A debug condition has been met on the Serial 0/1 interface.
- A debug condition has been met in which the user name is RouterB.
- All debug conditions in this scenario have been met.
- None of the debug conditions in this scenario have been met.
Explanation:
Based on the output in this scenario, you can determine that a PointtoPoint Protocol (PPP) authentication debug condition has been met on the Serial 0/1 interface of RouterA, which is the interface that is connected to RouterC. The debug condition command is used to enable restrictions on the data that the debugging process displays. If no conditions are specified, all output from enabled debugging commands will be displayed. You can configure a series of debug conditions, any one of which will cause debug messages to display when a match occurs. In order to display the output, the debugging process need only match one of the specified conditions, not all of them.
You can determine which debug conditions are configured and which have been met on a Cisco device by issuing the show debug condition command from privileged EXEC mode. For example, the following output indicates that three conditions have been enabled on the router, but only one condition has been matched so far:

350-401 Part 01 Q03 006 Because you have enabled PPP authentication debugging in this scenario, you can determine that PPP authentication has occurred on RouterA’s Serial 0/1 interface. In addition, you can determine that the user name RouterB has not been triggered. Therefore, no PPP authentication has occurred on RouterA that includes the user name of RouterB.
The debug condition interfaceinterface command limits debug messaging output to only enabled debugging that applies to the specified interface. For example, if you were to issue the debug condition interface serial 0/0 command followed by the debug ppp authentication command in this scenario, the debug output would consist of PPP authentication messages, but only if those messages also apply to the router’s Serial 0/0 interface.
Configuring a series of debug condition interface interface commands limits debug message output to the series of specified interfaces. The debug output need match only one of the interface conditions to be displayed. For example, you could issue the following commands on RouterA to ensure that PPP authentication debug messages that apply to either the Serial 0/0 interface or the Serial 0/1 interface are displayed on the router:

350-401 Part 01 Q03 007 After issuing the commands above, you could further limit the PPP authentication debug output by issuing the no debug condition interface interface command. For example, issuing the no debug condition interface serial 0/0 command would remove the Serial 0/0 interface condition from the debugging output, which means that only PPP authentication messages that apply to the Serial 0/1 interface would be displayed. You can remove all interface conditions from debugging output by issuing the no debug condition interface all command. After that command is issued, all PPP authentication debugging messages would be displayed unless you also issued the no debug ppp authentication command or the no debug all command.
The debug condition {username username | called dialstring | callerdialstring} command enables you to limit the output of debugging messages by user name, calling party number, or called party number. Applying only one of those conditions to debugging output stops the output of debug messages on all interfaces. The router will then monitor each interface for a condition match. If a match occurs, debug messages will be displayed for that match. In this scenario, the debug condition username RouterB command will display output when an interface sends or receives a PPP authentication packet that contains the user name RouterB. However, because you have also issued the debug condition interface serial 0/0 command and the debug condition interface serial 0/1 command, PPP authentication messages that apply to either of those interfaces will be displayed even if the RouterB user name is not matched.
-
You issue the ping 192.168.1.1 size 1501 dfbit command on a Cisco device. You notice a message indicating that the DF bit has been set. However, the ping fails.
You want to determine the largest datagram that the connection supports without fragmentation.
Which of the following should you do next? (Select the best answer.)
- Issue the command without the dfbit parameter.
- Issue the command without the size parameter.
- Issue the command with a lower size parameter value.
- Issue the command without the size parameter and without the dfbit parameter.
Explanation:
You should issue the command with a lower size parameter value to determine the largest datagram that the connection supports without fragmentation. The IP version 4 (IPv4) donotfragment bit, or DF bit, should be enabled if you want to determine the maximum transmission unit (MTU) size that a given connection supports. By default, packet fragmentation is used to enable oversized packets to traverse the network in chunks that are smaller than the configured MTU. The DF bit configures the ping command to attempt to send packets of a given size without fragmentation. By repeatedly pinging a destination device with smaller and smaller datagram sizes, you can determine the MTU.
The ping command supports the ability to modify the size of the datagram that it transmits as well as the ability to enable the DF bit, which is disabled by default. You can configure extended ping features either by issuing the ping command without parameters, which causes the ping command to display a series of configuration prompts, or by specifying parameters on the command line along with the ping command. For example, the ping 192.168.1.1 size 1500 dfbit command configures an extended ping with a destination IP address of 192.168.1.1, a datagram size of 1,500 bytes, and an enabled DF bit. On a connection with an MTU of 1,500 bytes, this ping succeeds, as shown in the following output:

350-401 Part 01 Q04 008 Based on the output, you can determine that the ping succeeded. You can also determine that the DF bit is, indeed, enabled. However, issuing the ping 192.168.1.1 size 1501 dfbit command on the same device results in a failure, as shown in the following output:
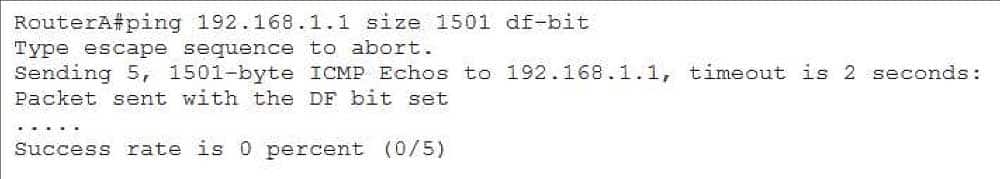
350-401 Part 01 Q04 009 In the output above, issuing the ping 192.168.1.1 size 1501 dfbit command results in a ping failure because the MTU is configured to 1,500 bytes and the DF bit is set. If you were to issue the same command without the dfbit parameter, the ping would succeed because the ping command is allowing the datagram to be fragmented, as shown in the following output:

350-401 Part 01 Q04 010 You should not issue the command without the dfbit option, because this disables the DF bit and enables datagram fragmentation. Ping attempts with fragmentation enabled will succeed even if the size parameter remains larger than the configured MTU.
