DevNet Associate (Version 1.0) – DevNet Associate 1.01 Module 6 Exam Answers 2025 Full 100%
DevNet Associate (Version 1.0) – DevNet Associate 1.01 Module 6 Exam Answers Full 100% 2025
This is a collection of Cisco NetAcad DevNet Associate (Version 1.0), DevNet Associate 1.01, and DEVASC 1.01 for Module 6 Exam Answers Full 100% in 2025. Our team expert has made this series for putting all on one page to be easy to navigate and learn. This DevNet Associate module 6 exam answer is for the Cisco Netacad learning platform. Review all questions and answers before you take the exam to get a full mark of 100%.
| DevNet - DEVASC 1.0 | |
| Final Exam Answers | |
| This Modules 6 | |
| Modules 6 Exam Answers | Online Test |
| Next Modules 7 | |
| Modules 7 Exam Answers | Online Test |
DevNet Associate 1.01 – Module 6: Application Deployment and Security Exam Answers Full 100% 2025
-
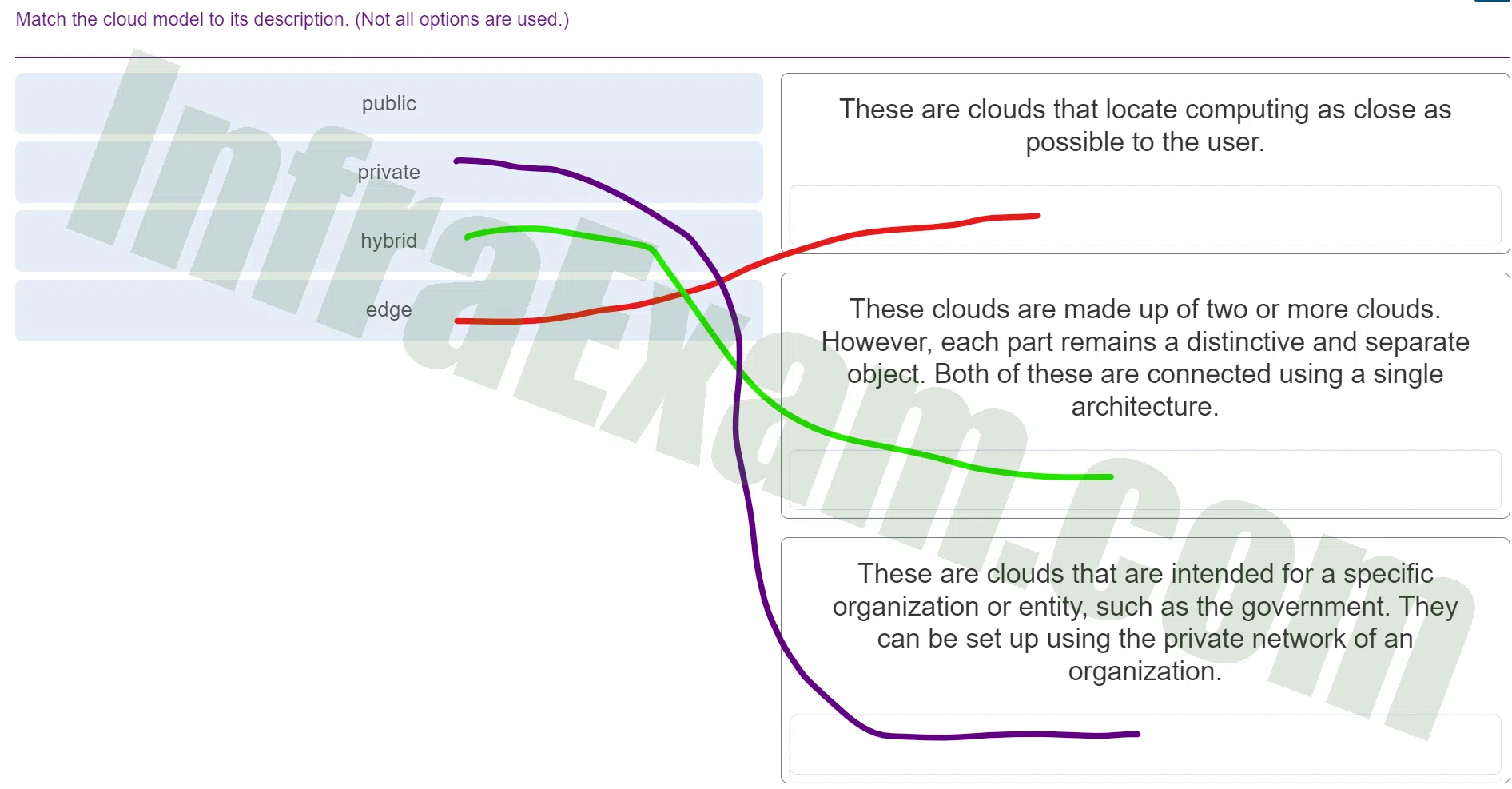
Match the cloud model to its description. (Not all options are used.)
