N10-007 : CompTIA Network+ : Part 21
NS – Modules 20 – 22
-
Which of the following allow for higher fault tolerance, availability, and performance across multiple systems? (Choose two.)
- Load balancer
- Jumbo frames
- Clustering
- Round robin
- TCP offloading
-
A technician is investigating an issue related to a single host that is unable to access the Internet. The technician records the following information: Host IP 169.254.1.10. The network IP address range on the DHCP server is 10.10.5.2-10.10.5.250 with a default gateway 10.10.5.1 and a DNS of 8.8.8.8. Which of the following should the technician perform to troubleshoot the issue?
- Change the IP scope on the DHCP server to a public IP address range.
- Perform a traceroute command to identify the router that is not functioning.
- Verify the host has physical connectivity and is on the correct VLAN.
- Configure the DNS address in the DHCP scope to a 10.10.5.0/24 address.
-
A network administrator wants to reduce the amount of time each user takes to log in to different systems in the network. Which of the following would reduce the time spent authenticating?
- Kerberos
- RADIUS
- Certificate
- SSO
- MFA
- NAC
-
A network technician arrives at a remote office and is unable to connect a laptop to corporate resources using the wireless network. After checking the IP address, the network technician notices the assigned IP address does not belong to the corporate network IP scheme. Which of the following has the network technician discovered?
- Evil twin
- ARP poisoning
- DHCP exhaustion
- Social engineering
-
Which of the following is an object held within an MIB?
- OUI
- OTDR
- OID
- SNMP host
- SNMP agent
- SNMP trap
-
Which of the following storage network technologies has the HIGHEST throughput?
- FCoE
- InfiniBand
- iSCSI
- OC3
-
The corporate head office has assigned the subnet of 10.1.100.0/24 to a network technician. The technician wants to create subnets for the finance department, human resources, and IT. Given the following device counts:
Finance: 70 devices
Human resources: 38 devices
IT: 16 devicesWhich of the following outlines how the technician should allocate the address space given?
- Finance: 10.1.100.0/21
Human resources: 10.1.100.128/22
IT: 10.1.100.192/23 - Finance: 10.1.100.0/23
Human resources: 10.1.100.128/22
IT: 10.1.100.192/21 - Finance: 10.1.100.0/25
Human resources: 10.1.100.128/26
IT: 10.1.100.192/27 - Finance: 10.1.100.0/26
Human resources: 10.1.100.128/27
IT: 10.1.100.192/28
- Finance: 10.1.100.0/21
-
A network administrator is configuring the 172.16.40.0/22 network for a new building. Which of the following is the number of hosts that will be supported on this network?
- 510
- 512
- 1022
- 1024
- 2046
- 2048
-
At which of the following layers of the OSI model does compression occur?
- Session
- Transport
- Data link
- Presentation
-
Users report that the network is slow. Upon investigation, the technician notices all users are on one large subnet. Which of the following devices should be used to break up broadcast domains?
- Layer 2 switch
- Layer 3 switch
- Signal repeater
- Bridge
- Domain server
-
Ann, a user, reports that her desktop phone is not working on one cable. However, that cable provides connectivity to her laptop. A technician determines PoE is not provided to the end device. Which of the following is MOST likely the cause?
- Transceiver mismatch
- Crosstalk
- Jitter
- Open/short on the cable
-
A network technician has been asked to create secure private networks between a company’s headquarters and several branch locations. The company has provided the on-premises equipment, but each branch has a different ISP. Which of the following technologies should the technician consider using to accomplish this?
- Site-to-site
- Client-to-site
- Point-to-point
- Point-to-multipoint
-
A department is reporting network issues. Users can ping each other and the switch, but not the default gateway. When looking at a wiring diagram and a physical blueprint, a technician notices the 1000BaseLX SFP connects to a distribution switch via a cable that runs behind a large industrial refrigerator. The technician also notices both switches have been worked on recently. Which of the following is MOST likely the issue?
- EMI
- TX/RX reverse
- Open/short
- Attenuation
-
DRAG DROP
You have been tasked with testing a CAT5e cable. A summary of the test results can be found on the screen.
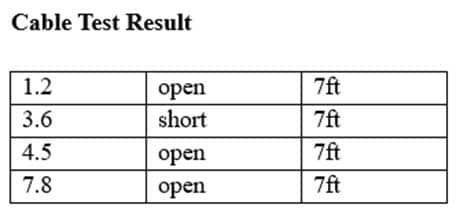
N10-007 Part 21 Q14 023 Instructions
Step 1: Select the tool that was used to create the cable test results.
Step 2: Interpret the test results and select the option that explains the results. After you are done with your analysis, click the ‘Submit’ button.
