CV0-002 : CompTIA Cloud+ (CV0-002) : Part 14
CV0-002 : CompTIA Cloud+ (CV0-002) : Part 14
-
A manufacturing company has the following DR requirements for its IaaS environment:
RPO of 24 hours
RTO of 8 hoursThe company experiences a disaster and has a two-site hot/cold configuration. Which of the following is the BEST way for the company to recover?
- Restore data from the archives on the hot site, point users to it, and resume operations.
- Bring the cold site online, point users to it, and resume operations.
- Rebuild the site from the cold site, bring the site back online, and point users to it.
- Replicate data from the non-failed site to another cloud provider, point users to it, and resume operations.
-
A company has developed a SaaS product for the financial services industry. The Chief Executive Officer (CEO) of the SaaS company has engaged an independent third party to run tests against its platform. Which of the following is the MOST likely test the third party has been engaged to perform?
- Penetration testing
- Load testing
- Vulnerability testing
- Functionality testing
-
A user cannot consume SaaS services while working remotely. IP whitelisting is implemented to connect to a SaaS provider as a security mechanism. Which of the following describes the MOST likely reason why the user cannot access the SaaS resources?
- The user is not utilizing VPN to connect to the home office.
- The user account does not exist in the SaaS provider.
- The user account is not assigned the correct role in RBAC policy.
- The user account has consumed all of the available subscriptions.
-
A systems administrator needs to deploy a database that saves a unique ID/hash at the beginning of each block into a private cloud. The administrator needs to maximize storage savings. The administrator has multiple storage policies set. Which of the following would be the BEST option for this deployment?
- Compression enabled
- Deduplication enabled
- Mirroring enabled
- Tokenization enabled
-
A cloud security analyst performs a vulnerability scan on a web application server across all staging environments. According to the vulnerability scan, the web content featured on the server in the staging environment is located on the C:\ drive, which is the same location housing the operating system.
The analyst determines the results are false positive and submits a report, which includes artifacts supporting the claim to the CAB. Given this scenario, which of the following test plans would be the MOST appropriate to include in the report?
- Penetration test plan
- Vulnerability test plan
- User acceptance test plan
- Smoke test plan
-
Of ten newly deployed VMs from a single template, the cloud administrator notices one VM has direct root access enabled and automatic configuration control disabled. These settings do not comply with the company’s policies for production VMs. Which of the following is the MOST likely cause of this situation?
- Another administrator intentionally changed the settings.
- The template is misconfigured.
- There is provisioning workflow breakdown.
- There is a bug in the current hypervisor version.
-
A healthcare provider determines a Europe-based SaaS electronic medical record system will meet all functional requirements. The healthcare provider plans to sign a contract to use the system starting in the next calendar year. Which of the following should be reviewed prior to signing the contract?
- Security auditing
- Storage cost and types
- Bandwidth utilization
- Third-party integration
-
A cloud administrator runs a maintenance script to remove unused resources. After the maintenance has been performed, users report they can no longer access the application website. The administrator confirms the server is up and responding on the proper ports. Which of the following cleanup actions MOST likely caused the problem?
- Removing inactive accounts
- Removing outdated firewall rules
- Removing stale DNS entries
- Removing orphaned resources
-
Given the IaaS cloud service model, at which of the following layers of the platform does microsegmentation BEST apply?
- Compute
- Storage
- Network
- Management
-
A cloud application has been in production for six months without any issues. Shortly after increasing the number of users assigned to the application, however, users start reporting errors. The administrator does not see any resource thresholds being exceeded in the cloud dashboard. Which of the following is the MOST likely cause of the errors?
- Failed autoscaling
- IP address limitations
- License exhaustion
- Bandwidth saturation
-
A cloud engineer recently applied the troubleshooting process for a major connectivity issue. Which of the following is the FINAL step in the troubleshooting methodology?
- Document findings, actions, and outcomes.
- Establish a plan of action to resolve the problem and implement the solution.
- Confirm the root cause of the issue.
- Verify full system functionality and, if applicable, implement preventive measures.
-
A company has a requirement of an active/active datacenter and wants to implement synchronous replication for all its storage services. The company is doing a proof of concept with a datacenter provider that has two datacenters 200mi (322km) apart that utilize MPLS. Each time the company starts synchronous replication, it fails. All network connectivity has been established and is functioning correctly. Which of the following is the MOST likely cause?
