350-601 : Implementing and Operating Cisco Data Center Core Technologies (DCCOR) : Part 01
-
Which of the following Cisco APIC configuration methods should not be mixed with other configuration methods?
- NX-OS CLI
- APIC REST API
- APIC GUI in Advanced mode
- APIC GUI in Basic mode
Explanation:
The Cisco Application Policy Infrastructure Controller (APIC) graphical user interface (GUI) in Advanced mode method of configuring a Cisco APIC should not be mixed with other configuration methods. The Cisco APIC is a means of managing the Cisco Application Centric Infrastructure (ACI). By using the APIC, administrators can deploy policies and monitor the health of the infrastructure. The APIC GUI has two modes: Advanced and Basic. Advanced mode is intended for large-scale infrastructures and uses different objects than the other methods.
The Cisco APIC GUI in Basic mode configuration method and the NX-OS command-line interface (CLI) configuration method can be mixed. Configuration changes that are made in the Cisco APIC’s NX-OS CLI are typically reflected in the Cisco APIC GUI in Basic mode. In addition, changes made in the APIC GUI in Basic mode are more accurately reflected in the NX-OS CLI. The APIC GUI in Basic mode is typically used to deploy more common ACI workflows. However, Cisco recommend not using the NX-OS CLI or Cisco APIC GUI in Basic mode prior to using the CISCO APIC GUI in Advanced mode; the former modes create objects that Advanced mode does not use and that cannot be deleted from the configuration.
The APIC representational state transfer (REST) application programming interface (API) is not itself an APIC configuration method. Instead, the APIC REST API is responsible for facilitating communication between the APIC and configuration methods or automation tools. By default, the APIC REST API relies on Hypertext Transfer Protocol Secure (HTTPS) to accept queries and return either JavaScript Object Notation (JSON) or Extensible Markup Language (XML) data. -
You issue the port-channel load-balance dst-port module 4 command on a Cisco Nexus 7000 Series switch running NX-OS 6.2.
How is distribution loaded for port channels on slot 4?
- based on the source port
- based on the source IP address and destination port
- based on the source MAC address and destination port only
- based on the defaults because the command contains invalid syntax
- based on the destination port
Explanation:
Distribution for port channels on slot 4 in this scenario is loaded based on the destination port because the command has been issued with the dst-port keyword and the module 4 keyword. The port-channel load-balance command can be used to modify the load distribution criteria used by EtherChannel. The basic syntax of the port-channel load-balance command is port-channel load-balance method [module slot], where method os one of the following 10 keywords:
– dst-ip
– dst-mac
– dst-port
– scr-dst-ip
– scr-dst-mac
– scr-dst-port
– scr-ip
– scr-mac
– scr-port
– vlan-only
The dst-ip keyword, dst-mac keyword, and dst-port keyword load port channel distribution based on the destination Internet Protocol (IP) address, Media Access Control (MAC) address, and port number, respectively. Similarly, the scr-ip keyword, scr-mac keyword, and scr-port keyword load port channel distribution based on the source IP address, source MAC address, and port number, respectively. The scr-dst-ip keyword, scr-dst-mac keyword, and scr-dst-port keyword load port channel distribution based on the source and destination IP addresses, MAC addresses, and port numbers, respectively. The vlan-only keyword loads distribution on only virtual local area network (VLAN) modules.
The optional module keyword accepts a slot number value. If you configure the port-channel load-balance command with the module keyword, the configuration applies only to the specified slot. Otherwise, the configuration applies to the entire device. By default, on a Cisco Nexus switch, a port channel load balances Layer 2 packets based on the source and destination MAC addresses. Layer 3 packets, on the other hand, are load balanced based on the source and destination IP addresses. You must be operating in the default virtual device context (VDC) on the switch in order to issue the port-channel load-balance command.
The command in this scenario does not contain invalid syntax, because the Nexus switch in this scenario is running NX-OS 6.2. Prior to NX-OS 5.1(3), the port-channel load-balanced command required an ethernet keyword. Therefore, the valid syntax for NX-OS versions older than 5.1(3) is port-channel load-balance ethernet method [module slot]. In NX-OS 5.1(3), Cisco removed that keyword. -
Which of the following best describes an endpoint registry?
