350-401 : Implementing Cisco Enterprise Network Core Technologies (ENCOR) : Part 04
-
Which of the following statements is true about DiffServ class AF41? (Select the best answer.)
- AF41 has a low priority and a low drop probability.
- AF41 has a low priority and a high drop probability.
- AF41 has a high priority and a low drop probability.
- AF41 has a high priority and a high drop probability.
Explanation:
DiffServ class AF41 has a high priority and a low drop probability. AF41 is a Differentiated Services Code Point (DSCP) value, which is a 6bit header value that identifies the Quality of Service (QoS) traffic class that is assigned to the packet. DSCP values beginning with AF are called Assured Forwarding (AF) perhop behaviors (PHBs), which are defined in Request for Comments (RFC) 2597. AF separates packets into four queue classes and three drop probabilities. The AF values are specified in the format AFxy, where x is the queue class and y is the drop probability. The following table displays the AF values with their queue classes and drop rates:
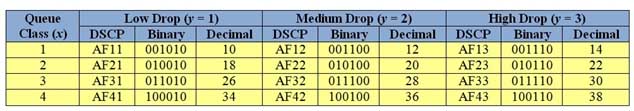
350-401 Part 04 Q01 042 AF11 has a low priority and a low drop probability. AF13 has a low priority and a high drop probability. AF43 has a high priority and a high drop probability.
The first three DSCP bits correspond to the queue class, the fourth and fifth DSCP bits correspond to the drop probability, and the sixth bit is always set to 0. To quickly convert AF values to decimal values, you should use the formula 8x + 2y. For example, AF41 converts to a decimal value of 34, because (8 x 4) + (2 x 1) = 32 + 2 = 34.
Packets with higher AF values are not necessarily given preference over packets with lower AF values. Packets with a higher queue class value are given queuing priority over packets with a lower queue class, but packets with a higher drop rate value are dropped more often than packets with a lower drop rate value. -
You issue the show mls qos maps cosdscp command and receive the following output:

350-401 Part 04 Q02 043 An untagged packet arrives on a CoStrusted port. The port is using the default CoS settings.
Which of the following internal DSCP values will the switch use for the packet? (Select the best answer.)- 0
- 8
- 24
- 46
- 56
Explanation:
The switch will use an internal Differentiated Services Code Point (DSCP) value of 0 for the packet. The Class of Service (CoS)toDSCP map is used to generate an internal DSCP value for packets that arrive on a CoStrusted port. By default, the CoS for untagged packets is set to 0. The CoStoDSCP map in this scenario indicates that a CoS value of 0 corresponds to a DSCP value of 0.
The CoStoDSCP map in this scenario is the default CoStoDSCP map. You can modify the CoStoDSCP map by issuing the mls qos map cosdscp dscp1 dscp2 …dscp8 command. The no mls qos map cosdscp command causes the switch to use the default CoStoDSCP map.
The CoS field is a Quality of Service (QoS) 3bit marking field, whereas the DSCP is a QoS 6bit marking field. The following table shows the relationship between CoS and DSCP values:
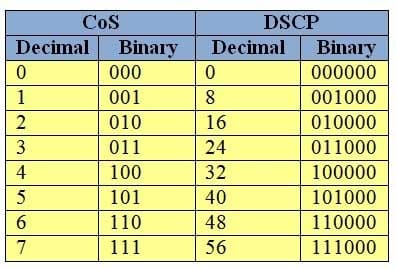
350-401 Part 04 Q02 044 The first three bits of the DSCP value are the same as the CoS value? the DSCP value just has three extra 0 bits appended to the end. If you know the CoS value of a packet, you can derive the default DSCP value by converting the CoS value to binary, appending three 0 bits, and converting back to decimal.
If the packet in this scenario had a CoS of 1, or if the default CoS for the port were set to a value of 1, the switch would have used an internal DSCP value of 8. If the packet in this scenario had a CoS of 3, or if the default CoS for the port were set to a value of 3, the switch would have used an internal DSCP value of 24. If the packet in this scenario had a CoS of 7, or if the default CoS for the port were set to a value of 7, the switch would have used an internal DSCP value of 56.
The DSCP value 46 corresponds to a special classification known as DSCP Expedited Forwarding (EF). DSCP EF, which is defined in Request for Comments (RFC) 2598, indicates a highpriority packet that should be given queuing priority over other packets but should not be allowed to completely monopolize the interface. Voice over IP (VoIP) traffic is often assigned to DSCP EF. -
Which of the following command sets correctly configures basic IPv6toIPv4 connectivity for NAT-PT? (Select the best answer.)
-
Router(config)#ipv6 nat prefix 2000:ABC::/32Router(config)#ipv6 nat
-
Router(config)#ipv6 nat prefix 2000:ABC::/64Router(config)#ipv6 nat
-
Router(config)#ipv6 nat prefix 2000:ABC::/96Router(config)#ipv6 nat
-
Router(config)#ipv6 nat prefix 2000:ABC::/32 Router(config)#interface fastethernet 1/1 Router(configif)#ipv6 nat Router(configif)#interface fastethernet 1/2 Router(configif)#ipv6 nat
-
Router(config)#ipv6 nat prefix 2000:ABC::/64 Router(config)#interface fastethernet 1/1 Router(configif)#ipv6 nat Router(configif)#interface fastethernet 1/2 Router(configif)#ipv6 nat
-
Router(config)#ipv6 nat prefix 2000:ABC::/96 Router(config)#interface fastethernet 1/1 Router(configif)#ipv6 nat Router(configif)#interface fastethernet 1/2 Router(configif)#ipv6 nat
Explanation:
The following command set correctly configures basic IPv6toIPv4 connectivity for Network Address TranslationProtocol Translation (NATPT):Router(config)#ipv6 nat prefix 2000:ABC::/96 Router(config)#interface fastethernet 1/1 Router(configif)#ipv6 nat Router(configif)#interface fastethernet 1/2 Router(configif)#ipv6 nat
NAT-PT is used to enable communication between IPv4only hosts and IPv6only hosts by translating IPv4 packets to IPv6 packets and IPv6 packets to IPv4 packets. To enable NATPT, you must assign a global NATPT prefix, enable NATPT on the incoming and outgoing interfaces, and create IPv4toIPv6 and IPv6toIPv4 address mappings. To assign a global NATPT prefix, you should issue the ipv6 nat prefixipv6prefix/ prefixlength command from global configuration mode, where prefixlength is always 96. Therefore, the ipv6 nat prefix 2000:ABC::/32 command and the ipv6 nat prefix 2000:ABC::/64 command are invalid.
