CCSK Module 2 Unit 4 Answers – Cloud Network Security Knowledge Check Quiz Full 100% 2023 2024
This is CCSK Module 2 Unit 4 Answers – Cloud Network Security Knowledge Check Quiz. Our expert team has verified questions and answers with clear explanations to get a full score of 100%. You can review all these questions before taking the exam.
-
Which of the following is the most effective security barrier to contain blast radius?
- Virtual subnet (with or without ACLs)
- Virtual network
- Cloud account/project/subscription
- Security group
-
Answers Explanation & Hint:
The most effective security barrier to contain blast radius among the options provided is Cloud account/project/subscription.
Using separate cloud accounts, projects, or subscriptions for different parts of an organization or different services can provide strong isolation between them. If one account, project, or subscription is compromised, it helps prevent the attacker from easily moving laterally to other accounts or projects, thus effectively containing the blast radius.
By using separate accounts/projects/subscriptions, you can enforce different access controls, resource policies, and security configurations tailored to the specific needs of each environment. This isolation enhances security and reduces the impact of a security breach or failure to a smaller portion of the overall cloud infrastructure.
Again, I apologize for the oversight, and thank you for pointing out the correct answer. Cloud account/project/subscription is indeed the most effective security barrier to contain blast radius in cloud deployments.
-
How does a virtual network affect network visibility?
- Virtual machines on the same physical host don’t use the physical network
- Virtual networks block packet capture for better isolation
- An SDN can provide more visibility than a physical network
- Virtual networks always encrypt traffic and break packet capturing
-
Answers Explanation & Hint:
The correct statement is:
Virtual machines on the same physical host don’t use the physical network.
This statement is true. When virtual machines (VMs) communicate with each other on the same physical host within a virtualized environment, the traffic often stays within the virtualization layer and does not traverse the physical network infrastructure. Instead, the communication occurs through the hypervisor or virtualization software, which manages the traffic between VMs on the same host.
As a result, traditional network monitoring tools that capture traffic on physical network devices may not be able to observe this intra-host communication. This can reduce network visibility for such local virtual machine communication. However, modern virtualization platforms often provide specialized tools and APIs that enable administrators to gain visibility into virtual network traffic on the same physical host. These tools can help monitor, capture, and analyze the traffic between VMs, even within the same physical host.
-
Place the following network security tools in the preferred order in most cloud deployments, from 1 (most preferred) to 4.
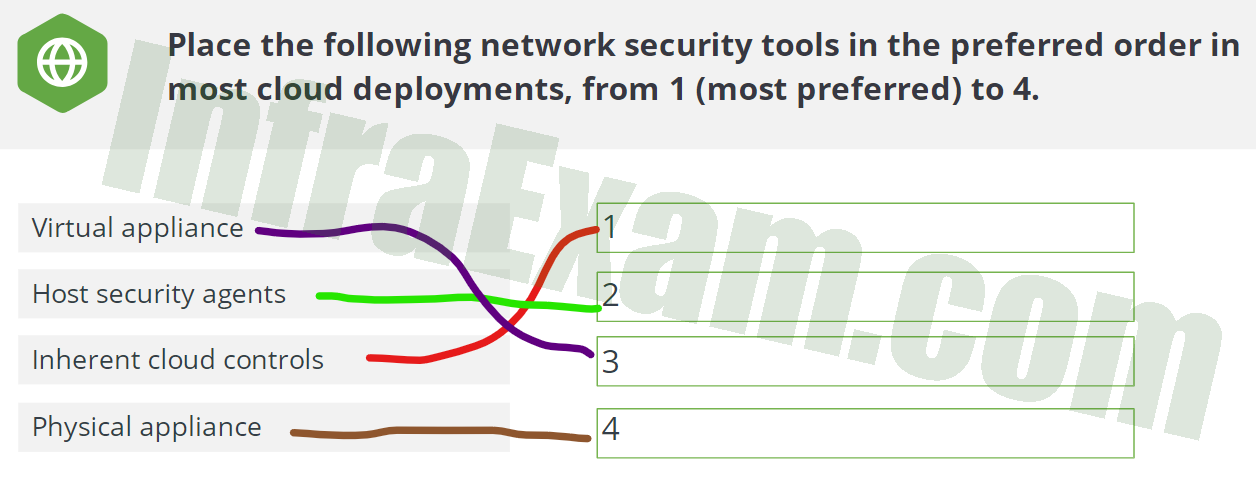
CCSK Module 2 Unit 4 Answers – Cloud Network Security Knowledge Check Quiz 001 -
Answers Explanation & Hint:
In most cloud deployments, the preferred order for network security tools would be as follows:
- Inherent cloud controls: These are security features and controls provided by the cloud service provider itself. They are often integrated into the cloud infrastructure and offer a good baseline level of security. As they are native to the cloud environment, they are usually the most seamless and easy to manage.
- Host Security agents: These are security software installed on individual cloud instances or virtual machines to protect them from various threats. They provide an additional layer of security, especially for workloads running on virtual machines.
- Virtual appliance: A virtual appliance is a software-based security tool deployed on a virtual machine. While it offers more flexibility compared to a physical appliance, it might have a slightly higher overhead due to the virtualization layer.
- Physical appliance: This refers to hardware-based security appliances that are often deployed on-premises and may not be as well-suited for cloud deployments. While they can still be effective, they may require more effort to integrate with cloud environments and might not be as scalable or flexible as cloud-native solutions.
