CV0-002 : CompTIA Cloud+ (CV0-002) : Part 02
CV0-002 : CompTIA Cloud+ (CV0-002) : Part 02
-
A file server is being migrated from physical hardware into a private cloud. Baselining of the server shows the disks average 90% full at all times. The contents of the file server consist mostly of compressed audio files. Multiple copies of the same files are often saved in different locations on the same disk. Which of the following storage technologies is MOST likely to help minimize storage utilization when moving this server to the private cloud?
- Compression
- Thin provisioning
- Deduplication
- Tokenization
-
A cloud administrator is looking at business requirements that specify the data available at the disaster recovery site must not be more than 24 hours old. Which of the following metrics correctly relates to these requirements?
- RTO
- MTBF
- MTTR
- PRO
-
A cloud implementation engineer successfully created a new VM. However, the engineer notices the new VM is not accessible from another network. A ping test works from another VM on the same subnet. Which of the following is the MOST likely problem?
- Incorrect subnet
- Incorrect host IP address
- Incorrect VLAN
- Incorrect gateway
-
A customer wants a cloud systems administrator to adjust the backup schedule after month-end to ensure the data can be restored as fast as possible while minimizing the time needed to perform the backup. Which of the following backup types should be scheduled?
- Synthetic full
- Incremental
- Differential
- Full
-
А cloud administrator uses a script to automatically restart all the servers running in the public cloud provider environment, which hosts e-commerce applications. The administrator decides to implement the same script for a similar environment that hosts the finance applications. After verifying the script is deployed to the public cloud environment for finance, the administrator schedules a job to run at 9:00 a.m. After 9:00 a.m., the administrator receives a report from the e-commerce team that the application is experiencing outages. Which of the following should the administrator do to resolve the issue?
- Update the version of the CLI tool for the public cloud provider.
- Copy the script up to a bastion host in the environment and run it from there.
- Validate the access credentials for the cloud provider are correct.
- Debug the script and modify it to remove the flawed logic.
-
A critical new security update has been released to fix an identified zero-day vulnerability with the SSH server process. Due to its severity, all development and staging servers must have this update applied immediately. Which of the following is the FASTEST way for the administrator to apply the patch and ensure all systems are configured consistently?
- Shut down all servers and use the server provisioning tools to deploy new ones that have the latest patch applied.
- Create a master inventory list of servers that must be patched. Log in to each server and deploy the patch, making sure to check off each server on the list.
- Use the existing tooling to clone the existing servers. Update each clone with the latest patch and shut down the original system.
- Update the set of configuration management scripts to include the latest patch. Execute these scripts against a master inventory of servers.
-
A company wants to take advantage of cloud benefits while retaining control of and maintaining compliance with all its security policy obligations. Based on the non-functional requirements, which of the following should the company use?
- Hybrid cloud, as use is restricted to trusted customers
- IaaS, as the cloud provider has a minimal level of security responsibility
- PaaS, as the cloud customer has the most security responsibility
- SaaS, as the cloud provider has less security responsibility
-
An administrator is deploying a new application platform with the following resource utilization:
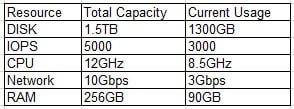
CV0-002 Part 02 Q08 013 Company policy requires that no resource utilization surpasses 80%. Which of the following resources will need to be upgraded prior to deployment?
- Disk
- IOPS
- CPU
- Network
- RAM
-
Several suspicious emails are being reported from end users. Organizational email is hosted by a SaaS provider. Upon investigation, the URL in the email links to a phishing site where users are prompted to enter their domain credentials to reset their passwords. Which of the following should the cloud administrator do to protect potential account compromise?
- Forward the email to the systems team distribution list and provide the compromised user list.
- Click on the URL link to verify the website and enter false domain credentials.
- Change the encryption key for the entire organization and lock out all users from using email until the issue is remediated.
- Notify users who received the email to reset their passwords regardless of whether they click on the URL.
-
Which of the following is the BEST way to ensure accounts in a cloud environment are disabled as soon as they no longer need to be active?
- Have the user contact the cloud systems administrator to disable the account when it is no longer needed.