To enable NATPT on an interface, you should issue the ipv6 nat command from interface configuration mode on the incoming and outgoing interfaces. You cannot issue the ipv6 nat command from global configuration mode.
A NATPT router must contain IPv6toIPv4 and IPv4toIPv6 address mappings so that the router knows how to correctly translate IPv4 and IPv6 addresses. There are four methods for using NATPT:-IPv4mapped NATPT
-Static NATPT
-Dynamic NATPT
-Port Address Translation (PAT)IPv4mapped NATPT enables IPv6 traffic to be sent to an IPv4 network without requiring that IPv6 destination address mapping be configured. To configure IPv4mapped NATPT, you should issue the ipv6 nat prefix ipv6prefixv4mapped {accesslistname | ipv6prefix} command from global configuration mode or interface configuration mode.
Static NATPT creates static IPv6toIPv4 or IPv4toIPv6 address mappings. To create a static IPv6toIPv4 address mapping, you should issue the ipv6 nat v6v4 source ipv6address ipv4address command. To create a static IPv4toIPv6 mapping, you should issue the ipv6 nat v4v6 source ipv6address ipv4address command.
Dynamic NATPT allocates IPv6toIPv4 or IPv4toIPv6 address mappings from a pool. When a session is established, a onetoone mapping is created? the mapping is then removed when the session is finished. To configure dynamic IPv6toIPv4 address mapping, you should issue the ipv6 nat v6v4 source {list accesslistname | routemapmapname} pool poolname command. You should then create the address pool by issuing the ipv6 nat v6v4 pool poolname startipv4 endipv4 prefixlength prefixlengthcommand. To configure dynamic IPv4toIPv6 address mapping, you should issue the ipv6 nat v4v6 sourcelist {accesslistnumber | accesslistname} pool poolname command. You should then create the address pool by issuing the ipv6 nat v4v6 pool poolname startipv6 endipv6 prefixlength prefixlength command.
PAT allows multiple IPv6 addresses to be mapped to one or more IPv4 addresses. To use PAT with a single IPv4 address, you should issue the ipv6 nat v6v4 source {list accesslistname | routemap mapname} interface interfacenameoverload command. To use PAT with a pool of IPv4 addresses, you should issue the ipv6 nat v6v4 source {listaccesslistname | routemap mapname} pool poolnameoverload command. You should then create the address pool by issuing the ipv6 nat v6v4 pool poolname startipv4 endipv4 prefixlength prefixlength command. -
-
In what order will a Rapid-PVST+ switch port pass through the port states? (Select the best answer.)
- blocking, spanning, listening, forwarding
- discarding, learning, forwarding
- blocking, listening, learning, forwarding
- learning, discarding, forwarding
- blocking, learning, listening, forwarding
- Ports enter the forwarding state immediately
Explanation:
A Rapid-Per-VLAN Spanning Tree Plus (PVST+) switch port will pass through the following states:
-Discarding
-Learning
-Forwarding
RapidPVST combines the rapid transition of ports by Rapid Spanning Tree Protocol (RSTP) with the creation of spanning trees for each virtual LAN (VLAN) by PVST+. RSTP improves the slow transition of a Spanning Tree Protocol (STP) port to the forwarding state, thereby increasing convergence speed.
STP is used to eliminate loops in a switched network that is designed with redundant paths. There can be only one active path at any given time between any two endpoints on an Ethernet network. If multiple paths between the same two endpoints exist at the same time, switching loops can occur. STP activates and deactivates links dynamically to allow the network to respond to and reroute traffic around a failed link.
When RSTP is enabled, each port first enters the discarding state, in which a port receives bridge protocol data units (BPDUs) and directs them to the system module? however, the port neither sends BPDUs nor forwards any frames. The switch port then transitions to the learning state, in which it begins to transmit BPDUs and learn addressing information. Finally, a switch port transitions to the forwarding state, in which the switch port forwards frames. If a switch port determines at any time during the RSTP state process that a switching loop would be caused by entering the forwarding state, the switch port again enters the discarding state, in which the switch receives BPDUs and directs them to the system module but does not send BPDUs or forward frames.
STP port states are somewhat different from RSTP port states. A switch port will pass through the following STP states after a switch is turned on:
-Blocking
-Listening
-Learning
-Forwarding
When STP is enabled and a switch is turned on, each port first enters the blocking state, which is similar to the RSTP discarding state. The switch port then transitions to the listening state, in which it begins processing BPDUs as it listens for information to determine whether it should transition to the learning state. After entering the learning state, a switch port begins to transmit BPDUs and learn addressing information with which to build the switching database. Finally, a switch port transitions to the forwarding state, in which the switch port forwards frames. If a switch port determines at any time during the STP state process that a switching loop would be caused by entering the forwarding state, the switch port enters the disabled state, in which the switch receives BPDUs but does not direct them to the system module.
The primary differences between STP and RSTP are the port states and the speed of convergence. By default, STP takes 50 seconds to converge. By contrast, RSTP takes less than 10 seconds to converge.
Switch ports do not immediately enter the forwarding state when the switch is first turned on, unless PortFast is enabled on the port. PortFast enables a switch port to go directly to the forwarding state rather than pass through the normal STP or RSTP states. However, you should enable PortFast only on switch ports that are connected directly to endpoint workstations? otherwise, switching loops may occur.
Blocking and listening are valid STP port states but are not valid RSTP port states. Spanning is not a valid STP or RSTP port state. -
Which of the following regular expression characters should be placed at the end of a BGP AS path filter to indicate the originating AS? (Select the best answer.)
- $
- ^
- *
- ]
- .
- _
Explanation:
The dollar sign ($) regular expression character should be placed at the end of a Border Gateway Protocol (BGP) autonomous system (AS) path filter to indicate the originating AS. Regular expressions are used to locate character strings that match a particular pattern. AS path filters are used to permit or deny routes that match the regular expression.
The $ character indicates that the preceding characters should match the end of the string. The originating router will insert its AS number into the AS path, and subsequent routers will prepend their AS numbers to the beginning of the AS path string. The last AS number in the AS path is the originating AS. For example, the ip as-path access-list 1 permit ^111_999$ command permits paths that originate from AS 999.
The caret (^) character should be placed at the beginning of a BGP AS path filter to indicate the AS from which the path was learned. The ^ character indicates that the subsequent characters should match the start of the string. The first number in an AS path indicates the AS from which the path was learned. For example, the ip aspath accesslist 1 permit ^111_999$ command permits paths that are learned from AS 111.
