7.3.3 Quiz – Cloud, Mobile, and IoT Security Answers 2025 Full 100%
7.3.3 Quiz – Cloud, Mobile, and IoT Security Answers Full 100% 2025
The 7.3.3 Quiz – Cloud, Mobile, and IoT Security Answer 2025 is an essential assessment in the Cisco NetAcad curriculum, focusing on modern security challenges in cloud computing, mobile devices, and the Internet of Things (IoT). As enterprises increasingly adopt these technologies, understanding their vulnerabilities and implementing robust security measures is crucial. This quiz tests knowledge of cloud security models, mobile device management (MDM), IoT threats, encryption methods, and best practices for securing distributed environments. Below, you’ll find the latest and verified 100% correct answers for 2025, helping you prepare effectively and boost your cybersecurity expertise.
-
Which term is an essential characteristic of cloud computing as defined in NIST SP 800-145?
- centralized storage
- resource pooling
- reduced bandwidth requirements
- slow elasticity
Explanation & Hint: NIST SP 800-145 defines cloud computing as “a model for enabling ubiquitous, convenient, on-demand network access to a shared pool of configurable computing resources that can be rapidly provisioned and released with minimal management effort or service provider interaction.”
The five essential characteristics of cloud computing are:
- On-demand self-service
- Broad network access
- Resource pooling
- Rapid elasticity
- Measured service
-
Which cloud technology attack method involves breaching the infrastructure to gather and steal information such as valid usernames, passwords, tokens, and PINs?
- account takeover
- credential harvesting
- privilege escalation
- side-channel attacks
Explanation & Hint: Credential harvesting is the act of gathering and stealing valid usernames, passwords, tokens, PINs, and any other types of credentials through infrastructure breaches.
-
Which cloud technology attack method could exploit a bug in a software application to gain access to resources that normally would not be accessible to a user?
- account takeover
- credential harvesting
- privilege escalation
- side-channel attacks
Explanation & Hint: Privilege escalation is exploiting a bug or design flaw in a software or firmware application to access resources normally protected from an application or a user.
-
Which term describes when a lower-privileged user accesses functions reserved for higher-privileged users?
- vertical privilege escalation
- horizontal privilege escalation
- credential harvesting
- metadata service attacks
Explanation & Hint: Vertical privilege escalation occurs when a lower-privileged user accesses functions reserved for higher-privileged users (for example, a standard user accessing functions of an administrator).
-
Which cloud technology attack method could a threat actor use to access a user or application account that allows access to more accounts and information?
- account takeover
- metadata service attacks
- resource exhaustion and DoS attacks
- side-channel attacks
Explanation & Hint: In an account takeover attack, the threat actor gains access to a user or application account and uses it to access more accounts and information.
-
Which tool could be used to find vulnerabilities that could lead to metadata service attacks?
- Nimbostratus
- Clair
- Falco
- Dagda
Explanation & Hint: Tools such as nimbostratus (https://github.com/andresriancho/nimbostratus) can be used to find vulnerabilities that could lead to metadata service attacks.
-
Which cloud technology attack method could generate crafted packets to cause a cloud application to crash?
- resource exhaustion attack
- account takeover
- metadata service attack
- side-channel attack
Explanation & Hint: Threat actors can launch strategic DoS attacks against applications hosted in the cloud that could lead to resource exhaustion. For example, they can leverage a single-packet DoS vulnerability in network equipment used in cloud environments, or they can leverage tools to generate crafted packets to cause an application to crash.
-
Which cloud technology attack method would require the threat actor to create a malicious application and install it into a SaaS, PaaS, or IaaS environment?
- resource exhaustion attack
- account takeover
- metadata service attack
- cloud malware injection attack
Explanation & Hint: In a cloud malware injection attack, the attacker creates a malicious application and injects it into a SaaS, PaaS, or IaaS environment. Once the malware injection is completed, the malware is executed as one of the valid instances running in the cloud infrastructure. Subsequently, the attacker can leverage this foothold to launch additional attacks, such as covert channels, backdoors, eavesdropping, data manipulation, and data theft.
-
What is a common cause of data breaches in attacks against misconfigured cloud assets?
- using insecure permission configurations for cloud object storage services
- using hard-coded credentials to access different services
- implementing metadata service to get a set of temporary access credentials
- adding sensitive information in user startup scripts
Explanation & Hint: Insecure permission configurations for cloud object storage services, such as Amazon’s AWS S3 buckets, often cause data breaches.
-
A threat actor has compromised a VM in a cloud environment that shares the same physical hardware as non-compromised VMs. Which cloud technology attack method could now be used to exfiltrate credentials, cryptographic keys, and other sensitive information?
