CV0-002 : CompTIA Cloud+ (CV0-002) : Part 11
CV0-002 : CompTIA Cloud+ (CV0-002) : Part 11
-
A service engineer is trying to determine why one of the company’s SaaS solution is no longer available. The internal systems are responding and other online applications using the same SaaS solution are responding as expected.
Which of the following is the MOST common cause of the availability issue?
- Cloud service provider outage
- Automation/orchestration issue
- Integration issue
- Subscription issue
-
An administrator is creating new severs in a public cloud. The workflow creates and application group with three VMs, one web server, one application server and one database server. The three VMs are all accessible via SSH, but the websites shows a 503-error referring to a database issue.
Which of the following is the MOST likely cause of the error?
- Misconfigured VLAN
- Misconfigured proxy
- Misconfigured firewall rule
- Misconfigure routing
-
A customer has indicated that bi-weekly full backups are taking too long to complete.
Which of the following would be the BEST action if minimizing restore time is very important to the customer?
- Change the backup to synthetic full backups.
- Change the second full backup in a week to incremental.
- Change the second full backup in a week to differential.
- Change the schedule of full backups to start earlier.
-
A facilities management company uses a private cloud that bursts to a public cloud at times. The CSA is asked to check the amount of storage that is used when the organization is overutilizing on-premises resources.
Which of the following should the CSA check?
- Ensure deduplication is enabled on all storage volumes.
- Check storage utilization in the public cloud.
- Verify storage utilization in the private cloud.
- Confirm storage utilization in the public cloud backup environment.
-
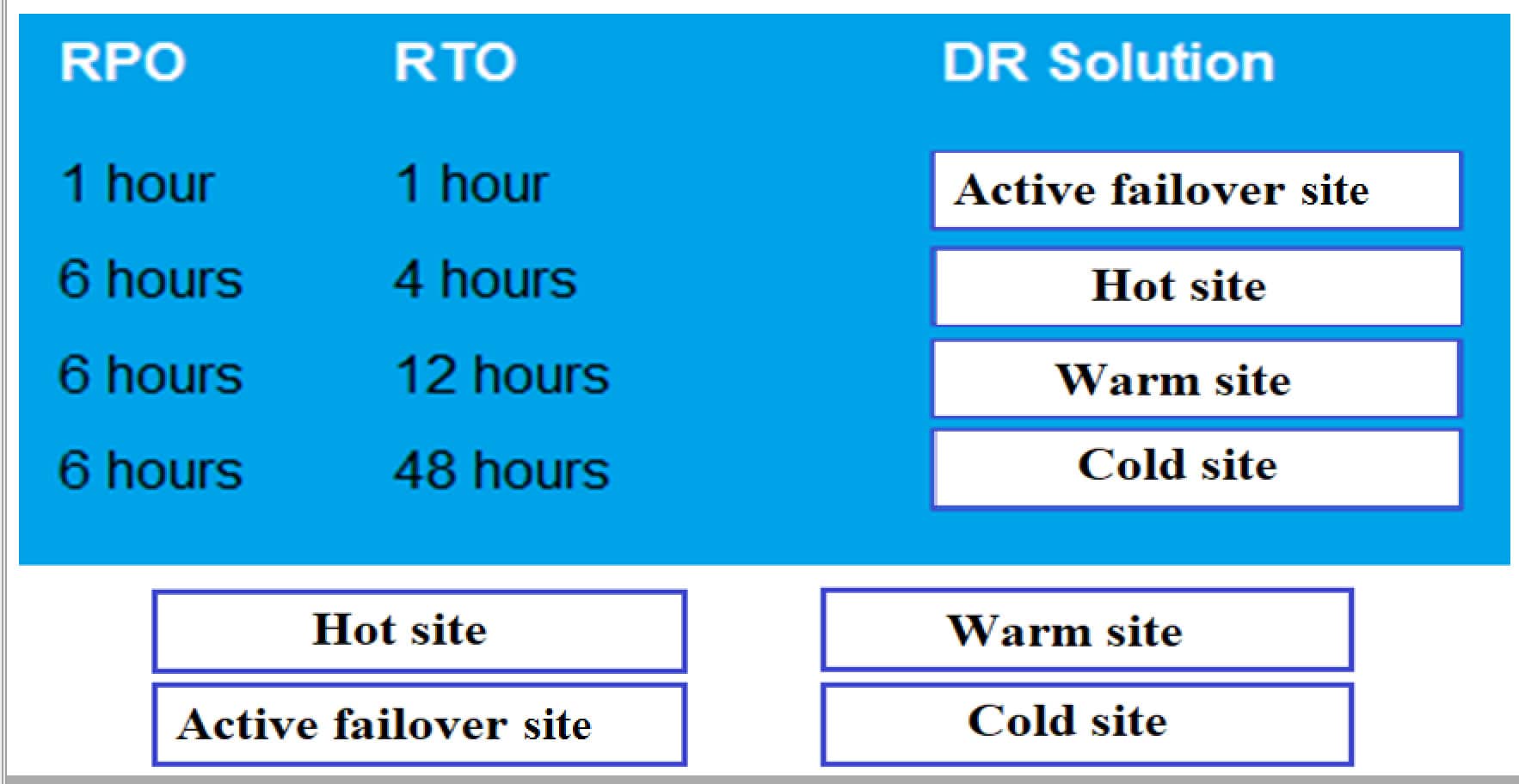
DRAG DROP
Drag and drop each Disaster Recovery Solution need to the corresponding SLA requirement. Options may be used once or not at all.
