350-601 : Implementing and Operating Cisco Data Center Core Technologies (DCCOR) : Part 09
-
Which of the following default Cisco UCS Manager user roles is automatically assigned to the default admin account?
- Administrator
- Operations
- AAA Administrator
- Read-Only
- Network Administrator
Explanation:
The Cisco Unified Computing System (UCS) default user role of Administrator is automatically assigned to the default admin account. The Cisco UCS System is installed with several default user roles for its role-based access control (RBAC) system. User accounts in Cisco UCS Manager are assigned one of the default roles or a custom role that is defined by an administrator. These roles define the access privileges for each account. Cisco Manager is web-based software that can be used to manage a single UCS domain. Administrators have read-write access to the entire system. Although the Administrator role can be assigned to other user accounts, this role cannot be removed from the default admin account.
The AAA Administrator user role is not automatically assigned to the default admin account. The AAA Administrator user role has read-write access to users, roles, and the system’s authentication, authorization, and accounting (AAA) configuration. AAA Administrators can read the rest of the system but cannot write to it.
The Network Administrator user role is not automatically assigned to the default admin account. The Network Administrator user role has read-write access to the fabric interconnect and network security. However, this role has only read access to the rest of the system.
The Operations user role is not automatically assigned to the default admin account. The Operations user role has read-write access to system logs and read access to the rest of the system. An Operations user can read and write to Syslog servers and faults.
The Read-Only user role is not automatically assigned to the default admin account. The Read-Only user role has read access to the configuration. In addition, the Read-Only user role cannot modify the system state. There are five other default Cisco UCS Manager user roles:
– Facility Manager — has read-write access to power management
– Server Equipment Administrator — has read-write access to physical server operations
– Server Profile Administrator — has read-write access to logical server operations
– Server Security Administrator — has read-write access to security operations
– Storage Administrator — has read-write access to storage operations -
You want to configure user authentication methods and user roles in the Cisco UCS Manager GUI.Which of the following Navigation pane tables should you click?
- LAN
- Admin
- Equipment
- Servers
- SAN
- VM
Explanation:
You should click the Admin tab in the Cisco Unified Computing System (UCS) Manager graphical user interface (GUI) if you want to configure authentication methods and user roles. Cisco UCS Manager GUI is a Java application. The main area of the GUI is divided into a Navigation pane and a work area. The selections you click in the Navigation pane determine the information and configuration fields that are displayed in the work area.
The Navigation pane of the Cisco UCS Manager GUI contains six tabs in a row across the top of the pane. To configure or view a given element of Cisco UCS Manager, you should first click the Navigation pane tab appropriate for that element. The Navigation pane contains all of the following tabs:
– The Equipment tab
– The Servers tab
– The LAN tab
– The SAN tab
– The VM tab
– The Admin tab
The Equipment tab can be used to display an inventory of the UCS domain. This information includes color-coded fault indicators, such as a red, yellow, or orange rectangle. If a device has a fault, one of these indicators will appear around the name of the device on the Equipment tab. The Equipment tab contains four nodes: Equipment, Chassis, Rack-mounts, and Fabric Interconnects. Selected nodes contain information specific to the devices indicated by the node name. For example, the Fabric Interconnects node contains information about expansion modules, fans, and power supply units (PSUs) connected to the domain’s fabric interconnects.
The Servers tab can be used to modify server-specific configurations, such as policies, profiles, and universally unique identifier (UUID) pools. The Servers tab contains six nodes: Servers, Service Profiles, Service Profile Templates, Policies, Pools, and Schedules. Selected nodes contain information specific to the server configurations indicated by the node name. For example, the Policies node allows the configuration of policies related to server adapters, server firmware, and other components.
The LAN tab can be used to configure local area network (LAN) components, such as Quality of Service (QoS) classes, virtual LANs (VLANs), and flow control policies. The LAN tab contains seven nodes: LAN Cloud, Appliances, Internal LAN, Policies, Pools, Traffic Monitoring Sessions, and Netflow Monitoring. Selected nodes contain information specific to the LAN component indicated by the node name. For example, the Pools node allows the configuration of both IP address pools and MAC address pools that have been defined for a LAN.
The SAN tab can be used to configure storage area network (SAN) components, such as virtual SANs (vSANs), and World Wide Name (WWN) pools. The SAN tab contains six nodes: SAN, SAN Cloud, Storage Cloud, Policies, Pools, and Traffic Monitoring Sessions. Selected nodes contain information specific to the SAN component indicated by the node name. For example, the SAN node allows the configuration of SAN uplinks, Fibre Channel (FC) address assignments, and vSANs.
The VM tab can be used to configure virtual machine-fabric extender (VM-FEX) for UCS domain servers that are equipped with virtual interface cards (VICs). The VM tab contains seven nodes: All, Clusters, Fabric Network Sets, Port Profiles, VM Networks, Microsoft, and VMware. Selected nodes contain information specific to the VM component indicated by the node name. For example, the VMware node can be used to configure Cisco UCS Manager connections to VMware vCenter.