- a collection of current endpoints known to the Cisco ACI
- a controller for distributing, tracking, and updating policies
- a collection of rules applied to endpoints, existing or hypothetical
- a collection of endpoints to which policies are distributed
Explanation:
Of the available choices, an endpoint registry can best be described as a collection of endpoints already known to the Cisco Application Centric Infrastructure (ACI). The endpoint registry is the second of two logically coupled components of an endpoint policy: it stores the operational state of each endpoint. In Cisco ACI, the endpoint registry is stored in a distributed database within the ACI fabric. Endpoint policies are used to define how endpoint groups (EPGs) communicate with each other.
A policy repository can be best described as a collection of rules applied to endpoints, existing or hypothetical. A policy repository is the first of two logically coupled components of an endpoint policy; it is typically centralized in the Cisco Application Policy Infrastructure Controller (APIC) or in leaf nodes in the ACI fabric. The policy repository component of an endpoint policy stores rules that can be applied to existing endpoints, planned endpoints, or deleted endpoints.
An EPG is a collection of endpoints with identical requirements; it is a primary element of a tenant. EPGs are logical groupings of endpoints that provide the same application or components of an application. For example, a collection of Hypertext Transfer Protocol Secure (HTTPS) servers could be logically grouped into EPG labeled WEB. EPGs are typically collected within application profiles. EPGs can communicate with other EPGs by using contracts.
The Cisco APIC is a controller for distributing, tracking, and updating policies. In other words, it is a central component of a Cisco ACI fabric that is used for both automation and management. -
Which of the following logically combines ports from multiple switches into a single bundle?
- a VIC
- a VRF instance
- a VDC
- a vPC
Explanation:
A virtual port channel (vPC) logically combines ports from multiple switches into a single port channel bundle. Conventional port channel, which are typically used to create high-bandwidth trunk links between two switches, require that all members of the bundle exist on the same switch. vPCs enable virtual domains that are comprised of multiple physical switches to connect as single entity to a fabric extender, server, or other device.
A virtual device context (VDC) does not logically combine ports from multiple switches into a single bundle. A VDC logically virtualizes a Cisco Nexus 7000 Series switch. A VDC is a single virtual instance of physical switch hardware. By default, the control plane of the Cisco Nexus 7000 Series switch is configured to run a single VDC. It is possible to configure multiple VDCs on the same hardware. A single VDC can contain multiple virtual local area networks (VLANs) and virtual routing and forwarding (VRF) instances.
A VRF instance does not logically combine ports from multiple switches into a single bundle. VRFs enable a router to maintain multiple, simultaneous routing table. Therefore, VRFs can be configured on a single router to serve multiple Layer 3 domain instead of implementing multiple hardware routers.
A virtual interface card (VIC) does not logically combine ports from multiple switches into a single bundle. A VIC is a Cisco device that can be used to create multiple logical network interface cards (NICs) and host bus adapters (HBAs). VICs such as Cisco M81KR send Fibre Channel over Ethernet (FCoE) traffic and normal Ethernet traffic over the same physical medium. -
Which of the following primary elements of a tenant can be of type regular, taboo, or OOB?
- a bridge domain
- a contract
- an EPG
- a filter
Explanation:
A contract is the primary element of a tenant that can be of type regular, taboo, or out-of-band (OOB). Contracts are policy objects that define how endpoint groups (EPGs) communicate with each other. There are three types of contracts that can be applied in a Cisco Application Centric Infrastructure (ACI) fabric:
– Regular – applies filters to matching traffic and typically follows taboo contracts
– Taboo – denies and logs matching traffic
– OOB – applies to OOB traffic from the management tenant
Tenants are containers that can be used to represent organizations, domains, or specific groupings of information. Typically, tenants are configured to ensure that different policy types are isolated from each other, similar to user groups or roles in a role-based access control (RBAC) environment.
A bridge domain is a primary element of a tenant; however, a bridge domain is not of type regular, taboo, or OOB. Bridge domains are logical Layer 2 forwarding configurations within a Cisco ACI fabric that use switched virtual interfaces (SVIs) for gateways and can be configured to span multiple physical devices. In this respect, bridge domains are similar to virtual local area networks (VLANs). However, the purpose of a bridge domain is to define the Media Access Control (MAC) address space and flood domain.
