CV0-002 : CompTIA Cloud+ (CV0-002) : Part 09
CV0-002 : CompTIA Cloud+ (CV0-002) : Part 09
-
A non-critical vulnerability has been identified by a Linux vendor, who has released a patch and recommends that it be applied immediately.
Which of the following is the BEST plan for the cloud administrator to install the patch?
- Schedule an emergency maintenance window and deploy the patch to servers in production.
- Deploy the patch to the failover cluster and force a failover to the patched environment.
- Deploy the patch to half of the servers in production and monitor for any issues.
- Deploy the patch to the development and QA environments and request a functional test review.
-
Government agencies currently operate their own websites, each with its own directory services. There is a mandate to minimize IT administration.
Which of the following should the cloud services architect choose to BEST meet this mandate?
- Set up a direct VPN tunnel between the government sites.
- Upgrade all stand-alone systems to use mobile technologies.
- Upgrade the operating systems on all of the web servers.
- Reengineer the identification and authorization process.
-
A company requires all system logs to be saved for a minimum 30 days. However, many employees are reporting storage near capacity alerts. A cloud administrator is trying to fix and prevent this issue from happening again.
Which of the following is the BEST option?
- Automate log deletion for logs older than 30 days. This job should run every day to clean up.
- Automate archiving of the logs older than 30 days, and create a scheduled job to clean up daily logs older than 30 days
- Automate migration of the log archiving storage to offline backup, and create a job to check and delete logs every 30 days.
- Automate the clearing of the logs older than 30 days, and add more capacity to the log file storage.
-
An administrator is implementing a new SaaS application. The administrator has been directed to enhance the user authentication experience.
Which of the following technologies BEST meets this requirement?
- Federation Services
- Multifactor authentication
- Biometric authentication
- Directory services
-
A cloud systems administrator manually archives security logs. Every time the administrator goes on vacation, users are unable to browse company websites.
Which of the following is the BEST way to resolve this issue?
- Automate the retention policies.
- Automate the removal of inactive accounts.
- Automate the removal of orphaned resources.
- Automate the addition of web servers.
-
There has been a change in requirements for two countries where PCI virtual instances exist. As such three virtual instances need to be added in both countries’ PCI environments, and two instances need to be removed.
Which of the following is the BEST way to ensure compliance is met in those two countries?
- By the effective date of the new requirement, in each country, remove the two out-of-compliance virtual instances.
- By the effective date of the new requirement, in each country, implement the three new virtual instances.
- By the effective date of the new requirement, in each country implement the three new virtual instances. After a month of testing remove the two out-of-compliance virtual instances.
- By the effective date of the new requirement, in each country, remove the two out-of-compliance virtual instances and implement the three new virtual instances.
-
While reviewing the auto-scaling events for a web application, a cloud engineer identified that the application upsized and downsized multiple times within the last hour.
Which of the following should the cloud engineer do NEXT?
- Add more systems into the scaling group.
- Review the load balancer configuration settings.
- Review auto-scaling policies to detect a misconfiguration.
- Monitor auto-scaling events for the next 24 hours.
-
Given the metric below:
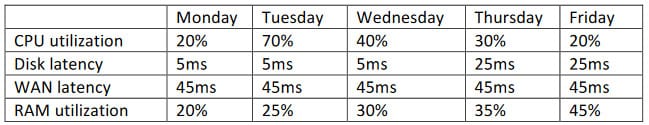
CV0-002 Part 09 Q08 030 Using iSCSI storage reports across three datacenters, which of the following recorded metrics indicates an anomaly in the performance?
- Disk latency
- CPU utilization
- WAN latency
- RAM utilization
-
A cloud application development team needs to consider the following requirements to the built in as part of the application’s authentication process:
– Customers should have the flexibility to use their own identity stores within the authentication process.
– Customers should not be asked to provide the credentials repeatedly for different applications with different permission sets.Which of the following solutions would BEST help the team achieve the above business objectives? (Choose two.)
