350-601 : Implementing and Operating Cisco Data Center Core Technologies (DCCOR) : Part 06
-
Examine the Cisco UCS Director Workflow Designer workflow in the following exhibit:
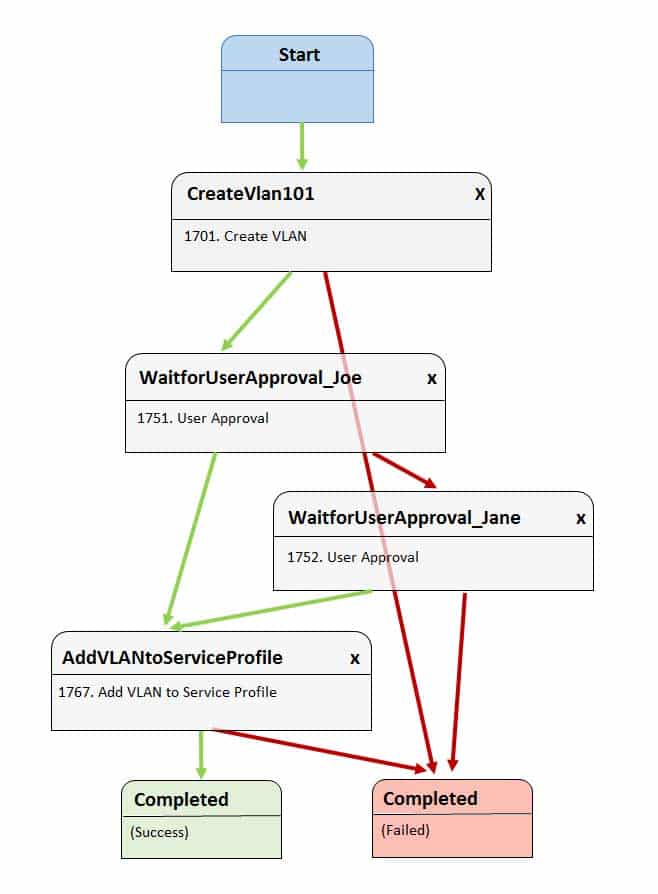
350-601 Part 06 Q01 009 How many users must approve before VLAN 101 can be added to the service profile?
- one
- three
- two
- none
Explanation:
In this scenario, only one user must approve before virtual local area network (VLAN) 101 can be added to the service profile. The Cisco Unified Computing System (UCS) Director Workflow Designer workflow in this scenario creates VLAN 101 after it starts. Before the next task is executed, the workflow requires the approval of a user named Joe. If Joe approves, the workflow attempts to add VLAN 101 to the service profile. If Joe does not approve, Jane is given an opportunity to approve. If Jane approves, VLAN 101 can be added to the service profile.
Cisco UCS Director Workflow Designer is a graphical user interface (GUI) that enables users to create automated workflows in a drag-and-drop fashion. Each task in a workflow is equipped with an On Success button and an On Failure button. Each button provides a drop-down list of other tasks in the workflow. In this way, the user can select which tasks are executed next if a task succeeds and which tasks are executed next if a task fails. Green arrows in Workflow Designer represent the On Success path. Red arrows represent the On Failure path.
At least one user will need to approve in this scenario for VLAN 101 to be added to the service profile. The On Failure path of the WaitforUserApproval_Joe task is tied to the WaitforUserApproval_Jane task. The On Failure path of the WaitforUserApproval_Jane task is tied to the Completed (Failure) task. Therefore, there is no chance of successfully adding VLAN 101 to the service profile without user approval.
No more than one user will need to approve in this scenario for VLAN 101 to be added to the service profile. The On Success path of the WaitforUserApproval_Joe task is tied to the AddVLANtoServiceProfile task. Therefore, the workflow attempts to add VLAN 101 to the service profile if Joe approves. Similarly, the On Success path of the WaitforUserApproval_Jane task is tied to the AddVLANtoServiceProfile task. Therefore, the workflow attempts to add VLAN 101 to the service profile if Joe rejects and Jane approves.
Only two user approval tasks are present in this workflow: WaitforUserApproval_Joe and WaitforUserApproval_Jane. Therefore, it is not possible to require more than two users to approve or reject the addition of VLAN 101 to the service profile. -
Which of the following examples best describes the PaaS service model?
- A company licenses an office suite, including email service, that is delivered to the end user through a web browser.
- A company obtains a subscription to use a service provider’s infrastructure, programming tools, and programming languages to develop and serve cloud-based applications.
- A company moves all company-wide policy documents to an Internet-based virtual file system hosted by a service provider.
- A company hires a service provider to deliver cloud-based processing and storage that will house multiple virtual hosts configured in a variety of ways.
Explanation:
A company that uses a service provider’s infrastructure, programming tools, and programming languages to develop and serve cloud-based applications is an example of the Platform as a Service (PaaS) service model. The National Institute of Standards and Technology (NIST) defines three service models in its definition of cloud computing: Software as a Service (SaaS), Infrastructure as a Service (IaaS), and PaaS. Cloud computing offers several benefits over traditional physical infrastructure and software licensing, including a reduction in downtime and administrative overhead.
The SaaS service model enables its consumer to access applications running in the cloud infrastructure but does not enable the consumer to manage the cloud infrastructure or the configuration of the provided applications. A company that licenses a service provider’s office suite and email service that is delivered to end users through a web browser is using SaaS. SaaS providers use an Internet-enabled licensing function, a streaming service, or a web application to provide end users with software that they might otherwise install and activate locally. Web-based email clients, such as Gmail and Outlook.com, are examples of SaaS.