The Admin tab can be used to configure system-wide settings that must be configured by an administrator or viewed by a security administrator. The Admin tab contains 10 nodes:
– All
– Faults, Events and Audit Log
– User Management
– Key Management
– Communication Management
– Stats Management
-Time Zone Management
– Capability Catalog
– Management Extension
– License Management
Selected nodes contain information specific to the administrative component indicated by the node name. For example, the User Management node allows the configuration of authentication methods and user roles as well as remote access methods. -
Which of the following best describes a policy repository?
- a controller for distributing, tracking, and updating policies
- collection of endpoints with identical requirements
- a collection of rules applied to endpoints, existing or hypothetical
- a collection of endpoints already known to the Cisco ACI
Explanation:
Of the available choices, a policy repository can be best described as a collection of rules applied to endpoints, existing or hypothetical. A policy repository is the first of two logically coupled components of an endpoint policy; it is typically centralized in the Cisco Application Policy Infrastructure Controller (APIC) or in leaf nodes in the Application Centric Infrastructure (ACI) fabric. The policy repository component of an endpoint policy stores rules that can be applied to existing endpoints, planned endpoints, or deleted endpoints. Endpoint policies are used to define how endpoint groups (EPGs) communicate with each other.
An endpoint registry is a collection of endpoints already known to the Cisco ACI. The endpoint registry is the second of two logically coupled components of an endpoint policy; it stores the operational state of each endpoint. In Cisco ACI, the endpoint registry is stored in a distributed database within the ACI fabric.
An EPG is a collection of endpoints with identical requirements; it is a primary element of a tenant. EPGs are logical groupings of endpoints that provide the same application or components of an application. For example, a collection of Hypertext Transfer Protocol Secure (HTTPS) servers could be logically grouped into an EPG labeled WEB. EPGs are typically collected within application profiles. EPGs can communicate with other EPGs by using contracts.
The Cisco APIC is a controller for distributing, tracking, and updating policies. In other words, it is a central component of a Cisco ACI fabric that is used for both automation and management. -
Which of the following OTV technologies is typically a VDC running on a Cisco Nexus switch?
- OTV join interface
- OTV edge device
- OTV overlay interface
- OTV internal interface
Explanation:
An Overlay Transport Virtualization (OTV) edge device is typically a virtual device context (VDC) running on a Cisco Nexus switch, such as a Nexus 7000 Series switch. OTV is a means of simplifying the deployment of data center interconnect (DCI), enabling the extension of Layer 2 applications between data centers. The edge device is responsible for receiving Open Systems Interconnection (OST) networking model Layer 2 traffic for virtual local area networks (VLANs) that are extended. Ethernet frame traffic is encapsulated into Internet Protocol (IP) packets and transmitted to the remote network.
An OTV join interface is an OTV technology that is a physical or logical Layer 3 interface. An OTV join interface is used to connect an overlay network to remote overlay edge devices. An OTV join interface can be a physical interface, subinterface, or logical interface such as a port channel.
An OTV internal interface is a Layer 2 interface. The OTV internal interface is an interface on the OTV edge device that connects to the VLANs that are being extended. Typically, the OTV internal interface operates similarly to any other Layer 2 switch trunk port or access port and does not require configuration specific to OTV.
An OTV overlay interface is a logical interface that is defined by the user. The OTV overlay interface receives and forwards any Layer 2 frames that must be transmitted to the remote site. -
Which of the following statements best describes vPC peer keepalive links?
- There can be only two peers per domain.
- They synchronize the control plane and the data plane.
- They monitor the status of vPC peers.
- They synchronize the state between two vPC peers.
Explanation:
A virtual port channel (vPC) peer keepalive link monitors the status of vPC peers. The peer keepalive link operates at Layer 3 of the Open Systems Interconnection (OSI) networking model; it is used to ensure that vPC switches are capable of determining whether a vPC domain peer has failed. Peer keepalive links can be configured to operate in any virtual routing and forwarding (VRF) instance, including the management VRF. Each vPC peer keepalive link is configured with the remote peer’s IP address as its destination IP address and the local peer’s IP address as its source address. Peer keepalive links must be trunk links.
There can be only two peers, or switches, per vPC domain. A vPC enables you to bundle ports from two peers, which form a domain, into a single OSI Layer 2 port channel. Similar to a normal port channel, a vPC bundles multiple switch ports into a single high-speed trunk port. A single vPC domain cannot contain ports from more than two switches. For ports on two switches to successfully form a vPC domain, all the following must be true:
– The vPC feature must be enabled on both switches.
– The vPC domain ID must be the same on both switches.
– The peer keepalive link must be configured and must be 10 gigabits per second (Gbps) or more.
– The vPC number must be the same on both switches.
A vPC peer link, not a vPC peer keepalive link, synchronizes the state between two vPC peers. A vPC peer link is typically comprised of a port channel made up of two physical ports on each switch. This link synchronizes Media Access Control (MAC) address tables between switches and serves as a transport for data plane traffic. Bridge protocol data unit (BPDU) and Link Aggregation Control Protocol (LACP) packets are also forwarded to the second peer over this link, which causes the vPC peers to appear to be a single control plane.
