CAS-003 : CompTIA Advanced Security Practitioner (CASP+) CAS-003 : Part 17
-
When implementing a penetration testing program, the Chief Information Security Officer (CISO) designates different organizational groups within the organization as having different responsibilities, attack vectors, and rules of engagement. First, the CISO designates a team to operate from within the corporate environment. This team is commonly referred to as:
- the blue team.
- the white team.
- the operations team.
- the red team.
- the development team.
-
An enterprise’s Chief Technology Officer (CTO) and Chief Information Security Officer (CISO) are meeting to discuss ongoing capacity and resource planning issues. The enterprise has experienced rapid, massive growth over the last 12 months, and the technology department is stretched thin for resources. A new accounting service is required to support the enterprise’s growth, but the only available compute resources that meet the accounting service requirements are on the virtual platform, which is hosting the enterprise’s website.
Which of the following should the CISO be MOST concerned about?
- Poor capacity planning could cause an oversubscribed host, leading to poor performance on the company’s website.
- A security vulnerability that is exploited on the website could expose the accounting service.
- Transferring as many services as possible to a CSP could free up resources.
- The CTO does not have the budget available to purchase required resources and manage growth.
-
A regional transportation and logistics company recently hired its first Chief Information Security Officer (CISO). The CISO’s first project after onboarding involved performing a vulnerability assessment against the company’s public facing network. The completed scan found a legacy collaboration platform application with a critically rated vulnerability. While discussing this issue with the line of business, the CISO learns the vulnerable application cannot be updated without the company incurring significant losses due to downtime or new software purchases.
Which of the following BEST addresses these concerns?
- The company should plan future maintenance windows such legacy application can be updated as needed.
- The CISO must accept the risk of the legacy application, as the cost of replacing the application greatly exceeds the risk to the company.
- The company should implement a WAF in front of the vulnerable application to filter out any traffic attempting to exploit the vulnerability.
- The company should build a parallel system and perform a cutover from the old application to the new application, with less downtime than an upgrade.
-
Ann, a retiring employee, cleaned out her desk. The next day, Ann’s manager notices company equipment that was supposed to remain at her desk is now missing.
Which of the following would reduce the risk of this occurring in the future?
- Regular auditing of the clean desk policy
- Employee awareness and training policies
- Proper employee separation procedures
- Implementation of an acceptable use policy
-
A security analyst for a bank received an anonymous tip on the external banking website showing the following:
Protocols supported
– TLS 1.0
– SSL 3
– SSL 2
Cipher suites supported
– TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA-ECDH p256r1
– TLS_DHE_RSA_WITH_AES_256_CBC_SHA-DH 1024bit
– TLS_RSA_WITH_RC4_128_SHA
TLS_FALLBACK_SCSV non supported
POODLE
Weak PFS
OCSP stapling supportedWhich of the following should the analyst use to reproduce these findings comprehensively?
- Query the OCSP responder and review revocation information for the user certificates.
- Review CA-supported ciphers and inspect the connection through an HTTP proxy.
- Perform a POODLE (SSLv3) attack using an exploitations framework and inspect the output.
- Inspect the server certificate and simulate SSL/TLS handshakes for enumeration.
-
A company is moving all of its web applications to an SSO configuration using SAML. Some employees report that when signing in to an application, they get an error message on the login screen after entering their username and password, and are denied access. When they access another system that has been converted to the new SSO authentication model, they are able to authenticate successfully without being prompted for login.
Which of the following is MOST likely the issue?
- The employees are using an old link that does not use the new SAML authentication.
- The XACML for the problematic application is not in the proper format or may be using an older schema.
- The web services methods and properties are missing the required WSDL to complete the request after displaying the login page.
- A threat actor is implementing an MITM attack to harvest credentials.
-
A penetration tester is trying to gain access to a remote system. The tester is able to see the secure login page and knows one user account and email address, but has not yet discovered a password.
Which of the following would be the EASIEST method of obtaining a password for the known account?
- Man-in-the-middle
- Reverse engineering
- Social engineering
- Hash cracking
-
A technician is reviewing the following log:
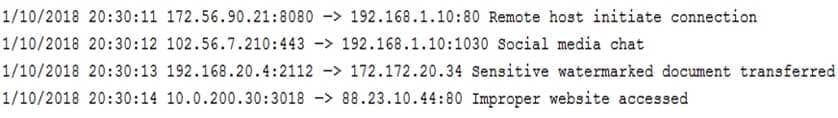
CAS-003 Part 17 Q08 090 Which of the following tools should the organization implement to reduce the highest risk identified in this log?
- NIPS
- DLP
- NGFW
- SIEM
-
A Chief Information Security Officer (CISO) is creating a security committee involving multiple business units of the corporation.
Which of the following is the BEST justification to ensure collaboration across business units?
- A risk to one business unit is a risk avoided by all business units, and liberal BYOD policies create new and unexpected avenues for attackers to exploit enterprises.
- A single point of coordination is required to ensure cybersecurity issues are addressed in protected, compartmentalized groups.
- Without business unit collaboration, risks introduced by one unit that affect another unit may go without compensating controls.
- The CISO is uniquely positioned to control the flow of vulnerability information between business units.