The PaaS service model provides its consumer with a bit more freedom than the SaaS model by enabling the consumer to install and possibly configure provider-supported applications in the cloud infrastructure. A company that uses a service provider’s infrastructure, programming tools, and programming languages to develop and serve cloud-based applications is using PaaS. PaaS enables a consumer to use the service provider’s development tools or Application Programming Interface (API) to develop and deploy specific cloud-based applications or services. Another example of PaaS might be using a third party’s MySQL database and Apache services to build a cloud-based customer relationship management (CRM) platform.
The IaaS service model provides the greatest degree of freedom by enabling its consumer to provision processing, memory, storage, and network resources within the cloud infrastructure. The IaaS service model also enables its consumer to install applications, including operating systems (OSs) and custom applications. However, with IaaS, the cloud infrastructure remains in control of the service provider. A company that hires a service provider to deliver cloud-based processing and storage that will house multiple physical or virtual hosts configured in a variety of ways is using IaaS. For example, a company that wanted to establish a web server farm by configuring multiple Linux Apache MySQL PHP (LAMP) servers could save hardware costs by virtualizing the farm and using a provider’s cloud service to deliver the physical infrastructure and bandwidth for the virtual farm. Control over the OS, software, and server configuration would remain the responsibility of the organization, whereas the physical infrastructure and bandwidth would be the responsibility of the service provider.
A company that moves all company-wide policy documents to an Internet-based virtual file system hosted by a third party is using cloud storage. Cloud storage is a term used to describe the use of a service provider’s virtual file system as a document or file repository. Cloud storage enables an organization to conserve storage space on a local network. However, cloud storage is also a security risk in that the organization might not have ultimate control over who can access the files. -
Which of the following best describes a port that operates as part of a FabricPath network?
- a trunk port
- an edge port
- an access port
- a core port
Explanation:
Of the available choices, a core port is a port that operates as part of a FabricPath network. Cisco FabricPath uses Open Systems Interconnection (OSI) networking model Layer 3 routing combined with Layer 2 switching to construct a unified and scalable Layer 2 fabric. Although Cisco FabricPath defines two types of ports, only core ports are considered to be part of the FabricPath network. Core ports forward Ethernet frames encapsulated within a FabricPath header. In addition, core ports are always trunk ports that include an Institute of Electrical and Electronics Engineers (IEEE) 802.1Q virtual local area network (VLAN) tag. Only FabricPath VLANs are allowed on core ports.
An edge port is a Cisco FabricPath component port that does not operate as part of the FabricPath network. Instead, edge ports send only normal Ethernet frames as part of a classic Layer 2 switched network. An edge port can be configured as either an access port or an IEEE 802.1Q trunk port.
Although all core ports are trunk ports, not all trunk ports are core ports. Therefore, of the available choices, the term trunk port does not best describe a port that operates as part of a FabricPath network. Trunk ports enable switches to transmit and receive data on multiple VLANs over the same link.
An access port does not best describe a port that operates as part of a FabricPath network. Core ports cannot be access ports. An access port is a switch port that typically connects to an end device, such as a server or workstation. Access ports transmit and receive data on a single VLAN. -
DRAG DROP
Drag the cloud computing deployment model on the left to its description on the right. All models will be used. Models will be used. Models can be used only once.

350-601 Part 06 Q04 010 Question 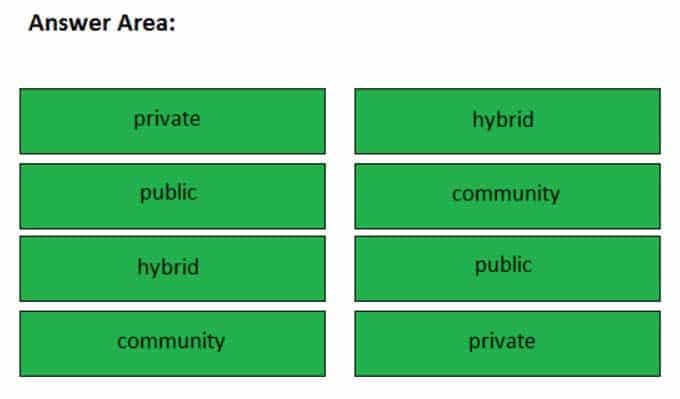
350-601 Part 06 Q04 010 Answer Explanation:
There are four different cloud computing deployment models: private cloud, public cloud, hybrid cloud, and community cloud. Cloud computing is a term used to describe computing services that are offered for consumption in a way that demands fewer infrastructure expenses from the organization. Cloud computing deployment models describe how the Cloud services are delivered to the customer. Cloud computing service models, on the other hand, describe the cloud services that the customer has purchased, such as infrastructure, platforms, or software.
Hybrid is a cloud computing deployment model that uses a mixture of private and public infrastructure resources to form a single organization’s cloud. Typically, the hybrid model relies on its private cloud component for some workload but uses the public cloud component to extend the private cloud services on demand.
Community is a cloud computing deployment model that can use a mixture of public and private infrastructure resources. However, community clouds share the public infrastructure resources between multiple organizations. Typically, the organizations involved in community cloud computing have common needs that the community cloud can provide.
Private is a cloud computing deployment model that is constructed for only the organization that uses its services. Private cloud computing is typically established by using either a third-party service or internal servers, not both. The use of a private cloud enables an administrator to ensure that the cloud’s resources are available only to an authorized few users.