DevNet Associate (Version 1.0) – DevNet Associate 1.01 Module 6 Exam Answers 001 -
Answers Explanation & Hint: Edge Cloud:
- Description: These clouds locate computing resources as close as possible to the user, typically at the edge of the network, to reduce latency and improve performance for applications that require real-time processing. Edge clouds are used to process data closer to the source, such as IoT devices or mobile devices, rather than sending all data to a centralized data center.
Hybrid Cloud:
- Description: A hybrid cloud is composed of two or more separate cloud environments, which could be a combination of public, private, or on-premises clouds. Despite being distinct, these environments are connected using a single architecture to facilitate data and application portability, as well as workload distribution between different cloud types.
Private Cloud:
- Description: Private clouds are cloud environments that are dedicated to a specific organization or entity. They can be hosted on-premises or by a third-party provider and are designed to provide greater control, security, and customization options compared to public clouds. Private clouds are often used by organizations that require stringent data security or compliance with specific regulations.
Public Cloud:
- Description: While not used in the given descriptions, a public cloud is a cloud computing model where resources (such as virtual machines, storage, and applications) are provided over the internet by a third-party cloud service provider. Public clouds are shared among multiple organizations and users, offering scalability and cost-efficiency, but with potentially less control and security compared to private clouds.
These cloud models offer various benefits and are chosen based on an organization’s specific needs, priorities, and requirements for performance, control, security, and flexibility.
-
-
What is a characteristic of a virtual machine running on a PC?
- A virtual machine runs its own operating system.
- A virtual machine is not susceptible to threats and malicious attacks.
- A virtual machine needs a physical network adapter to connect to the Internet.
- The number of virtual machines that can be made available depends on the software resources of the host machine.
Answers Explanation & Hint: Each virtual machine runs its own operating system. The number of virtual machines that can be made available depends on the hardware resources of the host machine. Virtual machines are susceptible to threats and malicious attacks, like physical computers. To connect to the Internet, a virtual machine uses a virtual network adapter, that acts like a physical adapter in a physical computer, connecting through the physical adapter on the host to establish a connection to the Internet.
