350-601 : Implementing and Operating Cisco Data Center Core Technologies (DCCOR) : Part 08
-
You are examining the following command-line output on a Nexus 7000 Series switch:
vdc_id vdc_name state mac --------- -------- ------ --------------- 2 acctg active 7F:52:92:26:29:CF
Which of the following have you most likely issued?
- the show vdc detail command in the default VDC
- the show vdc command in the default VDC
- the show vdc membership command in a nondefault VDC
- the show vdc detail command in a nondefault VDC
- the show vdc command in a nondefault VDC
Explanation:
Most likely, you have issued the show vdc command in a nondefault virtual device context (VDC) if you see the command-line output in this scenario on a Nexus 7000 Series switch. The show vdc command displays information about VDCs configured on the physical switch. However, the output of the show vdc command depends on the VDC in which the command has been issued. When issued in the default VDC, the command displays output for all VDCs configured on the device, as shown in the following output:
NEX7S#show vdc vdc_id vdc_name state mac --------- -------- ------ --------------- 1 sales active A8:CC:D8:D8:65:F4 2 acctg active 7F:52:92:26:29:CF 3 prod active 7B:05:CA:ED:41:E1
When issued in a nondefault VDC, the command displays output for only the current VDC, as shown in the following output:
NEX7S# show vdc vdc_id vdc_name state mac -------- -------- ------ --------------- 2 acctg active 7F:52:92:26:29:CF
To issue read and write commands in the default VDC, a user must be assigned the network-admin user role. The network-operator role has read-only access to the default VDC. Users that have been assigned the vdc-admin role or the vdc-operator role can review output from the show vdc command in the nondefault VDC in which they are operating. However, they do not have rights to read or write information in other VDCs.
It is not likely that you have issued the show vdc detail command in this scenario. Similar to the show vdc command, the show vdc detail command displays information about the VDCs configured on the physical device. However, the show vdc detail command provides extra information about the VDCs that is not visible in the summarized show vdc command output. For example, the output of the show vdc detail command contains information about the VDC ha policy, boot order, create time, and restart count in addition to the VDC ID, name, state, and Media Access Control (MAC) address. Also similar to the show vdc command, the show vdc detail command displays output for all VDCs when the command is issued in the default VDC. When issued in a nondefault VDC, the command displays output only for the VDC in which it was issued.
It is not likely that you have issued the show vdc membership command in this scenario. The show vdc membership command displays the interfaces that have been allocated to VDCs on the physical device, as shown in the following output:NEX7S#show vdc membership vdc_id: 2 vdc_name: acctg interfaces: Ethernet2/1Based on the output above, you can surmise that the command was issued in a nondefault VDC. The output displays information for only the VDC named acctg. If the command had been issued in the default VDC, the output would have displayed information about the interfaces assigned to every VDC that is configured on the physical device.
-
Which of the following describes a group of Layer 3 networks that can be shared with groups of private networks in a Cisco ACI fabric?
- EPG
- common
- tenant
- context
Explanation:
Of the available choices, common best describes a group of Layer 3 networks that can be shared with groups of private networks in a Cisco Application Centric Infrastructure (ACI) fabric. Common is the name for a special tenant in a Cisco ACI fabric. The common tenant typically contains policies that can be shared with other tenants.
Tenants are containers that can be used to represent physical tenants, organizations, domains, or specific groupings of information. A tenant in a Cisco ACI fabric can contain multiple Layer 3 networks. Typically, tenants are configured to ensure that different policy types are isolated from each other, similar to user groups or roles in a role-based access control (RBAC) environment.
A context is a Cisco ACI fabric logical construct that is equivalent to a single Internet Protocol (IP) network or IP name space. In this way, a context can be considered equivalent to a single virtual routing and forwarding (VRF) instance. An endpoint policy typically ensures that all endpoints within a given context exhibit similar behavior. Contexts that are placed in the common tenant can likewise be shared among tenants. Contexts that are placed within a private tenant, on the other hand, are not shared with other tenants.
Endpoint groups (EPGs) are logical groupings of endpoints that provide the same application or components of an application. For example, a collection of Hypertext Transfer Protocol Secure (HTTPS) servers could be logically grouped into an EPG labeled WEB. EPGs are typically collected within application profiles. EPGs can communicate with other EPGs by using contracts. -
Examine the Cisco UCS Director Workflow Designer workflow in the following exhibit:
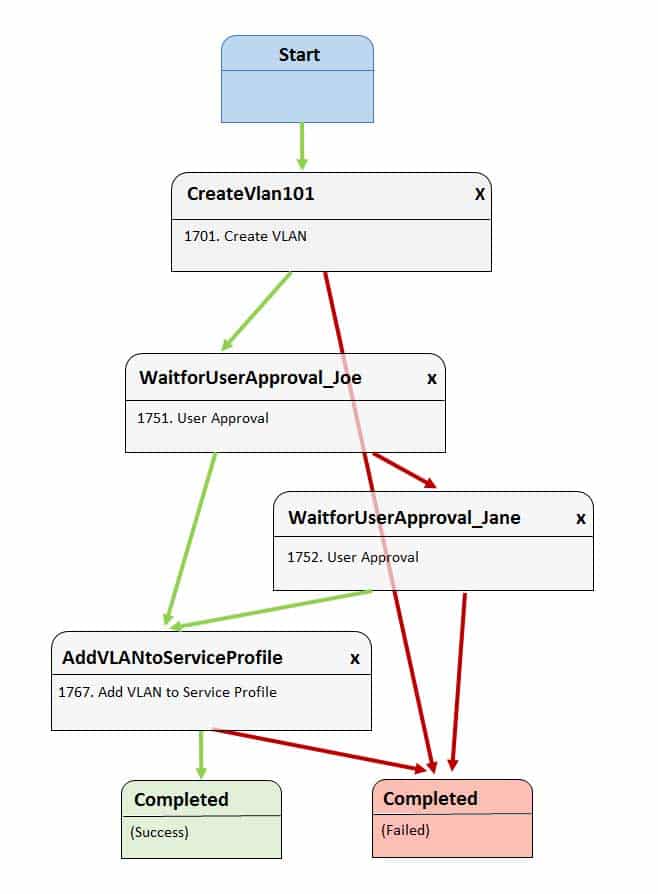
350-601 Part 08 Q03 015 How many users must reject before VLAN 101 is prevented from being added to the service profile?