Public is a cloud computing deployment model that is owned and operated by a service provider. Public cloud computing does not use a mixture of private and public infrastructure resources. Public clouds typically allow the general public to access storage and applications served from the cloud. For example, a Gmail account is a service that is provided from a public cloud. Other public cloud computing providers include Amazon and Rackspace. -
Which of the following statements about VE ports is true?
- They connect to peripheral devices.
- They enable multihop FCoE topologies.
- They cannot be configured with multiple vSANs on a single port.
- They are enabled in access mode by default.
Explanation:
Because virtual edge (VE) ports connect Fibre Channel over Ethernet (FCoE) inter-switch links (ISLs), VE ports enable multihop FCoE topologies. An FCoE hop is a connection from one domain ID to another domain ID. Therefore, a multihop FCoE switch is aware of multiple domains and can track and forward between them. In other words, VE ports connect to other VE ports.
VE ports do not connect to peripheral devices. Virtual F (VF) ports, on the other hand, are FCoE ports that typically connect to virtual N (VN) ports. VN ports are ports in peripheral devices, such as end hosts or disks.
VE ports are enabled in trunk mode by default. In addition, VE ports can be configured with multiple virtual storage area networks (vSANs) on a single port. In order to configure multiple vSANs on a single VE port, you must configure each corresponding FCoE virtual local area network (VLAN) on the Ethernet interface to which the VE port is bound. -
How many VRF instances are configured on a Nexus 7000 by default?
- none
- three
- two
- one
Explanation:
There are two virtual routing and forwarding (VRF) instances configured on a Nexus 7000 by default: the management VRF and the default VRF. The management VRF is used only for management, includes only the mgmt 0 interface, and uses only static routing.
VRFs are used to logically separate Open Systems Interconnection (OSI) networking model Layer 3 networks. Therefore, it is possible to have overlapping Internet Protocol version 4 (IPv4) or Internet Protocol version 6 (IPv6) addresses in environments that contain multiple tenants. However, an interface that has been assigned to a given VRF cannot be simultaneously assigned to another VRF. The address space, routing process, and forwarding table that are used within a VRF are local to that VRF.
The default VRF, on the other hand, includes all Layer 3 interfaces until you assign those interfaces to another VRF. Similarly, the default VRF runs any routing protocols that are configured unless those routing protocols are assigned to another VRF. All show and exec commands that are issued in the default VRF apply to the default routing context. Unless an administrator configures other VRFs on a Nexus 7000, any forwarding configurations that are made by the administrator will operate in the default VRF. -
Which of the following Cisco UCS Manager identity pools contains both types of FC1 identities?
- the MAC pool
- the IP pool
- the WWNN pool
- the WWxN pool
- the WWPN pool
Explanation:
Of the available choices, only the Cisco Unified Computing System (UCS) WWxN identity pool contains both Fibre Channel-Layer 2 (FC1) identities. This is because WWxN identity pools are a combination of World Wide Name (WWN) types: the World Wide Port Name (WWPN) and the World Wide Node Name (WWNN). Unlike other networking technologies, Fibre Channel (FC) does not make use of the Open Systems Interconnection (OSI) network model. Instead, FC uses the FC-Layers model, which is broken out in the following fashion:
– FC4: Protocol mapping layer
– FC3: Common services layer
– FC2: Network layer
– FC1: Data link layer
– FC0: Physical layer
FC0, FC1, and FC2 have similar names and functions to their OSI model equivalents, which are Layer 1, Layer 2, and Layer 3, respectively. FC3 is equivalent to the OSI model’s Transport layer, or Layer 4. FC4, on the other hand, is similar in function to a combination of all three top layers of the OSI model, which are the Session layer (Layer 5), the Presentation layer (Layer 6), and the Application layer (Layer 7).
WWNNs are 64-bit globally unique identifiers that specify a given FC node. These identifiers are typically used to assign FC1 addresses in storage area network (SAN) routing. Similar to the WWNN identity pool, the WWPN identity pool contains globally unique 64-bit identifiers that are used to assign FC1 addresses. However, WWPNs represent a specific FC port, not an entire node.
Media Access Control (MAC) identity pools contain MAC addresses, which are OSI Layer 2 48-bit hexadecimal addresses that are typically burned into a network interface card (NIC). The first 24 bits of a MAC address represent the Organizationally Unique Identifier (OUI), which is a value that is assigned by the Institute of Electrical and Electronics Engineers (IEEE). The OUI identifies the NIC’s manufacturer. The last 24 bits of a MAC address uniquely identify a specific NIC constructed by the manufacturer. This value is almost always an identifier that the manufacturer has never before used in combination with the OUI.
Internet Protocol (IP) identity pools contain IP addresses, which are 32-bit decimal addresses that are assigned to OSI Layer 3 interfaces. In a Cisco UCS domain, IP pools are typically used to assign one or more management IP addresses to each server’s Cisco Integrated Management Controller (IMC). -
Which of the following statements about contracts in a Cisco ACI fabric is true?
- Multicast traffic is not permitted among EPGs without a contract.
- Members of an EPG require contracts in order to communicate with other members.
- Contracts consist of subjects, filters, actions, and objects.
- EPGs communicate with each other according to contract rules.