You should not issue the command without the size parameter. The size parameter in addition to the presence of the DF bit is what enables you to test which datagrams are larger than the MTU. Without the size parameter, the ping datagram will use its small default size of 100 bytes.
-
RouterA’s Serial 0/0 interface is connected to RouterB. RouterA’s Serial 0/1 interface is connected to RouterC. You issue the debug ppp authentication on RouterA and then transition all connected interfaces to the up state.
Next, you issue the show debug condition command on RouterA and receive the following output:
350-401 Part 01 Q05 011 Using the least amount of administrative effort, which of the following should you issue to receive PPP authentication debug output from both RouterB and RouterC? (Select the best answer.)
- no debug alldebug condition interface serial 0/0 -0/1 debug condition username JohnnyB debug ppp authentication
- debug condition interface serial 0/1
- no debug alldebug condition interface serial 0/0 debug condition interface serial 0/1 debug condition username JohnnyB debug ppp authentication
- no debug condition interface all
Explanation:
You should issue the debug condition interface serial 0/1 command on RouterA to receive PointtoPoint (PPP) authentication debug output from both RouterB and RouterC by using the least amount of administrative effort. The debug condition interface interface command limits debug messaging output to only enabled debugging that applies to the specified interface. Issuing the debug condition interface serial 0/0command and the debug condition username JohnnyB command followed by the debug ppp authentication command in this scenario causes the debug output to consist of PPP authentication messages, but only if those messages also apply to the router’s Serial 0/0 interface or include the user name of JohnnyB.
Based on the output of the show debug condition command in this scenario, you can determine that PPP authentication output is only displayed if it occurs on the Serial 0/0 interface, which is connected to RouterB, or if it includes a user name of JohnnyB. In addition, you can determine that both the Serial 0/0 interface and the user name JohnnyB have already triggered flags a single time each. Therefore, it is likely that PPP authentication has occurred on the Serial 0/0 interface and included the user name JohnnyB.
The debug condition interface command accepts only one interface per line. However, it is not necessary to configure all interface conditions in a sequential fashion before enabling debugging. Therefore, issuing only the debug condition interface serial 0/1command will produce the results you require in this scenario by using the least amount of administrative effort.
Configuring a series of debug condition interface interface commands limits debug message output to the series of specified interfaces. The debug output need match only one of the interface conditions to be displayed. For example, you could issue the following commands on RouterA to ensure that PPP authentication debug messages that apply to either the Serial 0/0 interface or the Serial 0/1 interface are displayed on the router:
RouterA#debug condition interface serial 0/0 RouterA#debug condition interface serial 0/1 RouterA#debug ppp authentication
After issuing the commands above, you could further limit the PPP authentication debug output by issuing the no debug condition interface interface command. For example, issuing the no debug condition interface serial 0/0 command would remove the Serial 0/0 interface condition from the debugging output, which means that only PPP authentication messages that apply to the Serial 0/1 interface would be displayed.
The debug condition {username username | called dialstring | callerdialstring} command enables you to limit the output of debugging messages by user name, calling party number, or called party number. Applying only one of those conditions to debugging output stops the output of debug messages on all interfaces. The router will then monitor each interface for a condition match. If a match occurs, debug messages will be displayed for that match. In this scenario, the debug condition username RouterB command will display output when an interface sends or receives a PPP authentication packet that contains the user name RouterB. However, because you have also issued the debug condition interface serial 0/0 command and the debug condition interface serial 0/1 command, PPP authentication messages that apply to either of those interfaces will be displayed even if the RouterB user name is not matched.
It is not necessary to issue the no debug condition interface all command in this scenario, because this command would remove all existing interface conditions. After that command is issued, all PPP authentication debugging messages would be displayed unless you also issued the no debug ppp authentication command or the no debug all command. This would require you to reissue the debug condition interface serial 0/0command in addition to issuing the debug condition interface serial 0/1 command, which increases administrative effort.
There is no need to issue the no debug all command in this scenario, because you can add debug conditions to an existing debugging process. Issuing the no debug all command would disable the debugging process that is already running.
You do not need to issue the debug condition interface serial 0/0 command or the debug condition username Johnny B command in this scenario. Both of these commands have already been issued, as you can determine by the output of the show debug condition command. Reissuing these command would cause the router to produce the % Condition already set message.
Issuing the debug condition interface serial 0/0 -0/1 would not meet the requirements in this scenario. This command contains invalid syntax.
-
You issue the ping 192.168.1.1 size 1600 command on a Cisco device that is configured with the default system MTU. All pings succeed.
Which of the following is most likely true? (Select the best answer.)
- The interface is configured with an MTU of at least 1,600.
- The pings were sent to the destination in a fragmented fashion.
- The DF bit has been enabled, causing the pings to succeed.
- The datagram size specified is below the default MTU value.
Explanation:
Most likely, the pings were sent to the destination in a fragmented fashion because the IP version 4 (IPv4) donotfragment bit, or DF bit, has not been set in this scenario. By default, packet fragmentation is used to enable oversized packets to traverse the network in chunks that are smaller than the configured maximum transmission unit (MTU.) Enabling the DF bit configures the ping command to attempt to send packets of a given size without fragmentation. By repeatedly pinging a destination device with smaller and smaller datagram sizes, you can determine the MTU.