Cisco Fabric Services, not a vPC peer keepalive link, synchronizes the control plane and the data plane. Cisco Fabric Services is a messaging protocol that operates between vPC peers. Control plane and data plane information is synchronized over the vPC peer link. -
DRAG DROP
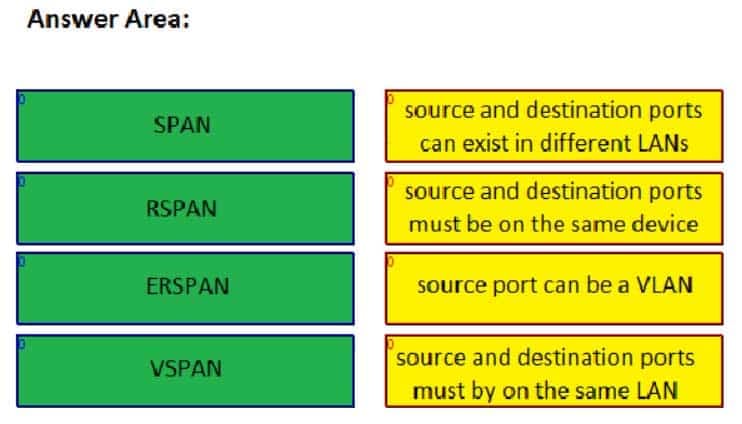
Drag the type of port mirroring on the left to its description on the right. Use all types. Each type can be used only once
350-601 Part 09 Q06 016 Question 
350-601 Part 09 Q06 016 Answer Explanation:
Switched Port Analyzer (SPAN) source and destination ports must be on the same device. SPAN is limited to monitoring traffic on only the local device and cannot direct traffic to destination ports on a separate device for analysis. The source port can be a physical or virtual Ethernet port, a port channel, or a virtual local area network (VLAN) if VLAN-based SPAN (VSPAN) is being used. The destination port can be a physical or virtual Ethernet port or a port channel. However, the source port and the destination port cannot be the same port.
Remote SPAN (RSPAN) source and destination ports must be on the same local area network (LAN). RSPAN enables you to monitor traffic on a network by capturing and sending traffic from a source port on one device to a destination port on a different device on a nonrouted network.
Encapsulated RSPAN (ERSPAN) source and destination ports can exist in different LANs. ERSPAN enables an administrator to capture and analyze traffic across a routed network. Therefore, ERSPAN can monitor traffic across multiple routers on a network that spans multiple locations.
A VSPAN source port can be a VLAN. All ports in a source VLAN become SPAN source ports. SPAN, RSPAN, and ERSPAN are all capable of using VLANs as sources by implementing VSPAN. -
DRAG DROP
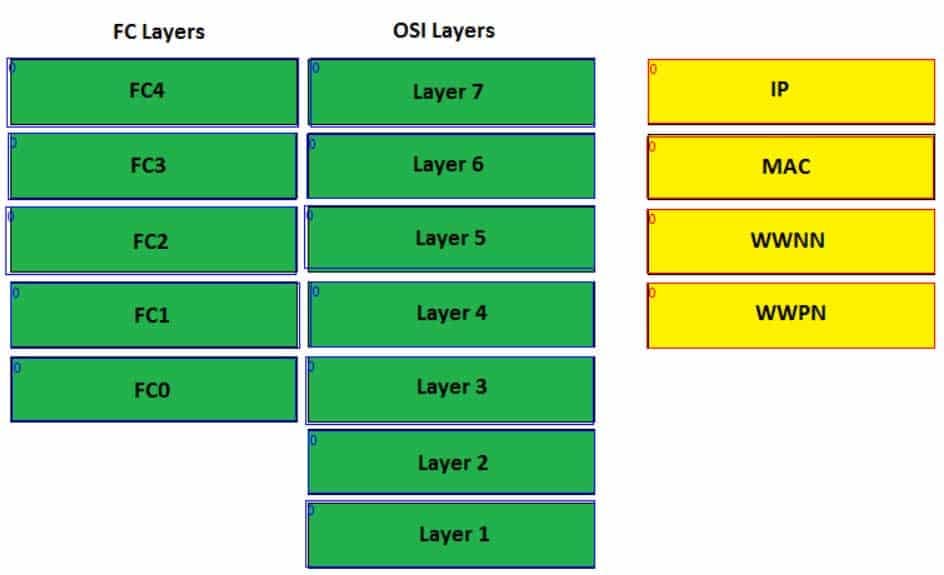
Drag the networking layer on the left to the appropriate identity type on the right. Layers can be used more than once. Not all layers will be used.