- two
- three
- one
- none
Explanation:
In this scenario, two users must reject before virtual local area network (VLAN) 101 is prevented from being added to the service profile. The Cisco Unified Computing System (UCS) Director Workflow Designer workflow in this scenario creates VLAN 101 after it starts. Before the next task is executed, the workflow requires the approval of a user named Joe. If Joe approves, the workflow attempts to add VLAN 101 to the service profile. If Joe does not approve, Jane is given an opportunity to approve. If Jane approves, VLAN 101 can be added to the service profile.
Cisco UCS Director Workflow Designer is a graphical user interface (GUI) that enables users to create automated workflows in a drag-and-drop fashion. Each task in a workflow is equipped with an On Success button and an On Failure button. Each button provides a drop-down list of other tasks in the workflow. In this way, the user can select which tasks are executed next if a task succeeds and which tasks are executed next if a task fails. Green arrows in Workflow Designer represent the On Success path. Red arrows represent the On Failure path.
In this scenario, the On Failure path of the WaitforUserApproval_Joe task is tied to the WaitforUserApproval_Jane task, which means that Jane gets an opportunity to approve the addition of VLAN 101 to the service profile if Joe does not. The On Failure path of the WaitforUserApproval_Jane task is tied to the Completed (Failure) task. By contrast, the On Success path of the WaitforUserApproval_Joe task is tied to the AddVLANtoServiceProfile task, as is the On Success path of the WaitforUserApproval_Jane task.
At least one user will need to approve in this scenario for VLAN 101 to be added to the service profile. The On Failure path of the WaitforUserApproval_Joe task is tied to the WaitforUserApproval_Jane task. The On Failure path of the WaitforUserApproval_Jane task is tied to the Completed (Failure) task. Therefore, there is no chance of successfully adding VLAN 101 to the service profile without user approval.
No more than one user will need to approve in this scenario for VLAN 101 to be added to the service profile. The On Success path of the WaitforUserApproval_Joe task is tied to the AddVLANtoServiceProfile task. Therefore, the workflow attempts to add VLAN 101 to the service profile if Joe approves. Similarly, the On Success path of the WaitforUserApproval_Jane task is tied to the AddVLANtoServiceProfile task. Therefore, the workflow attempts to add VLAN 101 to the service profile if Joe rejects and Jane approves.
Only two user approval tasks are present in this workflow: WaitforUserApproval_Joe and WaitforUserApproval_Jane. Therefore, it is not possible to require more than two users to approve or reject the addition of VLAN 101 to the service profile. -
Which of the following is not a type of contract that can be applied in an ACI fabric?
- regular
- in-band
- OOB
- taboo
Explanation:
Of the available choices, in-band is not a type of contract that can be applied in a Cisco Application Centric Infrastructure (ACI) fabric. Contracts are policy objects that define how endpoint groups (EPGs) communicate. There are three types of contracts that can be applied in an ACI fabric:
Regular — applies filters to matching traffic and typically follows taboo contracts
Taboo — denies and logs matching traffic
Out-of-Band (OOB) – applies to OOB traffic from the management tenant
EPGs are logical groupings of endpoints that provide the same application or components of an application. For example, a collection of Hypertext Transfer Protocol Secure (HTTPS) servers could be logically grouped into an EPG labeled WEB. With the exception of some types of traffic—such as network configuration traffic, routing protocol traffic, and multicast traffic—EPGs require contracts in order to communicate with each other.
Contracts consist of subjects, filters, actions, and optionally, labels. Subjects are groups of filters that are specific to a given application. Filters classify traffic by matching Open Systems Interconnection (OST) network model Layer 2 or Layer 4 characteristics. Actions are the action that is performed on traffic that matches the filters. Labels can be created to group EPGs or subjects. These groupings add granularity to the enforcement of a policy. -
You issue the following commands on a Nexus 7000 Series switch that is already configured to authenticate users by using TACACS+:
switchto vdc myvdc configure terminal aaa user default-role no aaa user default-role exit copy running-config start-config
Which of the following will occur when a remote user attempts to log in to the VDC named MyVDC by using TACACS+?
- The user will be assigned the vdc-operator role.
- The user will be assigned the network-operator role.
- The user will be assigned the network-admin role.
- The user will be assigned the vdc-admin role.
- The user will not be assigned a role and will be denied login.