The ping command supports the ability to modify the size of the datagram that it transmits as well as the ability to enable the DF bit, which is disabled by default. You can configure extended ping features either by issuing the ping command without parameters, which causes the ping command to display a series of configuration prompts, or by specifying parameters on the command line along with the ping command. For example, the ping 192.168.1.1 size 1500 dfbit command configures an extended ping with a destination IP address of 192.168.1.1, a datagram size of 1,500 bytes, and an enabled DF bit. On a connection with an MTU of 1,500 bytes, this ping succeeds, as shown in the following output:

350-401 Part 01 Q06 012 Based on the output, you can determine that the ping succeeded. You can also determine that the DF bit is, indeed, enabled. However, issuing the ping 192.168.1.1 size 1501 dfbit command on the same device results in a failure, as shown in the following output:
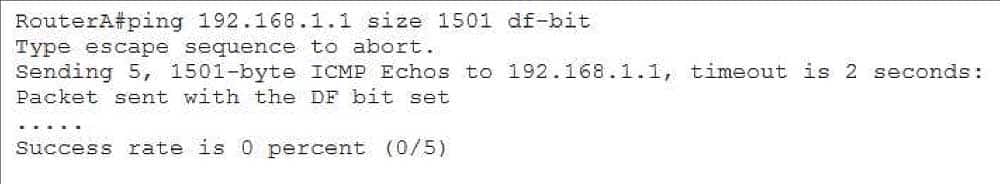
350-401 Part 01 Q06 013 In the output above, issuing the ping 192.168.1.1 size 1501 dfbit command results in a ping failure because the MTU is configured to 1,500 bytes and the DF bit is set. If you were to issue the same command without the dfbit parameter, the ping would succeed because the ping command is allowing the datagram to be fragmented, as shown in the following output:

350-401 Part 01 Q06 014 The interface is not configured with an MTU value of at least 1,600 in this scenario. In addition, the datagram size specified is not below the default MTU value on a Cisco device. By default, a Cisco device has a system MTU of 1,500 bytes. In this scenario, you have issued the ping 192.168.1.1 size 1600 command on a device that is configured with the system default MTU.
The DF bit has not been enabled in this scenario. In order to enable the DF bit, you should issue the ping command with the dfbit parameter.
-
You administer the network in the following exhibit:

350-401 Part 01 Q07 015 All routers are configured to the system MTU defaults.
You issue the ping 192.168.1.2 size 1500 dfbit command from RouterB, but the ping fails.
Which of the following is most likely the cause of the failure? (Select the best answer.)- The GRE tunnel MTU is 1,476.
- The system default MTU is 1,400.
- The DF bit is not enabled.
- The GRE tunnel does not support fragmented datagrams.
Explanation:
Most likely, the Generic Routing Encapsulation (GRE) tunnel maximum transmission unit (MTU) is 1,476 if the ping fails in this scenario. By default, Cisco routers are configured with a system MTU of 1,500 bytes, which includes a 20byte IP header and 1,480 bytes of payload. The ping 192.168.1.2 size 1500 dfbit command in this scenario attempts to send a datagram of 1,500 bytes to a destination address of 192.168.1.2 without fragmenting the datagram into smaller pieces.
In this scenario, the donotfragment, or DF bit, has been enabled with the pingcommand. When the DF bit is set, the device attempts to send packets without fragmentation. If the packet is larger than the MTU, the attempt will fail. Because the GRE tunnel’s MTU supports a maximum of 1,476 bytes, a ping with a size of 1,500 bytes that does not permit fragmentation will fail.
GRE tunnels add a 24byte header to an IP packet. However, a default GRE tunnel MTU is 24 bytes smaller than the MTU of the physical interface. When the DF bit is not set, an unencapsulated 1,500byte packet would be split into two unencapsulated packets: a 1,476byte packet and a 44byte packet, prior to being transported across the tunnel. This process enables each fragment of the packet to include the 24byte GRE header when it traverses the physical interface that is being used as the tunnel’s source. The total sizes of the packet fragments that traverse the physical interface thus become 1,500 bytes and 68 bytes, respectively.
The DF bit is enabled in this scenario. The ping command supports the ability to modify the size of the datagram it transmits as well as the ability to enable the DF bit, which is disabled by default. You can configure extended ping features either by issuing the ping command without parameters, which causes the ping command to display a series of configuration prompts, or by specifying parameters on the command line along with the ping command. For example, the ping 192.168.1.1 size 1500 dfbit command configures an extended ping with a destination IP address of 192.168.1.1, a datagram size of 1,500 bytes, and an enabled DF bit.
The system default MTU on Cisco devices is 1,500, not 1,400. Therefore, a system default MTU of 1,400 is not causing the failure in this scenario. In addition, GRE tunnels do support fragmented datagrams.
-
Which of the following statements is true regarding OSPF connections over a virtual link? (Select the best answer.)
- Traffic is encapsulated and decapsulated by tunnel endpoints.
- Packets contain additional overhead because of tunnel headers.
- The transit area can be a stub area.
- Only routing updates are tunneled.
Explanation:
Only routing updates are tunneled when an Open Shortest Path First (OSPF) connection is formed over a virtual link. All other traffic is sent natively over the physical links. An OSPF virtual link is useful for the following situations:
– Connecting a remote area to the backbone area through a standard area
– Connecting discontiguous backbone areasAll areas in an OSPF internetwork must be directly connected to the backbone area, Area 0. When a direct connection to the backbone area is not possible, a virtual link must be created between two area border routers (ABRs) to connect the remote area to the backbone area through a transit area. The following restrictions apply to virtual links:
– The routers at each end of the virtual link must share a common area.