The underscore (_) character is used to indicate a comma, a brace, the start or end of an input string, or a space. When used between two AS path numbers, the _ character indicates that the ASes are directly connected. For example, the ip aspath accesslist 1 permit ^111_999$ command indicates that AS 111 and AS 999 should be directly connected.
The period (.) character is used to represent any single character. For example, the ip aspath accesslist 1 permit ^…_999$ command permits paths that originate from AS 999 and are learned from any threedigit AS.
The bracket (]) character is used to indicate a set of characters or a range of characters. For example, the ip aspath accesslist 1 permit ^[09]_999$ command permits paths that originate from AS 999 and are learned from any AS numbered from 0 through 9, and the ip aspath accesslist 1 permit ^[123]_999$ command permits paths that originate from AS 999 and are learned from AS 1, AS 2, or AS 3.
The asterisk (*) character indicates zero or more sequences of the previous expression. For example, the expression [09]* indicates a string of zero or more digits. Therefore, the ip aspath accesslist 1 permit ^111_ [09]*$ command permits paths that are learned from AS 111 and originate from any AS. -
You issue the following commands:

350-401 Part 04 Q06 045 What will occur when a user enters a lowercase y at the prompt? (Select the best answer.)
- The configure terminal command will be executed, and the router will be placed into globalconfiguration mode.
- The configure terminal command will not be executed, because the EEM applet requires anuppercase Y.
- The configure terminal command will not be executed, because the EEM applet is missing the set 9_exit_status 0 command.
- The configure terminal command will not be executed, because the event cli command should usethe sync no keywords.
Explanation:
The configure terminal command will not be executed, because the Embedded Event Manager (EEM) applet requires an uppercase Y. The event cli command configures EEM to monitor commandline interface (CLI) commands and to trigger the event when a specified pattern is matched one or more times. The action command indicates the action that should take place. Actions are sorted based on the alphanumeric label, which is issued after the action keyword. The action string match command compares two values? if the values match, EEM sets the $_string_result variable to a value of 1, and if the values do not match, EEM sets the $_string_result variable to a value of 0. The action if command checks a condition? if the condition is true, the actions before the action end command are performed, and if the condition is false, the actions after the action end command are performed.
The action string match command is casesensitive. To force a caseinsensitive comparison, you can issue the action string match command with the nocase keyword. For example, the action 4 string match nocase “$answer” “Y” command would accept an uppercase Y or a lowercase y as a match. Alternatively, you can issue the action string tolower command to store a variable in lowercase or the action string touppercommand to store a variable in uppercase. For example, the following command set would store a lowercase y as an uppercase Y, effectively forcing a caseinsensitive comparison:

350-401 Part 04 Q06 046 When a user enters a lowercase y at the prompt, the string toupper command will store the answer in $_string_result as an uppercase Y. The strings are compared, and because they match, the router is placed into global configuration mode.
The EEM applet is not missing the set 9 _exit_status 0 command. The sync yeskeywords are used with the event cli command to configure synchronous processing. With synchronous processing, the EEM applet must finish before the CLI command can be executed, and the _exit_status variable determines whether the CLI command is executed or skipped. If the _exit_status variable is set to a value of 0 or is not configured, the CLI command will not execute after the EEM applet is finished; if the _exit_status variable is set to a value of 1, the CLI command will execute after the EEM applet is finished. Therefore, the set 9 _exit_status 0 command would not cause the configure terminal command to be executed. If the set 9 _exit_status 1 command were issued in this scenario, the configure terminal command would be executed after the applet is finished, regardless of what answer the user provided.
Issuing the sync no keywords in the event cli command would not cause the configure terminal command to be executed unless the skip no keywords were also issued. The sync no keywords are used with the event cli command to configure asynchronous processing. With asynchronous processing, the EEM applet is processed at the same time the CLI command is executed. When you issue the event cli command with the sync nokeywords, you must also include the skip no or skip yes keywords to indicate whether the CLI command should be executed or skipped, respectively. If you were to issue the event cli pattern “configure terminal” sync no skip yes command in this scenario, the configure terminal command would not be executed unless the user enters an uppercase Y at the prompt. If you were to issue the event cli pattern “configure terminal” sync no skip yes command, the configure terminal command would be executed immediately, regardless of what answer the user provided. -
You issue the following commands on RouterB:
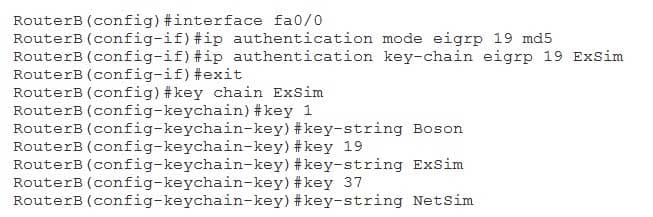
350-401 Part 04 Q07 047 Which of the following key strings will RouterB use when sending EIGRP packets? (Select the best answer.)
- Boson
- ExSim
- NetSim
- any of the three key strings
Explanation:
RouterB will use the key string Boson when sending Enhanced Interior Gateway Routing Protocol (EIGRP) packets. EIGRP supports Message Digest 5 (MD5) authentication of routing updates to prevent a router from receiving routing updates from unauthorized routers. Authentication is configured on a perinterface basis.
To configure an interface to authenticate EIGRP packets, you should first enter interface configuration mode by issuing the interfacetype number command from global configuration mode. Next, you should enable MD5 authentication by issuing the ip authentication mode eigrp autonomoussystemmd5 command in interface configuration mode. Finally, you should issue the ip authentication keychain eigrpautonomoussystem keychain command in interface configuration mode to specify the key chain that should be used. In this scenario, RouterB is configured for EIGRP autonomous system (AS) 19.
To create a key chain, you should issue the key chain chainname command from global configuration mode. The chain name is locally significant; it is used only to match a set of keys with a local router interface. Therefore, key chain names do not have to match between neighbor routers. In this scenario, RouterB is configured with the key chain name ExSim.
After you create a key chain, you must specify at least one key number by issuing the keynumber command in keychain configuration mode, where number is an integer from 0 through 2147483647. If multiple key commands are used to create multiple keys, the numbers do not need to be sequential. When sending EIGRP packets, the router will use the lowestnumbered key. Therefore, RouterB will use key 1 when sending EIGRP packets. When receiving EIGRP packets, the router will use any valid key that is configured on the router. Therefore, RouterB can use any of the keys when receiving EIGRP packets. However, the key numbers must match on each router; if a neighbor router uses the key string NetSim, it must also be assigned key number 37.
Each key can have only one authentication string. To specify the authentication string, you should issue the keystring text command in keychain key configuration mode, where text is a string of up to 80 casesensitive letters and numbers; the first character cannot be a number. -
You administer the OSPF network shown in the diagram above.