350-601 Part 09 Q07 017 Question 
350-601 Part 09 Q07 017 Answer Explanation:
Unlike other networking technologies, Fibre Channel (FC) does not make use of the Open Systems Interconnection (OSI) network model. Instead, FC uses the FC-Layers model, which is broken out in the following fashion:
– FC4: Protocol mapping layer
– FC3: Common services layer
– FC2: Network layer
– FC1: Data link layer
– FCO: Physical layer
– FCO, FC1, and FC2 have similar names and functions to their OSI model equivalents, which are Layer 1, Layer 2, and Layer 3, respectively. FC3 is equivalent to the OSI model’s Transport layer, or Layer 4. FC4, on the other hand, is similar in function to a combination of all three top layers of the OSI model, which are the Session layer (Layer 5), the Presentation layer (Layer 6), and the Application layer (Layer 7).
World Wide Node Names (WWNNs) are 64-bit globally unique identifiers that specify a given FC node. These identifiers are typically used to assign FC1 addresses in storage area network (SAN) routing. Similar to WWNN identities, World Wide Port Name (WWPN) identities are globally unique 64-bit identifiers that are used to assign FC1 addresses. However, WWPNs represent a specific FC port, not an entire node.
Media Access Control (MAC) identities are MAC addresses, which are OSI Layer 2 48-bit hexadecimal addresses that are typically burned into a network interface card (NIC). The first 24 bits of a MAC address represent the Organizationally Unique Identifier (OUD), which is a value that is assigned by the Institute of Electrical and Electronics Engineers (IEEE). The OUI identifies the NIC’s manufacturer. The last 24 bits of a MAC address uniquely identify a specific NIC constructed by the manufacturer. This value is almost always an identifier that the manufacturer has never before used in combination with the OUI.
Internet Protocol (IP) identities are IP addresses, which are 32-bit decimal addresses that are assigned to OSI Layer 3 interfaces. In a Cisco Unified Computing System (UCS) domain, IP pools are typically used to assign one or more management IP addresses to each server’s Cisco Integrated Management Controller (IMC). -
Which of the following FabricPath components provides access layer connectivity?
- a leaf switch
- the APIC
- a spine switch
- a CE network
Explanation:
Of the available choices, a leaf switch is the Cisco FabricPath component that provides access layer connectivity. Cisco FabricPath is a means of constructing a scalable Open Systems Interconnection (OSI) networking model Layer 2 network from both Layer 2 and Layer 3 components. End hosts and classic Ethernet (CE) networks are typically directly connected to leaf switches by using edge ports.
Spine switches do not provide access layer connectivity. Spine switches are the Cisco FabricPath component that form the backbone of the FabricPath’s switching fabric. Typically, leaf switches are connected to every spine switch along the backbone so that the spine switches provide connectivity between the leaf switches. Leaf switches connect to spine switches by using core ports.
The Cisco Application Policy Infrastructure Controller (APIC) is a means of managing the Cisco Application Centric Infrastructure (ACI). A Cisco ACI architecture requires both the APIC and the spine switches and leaf switches of FabricPath to complete the architecture. The APIC communicates with the spine and leaf nodes and provides policy distribution as well as centralized management.
A CE network, which is a traditional Ethernet network that uses Spanning Tree Protocol (STP) and transparent bridging, is not technically part of Cisco FabricPath. However, Cisco Nexus switches can connect to a CE network and Cisco FabricPath simultaneously. -
Which of the following is Cisco software that can be used to manage multiple UCS domains across geographical boundaries?
- Cisco UCS Director
- Cisco IMC Supervisor
- Cisco UCS Manager
- Cisco UCS Central
Explanation:
Cisco Unified Computing System (UCS) Central is software that can be used to manage multiple UCS domains, including domains that are separated by geographical boundaries. Cisco UCS Central can be used to deploy standardized configurations and policies from a central virtual machine (VM).
Cisco UCS Director is software that can automate actions and be used to construct a private cloud. Cisco UCS Director creates a basic Infrastructure as a Service (IaaS) framework by using hardware abstraction to convert hardware and software into programmable actions that can then be combined into an automated custom workflow. Thus Cisco UCS Director enables administrators to construct a private cloud in which they can automate and orchestrate both physical and virtual components of a data center. Cisco UCS Director is typically accessed by using a web-based interface.
Cisco UCS Manager is web-based software that can be used to manage a single UCS domain. The software is typically embedded in Cisco UCS fabric interconnects rather than installed in a VM or on separate physical servers.
Cisco Integrated Management Controller (IMC) Supervisor is software that can be used to centrally manage multiple standalone Cisco C-Series and E-Series servers. The servers need not be located at the same site. Cisco IMC Supervisor uses a web-based interface and is typically deployed as a downloadable virtual application. -
Which of the following Cisco UCS servers are typically installed directly in a rack?
- B-Series servers
- UCS Mini servers
- C-Series servers
- E-Series servers
- M-Series servers
Explanation:
Of the available options, Cisco Unified Computing System (UCS) C-Series servers are typically installed directly in a rack. Cisco UCS C-Series servers are rack-mount standalone servers that can operate either with or without integration with Cisco UCS Manager. Therefore, Cisco UCS C-Series servers do not require a UCS fabric. For administrators who are more familiar with traditional Ethernet networks than UCS Fabric Interconnect, C-Series servers will most likely be simpler to deploy and feel more familiar than other Cisco UCS server products.
