PT0-001 : CompTIA PenTest+ Certification Exam : Part 04
-
Which of the following excerpts would come from a corporate policy?
- Employee passwords must contain a minimum of eight characters, with one being alphanumeric.
- The help desk can be reached at 800-passwd1 to perform password resets.
- Employees must use strong passwords for accessing corporate assets.
- The corporate systems must store passwords using the MD5 hashing algorithm.
-
In which of the following scenarios would a tester perform a Kerberoasting attack?
- The tester has compromised a Windows device and dumps the LSA secrets.
- The tester needs to retrieve the SAM database and crack the password hashes.
- The tester has compromised a limited-privilege user and needs to target other accounts for lateral movement.
- The tester has compromised an account and needs to dump hashes and plaintext passwords from the system.
-
While trying to maintain persistence on a Windows system with limited privileges, which of the following registry keys should the tester use?
- HKEY_CLASSES_ROOT
- HKEY_LOCAL_MACHINE
- HKEY_CURRENT_USER
- HKEY_CURRENT_CONFIG
-
A penetration tester has a full shell to a domain controller and wants to discover any user account that has not authenticated to the domain in 21 days. Which of the following commands would BEST accomplish this?
-
dsrm -users “DN=company.com; OU=hq CN=users”
-
dsuser -name -account -limit 3
-
dsquery user -inactive 3
-
dsquery -o -rdn -limit 21
-
-
Which of the following properties of the penetration testing engagement agreement will have the LARGEST impact on observing and testing production systems at their highest loads?
- Creating a scope of the critical production systems
- Setting a schedule of testing access times
- Establishing a white-box testing engagement
- Having management sign off on intrusive testing
-
HOTSPOT
Instructions:
Given the following attack signatures, determine the attack type, and then identify the associated remediation to prevent the attack in the future.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
You are a security analyst tasked with hardening a web server.
You have been given a list of HTTP payloads that were flagged as malicious.

PT0-001 Part 04 Q06 010 Question 
PT0-001 Part 04 Q06 010 Answer -
In a physical penetration tester testing scenario. the penetration tester obtains physical access to a laptop. The laptop is logged in but locked. Which of the following is a potential NEXT step to extract credentials from the device?
- Brute force the user’s password.
- Perform an ARP spoofing attack.
- Leverage the BeEF framework to capture credentials.
- Conduct LLMNR/NETBIOS-ns poisoning.
-
A penetration tester is preparing to conduct API testing. Which of the following would be MOST helpful in preparing for this engagement?
- Nikto
- WAR
- W3AF
- Swagger
-
DRAG DROP
Instructions:
Analyze the code segments to determine which sections are needed to complete a port scanning script.
Drag the appropriate elements into the correct locations to complete the script.
If at any time you would like to bring back the initial state of the simulation, please click the reset all button.
During a penetration test, you gain access to a system with a limited user interface. This machine appears to have access to an isolated network that you would like to port scan.
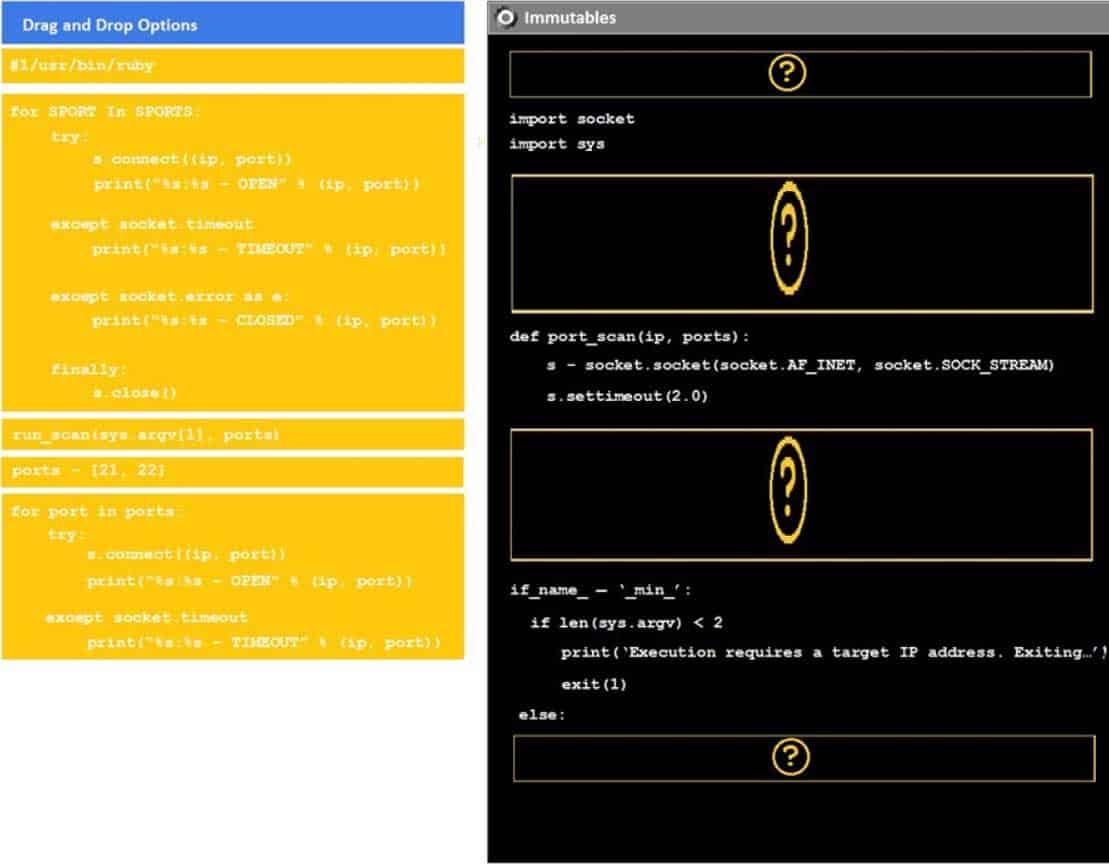
PT0-001 Part 04 Q09 011 Question 
PT0-001 Part 04 Q09 011 Answer -
If a security consultant comes across a password hash that resembles the following:
b117525b345470c29ca3d8ae0b556ba8
Which of the following formats is the correct hash type?