350-401 Part 04 Q08 048 The reference bandwidth has been changed to 1000 on every router in the network.
What is the cost of the route from RouterA to RouterC? (Select the best answer.)- 2
- 3
- 11
- 12
- 20
Explanation:
In this scenario, the cost of the route from RouterA to RouterC is 3. In an Open Shortest Path First (OSPF) network, a cost is associated with every link on the network. The OSPF routing process on each router calculates the optimal route to other routers in the network based on the sum of the link costs to those routers. The route with the lowest cost is considered the best. If there is more than one route with the same cost, then the OSPF routing process will use load balancing to distribute traffic evenly among the routes. The cost of each link and the optimal route from RouterA to RouterC are shown in the following exhibit:
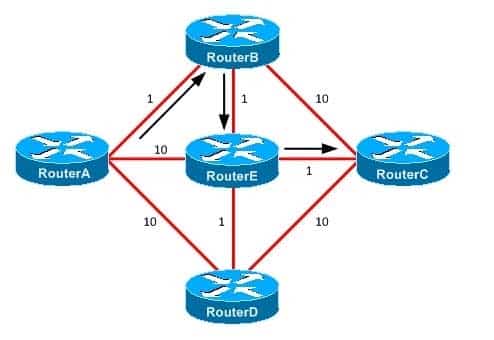
350-401 Part 04 Q08 049 The cost of a link is based on the interface bandwidth and the reference bandwidth, as indicated by the following formula:
cost = reference bandwidth / interface bandwidth
The default reference bandwidth is 100 Mbps. If a bandwidth has not been configured on an interface, the OSPF process will use the default value for the interface type. For example, a 100Mbps Fast Ethernet interface has a default interface bandwidth of 100. The minimum supported cost for an OSPF interface is 1, and any values that calculate to less than 1 are rounded up to 1. Therefore, any link with an interface bandwidth greater than or equal to 100 Mbps will result in a cost of 1 by default. In this scenario, the reference bandwidth is 1000 Mbps. Thus a FastEthernet interface will have a cost of 10, and a 1Gbps GigabitEthernet interface will have a cost of 1.
An OSPF process uses cost values to generate its shortest path first (SPF) tree and then to determine the optimal routes to all known networks. Because the minimum cost value is 1, the reference bandwidth should be a value greater than or equal to the bandwidth of the fastest routed link in the administrative domain. If the reference bandwidth is less than the fastest routed link on the network, a situation can arise where the costs of two interfaces are the same even though their link speeds are different. For example, if the reference bandwidth in this scenario were reset to its default value, the cost of every link would have a value of 1. Because all links would then appear to have the same cost, the OSPF routing process would not be able to distinguish between the FastEthernet and GigabitEthernet links in the network. The OSPF process would then perform equalcost load balancing to distribute packets evenly among the available paths. This distribution would cause some packets in this example to take suboptimal routes to their destinations.
You can issue the autocost command from router configuration mode to change the reference bandwidth for an OSPF routing process. The syntax for the autocost command is autocost reference-bandwidth ref-bw, where ref-bw is an integer between 1 and 4294967. Alternatively, you can manually configure a cost at the interface level by issuing the ip ospf cost command. -
Which of the following information does a Type 2 LSA contain? (Select the best answer.)
- subnet information for an entire area
- external routes redistributed into OSPF
- the router ID and the IP addresses for a single router
- subnet and router information for all the routers on a segment
Explanation:
A Type 2 linkstate advertisement (LSA) contains subnet and router information for all the routers on a segment. Type 2 LSAs, which are also called network LSAs, are generated by only the designated router (DR) to each of the segments connected to the DR. These LSAs are not propagated outside the area in which they originate? they are flooded only within the local area.
A Type 1 LSA contains the router ID and the IP addresses for a single router. Type 1 LSAs, which are also called router LSAs, are generated by all Open Shortest Path First (OSPF) routers on a segment. Like Type 2 LSAs, Type 1 LSAs are not propagated outside the area in which they originate; they are flooded only within the local area.
A Type 3 LSA contains subnet information for an entire area. Type 3 LSAs, which are also called network summary LSAs, are generated by area border routers (ABRs). Unlike Type 1 and Type 2 LSAs, Type 3 LSAs are advertised between areas throughout an autonomous system (AS) except into totally stubby areas.
A Type 5 LSA contains external routes redistributed into OSPF. Type 5 LSAs, which are also called ASexternal LSAs, are generated by autonomous system boundary routers (ASBRs). Therefore, Type 5 LSAs are advertised throughout an AS except into stub areas, totally stubby areas, and notsostubby areas (NSSAs). -
Which of the following terms refers to a method that is used to pass IPv6 traffic over an IPv4-only network? (Select the best answer.)
- 6to4 tunneling
- 4to6 tunneling
- NAT64
- dual stacks
Explanation:
To pass IPv6 traffic over a network that supports only IPv4, a tunneling method is required, such as 6to4 tunneling. The 6to4 tunneling method encapsulates an IPv6 packet inside an IPv4 header. Routers on the IPv4only network recognize only the IPv4 header information? the IPv6 packet is simply carried as the data payload of the IPv4 packet.
The 4to6 tunneling method is the reverse of the 6to4 tunneling method. Routers on the IPv6only network recognize only the IPv6 header information. Therefore, IPv4 packets must be encapsulated inside an IPv6 header so that they can pass over the IPv6only network.
Network Address Translation 64 (NAT64) enables communication between IPv4only hosts and IPv6only hosts. NAT64 translates IPv4 packets to IPv6 packets and translates IPv6 packets to IPv4 packets. However, a NAT64 router must contain address mappings so that the router can correctly translate IPv4 and IPv6 addresses. NAT64 supports stateless and stateful address translation. When performing stateless translation, NAT64 uses algorithms to create a onetoone relationship between IPv6 addresses on the inside network and IPv4 addresses on the outside network. When performing stateful translation, NAT64 maps multiple IPv6 addresses to a single IPv4 address and keeps track of the state of each connection. Static mappings can also be applied manually.
Dual stacks are used so that a host or router can use IPv4 and IPv6 simultaneously. Dualstack devices are configured with an IPv4 address and an IPv6 address; thus a dualstack device can communicate directly with both IPv4 and IPv6 devices without requiring protocol translation. However, a network infrastructure capable of routing both IPv4 and IPv6 traffic is required. -
You administer the network shown above.
