Cybersecurity Essentials 3.0 Checkpoint Exam: Network Security Module 1 – 6 Exam Answers 2025 Full 100%
Cybersecurity Essentials 3.0 Checkpoint Exam: Network Security Module 1 – 6 Exam Answers Full 100% 2025
-
The employees in a company receive an email stating that the account password will expire immediately and requires a password reset within 5 minutes. Which statement would classify this email?
- It is a hoax.
- It is a piggy-back attack.
- It is a DDoS attack.
- It is an impersonation attack.
Explanation & Hint: Social engineering uses several different tactics to gain information from victims.
-
What three best practices can help defend against social engineering attacks? (Choose three.)
- Enable a policy that states that the IT department should supply information over the phone only to managers.
- Deploy well-designed firewall appliances.
- Do not provide password resets in a chat window.
- Educate employees regarding policies.
- Add more security guards.
- Resist the urge to click on enticing web links.
Explanation & Hint: A cybersecurity specialist must be aware of the technologies and measures that are used as countermeasures to protect the organization from threats and vulnerabilities.
-
A cyber criminal sends a series of maliciously formatted packets to the database server. The server cannot parse the packets and the event causes the server to crash. What is the type of attack the cyber criminal launches?
- SQL injection
- man-in-the-middle
- packet Injection
- DoS
Explanation & Hint: A cybersecurity specialist needs to be familiar with the characteristics of the different types of malware and attacks that threaten an organization.
-
What does the term vulnerability mean?
- a computer that contains sensitive information
- a weakness that makes a target susceptible to an attack
- a potential threat that a hacker creates
- a known target or victim machine
- a method of attack to exploit a target
Explanation & Hint: A vulnerability is not a threat, but it is a weakness that makes the PC or the software a target for attacks.
-
What is the first line of defense to protect a device from improper access control?
- passwords
- end user license agreement (EULA)
- encryption
- shredding
Explanation & Hint: Improper access control is a common data loss vector. Passwords are the first line of defense because stolen or weak passwords provide a threat actor access to machines and data on the network.
-
A social media site is describing a security breach in a sensitive branch of a national bank. In the post, it refers to a vulnerability. What statement describes that term?
- A weakness in a system or its design that could be exploited by a threat.
- The likelihood that a particular threat will exploit a vulnerability of an asset and result in an undesirable consequence.
- The potential damage to the organization that is caused by the threat.
- The actions that are taken to protect assets by mitigating a threat or reducing risk.
Explanation & Hint: Review terms and descriptions from module 2.
-
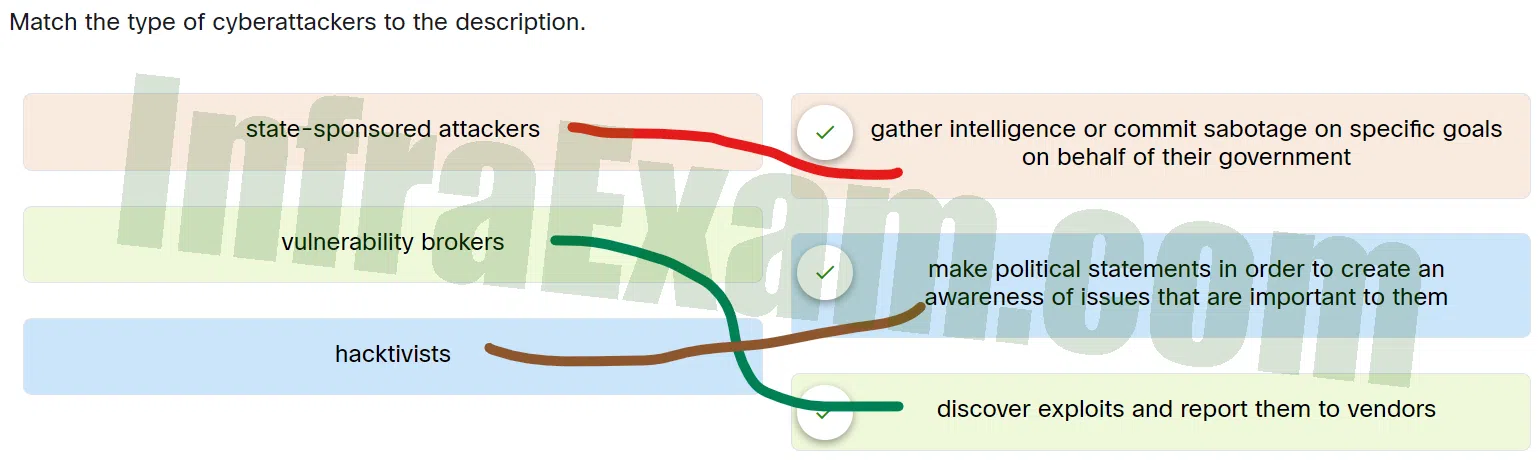
Match the type of cyberattackers to the description.