Explanation:
Endpoint groups (EPGs) in a Cisco Application Centric Infrastructure (ACI) fabric communicate with each other according to contract rules. EPGs are logical groupings of endpoints that provide the same application or components of an application. For example, a collection of Hypertext Transfer Protocol Secure (HTTPS) servers could be logically grouped into an EPG labeled WEB. Contracts are policy objects that define how EPGs communicate. There are three types of contracts that can be applied in an ACI fabric:
Regular – applies filters to matching traffic and typically follows taboo contracts
Taboo – denies and logs matching traffic
Out-of-Band (OOB) – applies to OOB traffic from the management tenant
With the exception of some types of traffic—such as network configuration traffic, routing protocol traffic, and multicast traffic—EPGs require contracts in order to communicate with each other.
Members of an EPG do not require contracts in order to communicate with other members. Instead, members of an EPG communicate with each other by using their own network configurations, rules, and filters.
Contracts consist of subjects, filters, actions, and optionally labels, not objects. Subjects are groups of filters that are specific to a given application. Filters classify traffic by matching Open Systems Interconnection (OSI) network model Layer 2 or Layer 4 characteristics. Actions are the action that is performed on traffic that matches the filters. Labels can be created to group EPGs or subjects. These groupings add granularity to the enforcement of a policy.
Multicast traffic is permitted among EPGs without a contract. In addition, some Dynamic Host Configuration Protocol version 4 (DHCPv4) traffic is permitted between EPGs without a contract. Other traffic types that are permitted between EPGs by default are Open Shortest Path First (OSPF), Enhanced Interior Gateway Routing Protocol (EIGRP), Protocol Independent Multicast (PIM), Internet Group Management Protocol (IGMP), and Internet Control Message Protocol version 6 (ICMPv6) neighbor discovery. -
Which Cisco ACI model implementation stage is an abstract expression that is derived by the APIC?
- the hardware model
- the resolved model
- the concrete model
- the logical model
Explanation:
Of the available choices, the Cisco Application Centric Infrastructure (ACI) model resolved model is an abstract expression that is derived by the Cisco Application Policy Infrastructure Controller (APIC). The resolved model is a stage that is derived by the APIC in abstract from the logical model stage. In other words, the logical model is converted to the resolved model by the APIC. This stage is a lower-level representation of the ACI model than the logical model stage in that it represents how configuration components are sent to the infrastructure when a policy is executed.
The logical model stage of the Cisco ACI model is not an abstract expression that is derived by the APIC. The logical model is typically configured by the user in the Cisco APIC. The application network profile, which is often simply referred to as the application profile, is an expression of the logical model. The application network profile is an object that acts as the container for all other objects in the model; it tiers endpoint groups (EPGs) and represents how they relate to each other.
The concrete model is not an abstract expression that is derived by the APIC. The concrete model is a stage that is derived from the resolved model in that it represents the ACI model after configuration has been delivered to each endpoint in the fabric. The concrete model is typically created when switches in the ACI model convert the resolved model. However, there are some objects in the logical model that do not require conversion to the resolved model to also be represented in the concrete model. These objects include physical port properties that are already local to a given leaf or port.
The hardware model is not an abstract expression that is derived by the APIC. The Cisco ACI model consists of only three implementation stages. The hardware model is not one of those stages. Instead, concrete objects are consumed by application-specific integrated circuits (ASICs) on hardware. -
You manage the Cisco ACI fabric in the following exhibit:
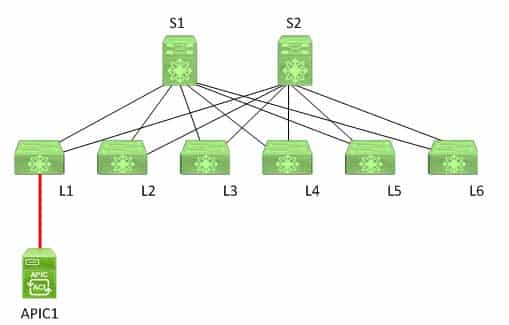
350-601 Part 06 Q10 011 S1 has just been discovered by APIC1. No other spine switches have yet been discovered.
Which of the following best describes the switches that might have been discovered before S1?- L1, L2, L3, L4, L5, and L6
- L4 and L6
- L1
- L2, L3, L4, L5, and L6
- S2
Explanation:
Most likely, L1 was discovered before S1 in this scenario because of the way that Cisco Application Policy Infrastructure Controllers (APICs) discover and register leaf and spine switches in a Cisco Application Centric Infrastructure (ACI) fabric. When a Cisco APIC begins the switch discovery process, it first detects only the leaf switch to which it is connected. After that leaf switch is registered, the APIC discovers each of the spine switches to which the leaf switch is connected. Spine switches do not automatically register with the APIC. When a spine switch is registered with the APIC, the APIC will discover all the leaf switches that are connected to that spine switch. Therefore, APIC1 will not discover all the leaf switches in this scenario until each spine switch is registered with the APIC.
S2 will be discovered by APIC1 next in this scenario; it was not discovered before S1. In this scenario, APIC1 has just discovered S1. This means that L1, the leaf switch to which APIC1 is directly connected, has already been discovered as well. L1 is directly connected to both spine switches in the topology. Because S1 was just discovered and no other spine switches have yet been discovered, it is likely that APIC1 will next discover S2.
APIC1 will not discover L2, L3, L4, L5, or L6 before it discovers S1 in this scenario. All these switches are leaf switches that are directly connected to both S1 and S2. However, none of these leaf switches are directly connected to APIC1. Although APIC1 in this scenario will eventually discover L2, L3, L4, L5, and L6, it will first discover all the spine switches to which L1 is directly connected because APIC1 is directly connected to L1. -
Which of the following is a benefit of CNAs in a Cisco Unified Fabric?