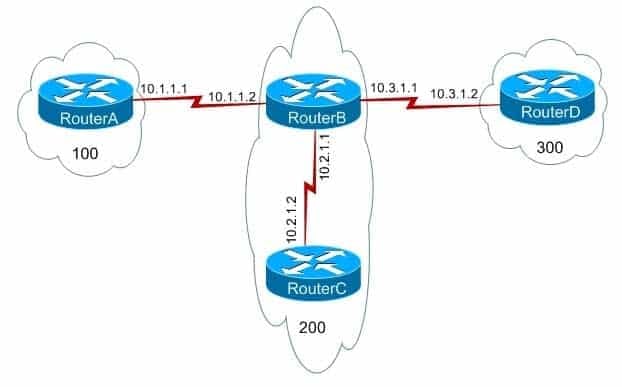
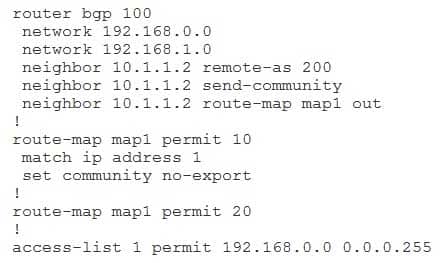
350-401 Part 04 Q11 050 You issue the show running-config command on RouterA and receive the following partial output:
350-401 Part 04 Q11 051 Which of the following statements are true? (Select 2 choices.)
- RouterA will not advertise any routes to RouterB.
- RouterA will advertise only the route to 192.168.1.0/24 to RouterB.
- RouterA will advertise the routes to 192.168.0.0/24 and 192.168.1.0/24 to RouterB.
- RouterB will not advertise any routes to RouterD.
- RouterB will advertise only the route to 192.168.0.0/24 to RouterD.
- RouterB will advertise only the route to 192.168.1.0/24 to RouterD.
- RouterB will advertise the routes to 192.168.0.0/24 and 192.168.1.0/24 to RouterD.
Explanation:
RouterA will advertise the routes to 192.168.0.0/24 and 192.168.1.0/24 to RouterB, and RouterB will advertise only the route to 192.168.1.0/24 to RouterD. RouterB will advertise both routes to RouterC because RouterB and RouterC are in the same autonomous system (AS). The neighbor 10.1.1.2 routemap map1 out command applies route map map1 to modify outgoing routes from RouterA. Because the routemap map1 permit 20 command overrides the implicit deny rule for map1, the route map will not restrict which routes are advertised from RouterA to RouterB. Additionally, map1 is configured to only apply the noexport community attribute to routes that match access list 1. Routes that do not match access list 1 are advertised without the attribute. Because route map map1 is configured to apply the noexport community attribute to only the routes that pass access list 1, the noexport community attribute will affect only the route to 192.168.0.0/24.
The neighbor 10.1.1.2 remoteas 200 command specifies that RouterB, which is in AS 200, is an external Border Gateway Protocol (eBGP) neighbor of RouterA. The neighbor 10.1.1.2 sendcommunity command configures RouterA to send community attribute settings to RouterB. The community attribute is an optional, transitive Border Gateway Protocol (BGP) attribute that is not required to be supported by all BGP implementations. Additionally, BGP implementations that do not support the community attribute are not required to pass the attribute to other routers. By default, Cisco routers do not pass community attributes to BGP neighbors. The community attribute can be modified in a route map by issuing the set community command with one of the following four keywords:-no-advertise -prevents advertisements to any BGP peer
-no-export-prevents advertisements to eBGP peers
-loca-las -prevents advertising outside the AS, or in confederation scenarios, outside the sub-AS internet-advertises the route to any routerThe set community no-export command configures the BGP community attribute to inform neighbor routers to not export the route to eBGP peers. Therefore, RouterB will not advertise the route to 192.168.0.0/24 outside of AS 200. Because RouterD is in AS 300, RouterB will not advertise the 192.168.0.0/24 route to RouterD. RouterB will advertise both routes to RouterC, which is in AS 200. The community attribute does not modify how RouterA advertises the routes; it modifies how neighbor routers advertise the routes received from RouterA.
-
You are configuring 802.1X authentication on the FastEthernet 0/1 port on a switch named SwitchA. You want to ensure that any hosts connected to the port are authenticated by using 802.1X before the hosts can transmit data through the switch.
Which of the following command sequences should you issue on SwitchA? (Select the best answer.)
-
SwitchA#configure terminalSwitchA(config)#aaa newmodel SwitchA(config)#aaa authentication dot1x default group radius SwitchA(config)#dot1x systemauthcontrol SwitchA(config)#interface fastethernet 0/1 SwitchA(configif)#dot1x portcontrol forceauthorized
-
SwitchA#configure terminalSwitchA(config)#aaa newmodel SwitchA(config)#aaa authentication dot1x default group radius SwitchA(config)#dot1x systemauthcontrol SwitchA(config)#interface fastethernet 0/1 SwitchA(configif)#dot1x portcontrol forceunauthorized
-
SwitchA#configure terminalSwitchA(config)#aaa newmodel SwitchA(config)#aaa authentication dot1x default group radius SwitchA(config)#dot1x systemauthcontrol SwitchA(config)#interface fastethernet 0/1 SwitchA(configif)#dot1x portcontrol auto
-
SwitchA#configure terminalSwitchA(config)#aaa newmodel SwitchA(config)#aaa authentication dot1x default group radius SwitchA(config)#dot1x systemauthcontrol SwitchA(config)#interface fastethernet 0/1 SwitchA(configif)#dot1x portcontrol all
Explanation:
You should issue the following command sequence on SwitchA to ensure that hosts connected to the FastEthernet 0/1 port are authenticated by using 802.1X before the hosts are allowed to send traffic through the switch:SwitchA#configure terminal SwitchA(config)#aaa newmodel SwitchA(config)#aaa authentication dot1x default group radius SwitchA(config)#dot1x systemauthcontrol SwitchA(config)#interface fastethernet 0/1 SwitchA(configif)#dot1x portcontrol auto
You can enable 802.1X portbased authentication on Cisco switches to ensure that only authenticated users can send traffic through the switch. Before a user is authenticated, the only traffic allowed through the switch port is Extensible Authentication Protocol over LANs (EAPOL), Spanning Tree Protocol (STP), and Cisco Discovery Protocol (CDP) traffic. This ensures that the host is not able to send traffic through the port until authentication occurs.
To configure 802.1X authentication on a switch, you should first enable Authentication, Authorization, and Accounting (AAA) authentication on the switch by issuing the aaa newmodel command in global configuration mode. A Remote Authentication DialIn User Service (RADIUS) server must exist on the network in order to support AAA authentication. After configuring AAA authentication on the switch, you should issue the aaa authentication dot1x default group radius command to configure the switch to use the RADIUS servers for authentication.