- SIMULATION The QA team is testing a newly implemented clinical trial management (CTM) SaaS application that uses a business intelligence application for reporting. The UAT users were instructed to use HTTP and HTTPS. Refer to the application dataflow:1A – The end user accesses the application through a web browser to enter and view clinical data.
2A – The CTM application server reads/writes data to/from the database server.1B – The end user accesses the application through a web browser to run reports on clinical data.
2B – The CTM application server makes a SOAP call on a non-privileged port to the BI application server.
3B – The BI application server gets the data from the database server and presents it to the CTM application server.When UAT users try to access the application using https://ctm.app.com or http://ctm.app.com, they get a message stating: “Browser cannot display the webpage.” The QA team has raised a ticket to troubleshoot the issue.

CV0-002 Part 11 Q06 034 
CV0-002 Part 11 Q06 035 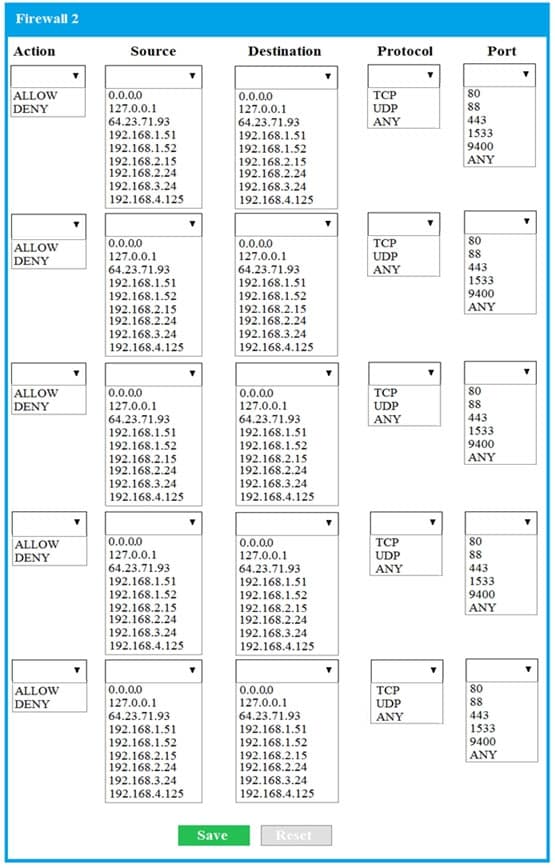
CV0-002 Part 11 Q06 036 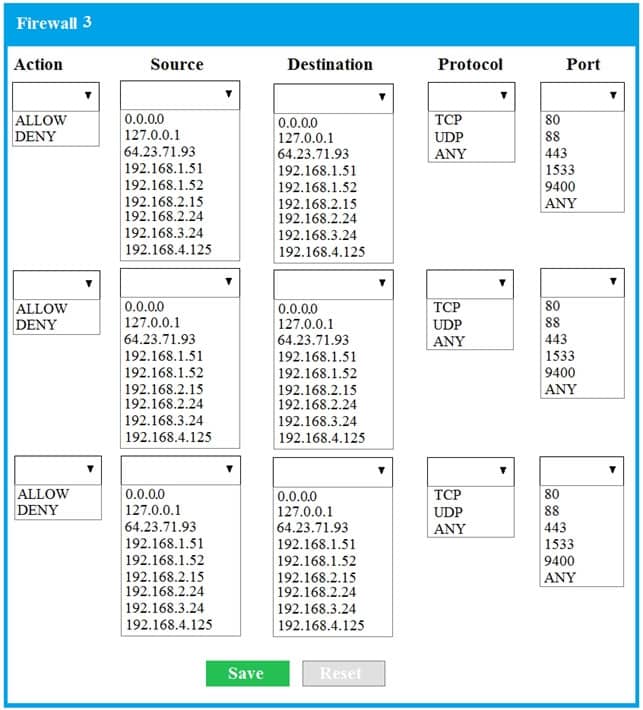
CV0-002 Part 11 Q06 037 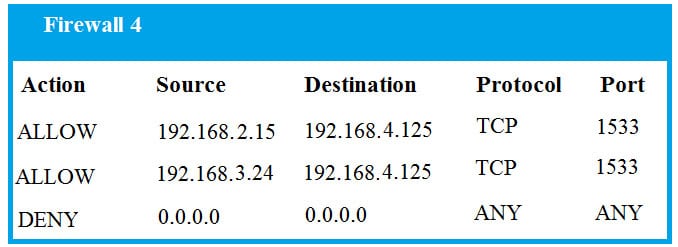
CV0-002 Part 11 Q06 038 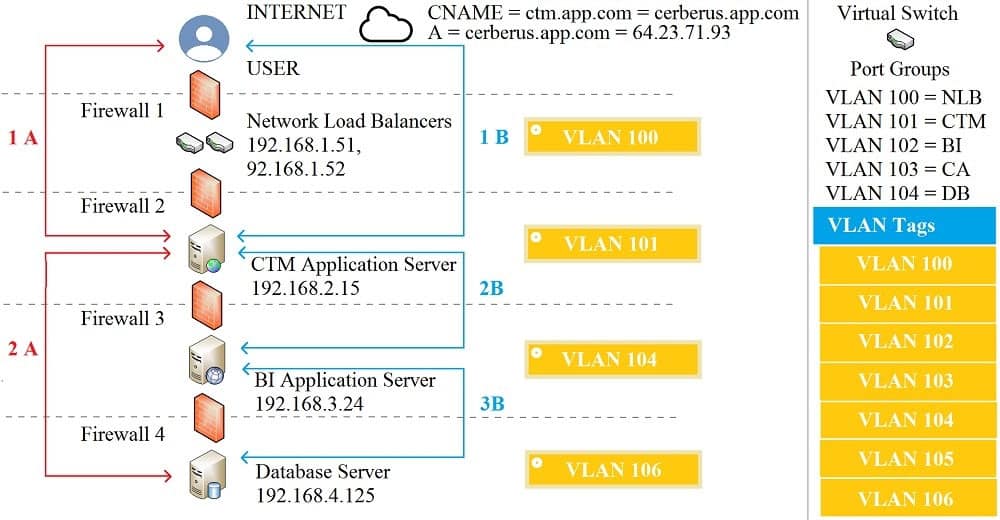
CV0-002 Part 11 Q06 039 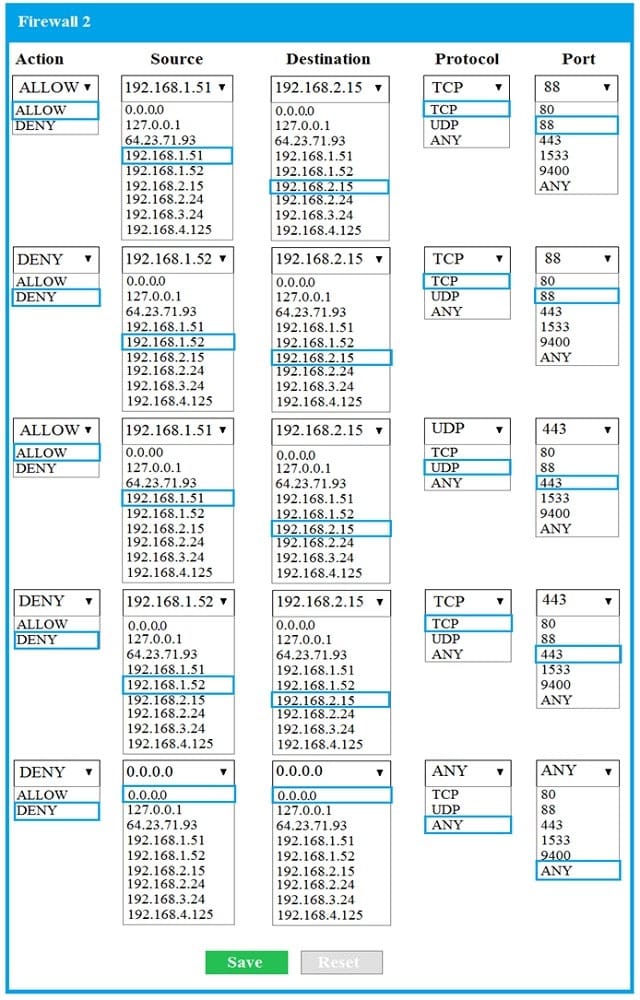
CV0-002 Part 11 Q06 040 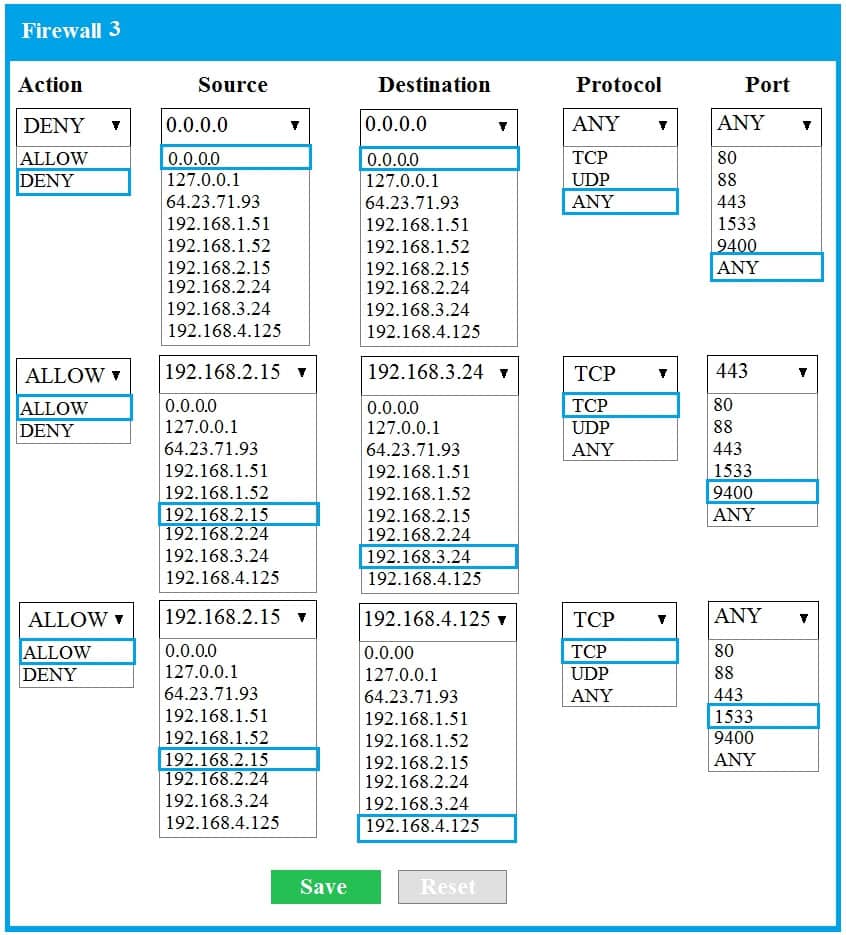
CV0-002 Part 11 Q06 041 -
A law firm wants to limit log retention to the minimum required by law and regulation. Which of the following is the engineer most likely to do FIRST?
- Create a 2GB external hard drive to log all activities.
- Configure all systems in scope to log activities in support of company policies.
- Configure a daily rotation on all workstations to limit the logs’ discovery scope.
- Deduplicate, compress, and encrypt all logs before archiving them.
-
Cloud developers are experiencing a delay caused by the static code review before each deployment. The security operator and developer must address the issue without cutting corners with security testing. Which of the following would BEST address the delay issue?
- Replace the static code analysis with hardening techniques.
- Perform the static code analysis earlier in the SDLC.
- Perform a penetration test instead of a static code analysis.
- Replace the static code analysis with a vulnerability analysis.
-
All the virtual server instances within an organization’s private cloud environment are having trouble logging into the Kerberos realm. Upon investigation, the CSA notices the time stamps are different on the server virtual instances. Which of the following should be the CSA’s NEXT step to resolve this issue?
- Check the Kerberos token time stamp.
- Check the NTP server to see when it last rebooted.
- Check the NTP server synchronization.
- Check the virtual server time display format.