- Kerberos
- NetNTLMv1
- NTLM
- SHA-1
-
During an internal network penetration test, a tester recovers the NTLM password hash for a user known to have full administrator privileges on a number of target systems. Efforts to crack the hash and recover the plaintext password have been unsuccessful.
Which of the following would be the BEST target for continued exploitation efforts?
- Operating system: Windows 7
Open ports: 23, 161 - Operating system: Windows Server 2016
Open ports: 53, 5900 - Operating system: Windows 8.1
Open ports: 445, 3389 - Operating system: Windows 8
Open ports: 514, 3389
- Operating system: Windows 7
-
Which of the following would be the BEST for performing passive reconnaissance on a target’s external domain?
- Peach
- CeWL
- OpenVAS
- Shodan
-
A penetration tester delivers a web application vulnerability scan report to a client. The penetration tester rates a vulnerability as medium severity. The same vulnerability was reported as a critical severity finding on the previous report. Which of the following is the MOST likely reason for the reduced severity?
- The client has applied a hot fix without updating the version.
- The threat landscape has significantly changed.
- The client has updated their codebase with new features.
- Thera are currently no known exploits for this vulnerability.
-
An attacker uses SET to make a copy of a company’s cloud-hosted web mail portal and sends an email in hopes the Chief Executive Officer (CEO) logs in to obtain the CEO’s login credentials. Which of the following types of attacks is this an example of?
- Elicitation attack
- Impersonation attack
- Spear phishing attack
- Drive-by download attack
-
A penetration tester is scanning a network for SSH and has a list of provided targets. Which of the following Nmap commands should the tester use?
-
nmap -p 22 -iL targets -
nmap -p 22 -sL targets
-
nmap -p 22 -oG targets
-
nmap -p 22 -oA targets
-
-
A penetration tester is required to perform OSINT on staff at a target company after completing the infrastructure aspect. Which of the following would be the BEST step for penetration?
- Obtain staff information by calling the company and using social engineering techniques.
- Visit the client and use impersonation to obtain information from staff.
- Send spoofed emails to staff to see if staff will respond with sensitive information.
- Search the internet for information on staff such as social networking sites.
-
During the information gathering phase of a network penetration test for the corp.local domain, which of the following commands would provide a list of domain controllers?
-
nslookup –type=srv _ldap._tcp.dc._msdcs.corp.local -
nmap –sV –p 389 - -script=ldap-rootdse corp.local
-
net group “Domain Controllers” /domain
-
gpresult /d corp.local /r “Domain Controllers”
-
-
A penetration tester has been assigned to perform an external penetration assessment of a company. Which of the following steps would BEST help with the passive-information-gathering process? (Choose two.)
- Wait outside of the company’s building and attempt to tailgate behind an employee.
- Perform a vulnerability scan against the company’s external netblock, identify exploitable vulnerabilities, and attempt to gain access.
- Use domain and IP registry websites to identify the company’s external netblocks and external facing applications.
- Search social media for information technology employees who post information about the technologies they work with.
- Identify the company’s external facing webmail application, enumerate user accounts and attempt password guessing to gain access.
-
A client has voiced concern about the number of companies being breached by remote attackers, who are looking for trade secrets. Which of the following BEST describes the type of adversaries this would identify?
- Script kiddies
- APT actors
- Insider threats
- Hacktivist groups
-
A company contracted a firm specializing in penetration testing to assess the security of a core business application. The company provided the firm with a copy of the Java bytecode. Which of the following steps must the firm take before it can run a static code analyzer?
- Run the application through a dynamic code analyzer.
- Employ a fuzzing utility.
- Decompile the application.
- Check memory allocations.