CV0-002 : CompTIA Cloud+ (CV0-002) : Part 04
CV0-002 : CompTIA Cloud+ (CV0-002) : Part 04
-
A customer wants to schedule a backup job that compares and saves changes from the last full backup. Which of the following backup types should be used?
- Differential
- Full
- Clone
- Incremental
-
A company security policy mandates education and training for new employees. The policy must outline acceptable use policies for SaaS applications. Given these requirements, which of the following security controls is BEST suited?
- Preventive
- Detective
- Corrective
- Physical
-
A private cloud customer is considering using the public cloud to accommodate the peak utilization workload. Which of the following would be considered the ideal scaling solution?
- Cloud bursting
- Load balancing
- Horizontal scaling
- Vertical scaling
-
A cloud administrator reports a problem with the maximum number of users reached in one of the pools. There are ten VMs in the pool, each with a software capacity to handle ten users. Based on the dashboard metrics, 15% of the incoming new service requests are failing. Which of the following is the BEST approach to resolve the issue?
- Check compute, storage, and networking utilization in the dashboard and increase capacity by adding more resources.
- Check current licensed capacity and purchase additional licenses to add more users.
- Check the DHCP scope and increase the number of available IP addresses by extending the pool.
- Check the rate-of-load increase to determine if the cloud capacity boundary has been exceeded and enable bursting to the pubic cloud.
-
In an IaaS environment, the security team issues a new signature file to prevent specific malware threats from infiltrating the company network. Which of the following describes where the security team should deploy the updated signatures?
- IDS
- Spam filter
- WAF
- NIPS
- HIPS
-
A small clinic is moving its health and accounting systems to a SaaS solution. The clinic holds patient- and business-sensitive information. Which of the following is the company expected to do to protect its data?
- Document, configure, and enforce strong account management policies.
- Disable and document unneeded ports and protocols on the SaaS servers.
- Install antivirus and disable unneeded services on all SaaS servers.
- Harden the underlying infrastructure: servers, firewalls, and load balancers.
-
A consultant is helping a large company migrate its development environment to a public cloud provider. The developers are working on a VDI solution. The development tools that employees utilize require greater control of the OS environment. Which of the following cloud types should the consultant implement?
- SaaS
- PaaS
- Bare metal service
- IaaS
-
A company changed its policy to have seven-year data retention in the public cloud. Which of the following would be the MOST cost-effective way to meet retention requirements?
- Site mirroring
- Automated archiving
- Replication
- Third-party sites
-
During peak times, users are unable to access their online wealth management applications in a timely fashion. The online banking application resides in a community cloud environment. Which of the following explains how the cloud systems administrator should start to resolve this issue?
- Access the cloud services portal and ensure memory ballooning is enabled.
- Access the cloud services portal and ensure there is adequate disk space available.
- Access the cloud services portal and ensure all users are accessing it through the same web service.
- Access the cloud services portal and ensure the ACLs are set correctly for the user community.
-
A business is planning to migrate from a private cloud to a public cloud. To document business continuity, which of the following should be done FIRST?
- Develop a disaster recovery plan with partners/third parties.
- Define the set of application-based SLAs.
- Identify HA technology to provide failover.
- Define the scope of requirements.
-
Joe, a systems administrator, deployed a computer and storage for a system and took it to the application team. The next day, the application team claimed the database was slow. The deployment request, result, and current utilization data are shown below.
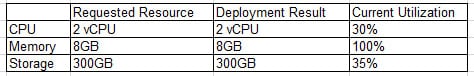
CV0-002 Part 04 Q11 017 Which of the following descriptions of the situation is correct?
- The deployment was done with the wrong memory configuration.
- The deployment was unsuccessful due to the cloud failure.
- The deployment was successful, but the capacity planning was inaccurate.
- The deployment was done with the wrong storage parameter.
-
A large finance firm processes three times as many transactions in December of each year. The transactions are processed in a private cloud. Management wants to avoid adding permanent resources to accommodate the single month increase. Which of the following is the BEST way to meet the need?
- Migrate all transaction processing to a public cloud and size capacity for the largest seasonal needs.
- Keep current capacity for processing, but implement cloud bursting to auto scale the resources without having to invest in infrastructure.