Match the type of cyberattackers to the description - state-sponsored attackers ==> Gather intelligence or commit sabotage on specific goals on behalf of their government
- vulnerability brokers ==> Discover exploits and report them to vendors
- hacktivists ==> Make political statements in order to create an awareness of issues that are important to them
Explanation & Hint: Place the options in the following order:
Hacktivists Make political statements in order to create an awareness of issues that are important to them Vulnerability brokers Discover exploits and report them to vendors State-sponsored attackers Gather intelligence or commit sabotage on specific goals on behalf of their government
-
A security service company is conducting an audit in several risk areas within a major corporate client. What attack or data loss vector term would be used to describe providing access to corporate data by gaining access to stolen or weak passwords?
- improper access control
- an internal threat
- unencrypted devices
- hard copy
Explanation & Hint: Improper access control allows the exploitation of stolen or weak passwords to gain access to corporate data.
-
Which type of network attack involves randomly opening many Telnet requests to a router and results in a valid network administrator not being able to access the device?
- man-in-the-middle
- DNS poisoning
- spoofing
- SYN flooding
Explanation & Hint: The TCP SYN Flood attack exploits the TCP three-way handshake. The threat actor continually sends TCP SYN session request packets with a randomly spoofed source IP address to an intended target. The target device replies with a TCP SYN-ACK packet to the spoofed IP address and waits for a TCP ACK packet. Those responses never arrive. Eventually the target host is overwhelmed with half-open TCP connections and denies TCP services.
-
Which three IPv4 header fields have no equivalent in an IPv6 header? (Choose three.)
- protocol
- TTL
- version
- flag
- fragment offset
- identification
Explanation & Hint: Unlike IPv4, IPv6 routers do not perform fragmentation. Therefore, all three fields supporting fragmentation in the IPv4 header are removed and have no equivalent in the IPv6 header. These three fields are fragment offset, flag, and identification. IPv6 does support host packet fragmentation through the use of extension headers, which are not part of the IPv6 header.
-
What kind of ICMP message can be used by threat actors to create a man-in-the-middle attack?
- ICMP unreachable
- ICMP mask reply
- ICMP echo request
- ICMP redirects
Explanation & Hint: Common ICMP messages of interest to threat actors include the following:
ICMP echo request and echo reply: used to perform host verification and DoS attacks
ICMP unreachable: used to perform network reconnaissance and scanning attacks
ICMP mask reply: used to map an internal IP network
ICMP redirects: used to lure a target host into sending all traffic through a compromised device and create a man-in-the-middle attack
ICMP router discovery: used to inject bogus route entries into the routing table of a target host
-
Which term describes a field in the IPv4 packet header used to detect corruption in the IPv4 header?
- header checksum
- version
- destination IPv4 address
- protocol
Explanation & Hint: The header checksum field is used to detect corruption in the IPv4 header.
-
An attacker is redirecting traffic to a false default gateway in an attempt to intercept the data traffic of a switched network. What type of attack could achieve this?
- DHCP spoofing
- ARP cache poisoning
- TCP SYN flood
- DNS tunneling
Explanation & Hint: In DHCP spoofing attacks, a threat actor configures a fake DHCP server on the network to issue DHCP addresses to clients with the aim of forcing the clients to use a false or invalid default gateway. A man-in-the-middle attack can be created by setting the default gateway address to the IP address of the threat actor.
-
Which risk management plan involves discontinuing an activity that creates a risk?