-
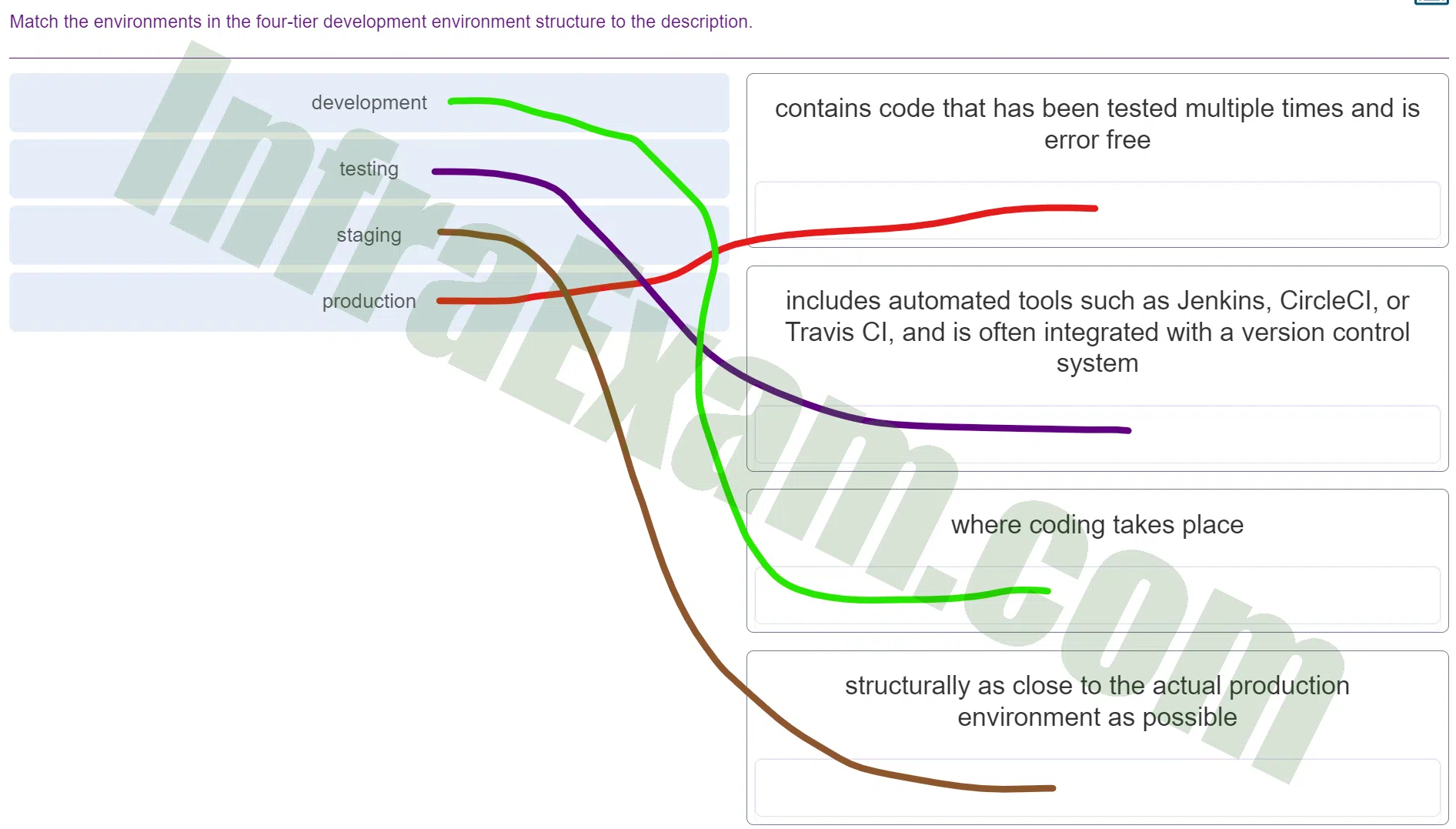
Match the environments in the four-tier development environment structure to the description.
DevNet Associate (Version 1.0) – DevNet Associate 1.01 Module 6 Exam Answers 002 -
Answers Explanation & Hint: Here’s an explanation for each of the environments in the four-tier development environment structure and their corresponding descriptions:
Production Environment:
- Description: Contains code that has been tested multiple times and is error-free.
- Explanation: The production environment is where the final version of the software or application is deployed for actual use by users. It’s expected to be stable, reliable, and thoroughly tested to ensure that it functions correctly and doesn’t contain any critical errors.