-
A company provides IaaS services. Which of the following disk provisioning models for creating standard template should the company use to provision virtual instances?
- Thin disk
- SCSI disk
- SATA disk
- Thick disk
-
Several state and local law enforcement agencies have decided to share information about traffic violations within their state by using a new search application. The state has policies around limiting the exposure of PII, and each local agency must comply with these policies. Which of the following cloud architecture models would be the BEST approach?
- Deploy the application to a public cloud and establish connections for each local agencies’ private cloud and use federation.
- Have each local agency publish its data to an account that has been set up in a public cloud provider and deploy the application there.
- Deploy the application in each local agency’s private cloud and create accounts for everyone to allow access to publish and search the data.
- Deploy the application in the state’s shared cloud environment and create federation between the local agencies.
- A cloud engineer is upgrading a high-performance computing cluster for the private cloud. The existing cluster is being replaced with GPU servers. A single GPU server is capable of the same teraflops output as 10 CPU servers. The current cluster configuration is as follows:
100 quad-core CPU servers capable of producing 100 teraflops.
The baseline and current usage is 100%.The new cluster was set up and benchmarked in four different configurations. Which of the following configurations will meet the baseline teraflops performance of the cluster while maintaining the current usage?
- 1 GPU server, 80 CPU servers
- 2 GPU servers, 50 CPU servers
- 5 GPU servers, 40 CPU servers
- 9 GPU servers, 10 CPU servers
-
A company wants to set up a new department using private cloud resources. The new department needs access to sales and financial data, but it should be prohibited from accessing human resources data. Which of the following is the BEST option to configure on the virtual (software-defined) network to meet these requirements?
- VSAN
- VLAN
- GRE
- VPN
-
An engineer is responsible for managing a private cloud environment at a software company. Company developers perform all programming in the cloud environment. There are two departments working on a highly classified product that now requires dedicated resources, which cannot be viewed or accessed by other departments in the cloud environment. Which of the following should the engineer perform to ensure the requirements are met? (Choose three.)
- Create a baseline
- Assign an ACL
- Verify segmentation
- Use thin provisioned storage
- Automate patch deployments
- Create a tenant
- Deploy a PKI solution
-
A company is in the process of evaluating cloud service providers, as it is planning to move all of its on-premises IT services to the cloud. Most of the applications are mission critical with four 9s and five 9s uptime. The area where the company is located is also prone to natural disasters. One of the main requirements is that IT services need to survive local outages as well as regional outages. One of the company’s main customers is a government entity. Which of the following is the BEST way for a cloud engineer to address these requirements?
- Select a cloud service provider with local, regional, and international failure zones.
- Select a cloud service provider with local, national, and international failure zones.
- Select a cloud service provider with local, regional, and national failure zones.
- Select a cloud service provider with regional, national, and international failure zones.
-
A cloud administrator is troubleshooting a network issue that was raised after the introduction of a CASB solution. The administrator attempts different ideas during troubleshooting but is unable to resolve the issue. In which of the following steps of the troubleshooting process is the administrator experiencing an issue?
- Identifying the problem
- Establishing a theory of probable cause
- Testing the theory to determine the cause
- Documenting the findings and actions
-
A large law firm is migrating all of its systems to the cloud to meet growing business needs. The firm wants to reduce IT staff while maintaining day-to-day operations, such as user provisioning, folder management, and permissions. Which of the following MUST the cloud provider and cloud customer implement to ensure user non-repudiation?
- Server certificate
- Client-to-site VPN
- Two-factor authentication
- Single sign-on
-
A multinational corporation is moving its worldwide cloud presence to a single region, which is called Region A. An administrator attempts to use a workflow, which was previously used to deploy VMs to Region E in the new Region A environment, and receives the following error: Invalid character set. Which of the following is the MOST likely cause of the error?
- Language support
- Licensing failure
- Authentication issues
- Time-zone misconfiguration
-
An administrator is using a script to create ten new VMs in a public cloud. The script runs and returns no errors. The administrator confirms that all ten VMs show up in the dashboard, but only the first eight reply to pings. Which of the following is the MOST likely cause of the issue?
- Workflow credential errors
- API request limitations
- IP address depletion
- Batch job scheduling issue
-
A company has hired a technician to build a cloud infrastructure for a massively parallel application. Which of the following should the technician consider doing FIRST?
- Add a GPU to the VMs
- Configure the VMs to scale up automatically
- Allocate maximum bandwidth to the VMs
- Select the most compute cores for the VMs