H12-261 : HCIE-R&S (Written) (Huawei Certified Internetwork Expert-Routing & Switching) : Part 06
-
Which of the following statements regarding the inter-AS MPLS VPN are false?
- In inter-AS VPN Option B mode, an MP-EBGP peer relationship needs to be established between two ASBRS.
- In inter-AS VPN Option B mode, two ASBR-Pes are interconnected through multiple interfaces (including sub-interfaces), each interface is associated with one VPN, and each ASBR-PE considers the remote device as a CE.
- In inter-AS VPN Option A mode, the routes advertised between two ASBRs are common IPv4 routes.
- In inter-AS VPN Option C solution 2, if only LDP is used to advertise public network labels, three labels need to be used during packet forwarding.
-
Which of the following statements regarding LDP reliability is false?
- By default, the policy for manually configuring LDP FRR specifies that backup routes with 32-bit addresses should trigger the setup of a backup LDP LSP.
- Synchronization between LDP and IGP requires suppression of IGP route advertisement to achieve consistent LDP and IGP.
- LDP FRR can generate an LSP as the backup of the primary LSP based on Label Mapping messages that are not from the optimal next hop. LDP FRR establishes forwarding entries for the backup LSP.
- LDP Graceful Restart (GR) leverages the separation of the forwarding plane and control plane by MPLS to ensure uninterrupted traffic transmission during a protocol restart or active/standby switchover.
-
The display mpls lsp command is run on a router to check LSP information. The command output is as follows:
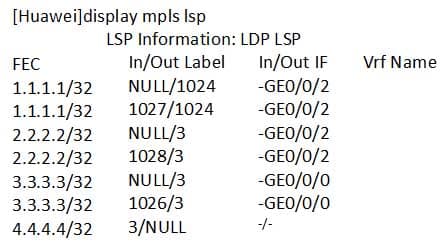
H12-261 HCIE-R&S (Written) (Huawei Certified Internetwork Expert-Routing & Switching) Part 06 Q03 019 Which of the following statements is true?
- When sending a data packet with the destination IP address 4.4.4.4, the router sends it directly without any label added.
- After receiving a data packet with label 1024, the router changes the label to label 1027 and then sends the packet.
- When sending a data packet with the destination IP address 2.2.2.2, the router sends it directly without any label added.
- When sending a data packet with the destination IP address 3.3.3.3, the router adds label 1026 to the packet before sending it.
-
If PIM-SM is enabled on a multicast network, only after multicast tress are established between the multicast source and receivers, the receiver can receive multicast data. Which of the following statements regarding the trees are true?
- An RPT is established between the RP and receivers.
- An SPT is established between the RP and receivers.
- An SPT is established between the multicast source and RP.
- An RPT is established between the multicast source and RP.
-
SSM is enabled on the entire IP multicast network. Which of the following statements regarding SSM are true?
- No RP is required.
- Only the RTP is used for SSM.
- SSM is recommended when multiple sources are available on the network and the multicast route is simple.
- SSM is applicable to one-to-many applications.
- Only the SPT is used for SSM.
-
What advantages does IGMPv2 have over IGMPv1?
- The Source-Specific Query message is added.
- The Group-Specific Query message is added.
- The Leave message is added.
- The maximum response time field is added.
-
Which of the following operations can implement fast fault detection on a multicast network?
- Shorten the holdtime of Join or Prune messages.
- Shorten the interval for sending Join or Prune messages.
- Shorten the interval of PIM Hello messages.
- Set up BFD for PM sessions between PIM SM neighbors.
-
Which of the following attacks are DoS (Denial of service) attacks?
- Single-packet attacks
- Flood attacks
- Man-in-the-middle attacks
- Source IP address spoofing attacks.
-
A Local Area Network Denial (LAND) attacker sends a SYN packet in which the source and destination addresses are the same as the target host’s address and the source port is the same as the destination port. While the receiver waits for the final ACK packet from the sender, the connection is in half-connected mode, which wastes limited TCP resources at the receive end.
- TRUE
- FALSE
-
Which of the following is not included in a digital certificate?