Explanation:
The user will not be assigned a role and will be denied login when the remote user attempts to log in to the virtual device context (VDC) named MyVDC by using Terminal Access Controller Access-Control System Plus (TACACS+). In this scenario, TACACS+ is already configured on the Cisco Nexus 7000 Series switch. In addition, the aaa user default-role command has been issued but is immediately followed by the no aaa user default-role command in the configuration. Remote users who attempt to log in to the VDC named MyVDC will be denied access because no user role is assigned to those users.
Cisco Nexus switches use role-based access control (RBAC) to assign management privileges to a given user. By default, a Nexus 7000 switch is configured with the following user roles:
network-admin — has read and write access to all VDCs on the switch
network-operator — has read-only access to all the VDCs on the switch
vdc-admin — has read and write access to a specific VDC on the switch
vdc-operator — has read-only access to a specific VDC on the switch
The user will not be assigned the vdc-operator role, because the no aaa user default-role command has been issued. In this scenario, the aaa user default-role command has been issued in the VDC named MyVDC, which is a nondefault VDC on the switch. The aaa user default-role command configures the Authentication, Authorization, and Accounting (AAA) feature on the switch to automatically assign remote users the default user role at login. The default remote user role for nondefault VDCs on a Cisco Nexus switch is the vdc-operator role. However, this configuration will not apply in this scenario because of the no aaa user default-role command.
The user will not be assigned the vdc-admin user role. The vdc-admin user role allows read and write access to a specific VDC on the switch. If remote users were automatically assigned the vdc-admin role when logging in to the VDC named MyVDC, those users would have administrative access to the VDC, which is a security risk.
The user will not be assigned the network-admin role. In addition, the user will not be assigned the network-operator role. These roles are applied to users who have access to all VDCs that are configured on the switch, not a specific nondefault VDC. If the aaa user default-role command had been issued in the default VDC in this scenario, remote users who log in to the default VDC would be assigned a network-operator user role. -
Which of the following is a cloud computing deployment model that uses public resources on demand to extend its private infrastructure?
- community
- hybrid
- private
- public
Explanation:
Hybrid is a cloud computing deployment model that uses public resources on demand to extend its private infrastructure. Hybrid uses a mixture of private and public infrastructure resources to form a single organization’s cloud.
There are four different cloud computing deployment models: private cloud, public cloud, hybrid cloud, and community cloud. Cloud computing is a term used to describe computing services that are offered for consumption in a way that demands fewer infrastructure expenses from the organization. Cloud computing deployment models describe how the cloud services are delivered to the customer. Cloud computing service models, on the other hand, describe the cloud services that the customer has purchased, such as infrastructure, platforms, or software.
Community is a cloud computing deployment model that can use a mixture of public and private infrastructure resources. However, community clouds share the public infrastructure resources between multiple organizations. Typically, the organizations involved in community cloud computing have common needs that the community cloud can provide.
Private is a cloud computing deployment model that is constructed for only the organization that uses its services. Private cloud computing is typically established by using either a third-party service or internal servers, not both. The use of a private cloud enables an administrator to ensure that the cloud’s resources are available only to an authorized few users.
Public is a cloud computing deployment model that is owned and operated by a service provider. Public cloud computing does not use a mixture of private and public infrastructure resources. Public clouds typically allow the general public to access storage and applications served from the cloud. For example, a Gmail account is a service that is provided from a public cloud. Other public cloud computing providers include Amazon and Rackspace. -
The application network profile is an expression of which Cisco ACI model implementation stage?
- the logical model
- the concrete model
- the hardware model
- the resolved model
Explanation:
Of the available choices, the application network profile is an expression of the logical model stage of the Cisco Application Centric Infrastructure (ACI) model. The application network profile, which is often simply referred to as the application profile, is an object that acts as the container for all other objects in the model; it tiers endpoint groups (EPGs) and represents how they relate to each other. The logical model is typically configured by the user in the Cisco Application Policy Infrastructure Controller (APIC).
The application network profile is not an expression of the resolved model stage of the Cisco ACI model. The resolved model is a stage that is derived by the APIC in abstract from the logical model stage. In other words, the logical model is converted to the resolved model by the APIC. This stage is a lower-level representation of the ACI model than the logical model stage in that it represents how configuration components are sent to the infrastructure when a policy is executed.
The application network profile is not an expression of the concrete model stage of the Cisco ACI model. The concrete model is a stage that is derived from the resolved model in that it represents the ACI model after configuration has been delivered to each endpoint in the fabric. The concrete model is typically created when switches in the ACI model convert the resolved model. However, there are some objects in the logical model that do not require conversion to the resolved model to also be represented in the concrete model. These objects include physical port properties that are already local to a given leaf or port.
The application network profile is not an expression of the hardware model stage of the Cisco ACI model. The Cisco ACI model consists of only three implementation stages. The hardware model is not one of those stages. Instead, concrete objects are consumed by application-specific integrated circuits (ASICs) on hardware. -
You want to extend the Layer 2 fabric of a data center’s network from its Cisco 7000 Series switches without the addition of unnecessary administrative overhead and configuration.
Which of the following devices are you most likely to add to the deployment?