- consistent policies
- elimination of STP
- reduced cabling
- segregation of LAN and SAN
Explanation:
Of the available choices, reduced cabling is a benefit of converged network adapters (CNAs) in a Cisco Unified Fabric. Cisco Unified Fabric is a combination of architecture and high performance concepts that is intended to simplify data center networks.
CNAs are network adapters that combine network interface cards (NICs) and host bus adapters (HBAs), enabling one adapter to support both Ethernet and Fibre Channel (FC). A server that contains separate FC and local area network (LAN) ports can require significantly more cabling than a server that is configured with a CNA.
Segregation of LAN and storage area network (SAN) is not a benefit of CNAs in a Cisco Unified Fabric. On the contrary, CNAs are a feature of Cisco Unified Fabric that help converge a data center’s LAN and SAN over a single transport in order to simplify management, provisioning, and operation.
Elimination of Spanning Tree Protocol (STP) is not a benefit of CNAs in a Cisco Unified Fabric. Virtual Port Channels (vPCs) reduce Cisco Unified Fabric’s reliance on STP by replacing EtherChannel. However, vPCs still require STP to mitigate switching loops if they occur. Cisco FabricPath can replace STP with the Layer 3 routing protocol Intermediate System-to-Intermediate System (IS-IS) in order to scale a Layer 2 network beyond normal limits.
Consistent policies are not a benefit of CNAs in a Cisco Unified Fabric. Consistent policies across Cisco Unified Fabric is a benefit of using Cisco NX-OS and policy templates that can be easily deployed across the fabric and in virtual environments. These templates reduce the likelihood of human error during configuration and ensure that security and performance are applied the same way across the network. -
You want to configure IP pools and MAC pools in the Cisco UCS Manager GUI.
Which of the following Navigation pane tables should you click?
- Servers
- SAN
- VM
- Admin
- LAN
- Equipment
Explanation:
You should click the LAN tab in the Cisco Unified Computing System (UCS) Manager graphical user interface (GUI) if you want to configure Internet Protocol (IP) pools and Media Access Control (MAC) pools. Cisco UCS Manager GUI is a Java application. The main area of the GUI is divided into a Navigation pane and a work area. The selections you click in the Navigation pane determine the information and configuration fields that are displayed in the work area.
The Navigation pane of the Cisco UCS Manager GUI contains six tabs in a row across the top of the pane. To configure or view a given element of Cisco UCS Manager, you should first click the Navigation pane tab appropriate for that element. The Navigation pane contains all of the following tabs:
– The Equipment tab
– The Servers tab
– The LAN tab
– The SAN tab
– The VM tab
– The Admin tab
The Equipment tab can be used to display an inventory of the UCS domain. This information includes color-coded fault indicators, such as a red, yellow, or orange rectangle. If a device has a fault, one of these indicators will appear around the name of the device on the Equipment tab. The Equipment tab contains four nodes: Equipment, Chassis, Rack-mounts, and Fabric Interconnects. Selected nodes contain information specific to the devices indicated by the node name. For example, the Fabric Interconnects node contains information about expansion modules, fans, and power supply units (PSUs) connected to the domain’s fabric interconnects.
The Servers tab can be used to modify server-specific configurations, such as policies, profiles, and universally unique identifier (UUID) pools. The Servers tab contains six nodes: Servers, Service Profiles, Service Profile Templates, Policies, Pools, and Schedules. Selected nodes contain information specific to the server configurations indicated by the node name. For example, the Policies node allows the configuration of policies related to server adapters, server firmware, and other components.
The LAN tab can be used to configure local area network (LAN) components, such as Quality of Service (QoS) classes, virtual LANs (VLANs), and flow control policies. The LAN tab contains seven nodes: LAN Cloud, Appliances, Internal LAN, Policies, Pools, Traffic Monitoring Sessions, and Netflow Monitoring. Selected nodes contain information specific to the LAN component indicated by the node name. For example, the Pools node allows the configuration of both IP address pools and MAC address pools that have been defined for a LAN.
The SAN tab can be used to configure storage area network (SAN) components, such as virtual SANs (vSANs), and World Wide Name (WWN) pools. The SAN tab contains six nodes: SAN, SAN Cloud, Storage Cloud, Policies, Pools, and Traffic Monitoring Sessions. Selected nodes contain information specific to the SAN component indicated by the node name. For example, the SAN node allows the configuration of SAN uplinks, Fibre Channel (FC) address assignments, and vSANs.
The VM tab can be used to configure virtual machine-fabric extender (VM-FEX) for UCS domain servers that are equipped with virtual interface cards (VICs). The VM tab contains seven nodes: All, Clusters, Fabric Network Sets, Port Profiles, VM Networks, Microsoft, and VMware. Selected nodes contain information specific to the VM component indicated by the node name. For example, the VMware node can be used to configure Cisco UCS Manager connections to VMware vCenter.
The Admin tab can be used to configure system-wide settings that must be configured by an administrator or viewed by a security administrator. The Admin tab contains 10 nodes:
– All
– Faults, Events and Audit Log
– User Management
– Key Management
– Communication Management
– Stats Management
– Time Zone Management
– Capability Catalog
– Management Extension
– License Management
Selected nodes contain information specific to the administrative component indicated by the node name. For example, the User Management node allows the configuration of authentication methods and user roles as well as remote access methods. -
You are configuring a Cisco Nexus 5000 Series switch for the first time.