You should enable 802.1X on the switch after you have configured AAA authentication on the switch. You can enable 802.1X by issuing the dot1x system authcontrol command. This command globally enables 802.1X on the switch. You should then configure each interface that will use 802.1X. In this scenario, you want to configure interface FastEthernet 0/1, so you should issue the interface fastethernet 0/1 command to enter interface configuration mode. After entering interface configuration mode, you should issue the dot1x portcontrol {forceauthorized | forceunauthorized | auto} command. The auto keyword enables 802.1X authentication on the port? consequently, the authentication process occurs between the switch and a connected host. If the host is configured with 802.1X authentication, the host will be authenticated and will be able to send traffic through the switch.
If the host is not configured with 802.1X authentication, the authentication process will fail and the host will be unable to send traffic through the port. The force authorized keyword of the dot1x portcontrol command configures the port to authorize any host that connects to the port? no 802.1X authentication process will take place. Any host connected to the port will be able to send traffic through the switch. The force unauthorized keyword configures the port to never allow authentication for a connected host. No authentication will take place, and the host will be unable to send traffic through the port.
The command sequence that contains the dot1x portcontrol all command does not configure 802.1X authentication on the FastEthernet 0/1 port on SwitchA. The dot1x portcontrol command does not include an all parameter. Issuing this command would result in an error being displayed. -
-
You issue the show running-config command on a Cisco 3700 series router named RouterA and receive the following partial output:
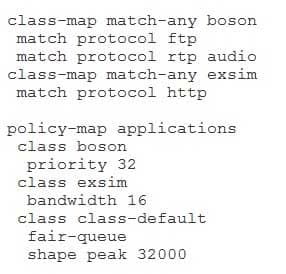
350-401 Part 04 Q13 052 RouterA begins to receive VoIP and FTP packets.
Which of the following statements is correct? (Select the best answer.)- The VoIP packets will be sent before the FTP packets.
- The FTP packets will be sent before the VoIP packets.
- Smaller packets will be sent before larger packets.
- Larger packets will be sent before smaller packets.
- Packets will be sent in the order they are received.
Explanation:
Packets will be sent in the order they are received. In this scenario, class-based weighted fair queuing (CBWFQ) and low latency queuing (LLQ) are used, as indicated by the priority and bandwidth commands. However, only the class-default class can use weighted fair queuing (WFQ); the other classes can use only firstinfirstout (FIFO) queuing within the class. With FIFO queuing, the first packet received is the first packet transmitted.
A traffic class can be prioritized over other traffic classes, but traffic within that class is processed in the order in which the traffic is received, without regard for packet size, protocol, or IP precedence. For example, Voice over IP (VoIP) packets might be transmitted ahead of File Transfer Protocol (FTP) packets, and FTP packets might be transmitted ahead of VoIP packets. Similarly, smaller packets might be transmitted ahead of larger packets, and larger packets might be transmitted ahead of smaller packets. -
You issue the following commands on a router:
line console 0
exec-timeout 1 30How long will the console session to the router remain established without input before the session is automatically disconnected? (Select the best answer.)
- 30 seconds
- 60 seconds
- 90 seconds
- 30 minutes
- 60 minutes
- 90 minutes
Explanation:
The console session to the router will remain established without input for 90 seconds before the session is automatically disconnected. The syntax of the exectimeoutcommand is exectimeoutminutes [seconds]. Therefore, the exectimeout 1 30command configures the router to automatically disconnect idle sessions after one minute and 30 seconds, which is equal to 90 seconds. If the exectimeout command has not been issued, an idle session will remain established for 10 minutes without input. Issuing the no exectimeout command or the exectimeout 0 0 command causes a session to never time out due to inactivity; therefore, the no exectimeout command does not restore the default setting of 10 minutes.
To configure an idle timeout of 30 seconds, you could issue the exectimeout 0 30command. To configure an idle timeout of 60 seconds, you could issue the exectimeout 1 command. To configure an idle timeout of 30 minutes, you could issue the exectimeout 30 command. To configure an idle timeout of 60 minutes, you could issue the exectimeout 60 command. To configure an idle timeout of 90 minutes, you could issue the exectimeout 90 command. -
Two routers have been set up to establish a VPN tunnel. Both routers support GRE and IPSec, and both routers are configured with IPv4 and IPv6 addresses. You issue the tunnel mode auto command on both routers.
Which of the following statements is true? (Select the best answer.)
- GRE will be used for the tunneling protocol, and IPv4 will be used for the transport protocol.
- GRE will be used for the tunneling protocol, and IPv6 will be used for the transport protocol.
- IPSec will be used for the tunneling protocol, and IPv4 will be used for the transport protocol.
- IPSec will be used for the tunneling protocol, and IPv6 will be used for the transport protocol.
- The tunnel will not establish, because one router must be configured statically.
Explanation:
The tunnel will not establish, because one router, the initiator, must be configured statically. The tunnel mode auto command enables the Tunnel Mode Auto Selection feature, which simplifies the configuration of a virtual private network (VPN) tunnel. When Tunnel Mode Auto Selection is configured, the responder will apply the tunneling protocol and transport protocol that is established by the initiator.
To configure a router to use Generic Routing Encapsulation (GRE) for the tunneling protocol and IPv4 for the transport protocol, you should issue the tunnel mode gre ipcommand. To configure a router to use GRE for the tunneling protocol and IPv6 for the transport protocol, you should issue the tunnel mode gre ipv6 command. To configure a router to use IP Security (IPSec) for the tunneling protocol and IPv4 for the transport protocol, you should issue the tunnel mode ipsec ipv4 command. To configure a router to use IPSec for the tunneling protocol and IPv6 for the transport protocol, you should issue the tunnel mode ipsec ipv6 command. -
DRAG DROP
Drag each protocol on the left to the seed metric that is assigned by default when routes are redistributed from another routing protocol into that protocol.