– The transit area cannot be a stub area.
– One of the routers at either end of the virtual link must connect to the backbone area.Area 0 must be contiguous. The loss of a router or the loss of a link between two routers can cause Area 0 to become discontiguous, or partitioned. A virtual link can be created to connect the discontiguous sections of the Area 0 backbone across a transit area. To connect a discontiguous backbone, the routers at each end of the virtual link must connect to the backbone area and the transit area.
It is important to note that adjacencies formed over virtual links are not visible in the output of the show ip ospf neighbors command. In order to verify that an OSPF adjacency has formed over a virtual link, you can examine the output of the show ip ospf virtuallinks command.
Generic Routing Encapsulation (GRE) tunnels can be used instead of virtual links to form OSPF connections between discontiguous backbone areas or to connect a remote area to the backbone area through a standard area. Unlike virtual links, a GRE tunnel encapsulates and decapsulates all traffic at the tunnel endpoints, including the routing updates. GRE tunnels can also transit a stub area. However, GRE tunnels create additional headers, adding overhead to the traffic.
It is important to note that an adjacency can only remain stable over a GRE tunnel if the destination remains reachable through the tunnel. If the OSPF neighbor is not reachable through the tunnel, OSPF will drop the adjacency.
-
Which of the following is not a GRE tunnel state on a Cisco device? (Select the best answer.)
- Administratively down/down
- Down/up
- Reset/down
- Up/down
- Up/up
Explanation:
Down/up is not a Generic Routing Encapsulation (GRE) tunnel state on a Cisco device. Nor is Down/up a valid state for any other connection on a Cisco device, because a line protocol cannot be in the up state when an interface is in the Down or Administratively down state. Interface states and line protocol states are often presented as a single connection state separated by a slash. The state preceding the slash represents the interface state. The state succeeding the slash represents the line protocol state. In order for the line protocol state to be up, the interface state must also be up.
A GRE tunnel can exist in one of the following four states:
– Administratively down/down
– Reset/down
– Up/down
– Up/upA tunnel in the Administratively down/down state has been configured with the shutdown command. By default, a tunnel interface automatically transitions to the upstate when it is created. Therefore, it is not normally necessary to issue the no shutdowncommand to bring a tunnel interface up unless you have previously issued the shutdowncommand.
A tunnel in the Reset/down state is typically transiting through that state because a software interface reset has occurred. Software resets can happen if the tunnel is misconfigured. For example, a software reset might occur if a tunnel interface has been configured to use its own IP address as a next hop.
A tunnel in the Up/down state indicates that the tunnel interface is configured but something is interfering with the line protocol. This state commonly occurs when the tunnel interface is configured to use an incorrect destination address or when the physical interface has no route to the tunnel’s destination address. It can also occur if the tunnel destination address lies through the tunnel itself.
A tunnel in the Up/up state indicates that both the tunnel interface and the line protocol are up and functional. If something is preventing communication between endpoints on opposite ends of the tunnel and the tunnel is in the Up/up state on each end, you should continue troubleshooting beyond the tunnel configuration.
-
Which of the following statements is true regarding OSPF connections over a GRE tunnel? (Select the best answer.)
- Traffic is encapsulated and decapsulated by tunnel endpoints.
- Tunnel headers do not create any additional overhead.
- The transit area cannot be a stub area.
- Only routing updates are tunneled.
Explanation:
Traffic is encapsulated and decapsulated by tunnel endpoints when Open Shortest Path First (OSPF) connections are formed over a Generic Routing Encapsulation (GRE) tunnel. All areas in an OSPF internetwork must be directly connected to the backbone area, Area 0. When a direct connection to the backbone area is not possible, a GRE tunnel or a virtual link can be created between two area border routers (ABRs) to connect the remote area to the backbone area through a transit area.
However, there are some important differences between the two methods. Unlike virtual links, a GRE tunnel encapsulates and decapsulates all traffic at the tunnel endpoints, including the routing updates. GRE tunnels can also transit a stub area. However, GRE tunnels create additional headers, adding overhead to the traffic. It is important to note that an adjacency can only remain stable over a GRE tunnel if the destination remains reachable through the tunnel. If the OSPF neighbor is not reachable through the tunnel, OSPF will drop the adjacency.
Only routing updates are tunneled when an OSPF connection is formed over a virtual link. All other traffic is sent natively over the physical links. The following restrictions apply to virtual links:
– The routers at each end of the virtual link must share a common area.
– The transit area cannot be a stub area.
– One of the routers at either end of the virtual link must connect to the backbone area.It is important to note that adjacencies formed over virtual links are not visible in the output of the show ip ospf neighbors command. In order to verify that an OSPF adjacency has formed over a virtual link, you can examine the output of the show ip ospf virtuallinks command.
-
Which of the following does not cause a GRE tunnel endpoint on a Cisco device to enter the Up/down state? (Select the best answer.)
- There is no route to the tunnel destination address.
- No IP address has been configured on the tunnel interface.
- The tunnel destination address lies through the tunnel itself.
- The tunnel source is a loopback interface.