An EPG is a primary element of a tenant: however, an EPG is not of type regular, taboo, or OOB. EPGs are logical groupings of endpoints that provide the same application or components of an application. For example, a collection of Hypertext Transfer Protocol Secure (HTTPS) servers could be logically grouped into an EPG labeled WEB. EPGs are typically collected within application profiles. EPGs can communicate with other EPGs by using contracts.
A filter is a primary element of a tenant; however, a filter is not of type regular, taboo, or OOB. Filters are low-level ACI objects that help define EPG contracts. Filters operate at Layer 2, Layer 3, and Layer 4 of the Open Systems Interconnection (OSI) networking model. -
A user retrieves data in XML format from a Cisco APIC device by submitting a GET request on TCP port 443.
Which of the following technologies are most likely in use? (Choose two.)
- JSON
- REST API
- HTTP
- SOAP API
- HTTPS
Explanation:
Most likely, representational state transfer (REST) Application Programming Interface (API) and Hypertext Transfer Protocol Secure (HTTPS) are in use if a user retrieves data in Extensible Markup Language (XML) format from an application by submitting a GET request on Transmission Control Protocol (TCP) port 443. REST is an API architecture that uses Hypertext Transfer Protocol (HTTP) or HTTPS to enable external resources to access and make use of programming methods that are exposed by the API. In this way, users can interact with specific portions of a data structure from a remote system. By default, HTTPS operates on TCP port 443. A GET request is an HTTP method of retrieving information from an HTTP server.
It is not likely that HTTP is in use in this scenario, because the TCP port on which the GET request is being made is the HTTPS port. If unencrypted HTTP was being used in this scenario, the TCP port on which the request is being made would most likely be TCP port 80. By default, HTTP servers listen for traffic on TCP port 80. On Cisco Application Policy Infrastructure Controller (APIC) devices, HTTPS, not HTTP, is enabled by default. It is possible to enable HTTP on an APIC device. However, HTTP is less secure than HTTPS and is therefore not recommended for that purpose.
It is not likely that Simple Object Access Protocol (SOAP) API is being used in this scenario, because the user is retrieving data from a Cisco APIC device. Cisco APIC does not support SOAP, which is an older API messaging protocol that uses HTTP and XML to enable communication between devices. SOAP APIs are typically more resource-intensive than more modern APIs and, therefore, slower. Open APIs can be used to enable services such as billing automation and centralized management of cloud infrastructure.
JavaScript Object Notation (JSON) is not in use in this scenario. JSON is an output format that is supported by REST API. However, in this scenario, the user has retrieved data from the Cisco APIC device in XML format. -
During the APIC cluster discovery process, LLDP is used for which of the following tasks?
- assignment of VTEP addresses
- discovering MAC addresses
- discovering private IP addresses
- serving the APIC GUI
Explanation:
Link-Layer Discovery Protocol (LLPD) is used for discovering private Internet Protocol (IP) addresses during the Cisco Application Policy Infrastructure Controller (APIC) cluster discovery process. LLDP is used by APIC controllers to discover the private IP addresses and other information assigned to other APIC controllers in the cluster. LLDP is a standard protocol that detects neighboring devices of any type.
LLDP is not used to assign virtual extensible local area network (VXLAN) tunnel endpoints (VTEPs). However, a Cisco Application Centric Infrastructure (ACI) fabric uses LLDP along with Dynamic Host Configuration Protocol (DHCP) to discover switch nodes and to assign IP addresses to VTEPs. LLDP is also used by APIC to detect virtual switches, although it is possible to use Cisco Discovery Protocol (CDP) for that purpose.
LLDP is not used to serve the APIC graphical user interface (GUI). The APIC GUI is constructed in Hypertext Markup Language (HTML) 5. Therefore, Hypertext Transfer Protocol (HTTP), not LLDP, serves the APIC GUI.
LLDP is not used to discover Media Access Control (MAC) addresses. A switched network uses Address Resolution Protocol (ARP) to map MAC addresses to IP addresses. -
In which of the following formats does a REST API produce output? (Choose two.)