- Digital envelope
- Issuer
- Public key information
- Digital signature
-
Which of the following are single-packet attacks?
- Malformed packet attacks
- Special control packet attacks
- Scanning and snooping attacks
- DDoS attacks
-
A bookstore provides a wired network for customers to learn online. However, some users are suddenly unable to access the network. After troubleshooting, it is found that all the IP addresses in the DHCP address pool have been used up. Which of the following is the best way to solve the problem?
- Configure static ARP binding entries
- Configure IPSG
- Configure DAI
- Limit the maximum number of DCHP snooping binding entries that can be learned on an interface.
-
Assume that the traffic shaping rate is set to 100 Mbit/s on an interface and that the input bandwidth and PIR of each service are configured as shown in the table below.
What is the bandwidth allocated to the EF queue after the first round of scheduling?
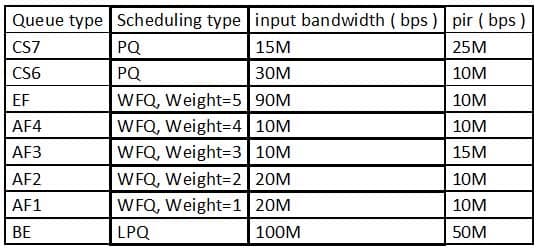
H12-261 HCIE-R&S (Written) (Huawei Certified Internetwork Expert-Routing & Switching) Part 06 Q13 020 - 30 Mbit/s
- 90 Mbit/s
- 25 Mbit/s
- 15 Mbit/s
-
The network administrator defines a traffic policy as follows:
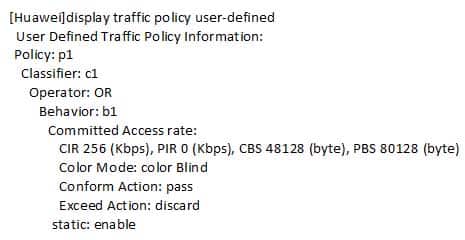
H12-261 HCIE-R&S (Written) (Huawei Certified Internetwork Expert-Routing & Switching) Part 06 Q14 021 The router port to which the traffic policy is applied has been idle for about 10 seconds. In this case, if there is suddenly a large amount of c1 burst traffic, what is the number of bytes in the green packets?
- 32 Kbytes
- 256 Kbytes
- 80128 Kbytes
- 48128 Kbytes
-
Which of the following type of SNMP messages sent to the NMS is reliable?
- Get
- GetBulk
- Trap
- Inform
- Response
-
Assume that BGP/MPLS IPv4 VPN configured with OSPF, LDP, and static routing has been deployed on a PE router. To enable the NSF function, which of the following protocols need to be configured to enable the GR function on the PE router?
- OSPF
- MPLS LDP
- BGP
- Static routing
-
The VRRP priority cannot be set to 0, so the device that sends a VRRP packet with priority 0 stops participating in the VRRP group and notifies the backup device to become the master device right away, without waiting for the Master_Down_Interval timer to expire.
- TRUE
- FALSE
-
Which of the following functions cannot be implemented using the EVPN Type2 route?
- Host MAC address advertisement
- Host ARP advertisement
- Host IP route advertisement
- BUM packet forwarding
-
Which of the following statements regarding the VXLAN gateway is false?
- VXLAN Layer 3 gateways can be classified into centralized and distributed gateways.
- VXLAN Layer 3 gateways allow their inter-subnet VXLAN communication and access to external networks.
- VXLAN Layer 2 gateways are bound to VPN instances.
- VXLAN Layer 2 gateways enable tenants to access VXLAN and are used for communication between subnets on the same VXLAN.
-
Subnets of one subnet is as follows: RT=10:10 both and TR=1000:1000 export in the EVPN instance and RT=100:100 in the VPN instance. Which of the following configurations can be made for another subnet?
- 1000:1000 both in the EVPN instance
- 1000:1000 both evpn in the VPN instance
- 10:10 both in the VPN instance
- 1000:1000 export in the EVPN instance
Subscribe
0 Comments
Newest