Testing Environment:
- Description: Includes automated tools such as Jenkins, CircleCI, or Travis CI, and is often integrated with a version control system.
- Explanation: The testing environment is where software undergoes various types of testing to identify and fix bugs and issues. Automated tools like Jenkins, CircleCI, or Travis CI are used to automate the testing process and ensure that code changes do not introduce new problems. Version control integration helps manage and track changes in the codebase.
Development Environment:
- Description: Where coding takes place.
- Explanation: The development environment is where software developers write, modify, and test code. It’s the primary workspace for developers, where they create new features, fix bugs, and make improvements to the software.
Staging Environment:
- Description: Structurally as close to the actual production environment as possible.
- Explanation: The staging environment is a near-replica of the production environment. It serves as a final testing ground before deploying code to production. By mimicking the production setup, developers can identify any issues that may arise when the software is deployed to the live environment.
These different environments serve distinct purposes within the software development lifecycle, helping to ensure that the software is developed, tested, and deployed in a controlled and efficient manner, ultimately leading to a reliable and high-quality end product.
-
-
Which technology is used to containerize applications and allows them to run in a variety of environments?
- Docker
- VirtualBox
- Cisco DNA
- GitHub
-
Answers Explanation & Hint: Docker is a technology designed to make it easier to create, deploy, and run applications by using containers. Containers allow a developer to package an application with all of the parts the application needs to run in most any environment.
-
What is used to isolate the different parts of a running container?
- wrappers
- namespaces
- control groups
- union file systems
-
Answers Explanation & Hint: Containers use namespaces to define and isolate each part of an application within a container.
-
What is a philosophy for software deployment used in the field of DevOps?
- CI/CD
- OWASP
- DevNet
- SOAP
-
Answers Explanation & Hint: CI/CD (continuous integration/continuous delivery) is a philosophy for software deployment that figures prominently in the field of DevOps.
-
What is a characteristic of the blue-green upgrade deployment strategy?
- A new environment is created with the new code in it, while the old environment is held in reserve in case users experience problems.
- The code changes are periodically rolled out in such a way that they do not impact current users.
- The new code version is first rolled out to a subset of users. Changes can then be rolled back if the users experience any problems.
- The new code is deployed all at once to the old environment. If users experience no issues, it is then moved to the new environment.
-
Answers Explanation & Hint: With a blue-green deployment, an entirely new environment (blue) is created with the new code in it. The old environment (green) is held in reserve so if users in the new environment experience problems, traffic can be diverted back to the original environment. If there are no problems, the new environment becomes the production environment.
-
In software development, what is the purpose of a jump box?
- to act as a single trusted machine used to launch connections to sensitive systems
- to filter packets based on Layer 3 and Layer 4 addressing
- to receive incoming requests and forward them to multiple servers
- to make all requests originating from within a network look like they come from the same source IP address
-
Answers Explanation & Hint: A jump box is a server that users must first access in order to launch a connection to a target system. Because the jump box is the trusted machine for accessing sensitive systems, it provides an additional layer of security.
-
Which security device is used to make responses to client requests look like they all come from the same server?
- reverse proxy
- forward proxy
- jump box
- stateful firewall
-
Answers Explanation & Hint: The job of a reverse proxy is to make sure responses look like they all come from the same server. This is the opposite of a forward proxy, which makes requests from multiple computers look like they all come from the same client.
-
Which attack involves the insertion of malicious code into SQL statements?
- SQL injection
- brute force
- cross-site scripting
- local file inclusion
-
Answers Explanation & Hint: SQL injection (SQLi) is basic web application attack technique where the attacker places malicious SQL code into a field on a web page and the server-side code submits it to the database without sanitizing it first. An SQLi attack, if successful, can delete or change sensitive data or reveal it to the attacker.
-
Which characters are used to separate batched SQL statements?
- semicolons ;
- colons :
- pound signs #
- parentheses ( )
-
Answers Explanation & Hint: A batch of SQL statements is a group of two or more SQL statements separated by semicolons.