- XML
- CSV
- HTML
- JSON
- HTTP
Explanation:
Representational state transfer (REST) produces output in either JavaScript Object Notation (JSON) or Extensible Markup Language (XML) format. REST is an Application Programming Interface (API) architecture that uses Hypertext Transfer Protocol (HTTP) or HTTP Secure (HTTPS) to enable external resources to access and make use of programming methods that are exposed by the API. For example, a web application that retrieves user product reviews from an online marketplace for display on third-party websites might obtain those reviews by using methods provided in an API that is developed and maintained by the marketplace. The JSON or XML output that is returned by the API is parsed by the third-party website for display.
A REST API does not produce output in Hypertext Markup Language (HTML) format. Although HTML is similar to XML, which uses tags like HTML does, XLM requires a strict syntax and is typically used to structure data, not format and render data in a web browser. HTML, on the other hand, is designed to inform a web browser about how given information should be displayed.
A REST API does not produce output in HTTP format. HTTP is the Open Systems Interconnection (OSI) networking model Application layer protocol that is used to transfer information from a web server to a web browser. A REST API uses HTTP to transmit requests for information to a web server, which is not the same as producing the formatted output that is returned from the server.
A REST API does not produce output in comma separated values (CSV) format. The CSV format is a common tabular format that is supported by spreadsheet applications and other business reporting applications. CSV files are plain-text files that segregate the fields of a table by using a combination of quotation marks, symbolic delimiters such as a comma or a semicolon, and line breaks. -
Which of the following is a cloud computing deployment model that shares infrastructure with multiple organizations that have common needs?
- hybrid
- community
- private
- public
Explanation:
Community is a cloud computing deployment model that shares infrastructure with multiple organizations that have common needs. Hybrid can use a mixture of public and private infrastructure recourses. However, community clouds share the public infrastructure resources between multiple organizations. Typically, the organizations involved in community cloud computing have common needs that the community cloud can provide.
There are four different cloud computing deployment models: private cloud, public cloud, hybrid cloud, and community cloud. Cloud computing is a term used to describe computing services that are offered for consumption in a way that demands fewer infrastructure expenses from the organization. Cloud computing deployment models describe how the cloud services are delivered to the customer. Cloud computing service models, on the other hand, describe the cloud services that the customer has purchased, such as infrastructure, platforms, or software.
Hybrid is a cloud computing deployment model that uses a mixture of private and public infrastructure resources to form a single organization’s cloud. Typically, the hybrid model relies on its private cloud component for some workload but uses the public cloud component to extend the private cloud services on-demand.
Private is a cloud computing deployment model that is constructed for only the organization that uses its services. Private cloud computing is typically established by using either a third-party service or internal servers, not both. The use of a private cloud enables an administrator to ensure that the cloud’s resources are available only to an authorized few users.
Public is a cloud computing deployment model that is owned and operated by a service provider. Public cloud computing does not use a mixture of private and public infrastructure resources. Public clouds typically allow the general public to access storage and applications served from the cloud. For example, a Gmail account is a service that is provided from a public cloud. Other public cloud computing providers include Amazon and Rackspace. -
Which of the following type of communication is not governed by contracts in an ACI fabric?
- between members of the same EPG
- between an EPG and an external network
- between EPGs
- between EPGs and in-band management EPG
Explanation:
Communication between members of the same endpoint group (EPG) is not governed by contracts in a Cisco Application Centric Infrastructure (ACI) fabric. Instead, members of an EPG communicate with each other by using their own network configurations, rules, and filters.
EPGs in a Cisco ACI fabric communicate with each other according to contract rules. In addition, contract rules determine how an EPG communicates with an in-band management EPG and with an external network. EPGs are logical groupings of endpoints that provide the same application or components of an application. For example, a collection of Hypertext Transfer Protocol Secure (HTTPS) servers could be logically grouped into an EPG labeled WEB. Contracts are policy objects that define how EPGs. There are three types of contracts that can be applied in an ACI fabric:
– Regular – applies filters to matching traffic and typically follows taboo contracts
– Taboo – denies and logs matching traffic
– Out-of-Band (OOB – applies to OOB traffic from the management tenant
With the exception of some types of traffic – such as network configuration traffic, routing protocol traffic, and multicast traffic – EGPs require contracts in order to communicate with each other.