- When users leave the company, ensure an account disablement request is initiated and will be fulfilled in less than four hours.
- Have accounts checked by the cloud systems administrator once per day to ensure active accounts are still valid.
- Reboot directory services servers once a day to ensure all account disablement requests are committed.
-
A cloud administrator has deployed a new all-flash storage array with deduplication and compression enabled, and moved some of the VMs into it. The goal was to achieve 4:1 storage efficiency while maintaining sub-millisecond latency. Which of the following results would BEST suit the requirements?
- Compression 1:1
Deduplication 4:1
Overall savings 4:1
Average latency 1.0ms - Compression 1.5:1
Deduplication 1.8:1
Overall savings 2.2:1
Average latency 600us - Compression 1.3:1
Deduplication 3.1:1
Overall savings 4.3:1
Average latency 900us - Compression 1.8:1
Deduplication 2.7:1
Overall savings 4.2:1
Average latency 1.2ms
- Compression 1:1
-
A newly established CSP allows for drive shipping to upload new data into the environment. Sensitive data on 40TB of storage needs to be transferred within one week. Which of the following is the MOST efficient and secure method for shipment of the data to the CSP with minimal downtime?
- Create a VPN between the sites and schedule data transfer during non-business hours.
- Copy the data to encrypted drives and use the CSP-certified shipping provider.
- Compress and SFTP the data to the CSP.
- Move the data to encrypted drives and use the CSP-certified shipping provider.
-
A manufacturing company’s current security policy mandates PII is not stored in the SaaS solution. Which of the following configuration controls should be used to block sensitive information from being stored in the SaaS solution?
- Implement file-level encryption.
- Implement a network ACL.
- Implement an IPS.
- Implement content filtering.
-
A new application with availability SLA requirements of 99.99% has been deployed in a cloud. For a test spanning a month, which of the following unavailability times would mean the test was successful? (Select TWO).
- 1 minute
- 4 minute
- 10 minutes
- 30 minutes
- 60 minutes
-
A company’s security policy requires full disk encryption on all clients with preboot enabled. The encryption server is hosted, and the requirement is to push an update to all endpoints. Which of the following is the BEST method to test and apply the update with minimal disruption to end users?
- Access the API of the encryption server, develop a custom script, and then update all endpoints.
- Access the web UI portal of the encryption server, apply the update to the test group, validate, and then update all endpoints.
- Add the update to the standard desktop configuration image, apply the update to a test VM, and then reimage clients.
- Access the web UI of the encryption server and disable preboot, apply the update, test, and then deploy the update to all endpoints.
-
A technician receives a report of system utilization:

CV0-002 Part 02 Q16 014 Which of the following additional resources should the technician add FIRST given the trend data shown above?
- CPU
- Disk
- Bandwidth
- RAM
-
A cloud architect is tasked with isolating traffic between subnets in an IaaS platform. The networks should be able to statefully communicate with each other. Given this scenario, which of the following should the architect implement?
- Configure security groups.
- Configure HIPS policies.
- Configure IDS policies.
- Configure a network ACL.
-
A cloud administrator is provisioning several user accounts that have administrator rights to assets using JSON within an IaaS cloud platform. The administrator is required to configure “alternate” settings using the API. Given this scenario, which of the following elements would allow the administrator to meet these requirements in the JSON file?
- Statement
- Effect
- Resource
- Condition
-
Before doing a change on a VM, a systems administrator wants to ensure there is an easy and fast way to rollback if needed. The change and testing should take approximately two hours. Which of the following is the EASIEST way to meet this requirement?
- Create a snapshot on the hypervisor.
- Make an on-demand, incremental backup to a VTL.
- Make an on-demand, full backup to a secondary location.
- Create a snapshot on a remote storage array.
-
The CSA needs to install a patch on 58 virtual server instances during the Friday evening maintenance window. Which of the following is the MOST efficient way to get the patches installed?
- Use the patch management tool to automate and orchestrate the patch installation.
- Use a security vulnerability scanning tool to apply the patch automatically.
- Schedule the patch to install from a remote file server upon server reboot.
- Connect the server instances to the Internet to download the patch automatically.