- the Cisco Nexus 2000 Series switch
- the Cisco Nexus 1000v switch
- the Cisco Nexus 5000 Series switch
- the Cisco Nexus 9000 Series switch
Explanation:
Most likely, you will add a Cisco Nexus 2000 Series switch to the deployment if you want to extend the Open Systems Interconnection (OSI) Layer 2 fabric of a data center’s network from its Cisco 7000 Series switches without the addition of unnecessary administrative overhead and configuration. The Cisco Nexus 2000 Series of switches are fabric extenders (FEXs) and cannot operate as standalone switches. By default, Cisco FEX devices are not configured with software. Instead, they depend on parent switches, such as a Cisco Nexus 7000 Series switch, to install and configure software, provide forwarding tables, and provide control plane functionality.
You are not likely to add a Cisco Nexus 1000v to the deployment, because adding that device would create additional administrative overhead and configuration. The Cisco Nexus 1000v is a virtual switch that is capable of connecting to upstream physical switches in order to provide connectivity for a virtual machine (VM) network environment. Although the Cisco Nexus 1000v operates similar to a standard switch, it exists only as software in a virtual environment and is therefore not a physical switch.
You are not likely to add a Cisco Nexus 5000 Series switch to the deployment, because adding that device would create additional administrative overhead and configuration. Cisco Nexus 5000 Series switches operate as standalone physical switches. Cisco Nexus 5000 Series switches are data center access layer switches that can support 10-gigabit-per-second (Gbps) or 40-Gbps Ethernet, depending on the model. Native Fibre Channel (FC) and FC over Ethernet (FCoE) are also supported by Cisco Nexus 5000 Series switches.
You are not likely to add a Cisco Nexus 9000 Series switch to the deployment, because adding that device would create additional administrative overhead and configuration. Cisco Nexus 9000 Series switches operate as standalone physical switches. Cisco Nexus 9000 Series switches can operate either as traditional NX-OS switches or in an Application Centric Infrastructure (ACI) mode. Unlike Cisco Nexus 7000 Series, Cisco Nexus 9000 Series switches do not support virtual device contexts (VDCs) or storage protocols. -
You issue the following commands on SwitchA:
feature vpc vpc domain 101 peer-keepalive destination 192.168.1.2 source 192.168.1.1 vrf mgmt interface port-channel 1 switchport mode access vpc peer-link interface port-channel 3 switchport mode trunk vpc 3
You issue the following commands on SwitchB: feature vpc vpc domain 101 peer-keepalive destination 192.168.1.1 source 192.168.1.2 vrf mgmt interface port-channel 1 switchport mode access vpc peer-link interface port-channel 3 switchport mode trunk vpc 3
Which of the following is true?
- The switch port mode is not correctly configured for port-channel 1.
- The peer keepalive configuration is in the wrong VRF.
- The vPC number in port-channel 3 is not correctly configured.
- The switch port mode is not correctly configured for port-channel 3.
Explanation:
In this scenario, the switch port mode is not correctly configured for port-channel 1. Port-channel 1 on SwitchA and SwitchB is configured as an access port. In addition, this port channel is configured with the peer keepalive link for this virtual port channel (vPC) domain. The peer keepalive link requires a trunk port.A vPC enables you to bundle ports from two switches into a single Open Systems Interconnection (OSI) Layer 2 port channel. Similar to a normal port channel, a vPC bundles multiple switch ports into a single high-speed trunk port. A single vPC domain cannot contain ports from more than two switches. For ports on two switches to successfully form a vPC domain, all the following must be true:- The vPC feature must be enabled on both switches.- The vPC domain ID must be the same on both switches.- The peer keepalive link must be configured and must be 10 gigabits per second (Gbps) or more.- The vPC number must be the same on both switches.In this scenario, the feature vpn command has been issued on both SwitchA and SwitchB. This command ensures that the vPC feature is enabled on each switch. In addition, the vpc domain 101 command has been issued on both switches. This command ensures that each switch is configured to operate in the same vPC domain.The switch port modes are correct for port-channel 3 in this scenario. Port-channel 3 is a normal port channel that has been configured with the vPC number. Normal port channels can be configured as either access ports or trunk ports. However, you should configure normal port channels as trunk ports if you intend to have traffic from multiple virtual local area networks (VLANs) traverse the port.The vPC number is correctly configured in this scenario. In order to correctly form a vPC domain between two switches, the vPC number must be the same on each switch. In this scenario, a vPC number of 3 has been configured on port-channel 3 on each switch. Port-channel 3 is a normal trunk port channel.The peer keepalive link is not in the wrong virtual routing and forwarding (VRF) instance in this scenario. Peer keepalive links can be configured to operate in any VRF, including the management VRF. The peer keepalive link operates at Layer 3 of the OSI networking model; it is used to ensure that vPC switches are capable of determining whether a vPC domain peer has failed. On SwitchA, the peer-keepalive command has been issued with a source Internet Protocol (IP) address of 192.168.1.1 and a destination IP address of 192.168.1.2. On SwitchB, the peer-keepalive command has been issued with a source IP address of 192.168.1.2 and a destination IP address of 192.168.1.1. Based on this information, you can conclude that SwitchA is configured with an IP address of 192.168.1.1 and that SwitchB is configured with an IP address of 192.168.1.2.
-
You issue the port-channel load-balance scr-dst-port module 4 command on a Cisco Nexus 7000 Series switch running NX-OS 5.0(5).
How is distribution loaded for port channels on slot 4?