Explanation:
A tunnel source that is a loopback interface will not cause a Generic Routing Encapsulation (GRE) tunnel endpoint on a Cisco device to enter the Up/down state. GRE tunnel interfaces support loopback interfaces as source addresses and IP addresses on loopback interfaces as destination addresses, as long as the destination address is reachable by the source device. Interface states and line protocol states are often presented as a single connection state separated by a slash. The state preceding the slash represents the interface state. The state succeeding the slash represents the line protocol state. In order for the line protocol state to be up, the interface state must also be up.
A GRE tunnel can exist in one of the following four states:
– Administratively down/down
– Reset/down
– Up/down
– Up/upA tunnel in the Administratively down/down state has been configured with the shutdown command. By default, a tunnel interface automatically transitions to the upstate when it is created. Therefore, it is not normally necessary to issue the no shutdowncommand to bring a tunnel interface up unless you have previously issued the shutdown command.
A tunnel in the Reset/down state is typically transiting through that state because a software interface reset has occurred. Software resets can happen if the tunnel is misconfigured. For example, a software reset might occur if a tunnel interface has been configured to use its own IP address as a next hop.
A tunnel in the Up/down state indicates that the tunnel interface is configured but something is interfering with the line protocol. This state commonly occurs when the tunnel interface is configured to use an incorrect destination address or when the physical interface has no route to the tunnel’s destination address. It can also occur if the tunnel destination address lies through the tunnel itself.
A tunnel in the Up/up state indicates that both the tunnel interface and the line protocol are up and functional. If something is preventing communication between endpoints on opposite ends of the tunnel and the tunnel is in the Up/up state on each end, you should continue troubleshooting beyond the tunnel configuration.
-
Which of the following cannot be used to connect an OSPF nonbackbone area to the backbone area?
(Select the best answer.)
- a GRE tunnel that connects to the OSPF backbone area
- a virtual link that connects to the OSPF backbone area
- a configuration that redistributes the two OSPF areas into another protocol
- a direct connection to the OSPF backbone area
Explanation:
A configuration that redistributes the two Open Shortest Path First (OSPF) areas into another protocol cannot be used to connect an OSPF nonbackbone area to the backbone area. Redistribution can be used to enable devices in two separate autonomous systems (ASes) to connect and communicate. Therefore, you could enable communication between two separate OSPF configurations by redistributing traffic into another protocol that bridges the two ASes. However, you cannot use redistribution to enable an OSPF connection between a nonbackbone area and a backbone area in a single AS.
You can use a direct connection to the OSPF backbone area to connect an OSPF nonbackbone area to the backbone area. All areas in an OSPF internetwork must be directly connected to the backbone area, Area 0. When a direct connection to the backbone area is not possible, either a virtual link or a Generic Routing Encapsulation (GRE) tunnel must be created between two area border routers (ABRs) to connect the remote area to the backbone area through a transit area. Although it is possible to use either a virtual link or a GRE tunnel to accomplish this task, there are some important differences between the two methods.
Traffic is encapsulated and decapsulated by tunnel endpoints when OSPF connections are formed over a GRE tunnel. All areas in an OSPF internetwork must be directly connected to the backbone area, Area 0. When a direct connection to the backbone area is not possible, a GRE tunnel or a virtual link can be created between two ABRs to connect the remote area to the backbone area through a transit area.
You can use a virtual link that connects to the backbone area. However, only routing updates are tunneled when an OSPF connection is formed over a virtual link. All other traffic is sent natively over the physical links. The following restrictions apply to virtual links:
– The routers at each end of the virtual link must share a common area.
– The transit area cannot be a stub area.
– One of the routers at either end of the virtual link must connect to the backbone area.It is important to note that adjacencies formed over virtual links are not visible in the output of the show ip ospf neighbors command. In order to verify that an OSPF adjacency has formed over a virtual link, you can examine the output of the show ip ospf virtuallinks command.
You can use a GRE tunnel that connects to the backbone area. Unlike virtual links, a GRE tunnel encapsulates and decapsulates all traffic at the tunnel endpoints, including the routing updates. GRE tunnels can also transit a stub area. However, GRE tunnels create additional headers, adding overhead to the traffic. It is important to note that an adjacency can only remain stable over a GRE tunnel if the destination remains reachable through the tunnel. If the OSPF neighbor is not reachable through the tunnel, OSPF will drop the adjacency.
-
A GRE tunnel is configured between RouterB and RouterC. The GRE tunnel sources on each router are loopback interface IP addresses. The GRE tunnel destinations on each router are publicly routable IP addresses and are accessible by each tunnel source router.
After you attempt to bring up the tunnel, which of the following states will the tunnel endpoint on RouterB most likely enter? (Select the best answer.)
- Administratively down/down
- Down/up
- Reset/down
- Up/down
- Up/up
Explanation:
Most likely, the tunnel endpoint on RouterB will enter the Up/up state in this scenario. GRE tunnels can use loopback interfaces as source interfaces. In addition, the destination IP addresses in this scenario are publicly routable and accessible by the sources. Interface states and line protocol states are often presented as a single connection state separated by a slash. The state preceding the slash represents the interface state. The state succeeding the slash represents the line protocol state. In order for the line protocol state to be up, the interface state must also be up.
A GRE tunnel can exist in one of the following four states:
– Administratively down/down
– Reset/down
– Up/down
– Up/upA tunnel in the Administratively down/down state has been configured with the shutdown command. By default, a tunnel interface automatically transitions to the upstate when it is created. Therefore, it is not normally necessary to issue the no shutdowncommand to bring a tunnel interface up unless you have previously issued the shutdown command.
A tunnel in the Reset/down state is typically transiting through that state because a software interface reset has occurred. Software resets can happen if the tunnel is misconfigured. For example, a software reset might occur if a tunnel interface has been configured to use its own IP address as a next hop.