- side-channel attack
- cloud malware injection attack
- resource exhaustion attack
- account takeover
Explanation & Hint: Side-channel attacks are often based on information gained from implementing the underlying computer system (or cloud environment) instead of a specific weakness in the implemented technology or algorithm.
-
Which tool helps software developers and cloud consumers deploy applications in the cloud and use the resources that the cloud provider offers?
- Software development kits (SDKs)
- Cloud development kits (CDKs)
- Identity and access management (IAM)
- Nimbostratus
Explanation & Hint: Cloud development kits (CDKs) help software developers and cloud consumers deploy applications in the cloud and use the resources that the cloud provider offers.
-
Which mobile device vulnerability is targeted when a threat actor reverse engineers a mobile app to see how it creates and stores keys in the iOS Keychain?
- insecure storage
- passcode vulnerabilities and biometric integrations
- certificate pinning
- using known vulnerable components
Explanation & Hint: An attacker could use static analysis or reverse engineering to see how applications create and store keys in the iOS Keychain.
-
Which tool is an open-source framework used to test the security of iOS applications?
- Needle
- Drozer
- APK Studio
- ApkX
Explanation & Hint: Needle is an open-source framework used to test the security of iOS applications. Drozer, APK Studio, and ApkX are Android testing tools.
-
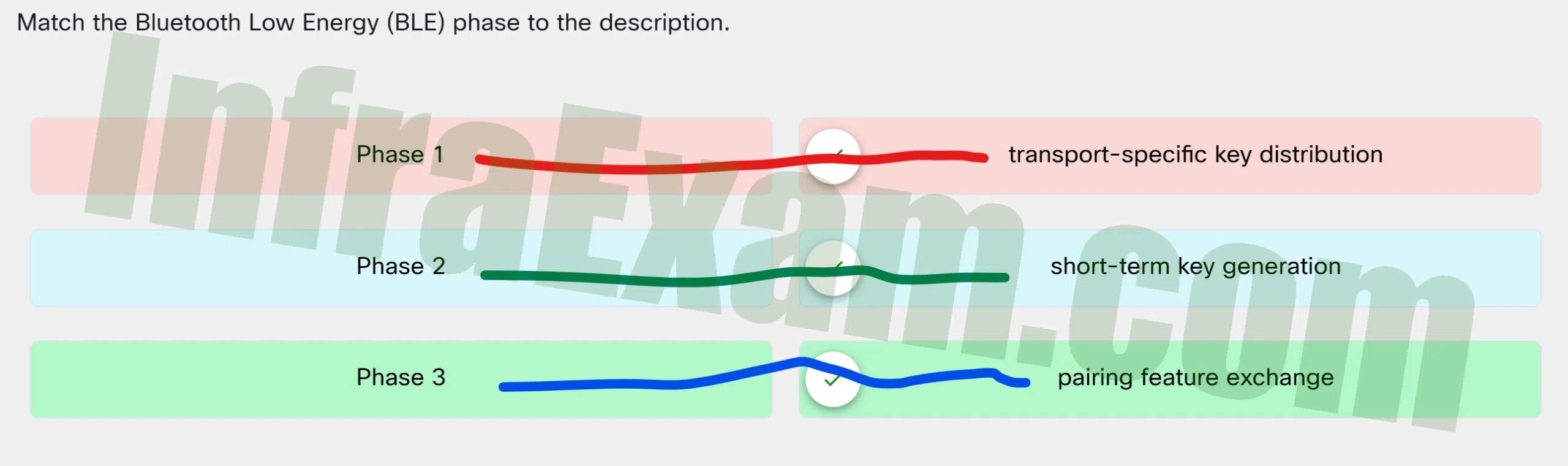
Match the Bluetooth Low Energy (BLE) phase to the description.
Match the Bluetooth Low Energy (BLE) phase to the description - Phase 1 ==> Transport-specific key distribution
- Phase 2 ==> Short-term key generation
- Phase 3 ==> Pairing feature exchange
Explanation & Hint: Place the options in the following order:
Phase 1 Transport-specific key distribution Phase 2 Short-term key generation Phase 3 Pairing feature exchange
-
Which option is a security vulnerability that affects IoT implementations?
- plaintext communication and data leakage
- VM escape vulnerabilities
- certificate pinning
- hyperjacking
Explanation & Hint: Common IoT security vulnerabilities include:
- Insecure defaults
- Plaintext communication and data leakage
- Hard-coded configurations
- Outdated firmware/hardware and the use of insecure or outdated components
-
Which two IoT systems should never be exposed to the Internet? (Choose two.)