- risk retention
- risk avoidance
- risk sharing
- risk reduction
Explanation & Hint: During a risk assessment it may be determined that an activity involves more risk than benefit. In such a situation an organization may decide to avoid the risk altogether by discontinuing the activity. This is known as risk avoidance.
-
What is a vulnerability that allows criminals to inject scripts into web pages viewed by users?
- SQL injection
- XML injection
- Cross-site scripting
- buffer overflow
Explanation & Hint: Cross-site scripting (XSS) allows criminals to inject scripts that contain malicious code into web applications.
-
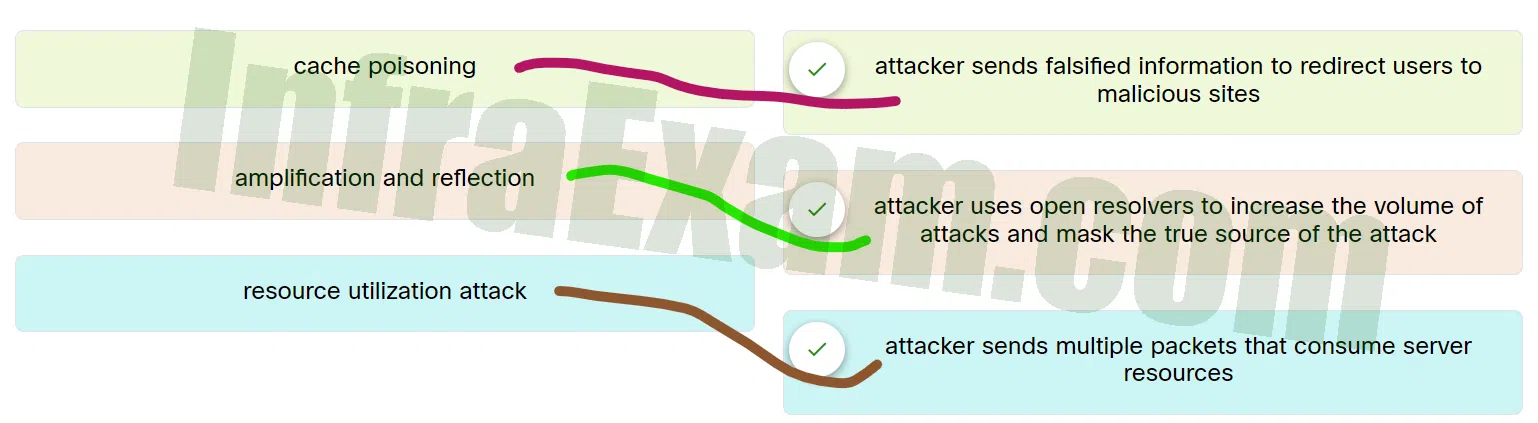
Match the attack to the definition.
Match the attack to the definition - cache poisoning ==> Attacker sends falsified information to redirect users to malicious sites
- resource utilization attack ==> Attacker sends multiple packets that consume server resources
- amplification and reflection ==> Attacker uses open resolvers to increase the volume of attacks and mask the true source of the attack
Explanation & Hint: Place the options in the following order:
Resource utilization attack Attacker sends multiple packets that consume server resources Cache poisoning Attacker sends falsified information to redirect users to malicious sites Amplification and reflection Attacker uses open resolvers to increase the volume of attacks and mask the true source of the attack
-
A network administrator of a small advertising company is configuring WLAN security by using the WPA2 PSK method. Which credential do office users need in order to connect their laptops to the WLAN?
- a user passphrase
- the company username and password through Active Directory service
- a username and password configured on the AP
- a key that matches the key on the AP
Explanation & Hint: When a WLAN is configured with WPA2 PSK, wireless users must know the pre-shared key to associate and authenticate with the AP.
-
What is a characteristic of the WLAN passive discover mode?
- The beaconing feature on the AP is disabled.
- The client must know the name of the SSID to begin the discover process.
- The client begins the discover process by sending a probe request.
- The AP periodically sends beacon frames containing the SSID.
Explanation & Hint: In passive mode, the wireless clients learn what networks and APs are available. The client learns this information from beacon frames, sent by the APs, that contain the WLAN SSID, supported standards, and security settings.