A tunnel in the Up/down state indicates that the tunnel interface is configured but something is interfering with the line protocol. This state commonly occurs when the tunnel interface is configured to use an incorrect destination address or when the physical interface has no route to the tunnel’s destination address. It can also occur if the tunnel destination address lies through the tunnel itself.
A tunnel in the Up/up state indicates that both the tunnel interface and the line protocol are up and functional. If something is preventing communication between endpoints on opposite ends of the tunnel and the tunnel is in the Up/up state on each end, you should continue troubleshooting beyond the tunnel configuration.
-
You issue the show ip ospf neighbor command on a Cisco router after OSPF has converged. The router has a single OSPF neighbor. The output indicates that the OSPF neighbor relationship is in the 2WAY/ DROTHER state.
Which of the following is true? (Select the best answer.)
- The router has not seen its own router ID in a hello packet.
- The router is not connected to a DR or BDR.
- The router is connected to a pointtopoint network.
- The router is about to transition to the FULL/DR state.
Explanation:
A Cisco Open Shortest Path First (OSPF) router that displays the 2WAY/DROTHER state in the output of the show ip ospf neighbor command is not connected to a designated router (DR) or backup DR (BDR). The following is sample output from the show ip ospf neighbor command:
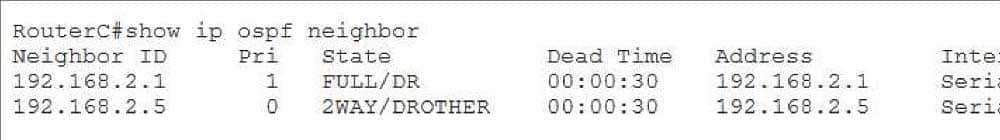
350-401 Part 01 Q14 016 In the output above, RouterC displays an OSPF state of FULL/DR with the neighbor at 192.168.2.1. This state indicates that RouterC has established a full adjacency with the router at 192.168.2.1 and that the router at 192.168.2.1 is the DR. OSPF neighbor routers on a multiaccess network establish full adjacencies only with a DR or BDR. Relationships with other OSPF routers establish twoway adjacencies. A twoway adjacency confirms that bidirectional communication has been established between the neighbors.
OSPF routers in each multiaccess network segment elect a DR and a BDR. The DR generates linkstate advertisements (LSAs) that contain OSPF routing information, and the BDR takes over for the DR if the DR fails. Because only the DR and BDR generate LSAs, network bandwidth is conserved. The DR is typically the router with the highest OSPF priority, and the BDR is typically the router with the secondhighest OSPF priority. If priorities are equal between two or more routers, the router with the highest router ID will be elected. OSPF priorities can range from 0 through 255? the default OSPF priority is 1. A router with a priority of 0 will never become the DR or BDR. A router that is not the DR or BDR will display a state of DROTHER.
When an election occurs, it is not to elect a DR but to elect a BDR. The router with the highest interface priority (or the highest router ID from among routers with the highest priority) elects itself as the BDR. If there is no DR on the segment, the BDR will promote itself to DR and a new BDR election is held by the remaining routers. If the DR on a segment fails, the BDR promotes itself to the DR and a new BDR election is again held by the remaining routers.
The router is not connected to a pointtopoint network. A DR and BDR are elected only on multiaccess networks? they are not elected on pointtopoint networks. An OSPF router that has formed a neighbor relationship with another OSPF router on a pointtopoint network will display the FULL/-state in the output of the show ip ospf neighbor command.
The router is not about to transition to the FULL/DR state, because in this scenario the OSPF network has already converged. This means that a BDR and DR have already been elected. In addition, the router has seen its router ID in a hello packet, because the OSPF network has converged and the neighbor relationship is in its final state.
-
You issue the show ip ospf neighbor command on a Cisco router. The router’s OSPF neighbor state is FULL/-.
Which of the following is most likely true about the OSPF router? (Select the best answer.)
- It is the DR.
- It is the BDR.
- It is on a multiaccess network.
- It is on a pointtopoint network.
- It is not capable of forming a neighbor relationship.
Explanation:
Most likely, the router is on a pointtopoint network if the output of the show ip ospf neighbor command reveals that the router’s Open Shortest Path First (OSPF) state is FULL/-. This output indicates that the router has formed a full adjacency with its neighbor but that the neighbor is neither a designated router (DR) nor a backup DR (BDR). OSPF routers that are connected in a pointtopoint fashion do not elect a DR or BDR. If the OSPF neighbor were not on a pointtopoint network and the network had converged without error, the neighbor state would most likely be one of the following:
– FULL/DR
– FULL/BDR
– 2WAY/DROTHEROn a multiaccess network, OSPF routers exchange databases only with the DR and BDR, which helps prevent congestion. Therefore, routers with a 2WAY/DROTHER state do not exchange full databases with those neighbors.
The router is not only capable of forming a neighbor relationship, but has formed a relationship with its neighbor. On a pointtopoint OSPF network, a neighbor state of FULL/-indicates that the OSPF neighbors have formed a full adjacency and are thus capable of exchanging their entire databases.
The router is neither the DR nor the BDR. In addition, the router is not on a multiaccess network. OSPF routers in each multiaccess network segment elect a DR and a BDR. The DR generates linkstate advertisements (LSAs) that contain OSPF routing information, and the BDR takes over for the DR if the DR fails. Because only the DR and BDR generate LSAs, network bandwidth is conserved. The DR is typically the router with the highest OSPF priority, and the BDR is typically the router with the secondhighest OSPF priority. If priorities are equal between two or more routers, the router with the highest router ID will be elected. OSPF priorities can range from 0 through 255; the default OSPF priority is 1. A router with a priority of 0 will never become the DR or BDR. A router that is not the DR or BDR will display a state of DROTHER.
