CCSK Module 2 Unit 2 Answers – Introduction to Infrastructure Security for Cloud Computing Knowledge Check Quiz Full 100% 2023 2024
This is CCSK Module 2 Unit 2 Answers – Introduction to Infrastructure Security for Cloud Computing Knowledge Check Quiz. Our expert team has verified questions and answers with clear explanations to get a full score of 100%. You can review all these questions before taking the exam.
-
Cloud infrastructure security does not include the virtualization components:
- True
- False
-
Answers Explanation & Hint:
Cloud infrastructure security does include virtualization components. Virtualization is a fundamental technology in cloud computing that allows for the creation and management of virtual machines (VMs) or containers on a physical server. These virtualization components are critical for delivering and managing cloud services. Securing the virtualization layer is crucial to ensuring the overall security of the cloud infrastructure.
The virtualization layer can be vulnerable to various security risks, such as hypervisor vulnerabilities, VM escape attacks, and resource exploitation. Proper security measures and best practices need to be implemented at the virtualization layer to protect against these threats and ensure the isolation and integrity of virtual machines and containers running on the cloud infrastructure.
-
Which of the following resource pools is not associated with IaaS:
- Network
- Middleware
- Compute
- Storage
-
Answers Explanation & Hint:
The resource pool that is not associated with IaaS (Infrastructure as a Service) is “Middleware.”
In the context of cloud computing service models:
- IaaS (Infrastructure as a Service) provides virtualized computing resources over the internet, including virtual machines, storage, and networking.
- PaaS (Platform as a Service) provides a platform and environment for developers to build, deploy, and manage applications without managing the underlying infrastructure. Middleware services are often included in PaaS offerings.
- SaaS (Software as a Service) provides software applications over the internet on a subscription basis, eliminating the need for users to manage any infrastructure or software updates.
- Storage is a resource pool that is indeed associated with IaaS, as IaaS includes providing storage services as part of its infrastructure offerings.
So, the correct answer is “Middleware.”
-
Click on the components that the cloud consumer is primarily responsible for securing.
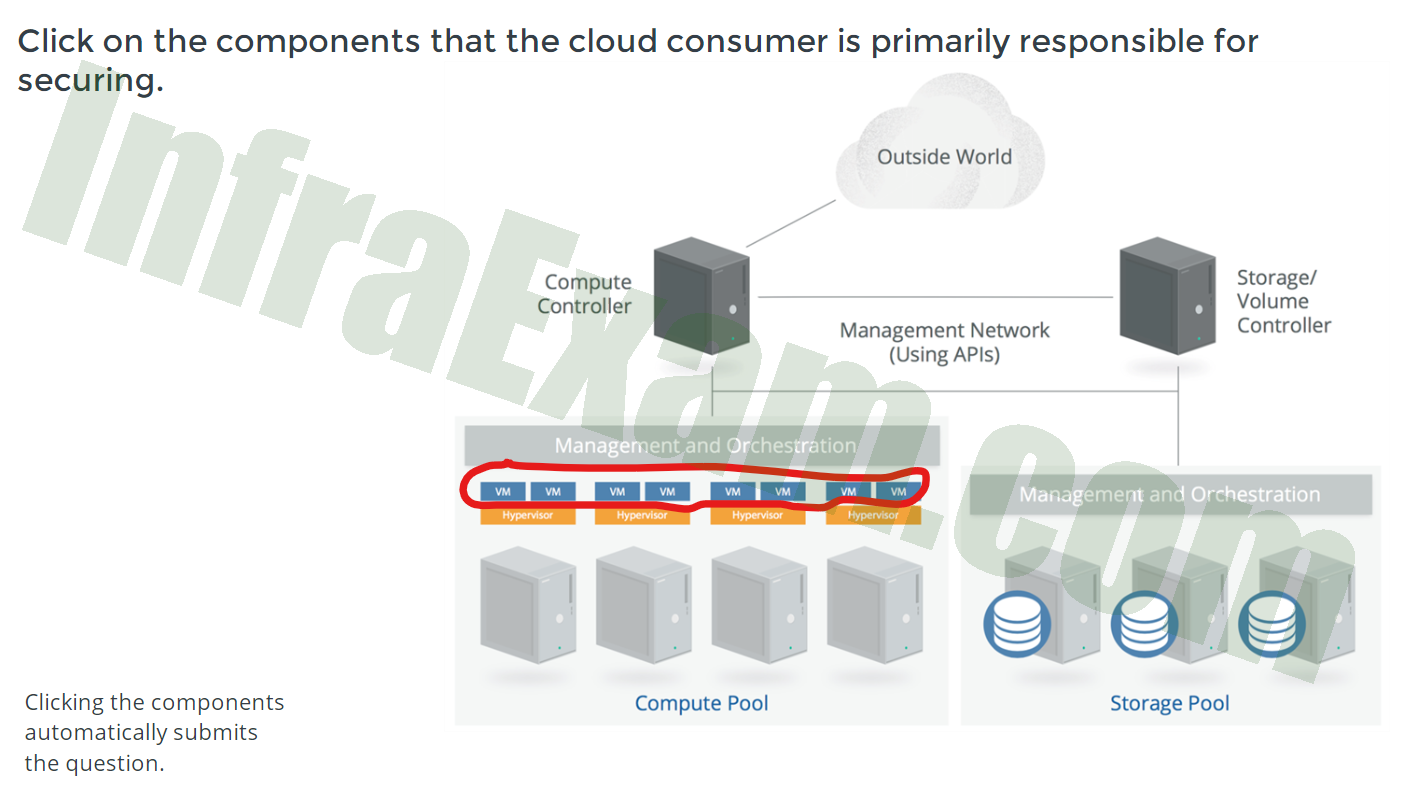
CCSK Module 2 Unit 2 Answers – Introduction to Infrastructure Security for Cloud Computing Knowledge Check Quiz 001 -
Answers Explanation & Hint:
Virtual Machines (VMs): The cloud consumer is responsible for securing the virtual machines running on the private cloud infrastructure. This includes applying security patches to the VM operating systems, configuring firewalls, implementing access controls, and ensuring the overall security of the VMs.
-
-
Which of the following are typically in the underlying infrastructure of a cloud? (click all that apply)
- Database
- Hypervisors
- API server
- Identity service
- Message queue
-
Answers Explanation & Hint:
- Database: Databases are commonly found in cloud environments, especially in the context of cloud-based applications and services. While they are not part of the core underlying infrastructure of the cloud, they are hosted on the cloud platform and are integral components of many cloud-based applications.
- Hypervisors: Hypervisors are essential components of cloud infrastructure, particularly in virtualized environments like IaaS (Infrastructure as a Service). They allow for the creation and management of virtual machines, enabling efficient resource allocation and isolation.
- API server: API servers are crucial in cloud environments. They provide a way for different components and services within the cloud to communicate and interact with each other through standardized APIs.
- Identity service: Identity services, such as an Identity and Access Management (IAM) system, are commonly part of cloud infrastructure. They manage user identities, authentication, and access controls for various cloud services and resources.
- Message queue: Message queues are used in cloud environments to facilitate communication and data exchange between different services and components asynchronously.
-
Why is hardening infrastructure components so important?
- Clouds are sometimes based on common components that may contain vulnerabilities.
- All security is important
- Infrastructure components are most likely to be exposed to cloud consumers
- This prevents the cloud provider from accessing cloud consumer data.
-
Answers Explanation & Hint:
The statement “Clouds are sometimes based on common components that may contain vulnerabilities” is a valid reason why hardening infrastructure components is so important in cloud environments.
Cloud providers often use widely-used and standardized components, which may have known vulnerabilities or weaknesses. Since these components are shared across multiple cloud customers, it becomes even more critical to harden them to reduce the risk of potential security breaches and attacks. By hardening the infrastructure components, cloud providers aim to improve the overall security posture and protect their customers’ data and applications from potential threats and exploits.