-
Due to a recent acquisition, the security team must find a way to secure several legacy applications. During a review of the applications, the following issues are documented:
– The applications are considered mission-critical.
– The applications are written in code languages not currently supported by the development staff.
– Security updates and patches will not be made available for the applications.
– Username and passwords do not meet corporate standards.
– The data contained within the applications includes both PII and PHI.
– The applications communicate using TLS 1.0.
– Only internal users access the applications.Which of the following should be utilized to reduce the risk associated with these applications and their current architecture?
- Update the company policies to reflect the current state of the applications so they are not out of compliance.
- Create a group policy to enforce password complexity and username requirements.
- Use network segmentation to isolate the applications and control access.
- Move the applications to virtual servers that meet the password and account standards.
-
A new security policy states all wireless and wired authentication must include the use of certificates when connecting to internal resources within the enterprise LAN by all employees.
Which of the following should be configured to comply with the new security policy? (Choose two.)
- SSO
- New pre-shared key
- 802.1X
- OAuth
- Push-based authentication
- PKI
-
A security consultant was hired to audit a company’s password are account policy. The company implements the following controls:
– Minimum password length: 16
– Maximum password age: 0
– Minimum password age: 0
– Password complexity: disabled
– Store passwords in plain text: disabled
– Failed attempts lockout: 3
– Lockout timeout: 1 hourThe password database uses salted hashes and PBKDF2. Which of the following is MOST likely to yield the greatest number of plain text passwords in the shortest amount of time?
- Offline hybrid dictionary attack
- Offline brute-force attack
- Online hybrid dictionary password spraying attack
- Rainbow table attack
- Online brute-force attack
- Pass-the-hash attack
-
As part of the asset management life cycle, a company engages a certified equipment disposal vendor to appropriately recycle and destroy company assets that are no longer in use. As part of the company’s vendor due diligence, which of the following would be MOST important to obtain from the vendor?
- A copy of the vendor’s information security policies.
- A copy of the current audit reports and certifications held by the vendor.
- A signed NDA that covers all the data contained on the corporate systems.
- A copy of the procedures used to demonstrate compliance with certification requirements.
-
Following a complete outage of the electronic medical record system for more than 18 hours, the hospital’s Chief Executive Officer (CEO) has requested that the Chief Information Security Officer (CISO) perform an investigation into the possibility of a disgruntled employee causing the outage maliciously. To begin the investigation, the CISO pulls all event logs and device configurations from the time of the outage. The CISO immediately notices the configuration of a top-of-rack switch from one day prior to the outage does not match the configuration that was in place at the time of the outage. However, none of the event logs show who changed the switch configuration, and seven people have the ability to change it. Because of this, the investigation is inconclusive.
Which of the following processes should be implemented to ensure this information is available for future investigations?
- Asset inventory management
- Incident response plan
- Test and evaluation
- Configuration and change management
-
A company’s user community is being adversely affected by various types of emails whose authenticity cannot be trusted. The Chief Information Security Officer (CISO) must address the problem.
Which of the following solutions would BEST support trustworthy communication solutions?
- Enabling spam filtering and DMARC.
- Using MFA when logging into email clients and the domain.
- Enforcing HTTPS everywhere so web traffic, including email, is secure.
- Enabling SPF and DKIM on company servers.
- Enforcing data classification labels before an email is sent to an outside party.
-
The audit team was only provided the physical and logical addresses of the network without any type of access credentials.
Which of the following methods should the audit team use to gain initial access during the security assessment? (Choose two.)
- Tabletop exercise
- Social engineering
- Runtime debugging
- Reconnaissance
- Code review
- Remote access tool
-
A product manager is concerned about the unintentional sharing of the company’s intellectual property through employees’ use of social media. Which of the following would BEST mitigate this risk?
- Virtual desktop environment
- Network segmentation
- Web application firewall
- Web content filter
-
An organization is evaluating options related to moving organizational assets to a cloud-based environment using an IaaS provider. One engineer has suggested connecting a second cloud environment within the organization’s existing facilities to capitalize on available datacenter space and resources. Other project team members are concerned about such a commitment of organizational assets, and ask the Chief Security Officer (CSO) for input. The CSO explains that the project team should work with the engineer to evaluate the risks associated with using the datacenter to implement:
- a hybrid cloud.
- an on-premises private cloud.
- a hosted hybrid cloud.
- a private cloud.
-
A company uses an application in its warehouse that works with several commercially available tablets and can only be accessed inside the warehouse. The support department would like the selection of tablets to be limited to three models to provide better support and ensure spares are on hand. Users often keep the tablets after they leave the department, as many of them store personal media items.
Which of the following should the security engineer recommend to meet these requirements?
- COPE with geofencing
- BYOD with containerization
- MDM with remote wipe
- CYOD with VPN
-
During a recent incident, sensitive data was disclosed and subsequently destroyed through a properly secured, cloud-based storage platform. An incident response technician is working with management to develop an after action report that conveys critical metrics regarding the incident.
Which of the following would be MOST important to senior leadership to determine the impact of the breach?
- The likely per-record cost of the breach to the organization
- The legal or regulatory exposure that exists due to the breach
- The amount of downtime required to restore the data
- The number of records compromised
Subscribe
0 Comments
Newest