-
A user calls the help desk complaining that the password to access the wireless network has changed without warning. The user is allowed to change the password, but an hour later, the same thing occurs. What might be happening in this situation?
- weak password
- password policy
- rogue access point
- user laptop
- user error
Explanation & Hint: Man-in-the-middle attacks are a threat that results in lost credentials and data. These type of attacks can occur for different reasons including traffic sniffing.
-
Which combination of WLAN authentication and encryption is recommended as a best practice for home users?
- WEP and TKIP
- WEP and RC4
- WPA and PSK
- EAP and AES
- WPA2 and AES
Explanation & Hint: WPA2 is the Wi-Fi alliance version of 802.11i, the industry standard for authentication. Neither WEP nor WPA possess the level of authentication provided by WPA2. AES aligns with WPA2 as an encryption standard, and is stronger than TKIP or RC4. PSK refers to pre-shared passwords, an authentication method that can be used by either WPA or WPA2. EAP is intended for use with enterprise networks which use a RADIUS server.
-
What is a function of SNMP?
- synchronizes the time across all devices on the network
- captures packets entering and exiting the network interface card
- provides a message format for communication between network device managers and agents
- provides statistical analysis on packets flowing through a Cisco router or multilayer switch
Explanation & Hint: SNMP is an application layer protocol that allows administrators to manage devices on the network by providing a messaging format for communication between network device managers and agents.
-
Which statement describes a VPN?
- VPNs use virtual connections to create a private network through a public network.
- VPNs use logical connections to create public networks through the Internet.
- VPNs use dedicated physical connections to transfer data between remote users.
- VPNs use open source virtualization software to create the tunnel through the Internet.
Explanation & Hint: A VPN is a private network that is created over a public network. Instead of using dedicated physical connections, a VPN uses virtual connections routed through a public network between two network devices.
-
Which statement describes one of the rules that govern interface behavior in the context of implementing a zone-based policy firewall configuration?
- An administrator can assign an interface to multiple security zones.
- By default, traffic is allowed to flow between a zone member interface and any interface that is not a zone member.
- By default, traffic is allowed to flow among interfaces that are members of the same zone.
- An administrator can assign interfaces to zones, regardless of whether the zone has been configured.
Explanation & Hint: An interface can belong to only one zone. Creating a zone is the first step in configuring a zone-based policy firewall. A zone cannot be assigned to an interface if the zone has not been created. Traffic can never flow between an interface that is assigned to a zone and an interface that has not been assigned to a zone.
-
What are two drawbacks to using HIPS? (Choose two.)
- With HIPS, the network administrator must verify support for all the different operating systems used in the network.
- HIPS installations are vulnerable to fragmentation attacks or variable TTL attacks.
- HIPS has difficulty constructing an accurate network picture or coordinating events that occur across the entire network.
- If the network traffic stream is encrypted, HIPS is unable to access unencrypted forms of the traffic.
- With HIPS, the success or failure of an attack cannot be readily determined.
Explanation & Hint: Two disadvantages of deploying HIPS are (1) that it cannot create a complete view of the network or have knowledge of events that might be occurring beyond an individual host and (2) every host operating system within the organization must be supported. However, an advantage of using HIPS is that it can monitor and protect the operating system as well as critical system processes on each network host.
-
What type of attack targets an SQL database using the input field of a user?
- buffer overflow
- SQL injection
- XML injection
- Cross-site scripting
Explanation & Hint: A criminal can insert a malicious SQL statement in an entry field on a website where the system does not filter the user input correctly.
-
A disgruntled employee is using Wireshark to discover administrative Telnet usernames and passwords. What type of network attack does this describe?
- reconnaissance
- denial of service
- port redirection
- trust exploitation
Explanation & Hint: Wireshark is a free download that allows network packet inspection. Someone using this tool for malicious intent would be performing a reconnaissance attack. Through the capture of network packets, weak security network connectivity protocols such as Telnet can be caught, inspected, and then analyzed for detailed network information, including passwords.
-
How do cybercriminals make use of a malicious iFrame?
- The iFrame allows multiple DNS subdomains to be used.
- The attacker embeds malicious content in business appropriate files.
- The iFrame allows the browser to load a web page from another source.
- The attacker redirects traffic to an incorrect DNS server.