- based on the source IP address and destination port
- based on the source and destination MAC address
- based on the source and destination port
- based on the source MAC address and destination port only
- based on the defaults because the command contains invalid syntax
Explanation:
Distribution for port channels on slot 4 in this scenario will be based on the defaults because the command contains invalid syntax. In this scenario, the Cisco Nexus 7000 Series switch is running NX-OS 5.0(5). Prior to NX-OS 5.1(3), the port-channel load-balance command required an ethernet keyword. Therefore, the valid syntax for NX-OS versions older than 5.1(3) is port-channel load-balance ethernet method [module slot]. In NX-OS 5.1(3), Cisco removed the ethernet keyword. After NX-S 5.1(3), the basic syntax of the port-channel load-balance command is port-channel load-balance method [module slot], where method is one of the following 10 keywords:
– dst-ip
– dst-mac
– dst-port
– src-dst-ip
– src-dst-mac
– src-dst-port
– src-ip
– src-mac
– src-port
– vlan-only
The dst-ip keyword, dst-mac keyword, and dst-port keyword load port channel distribution based on the destination Internet Protocol (IP) address, Media Access Control (MAC) address, and port number, respectively. Similarly, the src-ip keyword, src-mac keyword, and src-port keyword load port channel distribution based on the source IP address, source MAC address, and port number, respectively. The src-dst-ip keyword, src-dst-mac keyword, and src-dst-port keyword load port channel distribution based on the source and destination IP addresses, MAC addresses, and port numbers, respectively. The vlan-only keyword loads distribution on only the virtual local area network (VLAN) modules.
The optional module keyword accepts a slot number value. If you configure the port-channel load-balance command with the module keyword, the configuration applies only to the specified slot. Otherwise, the configuration applies to the entire device. By default on a Cisco Nexus switch, a port channel load balances Layer 2 packets based on the source and destination MAC addresses. Layer 3 packets, on the other hand, are load balanced based on the source and destination IP addresses. You must be operating in the default virtual device context (VDC) on the switch in order to issue the port-channel load-balance command. -
You administer the Cisco UCS domain in the following exhibit:
Which of the following policies could you implement to ensure that all three UCS chassis are discovered by Cisco UCS Manager? (Choose two.)
- 4-Link Chassis Discovery Policy
- 8-Link Chassis Discovery Policy
- 3-Link Chassis Discovery Policy
- 1-Link Chassis Discovery Policy
- 2 Link Chassis Discovery Policy
Explanation:
You could implement either a 1-Link Chassis Discovery Policy or a 2-Link Chassis Discovery Policy to ensure that all three Cisco Unified Computing System (UCS) chassis are discovered by Cisco UCS Manager in this scenario. The link chassis discovery
policy that is configured on Cisco UCS Manager specifies the minimum number of links that a UCS chassis must have to the fabric interconnect in order to be automatically discovered and added to the UCS domain. If a UCS chassis has fewer than the minimum number of links specified by the policy, the chassis will be neither discovered nor added to the UCS domain by Cisco UCS Manager. The two Cisco fabric interconnects in this scenario, FEX 1 and FEX 2, are connected together. UCS 1 has a two-link connection to FEX 1. UCS 2 has a two-link connection to FEX 1. UCS 3 has a three-link connection to FEX 2.
A 1-Link Chassis Discovery Policy in this scenario would cause Cisco UCS Manager to discover and add UCS 1, UCS 2, and UCS 3 to the UCS domain because each of those devices has at least one link to the fabric interconnect. However, each of the devices
will be discovered and added as a chassis with only one link to the fabric interconnect. In order to have Cisco UCS Manager recognize and use the other links between the UCS devices and the fabric interconnect, you would need to reacknowledge the chassis in Cisco UCS Manager after the initial discovery has been completed.
A 2-Link Chassis Discovery Policy in this scenario would cause Cisco UCS Manager to discover and add UCS 1, UCS 2, and UCS 3 to the UCS domain because each of those devices has at least two links to the fabric interconnect. However, UCS 3, which has three links to the fabric interconnect, will be discovered and added as a chassis with only two links. In order to have Cisco UCS Manager recognize and use the other links between UCS 3 and the fabric interconnect, you would need to reacknowledge the chassis in Cisco UCS Manager after the initial discovery has been completed.
A 3-Link Chassis Discovery Policy would not cause Cisco UCS Manager to discover the UCS devices in this scenario, because Cisco UCS Manager does not support a 3-Link Chassis Discovery Policy. There are five link chassis discovery policies that are supported by Cisco UCS Manager: 1-Link Chassis Discovery Policy, 2-Link Chassis Discovery Policy, 4-Link Chassis Discovery Policy, 8-Link Chassis Discovery Policy, and Platform-Max Discovery Policy. The Platform-Max Discovery Policy is not a choice in this scenario.
A 4-Link Chassis Discovery Policy would not cause Cisco UCS Manager to discover the UCS devices in this scenario. For a 4-Link Chassis Discovery Policy to discover any of the UCS devices in this scenario, at least one of those devices would need to have a minimum of four links to the fabric interconnect. For example, if UCS 3 had four or more links to the fabric interconnect in this scenario and Cisco UCS Manager was configured with a 4-Link Chassis Discovery Policy, only UCS 3 would be discovered and added to the UCS domain.