Cisco UCS B-Series servers are blade servers that are installed in a UCS blade chassis. These blade servers can connect only to Cisco UCS Fabric Interconnect, not directly to a traditional Ethernet network. Blade servers in a chassis are typically hot-swappable, unlike the components of a rack-mount server. Therefore, blade server configurations are less likely to result in prolonged downtime if hardware fails.
Cisco UCS E-Series servers are typically installed in a blade chassis. However, Cisco UCS E-Series servers have similar capabilities to the standalone C-Series servers and do not require connectivity to a UCS fabric. In a small office environment, Cisco UCS E-Series servers are capable of providing the network connectivity and capabilities of a C-Series server along with the availability of B-Series servers.
Cisco UCS Mini servers are a compact integration of a Cisco UCS 5108 blade chassis, Cisco UCS 6324 Fabric Interconnects, and Cisco UCS Manager. Unlike other Cisco UCS servers, the UCS Mini server requires a special version of Cisco UCS Manager for management. It is possible to connect Cisco UCS C-Series servers to Cisco UCS Mini servers in order to expand their abilities.
Cisco UCS M-Series servers are neither rack servers nor blade servers. M-Series servers are comprised of computing modules that are inserted into a modular chassis. The chassis, not the server, can be installed in a rack. The modular design enables the segregation of computing components from infrastructure components. -
Which of the following types of identity pools consists of 48-bit hexadecimal identifiers?
- WWNN pools
- WWPN pools
- UUID pools
- MAC pools
- IP pools
Explanation:
Of the available choices, only Media Access Control (MAC) identity pools consist of 48-bit hexadecimal identifiers. MAC identity pools contain MAC addresses, which are 48-bit hexadecimal addresses that are typically burned into a network interface card (NIC). The first 24 bits of a MAC address represent the Organizationally Unique Identifier (OUI), which is a value that is assigned by the Institute of Electrical and Electronics Engineers (IEEE). The OUI identifies the NIC’s manufacturer. The last 24 bits of a MAC address uniquely identify a specific NIC constructed by the manufacturer. This value is almost always an identifier that the manufacturer has never before used in combination with the OUI.
Identity pools are logical resource pools that can be read and consumed by a service profile or a service profile template. These pools are used to uniquely identify groups of servers that share the same characteristics. A service profile can be used from Cisco Unified Computing System (UCS) Manager to automatically apply configurations to the servers identified by the pool. For Cisco UCS configurations or scenarios that require virtualized identities, the use of identity pools can greatly speed the server creation and template updating processes. There are five types of identity pools that can serve Cisco UCS service profile templates:
– Internet Protocol (IP) pools
– MAC pools
– Universally unique identifier (UUID) pools
– World Wide Node Name (WWNN) pools
– World Wide Port Name (WWPN) pools
– World Wide Node/Port Name (WWxN) pools
IP identity pools contain IP addresses, which are 32-bit decimal addresses that are assigned to interfaces. In a Cisco UCS domain, IP pools are typically used to assign one or more management IP addresses to each server’s Cisco Integrated Management Controller (IMC).
UUID identity pools contain Open Software Foundation 128-bit addresses. These addresses, known as UUIDs, contain a prefix and a suffix. The prefix identifies the unique UCS domain. The suffix is assigned sequentially and can represent the domain ID and host ID. UUIDs are typically used to assign software licenses to a given device.
The WWNN identity pool is a single pool for an entire Cisco UCS domain. WWNNs are 64-bit globally unique identifiers that specify a given Fibre Channel (FC) node. These identifiers are typically used in storage area network (SAN) routing.
Similar to the WWNN identity pool, the WWPN identity pool contains globally unique 64-bit identifiers. However, WWPNs represent a specific FC port, not an entire node.
WWxN identity pools contain a mix of WWNNs and WWPNs. WWxN pools can be used in any place in Cisco UCS Manager that can use WWNN pools and WWPN pools. -
Which of the following is true of the default VRF on a Cisco router?
- It includes only the mgmt 0 interface.
- No routing protocols are allowed to run there.
- It is similar to a router’s global routing table.
- It is used only for management.
Explanation:
A Cisco router’s default virtual routing and forwarding (VRF) instance is similar to a router’s global routing table. The default VRF includes all Layer 3 interfaces until you assign those interfaces to another VRF. Similarly, the default VRF runs any routing protocols that are configured unless those routing protocols are assigned to another VRF. All show and exec commands that are issued in the default VRF apply to the default routing context.
VRFs are used to logically separate Open Systems Interconnection (OSI) networking model Layer 3 networks. Therefore, it is possible to have overlapping Internet Protocol version 4 (IPv4) or Internet Protocol version 6 (IPv6) addresses in environments that contain multiple tenants. However, an interface that has been assigned to a given VRF cannot be simultaneously assigned to another VRF. The address space, routing process, and forwarding table that are used within a VRF are local to that VRF. By default, a Cisco router is configured with two VRFs: the management VRF and the default VRF.