-
Which technique is used to help mitigate SQL injection attacks?
- limiting the read access to specific fields of a table or joins of tables
- assigning DBA or admin access rights to the application account
- using the same owner or admin account in the web applications to connect to the database
- using stored procedures with the “db_owner” default role
-
Answers Explanation & Hint: Recommended practices for defending against SQL injection include the following:
Not assigning DBA or admin type access rights to application accounts
Avoid using the same owner/admin account in the web applications to connect to the database
Limiting the read access to specific fields of a table or joins of tables
Not assigning db_owner rights to stored procedures
-
Which mitigation method is effective against cross-site scripting?
- sanitizing untrusted content
- consistent hardening of systems and applications
- requiring multifactor authentication
- using only necessary features and secure packages downloaded from official sources and verified with a signature
-
Answers Explanation & Hint: Cross-site scripting occurs when an attacker uses the dynamic functions of a site to inject malicious content into a page. Mitigating the attacks requires careful consideration of where untrusted content is included on a page, as well as sanitizing any untrusted content.
-
Which statement is a characteristic of the broken access control threat to web applications?
- It allows users to circumvent existing authentication requirements.
- It allows attackers to steal sensitive information such as passwords or personal information.
- It allows attackers to access, and potentially change, serialized versions of data and objects.
- It allows an attacker to use the dynamic functions of a site to inject malicious content into the page.
-
Answers Explanation & Hint: Broken access control can occur if a developer builds an application that enables users to circumvent existing authentication requirements. Developers must make sure to protect all resources and functions that need to be protected on the server side, ensuring that all access is authorized.
-
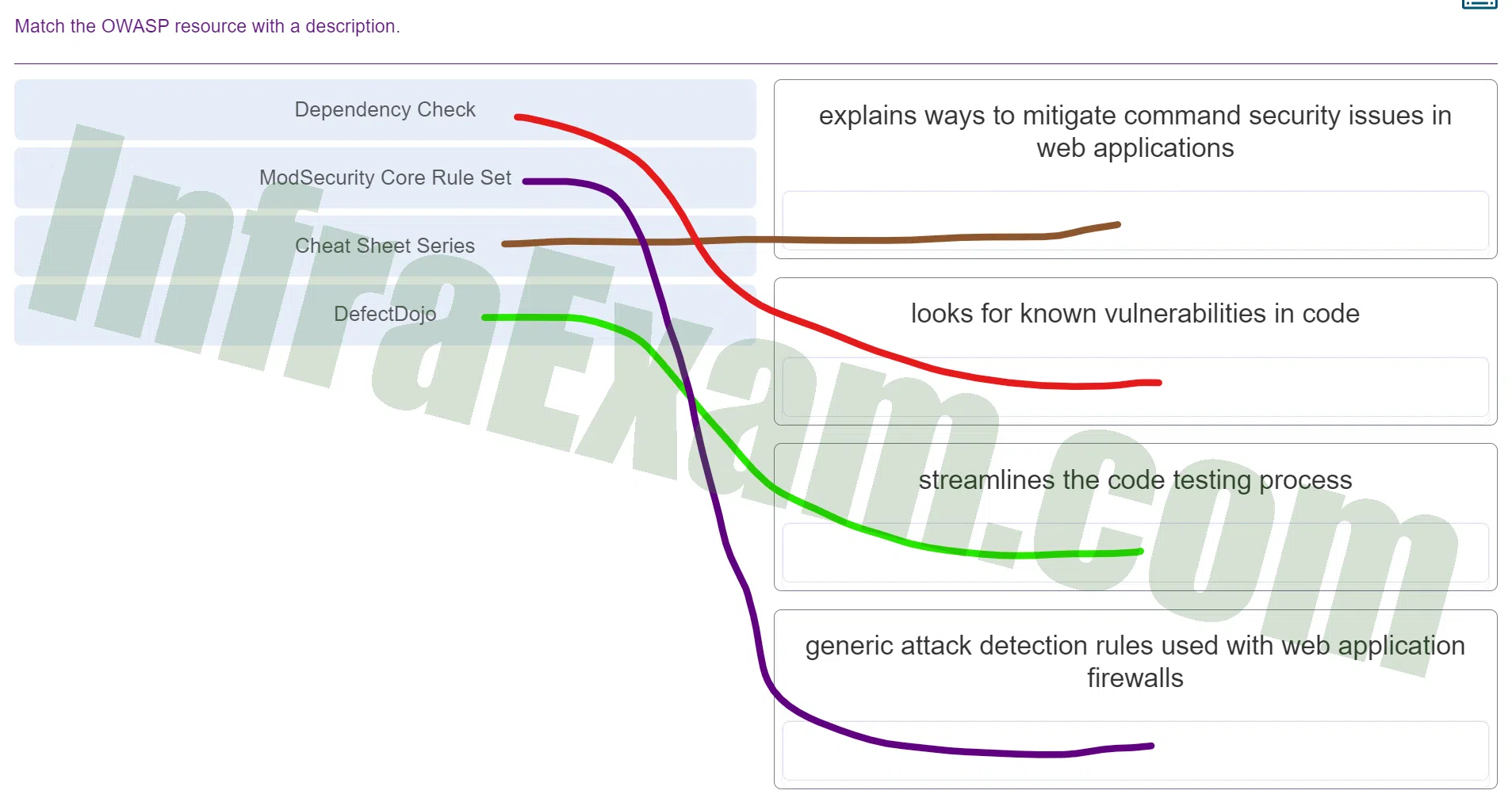
Match the OWASP resource with a description.
DevNet Associate (Version 1.0) – DevNet Associate 1.01 Module 6 Exam Answers 003 -
Answers Explanation & Hint: Cheat Sheet Series:
