H12-711 : HCNA-Security-CBSN (Huawei Certified Network Associate – Constructing Basic Security Network) : Part 03
H12-711
-
Which of the following statement about the NAT is wrong?
- NAT technology can effectively hide the costs of the LAN; it is an effective network security protection technology
- Address Translation can follow the needs of users, providing FTP, WWW, Telnet and other services outside the LAN
- Some application layer protocols carry IP address information in the data, but also modify the IP address information in the data of the upper layer when they are as NAT
- For some non-TCP, UDP protocols (such as ICMP, PPTP), unable to do the NAT translation
-
As shown, when configuring the point-to-multipoint scenarios, the headquarters network segment is 10.1.1.0/24, the segment of branch 1 is 10.1.2.0/24, of branch 2 is 10.1.3.0/24.
About the protected data flow configuration which defined by headquarters and branch offices, which of the following combinations can be the full matched requirements?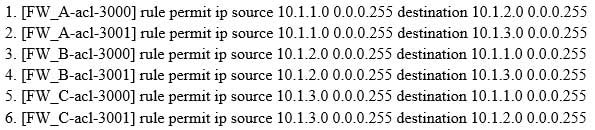
H12-711 HCNA-Security-CBSN (Huawei Certified Network Associate – Constructing Basic Security Network) Part 03 Q02 002 
H12-711 HCNA-Security-CBSN (Huawei Certified Network Associate – Constructing Basic Security Network) Part 03 Q02 003 - 1 2
- 1 2 3 5
- 1 2 4 6
- 3 4 5 6
-
Which of the following addresses can be used for web management address of USG product? (Choose three.)
- Interface Address
- Sub-interface address
- Slave IP address of the interface
- AUX interface address
-
Which of the following statement about Internet user group management is wrong?
- Each user group can include multiple users and user group
- Each user group can belong to more than one parent user group
- There is a default user group in the system; the user group is also the default authentication domain
- Each user belongs to at least one user group, who can also belong to multiple user groups
-
In SSL handshake protocol, what is the role of Server Key Exchange message?
- server key exchange message indicates that the server has finished sending all the information
- in the server key exchange message, it contains set of parameters required for completing key exchange
- it contains an X.509 certificate in server key exchange message, the public key is contained in the certificate, which is issued to the client to verify signatures or to encrypt messages when key exchange
- in the server key exchange message, it contains the negotiated CipherSuite which is copied to the state of the current connection
-
About the default security zones of USG series security firewall, which of the following statement is correct?
- The default security zone can be deleted
- The security level of the default security zone can be modified
- The default security zone cannot be deleted, but can modify the security level
- There are four default security zones
-
Administrators want to clear the current session table. Which of the following command is correct?
- clear firewall session table
- reset firewall session table
- display firewall session table
- display session table
-
When using the web configuration type to do the configuration, the correct statements as following are: (Choose two.)
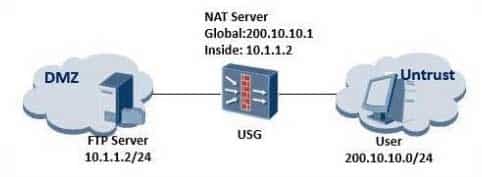
H12-711 HCNA-Security-CBSN (Huawei Certified Network Associate – Constructing Basic Security Network) Part 03 Q08 004 - When configuring the inter-domain security policy, it needs to set the source security area as Untrust, the target security area as DMZ
- When configuring the NAT Server, the internal address is 10.1.1.2, the external address is 200.10.10.1
- When configuring the inter-domain security policy, setting the source security area as DMZ, the target security area as Untrust
- When configuring the NAT server, the internal address is 200.10.10.1, the external address is 10.1.1.2
-
In the SSL handshake protocol, which of the following message is optional? (Choose two.)
- Server Key Exchange
- ChangeCipherSpec
- Certificate verify
- ServerHelloDone
-
What are the following values can be set as in USG series firewall security level definition from the security zone? (Choose two.)
- 150
- 100
- 80
- 40
-
What are the classification of USG firewall user authentication? (Choose three.)
- no authentication
- password authentication
- single sign-on (sso)
- the fingerprint authentication
-
In the inter-domain security firewall policy, which of the following data stream is not Outbound direction?
- Data flow from the DMZ to Untrust zone
- Data flow from the Trust zone to the DMZ zone
- Data flow from Trust area to the Untrust zone
- Data flow from the Trust zone to the Local zone
H12-711
Subscribe
0 Comments
Newest