The management VRF, not the default VRF, is used only for management. No routing protocols are allowed to run in the management VRF. All routing is static. The management VRF includes only the mgmt 0 interface, which cannot be assigned to any other VRF. However, the mgmt 0 interface is shared among virtual device contexts (VDCs). -
You are configuring a service profile for a Cisco UCS server that contains two physical HBAs and no NICs.
How many vNICs can be configured for this server?
- four
- eight
- six
- none
- two
Explanation:
No virtual network interface cards (vNICs) can be configured for a Cisco Unified Computing System (UCS) server that contains two physical host bus adapters (HBAs) and no network interface cards (NICs). Cisco UCS server can be configured with the number of vNICs that corresponds to available physical NICs on the server. Similarly, a Cisco UCS can be configured with the number of virtual HBAs (vHBAs) that corresponds to available physical HBAs on the physical adapters that are installed in the device. In this scenario, it is possible to configure the server with two VHBAs.
It is not possible to configure two vNICs for the Cisco UCS server in this scenario. In order to configure two NICs, the server would need to be configured with one or more adapters that each contains one or more physical NICs. For example, a Cisco converged network adapter typically contains two physical ports. Therefore, a Cisco UCS server that is configured with a single converged network adapter could be configured with two NICs. A converged network adapter is a single unit that combines a physical HBA and a physical Ethernet NIC. A Cisco converged network adapter typically contains two of these types of ports.
It is not possible to configure four vNICs for the Cisco UCS server in this scenario. To configure four vNICs, the UCS server would need to be configured with adapters that contain up to four physical NICs.
It is not possible to configure eight VNICs for the Cisco UCS server in this scenario. To configure eight vNICs, the UCS server would need to be configured with adapters that contain up to eight physical NICs. -
Which of the following Cisco UCS servers is most likely to require a special version of Cisco UCS Manager?
- C-Series servers
- B-Series servers
- E-Series servers
- UCS Mini servers
Explanation:
Of the available options, Cisco Unified Computing System (UCS) Mini servers are most likely to require a special version of Cisco UCS Manager. Cisco UCS Mini servers are a compact integration of a Cisco UCS 5108 blade chassis, Cisco UCS 6324 Fabric Interconnects, and Cisco UCS Manager. Unlike other Cisco UCS servers, the UCS Mini server requires a special version of Cisco UCS Manager for management. It is possible to connect Cisco UCS C-Series servers to Cisco UCS Mini servers in order to expand their abilities.
Cisco UCS C-Series servers do not require a UCS fabric, nor do they require Cisco UCS Manager. Cisco UCS C-Series servers are rack-mount standalone servers that can operate either with or without integration with Cisco UCS Manager. For administrators who are more familiar with traditional Ethernet networks than UCS Fabric Interconnect, C-Series servers will most likely be simpler to deploy and feel more familiar than other Cisco UCS server products.
Cisco UCS B-Series servers require a UCS fabric and use a standard version of Cisco UCS Manager. Cisco UCS B-Series servers are blade servers that are installed in a UCS blade chassis. These blade servers can connect only to Cisco UCS Fabric Interconnect, not directly to a traditional Ethernet network. Blade servers in a chassis are typically hot-swappable, unlike the components of a rack-mount server. Therefore, blade server configurations are less likely to result in prolonged downtime if hardware fails.
Cisco UCS E-Series servers are blade servers that can use a standard version of Cisco UCS Manager. However, Cisco UCS E-Series servers have similar capabilities to the standalone C-Series servers and do not require connectivity to a UCS fabric. In a small office environment, Cisco UCS E-Series servers are capable of providing the network connectivity and capabilities of a C-Series server along with the availability of B-Series servers. -
Which of the following statements about VE ports is not true?
- They connect to peripheral devices.
- They enable multihop FCoE topologies.
- They can be configured with multiple vSANs on a single port.
- They are enabled in trunk mode by default.
Explanation:
Virtual edge (VE) ports do not connect to peripheral devices. Virtual fabric (VF) ports, on the other hand, are Fibre Channel over Ethernet (FCoE) ports that typically connect to virtual node (VN) ports. VN ports are ports in peripheral devices, such as end hosts or disks. VE ports, on the other hand, are used to connect FCoE inter-switch links (ISLs). In other words, VE ports connect to other VE ports.
Because VE ports connect FCoE ISLs, VE ports enable multihop FCoE topologies. An FCoE hop is a connection from one domain ID to another domain ID. Therefore, a multihop FCoE switch is aware of multiple domains and can track and forward between them.
VE ports are enabled in trunk mode by default. In addition, VE ports can be configured with multiple virtual storage area networks (vSANs) on a single port. In order to configure multiple vSANs on a single VE port, you must configure each corresponding FCoE virtual local area network (VLAN) on the Ethernet interface to which the VE port is bound. -
Which of the following statements is not true regarding the IaaS service model?
- The consumer has control over the physical infrastructure in the cloud.
- The consumer has control over the allocation of processing, memory, storage, and network resources within the cloud.