Explanation & Hint: An inline frame or iFrame is an HTML element that allows the browser to load a different web page from another source.
-
Which security measure is best used to limit the success of a reconnaissance attack from within a campus area network?
- Implement a firewall at the edge of the network.
- Implement restrictions on the use of ICMP echo-reply messages.
- Implement encryption for sensitive traffic.
- Implement access lists on the border router.
Explanation & Hint: The implementation of an access list may provide extra security by permitting denying a flow of traffic, but it will not provide a direct response to limit the success of the attack. The implementation of a firewall on the network edge may prevent reconnaissance attacks from the Internet, but attacks within the local network are not prevented. By implementing restrictions on the sending of ICMP echo-reply messages within a local network, devices may not respond to ping messages, but port scans are not prevented and clear-text data sent on the network are still vulnerable. The best security measure is to encrypt as much network traffic as possible, both user data and network management traffic.
-
What are the two methods that a wireless NIC can use to discover an AP? (Choose two.)
- receiving a broadcast beacon frame
- transmitting a probe request
- sending an ARP request broadcast
- sending a multicast frame
- initiating a three-way handshake
Explanation & Hint: Two methods can be used by a wireless device to discover and register with an access point: passive mode and active mode. In passive mode, the AP sends a broadcast beacon frame that contains the SSID and other wireless settings. In active mode, the wireless device must be manually configured for the SSID, and then the device broadcasts a probe request.
-
What is an IPS signature?
- It is a set of rules used to detect typical intrusive activity.
- It is the timestamp that is applied to logged security events and alarms.
- It is the authorization that is required to implement a security policy.
- It is a security script that is used to detect unknown threats.
Explanation & Hint: An IPS signature uniquely identifies specific malware, protocol anomalies, or malicious traffic. IPS sensors are tuned to look for matching signatures or abnormal traffic patterns. IPS signatures are conceptually similar to the virus.dat file used by virus scanners.
-
What name is given to hackers who hack for a cause?
- hactivist
- hacker
- white hat
- blue hat
Explanation & Hint: The term is used to describe gray hackers who rally and protect for a cause.
-
What is the workforce framework category that includes highly specialized review and evaluation of incoming cybersecurity information to determine if it is useful for intelligence?
- Analyze
- Protect and Defend
- Securely Provision
- Oversight and Development
Explanation & Hint: The “Analyze” category of the workforce framework includes specialty areas responsible for highly specialized review and evaluation of incoming cybersecurity information to determine its usefulness.
-
What does the term BYOD represent?
- bring your own disaster
- bring your own decision
- bring your own device
- buy your own disaster
Explanation & Hint: The term bring-your-own-device is used to describe mobile devices such as iPhones, smartphones, tablets, and other devices.
-
What type of an attack can disable a computer by forcing it to use memory or by overworking its CPU?
- APT
- DDoS
- exhaustion
- algorithm
Explanation & Hint: Algorithm attacks can force computers to use memory or overwork the CPU.
-
What name is given to a amateur hacker?
- script kiddie
- blue team
- black hat
- red hat
Explanation & Hint: Script kiddies is a term used to describe inexperienced hackers.
-
Pick three types of records that cyber criminals would be interested in stealing from organizations. (Choose three.)
- flight
- food
- game
- employment
- rock
- medical
- education
Explanation & Hint: The correct answers are: medical, education, employment
-
What is an example of an Internet data domain?
- Juniper
- Palo Alto
- Cisco
Explanation & Hint: A data domain is a repository for data.
-
What type of attack uses many systems to flood the resources of a target, thus making the target unavailable?
- DoS
- ping sweep
- spoof
- DDoS
Explanation & Hint: DDoS is is an attack that involves multiple systems. DoS involves only a single attack system.
-
Thwarting cyber criminals includes which of the following? (Choose two.)
- hiring hackers
- sharing cyber Intelligence information
- shutting down the network
- changing operating systems
- establishing early warning systems
Explanation & Hint: Organization can join efforts to thwart cyber crime by establishing early warning systems and sharing cyber intelligence.
-
What does the acronym IoE represent?
- Internet of Everyday
- Internet of Everything
- Intelligence on Everything
- Insight into Everything
Explanation & Hint: Internet of Everything is the term used for Internet-connected devices