Which of the following is true about the default login?
- You can configure a short, trivial password at first boot and change it later.
- You will be required to configure an admin password before configuration.
- The default user is the network admin, and the password is password.
- The default user is the network admin, and the password is password.
Explanation:
When configuring a Cisco Nexus 5000 Series switch for the first time, you will be required to configure an admin password before configuration. This step in the configuration process is required and cannot be skipped by using the Ctrl-C keyboard combination. After you have successfully configured an admin password, you can enter setup mode by entering yes at the prompt.
The default user is the network admin; however, the default password is not password. When configuring a Cisco Nexus 5000 Series switch for the first time, the admin account is not configured with a password. By default, the network admin account is named admin. This account cannot be changed or deleted. However, the account password can and must be set at first boot.
You cannot configure a short, trivial password at first boot and change it later. If you attempt to configure a short, trivial password at boot, the Cisco Nexus 5000 Series configuration script will reject the password.
You will not be automatically logged in as a low-level local user. When a Cisco Nexus 5000 Series switch boots for the first time, only one default account, named admin, exists on the switch. After you have configured a strong password for the admin account, you can create additional user accounts on the switch. However, the switch must be initially configured by using the admin account. -
Which of the following Cisco Unified Fabric features improves on data center security?
- use of iSCSI instead of FCoE
- deployment of consistent network policies
- elimination of reliance on STP
- convergence of network and storage
Explanation:
Of the available choices, the deployment of consistent network policies is a Cisco Unified Fabric feature that improves on data center security. Cisco Unified Fabric allows the use of templates and a common switch operating system (OS) to ensure the deployment of network policies consistently across the fabric and its virtualized environments. The use of templates reduces the likelihood of human error when deploying network policies. In addition, Cisco Unified Fabric contains virtualization-aware security products.
The elimination of reliance on Spanning Tree Protocol (STP) to ensure a loop-free switching environment is a Cisco FabricPath feature that improves data center scalability and growth, not a Cisco Unified Fabric feature that improves security. Cisco Unified Fabric uses virtual Port Channel (vPC) in place of technologies such as EtherChannel, which was developed to enable redundant high-speed connectivity between switches in an STP topology. However, STP is still present to ensure that switching loops can be mitigated if they occur. Cisco FabricPath, on the other hand, is a Cisco Unified Fabric technology that completely replaces STP with the Intermediate System-to-Intermediate System (IS-IS) routing protocol. The combination of IS-IS with the Open Systems Interconnection (OSI) networking model Layer 2 fabric’s simplicity and fabric extenders enhances the scalability of Cisco Unified Fabric beyond the practical limits of a normal Layer 2 topology.
The use of Internet Small Computer Systems Interface (iSCSI) instead of Fibre Channel over Ethernet (FCoE) in a Cisco Unified Fabric enables the encapsulation of Fibre Channel (FC) in Transmission Control Protocol/Internet Protocol (TCP/IP) packets; it does not improve on data center security. The use of iSCSI in a Cisco Unified Fabric can be considered an alternative to the use of FCoE in a fabric that does not have strict storage connectivity requirements. Unlike iSCSI, FCoE encapsulates FC in Ethernet frames.
Convergence of network and storage is a Cisco Unified Fabric feature that simplifies operation and reduces management endpoints; it does not increase security. A typical Cisco Unified Fabric architecture is used to merge storage area network (SAN) features with a local area network (LAN). The resulting converged network and storage is delivered over an Ethernet fabric. -
Which of the following are not true about Cisco UCS Director workflow templates? (Choose two.)
- They can be executed like normal workflows.
- They can be used to schedule workflows.
- They contain task names, a workflow structure, and input names.
- Some templates are predefined in the system.
- They can be used to instantiate new workflows.
Explanation:
Cisco Unified Computing System (UCS) Director workflow templates cannot be executed like normal workflows. In addition, workflow templates cannot be used to schedule workflows. Cisco UCS Director is a resource automation and orchestration tool. UCS Director workflows are task sequences that accept user input and then automatically perform a series of tasks to complete a complex operation. Workflow templates simplify the creation of workflows based on a set of predefined tasks and therefore cannot themselves be executed. Workflows can be executed in several ways, including by using service requests, the Execute Now action, a virtual machine (VM) Action policy, a trigger, a schedule, or the rollback feature.
Cisco UCS Director workflow templates can be used to instantiate new workflows. Workflow templates are used as blueprints to create new workflows. In addition, you can create a new workflow and then export that workflow as a template in order to create other workflows built around the same tasks.
Cisco UCS Director workflow templates contain task names, a workflow structure, and input names. Task names are literally the string names of the tasks that are to be executed in the workflow. The tasks themselves are already built into the system in which the workflow template is defined. A workflow structure defines how the tasks are connected in the series. Input names define the details about the variables that are used to store the workflow’s user input.
Some Cisco UCS Director workflow templates are predefined in the system. Predefined workflow templates can be accessed by using the Workflow Templates tab in Cisco UCS Director Orchestration. -
You are examining the following command-line output on a Nexus 7000 Series switch:
vdc_id vdc_name state mac --------- -------- ------ --------------- 1 sales active A8:CC:D8:D8:65:F4 2 acctg active 7F:52:92:26:29:CF 3 prod active 7B:05:CA:ED:41:E1
Which of the following have you most likely issued?