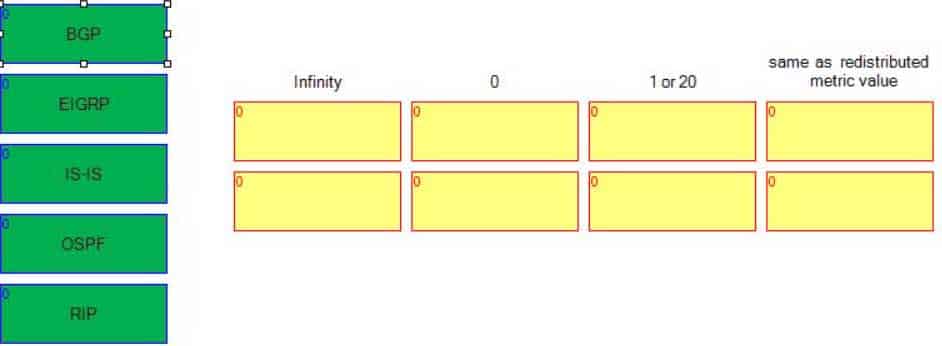
350-401 Part 04 Q16 053 Question 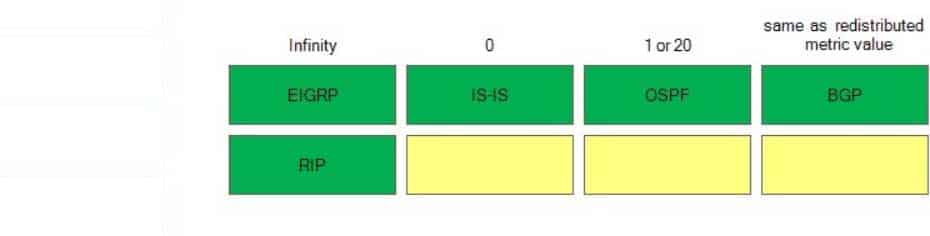
350-401 Part 04 Q16 053 Answer Explanation:
A default seed metric with the value of infinity is assigned to routes that are redistributed into Enhanced Interior Gateway Routing Protocol (EIGRP) from another routing protocol. Routes with an infinite metric are ignored by EIGRP and are not entered into the routing table. Because EIGRP uses a complex metric based on bandwidth, delay, reliability, and load, the metric value used by the redistributing protocol cannot be automatically converted into a metric that EIGRP understands. Therefore, EIGRP requires that the metric be defined for all redistributed routes before those routes are entered into the routing table.
A default seed metric of infinity is also assigned to routes that are redistributed into Routing Information Protocol (RIP) from another routing protocol. Like EIGRP, RIP requires that the metric be defined for all redistributed routes before those routes are entered into the routing table. RIP uses hop count as a metric. Valid hop count values are from 1 through 15; a value of 16 is considered to be infinite. The hop count metric increases by 1 for each router along the path. Cisco recommends that you set a low value for the hop count metric for redistributed routes.
A default seed metric of 0 is assigned to routes that are redistributed into Intermediate SystemtoIntermediate System (ISIS) from another routing protocol. ISIS uses a cost metric assigned to each participating interface. ISIS prefers routes with the lowest cost. Routes redistributed into ISIS are designated as Level 2 routes unless otherwise specified.
A default seed metric of 1 is assigned to Border Gateway Protocol (BGP) routes that are redistributed into Open Shortest Path First (OSPF), and a default seed metric of 20 is assigned to routes that are redistributed into OSPF from another internal gateway protocol (IGP). By default, all routes redistributed into OSPF are designated as Type 2 external (E2) routes. E2 routes have a metric that remains constant throughout the routing domain. Alternatively, routes redistributed into OSPF can be designated as Type 1 external (E1) routes. With E1 routes, the internal cost of the route is added to the initial metric assigned during redistribution.
Routes that are redistributed into BGP are set to the same metric value that is used by the IGP. However, Cisco does not recommend redistributing IGP routes into BGP, because doing so can cause instability. -
You issue the show ip route command on RouterE and receive the following output:

350-401 Part 04 Q17 054 Which of the following statements are accurate about the route to 192.0.3.0/24? (Select 2 choices.)
- The link cost is 66.
- The link cost is 110.
- The AD is 66.
- The AD is 110.
- The bandwidth of the link is 66 Kbps.
- The bandwidth of the link is 110 Kbps.
Explanation:
The administrative distance (AD) of the route in the scenario is 110, and the link cost is 66. In the output of the show ip route command, the first number within the brackets indicates the AD. When multiple routes to a network exist and each route uses a different routing protocol, a router prefers the routing protocol with the lowest AD. The following list contains the most commonly used ADs:
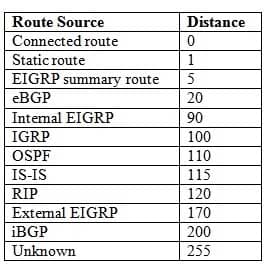
350-401 Part 04 Q17 055 The AD of the route in this scenario is 110, the same as the default distance for an Open Shortest Path First (OSPF) route. AD for a routing protocol can be manually configured by issuing the distance command in router configuration mode. For example, to change the AD of OSPF process ID 1 from 110 to 80, you could issue the following commands:
RouterE(config)#router ospf 1 RouterE(config-router)#distance 80
The second number within the brackets indicates the metric. Because this is an OSPF link, as indicated by the O at the start of the route statement, the second number within the brackets indicates the cost metric. Therefore, the cost of the link in this scenario is 66. When two OSPF paths exist to the same destination, the router will choose the OSPF path with the lowest cost.
OSPF calculates cost based on the bandwidth of an interface: the higher the bandwidth, the lower the cost. To calculate the cost, divide 100,000,000 by the bandwidth in bits per second. Thus a 100Mbps link would have a cost of 1, a 10Mbps link would have a cost of 10, a T1 line would have a cost of 64 (100,000,000 / 1,544,000), and a 64Kbps line would have a cost of 1,562.
As the hops between a router and a destination increase, the cost increases by the bandwidth calculation of the additional links. Therefore, the route in this scenario is the cost of the FastEthernet link between RouterE and RouterC added to the cost of the T1 link between RouterC and RouterB added to the cost of the FastEthernet link between RouterB and the 192.0.3.0/24 network. Therefore, the cost for RouterE to reach the 192.0.3.0/24 network is 1 + 64 + 1, or 66. -
You have issued the following commands on RouterA:
Pseudowire-class boson
ip pmtuRouterA receives a packet that is larger than the path MTU and that has a DF bit set to 0.
Which of the following will RouterA do? (Select 2 choices.)- RouterA will forward the packet.
- RouterA will drop the packet.
- RouterA will return an ICMP unreachable message to the sender.
- RouterA will fragment the packet before L2TP/IP encapsulation occurs.
- RouterA will fragment the packet after L2TP/IP encapsulation has occurred.
Explanation:
When RouterA receives a packet that is larger than the path maximum transmission unit (MTU) and that has a Don’t Fragment (DF) bit set to 0, RouterA will fragment the packet before Layer 2 Tunneling Protocol (L2TP)/IP encapsulation has occurred and then forward the packet. The ip pmtu command enables path MTU discovery (PMTUD) so that fragmentation issues can be avoided on the service provider backbone.