Contracts consist of subjects, filters, actions, and optionally, labels, but not objects. Subjects are group of filters that are specific to a given application. Filters classify traffic by matching Open Systems Interconnection (OSI) network model Layer 2 or Layer 4 characteristics. Actions are the action that is performed on traffic that matches the filters. Labels can be created to group EPGs or subjects. These groupings add granularity to the enforcement of a policy. -
You manage the Cisco ACI fabric in the following exhibit:

350-601 Part 01 Q11 001 S2 has just been discovered by APIC1. Only one leaf switch has been discovered and registered with APIC1 so far. No other spine switches have been discovered.
Which of the following switches will most likely be discovered next?- L5
- S1
- L1, L2, and L3
- L4 and L6
- L1, L2, L3, L4, and L6
Explanation:
Most likely, S1 will be discovered next because of the way that Cisco Application Policy Infrastructure Controllers (APICs) discover and register leaf and spine switches in a Cisco Application Centric Infrastructure (ACI) fabric. In this scenario, APIC1 Has just discovered S2. This means that L5, the leaf switch to which APIC1 is directly connected, has already been discovered as well. L5 is directly connected to both spine switches in the topology. Because S2 was just discovered and no other spine switches have yet been discovered, it is likely that APIC1 will next discover S1.
APIC1 will not discover L5 next, because APIC1 has already discovered and registered L5. When a Cisco APIC begins the switch discovery process, it first detects only the leaf switch to which it is connected. After that leaf switch is registered, the APIC discovers each of the spine switches to which the leaf switch is connected. Spine switches do not automatically register with the APIC. When a spine switch is registered with the APIC, the APIC will discover all the leaf switches that are connected to that spine switch. Therefore, APIC1 will not discover all the leaf switches in this scenario until each spine switch is registered with the APIC.
APIC1 will not discover L1, L2, L3, L4, or L6 next. All these switches are leaf switches that are directly connected to both S1 and S2. Although APIC1 in this scenario will eventually discover L1, L2, and L3, it will first discover all the spine switches to which L5 is directly connected. -
You want to implement GSLB.
Which of the following are you most likely to deploy?
- a spine switch
- a Cisco Nexus 1000v virtual switch
- a leaf switch
- a GSS device
- an APIC server
Explanation:
Most likely, you will deploy a Cisco Global Site Selector (GSS) device if you want to implement global server load balancing (GSLB). A Cisco GSLB solution is designed to optimize Domain Name System (DNS) infrastructure, thereby ensuring business continuity in the event of disaster. When DNS services are migrated to GSS, disaster recovery is enhanced by the global load balancing of server load balancers (SLBs) across data centers in disparate geographic locations.
You will not deploy a spine switch or a leaf switch to implement GSLB. Spine switches are the Cisco FabricPath component that form the backbone of Cisco FabricPath’s switching fabric. Typically, leaf switches are connected to every spine switch along the backbone so that provides access layer connectivity. End hosts and classic Ethernet (CE) networks are typically directly connected to leaf switches by using edge ports. Leaf switches connect to spine switches by using core ports.
You will not deploy an Application Policy Infrastructure Controller (APIC) server to implement GSLB. The Cisco APIC is a means of managing the Cisco Application Centric Infrastructure (ACI). A Cisco ACI architecture requires both the APIC and the spine switches and leaf switches of FabricPath to complete the architecture. The APIC communicates with the spine and leaf nodes and provides policy distribution as well as centralized management.
You will not deploy a Cisco Nexus 1000v virtual switch to implement GSLB. The Cisco Nexus 1000v is a virtual switch that is designed to provide a switching environment for virtual machines (VMs) and cloud networks. Typically, a Cisco Nexus 1000v is embedded in the kernel of VMware vSphere ESX. -
Which of the following is true of Cisco FabricPath edge ports?
- They allow only FabricPath VLAN traffic.
- The can be configured only as trunk ports.
- The encapsulate Ethernet frames in a FabricPath header.
- They are classic Ethernet ports.
Explanation:
Cisco FabricPath edge ports are classic Ethernet ports. Cisco FabricPath uses Open Systems Interconnection (OSI) networking model Layer 3 routing combined with Layer 2 switching to construct a unified and scalable Layer 2 fabric. An edge port is a Cisco FabricPath component port that does not operate as part of the FabricPath network.
