H12-261 : HCIE-R&S (Written) (Huawei Certified Internetwork Expert-Routing & Switching) : Part 12
-
In inter-AS VPN Option B mode, two Autonomous System Boundary Routers (ASBRs) need to exchange public network LSP labels once during packet forwarding.
- TRUE
- FALSE
-
A network administrator plans to migrate IGMPv2 to IGMPv3 on the multicast network. What advantages does IGMPv3 have over IGMPv2?
- IGMPv3 deletes suppression of IGMPv3 Membership Report messages
- IGMPv3 deletes the function of matching all sources through wildcard belong to specific multicast group
- IGMPv3 enables a host to join a specified multicast group that excludes a specified multicast source
- IGMPv3 adds Request-to-Send and Clear-to-Send messages between source and local IGMP queries
- IGMPv3 enables a host to join a specified multicast group that includes a specified multicast source
-
To deploy multicast video applications on your private internal network, you need to use private multicast IP addresses on the network.
Which range of IP addresses can be used?
- 226.0.0.0 – 226.255.255.255
- 241.0.0.0 – 241.255.255.255
- 224.0.0.0 – 224.255.255.255
- 239.0.0.0 – 239.255.255.255
- 240.0.0.0 – 254.255.255.255
-
Which of the following statements regarding Security Association (SA) in IPsec is false?
- An IPsec VPN connection can be established only when the bidirectional SA exists between IPsec peers
- An SA is identified by three parameters: security parameter index (SPI), destination IP address, and security protocol ID (AH or ESP)
- You can run the display ipsec sa command to view the encryption algorithm used and traffic of interest between IPsec peers
- IPsec can only use symmetric encryption algorithms to encrypt and decrypt data
-
As shown in the figure, the routers load balances the traffic between Branch network 1 and Branch network 2. In this case, URPF in loose mode must be configured on a physical interface to defend against attacks using spoofed source IP addresses.
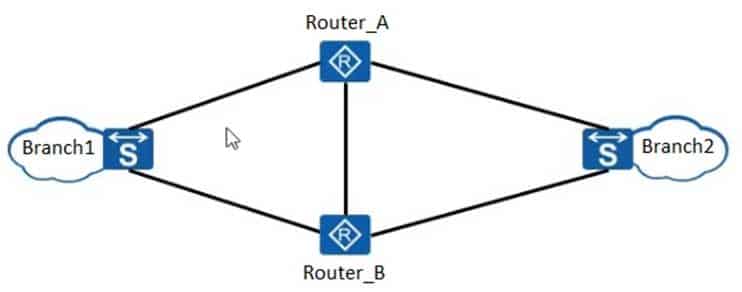
H12-261 HCIE-R&S (Written) (Huawei Certified Internetwork Expert-Routing & Switching) Part 12 Q05 048 - TRUE
- FALSE
-
As shown in the figure, two IPv6 networks need to access the IPv4 network. An IPsec tunnel needs to be established between the two IPv6 networks to enable communication. Which of the following encapsulation modes can meet the preceding requirements?
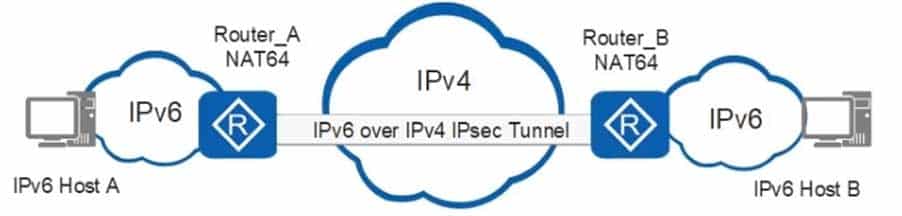
H12-261 HCIE-R&S (Written) (Huawei Certified Internetwork Expert-Routing & Switching) Part 12 Q06 049 - AH+ transmission mode
- AH+ tunnel mode
- ESP+ tunnel mode
- All the preceding options are incorrect
-
Which of the following statements regarding 802.1X authentication, RADIUS authentication, and HWTACACS authentication are true?
- A user cannot be authenticated by both RADIUS authentication and 802.1X authentication.
- A user cannot be authenticated by both RADIUS authentication and HWTACACS authentication.
- A user can be authenticated by both RADIUS authentication and HWTACACS authentication. This is more secure than using just one authentication method.
- Users can access a network through 802.1X authentication, and can be authenticated through RADIUS authentication.
-
A family user has subscribed to a bandwidth of 10 Mbit/s. To improve user experience, the carrier ensures a rate of 12 Mbit/s during tests. If token bucket technology is used to cope with this requirement, which of the following methods is optimal?
- cir 10000 cbs 12000 pbs 12000
- cir 8000 pir 12000
- cir 10000 pir 12000
- cir 10000 cbs 10000 pbs 12000
-
A new office needs to use a router as the DHCP server. Which of the following items need to be configured when the DHCP server is configured to provide the DHCP service for the office?
- Manually binding a specified IP address to a specified terminal
- Timeout period of a ping packet
- Excluding idle IP addresses from the DHCP server
- Startup file of the DHCP server
- DHCP address pool
-
Which of the following statements regarding VRRP is true?
- Both VRRPv2 and VRRPv3 support authentication
- VRRPv3 does not support authentication, whereas VRRPv2 supports authentication
- The VRRP priority of the master IP address owner is 255. Therefore, the priority can be a value in the range from 0 to 254.
- VRRPv2 only applies to an IPv4 network, and VRRPv3 applies only to an IPv6 network
-
In a BGP EVPN distributed gateway scenario, which of the following packet types is required to implement VM migration?
- Type 1
- Type 2
- Type 3
- Type 5
- Type 4
-
The precedence field in VLAN (802.1Q) data encapsulation has six bits.
- TRUE
- FALSE
-
On a switch with factory default settings, its MAC address table is empty. Host A connected to the switch sends the first unicast data frame. What operation will the switch perform after receiving the data frame?
- The switch discards the data frame
- The switch records the source MAC address of the data frame and floods the data frame out of all interfaces except the one it received the frame
- The switch buffers the data frame and forwards the data frame after the destination host sends a data frame
- The switch forwards the data frame out through an interface based on the destination MAC address of the data frame
-
Which of the following configurations can be used to prevent users from connecting a hub to an access port on a switch allowing multiple device to access the network?
-

