H12-261 : HCIE-R&S (Written) (Huawei Certified Internetwork Expert-Routing & Switching) : Part 07
-
A VXLAN tunnel can be established between two VTEPs and shared by all VXLAN Network Identifiers (VNIs) between two NVE nodes.
- TRUE
- FALSE
-
Which of the following statements regarding the IPv6 over VXLAN network is false?
- The IPv6 over VXLAN network indicates that the VXLAN overlay network is an IPv6 network.
- The IPv6 Over VXLAN network does not generate ND entries.
- Tunnels between Layer 2 and Layer 3 VXLAN gateways are deployed on an IPv4 network.
- The IPv6 over VXLAN network enables tenants to have sufficient IP address resources.
-
A Bridge Domain (BD) in a VXLAN can map to multiple VNIs.
- TRUE
- FALSE
-
Which of the following statements regarding the BFD one-arm-Echo function are true? (Choose two.)
- Local and remote discriminators must be configured for this function.
- After this function is enabled, the destination and source IP addresses of BFD packets are the same.
- This function is applicable when one device supports BFD and the other device does not.
- The default destination IP address of a BFD packet is 224.0.0.184.
-
Router HW1 functions as an MPLS LSR router on the carrier’s network. The router receives a labelled packet, but the label entry does not exist in the router’s LFIB. Given this information, how will the router process the packet?
- Router HW1 discards the packet.
- Router HW1 uses the default label to forward the packet.
- Router HW1 removes the label, searches the FIB, and uses the destination IP address to forward the packet.
- Router HW1 uses LDP to create an LSP and creates a path in its LFIB for the label carried in the packet.
-
Which of the following statements regarding the basic MPLS forwarding process is false?
- When an IP packet enters an MPLS domain, the device checks whether the tunnel ID corresponding to the destination IP address of the packet is 0x0. If so, the MPLS forwarding process starts.
- By default, the egress node supporting PHP allocates the label with the value of 3 to the penultimate hop.
- A transit node replaces a label on the top of the label stack in an MPLS packet with the label assigned by the next hop.
- When an IP packet enters an MPL5 domain, the MPLS edge device inserts a new label between the Layer 2 header and the IP header of the packet.
-
In which of the following scenarios will gratuitous ARP packets be sent?
- A host connected to the switch sends a ping packet.
- The DHCP client receives an acknowledgment message from the server
- A new host with an IP address is connected to the network.
- The master and backup devices are elected in VRRP.
-
What is the function of Route Target (RT) on an MPLS VPN?
- Allows the remote PE to determine which VPNv4 routes should not be imported to a specific VRF instance.
- Allows the remote CE to determine which VPNv4 routes be imported to a specific VRF instance.
- Allows the remote PE to determine which VPNv4 routes be imported to a specific VPN routing and forwarding (VRF) instance.
- Allows the remote CE to determine which VPNv4 routes should not be imported to a specific VRF instance.
-
The function of the Hop Limit field in an IPv6 basic header is similar to the function of which field in an IPv4 header?
- Protocol
- Time to Live
- Flags
- Identification
-
On the network shown in the figure below, SW1, SW2 and SW3 are deployed. SW1 is the root bridge, link congestion occurs between SW1 and SW2, and SW2 cannot receive configuration BPDUs sent by the root bridge. Given this information, which of the following spanning tree protection mechanisms needs to be configured to prevent problems caused by link congestion?
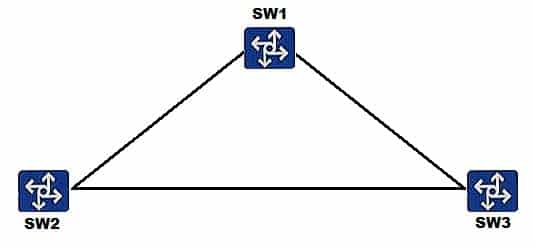
H12-261 HCIE-R&S (Written) (Huawei Certified Internetwork Expert-Routing & Switching) Part 07 Q10 022 - Defense against TC BPDU attacks
- Root protection
- BPDU protection
- Loop protection
-
Which of the following statements regarding OSPF route filtering is false?
- The filtering of Type 3 LSAs needs to be configured on ABRs in OSPF.
- In a NSSA, when external routes are imported to the OSPF router and LSAs are advertised to its neighbors, LSA filtering can be performed on the ASBR or ABR.
- All LSAs, except Grace LSAs, can be filtered based on interfaces in the inbound and outbound directions.
- When routes are calculated based on the LSDB, the filter-policy import command can be executed to filter routes. This filtering mode affects only the addition of routes in the routing table, and has no impact on the OSPF LSDB.
-
Which messages are sent to the agent by the network management station (NMS) running SNMPv1?
- Trap, Get, and Set messages
- Only Trap messages
- Get, Set, and GetNext messages
- Get, Set, and GetBulk messages
- Get, Set, and GetNext, and GetBulk messages
-
What are the differences between traffic policing and traffic shaping?