With PMTUD, the DF bit is copied from the IP header to the Layer 2 encapsulation header. If an IP packet is larger than the MTU of any interface on the path, the packet is dropped or fragmented based on the DF bit. If the DF bit is set to 0, the packet is fragmented before encapsulation occurs and is then forwarded. If the DF bit is set to 1, the packet is dropped and the router will return an Internet Control Message Protocol (ICMP) unreachable message to the sender. -
In which of the following locations does BGP PIC store an alternate path? (Select the best answer.)
- only in the RIB
- only in the FIB
- only in CEF
- only in the RIB and the FIB
- in the RIB, in the FIB, and in CEF
Explanation:
Border Gateway Protocol (BGP) Prefix-Independent Convergence (PIC) improves convergence by creating and storing an alternate path in the Routing Information Base (RIB), in the Forwarding Information Base (FIB), and in Cisco Express Forwarding (CEF). As soon as a failure is detected, BGP uses the alternate path.
BGP PIC is capable of improving convergence for both core and edge failures on IPv4, IPv6, and Multiprotocol Label Switching (MPLS) networks. Bidirectional Forwarding Detection (BFD) must be enabled on directly connected neighbors in order to detect link failures. -
Which of the following command sets should you issue on RouterA to set the next hop to 192.168.1.1 only for packets that are destined to the 10.17.88.0/24 network or sent from 172.16.223.82? (Select the best answer.)
-
RouterA(config)#accesslist 101 permit ip host 172.16.223.82 10.17.88.0 0.0.0.255 RouterA(config)#routemap map1 permit 10 RouterA(configroutemap)#match ip address 101 RouterA(configroutemap)#set nexthop 192.168.1.1
-
RouterA(config)#accesslist 101 permit ip 10.17.88.0 0.0.0.255 host 172.16.223.82 RouterA(config)#routemap map1 permit 10 RouterA(configroutemap)#match ip address 101 RouterA(configroutemap)#set nexthop 192.168.1.1
-
RouterA(config)#accesslist 101 permit ip any 10.17.88.0 0.0.0.255 RouterA(config)#accesslist 101 permit ip host 172.16.223.82 any RouterA(config)#routemap map1 permit 10 RouterA(configroutemap)#match ip address 101 RouterA(configroutemap)#set nexthop 192.168.1.1
-
RouterA(config)#accesslist 101 permit ip 10.17.88.0 0.0.0.255 any RouterA(config)#accesslist 101 permit ip any host 172.16.223.82 RouterA(config)#routemap map1 permit 10 RouterA(configroutemap)#match ip address 101 RouterA(configroutemap)#set nexthop 192.168.1.1
Explanation:
You should issue the following command set on RouterA to set the next hop to 192.168.1.1 only for packets that are destined to the 10.17.88.0/24 network or sent from 172.16.223.82:RouterA(config)#accesslist 101 permit ip any 10.17.88.0 0.0.0.255 RouterA(config)#accesslist 101 permit ip host 172.16.223.82 any RouterA(config)#routemap map1 permit 10 RouterA(configroutemap)#match ip address 101 RouterA(configroutemap)#set nexthop 192.168.1.1
Route maps are conditional statements that determine whether a packet is processed normally or modified. A route map can be divided into a series of sequences that are processed in sequential order. If a route matches all the match criteria in a sequence, the route is permitted or denied based on the permit or deny keywords in the routemapcommand and any set conditions are applied. If a route does not match all the matchcriteria in any sequence, the route is discarded.
In this scenario, the routemap map1 permit 10 command creates a route map named map1. The permit10 keywords indicate that any route satisfying all the matchstatements in route map sequence number 10 will be redistributed. In this sequence, there is only one match statement, match ip address 101, which indicates that packets that match the IP addresses in access list 101 will be processed by the route map.
Access list 101 contains two accesslist commands. The accesslist 101 permit ip any 10.17.88.0 0.0.0.255 command indicates that IP packets from anywhere destined to the 10.17.88.0/24 network are processed by the route map. The accesslist 101 permit ip host 172.16.223.82 any command indicates that IP packets from 172.16.223.82 destined for anywhere are also processed by the route map. Packets have to match only one of these accesslist statements in order to be processed by the route map.
The set command is used to define or alter a route attribute for packets that match the route map criteria. In this scenario, the set nexthop 192.168.1.1 command sets the next hop to 192.168.1.1 for the packets that match access list 101.
You should not issue the following command set on RouterA:RouterA(config)#accesslist 101 permit ip 10.17.88.0 0.0.0.255 any RouterA(config)#accesslist 101 permit ip any host 172.16.223.82 RouterA(config)#routemap map1 permit 10 RouterA(configroutemap)#match ip address 101 RouterA(configroutemap)#set nexthop 192.168.1.1
This command set incorrectly specifies the accesslist statements. If you were to issue the accesslist 101 permit ip 10.17.88.0 0.0.0.255 any command and the accesslist 101 permit ip any host 172.16.223.82command, packets that are sent from the 10.17.88.0/24 network or destined to 172.16.223.82 would be modified so that the next hop is 192.168.1.1.
You should not issue the following command set on RouterA:RouterA(config)#accesslist 101 permit ip host 172.16.223.82 10.17.88.0 0.0.0.255 RouterA(config)#routemap map1 permit 10 RouterA(configroutemap)#match ip address 101 RouterA(configroutemap)#set nexthop 192.168.1.1
This command set incorrectly combines the accesslist statements into a single statement. If you were to issue the accesslist 101 permit ip host 172.16.223.82 10.17.88.0 0.0.0.255 command, packets that are sent from 172.16.223.82 and destined for the 10.17.88.0/24 network would be modified so that the next hop is 192.168.1.1. Packets sent from 172.16.223.82 to other destinations would not be modified, nor would packets sent from other hosts destined for the 10.17.88.0/24 network be modified. You should not issue the following command set on RouterA:
RouterA(config)#accesslist 101 permit ip 10.17.88.0 0.0.0.255 host 172.16.223.82 RouterA(config)#routemap map1 permit 10 RouterA(configroutemap)#match ip address 101 RouterA(configroutemap)#set nexthop 192.168.1.1
This command set also incorrectly combines the accesslist statements into a single statement. If you were to issue the accesslist 101 permit ip 10.17.88.0 0.0.0.255 host 172.16.223.82 command, packets that are sent from the 10.17.88.0/24 network and destined for 172.16.223.82 would be modified so that the next hop is 192.168.1.1. Packets sent from the 10.17.88.0/24 network to other destinations would not be modified, nor would packets sent from other networks destined for 172.16.223.82 be modified.
-