H12-261 HCIE-R&S (Written) (Huawei Certified Internetwork Expert-Routing & Switching) Part 12 Q14 050 -

H12-261 HCIE-R&S (Written) (Huawei Certified Internetwork Expert-Routing & Switching) Part 12 Q14 051 -

H12-261 HCIE-R&S (Written) (Huawei Certified Internetwork Expert-Routing & Switching) Part 12 Q14 052 -
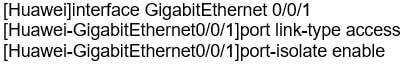
H12-261 HCIE-R&S (Written) (Huawei Certified Internetwork Expert-Routing & Switching) Part 12 Q14 053
-
-
On a LAN running STP (802.1D), which of the following parameters will not be received by a non-root switch from the root switch?
- Forward delay
- Hold time
- MaxAge
- Hello time
- Root Path cost
-
When a router receives an LSP on a broadcast network or a P2P network enabled with IS-IS, the router needs to send a PSNP to ensure LSDB synchronization.
- TRUE
- FALSE
-
Which of the following statements regarding OSPFv3 Link-LSAs is true?
- The Link-LSA contains both the link-local address and all IPv6 prefixes of the interface
- The Link-LSA contains both the link-local address of the interface and all IPv6 prefixes of the same area on the router
- The Option field exists in an LSA header rather than the data area of a Link-LSA
- If the PrefixOptions field of a prefix in the Link-LSA is 0x00, the prefix is not involved in the IPv6 unicast calculation
-
Assuming three routers (A, B, and C) uses BGP as the routing protocol. A sends Update packets to B and B sends the Update packets to C. Which of the following attributes meet the following two conditions?
(1) A can select whether to carry this attribute in Update packets.
(2) If B receives an Update packet carrying this attribute, B still advertises the Update packet to C although B cannot identify this attribute. Then, Router C may identify and use this attribute.
- Multi_Exit_Disc
- Local_Pref
- Community
- Aggregator
-
Which of the following statements regarding deploying IS-IS in an IPv6 environment is true?
- On a broadcast network, the IPv4 DIS priority and IPv6 DIS priority can be set, respectively.
- If the isis silent command is run on an IS-IS interface, the interface does not send but receives IS-IS packets.
- On a broadcast network, if each router supports both IPv4 and IPv6, the IPv4 DIS and IPv6 DIS must be the same device.
- By default, the DIS priority of Level-1 and Level-2 broadcast interfaces is 1.
-
Which of the following statements regarding MP-BGP is false?
- The MP_UNREACH_NLRI attribute of Update packets does not contain path information
- MP_REACH_NLRI and MP_UNREACH_NLRI are optional transitive attributes
- The complete MP_REACH_NLRI attribute structure contains the address family, next hop, and prefix information
- MP-BGP can be used to allocate labels
Subscribe
0 Comments
Newest