- Certificates
- Single sign-on
- One-time passwords
- Federation
- Multifactor authentication
- Hardware tokens
-
To enhance availability, a company has expanded its public cloud presence to multiple regions from a single CSP. The company wants to ensure resources in the public cloud are highly available to users at company headquarters.
Which of the following is the BEST solution to fulfill this requirement?
- Dual direct peering/connections from headquarters to one cloud region.
- Dual VPN connections over a single ISP from headquarters to one cloud region.
- Dual VPN connections over two separate ISPs from headquarters to both cloud regions.
- Dual direct peering/connections over a single ISP from headquarters to both cloud regions
-
The sales department is preparing to launch a high-demand product for purchase through the company’s online store. The senior engineer asks the junior engineer to review the sales cloud resources to plan for a surge in online traffic:
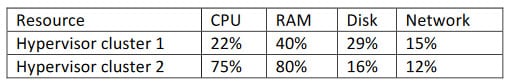
CV0-002 Part 09 Q11 031 Given the metrics in the table above, which of the following resources should be adjusted to plan for future growth?
- Propose additional memory for cluster 1.
- Propose additional storage for cluster 1.
- Propose additional guests for cluster 2.
- Propose additional hosts for cluster 2.
-
Ann, a cloud administrator, is reporting on how the organization has adhered to its marketing of 99.99999% system availability SLA.
Given this scenario, which of the following should Ann include in her report?
- System clock time
- System idle percentage
- System response time
- System uptime
-
A cloud-based web proxy is blocking key sites that a business requires for operation. After validation, the sites are legitimate, and access is required for end users to complete their work.
Which of the following is the BEST solution to allow access to the sites?
- Instruct users to bypass the cloud-based web proxy.
- Whitelist the URLs.
- Blacklist the URLs.
- Create a security group for those users and enforce MFA.
-
A SaaS customer reports that no one can access the application portal. After some troubleshooting, the cloud administrator finds a problem and provides a remedy by restarting the cluster. After documenting the solution, the support case is closed. Multiple tenants lose access to their hosts the following day.
Which of the following troubleshooting steps did the administrator miss?
- Identify the problem.
- Establish a theory.
- Verify full system functionality.
- Test the theory.
- Establish a plan of action.
-
A new version of an e-commerce application was deployed using a standard template configuration of 4 vCPU and 8GB of RAM. The administrator has configured the application to automatically add 4 GB of RAM after 80% utilization of continuous use over a period of time.
Which of the following testing techniques should be used to test this scenario?
- Integration testing
- Load testing
- Penetration testing
- Automation testing
-
Upon discovery several SaaS applications are being utilized by users, and the InfoSec team needs to update a configuration file on all client machines.
Which of the following file types is used to redirect users through a web proxy?
- dat
- tmp
- log
- pac
-
With increased traffic to a website, several outages have occurred due to a log files filling the root drive of the web servers. An administrator is considering several possible solutions to prevent future outages.
Which of the following techniques is MOST likely to impact server performance if implemented?
- Archiving logs.
- Clearing logs.
- Log redirection.
- Drive compression.
-
Based on demand, an IaaS provider wants to deploy a security application for its customers.
Which of the following is the BEST technique for the IaaS provider to apply this to target systems?
- Vendor application
- Scripting
- Orchestration
- Custom programming
-
A company is using storage-as-a-service from an IaaS provider for application services. The company has a mandate to protect personal information being stored on the cloud. The service provided includes encryption for in-transit data and requires a security solution for data-at-rest.
Which of the following should be deployed to secure the personal information?
- Implement data tokenization.
- Implement hardware-based encryption.
- Implement centralized key management.
- Implement database-embedded encryption.
-
Asynchronous data replication for a SaaS application occurs between Regions A and B. Users in Region A are reporting that the most current data for an insurance claims application is not available to them until after 11:30 a.m. The cloud administrator for this SaaS provider checks the network utilization and finds that only about 10% of the network bandwidth is being used.
Which of the following describes how the cloud administrator could BEST resolve this issue?
- Check the storage utilization logs in both regions.
- Check the RAM utilization logs in both regions.
- Check the CPU utilization logs in both regions.
- Check the storage commit logs in both regions.