- the show vdc command in the default VDC
- the show vdc command in a nondefault VDC
- the show vdc detail command in a nondefault VDC
- the show vdc membership command in a nondefault VDC
- the show vdc detail command in the default VDC
Explanation:
Most likely, you have issued the show vdc command in the default virtual device context (VDC) if you see the command-line output in this scenario on a Nexus 7000 Series switch. The show vdc command displays information about VDCs configured on the physical switch. However, the output of the show vdc command depends on the VDC in which the command has been issued. When issued in the default VDC, the command displays output for all VDCs configured on the device. When issued in a nondefault VDC, the command displays output for only the current VDC. To issue read and write commands in the default VDC, a user must be assigned the network-admin user role. The network-operator role has read-only access to the default VDC.
It Is not likely that you have issued the show vdc command in a nondefault VDC in this scenario If you had issued the show vdc command in a nondefault VDC, the output of this command would be limited to only the current VDC, which is the VDC in which the command was issued, as shown in the following output:NEX7S#show vdc
vdc_id vdc_name state mac --------- -------- ------ --------------- 1 sales active A8:CC:D8:D8:65:F4
Users that have been assigned the vdc-admin role or the vdc-operator role can review output from the show vdc command in the nondefault VDC in which they are operating. However, they do not have rights to read or write information in other VDCs.
It Is not likely that you have issued the show vdc detail command in this scenario. Similar to the show vdc command, the show vdc detail command displays information about the VDCs configured on the physical device. However, the show vdc detail command provides extra information about the VDCs that is not visible in the summarized show vdc command output. For example, the output of the show vdc detail command contains information about the VDC ha policy, boot order, create time, and restart count in addition to the VDC ID, name, state, and Media Access Control (MAC) address. Also similar to the show vdc command, the show vdc detail command displays output for all VDCs when the command is issued in the default VDC. When issued in a nondefault VDC, the command displays output only for the VDC in which it was issued.
It Is not likely that you have issued the show vdc membership command in this scenario. The show vdc membership command displays the interfaces that have been allocated to VDCs on the physical device, as shown in the following output:NEX7S#show vdc membership
vdc_id: 2 vdc_name: acctg interfaces:
Ethernet2/1
Based on the output above, you can surmise that the command was issued in a nondefault VDC. The output displays information for only the VDC named acctg. If the command had been issued in the default VDC, the output would have displayed information about the interfaces assigned to every VDC that is configured on the physical device.
-
Which of the following network devices do not connect to a leaf switch?
- a spine switch
- a router
- another leaf switch
- an APIC controller
Explanation:
Of the available choices, only another leaf switch does not connect to a leaf switch. In a spine-leaf architecture, the leaf layer of switches provides connectivity to and scalability for all other devices in the data center network. However, leaf switches do not connect to other leaf switches. Instead, a leaf switch communicates with another leaf switch by using a spine switch. The following exhibit displays a typical spine-leaf architecture wherein the top row of devices represents the spine layer of switches and the bottom row of devices represents the leaf layer of switches:
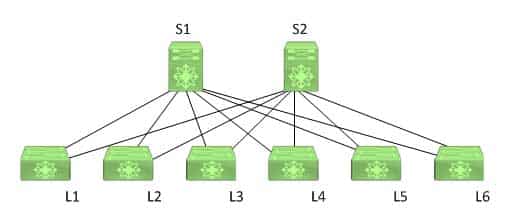
350-601 Part 06 Q17 012 In the exhibit above, the leaf switches are each directly connected to both spine switches. Switches S1 and S2 comprise the spine layer of the topology. Switches L1, L2, L3, L4, L5, and L6 comprise the leaf layer of the topology. In order for L1 to send a packet to L6, the packet must traverse either S1 or S2. The spine-leaf architecture differs from the traditional three-tier network architecture, which consists of a core layer, an aggregation layer, and an access layer.
Leaf switches connect to spine switches. In a spine-leaf architecture, spine switches are used to provide bandwidth and redundancy for leaf switches. Therefore, spine switches do not connect to devices other than leaf switches. As the name implies, spine switches are the backbone of the architecture.
Leaf switches connect to Cisco Application Policy Infrastructure Controllers (APICs). The leaf switch to which a Cisco APIC is directly connected is the first device in a spine-leaf architecture that will be discovered by and registered with the APIC. When a Cisco APIC begins the switch discovery process, it first detects only the leaf switch to which it is connected. After that leaf switch is registered, the APIC discovers each of the spine switches to which the leaf switch is connected. Spine switches do not automatically register with the APIC. When a spine switch is registered with the APIC, the APIC will discover all the leaf switches that are connected to that spine switch.
Leaf switches connect to routers. Routers are typically used to connect to the Internet or to a wide area network (WAN). Leaf switches in a spine-leaf architecture directly connect to routers. -
You connect Ethernet links to four ports on slot 1 of a new Cisco Nexus 5548UP switch and receive the following error:
ERROR: Ethernet range starts from first port of the module
ERROR: FC range should end on last port of the module
Which of the following is most likely true?
- Slot 1 does not support unified ports.
- No more Ethernet ports are available on the module.
- The Ethernet links were connected in an incorrect port order.
- FC links are already connected to slot 1.
- Slot 1 does not support Ethernet links.