Cisco FabricPath edge ports can be configured either as Institute of Electrical and Electronics Engineers (IEEE) 802.1Q trunk ports or as access ports. Trunk ports enable switches to transmit and receive data on multiple virtual local area networks (VLANs) over the same link. In a Cisco FabricPath network, core ports can be configured only as trunk ports. Core ports are ports that operate as part of the FabricPath network.
Cisco FabricPath core ports, not edge ports, allow only FabricPath VLAN traffic. Edge ports or normal trunk ports can carry classic Ethernet VLAN traffic. In addition, core ports encapsulate Ethernet frames in a FabricPath header because core ports operate as part of the FabricPath network. Edge ports carry classic Ethernet traffic and do not need to encapsulate that traffic in FabricPath headers. -
Which of the following is best described as the atomic units of work in Cisco UCS Director Orchestrator?
- rollbacks
- approvals
- service requests
- workflows
- tasks
Explanation:
Of the available choices, tasks are best described as the atomic units of work in Cisco Unified Computing System (UCS) Director Orchestrator. Cisco UCS Director uses hardware abstraction to convent hardware and software into programmable actions that can then be combined into an automated custom workflow. Cisco UCS Director Orchestrator is the Cisco UCS Director engine that enables this automation. A task is a single action and is therefore the smallest unit of work.
A workflow is a series of tasks and is therefore not the atomic unit of work in Cisco UCS Director Orchestrator. A workflow is a container that defines the order in which tasks should be performed. However, it is possible for a workflow to contain a single task. Workflows can be created and deployed from workflow templates.
Service requests are created when a workflow is executed and are therefore not the atomic unit of work in Cisco UCS Director Orchestrator. Service requests are Cisco UCS Director processes that can be exist in one of several states. For example, a service request that has not run yet might exist in a scheduled state. A service request that has been successfully executed exists in a completed state. A service request that was attempted but not successfully executed might exist in a failed state.
Approvals are points in a workflow that require user intervention. For example, a service request might exist in a blocked state if the request cannot complete until an administrator approves the service request. Approvals enable administrators to provide input values that can affect the product of a given workflow.
Rollbacks can be used to undo the results of workflows. For example, a workflow that creates unintended objects or components in a system can be rolled back so that those objects or components are removed. Cisco UCS Director Orchestrator rollbacks are different from relational database rollbacks in that they are not transactional. Instead, tasks in the workflow are executed in reserve order when a workflow is rolled back. -
Which OTV failure isolation feature ensures that BPDUs are not forwarded across the overlay?
- ARP optimization
- unknown unicast handling
- STP isolation
- broadcast policy control
Explanation:
Overlay Transport Virtualization (OTV)’s Spanning Tree Protocol (STP) isolation feature ensures that bridge protocol data units (BPDUs) are not forwarded across the overlay. This feature is enabled by default. Because BPDUs are suppressed, each data center’s STP domain remains independent of other data centers connected to the overlay. This prevents data centers from accidentally creating Open System Interconnection (OSI) networking model Layer 2 loops over OTV.
OTV is a technology that extends Layer 2 networks across data centers. Similar to Ethernet over Multiprotocol Label Switching (EoMPLS), virtual private LAN services (VPLS), and dark fiber, OTV is intended to enable the extension of Layer 2applications across large geographic distances. It is typically deployed on data center edge devices. OTV used Media Access Control (MAC) address routing to ensure that Layer 2 reachability information can be transmitted between data centers. Unlike other Layer 2 extension technologies, OTV’s MAC address routing takes place at the control plane level. Other technologies rely on data plane forwarding and flooding,
OTV’s unknown unicast handling feature maps a MAC address from a remote data center to that data center’s join interface Internet Protocol (IP) address. The join interface is the Layer 3 interface on which OTV is deployed and that is capable of discovering other OTV-enabled data centers. OTV’s unicast traffic handling feature advertises MAC addresses between data centers. Because of this advertisement and mapping process, OTV is capable of suppressing the transmission of unknown unicast traffic across data centers.
Broadcast policy control and Address Resolution Protocol (ARP) optimization are OTV features that reduce traffic between OTV-connected data centers. Each of these features reduces the amount of broadcast traffic that is flooded between data centers. -
Which of the following is true about the ports in slot 1 on a Cisco Nexus 5548UP?
- Only 16 of them are unified ports.
- The first 16 are FC ports.