-
Which of the following would be displayed when you issue the show ip eigrp interfacescommand? (Select the best answer.)
- the number of EIGRP peers per interface
- the IP addresses of EIGRP peers on each interface
- the uptime for active neighbors on a particular interface
- the FD to a network from an interface
Explanation:
The number of Enhanced Interior Gateway Routing Protocol (EIGRP) peers per interface would be displayed when you issue the show ip eigrp interfaces command. The show ip eigrp interfaces command will also display information regarding EIGRPspecific settings and statistics on interfaces in which EIGRP is active. You can include a specific interface in the command to ensure that only information for that interface will be displayed? otherwise, information for all active EIGRP interfaces will be returned. The following displays sample output from the show ip eigrp interfaces command:
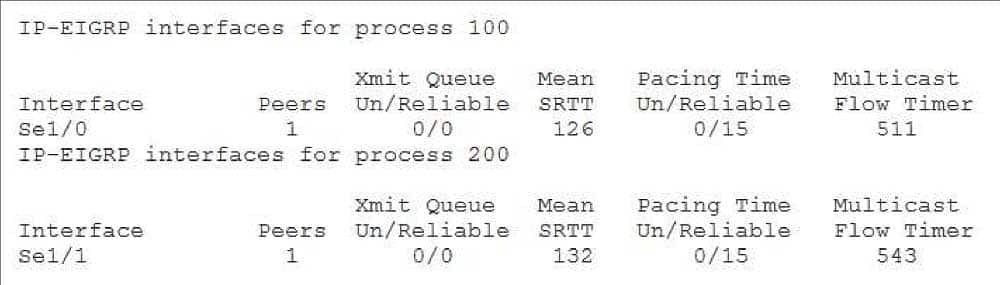
350-401 Part 01 Q16 017 This output contains information such as the elapsed time required for a packet to travel roundtrip through an interface and the number of directly connected neighbors. In addition, the output contains information about the EIGRP multicast flow timer.
The IP address of EIGRP peers on each interface and the uptime for active neighbors on a particular interface are not displayed when you issue the show ip eigrp interfaces command. There are multiple commands you could issue in order to find the IP address of EIGRP peers on each interface. For example, you could issue the show ip eigrp neighborscommand, which displays the autonomous system (AS) number for this neighbor pair and the uptime for active neighbors in addition to the peer’s IP address. You could also issue the show ip eigrp accounting command, which displays the number of prefixes learned by a source and the interface that received the information from the peer in addition to the peer’s IP address.
The feasible distance (FD) to a network from an interface is not displayed when you issue the show ip eigrp interfaces command. The topology table contains successors and feasible successors. Feasible successors are neighbors that are guaranteed to represent a loopfree path to a destination. To display the topology table, you should issue the show ip eigrp topology command. Each route contains two numbers inside parentheses. The first number is the FD, which is the total distance to the destination network through that nexthop router. The second number is the advertised distance (AD), also known as the reported distance (RD), which is the cost that the nexthop router has calculated for the route. The router with the lowest FD becomes the successor. The route through the successor is placed in the routing table and is used to route packets to the destination network.
-
You issue the show ip ospf neighbor command on a Cisco router. The router’s OSPF neighbor state is FULL/DR.
Which of the following is most likely true about the OSPF router? (Select the best answer.)
- It is the DR.
- It is the BDR.
- It will exchange its entire database with the DR.
- It is on a pointtopoint network.
Explanation:
Most likely, the router will exchange its entire database with the designated router (DR) if the output of the show ip ospf neighbor command reveals that the router’s Open Shortest Path First (OSPF) state is FULL/ DR. This output indicates that the router has formed a full adjacency with its neighbor and that the neighbor is the DR. This output also indicates that the router is configured on a multiaccess network because OSPF routers that are connected in a pointtopoint fashion do not elect a DR or BDR. The neighbor states for a multiaccess OSPF router include all of the following:
– FULL/DR
– FULL/BDR
– 2WAY/DROTHEROn a multiaccess network, OSPF routers exchange databases only with the DR and BDR, which helps prevent congestion. Therefore, routers with a 2WAY/DROTHER state do not exchange full databases with those neighbors.
The router is not on a pointtopoint network. On a pointtopoint OSPF network, a neighbor state of FULL/indicates that the OSPF neighbors have formed a full adjacency and are thus capable of exchanging their entire databases. Because neither a DR nor a BDR exists on a pointtopoint network, the second field in the state output will be a dash.
The router is neither the DR nor the BDR. The first field in the state output indicates the state of the adjacency. The second field in the state indicates the type of OSPF router to which the router is connected, not the role of the router itself.
The DR generates linkstate advertisements (LSAs) that contain OSPF routing information, and the BDR takes over for the DR if the DR fails. Because only the DR and BDR generate LSAs, network bandwidth is conserved. The DR is typically the router with the highest OSPF priority, and the BDR is typically the router with the secondhighest OSPF priority. If priorities are equal between two or more routers, the router with the highest router ID will be elected. OSPF priorities can range from 0 through 255? the default OSPF priority is 1. A router with a priority of 0 will never become the DR or BDR. A router that is not the DR or BDR will display a state of DROTHER.
-
Which of the following would not be displayed in the output of the show ip eigrp interfaces command?
(Select the best answer.)