- Latency between datacenters
- Applications are latency tolerant
- Link bandwidth between datacenters
- Link between datacenters is not fiber
-
A cloud engineer needs to deploy a new virtual firewall in a private cloud. Which of the following should the engineer do as a FIRST step?
- Document the deployment in a knowledge base.
- Create a change for deploying the firewall.
- Put the hypervisor in maintenance mode.
- Inform users that the cloud will be momentarily unavailable.
-
A cloud administrator is securing an application hosted by an IaaS provider. The operating system on the VM has been updated. Which of the following should the administrator use to BEST secure the VM from attacks against vulnerable services regardless of operating system?
- Firewall
- Antivirus
- Intrusion detection
- Patch management
-
The development team of an e-commerce organization is migrating its code libraries to a public IaaS cloud provider, and the security policy states that source code must use multiple security controls to secure and restrict access. Which of the following combinations of controls would be BEST to meet the requirements?
- Use directory federation across the organization for all users and biometric access on the developers’ laptop instead of VPN.
- Use VPN and two-factor authentication for the developers to access the online repositories for remote developers.
- Use SSO across the organization and an existing data loss prevention solution to prevent code repository leakage.
- Use a third-party CASB solution that sets policies to detect potential compromise of code libraries.
-
A cloud engineer is migrating an application running on an on-premises server to a SaaS solution. The cloud engineer has validated the SaaS solution, as well as created and tested a migration plan. Which of the following should the cloud engineer do before performing the migration? (Choose two.)
- Document in the change management database.
- Document the test findings.
- Gain approval from the CAB.
- Create a rollback plan.
- Submit a request for change.
- Agree upon a change windows.
- Establish a plan of action.
-
A CSA is reviewing the deployment of an e-commerce application in a public cloud provider. The CSA wants to ensure the sizing is optimal to keep the cost of the environment down. The available server configurations are as follows:
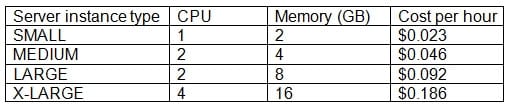
CV0-002 Part 14 Q17 044 A review of the current system shows the following utilization information:
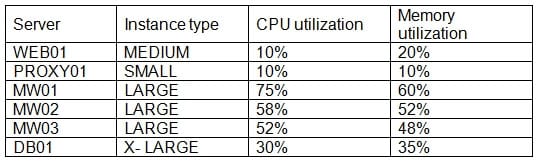
CV0-002 Part 14 Q17 045 Which of the following should the CSA implement to ensure the MOST optimal sizing?
- Change the MW01, MW02, and MW03 servers to the MEDIUM instance type.
- Change the PROXY01 server to the MEDIUM instance type.
- Change the DB01 server to the LARGE instance type.
- Change the WEB01 server to the SMALL instance type.
-
Company A acquires Company B. The resources need to be added accordingly to the SaaS environment. Which of the following resources should be changed by the tenant?
- Compute
- Storage
- Users
- Application
-
A new cloud infrastructure needs to meet the following requirements:
Resources are accessible to internal and external clients.
Existing hardware assets are utilized.
Security controls are managed by company employees.Which of the following deployment models BEST fit these requirements?
- Public cloud using IPS
- Community cloud with IDS
- Private cloud with a DMZ
- Public cloud using PaaS
-
A security analyst is reviewing logs and sees a former employee’s account has been used to access critical information on a private cloud resource. The analyst examines firewall and IPS logs but does not find traffic that is relevant to the breach. Which of the following is the MOST likely source of the compromise?
- External attack
- Internal role change
- External privilege escalation
- Internal attack
-
A company is migrating its application to a cloud provider. Six months before going live, a representative from each stakeholder group validated the functionality and performance in the QA environment and did not identify any issues. After going live, the system response time is slower that the testing environment. Which of the following is the MOST likely gap in the testing plan?
- The test scenario audiences are different between QA and production.
- The application version deployed in production is different than the one deployed in QA.
- System configuration testing in QA and production is different.
- The test plan in QA is different than the production environment.