An 8-Link Chassis Discovery Policy would not cause Cisco UCS Manager to discover the UCS devices in this scenario. For an 8-Link Chassis Discovery Policy to discover any of the UCS devices in this scenario, at least one of those devices would need to have a minimum of eight links to the fabric interconnect. None of the UCS devices in this scenario are connected with more than three links to the FEX devices. -
You are configuring a Cisco Nexus 5000 Series switch for the first time. The switch requires an IPv4 management interface.
Which of the following setup information is required at first boot? (Choose two.)
- an IPv4 subnet mask for the management interface
- a new strong password for the admin user
- an SNMP community string
- additional account names and passwords for account creation
- a switch name
Explanation:
Of the available choices, only a new strong password for the admin user and an Internet Protocol version 4 (IPv4) subnet mask for the management interface are required. In this scenario, you are configuring a Cisco Nexus 5000 Series switch for the first time. The switch requires an IPv4 management interface. Because the switch requires an IPv4 management interface, a subnet mask for the management interface must be configured at first boot.
When configuring a Cisco Nexus 5000 Series switch for the first time, you will be required to configure an admin password before configuration. This step in the configuration process is required and cannot be skipped by using the Ctrl-C keyboard combination. After you have successfully configured an admin password, you can enter setup mode by entering yes at the prompt.
Configuring additional account names and passwords when you are configuring a Cisco Nexus 5000 Series switch for the first time is optional. At first boot, a Cisco Nexus 5000 Series switch is configured with the single user account named admin. This account is also the network admin and cannot be changed or deleted.
Configuring a switch name when you are configuring a Cisco Nexus 5000 Series switch for the first time is optional. The name you choose for the switch will also be used at the command-line interface (CLI) prompt. If you choose not to configure a switch name during initial setup, the default name for the switch is switch.
Configuring a Simple Network Management Protocol (SNMP) community string when you are configuring a Cisco Nexus 5000 Series switch for the first time is optional. An SNMP read-only community name enables another SNMP device with that community string to request SNMP management information from the Nexus switch. -
You are creating a workflow in UCS Director’s Workflow Designer.
Which of the following are not predefined workflow tasks? (Choose three.)
- completed (failed)
- completed
- start
- completed (success)
- start (failed)
- start (success)
Explanation:
Of the available choices, the following Cisco Unified Computing System (UCS) Director’s Workflow Designer tasks are not predefined:
– Completed
– Start (Failed)
– Start (success)
Workflows determine the order in which tasks that are designed to automate complex IT operations are performed. Workflow Designer allows administrators to create workflows that can then be automated by using UCS Director’s orchestrator. By default, the following tasks are predefined when a workflow is created:
– Completed (failed)
– Completed (success)
– Start
The start task is the beginning of the workflow. The completed (failed) task represents the end of a workflow when the desired result could not be achieved. The completed (success) task represents a successfully completed workflow. Each task in a workflow processes input and produces output that is sent to the next task in the workflow. In addition, each task contains an On Success event and an On Failure event that can be used to determine which task should be performed next based on whether the task could be successfully completed. -
Which of the following primary elements of a tenant defines the MAC address space?
- a contract
- a filter
- a bridge domain
- an EPG
Explanation:
A bridge domain is the primary element of a tenant that defines the Media Access Control (MAC) address space. Bridge domains are logical Layer 2 forwarding configurations within a Cisco Application Centric Infrastructure (ACI) fabric that use switched virtual interfaces (SVIs) for gateways and can be configured to span multiple physical devices. In this respect, bridge domains are similar to virtual local area networks (VLANs). However, the purpose of a bridge domain is to define the MAC address space and flood domain.
Tenants are containers that can be used to represent organizations, domains, or specific groupings of information. Typically, tenants are configured to ensure that different policy types are isolated from each other, similar to user groups or roles in a role-based access control (RBAC) environment.
An endpoint group (EPG) is a primary element of a tenant; however, an EPG does not define the MAC address space. EPGs are logical groupings of endpoints that provide the same application or components of an application. For example, a collection of Hypertext Transfer Protocol Secure (HTTPS) servers could be logically grouped into an EPG labeled WEB. EPGs are typically collected within application profiles. EPGs can communicate with other EPGs by using contracts.
A contract is a primary element of a tenant; however, a contract does not define the MAC address space. Contracts are policy objects that define how EPGs communicate with each other. There are three types of contracts that can be applied in an ACI fabric:
– Regular — applies filters to matching traffic and typically follows taboo contracts
– Taboo — denies and logs matching traffic
– Out-of-Band (OOB) – applies to OOB traffic from the management tenant
A filter is a primary element of a tenant; however, a filter does not define the MAC address space. Filters are low-level ACI objects that help define EPG contracts. Filters operate at Layer 2, Layer 3, and Layer 4 of the Open Systems Interconnection (OSI) networking model. -
Which of the following FCoE switch port types is typically connected to a VN port?
- another VN port
- a VF port
- a SPAN port
- a VE port
Explanation:
A Fibre Channel over Ethernet (FCoE) virtual fabric (VF) interface port type is typically connected to a virtual node (VN) port. FCoE is used in data centers to encapsulate Fibre Channel (FC) over an Ethernet network. This encapsulation enables the FC protocol to communicate over 10 gigabit-per-second (Gbps) Ethernet. There are two types of FCoE switch ports: a VF port and a virtual edge (VE) port.