- the number of EIGRP peers per interface
- the value of the multicast flow timer
- the mean roundtrip time for EIGRP packets through an interface
- the number of EIGRP Hello packets sent and received
Explanation:
Of the available choices, the number of Enhanced Interior Gateway Routing Protocol (EIGRP) Hello packets sent and received on an interface will not be displayed in the output of the show ip eigrp interfaces command. To see the number of Hello packets sent and received by an EIGRP process on a router, you should issue the show ip eigrp traffic command.
The number of Enhanced Interior Gateway Routing Protocol (EIGRP) peers per interface would be displayed when you issue the show ip eigrp interfaces command. The show ip eigrp interfaces command will also display information regarding EIGRP specific settings and statistics on interfaces in which EIGRP is active. You can include a specific interface in the command to ensure that only information for that interface will be displayed? otherwise, information for all active EIGRP interfaces will be returned. The following displays sample output from the show ip eigrp interfaces command:

350-401 Part 01 Q18 018 This output contains information such as the elapsed time required for a packet to travel roundtrip through an interface and the number of directly connected neighbors. In addition, the output contains information about the EIGRP multicast flow timer.
-
Which of the following cannot be exchanged between spoke sites in a DMVPN design? (Select 2 choices.)
- unicast traffic
- multicast traffic
- VoIP traffic
- dynamic routing traffic
Explanation:
Multicast traffic and dynamic routing traffic cannot be exchanged between spoke sites in a Dynamic Multipoint virtual private network (DMVPN) design. Multicast traffic and dynamic routing traffic must be sent from spoke to hub.DMVPN enables an administrator to easily configure scalable IP Security (IPSec) virtual private networks (VPNs) using a hubandspoke design. The hub router or routers are typically assigned a static IP address? the spoke routers can be dynamically addressed. DMVPN requires Generic Routing Encapsulation (GRE), Next Hop Resolution Protocol (NHRP), and a dynamic routing protocol such as Enhanced Interior Gateway Routing Protocol (EIGRP) or Open Shortest Path First (OSPF). A multipoint GRE (mGRE) tunnel is used to carry multiple IPSec or GRE tunnels. NHRP is used to create a database of tunnel addresstoreal address mappings.
Unicast traffic and Voice over IP (VoIP) traffic can be exchanged between spoke sites. However, only limited Quality of Service (QoS) mechanisms can be provided between spokes, thereby preventing VoIP and video traffic from being properly prioritized. -
RouterA and RouterB are connected routers.
You issue the show clns neighbors command on RouterA and receive the following output:
System Id Interface SNPA State Holdtime ….. Type Protocol
RouterB Et0/0 0000.0000.000b Up 23 L1 IS-ISWhich of the following statements must be true? (Select the best answer.)
- RouterA and RouterB are in the same area.
- RouterA and RouterB are in different areas.
- RouterB is configured for L1 routing only.
- RouterB is configured for L1/L2 routing.
- RouterA is a backbone router.
Explanation:
RouterA and RouterB are in the same area. Routers running the Intermediate SystemtoIntermediate System (IS-IS) routing protocol are placed into administrative domains called areas. Each ISIS router resides in only one area. The collection of all areas managed by a single organization is called a routing domain.Each ISIS router is configured with a routing level. Level 1 (L1) routers are capable of intraarea routing, which delivers data within a single area. The output of the show clns neighbors command indicates that RouterB has established an L1 adjacency with RouterA; therefore, both routers must be in the same area.
Level 2 (L2) routers are capable of interarea routing, which delivers data between areas. If RouterA and RouterB were in separate areas and both routers were configured for L2 routing, you would have received the following output from the show clns neighbors command:
System Id Interface SNPA State Holdtime Type Protocol
RouterB Et0/0 0000.0000.000b Up 23 L2 IS-IS
Level 1/Level 2 (L1/L2) routers are capable of both intraarea and interarea routing and maintain a separate linkstate database for each. If RouterA and RouterB were in the same area and both routers were configured for L1/L2 routing, you would have received the following output from the show clns neighbors command:System Id Interface SNPA State Holdtime Type Protocol
RouterB Et0/0 0000.0000.000b Up 23 L1L2 IS-ISYou can configure the routing level for an ISIS process by issuing the istype {level1 | level12 | level2only} command, and you can configure the routing level for an ISIS interface by issuing the isis circuittype {level1 | level12 | level2only} command. By default, all ISIS routing processes and interfaces are configured for L1/ L2 routing.
RouterB is configured for either L1 routing or L1/L2 routing. However, the output of the show clns neighbors command in this scenario does not indicate which routing level RouterB is configured to use. If either router was configured for L1 routing only, the Typefield of the show clns neighbors command would show L1, even if the other router were an L1/L2 router.
The output of the show clns neighbors command in this scenario does not indicate whether RouterA is a backbone router. ISIS requires that all Level 2 (L2) and L1/L2 routers be connected to form a backbone through the routing domain. If RouterA were configured for L1/L2 routing, RouterA would be a backbone router.When an ISIS routing level mismatch, authentication mismatch, or maximum transmission unit (MTU) mismatch occurs, an ISIS adjacency will not form, but the output of the show clns neighbors command might instead show an End SystemtoIntermediate System (ESIS) adjacency. ESIS is used to discover end systems. If RouterA and RouterB were in different areas and if either router was configured for L1 routing only, you might see the following output after issuing the show clns neighbors command on RouterA:
System Id Interface SNPA State Holdtime Type Protocol
RouterB Et0/0 0000.0000.000b Up 23 IS ES-IS