- For traffic shaping, you can adjust the usage of the buffer for the traffic that exceeds the CIR.
- For traffic policing, you can adjust the usage of the buffer for the traffic that exceeds the CIR.
- For traffic shaping, the router buffers excess packets until the bandwidth is available again.
- Traffic policing uses the token bucket algorithm and traffic shaping uses the SPD algorithm.
- Traffic shaping is applied in the inbound direction and traffic policing is applied in the outbound direction.
-
Which of the following statements regarding URPF, IPSG, and DAI are false?
- IPSG checks the source IP addresses and source MAC addresses of IP packets, and DAI checks only the mapping between IP addresses and MAC addresses.
- DAI binding entries cannot be manually configured.
- URPF can be used to defend against DDoS attacks from forged sources.
- IPSG checks IP packets to defend against attacks using spoofed source IP addresses, and DAI checks ARP packets to filter out attack sources.
-
By default, WRED is configured on a newly deployed Huawei router. Which of following statements regarding WRED are true?
- When traffic exceeds the minimum threshold, WRED starts to discard all inbound traffic (tail drop).
- Traffic with low bandwidth is more likely to be discarded than traffic with high bandwidth.
- WRED selectively discards multiple TCP flows to avoid global synchronization.
- WRED can be used to set different drop thresholds and packet loss rations for data packets with different priorities.
-
Which of the following statements regarding RADIUS are true?
- Authentication, authorization, and accounting are separated in RADIUS protocol.
- RADIUS authentication, and Portal authentication cannot be used together because users can be authenticated using the Portal server when Portal authentication is enabled.
- MAC address authentication does not require a user name and password. Therefore, users cannot be authenticated through RADIUS when using MAC address authentication.
- RADIUS supports user access in wired and wireless modes.
-
Router HW1 and Router HW2 are connected to Network A and Network B respectively. Referring to the figure, if you want to set up an IPsec VPN tunnel between HW1 and HW2, which of the following ACL rules needs to be configured on HW1 to transmit the traffic across networks A and B pass through the encrypted VPN tunnel?
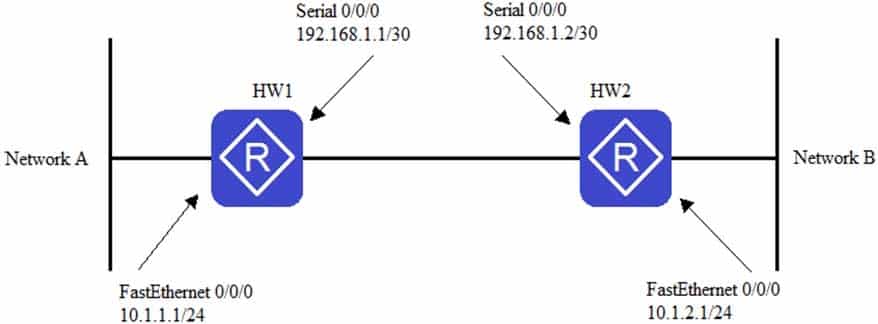
H12-261 HCIE-R&S (Written) (Huawei Certified Internetwork Expert-Routing & Switching) Part 07 Q17 023 - rule permit ip source 10.1.2.0.0.0.0.255 destination 10.1.1.0.0.0.0.255
- rule permit ip source 10.1.1.0.0.0.0.255 destination 10.1.2.0.0.0.0.255
- rule permit ip source 10.1.1.0.0.0.0.255 destination 192.168.1.2.0
- rule permit ip source 192.168.1.1.0 destination 10.1.2.0.0.0.0.255
- rule permit ip source 192.168.1.1.0 destination 192.168.1.2.0
-
The HTTP protocol is based on TCP. Therefore, TCP flood attacks and HTTP flood attacks are defended against in the same way.
- TRUE
- FALSE
-
A DR needs to be elected from a set of candidate PIM-SM routers for multicast data forwarding on the source side or the receiver side. Which of the following statements regarding DR election rules is true?
- The PIM-SM router with the lowest DR priority is elected as the DR.
- The PIM-SM router with the smallest IP address is elected as the DR.
- The PIM-SM router with the longest interface mask is elected as the DR.
- DR priorities of the PIM-SM routers are compared first. If their DR priorities are the same, their interface IP addresses are then compared.
-
If PIM-SM is enabled on a multicast network, an RP needs to be configured. The RP can be configured as a dynamic or static RP. Which of the following statements regarding RP configuration is true?
- No BSR needs to be configured when a dynamic RP is configured.
- When a static RP is configured, you need to configure a BSR that advertises RP information.
- The BSR needs to be configured as the RP backup when a dynamic RP is configured.
- RP information needs to be specified on all PIM routers when a static RP is configured.
Subscribe
0 Comments
Newest