- The consumer has control over development tools or APIs in the cloud running on the physical infrastructure in the cloud.
- The consumer has control over the configuration of the OS running on the physical infrastructure in the cloud.
Explanation:
In the Infrastructure as a Service (IaaS) service model, the consumer does not have control over the physical infrastructure in the cloud. The National Institute of Standards and Technology (NIST) defines three service models in its definition of cloud computing: Software as a Service (SaaS), IaaS, and Platform as a Service (PaaS). Cloud computing offers several benefits over traditional physical infrastructure and software licensing, including a reduction in downtime and administrative overhead.
The SaaS service model enables its consumer to access applications running in the cloud infrastructure but does not enable the consumer to manage the cloud infrastructure or the configuration of the provided applications. A company that licenses a service provider’s office suite and email service that is delivered to end users through a web browser is using SaaS. SaaS providers use an Internet-enabled licensing function, a streaming service, or a web application to provide end users with software that they might otherwise install and activate locally. Web-based email clients, such as Gmail and Outlook.com, are examples of SaaS.
The PaaS service model provides its consumer with a bit more freedom than the SaaS model by enabling the consumer to install and possibly configure provider-supported applications in the cloud infrastructure. A company that uses a service provider’s infrastructure, programming tools, and programming languages to develop and serve cloud-based applications is using PaaS. PaaS enables a consumer to use the service provider’s development tools or Application Programming Interface (API) to develop and deploy specific cloud-based applications or services. Another example of PaaS might be using a third party’s MySQL database and Apache services to build a cloud-based customer relationship management (CRM) platform.
The IaaS service model provides the greatest degree of freedom by enabling its consumer to provision processing, memory, storage, and network resources within the cloud infrastructure. The IaaS service model also enables its consumer to install applications, including operating systems (OSs) and custom applications. However, with IaaS, the cloud infrastructure remains in control of the service provider. A company that hires a service provider to deliver cloud-based processing and storage that will house multiple physical or virtual hosts configured in a variety of ways is using IaaS. For example, a company that wanted to establish a web server farm by configuring multiple Linux Apache MySQL PHP (LAMP) servers could save hardware costs by virtualizing the farm and using a provider’s cloud service to deliver the physical infrastructure and bandwidth for the virtual farm. Control over the OS, software, and server configuration would remain the responsibility of the organization, whereas the physical infrastructure and bandwidth would be the responsibility of the service provider. -
Which of the following are true about Cisco UCS Director workflow templates? (Choose three.)
- They contain task names, a workflow structure, and input names.
- They can be executed like normal workflows.
- They can be used to schedule workflows.
- They can be used to instantiate new workflows.
- Some templates are predefined in the system.
Explanation:
Cisco Unified Computing System (UCS) Director workflow templates can be used to instantiate new workflows. Workflow templates are used as blueprints to create new workflows. In addition, you can create a new workflow and then export that workflow as a template in order to create other workflows built around the same tasks.
Cisco UCS Director workflow templates contain task names, a workflow structure, and input names. Task names are literally the string names of the tasks that are to be executed in the workflow. The tasks themselves are already built into the system in which the workflow template is defined. A workflow structure defines how the tasks are connected in the series. Input names define the details about the variables that are used to store the workflow’s user input.
Some Cisco UCS Director workflow templates are predefined in the system. Predefined workflow templates can be accessed by using the Workflow Templates tab in Cisco UCS Director Orchestration.
Cisco UCS Director workflow templates cannot be executed like normal workflows. In addition, workflow templates cannot be used to schedule workflows. Cisco UCS Director is a resource automation and orchestration tool. UCS Director workflows are task sequences that accept user input and then automatically perform a series of tasks to complete a complex operation. Workflow templates simplify the creation of workflows based on a set of predefined tasks and therefore cannot themselves be executed. Workflows can be executed in several ways, including by using service requests, the Execute Now action, a virtual machine (VM) Action policy, a trigger, a schedule, or the rollback feature. -
Which of the following is least likely to be used to construct or access a cloud-based API?
- a SOAP API
- GraphQL
- the Java API
- a REST API
Explanation:
Of the available choices, the Java Application Programming Interface (API) is least likely to be used to construct or access a cloud-based API. The Java API is typically accessed by Java applications that are running in the Java virtual machine (VM), which is the Java component that executes compiled Java programs. The Java API is a collection of Java classes that developers can use for data collection or to build interfaces. Open APIs can be used to enable services such as billing automation and centralized management of cloud infrastructure.
Representational state transfer (REST) is an API architecture that uses Hypertext Transfer Protocol (HTTP) or HTTP Secure (HTTPS) to enable external resources to access and make use of programmatic methods that are exposed by the API. Therefore, it is possible to construct or access a cloud-based API from REST. For example, a web application that retrieves user product reviews from an online marketplace for display on third-party websites might obtain those reviews by using methods provided in an API that is developed and maintained by that marketplace. REST APIs can return data in Extensible Markup Language (XML) format or in JavaScript Object Notation (JSON) format.