An FCoE VF port typically connects to an end host. A VN port is a port on an end host, such as a host bus adapter (HBA) port. If the end host is connected to an Ethernet network that is configured with virtual local area networks (VLANs), the Spanning Tree Protocol (STP) configuration on the Ethernet fabric might require extra attention, especially if the Ethernet fabric is not using Per-VLAN Spanning Tree Plus (PVST+). A proper STP configuration on the Ethernet fabric prevents the Ethernet topology from affecting storage area network (SAN) traffic.
An FCoE VE port typically connects to a port on another FC forwarder (FCF). STP does not operate on VE ports, because these ports typically connect two FCFs. FC does not require switching loop prevention, because FCFs have no concept of switching loops. VE ports typically default to trunk mode.
A switched port analyzer (SPAN) port, which is also known as a mirroring port, is a type of port that is used to collect copies of packets transmitted over another port, over a given device, or over a network. In an FCoE configuration, a SPAN destination port can be either an FC interface or an Ethernet interface. SPAN source ports, on the other hand, can be FC interfaces, virtual FC (vFC) interfaces, a virtual SAN (vSAN), a VLAN, an Ethernet interface, a port channel interface, or a SAN port channel interface. -
Which OTV failure isolation feature maps a MAC address from a remote data center to that remote data center’s join interface IP address?
- unknown unicast handling
- broadcast policy control
- ARP optimization
- STP isolation
Explanation:
Overlay Transport Virtualization (OTV)’s unknown unicast handling feature maps a Media Access Control (MAC) address from a remote data center to that data center’s join interface Internet Protocol (IP) address. The join interface is the Open Systems Interconnection (OSI) networking model Layer 3 interface on which OTV is deployed and that is capable of discovering other OTV-enabled data centers. OTV’s unicast traffic handling feature advertises MAC addresses between data centers. Because of this, advertisement and mapping process, OTV is capable of suppressing the transmission of unknown unicast traffic across data centers.
OTV is a technology that extends Layer 2 networks across data centers. Similar to Ethernet over Multiprotocol Label Switching (EoMPLS), virtual private LAN services (VPLS), and dark fiber, OTV is intended to enable the extension of Layer 2 applications across large geographic distances. It is typically deployed on data center edge devices. OTV uses MAC address routing to ensure that Layer 2 reachability information can be transmitted between data centers. Unlike other Layer 2 extension technologies, OTV’s MAC address routing takes place at the control plane level. Other technologies rely on data plane forwarding and flooding.
OTV’s Spanning Tree Protocol (STP) isolation feature ensures that bridge protocol data units (BPDUs) are not forwarded across the overlay. This feature is enabled by default. Because BPDUs are suppressed, each data center’s STP domain remains independent of other data centers connected to the overlay. This prevents data centers from accidentally creating Layer 2 loops over OTV.
Broadcast policy control and Address Resolution Protocol (ARP) optimization are OTV features that reduce traffic between OTV-connected data centers. Each of these features reduces the amount of broadcast traffic that is flooded between data centers. -
Which of the following formats are not used by a REST API to produce output? (Choose three.)
- HTTP
- JSON
- CSV
- XML
- HTML
Explanation:
Representational state transfer (REST) does not produce output in comma separated values (CSV) format, Hypertext Markup Language (HTML) format, or Hypertext Transfer Protocol (HTTP) format. Instead, REST produces output in JavaScript Object Notation (JSON) or Extensible Markup Language (XML) format. REST is an Application Programming Interface (API) architecture that uses HTTP or HTTP Secure (HTTPS) to enable external resources to access and make use of programmatic methods that are exposed by the API. For example, a web application that retrieves user product reviews from an online marketplace for display on third-party websites might obtain those reviews by using methods provided in an API that is developed and maintained by that marketplace. The JSON or XML output that is returned by the API is parsed by the third-party website for display.
HTTP is the Open Systems Interconnection (OSI) networking model Application layer protocol that is used to transfer information from a web server to a web browser. A REST API uses HTTP to transmit requests for information to a web server, which is not the same as producing the formatted output that is returned from the server.
Although HTML is similar to XML, which uses tags like HTML does, XML requires a strict syntax and is typically used to structure data, not format and render data in a web browser. HTML, on the other hand, is designed to inform a web browser about how given information should be displayed.
The CSV format is a common tabular format that is supported by spreadsheet applications and other business reporting applications. CSV files are plain-text files that segregate the fields of a table by using a combination of quotation marks, symbolic delimiters such as a comma or a semicolon, and line breaks. -
You issue the following commands on SwitchA and SwitchB, which are Cisco Nexus 7000 Series switches:
SwitchA(config)#vpc domain 101 SwitchA(config-vpc-domain)#peer-keepalive destination 192.168.1.2 source 192.168.1.1 vrf default SwitchA(config-vpc-domain)#exit SwitchA(config)#interface range ethernet 2/1 - 2 SwitchA(config-if-range)#switchport SwitchA(config-if-range)#channel-group 1 mode active SwitchA(config-if-range)#interface port-channel 1 SwitchA(config-if)#switchport mode trunk SwitchA(config-if)#vpc peer-link SwitchB(config)#vpc domain 10 SwitchB(config-vpc-domain)#peer-keepalive destination 192.168.1.1 source 192.168.1.2 vrf default SwitchB(config-vpc-domain)#exit SwitchB(config)#interface range ethernet 2/1 - 2 SwitchB(config-if-range)#switchport SwitchB(config-if-range)#channel-group 1 mode active SwitchB(config-if-range)#interface port-channel 1 SwitchB(config-if)#switchport mode access SwitchB(config-if)#vpc peer-link
Which of the following is most likely a problem with this configuration?