Step 3: You have determined that the original crimp is faulty. Re-crimp the cable connector using the T568B cabling standard. Choose the correct cable for each pin in the connector by clicking on the pin and selecting a cable color.If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
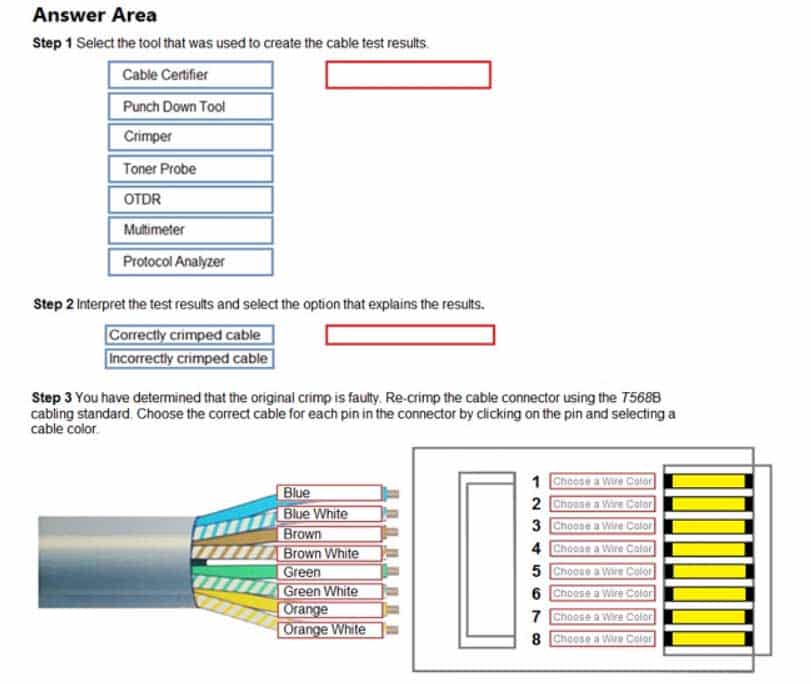
N10-007 Part 21 Q14 024 Question 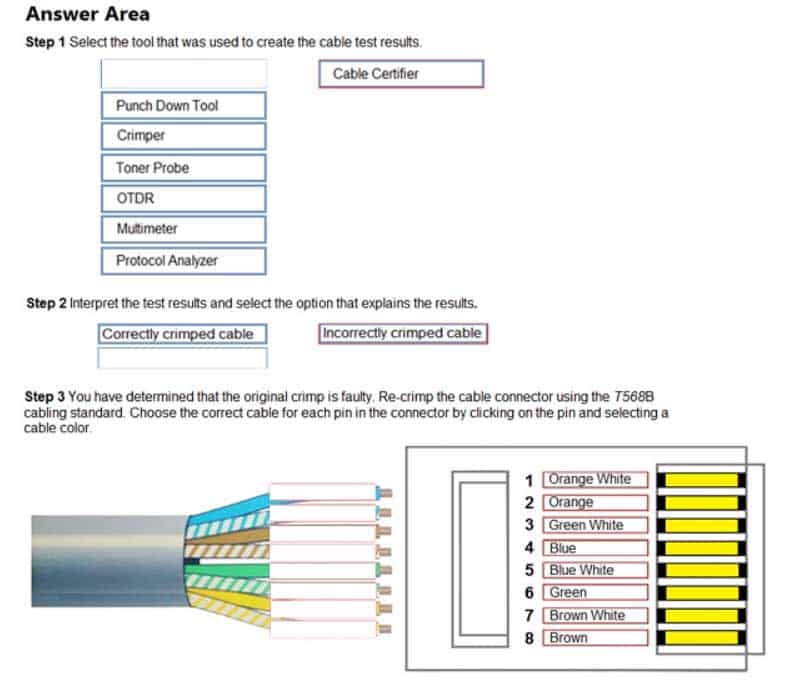
N10-007 Part 21 Q14 024 Answer -
A shop owner wants to ensure that only a specified group of devices can access the wireless network. Which of the following methodologies will BEST ensure unauthorized devices cannot consume the shop owner’s limited Internet bandwidth?
- Disable the SSID broadcast.
- Implement WEP authentication.
- Change the WiFi password.
- Activate MAC address filtering.
-
A large company uses an AAA server to manage network device access. The engineers can use their domain credentials to access all other servers. Currently, the network engineers cannot access the AAA server using domain credentials, but they can access it using a local account. Which of the following should the engineers update?
- Host-based firewall settings
- TACAS+ server time
- Server IP address
- DNS SRV record
-
A network technician has been asked to install an additional switch in an IDF, but all of the single-mode fiber is in use between the IDF and MDF. The technician has deployed new transceivers that allow for the use of a single fiber stand, providing the additional fiber needed for the new switch. Which of the following has the technician deployed?
- 1000BaseLX SFP
- Duplex GBIC
- Duplex SFP+
- Bidirectional SFP
-
A network administrator wants to ensure all traffic is inspected and abides by the AUP, and that malicious traffic is stopped. Which of the following features should be enabled on a firewall to meet this requirement?
- Intrusion detection
- Proxy service
- Dynamic DNS
- Content filtering
-
A network technician has purchased a 10GBase-T switch and wishes to connect it to 30 computers with 10GB network cards. The computers are 225ft (69m) away, and all need to establish a 10 Gbps connection to meet business requirements. To minimize costs while still meeting these requirements, which of the following cable types should the technician choose?
- Cat 5e
- Cat 6
- Cat 6a
- Cat 7
-
A technician is configuring a new email server and needs to modify DNS records. Which of the following records should the technician update to ensure email functions as expected?
- MX
- CNAME
- AAAA
- SRV
NS – Modules 20 – 22
Subscribe
0 Comments
Newest