Remember that the specific requirements of each cloud deployment can vary, and the order might be adjusted accordingly. However, in general, starting with inherent cloud controls and then complementing them with other security measures is a common approach.
-
-
What is the purpose of a bastion network/transit VPC?
- To better support multiple virtual networks and accounts in hybrid scenarios
- To better lock down a hybrid cloud
- To create a cloud DMZ
- To improve internal routing and IP address space availability
-
Answers Explanation & Hint:
The purpose of a bastion network or transit VPC (Virtual Private Cloud) is:
To better support multiple virtual networks and accounts in hybrid scenarios
A bastion network or transit VPC acts as an intermediary or hub for connecting multiple virtual networks or cloud accounts in a hybrid cloud architecture. It serves as a centralized point for managing and routing traffic between different network segments or cloud environments, providing connectivity and communication between them.
Here’s how it achieves the purpose:
- Centralized Connectivity: In a hybrid cloud setup, you may have on-premises data centers and multiple cloud environments (e.g., AWS, Azure, GCP) with different virtual networks and accounts. The bastion network or transit VPC acts as a central hub that connects these networks and cloud accounts.
- Routing and Traffic Management: The bastion network or transit VPC typically implements various routing and traffic management strategies to ensure that communication between different virtual networks or cloud accounts is efficient and secure.
- Security and Isolation: By centralizing connectivity, the bastion network can also enhance security by implementing security policies and access controls at the hub level. This allows for better control and monitoring of traffic flowing between different environments.
- Simplification and Scalability: A bastion network or transit VPC can simplify the network architecture by reducing the number of direct connections between individual networks or cloud accounts. It also provides a scalable solution as new networks or accounts can be easily added to the hub without requiring complex point-to-point connections.
In summary, a bastion network or transit VPC is a key component in hybrid cloud architectures, allowing organizations to create a unified and interconnected network environment, better supporting multiple virtual networks and accounts in hybrid scenarios. It enhances the overall manageability, security, and scalability of network communications across hybrid cloud deployments.
-
Which of the following is primarily a responsibility of the cloud provider?
- Configuring security groups
- Securing the underlying virtualization technology
- Correct configuration in the management plane
- Designing subnets, virtual networks, and ACLs2
-
Answers Explanation & Hint:
The primarily responsibility of the cloud provider among the options provided is:
Securing the underlying virtualization technology
Explanation:
- Configuring security groups: Configuring security groups is a shared responsibility between the cloud provider and the customer. The cloud provider typically offers security group features, but the customer is responsible for setting up and defining the rules within those security groups to control network traffic to their resources.
- Securing the underlying virtualization technology: This is a core responsibility of the cloud provider. The cloud provider is responsible for securing the underlying infrastructure, including the virtualization technology that powers the cloud platform. This involves ensuring the hypervisors, virtual machines, and other components of the virtualization layer are protected against vulnerabilities and unauthorized access.
- Correct configuration in the management plane: The correct configuration in the management plane is a shared responsibility between the cloud provider and the customer. The cloud provider ensures that their management tools and interfaces are secure and properly configured, while the customer is responsible for using those tools securely and configuring them appropriately for their specific needs.
- Designing subnets, virtual networks, and ACLs: Designing subnets, virtual networks, and Access Control Lists (ACLs) is a shared responsibility. The cloud provider typically provides the necessary tools and interfaces for creating and managing these network components, while the customer is responsible for designing them to suit their application’s requirements and security needs.
In summary, securing the underlying virtualization technology is a core responsibility of the cloud provider, ensuring the foundational infrastructure that runs the cloud platform is secure and protected. However, other aspects mentioned in the options are shared responsibilities between the cloud provider and the customer, where each party has their respective role in ensuring the overall security of the cloud environment.
-
Of the following, which is the most important use case for the Sofware Defined Perimeter?
- To secure hybrid networks
- To encrypt SDN traffic
- For federated network identity
- To improve and secure remote access
-
Answers Explanation & Hint:
The most important use case for the Software Defined Perimeter (SDP) among the options provided is:
To improve and secure remote access
Explanation:
The Software Defined Perimeter (SDP) is a security architecture that focuses on dynamically creating “invisible” perimeters around individual devices or users rather than the traditional network-based perimeters. It ensures that only authorized users and devices have access to specific applications or resources, regardless of their location.
The primary use case of SDP revolves around improving and securing remote access to sensitive resources. Here’s why:
- Secure Remote Access: SDP provides a robust and secure method for remote users to access critical applications and resources. It offers a Zero Trust approach, where users are not trusted by default, and their identity and device posture are verified before granting access.
- Dynamic Perimeter: With SDP, access is dynamically granted to specific applications based on user identity, device health, and other contextual information. This eliminates the traditional static network perimeter and reduces the attack surface by limiting exposure to authorized users only.
- Protection Against Network Attacks: SDP helps protect against various network-based attacks, such as Distributed Denial of Service (DDoS) attacks, by effectively hiding resources from unauthorized users. Attackers cannot target what they cannot see.
- Safeguarding Sensitive Data: By controlling access to resources at a granular level, SDP helps safeguard sensitive data and intellectual property from unauthorized access or data breaches.
While SDP can be beneficial in other scenarios, such as securing hybrid networks and implementing federated network identity, its most important and impactful use case is its ability to improve and secure remote access. In an era where remote work and mobile access are prevalent, SDP helps organizations maintain a strong security posture while enabling secure and seamless remote access for employees and authorized users.