- All 32 ports are unified ports
- The first 16 are Ethernet ports.
Explanation:
All 32 ports in slot 1 on a Cisco Nexus 5548UP switch are unified ports. A unified port is a physical port on a Cisco switch that can be configured as either an Ethernet port or a Fibre Channel (FC) port. Typically, a Nexus switch that contains unified ports requires that all Ethernet ports be configured from the first port in the slot forward and that all FC ports be configured from the last port in the slot backward. In other words, a slot that contains 32 unified ports, two acting as Ethernet and two acting as FC, will typically use ports 1 and 2 for Ethernet links and ports 32 and 31 for FC links.
The last 16 ports in slot 1 of a Cisco Nexus 5596T are FC ports, not the first 16 ports in a Cisco Nexus 5548UP. However, the last 16 ports in a Nexus 5596T can be configured as unified ports. The first 32 ports in the Cisco Nexus 5596T are all 10-gigabit per second (Gbps) Ethernet ports; they cannot be configured as unified ports. -
Which of the following are most likely to operate in the data plane of a Nexus switch? (Choose two.)
- BGP
- EIGRP
- OSPF
- store-and-forward switching
- SNMP
- cut-through switching
Explanation:
Of the available choices, cut-through switching and store-and-forward switching are most likely to operate in the data plane of a Nexus switch. A Nexus switch consists of three operational planes: the data plane, which is also known as the forwarding plane, the control plane, and the management plane. Of the three, the data plane is where traffic forwarding occurs. Cut-through switching allows a switch to begin forwarding a frame before the frame has been received in its entirety. Store-and-forward switching receives an entire frame and stores it in memory before forwarding the frame to its destination.
Enhanced Interior Gateway Routing Protocol (EIGRP), Open Shortest Path First (OSPF), and Border Gateway Protocol (BGP) all operate in the control plane of a Nexus switch. The control plane is responsible for gathering and calculating the information required to make the decisions that the data plane needs for forwarding. Routing protocols operate in the control plane because they enable the collection and transfer of routing information between neighbors. This information is used to construct routing tables that he data plane can then use for forwarding.
Simple Network Management Protocol (SNMP) is an Internet Protocol (IP) network management protocol that operates in the management plane of a Nexus switch. The management plane is responsible for monitoring and configuration of the control plane. Therefore, network administrators typically interact directly with protocols running in the management plane. -
DRAG DROP
Drag the Cisco UCS Manager user role on the left to the best description on the right. All user roles will be used. Each role can be used only once.
350-601 Part 01 Q18 002 Question 
350-601 Part 01 Q18 002 Answer Explanation:
Cisco Unified Computing System (UCS) is installed with several default user roles for its role-based access control (RBAC) system. User accounts in Cisco UCS Manager are assigned one of the default roles or a custom role that is defined by an administrator. These roles define the access privileges for each account. Cisco UCS Manager is web-based software that can be used to manage a single UCS domain.
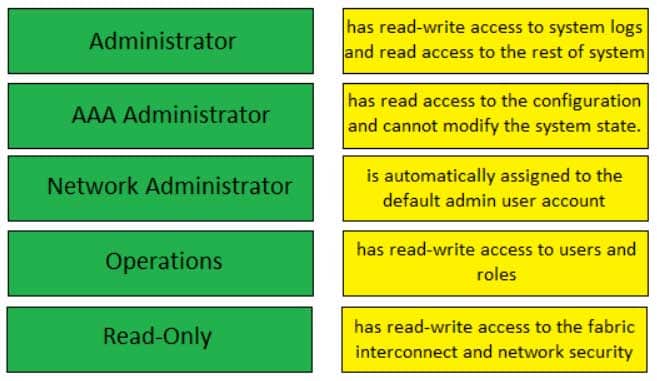
The AAA Administrator user role has read-write access to users, roles, and the system’s authentication, authorization, and accounting (AAA) configuration. AAA Administrators can read the rest of the system buy cannot write to it.
The Administrator user role is automatically assigned to the default admin user account. Administrators have read-write access to the entire system. Although the Administrator role can be assigned to other user accounts, this role cannot be removed from the default admin account.
The Network Administrator user role has read-write access to the fabric interconnect and network security. However, this role has only read access to the rest of the system.
