N10-007 : CompTIA Network+ : Part 33
NS – Modules 20 – 22
-
A network administrator is reviewing security logs and notes a strange IP address logging into the management console of a switch. The administrator verifies the switch is not using default credentials. Which of the following steps should the administrator take NEXT?
- Implement restrictions via ACL.
- Update firmware to the current version.
- Disable unnecessary services.
- Check the hash of the running firmware.
-
Management asks a network technician to install a new connection between two main locations. Management requests that the connection be the fastest possible for data replication. Which of the following would be the MOST appropriate type?
- PRI
- ADSL
- T3/E3
- ISDN
-
A user in the finance department can access the department printer and file server yet is unable to print to the marketing department’s printer. A technician runs ipconfig and sees the following output:
IPv4 Address. . . . . . . . . . . : 192.168.0.101 Subnet Mask . . . . . . . . . . . : 255.255.255.0 Default Gateway . . . . . . . . . : 192.168.1.1
The technician has verified the user’s PC is in the proper VLAN and sees an UP/UP status on the switchport. Which of the following is MOST likely causing the issue?
- The user’s IP is the broadcast address.
- The two printers share the same IP address.
- There is an incorrect default gateway on the user’s PC.
- The ARP table on the switch has not been cleared.
-
A wireless technician needs to deploy a single 802.11 standard that supports both 2.4GHz and 5GHz frequencies with up to 40MHz channel widths. Which of the following wireless standards should the technician configure?
- ac
- b
- g
- n
-
To increase security and usability of the wireless network, a back-end RADIUS server is used to authenticate users. Which of the following encryptions methods should be used to accomplish this?
- WPA2-Personal
- WPA2-Enterprise
- WPA
- WEP
-
A network technician is investigating a device that has been reported as responding slowly. Which of the following should the technician check FIRST?
- Power status
- Traffic analysis
- Logical diagram
- Utilization
-
A network engineer utilizes a box of Cat5e cable in a datacenter for use between 10Gbps switches in a single rack. After the engineer finishes the installation, switch administrators notice random speed drops and intermittent connection issues. Which of the following is this an example of?
- Incorrect cable type
- Attenuation
- Incorrect pinout
- Bad ports
-
A document outlining the types of actions allowed on the corporate network would be BEST defined as an:
- AUP.
- NDA.
- MOU.
- MOA.
-
Which of the following may state: “Employees may not browse social media websites from company-owned computers?”
- AUP
- BYOD
- NDA
- SLA
-
A technician is performing a site survey in an area of a university where both faculty and students are reporting poor performance of their wireless connections. The technician gathers the following data in the problem area:

N10-007 Part 33 Q10 051 Which of the following would MOST likely resolve the issue?
- There are too many wireless clients. Increase the number of APs to handle the traffic load.
- The SNR is not at an acceptable level. Change the channel on the APs.
- The signal strength is too low. Replace the equipment with devices that have better radio antennas.
- The channel numbers on some APs are invalid. Switch AP2 and AP3 to use channel 1.
- The type of antenna is inappropriate for the environment. Switch to 13dBi Yagi antennas.
-
A company recently completed construction of a new remote office. The network administrator needs to set up new network devices, such as printers and a local file server, at the remote location. The new devices need to be configured on the same Layer 2 network as the main office. Which of the following should the network administrator configure?
- Remote desktop gateway
- Transport mode IPSec
- SSH tunneling
- TLS VPN
-
A lab environment hosts Internet-facing web servers and other experimental machines, which technicians use for various tasks. A technician installs software on one of the web servers to allow communication to the company’s file server, but it is unable to connect to it. Other machines in the building are able to retrieve files from the file server. Which of the following is the MOST likely reason the web server cannot retrieve the files, and what should be done to resolve the problem?
- The lab environment’s IDS is blocking the network traffic. The technician can whitelist the new application in the IDS.
- The lab environment is located in the DMZ, and traffic to the LAN zone is denied by default. The technician can move the computer to another zone or request an exception from the administrator.
- The lab environment has lost connectivity to the company router, and the switch needs to be rebooted. The technician can get the key to the wiring closet and manually restart the switch.
- The lab environment is currently set up with hubs instead of switches, and the requests are getting bounced back. The technician can submit a request for upgraded equipment to management.
-
An organization wants to implement a method of centrally managing logins to network services. Which of the following protocols should the organization use to allow for authentication, authorization, and auditing?
- MS-CHAP
- RADIUS
- LDAPS
- RSTP
-
A network administrator has set up a corporate network at a branch office. Users are able to log into the wireless network with their network credentials after they accept the company root certificate. Which of the following is the wireless network MOST likely using?
- WPA2 Enterprise with PSK
- WPA2 Personal with PEAP
- WPA2 Enterprise with Kerberos
- WPA2 Personal with LEAP
-
Ann, a network technician, set up a new server and enabled the host-based firewall. She attempts to connect to the server from several different workstations using RDP but is not successful. Which of the following ports on the firewall should she verify is open?
- 22
- 389
- 443
- 3389
-
A network administrator is setting up a wireless network with poor security for a computer science class to hack. Which of the following security methods would be MOST easily circumvented?
- MAC filtering
- WPA
- WPA2
- Shared key
-
Given the table below:
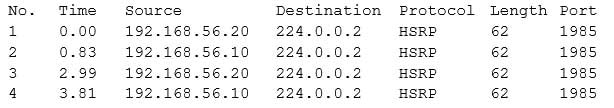
N10-007 Part 33 Q17 052 Which of the following describes the output?
- Error rate
- Network baseline
- Traffic analysis
- Port scan
-
Which of the following are reasons for enabling jumbo frames? (Choose two.)
- To increase payload size
- To increase bandwidth
- To provide additional SANs storage capacity
- To implement larger SQL queries
- To reduce CPU overhead
-
A technician set up a small network, which is not connected to the company LAN, for several employees to play a peer-to-peer networking game during breaks. The users know how to set up the software, but they do not know anything about networking. The technician has wired the network but has not configured any networking information and does not want the employees to have access outside the network. Which of the following should be used to apply addressing to the network?
- NAT
- VLSM
- APIPA
- CIDR
-
A network manager has received reports that some employees have been using the company’s WiFi to log onto their social media accounts from their personal devices. The network manager is looking for a solution to prevent this type of activity. The Chief Information Officer (CIO) wants to continue using a pre-shared key and add an additional layer of security to allow only authorized users to authenticate to the WiFi. Which of the following solutions would address this request? (Choose two.)
- Port security
- MAC filtering
- Geofencing
- 802.1X
- Proxy server
- SSO
NS – Modules 20 – 22
Subscribe
0 Comments
Newest