312-39 : Certified SOC Analyst : Part 03
-
A type of threat intelligent that find out the information about the attacker by misleading them is known as __________.
- Threat trending Intelligence
- Detection Threat Intelligence
- Operational Intelligence
- Counter Intelligence
-
Chloe, a SOC analyst with Jake Tech, is checking Linux systems logs. She is investigating files at /var/log/wtmp.
What Chloe is looking at?
- Error log
- System boot log
- General message and system-related stuff
- Login records
-
Which of the following threat intelligence is used by a SIEM for supplying the analysts with context and “situational awareness” by using threat actor TTPs, malware campaigns, tools used by threat actors.
1. Strategic threat intelligence
2. Tactical threat intelligence
3. Operational threat intelligence
4. Technical threat intelligence- 2 and 3
- 1 and 3
- 3 and 4
- 1 and 2
-
Properly applied cyber threat intelligence to the SOC team help them in discovering TTPs.
What does these TTPs refer to?
- Tactics, Techniques, and Procedures
- Tactics, Threats, and Procedures
- Targets, Threats, and Process
- Tactics, Targets, and Process
-
Which of the following data source can be used to detect the traffic associated with Bad Bot User-Agents?
- Windows Event Log
- Web Server Logs
- Router Logs
- Switch Logs
-
Daniel is a member of an IRT, which was started recently in a company named Mesh Tech. He wanted to find the purpose and scope of the planned incident response capabilities.
What is he looking for?
- Incident Response Intelligence
- Incident Response Mission
- Incident Response Vision
- Incident Response Resources
-
John, a SOC analyst, while monitoring and analyzing Apache web server logs, identified an event log matching Regex /(\.|(%|%25)2E)(\.|(%|%25)2E)(\/|(%|%25)2F|\\|(%|%25)5C)/i.
What does this event log indicate?
- XSS Attack
- SQL injection Attack
- Directory Traversal Attack
- Parameter Tampering Attack
-
According to the Risk Matrix table, what will be the risk level when the probability of an attack is very high, and the impact of that attack is major?
NOTE: It is mandatory to answer the question before proceeding to the next one.
- High
- Extreme
- Low
- Medium
-
Jason, a SOC Analyst with Maximus Tech, was investigating Cisco ASA Firewall logs and came across the following log entry:
May 06 2018 21:27:27 asa 1: %ASA -5 – 11008: User ‘enable_15’ executed the ‘configure term’ command
What does the security level in the above log indicates?
- Warning condition message
- Critical condition message
- Normal but significant message
- Informational message
-
What is the correct sequence of SOC Workflow?
- Collect, Ingest, Validate, Document, Report, Respond
- Collect, Ingest, Document, Validate, Report, Respond
- Collect, Respond, Validate, Ingest, Report, Document
- Collect, Ingest, Validate, Report, Respond, Document
-
Wesley is an incident handler in a company named Maddison Tech. One day, he was learning techniques for eradicating the insecure deserialization attacks.
What among the following should Wesley avoid from considering?
- Deserialization of trusted data must cross a trust boundary
- Understand the security permissions given to serialization and deserialization
- Allow serialization for security-sensitive classes
- Validate untrusted input, which is to be serialized to ensure that serialized data contain only trusted classes
-
An attacker, in an attempt to exploit the vulnerability in the dynamically generated welcome page, inserted code at the end of the company’s URL as follows:
http://technosoft.com.com/<script>alert(“WARNING: The application has encountered an error”);</script>.
Identify the attack demonstrated in the above scenario.
- Cross-site Scripting Attack
- SQL Injection Attack
- Denial-of-Service Attack
- Session Attack
-
Which of the following formula represents the risk levels?
- Level of risk = Consequence × Severity
- Level of risk = Consequence × Impact
- Level of risk = Consequence × Likelihood
- Level of risk = Consequence × Asset Value
-
In which of the following incident handling and response stages, the root cause of the incident must be found from the forensic results?
- Evidence Gathering
- Evidence Handling
- Eradication
- Systems Recovery
-
Jane, a security analyst, while analyzing IDS logs, detected an event matching Regex /((\%3C)|<)((\%69)|i|(\%49))((\%6D)|m|(\%4D))((\%67)|g|(\%47))[^\n]+((\%3E)|>)/|.
What does this event log indicate?
- Directory Traversal Attack
- Parameter Tampering Attack
- XSS Attack
- SQL Injection Attack
-
Which of the following Windows Event Id will help you monitors file sharing across the network?
- 7045
- 4625
- 5140
- 4624
-
The threat intelligence, which will help you, understand adversary intent and make informed decision to ensure appropriate security in alignment with risk.
What kind of threat intelligence described above?
- Tactical Threat Intelligence
- Strategic Threat Intelligence
- Functional Threat Intelligence
- Operational Threat Intelligence
-
Identify the type of attack, an attacker is attempting on www.example.com website.
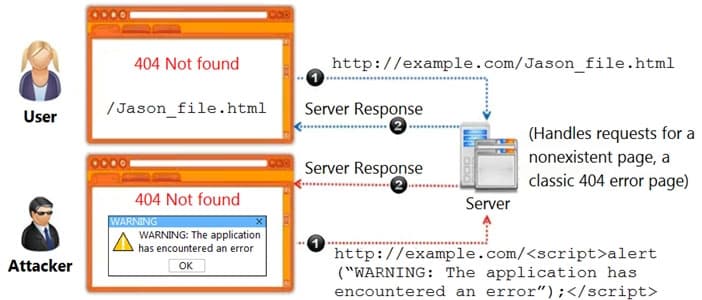
312-39 Part03 Q18 002 - Cross-site Scripting Attack
- Session Attack
- Denial-of-Service Attack
- SQL Injection Attack
-
Which of the following fields in Windows logs defines the type of event occurred, such as Correlation Hint, Response Time, SQM, WDI Context, and so on?
- Keywords
- Task Category
- Level
- Source
-
Which of the following tool is used to recover from web application incident?
- CrowdStrike FalconTM Orchestrator
- Symantec Secure Web Gateway
- Smoothwall SWG
- Proxy Workbench
Subscribe
0 Comments
Newest