The Operations user role has read-write access to system logs and read access to the rest of the system. An Operations user can read and write to Syslog servers and faults.
The Read-Only user role has read access to the configuration. In addition, the Read-Only user role cannot modify the system state.
There are five other default Cisco UCS Manager user roles:
– Facility Manager – has read-write access to power management
– Server Equipment Administrator – has read-write access to physical server operations
– Server Profile Administrator – has read-write access to logical server operations
– Server Security Administrator – has read-write access to security operations
– Storage Administrator – has read-write access to storage operations -
You manage the Cisco FabricPath network in the following exhibit:
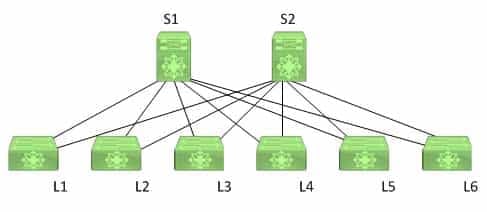
350-601 Part 01 Q19 003 A host that is directly connected to L2 sends a unicast packet to a known host that is also directly connected to L2.
Which of the following is true?- L2 receives an unknown unicast packet from the sending host.
- L2 will forward the packet to the multidestination tree.
- L2 will not perform a lookup on the destination MAC address.
- L2 will not forward the packet to a spine switch.
Explanation:
L2 will not forward the packet to a spine switch. In this scenario, it is not necessary for L2 to forward the packet to a spine switch, because both the sending host and the receiving host are directly connected to L2. If the destination host in this scenario were connected to a different leaf switch, the known unicast packet would be forwarded from L2 to one of the spine switches and then on to the switch on which the destination host is located.
When L2 receives a known unicast packet, which is unicast packet with a destination address that the switch knows how to reach, that is intended for a host on a different switch the following occurs:
– L2 performs a Media Access Control (MAC) address lookup and located the destination switch.
– L2 looks up the switch ID of the destination switch and chooses a FabricPath core port on which to send the packet.
– L2 encapsulated the packet in a FabricPath header, including its own switch ID in the outer source address (OSA) field and the destination switch’s ID in the outer destination address (ODA) field.
– L2 sends the packet.
By contrast, when L2 receives an unknown unicast packet, the following occurs:
– L2 updates the classic Ethernet MAC table with the sending host’s source Mac address.
– L2 performs a lookup for the destination Mac address of the destination host.
– L2 encapsulates the classic Ethernet frame in a FabricPath header and floods it to the multidestination forwarding tree with L2’s switch ID as the OSA.
Because of the spine-and-leaf configuration of the topology, L2 would flood an unknown unicast packet to its directly connected spine switches, S1 and S2, which would then flood the packet to the other leaf switches. Each leaf switch would then perform a MAC address lookup. The switch that has the destination host in its MAC address table adds the sending host to its own MAC address table. At this point, the packet is sent to the destination host. -
Which of the following OTV technologies is a logical interface and cannot be a physical interface?
- OTV join interface
- OTV overlay interface
- OTV internal interface
- OTV edge device
Explanation:
An Overlay Transport Virtualization (OTV) overlay interface is a logical interface and cannot be a physical interface. OTV is a means of simplifying the deployment of data center interconnect (DCI), enabling the extension of Layer 2 applications between data centers. An OTV overlay interface is a logical interface that is defined by the user. The OTV overlay interface receives and forwards any Open Systems Interconnection (OSI) networking model Layer 2 frames that must be transmitted to the remote site.
An OTV edge device is typically a virtual device context (VDC) running on A Cisco Nexus switch, such as a Nexus 7000 Series switch. The edge device is responsible for receiving Layer 2 traffic for virtual local area networks (VLANs) that are extended. Ethernet frame traffic is encapsulated into Internet Protocol (IP) packets are transmitted to the remote network.
An OTV join interface is an OTV technology that is a physical or logical Layer 3 interface. An OTV join interface is used to connect an overlay network to remote overlay edge devices. An OTV join interface can be a physical interface, subinterface, or logical interface such as a port channel.
An OTV internal interface is a Layer 2 interface. The OTV internal interface is an interface on the OTV edge device that connects to the VLANs that are being extended. Typically, the OTV internal interface operates similarly to any other Layer 2 switch trunk port or access port and does not require configuration specific to OTV.