- The vpc peer-link command should be issued only on SwitchA.
- Port-channel 1 on both switches should be an access port.
- The Ethernet port range is using the wrong channel group mode on Switch B.
- The vPC domain ID on SwitchB should be the same as the value on SwitchA.
Explanation:
Most likely, the problem with the configuration in this scenario is that the virtual port channel (vPC) domain ID on SwitchB should be the same as the value on SwitchA. A vPC domain is comprised of two switches per domain. Each switch in the vPC domain must be configured with the same vPC domain ID. To enable vPC configuration on a Cisco Nexus 7000 Series switch, you should issue the feature vpc command on both switches. To assign the vPC domain ID, you should issue the vpc domain domain-id command, where domain-id is an integer in the range from 1 through 1000, in global configuration mode. For example, issuing the vpc domain 101 command on a Cisco Nexus 7000 Series switch configures the switch with a vPC domain ID of 101.
The vpc peer-link command should be issued on both switches in this scenario. A vPC peer link should always be comprised of 10-gigabit-per-second (Gbps) Ethernet ports. Peer links are configured as a port channel between the two members of the vPC domain. You should configure vPC peer links after you have successfully configured a peer keepalive link. Cisco recommends connecting two 10-Gbps Ethernet ports from two different input/output (I/O) modules. To configure a peer link, you should issue the vpc peer-link command in interface configuration mode. For example, the following commands configure a peer link on Port-channel 1:SwitchA(config)#interface port-channel 1 SwitchA(config-if)#switchport mode trunk SwitchA(config-if)#vpc peer-link SwitchB(config)#interface port-channel 1 SwitchB(config-if)#switchport mode trunk SwitchB(config-if)#vpc peer-linkPort-channel 1 on both switches should be a trunk port. Trunk ports are used to carry traffic from multiple virtual local area networks (VLANs) across physical switches. Access ports can only carry data from a single VLAN and are typically connected to end devices, such as hosts or servers.
It is not a problem that the channel group mode is configured to active on the Ethernet ports in this scenario. It is important to issue the correct channel-group commands on a port channel’s member ports prior to configuring the port channel. For example, if you are creating Port-channel 1 by using the Ethernet 2/1 and Ethernet 2/2 interfaces, you could issue the following commands on each switch to correctly configure those interfaces as members of the port channel:SwitchA(config)#interface range ethernet 2/1 - 2 SwitchA(config-if-range)#switchport SwitchA(config-if-range)#channel-group 1 mode active SwitchB(config)#interface range ethernet 2/1 - 2 SwitchB(config-if-range)#switchport SwitchB(config-if-range)#channel-group 1 mode active
-
Which of the following is true about the first 32 ports on a Cisco Nexus 5596T?
- They are Ethernet ports.
- They are management ports.
- They are FC ports.
- They are unified ports.
Explanation:
The first 32 ports in the Cisco Nexus 5596T are all 10-gigabit-per-second (Gbps) Ethernet ports; they cannot be configured as unified ports. A unified port is a physical port on a Cisco switch that can be configured as either an Ethernet port or a Fibre Channel (FC) port.
The last 16 ports in slot 1 of a Cisco Nexus 5596T are FC ports, not the first 32 ports. However, the last 16 ports in a Nexus 5596T can be configured as unified ports.
The Cisco Nexus 5596T has one Ethernet management port, not 32. In addition, the Cisco Nexus 5596T supports one console management port.
All 32 ports in slot 1 on a Cisco Nexus 5548UP switch are unified ports, not the first 32 ports on a Cisco Nexus 5596T. Typically, a Nexus switch that contains unified ports requires that all Ethernet ports be configured from the first port in the slot forward and all FC ports be configured from the last port in the slot backward. In other words, a slot that contains 32 unified ports, two acting as Ethernet and two acting as FC, will typically use ports 1 and 2 for Ethernet links and ports 32 and 31 for FC links. -
Which of the following default user roles are common to both the Nexus 5000 switch and the Nexus 7000 switch? (Choose two.)
- network-admin
- san-admin
- network-operator
- vdc-admin
- vdc-operator
Explanation:
Both the network-admin user role and the network-operator user role are common default user roles to both the Nexus 5000 switch and the Nexus 7000 switch. However, the privileges associated with these roles are different between the switch models because the Nexus 5000 switch does not support the virtual device context (VDC) feature. A VDC is a virtual switch.
Cisco Nexus switches use role-based access control (RBAC) to assign management privileges to a given user. The Nexus 7000 switch is capable of supporting the VDC feature. By default, a Nexus 7000 switch is configured with the following user roles:
– network-admin — has read and write access to all VDCs on the switch
– network-operator — has read-only access to all the VDCs on the switch
– vdc-admin — has read and write access to a specific VDC on the switch
– vdc-operator — has read-only access to a specific VDC on the switch
Unlike the Nexus 7000 switch, a Nexus 5000 switch does not support the VDC feature. By default, a Nexus 5000 switch is configured with the following user roles:
– network-admin — has complete read and write access to the switch
– network-operator — has read-only access to the switch
– san-admin — has complete read and write access to Fibre Channel (FC) and FC over Ethernet (FCoE) by using Simple Network Management Protocol (SNMP) or the command-line interface (CLI)