Explanation:
Most likely, the Ethernet links were connected in an incorrect port order if you receive the error message in this scenario when you connect Ethernet links to four ports on slot 1 of a new Cisco Nexus 5548UP switch. Unified ports are ports that can be either Ethernet or Fibre Channel (FC) ports. Cisco Nexus switches that support unified ports require that Ethernet links be connected from the beginning of the port range forward and that FC links be connected from the end of the port range backward. Therefore, in this scenario, the Ethernet links would need to be connected to port 1/1, port 1/2, port 1/3, and port 1/4.
As a further example, if you were to connect a single Ethernet link and a single FC link to slot 1 of a Cisco Nexus 5548UP switch that has no other links connected, you must connect the Ethernet link to port 1/1 and the FC link to port 1/32. Slot 1 of a Cisco Nexus 5548UP switch contains 32 unified ports. If you were to then connect an additional Ethernet link to slot 1, that link must be connected to port 1/2. If you were to connect an additional FC link to slot 1, that link must be connected to port 1/31. Link additions should continue in that way until the Ethernet range ends where the FC range begins and no more ports are available in the slot.
There is nothing in this scenario to indicate that FC links are already connected to slot 1 of the Cisco Nexus 5548UP switch. However, even if FC links were already connected to slot 1 of the switch, the error would still indicate that the Ethernet links were connected in an incorrect port order.
It is not likely that there are no more Ethernet ports available on the switch. In this scenario, you have already connected four Ethernet links to the switch when the error message occurs. There would have to have been at least five Ethernet links available on the switch in this scenario in order for the switch to have detected the incorrect port order.
Slot 1 on the Cisco Nexus 5548UP switch supports Ethernet links because slot 1 on the Cisco Nexus 5548UP switch contains only unified ports. Other Nexus switches might contain different port configurations. For example, on the Cisco Nexus 5596T, only the last 16 ports are unified ports. -
You connect a FEX to a Cisco Nexus switch. After configuration is complete, you issue the show fex 100 command on the switch and receive the following partial output:
Switch#show fex 100
<output omitted> Pinning-mode: static Max-links: 1 Fabric port for control traffic: Po100 Fabric interface state: Po100 – Interface Up. State: Active Eth1/1 – Interface Up. State: Active Eth1/2 – Interface Up. State: Active Eth2/1 – Interface Up. State: Active Eth2/2 – Interface Up. State: Active
Which of the following is true?
- The fex associate Eth2/1 command has been issued on the Po100 interface.
- The fex associate Eth2/2 command has been issued on the Po100 interface.
- The fex associate Eth1/1 command has been issued on the Po100 interface.
- The fex associate 100 command has been issued on the Po100 interface.
- The fex associate Eth1/2 command has been issued on the Po100 interface.
Explanation:
The fex associate 100 command has been issued on the Po100 port-channel interface in this scenario. There are two methods for connecting a Cisco fabric extender (FEX) to a Cisco Nexus switch: static pinning and port channel. In this scenario, the output of the show fex 100 command on the Nexus switch indicates that four Nexus switch physical interfaces and one port channel have been associated with the FEX: Ethernet 1/1, Ethernet 1/2, Ethernet 2/1, Ethernet 2/2, and P0100. In addition, the Po100 port channel is acting as the FEX fabric port.
To associate a port channel with a FEX, you should first create the port channel, configure the port channel to support a FEX, and then associate the port channel with a specific FEX. For example, the following commands configure Po100 on a Cisco Nexus switch to support a FEX and associate with FEX 100:
interface port-channel 100
switchport mode fex-fabric
fex associate 100
The switchport mode fex-fabric command and the fex associate 100 command should also be issued on each physical port that is a member of Po100’s channel group 100.
None of the other commands in this scenario could be issued on the Cisco Nexus switch, because they all contain invalid syntax. The syntax of the fex associate command is fex associate FEX-number, where FEX-number is the FEX chassis ID that is assigned to the FEX. Chassis IDs are assigned by the administrator and are valid in the range from 100 through 199. Chassis ID values less than 100 are typically ports on the parent switch. Ports on a FEX device are identified by chassis number, slot number, and port number. For example, a FEX interface might be identified as Ethernet 100/1/1, which indicates the interface in FEX 100 slot 1, port 1. -
Which of the following Cisco ACI logical constructs is equivalent to a private IP name space or IP network?
- common
- EPG
- context
- tenant
Explanation:
Of the available choices, a context is a Cisco Application Centric Infrastructure (ACI) fabric logical construct that is equivalent to a single Internet Protocol (IP) network or IP name space. In this way, a context can be considered equivalent to a single virtual routing and forwarding (VRF) instance. An endpoint policy typically ensures that all endpoints within a given context exhibit similar behavior.
Tenants are containers that can be used to represent physical tenants, organizations, domains, or specific groupings of information. A tenant in a Cisco ACI fabric can therefore contain multiple contexts. Typically, tenants are configured to ensure that different policy types are isolated from each other, similar to user groups or roles in a role-based access control (RBAC) environment.
Common is the name for a special tenant in a Cisco ACI fabric. The common tenant typically contains policies that can be shared with other tenants. Contexts that are placed in the common tenant can likewise be shared among tenants. Contexts that are placed within a private tenant, on the other hand, are not shared with other tenants.
Endpoint groups (EPGs) are logical groupings of endpoints that provide the same application or components of an application. For example, a collection of Hypertext Transfer Protocol Secure (HTTPS) servers could be logically grouped into an EPG labeled WEB. EPGs are typically collected within application profiles. EPGs can communicate with other EPGs by using contracts.