H12-711 : HCNA-Security-CBSN (Huawei Certified Network Associate – Constructing Basic Security Network) : Part 02
H12-711
-
VPN tunnel technology refers to through encryption algorithm (such as DES, 3DE5) to achieve data transmitted in the network will not be intercepted.
- True
- False
-
Which VPN access modes are suitable for mobile office workers? (Choose three.)
- GRE VPN
- L2TP VPN
- SSL VPN
- L2TP over IPsec
-
In the GRE configuration environment, which of the following interface or IP address is the local GRE device configuration of the end private network route required to point to? (Choose two.)
- Tunnel Interface
- External networks (Internet) Interface
- Tunnel interface IP address
- External network (Internet) interface IP address
-
Which of the following belongs to multi-channel protocol?
- FTP
- Telnet
- HTTP
- SMTP
-
What problem does IPsec IKE aggressive mode mainly solve?
- solve the problem of slow negotiation on both ends of the tunnel
- solve the security problem in the process of negotiation
- solve NAT traversal problem
- solve because of uncertain originator source address cannot select pre-shared key problem
-
Which statement about NAT is wrong? (Choose two.)
- NAT Outbound refers to conversion to the source IP address, NAT Inbound refers to conversion to the destination IP address
- NAT Inbound command and NAT Server command have the same functions, can choose to configure according to personal preference
- Outbound direction NAT can support the following application modes: one-on-one, many-to-many and many-to-one
- NAT technology can support multi-channel protocols such as FTP and other standard multi-channel protocol
-
When you configure a firewall between the domain security policy, if the 192.168.0.0/24 network segment is set to match object, the following configuration, which is correct? (Choose two.)
- policy 1
policy source 192.168.0.0 mask 255.255.255.0 - policy 1
policy source 192.168.0.0 255.255.255.0 - policy 1
policy source 192.168.0.0 mask 0.0.0.255 - policy 1
policy source 192.168.0.0 0.0.0.255
- policy 1
-
HRP (Huawei Redundancy Protocol) Protocol to backup the connection state of data includes:
- TCP/UDP sessions table
- Server Map table
- The dynamic blacklist
- The routing table
-
In a Firewall hot standby configuration, HRP key configuration includes which of the following? (Choose three.)
- Enable HRP backup
hrp enable - Enabling fast backup session summary
hrp mirror session enable - Specifies the heartbeat port
hrp interface interface-type interface-number - Preemption delay
hrp preempt [delay interval]
- Enable HRP backup
-
For E1/CE1 configuration:
1, configure the virtual serial port IP address
2, configure the virtual serial port link layer protocol
3, configure E1 working mode
4, configure the timeslot bundlingThe correct configuration sequence is:
- 1-2-3-4
- 2-1-3-4
- 3-4-2-1
- 4-3-2-1
-
What do VLAN port types include? (Choose three.)
- Access Port
- Trunk port
- Hybrid port
- Ethernet port
-
Which scenarios does IPSec WEB configuration wizard not support?
- Gateway to Gateway
- Center Gateway
- Branch Gateway
- Host and Host
-
Which of the Policy Center functional areas is wrong?
- Pre-authentication domain refers to the client through the identity authentication before access to the area
- Post-authentication domain refers to the client can access through the security certification area
- Isolation domain refers to the client after authenticated must have access to the area
- Isolation domain refers to the client security authentication failed the required access area
-
In the firewall, detect ftp command to set in which mode? (Choose two.)
- System Model
- Interface Mode
- Domain Model
- Inter-Domain mode
-
In most scenarios, NAT Inbound is used to the enterprise private network users to access the Internet scenario.
- True
- False
-
What are common hash algorithms? (Choose two.)
- DES
- AES
- MD5
- SHA-1
-
In the environment of GRE configuration, which of the following statements are true? (Choose three.)
- In order to make the ends of the tunnel forward data packets normally, the devices of both ends are configured routing which through the Tunnel interface
- If both ends enable the configuration of keyword verification, the keyword must be the same
- When the local device send data packets, by identifying the protocol field value of IP header for GRE to determine whether send the data packet to GRE module for processing
- When the opposite end receives data packets, by identifying the protocol field value of IP header for GRE to determine whether send the data packet to GRE module for processing
-
Execute the command on the Firewall and display the above information.
Which of the following description is correct? (Choose two.)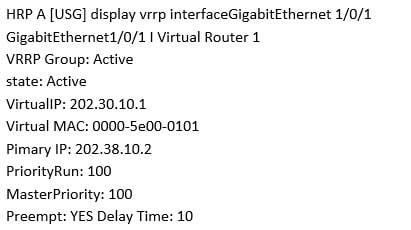
H12-711 HCNA-Security-CBSN (Huawei Certified Network Associate – Constructing Basic Security Network) Part 02 Q18 001 - This Firewall VGMP group status is Active
- The virtual IP address of the firewall G1/0/1 interface is 202.30.10.2
- The priority of the VRRP backup group of the firewall VRID 1 is 100
- If the master device fails, it will not switch
-
Which of the following are the key features of the state inspection firewall include?
- The processing speed is slow
- Follow-up packet processing performance is excellent
- Can only detect network layer
- Do the packet filtering detection to each packet
-
In IPSEC VPN, which of the following scenarios can be applied by tunnel mode?
- between the host and the host
- between hosts and security gateways
- between security gateways
- between tunnel mode and transport mode
H12-711
Subscribe
0 Comments
Newest