- Determine usage patterns over time and virtualize the processing traffic to give room for seasonal changes in resource demand.
- Determine usage patterns for the seasonal capacity needs and add physical resources to allow additional processing.
-
A cloud administrator is adding several accounts for new development team interns. These interns will need access to some, but not all, of the resources and will only be working over the summer. Which of the following user provisioning techniques should be used?
- Create a single account for the interns to share. Set the expiration date for the account to six months.
- Create a role labeled “interns” with the appropriate permissions. Create a separate account with an expiration date for each intern and add each intern to that role.
- Create one template user account with the appropriate permissions and use it to clone the other accounts. Set an expiration date for each account individually.
- Create individual accounts for each intern, set the permissions and expiration date for each account, and link them to a temporary guests user group.
-
After deploying new VMs, the systems administrator notices it is not possible to connect to them using network credentials; however, local accounts work. After logging in, the administrator notices the NTP servers are not set. Which of the following is MOST likely causing this issue?
- Directory services requires the use of NTP servers.
- The VMs are insufficiently licensed.
- There is a directory services outage.
- There is a time synchronization issue.
-
A cloud engineer notices on a dashboard that the host is close to reaching maximum capacity for the CPU and memory in the cloud environment, which could cause performance issues. The cloud environment has 100 servers, with 25% of the servers consuming their compute only during peak business hours, 25% consuming half of the allocated resources, and the remaining 50% using the compute during off hours. Which of the following should the engineer perform to optimize the efficiency of the compute usage in the cloud?
- Add additional CPUs and RAM to the host that is serving the cloud.
- Adjust the cloud workload by migrating resource-intensive applications to different hosts.
- Add additional hosts to the environment using the cloud management tool.
- Enable automatic scaling in the cloud management tool.
-
A cloud administrator is managing two private cloud environments. In cloud A, the disaster recovery solution has an SLA for RPO of five minutes and RTO of one hour. In cloud B, the disaster recovery solution has an SLA for RPO of one hour and RTO of 24 hours. A new customer’s application requires that, in case of a disaster, no more than 15 minutes of data can be lost, and it should be fully recovered within one day. Which of the following would be the BEST approach to this application?
- Tell the customer cloud A is the best solution
- Put it in cloud B and ask the customer to create snapshots every 15 minutes
- Both cloud A and cloud B would suit the customer’s needs
- Change the cloud B disaster recovery solution so RPO will be 15 minutes
-
A new private cloud platform is being deployed by an engineer. SLA requirements state that any clusters should have a baseline redundancy sufficient to handle the failure of at least two hosts. The engineer records the following metrics after the deployment:
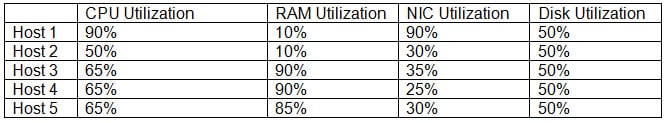
CV0-002 Part 04 Q17 018 Which of the following metrics is MOST likely to represent a violation of SLA?
- RAM utilization
- NIC utilization
- CPU utilization
- Disk utilization
-
Email users report that it takes more than one minute to open emails, including those without attachments. There are three email instances in three different regions hosted by the same CSP. Other applications hosted by the same CSP have no reported issues. Which of the following solutions BEST resolves the issue?
- Confirm that the email instances have sufficient bandwidth.
- Install monitoring software on the email instances.
- Check the antivirus software settings and disable real-time message scanning.
- Ensure the requested IOPS are being provided to the email instances.
-
A hospital is deploying a web-based application in its private cloud to service multiple facilities in a region. This application is used by employees of the hospital, as well as the patients and their families. Which of the following security configurations is MOST likely to be deployed to secure the information from the application?
- IPSec
- PPTP
- L2TP
- SSL/TLS
-
A cloud-based web store is experiencing poor website performance and unavailability. Which of the following approaches would prevent the issue without administrator intervention?
- Install and deploy a load balancer in the front of the web server.
- Increase the computing resources to the web server.
- Increase the network’s bandwidth to handle the spike.
- Partner with a cloud provider to scale the required resources as needed.