- Description: Explains ways to mitigate command security issues in web applications.
- Explanation: The OWASP Cheat Sheet Series provides concise and practical guidance on how to prevent and mitigate common security vulnerabilities in web applications. In this context, the cheat sheets related to command security issues offer developers quick and actionable recommendations to prevent security vulnerabilities related to command execution and injection attacks.
Dependency Check:
- Description: Looks for known vulnerabilities in code.
- Explanation: OWASP Dependency-Check is a tool that helps identify known vulnerabilities in software dependencies (third-party libraries and components) used in a project. It scans project dependencies and checks them against a database of known vulnerabilities, helping developers identify and address potential security issues in the software supply chain.
DefectDojo:
- Description: Streamlines the code testing process.
- Explanation: OWASP DefectDojo is an open-source application vulnerability management tool. It helps security teams and developers manage the entire software vulnerability assessment process by providing a platform to track, manage, and prioritize security findings. DefectDojo streamlines the testing process by centralizing vulnerability data, facilitating collaboration, and enabling efficient vulnerability remediation.
ModSecurity Core Rule Set:
- Description: Generic attack detection rules used with web application firewalls.
- Explanation: The ModSecurity Core Rule Set (CRS) is a set of generic attack detection rules for the ModSecurity web application firewall (WAF). These rules are designed to provide protection against common web application security threats, such as SQL injection, cross-site scripting (XSS), and other malicious activities. By using the CRS, organizations can enhance the security of their web applications by detecting and blocking various types of attacks.
These OWASP resources play important roles in helping developers and security professionals address and mitigate security vulnerabilities in web applications, ensuring that software is developed and deployed with a higher level of security and resilience against potential threats.
-
| DevNet - DEVASC 1.0 | |
| Final Exam Answers | |
| This Modules 6 | |
| Modules 6 Exam Answers | Online Test |
| Next Modules 7 | |
| Modules 7 Exam Answers | Online Test |