Simple Object Access Protocol (SOAP) APIs can be used to construct or access cloud-based APIs. SOAP is an older API messaging protocol that uses HTTP and XML to enable communication between devices. SOAP APIs are typically more resource-intensive than REST APIs and, therefore, slower. Unlike REST APIs, SOAP APIs do not return JSON-formatted output.
Graph Query Language (GraphQL) can be used to access cloud-based APIs. GraphQL is an API query language and a runtime that is intended to lower the burden of making multiple API calls to obtain a single set of data. For example, data that requires three or four HTTP GET requests when constructed from a standard REST API might take only one request when using GraphQL. Similar to REST API, GraphQL output is in JSON format. Although GraphQL can use HTTP or HTTPS, it is not limited to those protocols. -
You connect an FC link to unified port 1/31 on a new Cisco Nexus 5548UP switch and receive the following error messages:
ERROR: Ethernet range starts from first port of the module ERROR: FC range should end on last port of the module
- The link you connected should have been to unified port 1/32.
- The link you connected was actually Ethernet, not FC.
- The link you connected should have been to unified port 1/17.
- The link you connected was FC but should have been Ethernet.
- The link you connected should have been to unified port 1/1.
Explanation:
Of the available choices, it is most likely that the link you connected should have been to unified port 1/32 on the Cisco Nexus 5548UP switch in this scenario. Unified ports are ports that can be either Ethernet or Fibre Channel (FC) ports. Cisco Nexus switches that support unified ports require that Ethernet links be connected from the beginning of the port range forward and that FC links be connected from the end of the port range backward. Slot 1 of a Cisco Nexus 5548UP switch contains 32 unified ports. Therefore, in this scenario, the FC link on the new switch would need to be connected to port 1/32 before any other FC links could be connected in the FC range.
As a further example, if you were to connect a single Ethernet link and a single FC link to slot 1 of a Cisco Nexus 5548UP switch that has no other links connected, you must connect the Ethernet link to port 1/1 and the FC link to port 1/32. If you were to then connect an additional Ethernet link to slot 1, that link must be connected to port 1/2. If you were to connect an additional FC link to slot 1, that link must be connected to port 1/31. Link additions should continue in that way until the Ethernet range ends where the FC range begins and no more ports are available in the slot.
The link in this scenario should not have been connected to unified port 1/17. Unified port 1/17 on a Cisco Nexus 5548UP switch falls in the middle of the 32-port range of slot 1. This port could be the end of an Ethernet port range if it were preceded by 16 other Ethernet links or the beginning of an FC port range if it were succeeded by 15 other FC links.
The link in this scenario should not have been connected to unified port 1/1. In addition, there is nothing in this scenario to indicate that the link was or should have been an Ethernet link. -
A UCS administrator connects Fabric Interconnect A’s Layer 1 and Layer 2 high availability ports to Fabric Interconnect B’s Layer 1 and Layer 2 high availability ports. In addition, the administrator connects each Fabric Interconnect’s Mgmt 0 port to a switch. No FC connections have been made between Fabric Interconnect A and Fabric Interconnect B.
Which of the following statements about the Fabric Interconnect cluster is true?
- Failover will not work, because no FC connections have been made.
- Failover will not work, because no Ethernet connections have been made.
- Failover will work, but there will be no link-level redundancy.
- Failover will work, and link-level redundancy is available.
Explanation:
Cisco Unified Computing System (UCS) Fabric Interconnect failover will work, and link-level redundancy is available. In this scenario, the UCS administrator connects two Cisco Fabric Interconnects, A and B, together by using each device’s Layer 1 and Layer 2 high availability ports. This configuration is known as a Fabric Interconnect cluster.
Each Fabric Interconnect in a cluster is capable of monitoring the status of the Fabric Interconnect to which it is connected. If Fabric Interconnect A fails, Fabric Interconnect B can take over the duties of Fabric Interconnect A. If Fabric Interconnect B fails, Fabric Interconnect A can take over the duties of Fabric Interconnect B.
Link-level redundancy is available in this scenario because the Mgmt 0 port on each Fabric Interconnect has been connected to a switch. In a Fabric Interconnect cluster, it is possible to connect only one device’s Mgmt 0 port to a switch to enable management of the entire cluster. However, the connection of both Mgmt 0 ports ensures redundancy in case of failure of one of the devices.
Failover will work even though there are no Fibre Channel (FC) connections between the devices in this scenario. A Fabric Interconnect cluster requires that no FC connections exist between the cluster members. Therefore, connecting the two Fabric Interconnects by using FC connections is more likely to prevent failover than to facilitate it.
Ethernet connections have been made in this scenario. The Layer 1 and Layer 2 high availability ports on the first Fabric Interconnect are connected to the Layer 1 and Layer 2 high availability ports on the second Fabric Interconnect by using Ethernet cables. The Layer 1 high availability port on the first device should connect to the Layer 1 high availability port on the second device. Likewise, the Layer 2 high availability port on the first device should connect to the Layer 2 high availability port on the second device.