- turbines in a power plant
- robots in a factory
- refrigerators in a restaurant
- thermostat in a home
- carbon monoxide detectors in a home
Explanation & Hint: Many IoT, ICS, and SCADA systems should never be exposed to the Internet. For example, programmable logic controllers (PLCs) controlling turbines in a power plant, stadium lighting, and factory robots should never be exposed to the Internet.
-
Which option is a collection of compute interface specifications designed to offer management and monitoring capabilities independently of the CPU, firmware, and operating system of the host?
- Intelligent Platform Management Interface (IPMI)
- Shodan
- Supervisory control and data acquisition (SCADA)
- Mobile Security Framework (MobSF)
Explanation & Hint: The Intelligent Platform Management Interface (IPMI) is a collection of compute interface specifications (often used by IoT systems) designed to offer management and monitoring capabilities independently of the host system’s CPU, firmware, and operating system.
-
A threat actor uploaded a VM with malicious software to the VMware Marketplace. When an organization deploys the VM, the threat actor can manipulate the systems, applications, and user data. What type of VM vulnerability has been enabled?
- VM repository vulnerability
- Hypervisor vulnerability
- Hyperjacking
- VM escape vulnerability
Explanation & Hint: A VM repository vulnerability is when a threat actor has found a way to upload fake or impersonated VMs with malicious software and backdoors. These ready-to-use VMs are deployed by many organizations, allowing the threat actor to manipulate the systems, applications, and data of the user.
-
Which tool is a set of open-source analysis tools that uses the ClamAV antivirus engine to help detect vulnerabilities, Trojans, backdoors, and malware in Docker images and containers?
- Anchore’s Grype
- Clair
- Dagda
- Falco
Explanation & Hint: Dagda is a set of open-source static analysis tools that can help detect vulnerabilities, Trojans, backdoors, and malware in Docker images and containers. It uses the ClamAV antivirus engine to detect malware and vulnerabilities.
-
Which credential harvesting tool could be used to send a spear phishing email with a link to a malicious site to a target victim?
- Social-Engineer Toolkit (SET)
- Searchsploit
- Drozer
- Dagda
Explanation & Hint: The Social-Engineer Toolkit (SET) can perform a social engineering attack and instantiate a fake website to perform a credential harvesting attack.
-
Why do cloud architectures help minimize the impact of DoS or DDoS attacks compared to hosting services on-premise?
- cloud providers use a distributed architecture
- cloud providers provide sandbox analysis
- cloud providers limit network exposure to the internet
- cloud providers use Intelligent Platform Management Interfaces (IPMI)
Explanation & Hint: One of the benefits of leveraging cloud services is the distributed and resilient architecture that most leading cloud providers offer. This architecture helps minimize the impact of a DoS or distributed denial-of-service (DDoS) attack compared to what it would be if you were hosting your application on-premises in your data center.
-
Which option is a characteristic of a VM hypervisor?
- Type 1 hypervisors are also known as native or bare-metal hypervisors.
- Type 1 hypervisors run on top of other operating systems.
- Type 2 hypervisors include VMware ESXi and Microsoft Hyper-V.
- Type 2 hypervisors run directly on the physical (bare-metal) system.
Explanation & Hint: There are two types of hypervisors:
- Type 1 hypervisors (native or bare-metal hypervisors) run directly on the physical (bare-metal) system. Examples of Type 1 hypervisors include VMware ESXi, Proxmox Virtual Environment, Xen, and Microsoft Hyper-V.
- Type 2, or hosted, hypervisors run on top of other operating systems. Examples of type 2 hypervisors include VirtualBox and VMware Player or Workstation.
-
A threat actor has compromised a VM in a data center and discovered a vulnerability that provides access to data in another VM. What type of VM vulnerability has been discovered?
- VM escape vulnerability
- VM repository vulnerability
- Hypervisor vulnerability
- Hyperjacking
Explanation & Hint: VM escape vulnerabilities allow a threat actor to “escape” the VM and obtain access to other virtual machines on the system or access to the hypervisor.
-
Which tool can be used to perform on-path attacks in BLE implementations?
- GATTacker
- Social-Engineer Toolkit (SET)
- Nimbostratus
- Dagda
Explanation & Hint: Tools such as GATTacker can be used to perform on-path attacks in Bluetooth Low-Energy (BLE) implementations.
-
Which tool is an open-source container vulnerability scanner that can be used to find vulnerabilities in a Docker image?
- Anchore’s Grype
- GATTacker
- Social-Engineer Toolkit (SET)
- Nimbostratus
Explanation & Hint: Anchore’s Grype is an open-source container vulnerability scanner that can be used to find vulnerabilities in a Docker image.